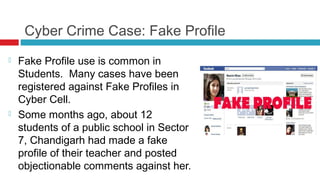
Cyber crime is becoming common among students in India. India ranks 5th globally for reported cyber crimes, with states like Andhra Pradesh and Maharashtra experiencing many cases. Common cyber crimes among students include creating fake profiles of others online, hacking passwords, cyber bullying, and falling victim to phishing scams. Teachers must educate students on safe internet practices and the consequences of cyber crimes to help prevent such incidents.