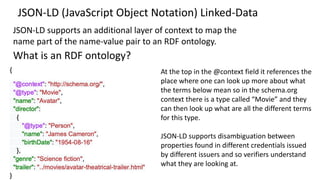
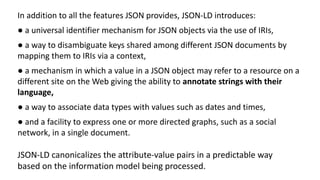
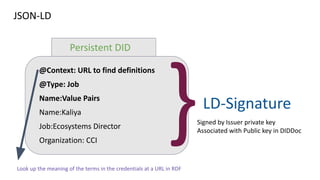
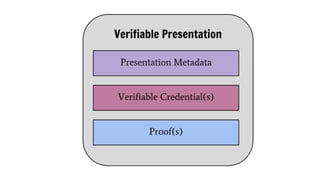
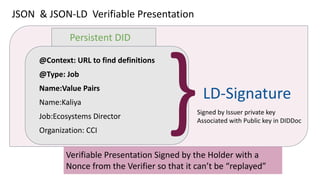
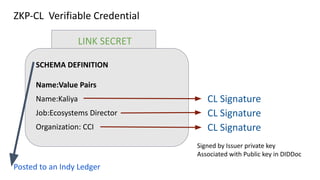
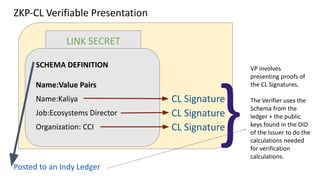
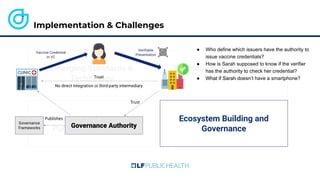
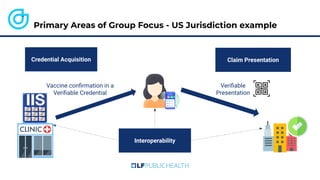
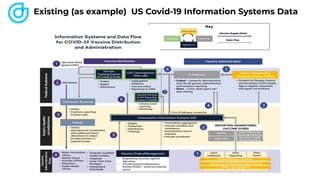
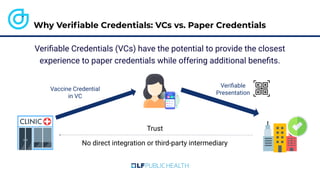
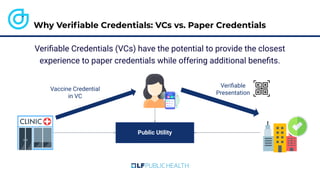
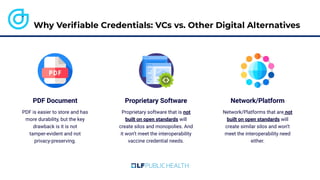
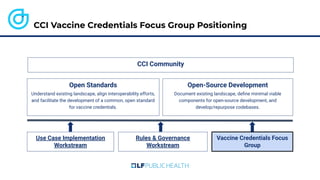
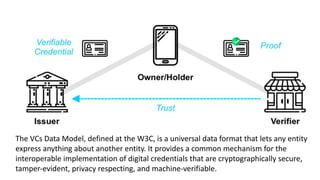
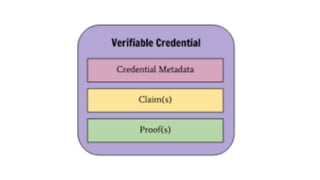
The document discusses the technical aspects of verifiable credentials (VCs) and their implementation, particularly in the context of the Covid-19 Credentials Initiative. It details the various data formats and cryptographic methods used for secure and privacy-respecting digital credentials, emphasizing the role of JSON-LD and zero-knowledge proofs in achieving selective disclosure. The initiative aims to create open standards and interoperability for vaccine credentials among public health authorities and commercial entities.





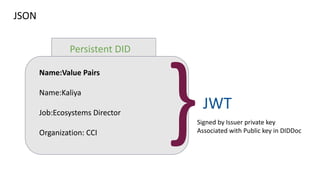
![What is JWT Claim?
JWT approach to determining the meaning of claim terms in credentials.
There is an IANA registry for JWT claims as a first place to look for JWT claim
definitions.
If the claim name isn’t in the IANA register, then the claim can be given a “give it a
public name (i.e., a URI), [or] a local name (i.e., any string)”. The meaning of the
terms is guessed at or decided between the issuers and verifiers.](https://image.slidesharecdn.com/verifiablecredentialsexplainedbycci-210217173909/85/Verifiable-credentials-explained-by-CCI-8-320.jpg)