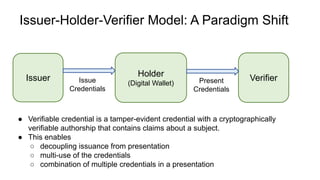
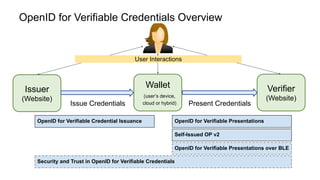
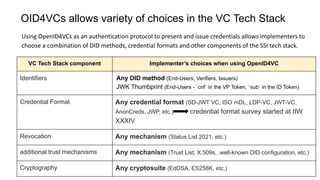
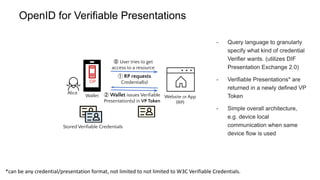
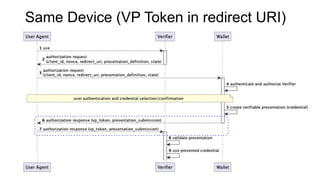
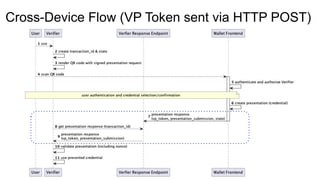
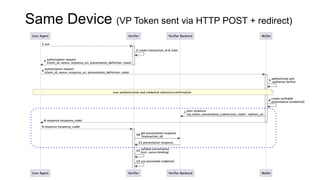
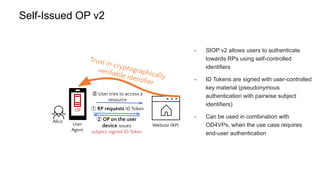
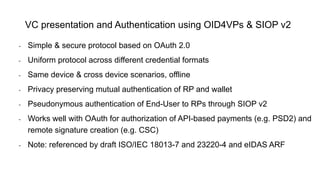
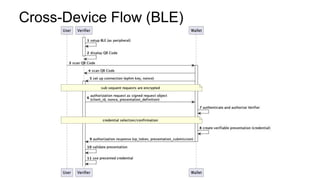
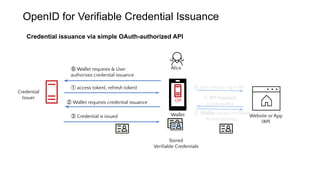
OpenID for Verifiable Credentials is the next generation of OpenID that enables issuing and presenting verifiable credentials in a decentralized manner. It uses an issuer-holder-verifier model where credentials are issued to a holder (digital wallet) and then presented to a verifier (website). This allows decoupling of issuance from presentation and reuse of credentials. OpenID for Verifiable Credentials specifications provide standards for credential issuance, presentation, and authentication that build upon OAuth 2.0 and OpenID Connect to enable a variety of decentralized identity use cases.






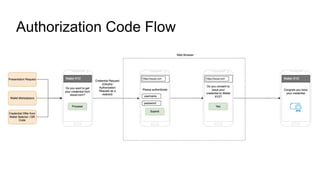
![Presentation Request
{
"id": "example_ldp_vc",
"input_descriptors": [
{
"id": "id_card_credential",
"format": {
"ldp_vc": {
"proof_type": [
"Ed25519Signature2018"
]
}
},
"constraints": {
"fields": [
{
"path": [
"$.type"
],
"filter": {
"type": "array",
"contains": {
"const": "IDCredential"
}
}
}
]
}
}
]
}
GET /authorize?
response_type=vp_token
&client_id=https%3A%2F%2Fclient.example.org%2Fcb
&redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb
&presentation_definition=...
&nonce=n-0S6_WzA2Mj HTTP/1.1
Host: wallet.example.com
presentation_definition](https://image.slidesharecdn.com/openidforverifiablecredentials04231-230509111607-be38fabf/85/OpenID-for-Verifiable-Credentials-IIW-36-17-320.jpg)
![Presentation Response
{
"definition_id": "example_ldp_vc",
"id": "example_ldp_vc_presentation_submission",
"descriptor_map": [
{
"id": "id_credential",
"path": "$",
"format": "ldp_vp",
"path_nested": {
"format": "ldp_vc",
"path": "$.verifiableCredential[0]"
}
}
]
}
{
"@context": [
"https://www.w3.org/2018/credentials/v1"
],
"type": [
"VerifiablePresentation"
],
"verifiableCredential": [
{
"@context": [
"https://www.w3.org/2018/credentials/v1",
"https://www.w3.org/2018/credentials/examples/v1"
],
"id": "https://example.com/credentials/1872",
"type": [
"VerifiableCredential",
"IDCredential"
],
"issuer": {
"id": "did:example:issuer"
},
"issuanceDate": "2010-01-01T19:23:24Z",
"credentialSubject": {
"given_name": "Max",
"family_name": "Mustermann",
"birthdate": "1998-01-11",
"address": {
"street_address": "Sandanger 25",
"locality": "Musterstadt",
"postal_code": "123456",
presentation_submission
vp_token
HTTP/1.1 302 Found
Location: https://client.example.org/cb#
presentation_submission=...
&vp_token=...](https://image.slidesharecdn.com/openidforverifiablecredentials04231-230509111607-be38fabf/85/OpenID-for-Verifiable-Credentials-IIW-36-18-320.jpg)







![Example: Issued Credential
{
"iss": "https://credential-issuer.example.com",
"iat": 1516239022,
"exp": 1516247022,
"type": "Identity",
"_sd": [
"UiuRGkTW7e_5UQauGeQRQdF8u3WYevS4Fs0IuB_DgYM",
"tmPlXq0MID-oRXbUNHyoVZrc9Qkm8cwJTohVyOVlUgQ",
"vTz0JI103v4k4pKIloT83Yzi33L1SdZlWBPmsfJBefk"
],
"_sd_alg": "sha-256",
"cnf": {
"jwk": {
"kty": "EC",
"crv": "P-256",
"x": "TCAER19Zvu3OHF4j4W4vfSVoHIP1ILilDls7vCeGemc",
"y": "ZxjiWWbZMQGHVWKVQ4hbSIirsVfuecCE6t4jT9F2HZQ"
}
}
}](https://image.slidesharecdn.com/openidforverifiablecredentials04231-230509111607-be38fabf/85/OpenID-for-Verifiable-Credentials-IIW-36-33-320.jpg)