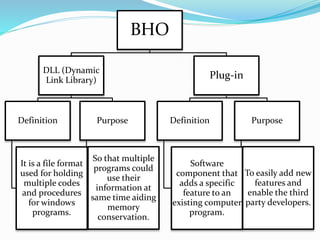
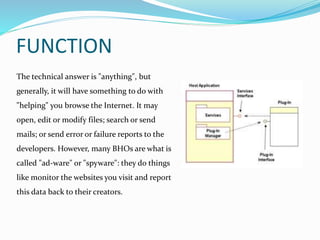
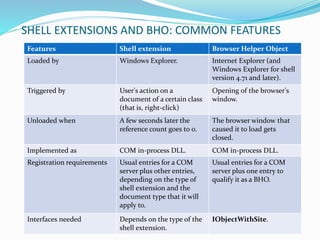
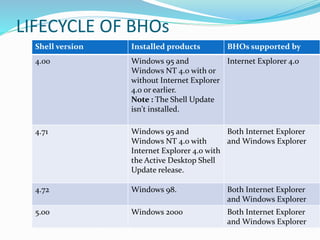
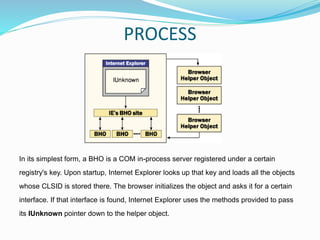
Browser Helper Objects (BHO) are components of Microsoft's Internet Explorer designed to enhance browser functionality as add-ins. They can run automatically at browser start-up, often installed by other software, facilitating tasks such as file modification or web browsing enhancement, but may also pose security risks by acting as malware or spyware. Effective management and removal of BHOs, including malicious variants, can be performed using specialized tools and registry management techniques.








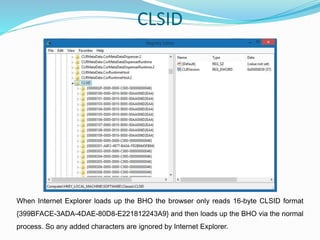

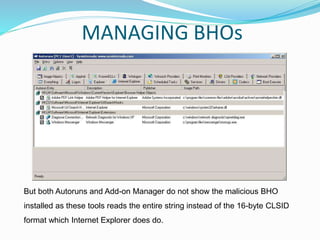






![Now when the malicious BHO (e.g. flashcpx.dll) gets installed it does something clever to
hide its presence yet still manage to load up. As you can see below the CLSID string is
longer than usual. The added characters cause most tools not to list out the BHO even
though Internet Explorer loads it up.
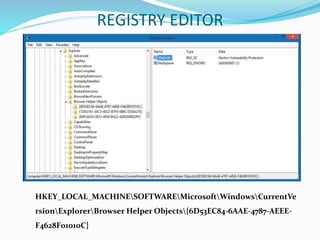
HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowserHelperObj
ects{399BFACE-3ADA-4DAE-80D8-E221812243A9}80D8-E221812243A9}
Since the string is longer than recommended when it goes to find the CLSID key in
[HKEY_LOCAL_MACHINESOFTWAREClassesCLSID] the key is not found and
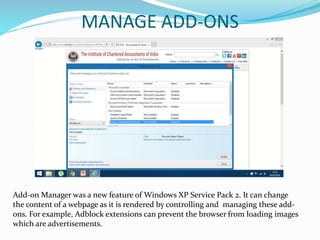
therefore the DLL module does not get listed. Quite odd that “manage add-ons” is part of
Internet Explorer but does not list it.
MALICIOUS BHO](https://image.slidesharecdn.com/newmicrosoftpowerpointpresentation-160309040602/85/Browser-Helper-Object-31-320.jpg)




