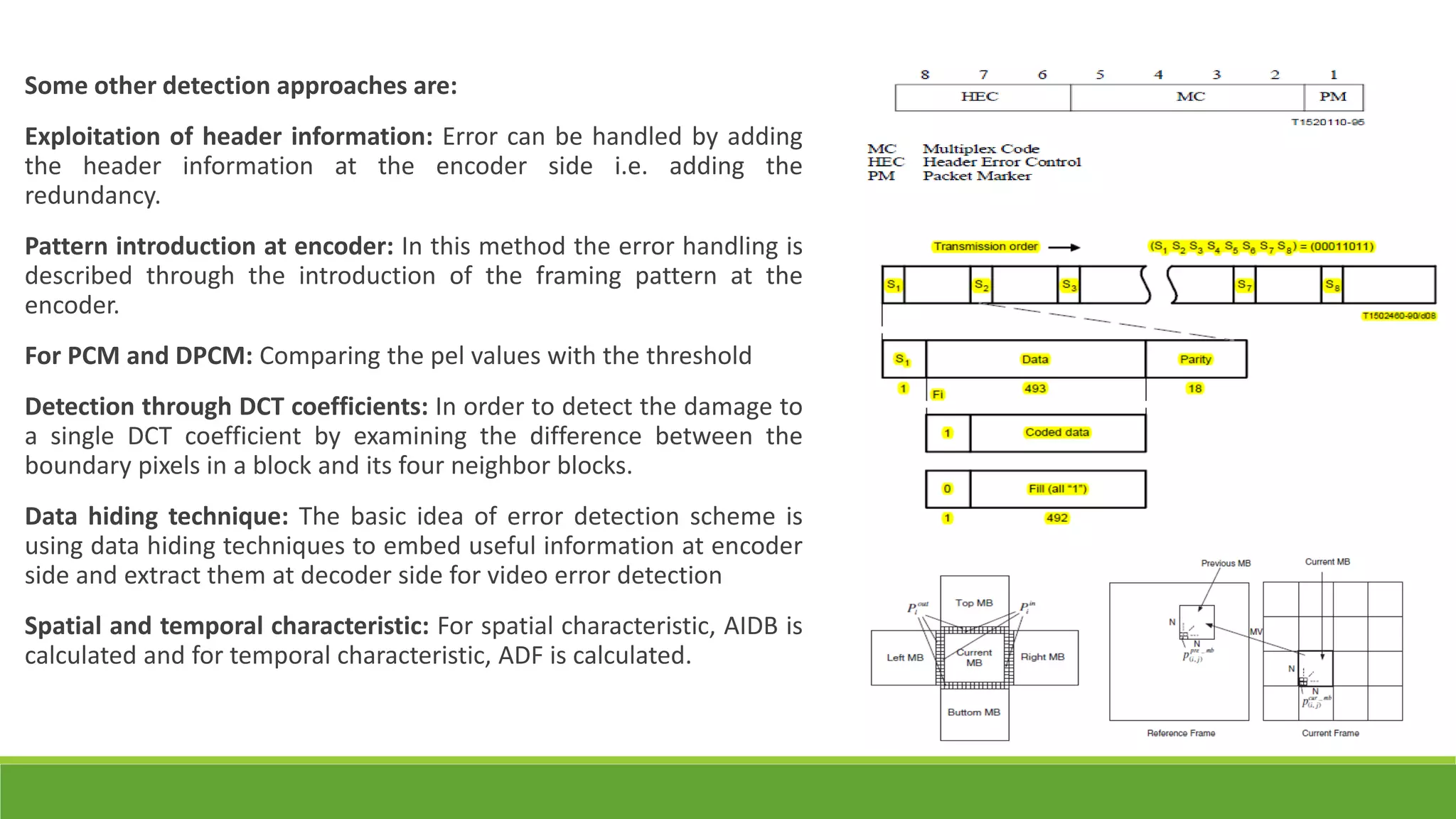
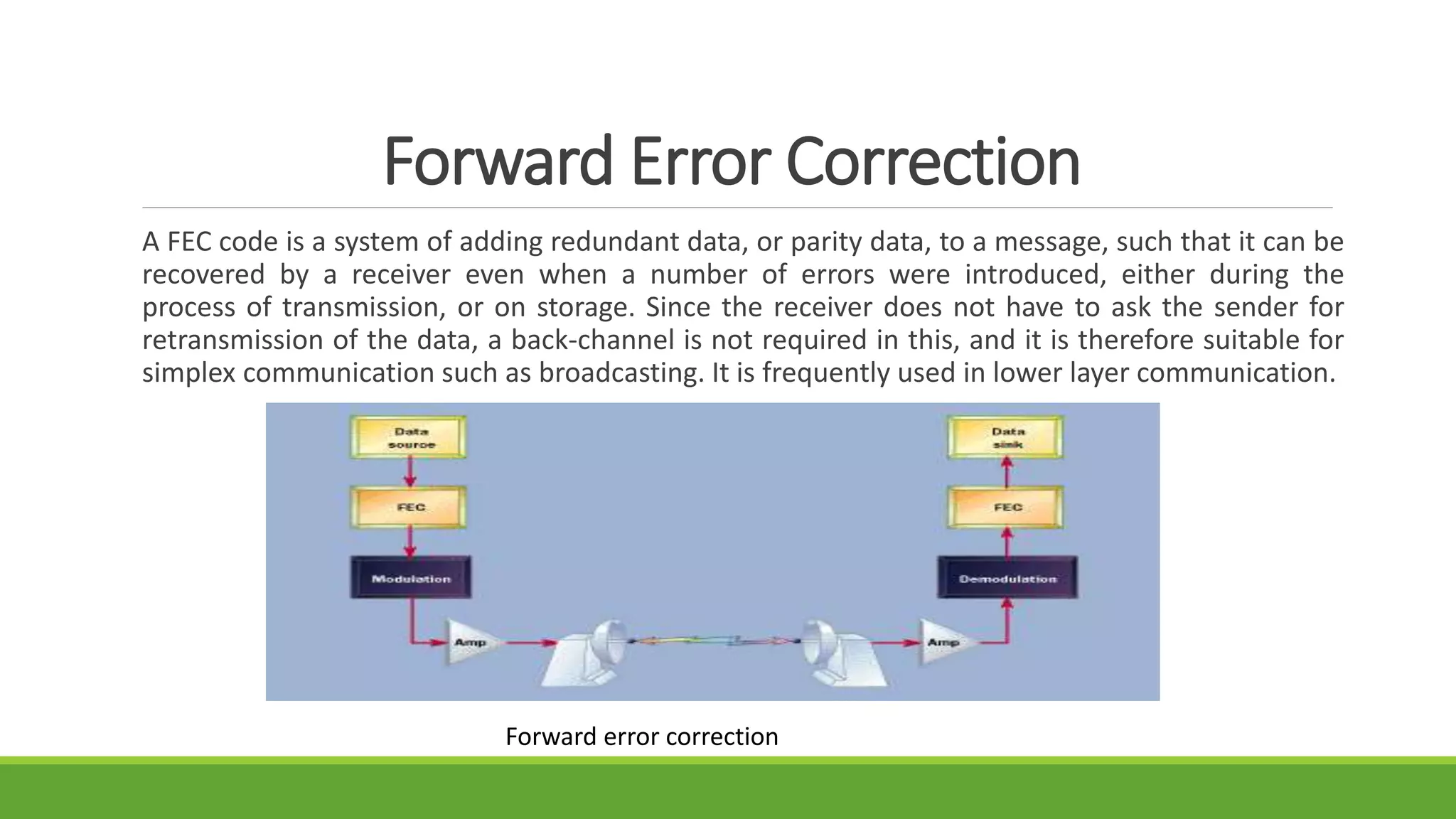
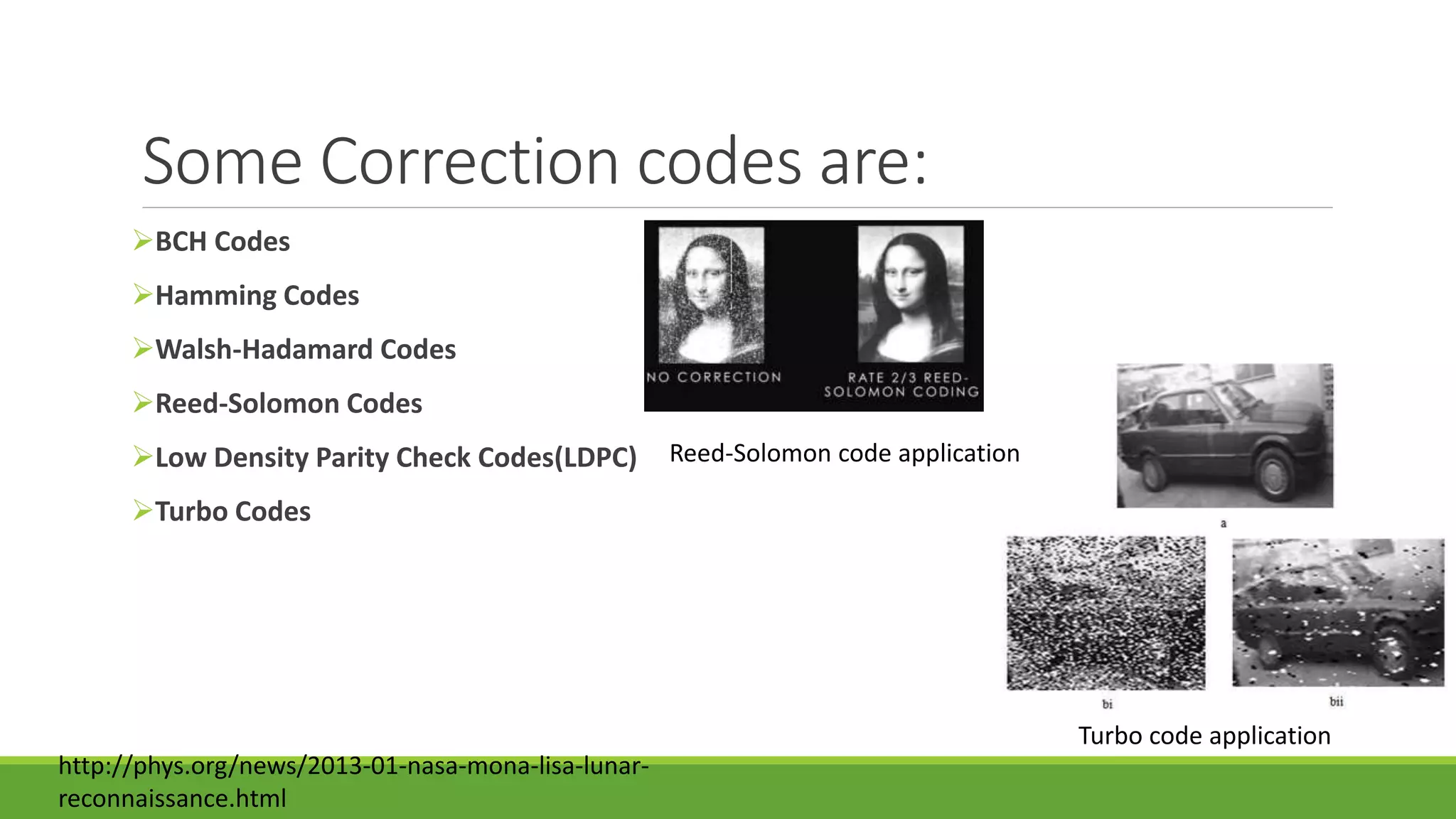
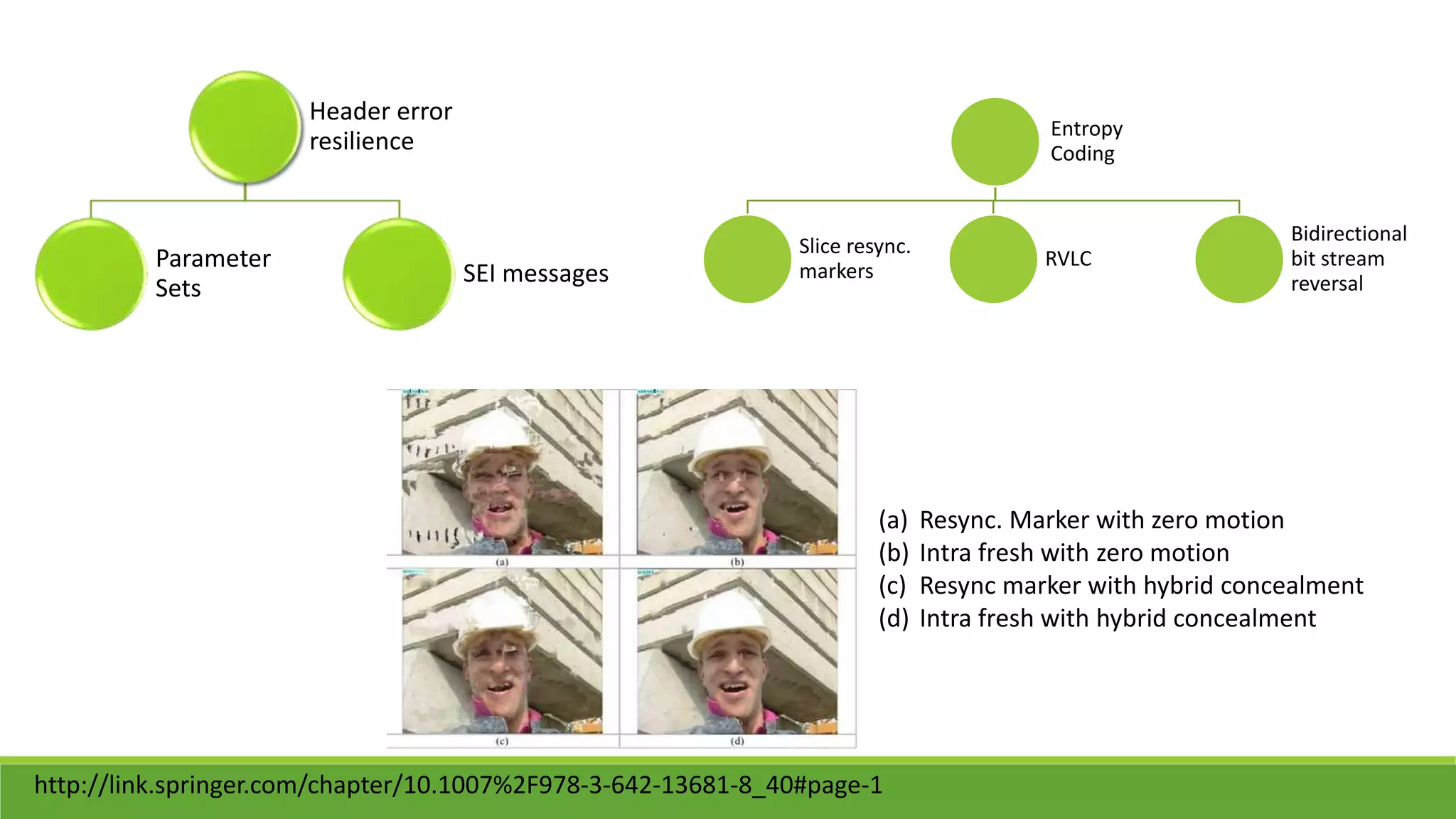
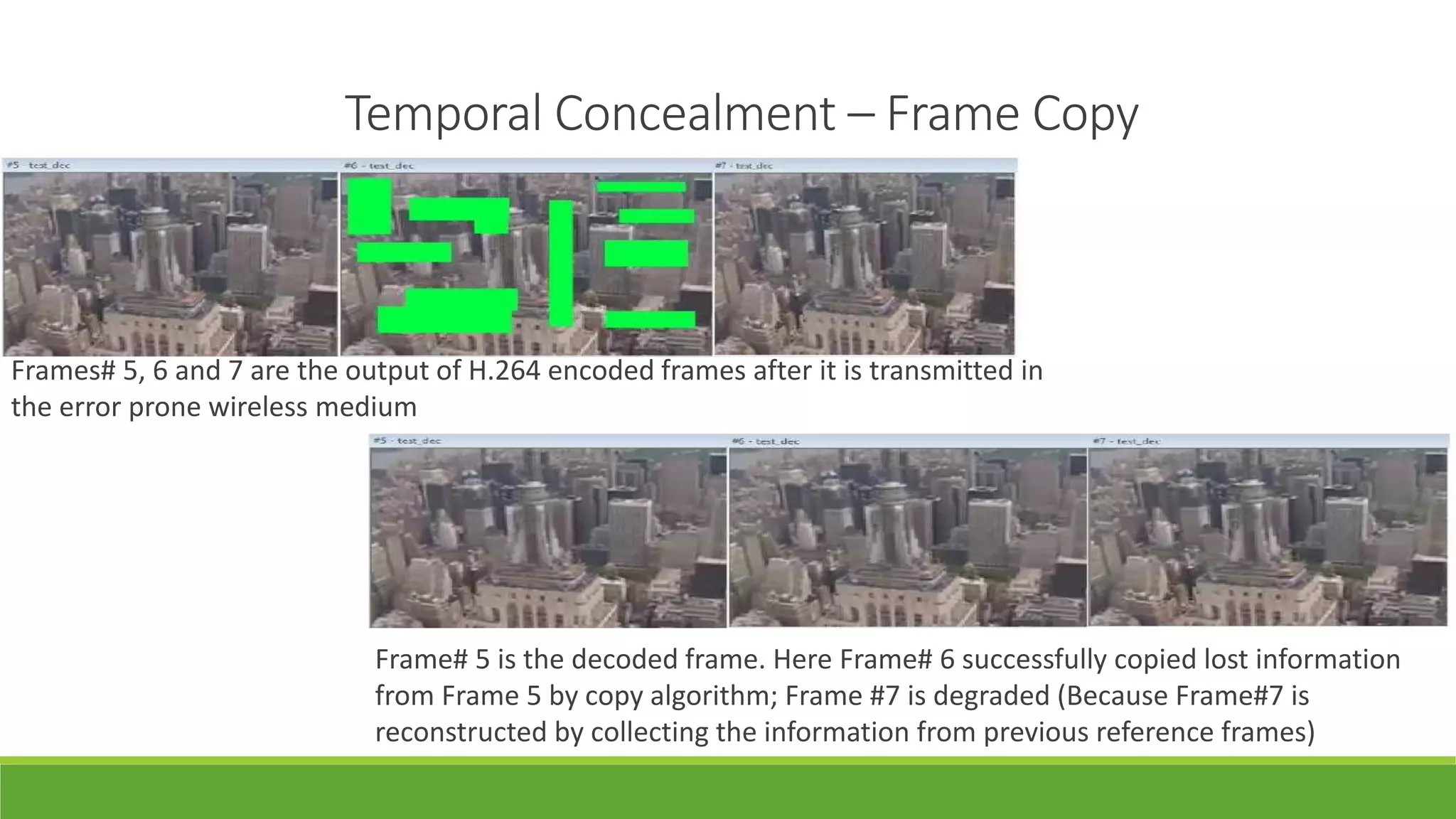
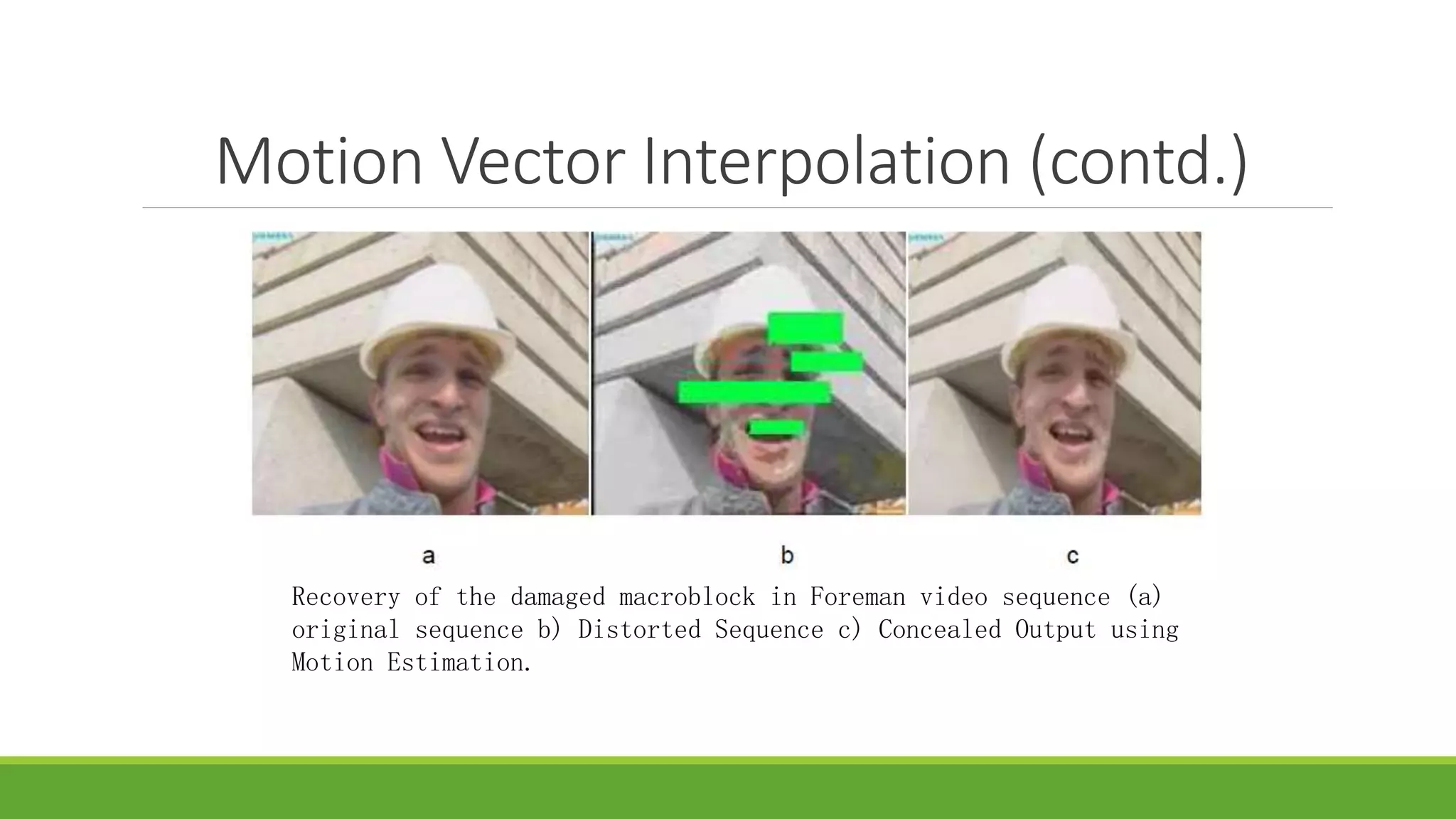
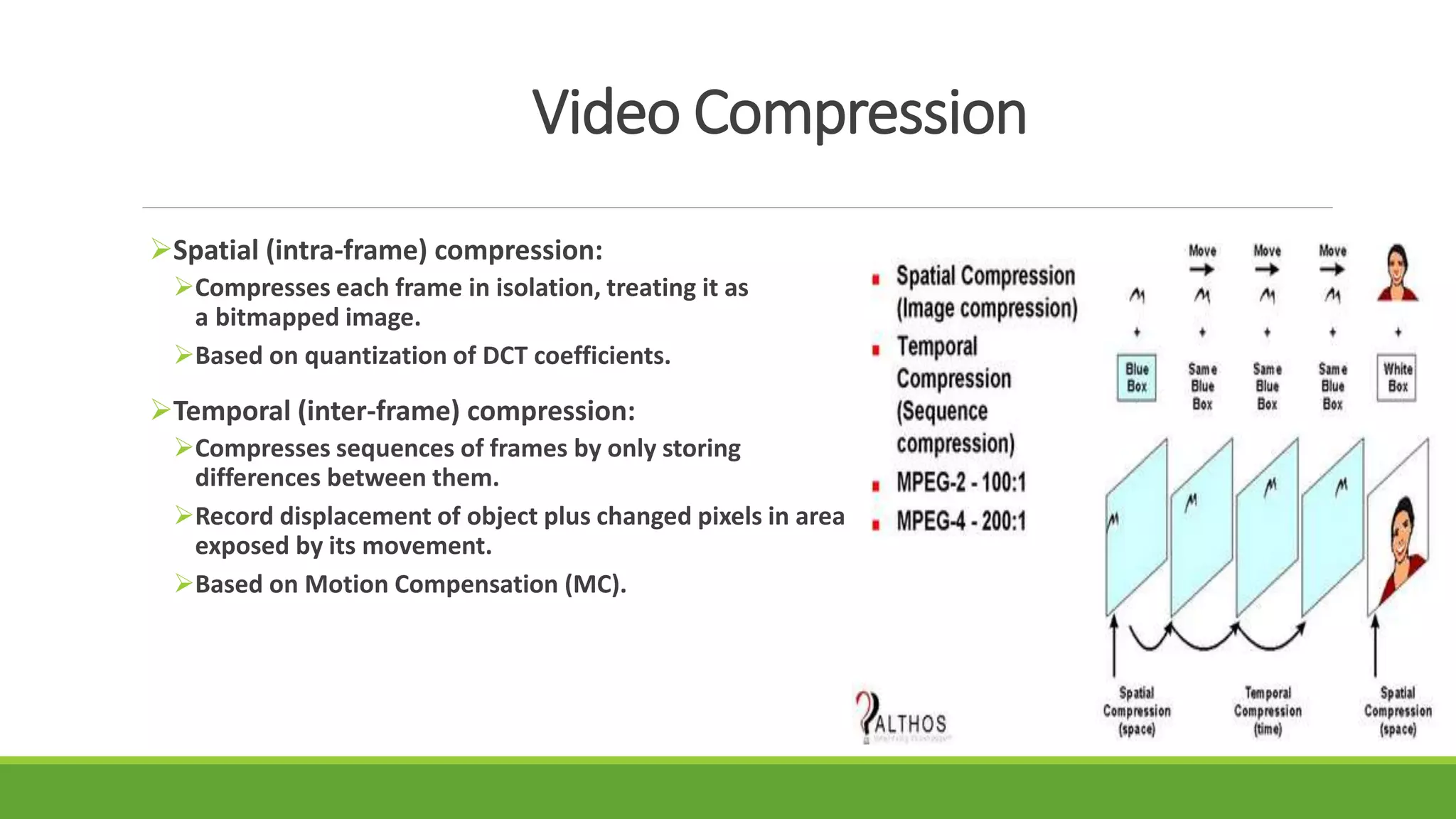
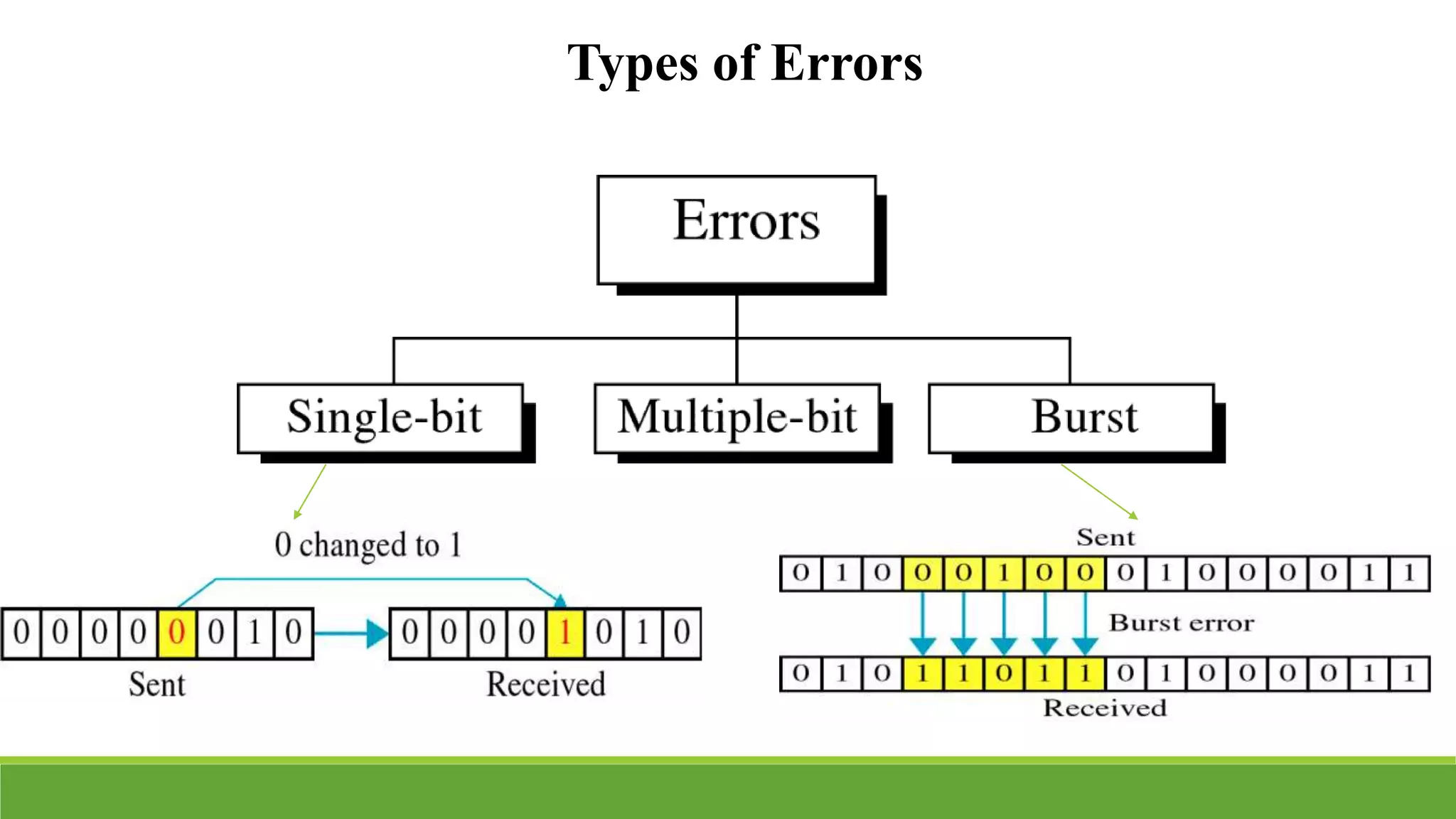
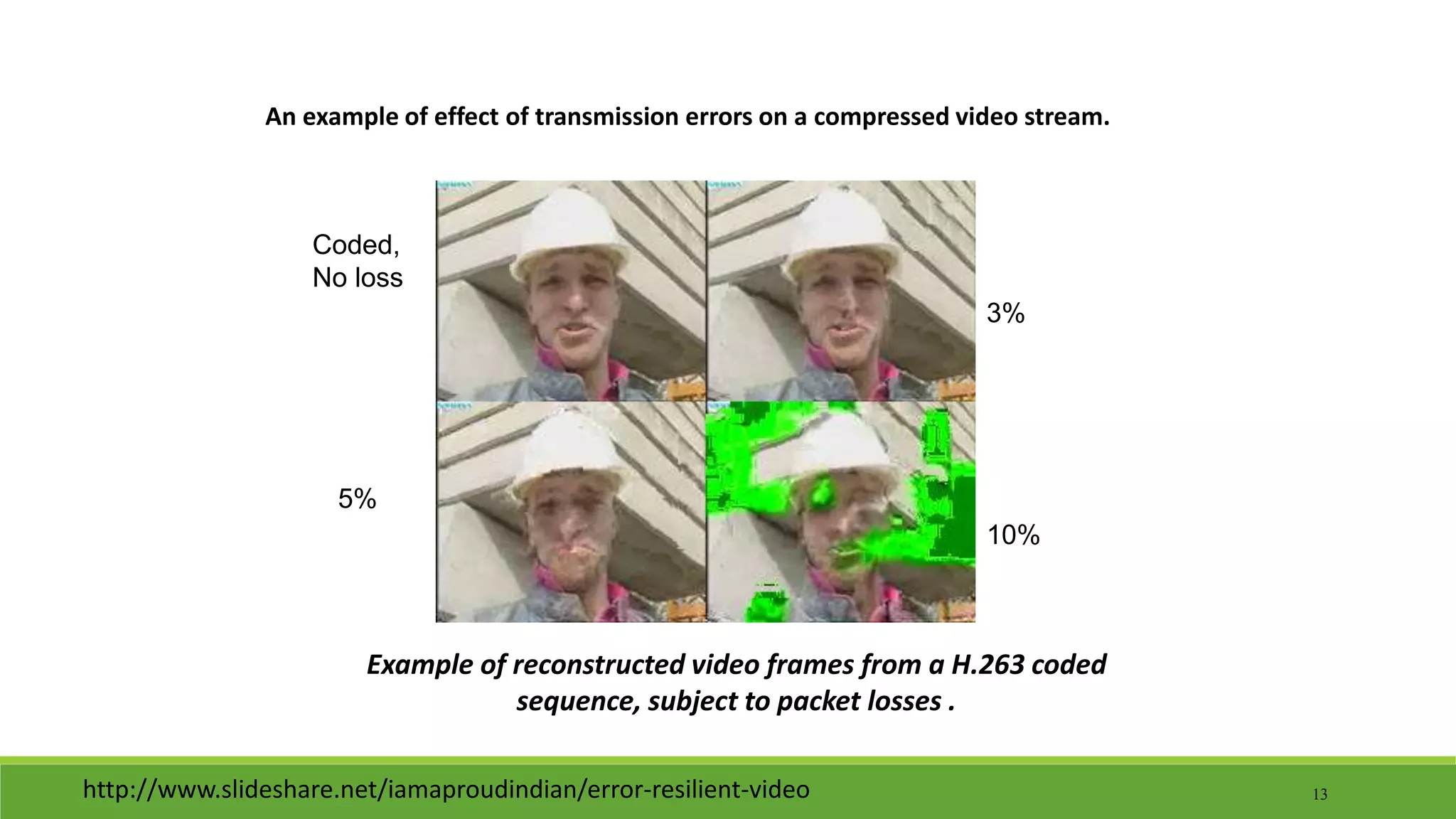
The seminar on error control techniques for video communications covers the importance of video compression and the challenges faced in video transmission due to network constraints, quality of service, and error types. It discusses error detection and correction methods, including forward error correction and various concealment techniques to address packet loss and maintain video quality. Finally, it highlights the significance of real-time error concealment strategies as crucial for effective video communication, especially in error-prone environments.





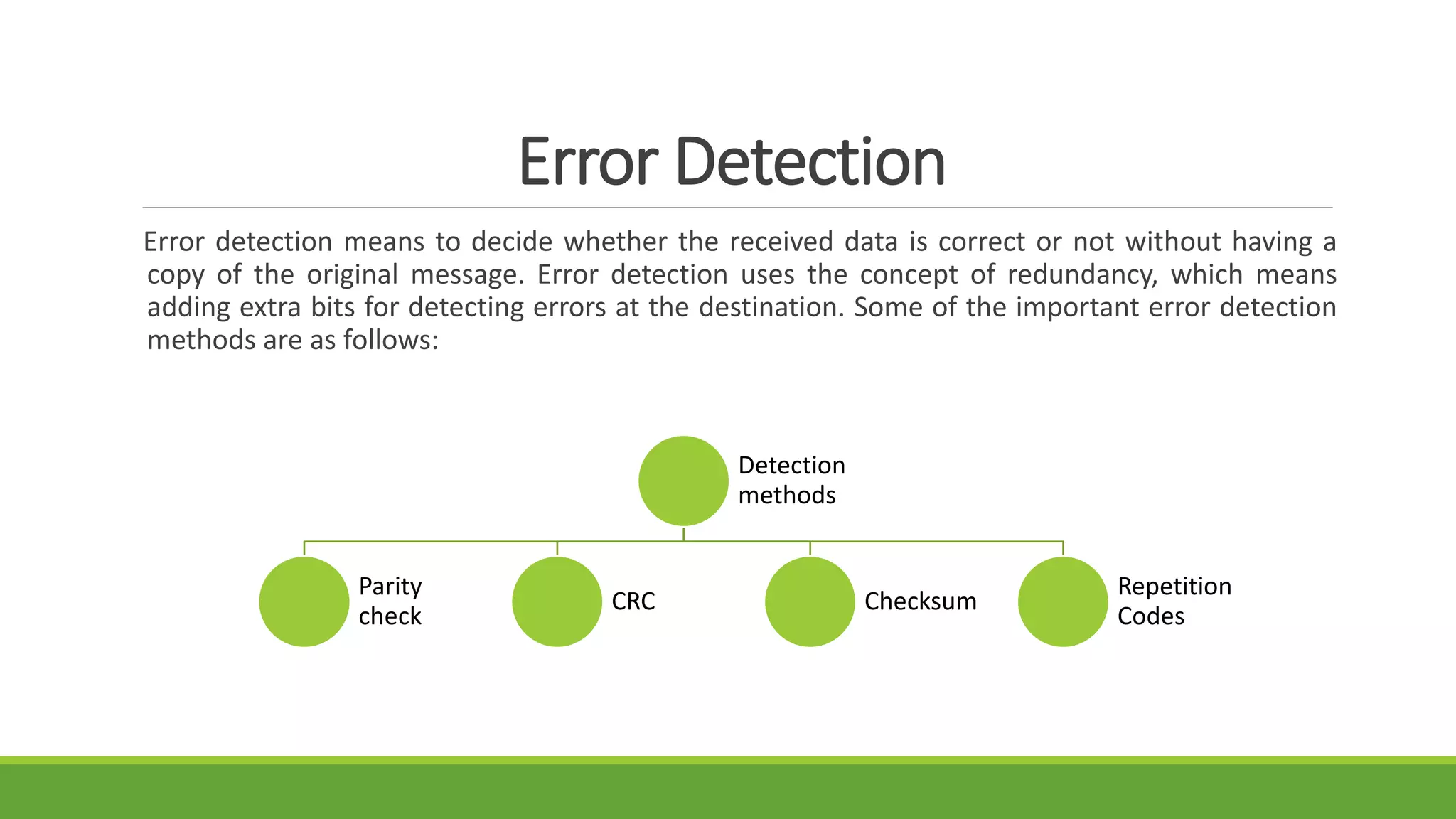
![Different Detection Approaches
Detection By Syntax Analysis: A first error analysis consists of subdividing detectable errors in different
sets depending on their characteristics: Illegal Code word, Out of Range Code word and Contextual Error.
The decoding of a slice containing an error at the position b can be described by three intervals illustrated
in the below Figure:
Interval [a,b): The slice is correctly decoded from its begin up to the error at the position b.
Interval [b,c): The error is undetected until the position c b. This part is decoded incorrectly.
Interval [c,d]: Starting from the position c until the end of the slice d concealment is used.](https://image.slidesharecdn.com/errorcontroltechniquesforvideocommunications-slideshare-151008183747-lva1-app6892/75/Error-control-techniques-for-video-communications-16-2048.jpg)