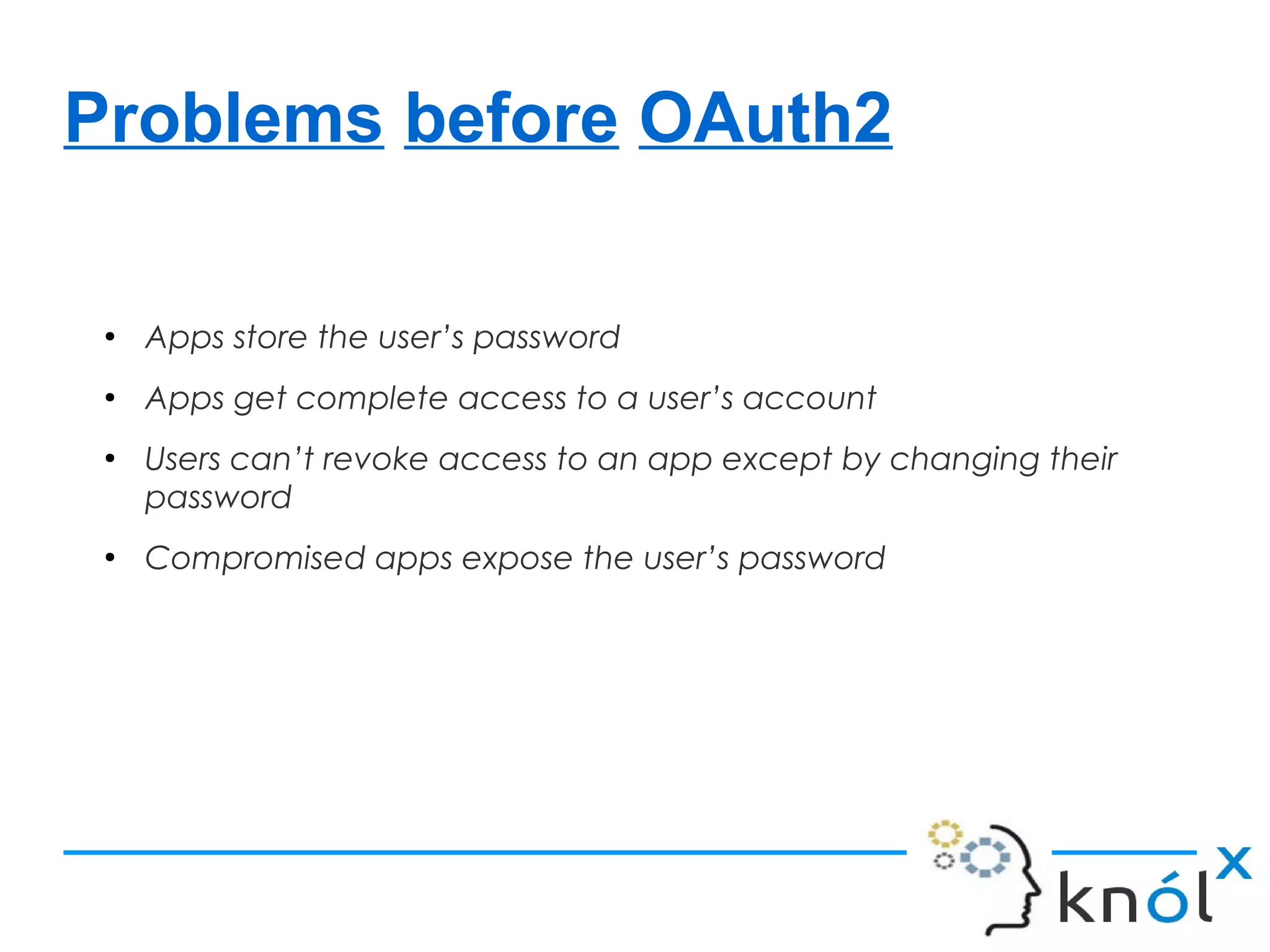
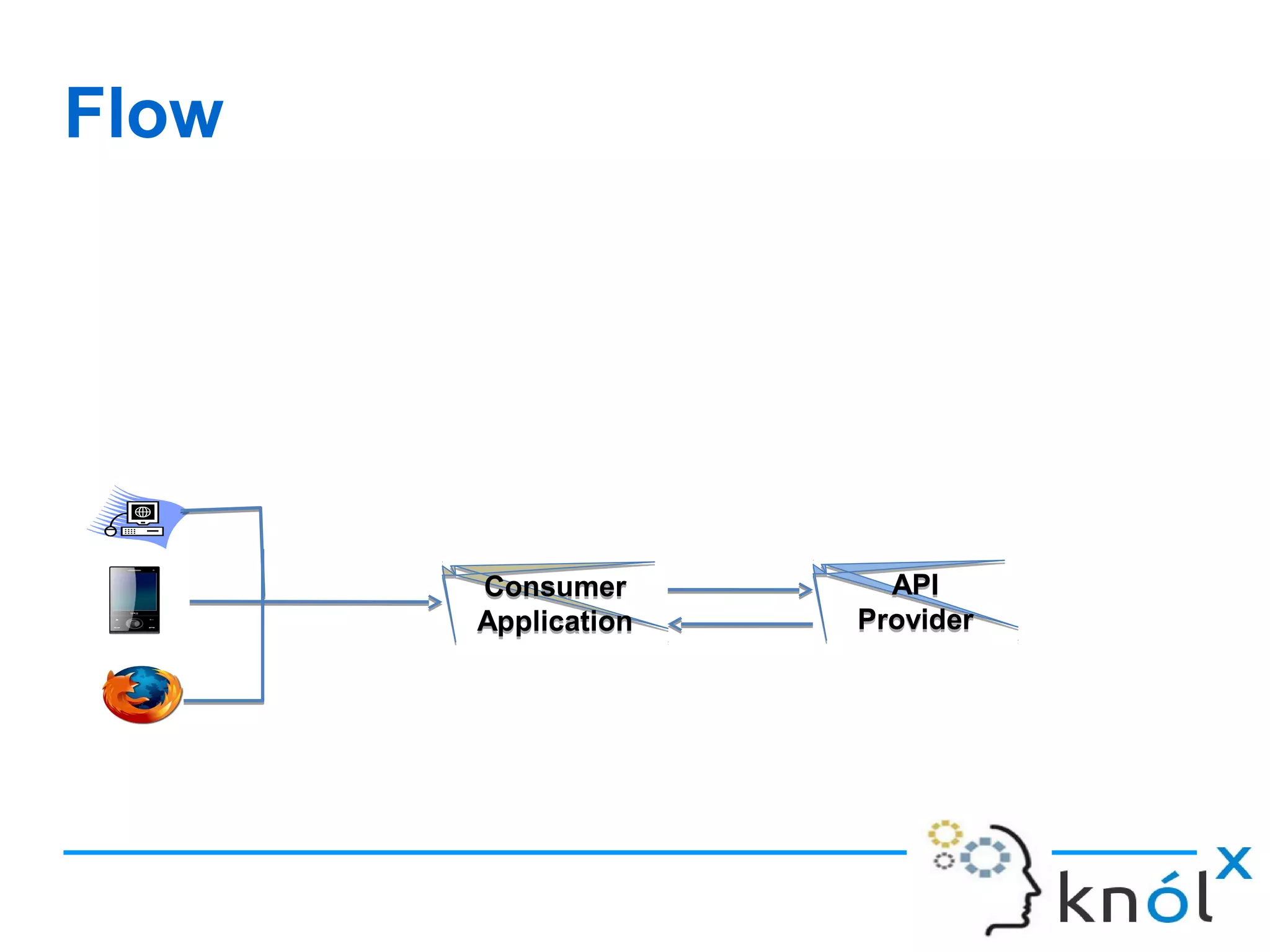
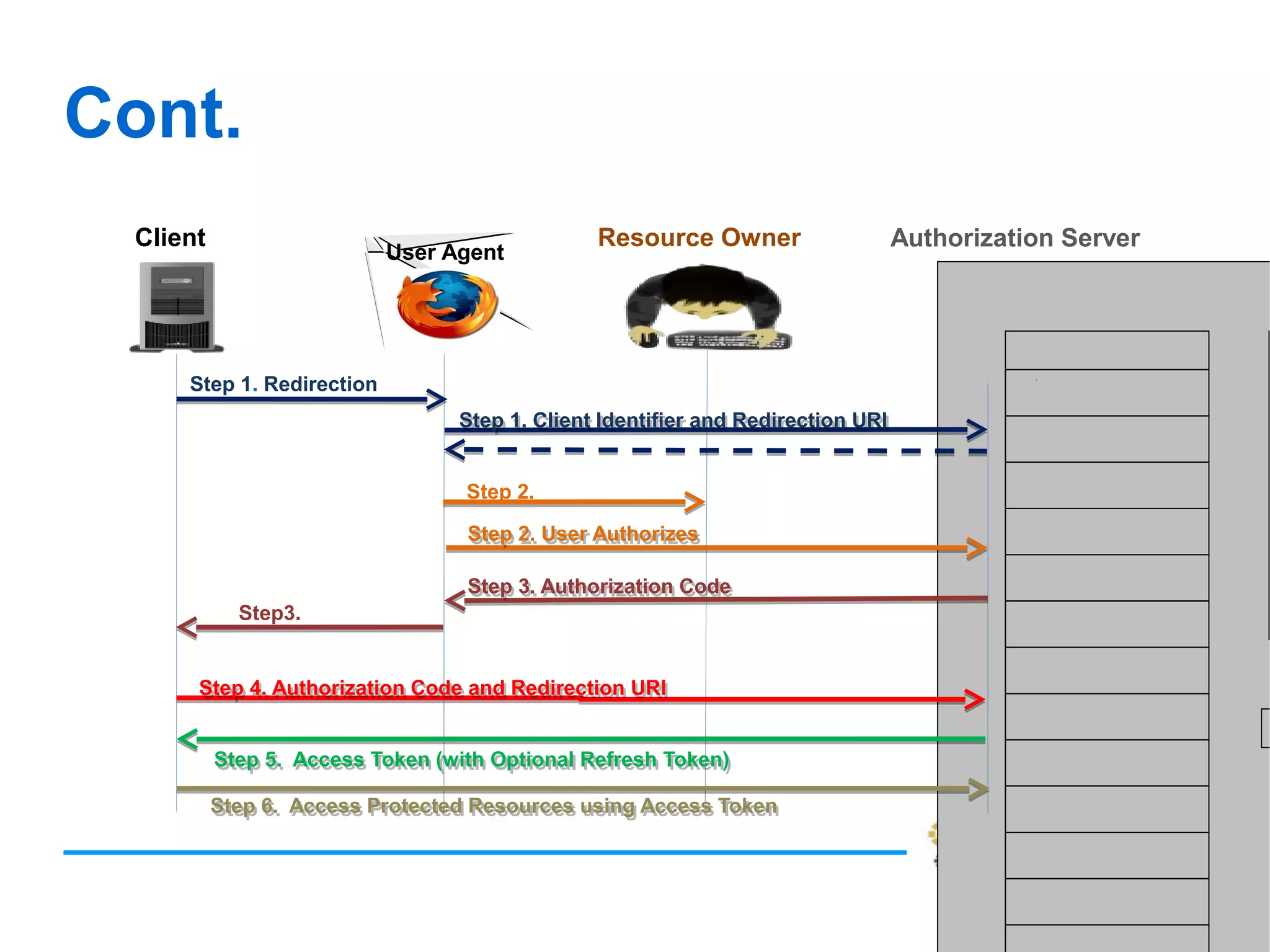
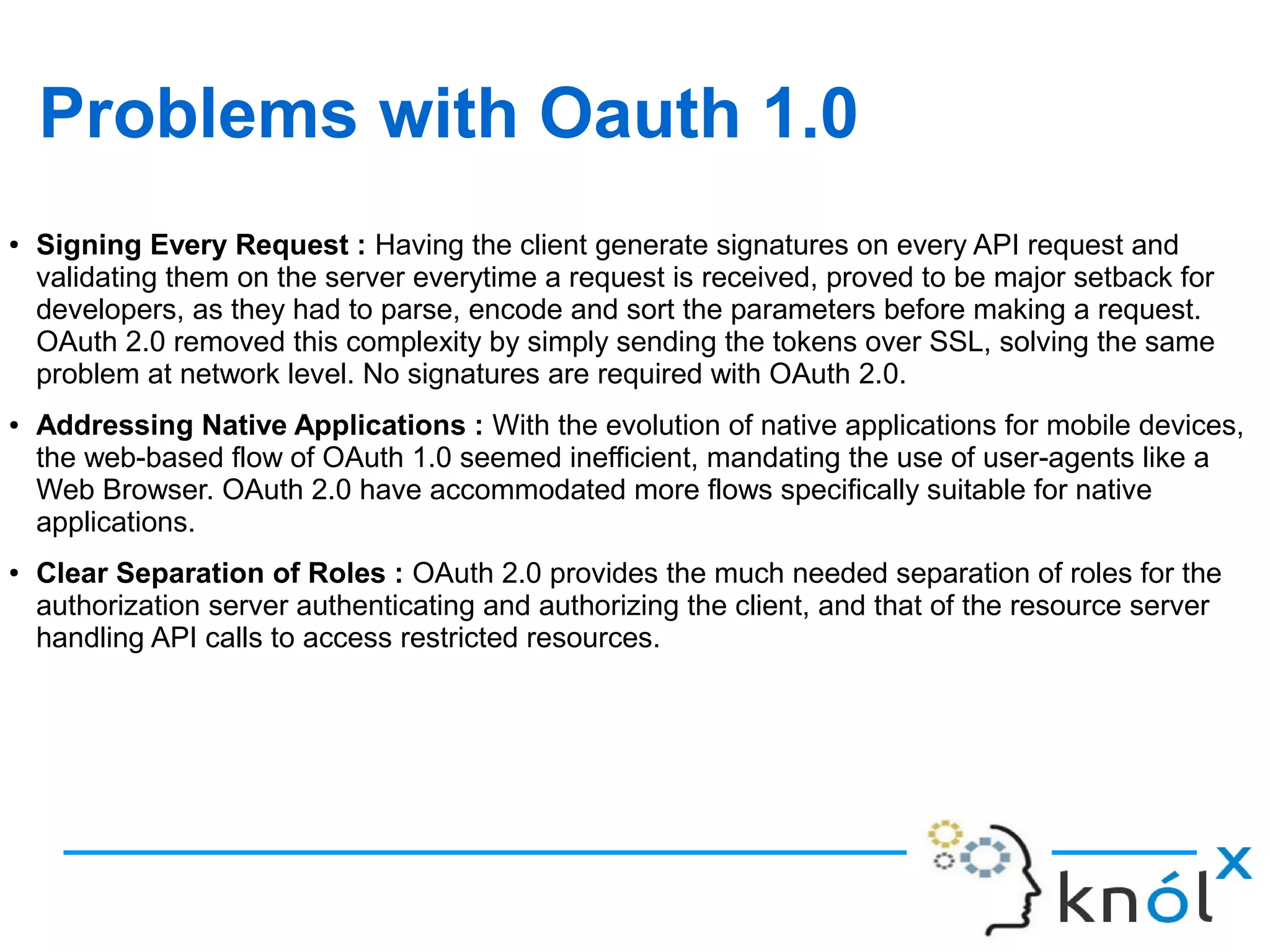
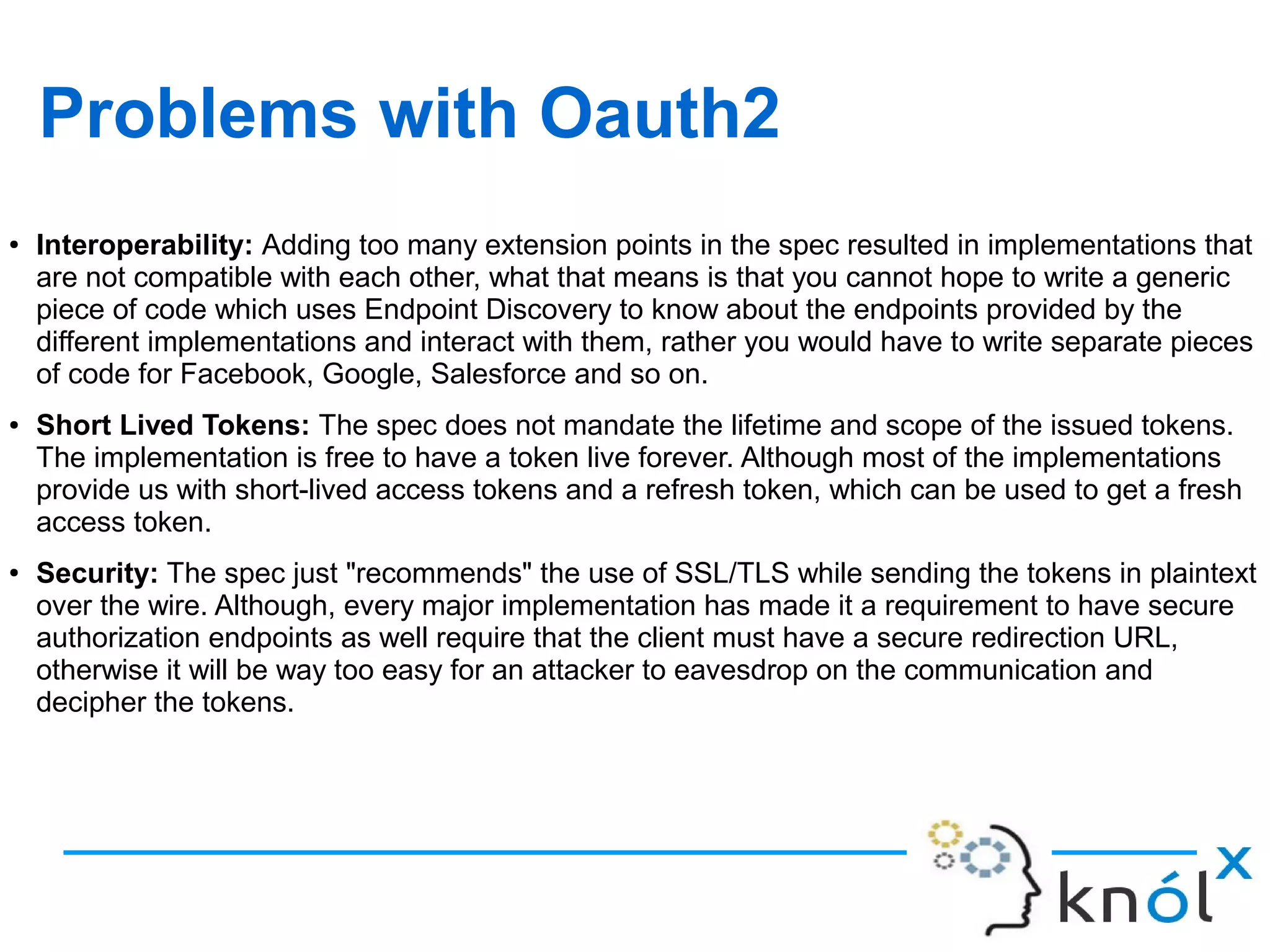
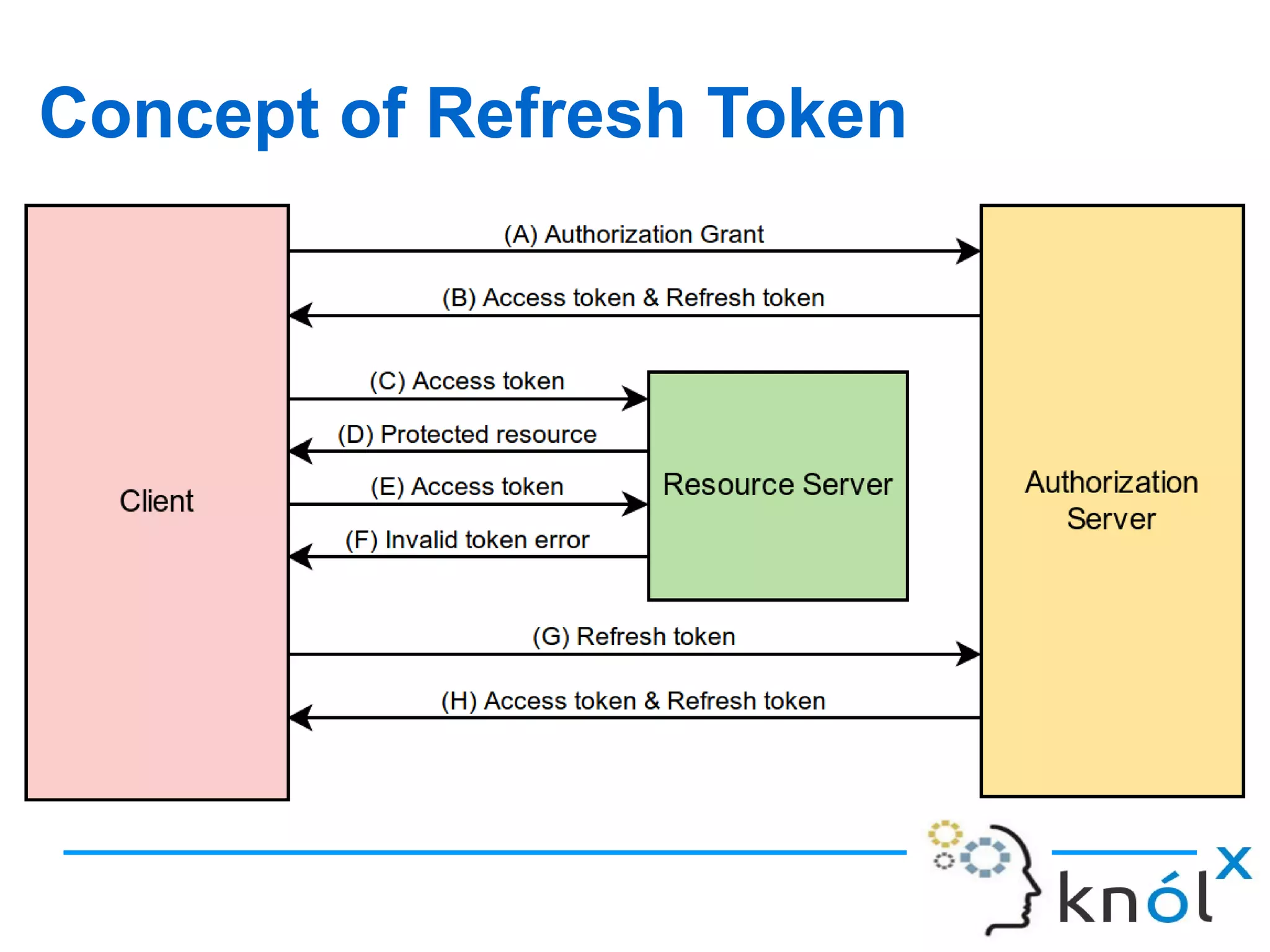
The document discusses OAuth 2.0, an authorization framework that allows third-party applications limited access to HTTP services on behalf of users, addressing issues from its predecessor, OAuth 1.0. It highlights problems like password storage and application access control, while emphasizing the improvements in token handling, separation of roles, and native application support. Key challenges with OAuth 1.0, including interoperability and security concerns, are also analyzed.