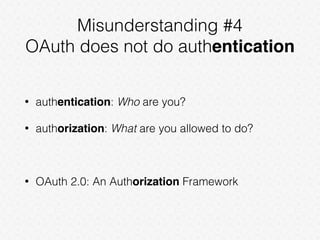
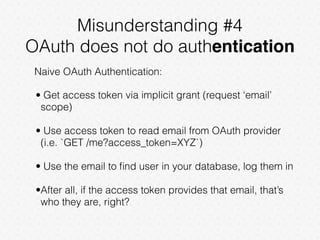
This document discusses common misconceptions about OAuth 2.0. It clarifies that while OAuth 2.0 is an authorization framework, it does not directly provide authentication. It also explains differences between access tokens and refresh tokens, and notes that bearer tokens issued to different clients are not equal. Additionally, it clarifies the differences between authorization code flow and implicit grant flow.