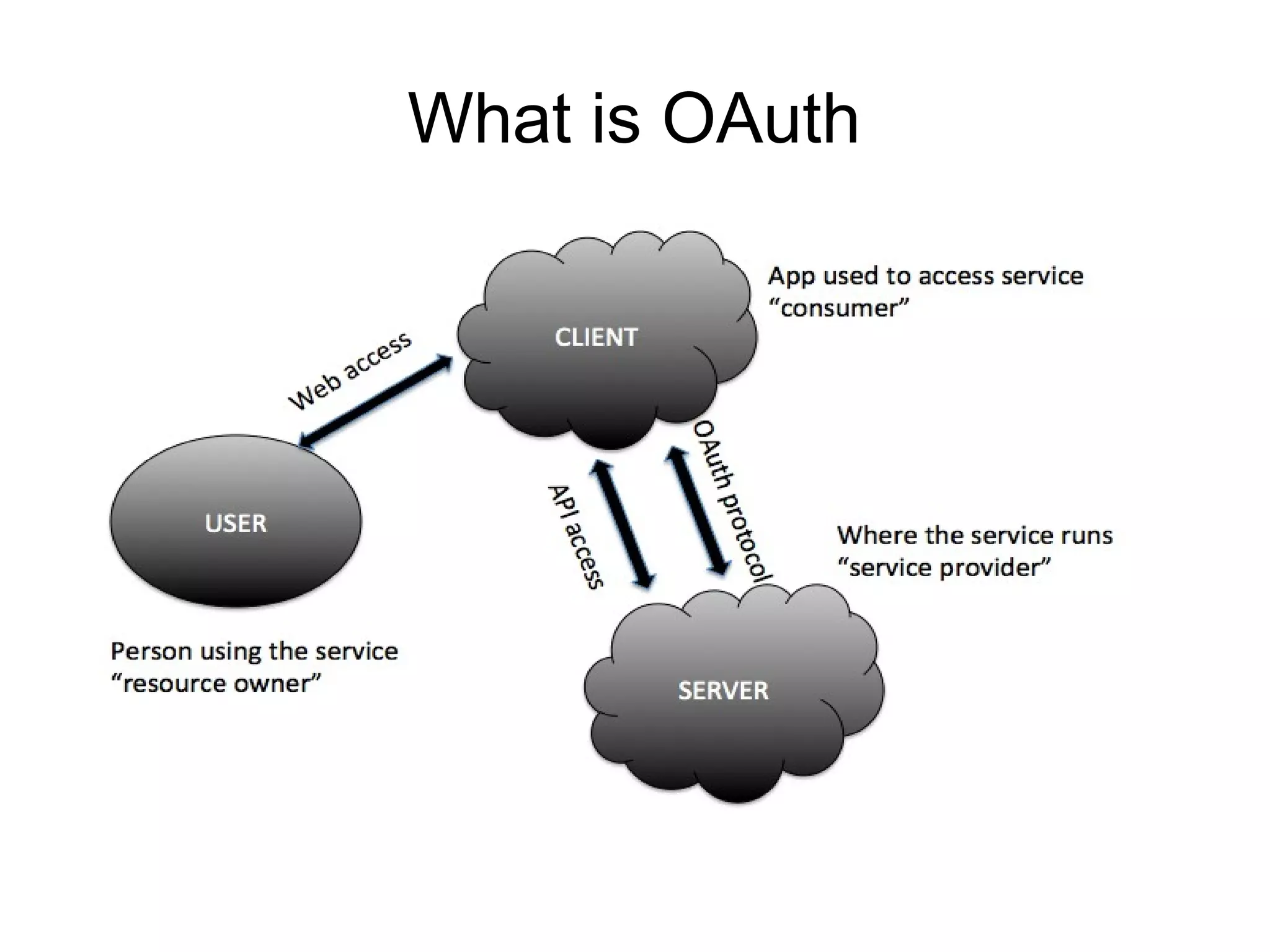
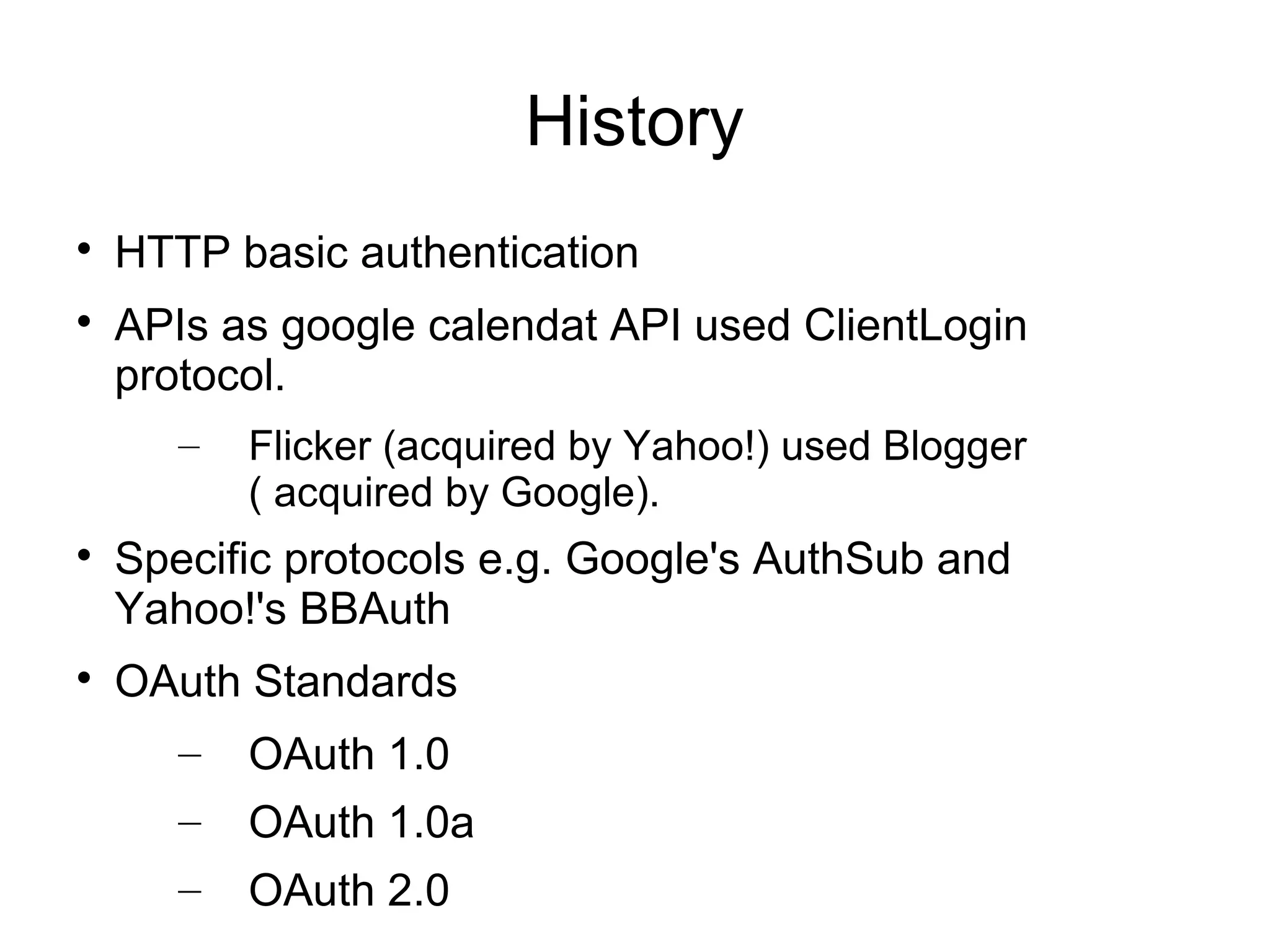
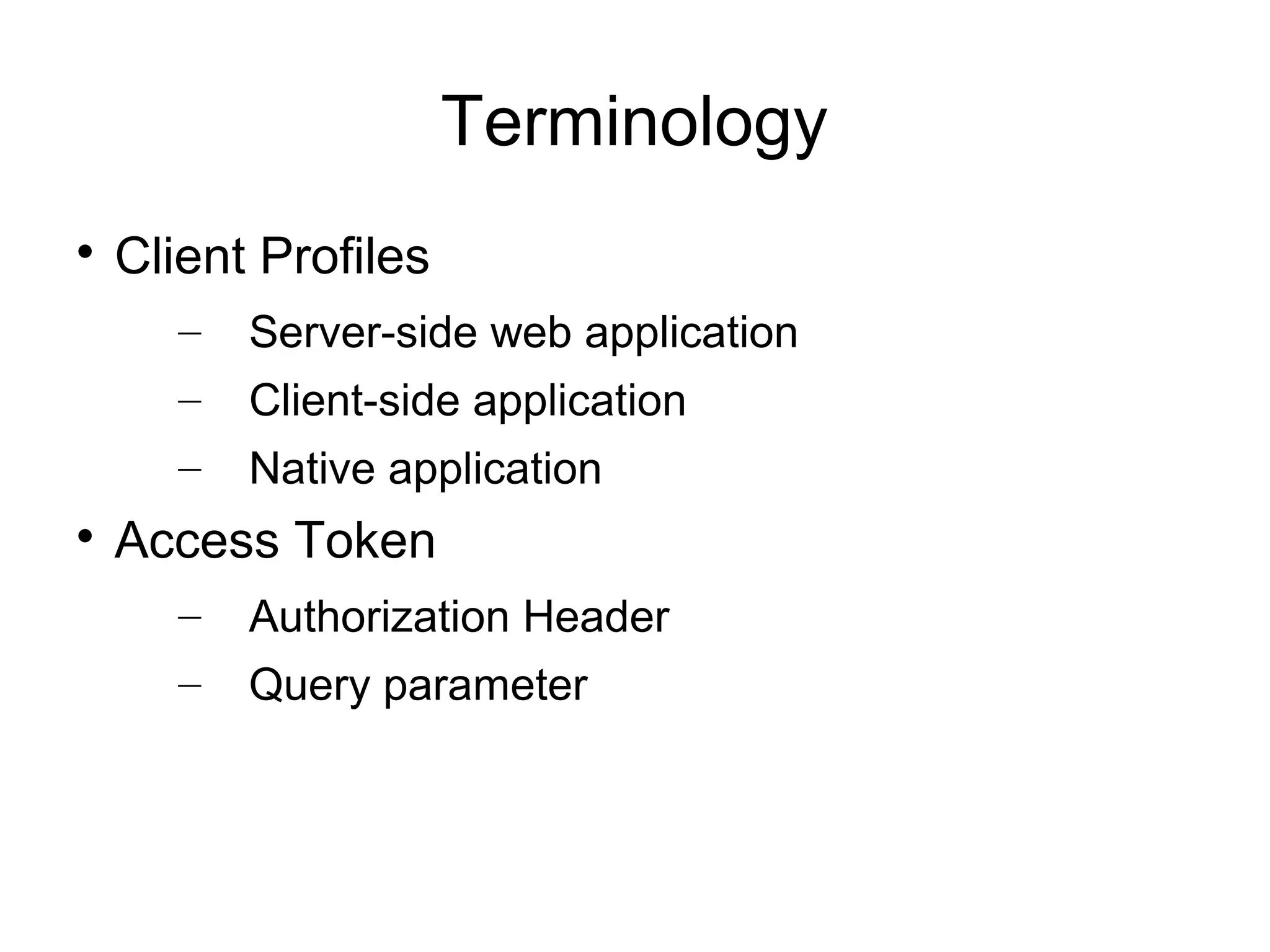
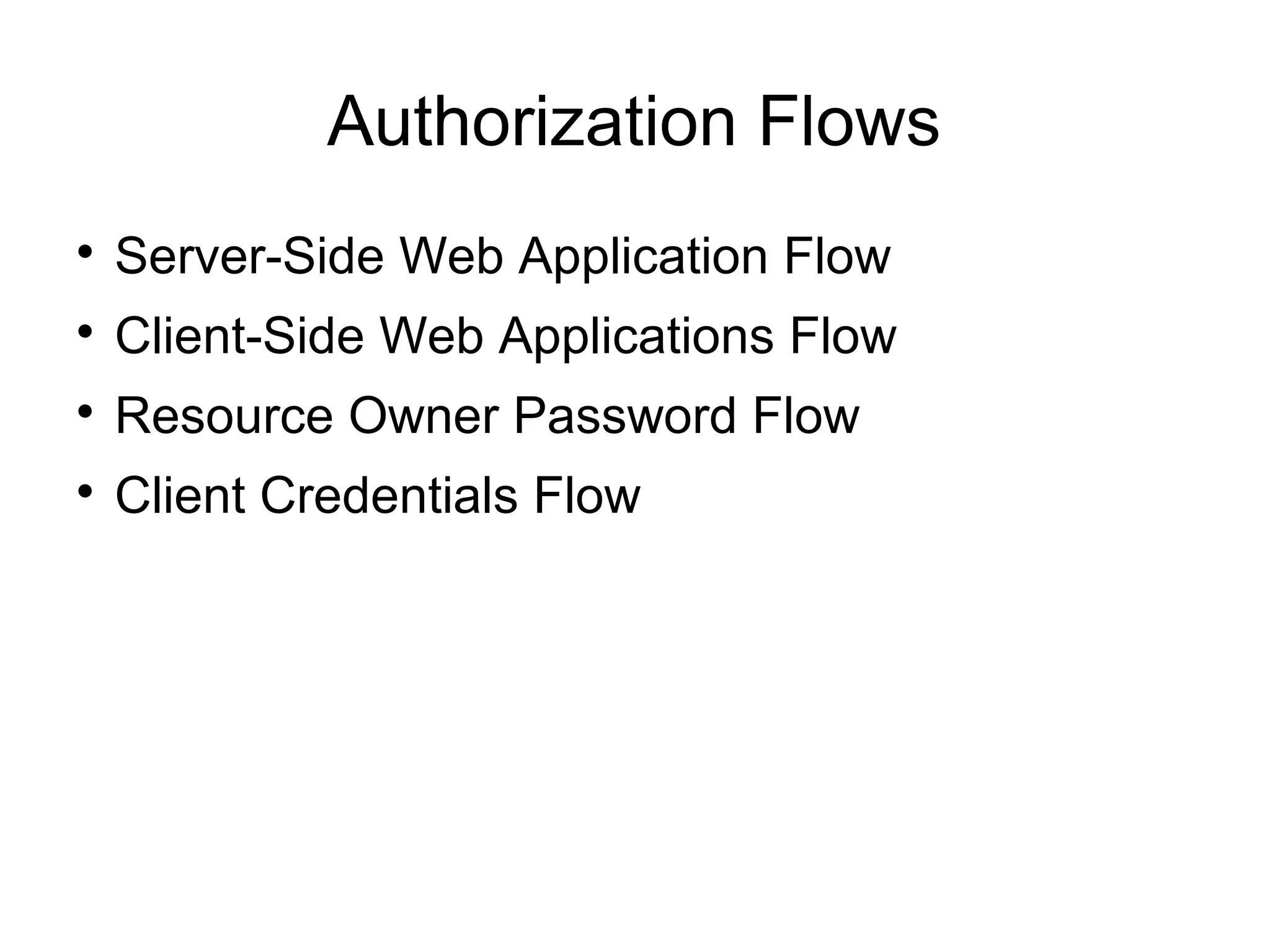
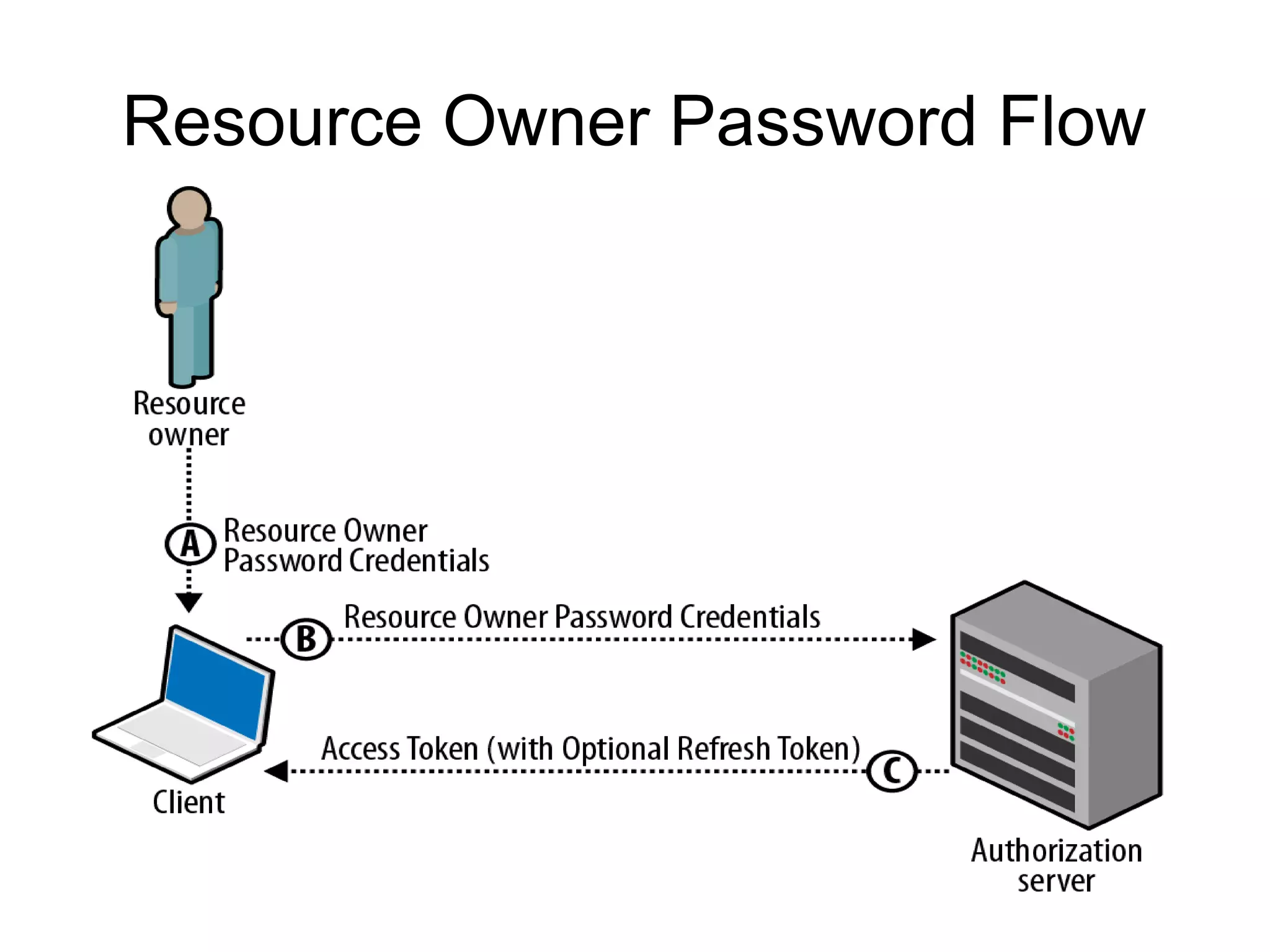
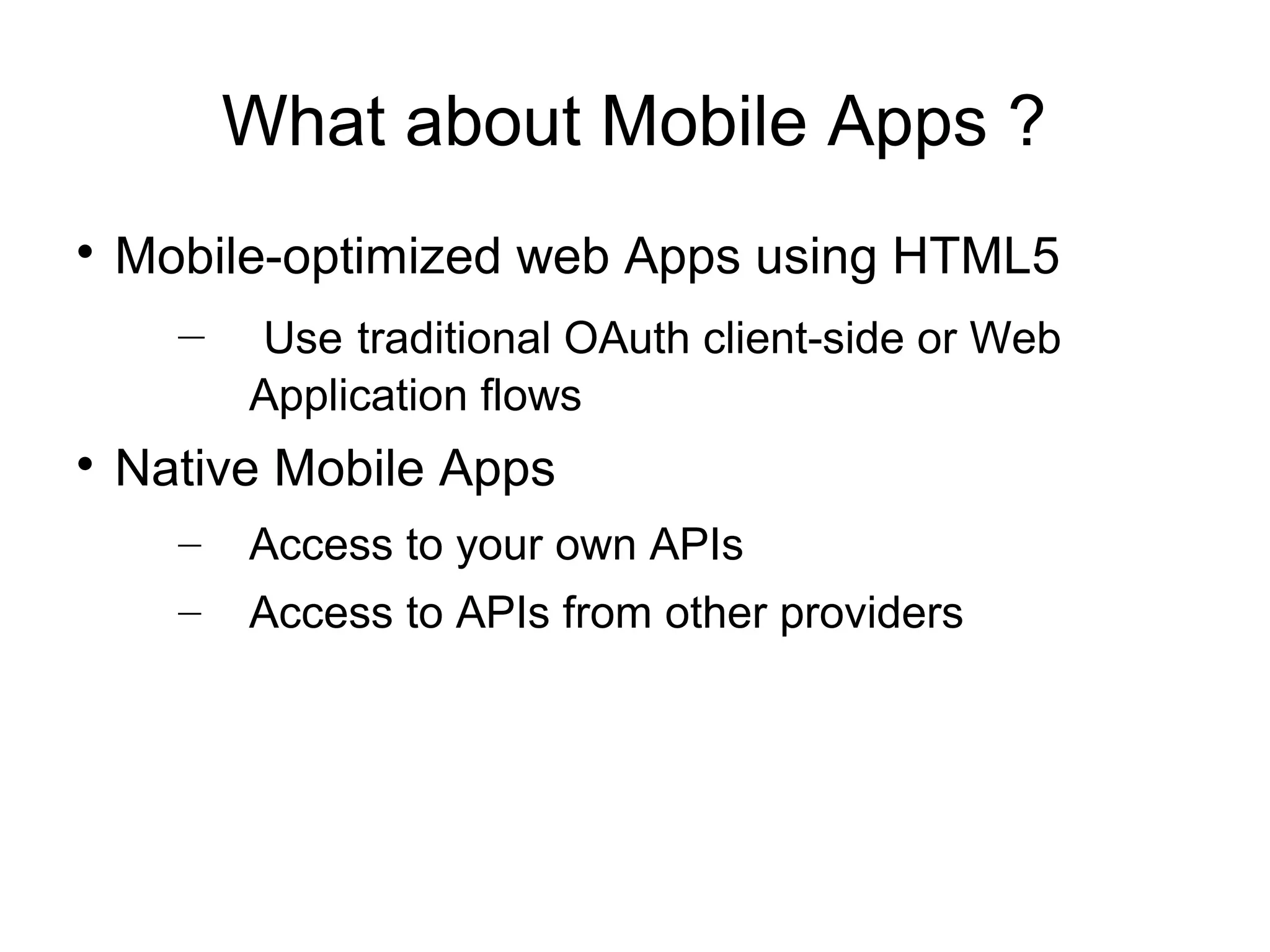
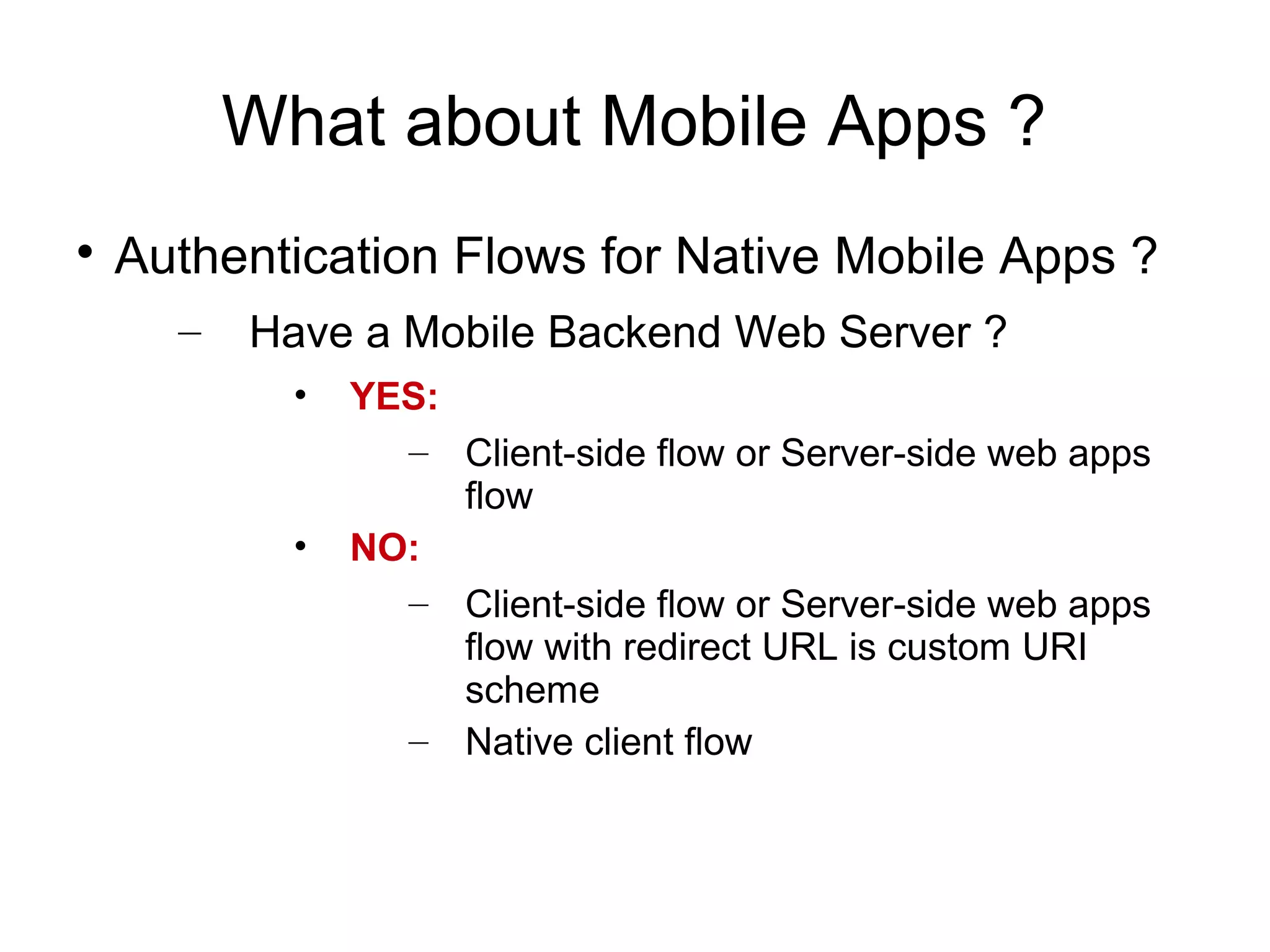
This document provides an overview of OAuth 2.0. It discusses what OAuth is, its history and terminology. It then covers the main authorization flows in OAuth 2.0 including server-side web applications, client-side web applications, resource owner passwords, and client credentials. Considerations for using OAuth in mobile apps are also outlined. The document concludes with information about tools, libraries and a demo for implementing OAuth.