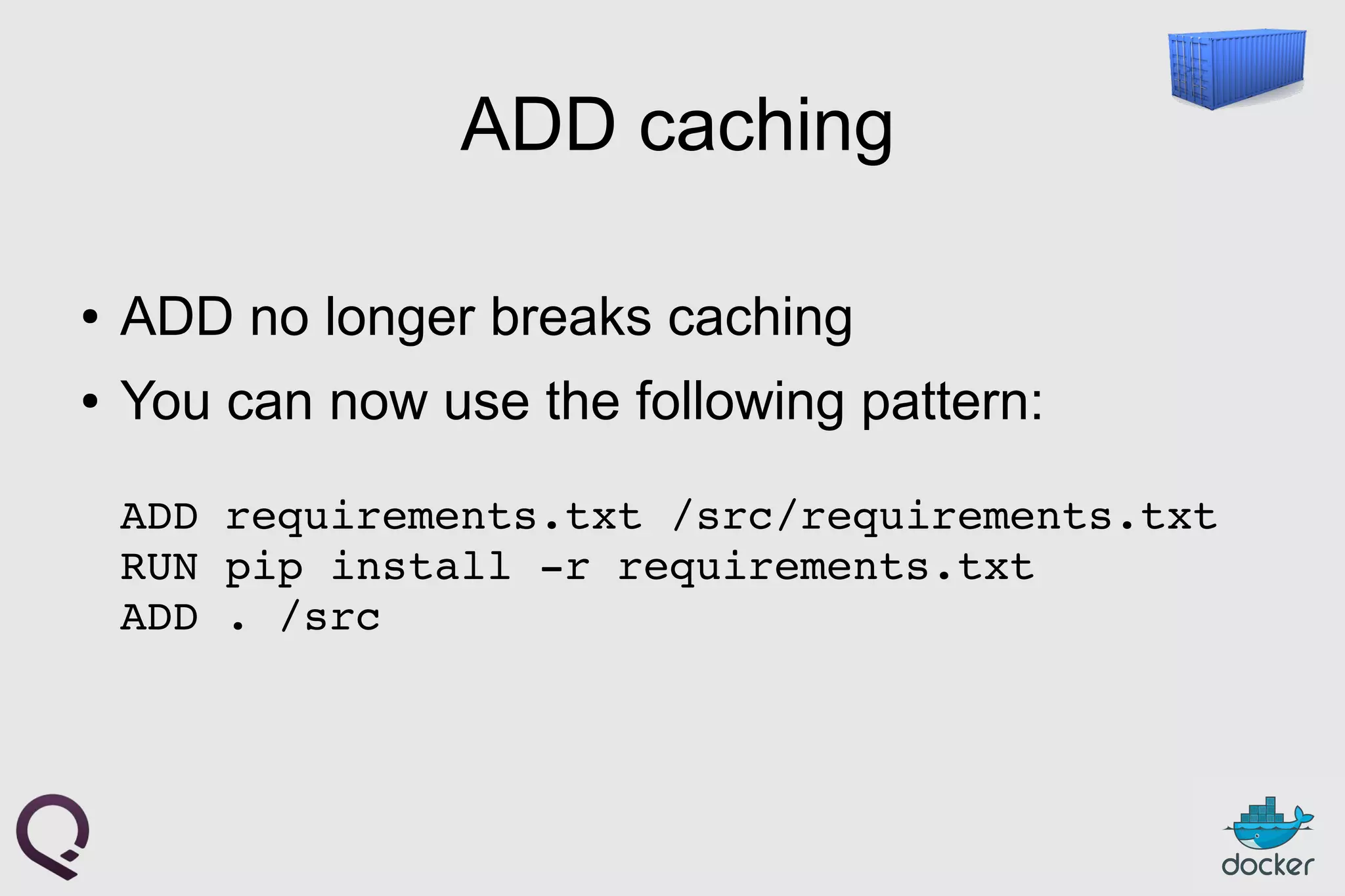
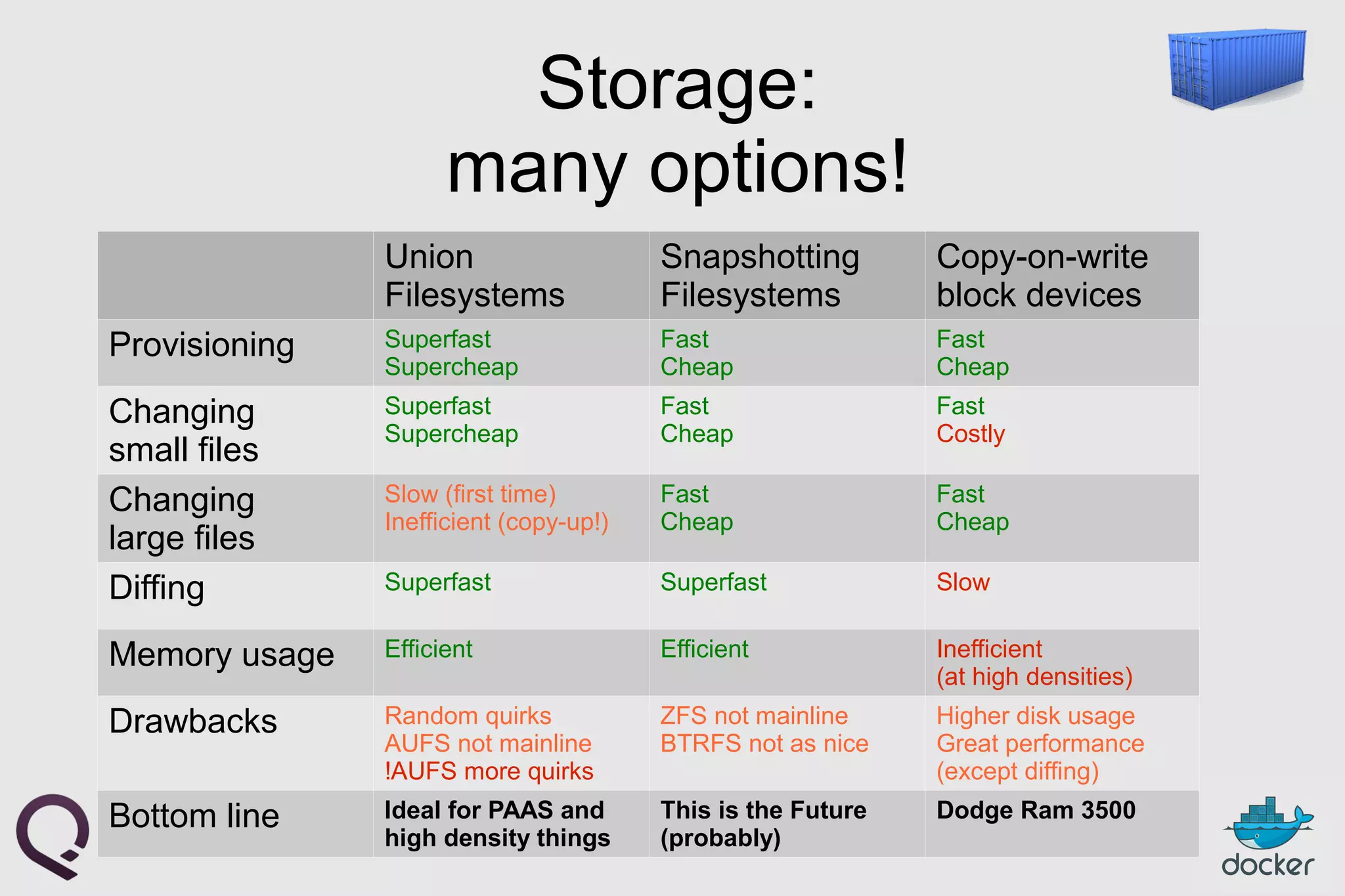
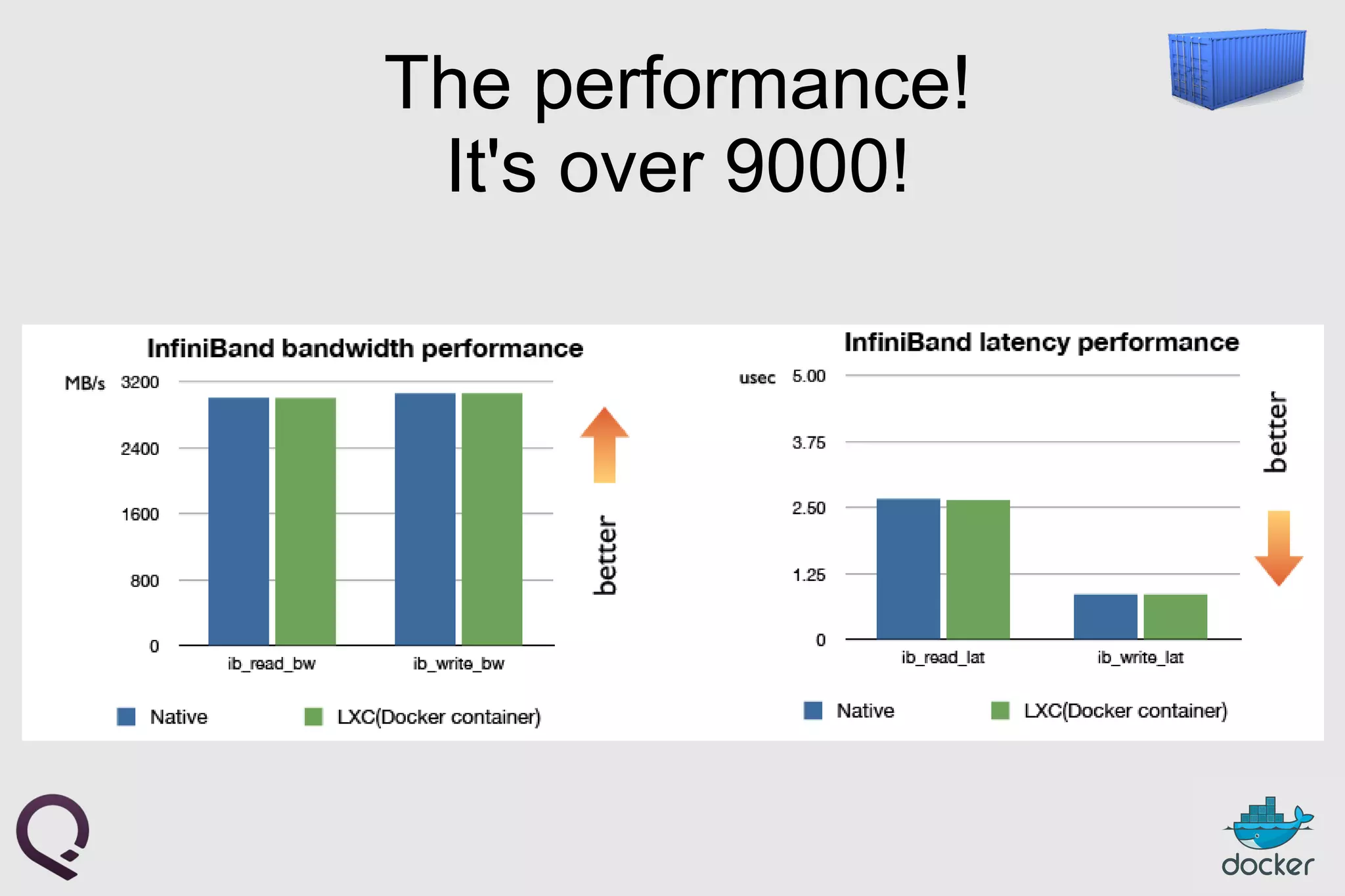
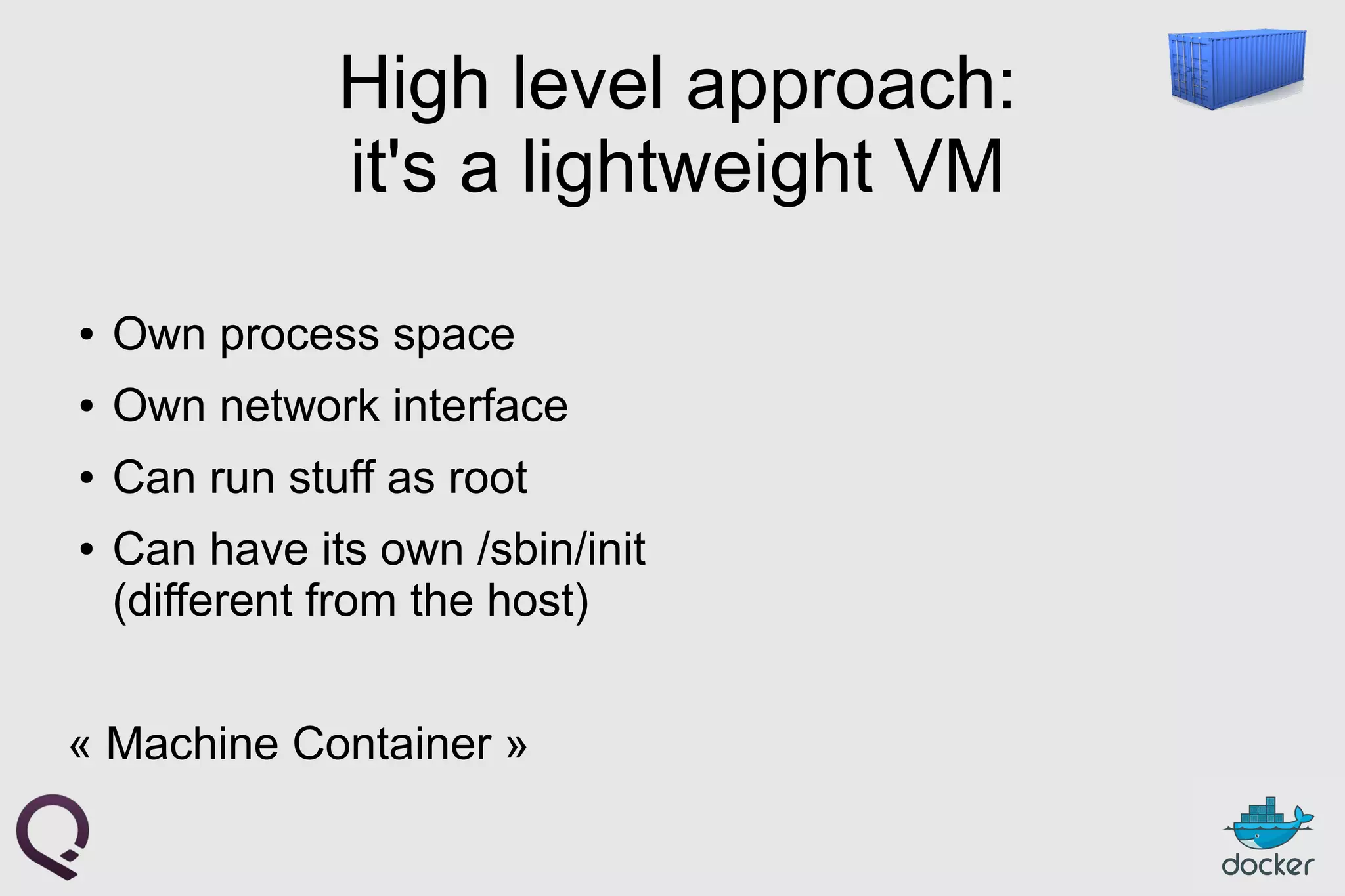
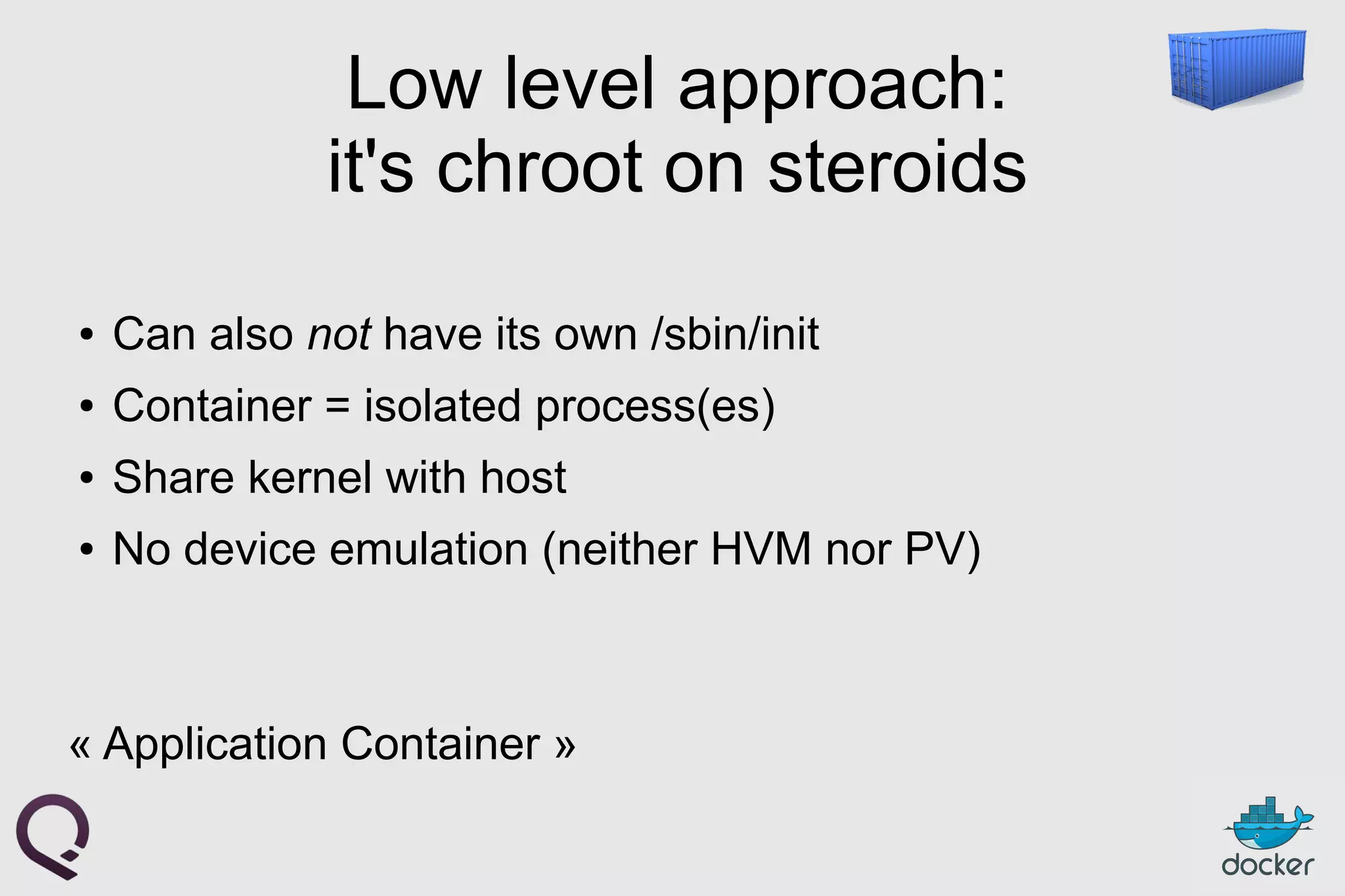
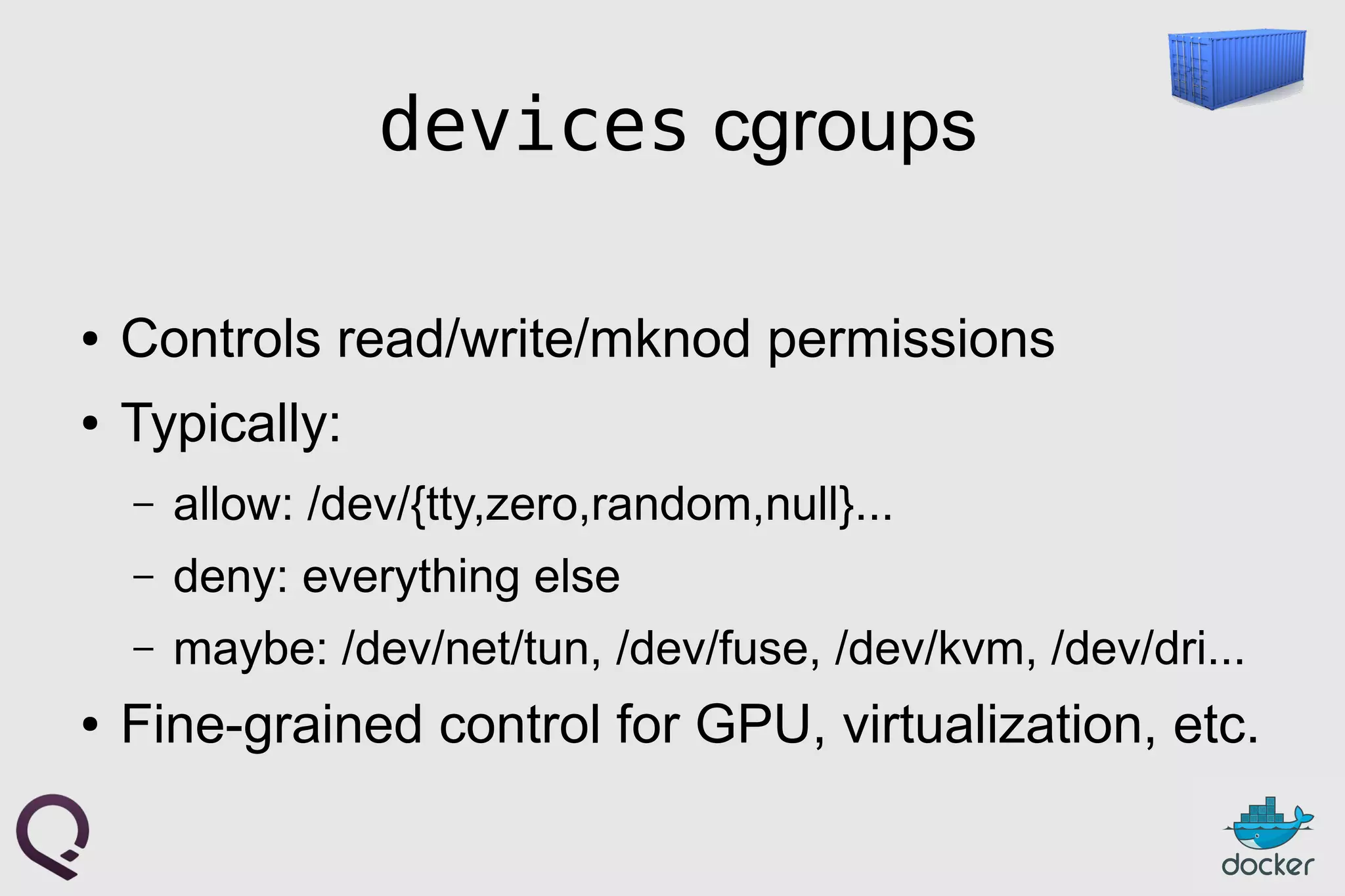
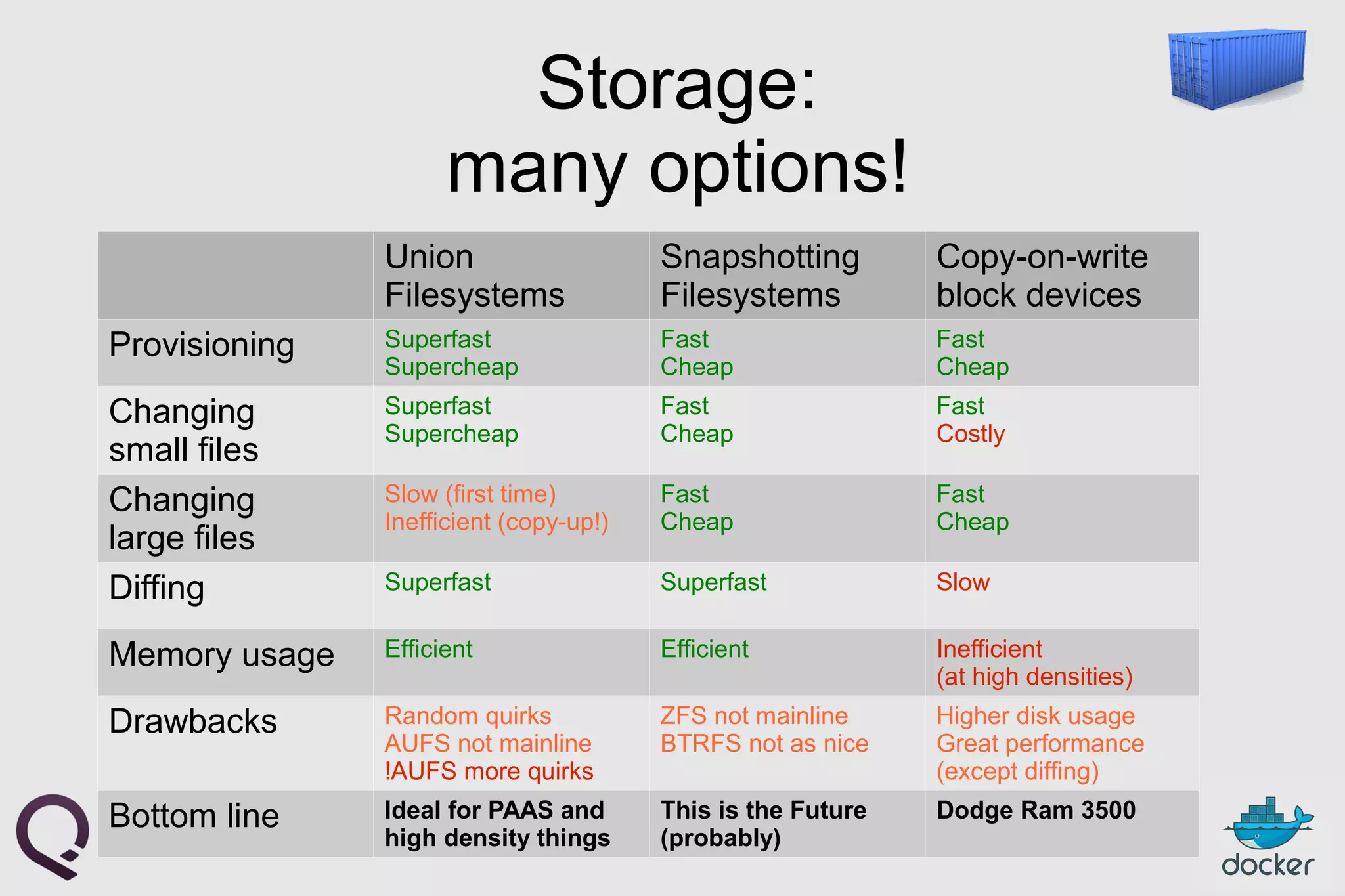
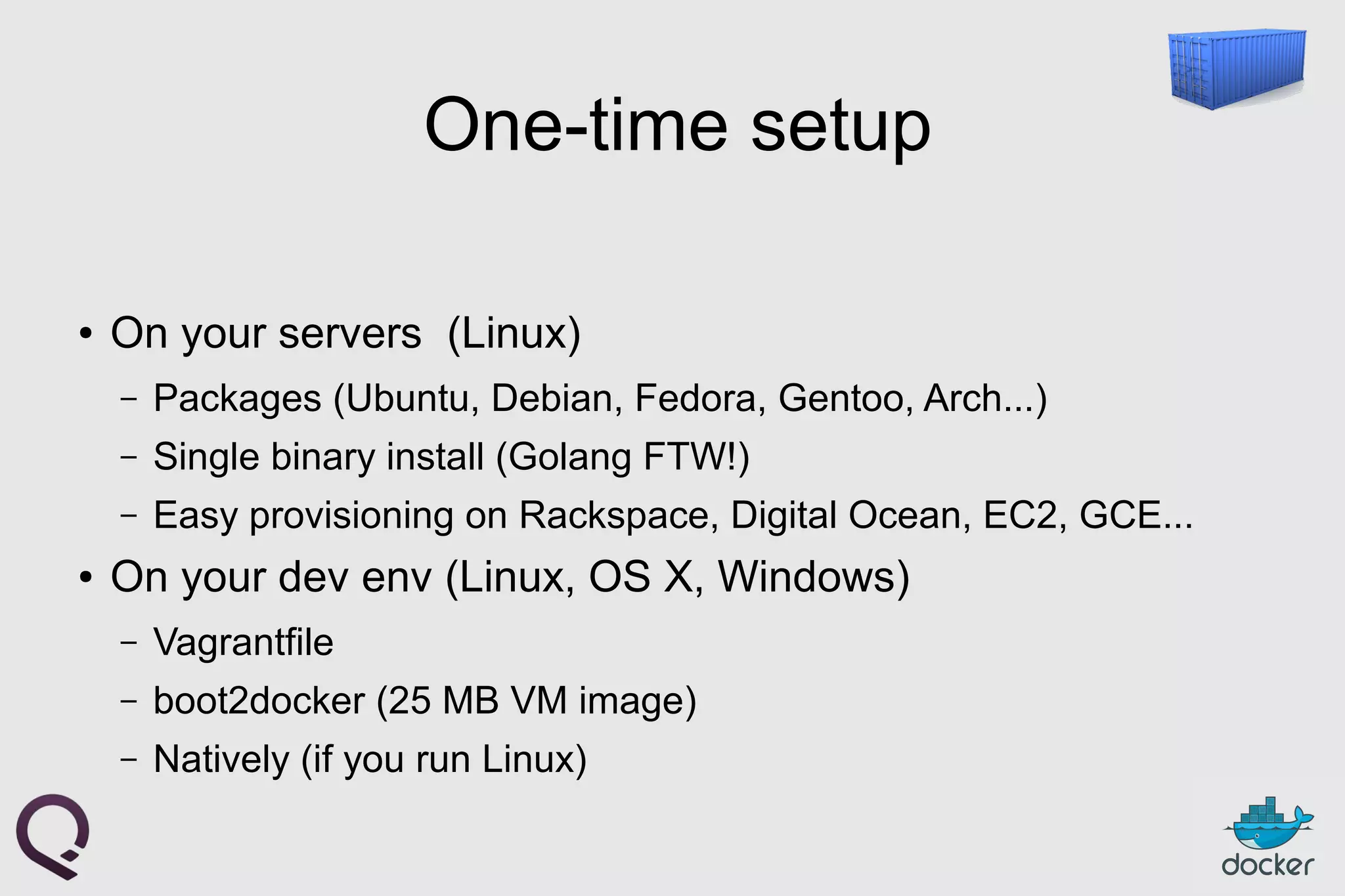
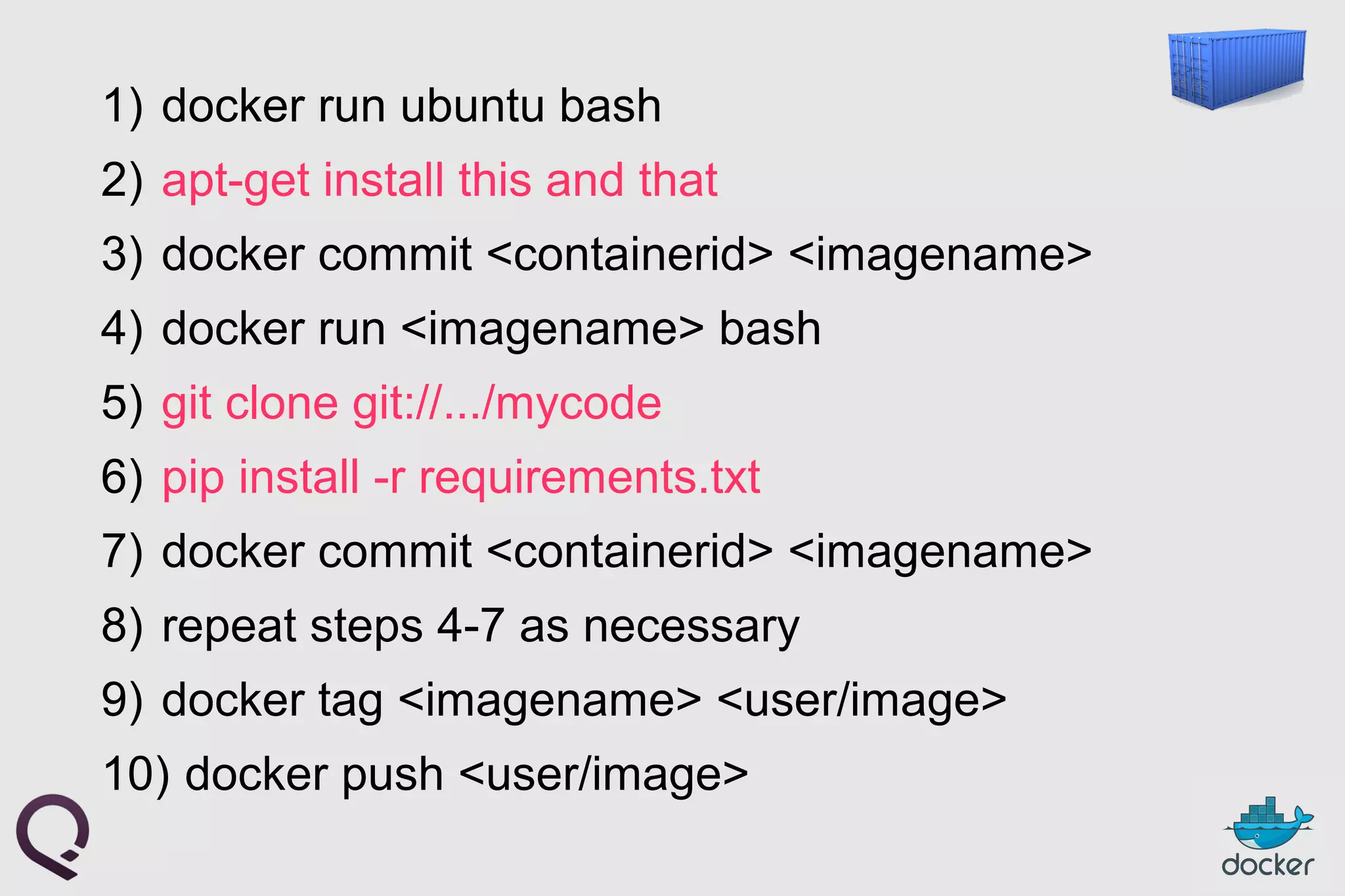
The document provides an introduction to Docker, outlining its capabilities for containerizing applications across various environments, including production deployment on Linux servers. It discusses Docker's efficient lightweight container model, offering isolation through namespaces and control groups, as well as features like copy-on-write storage for quick provisioning. Additionally, it highlights the Docker ecosystem, workflow, and the advantages of using Dockerfiles for image authoring.








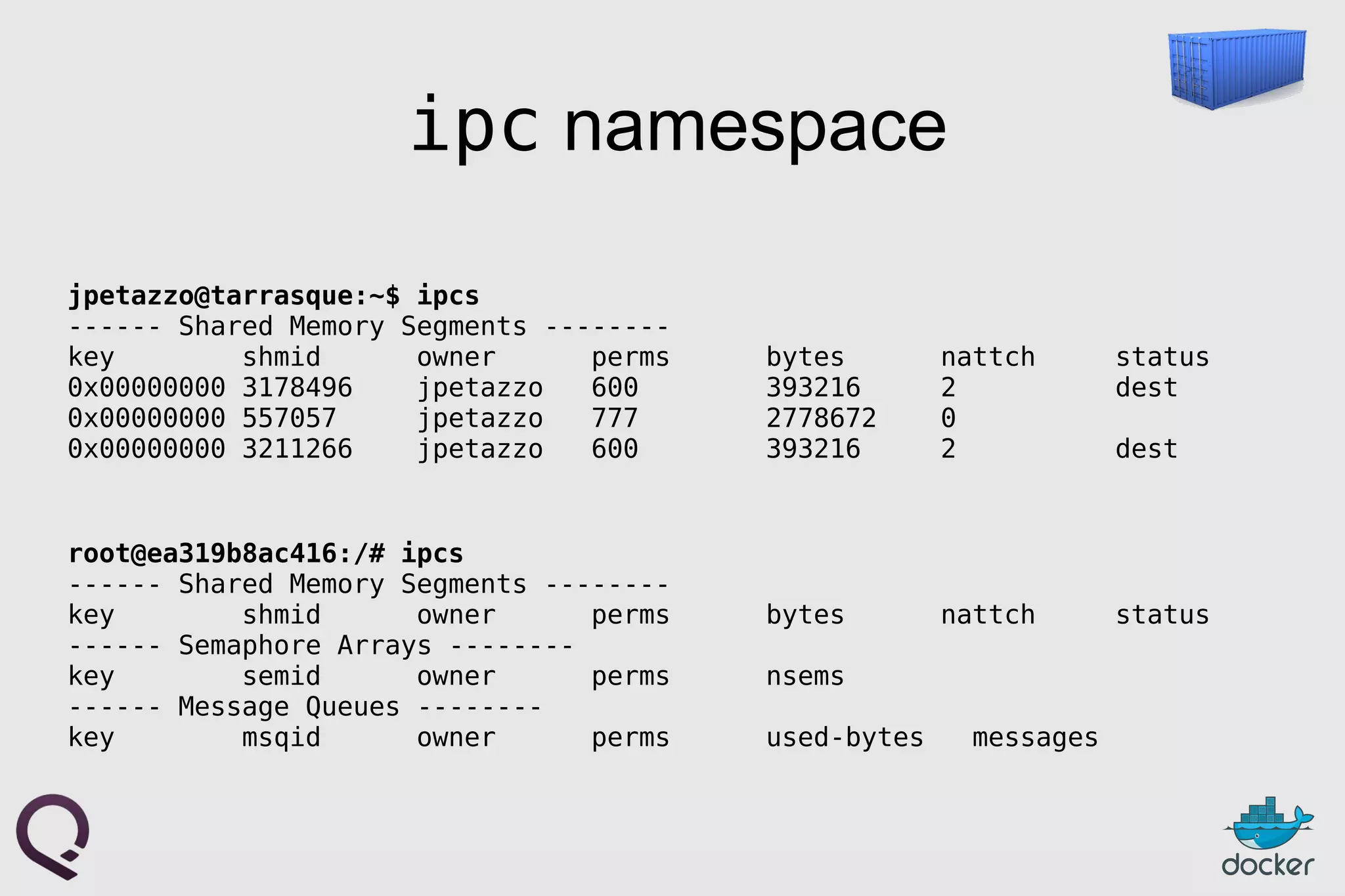
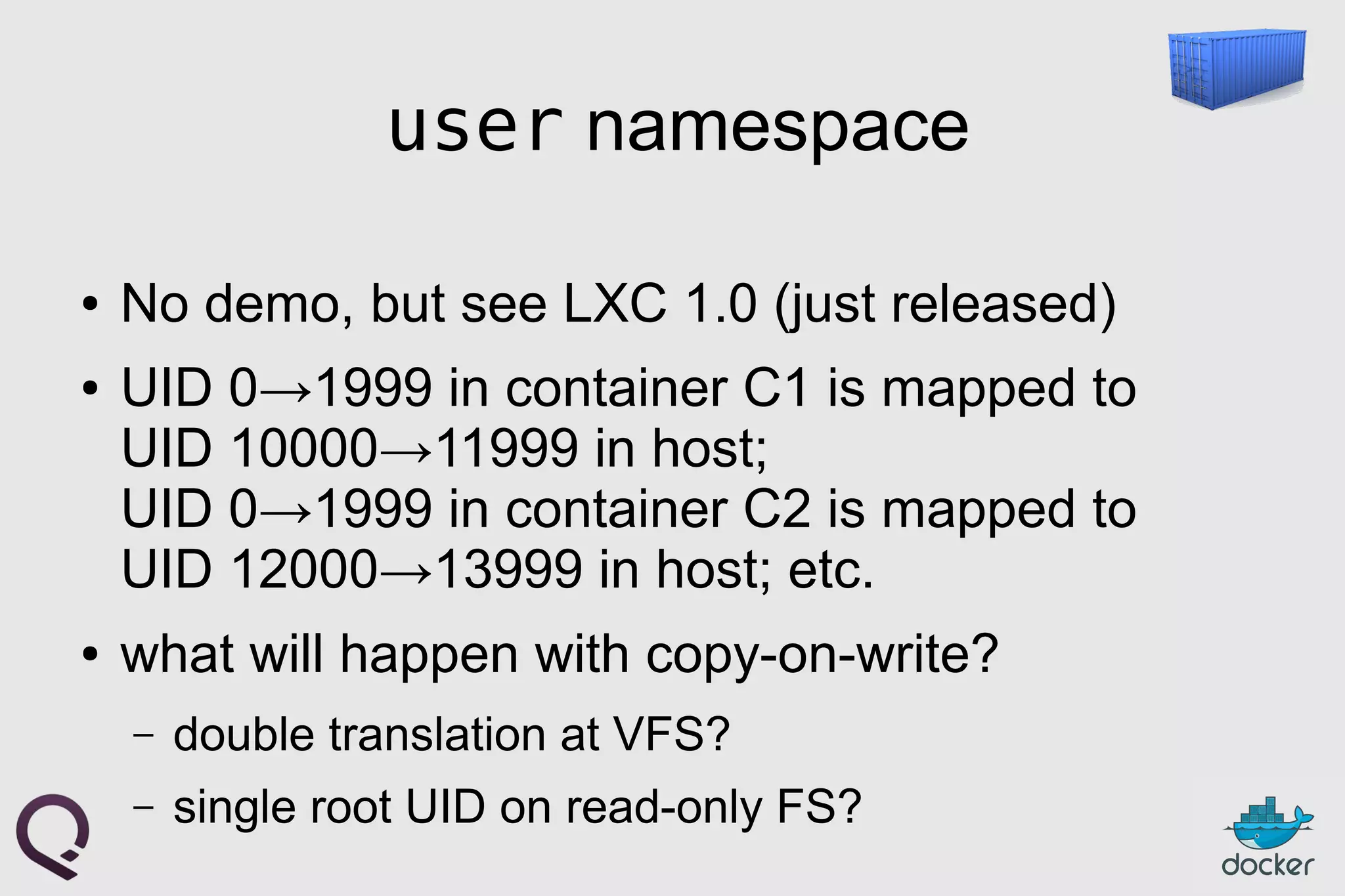

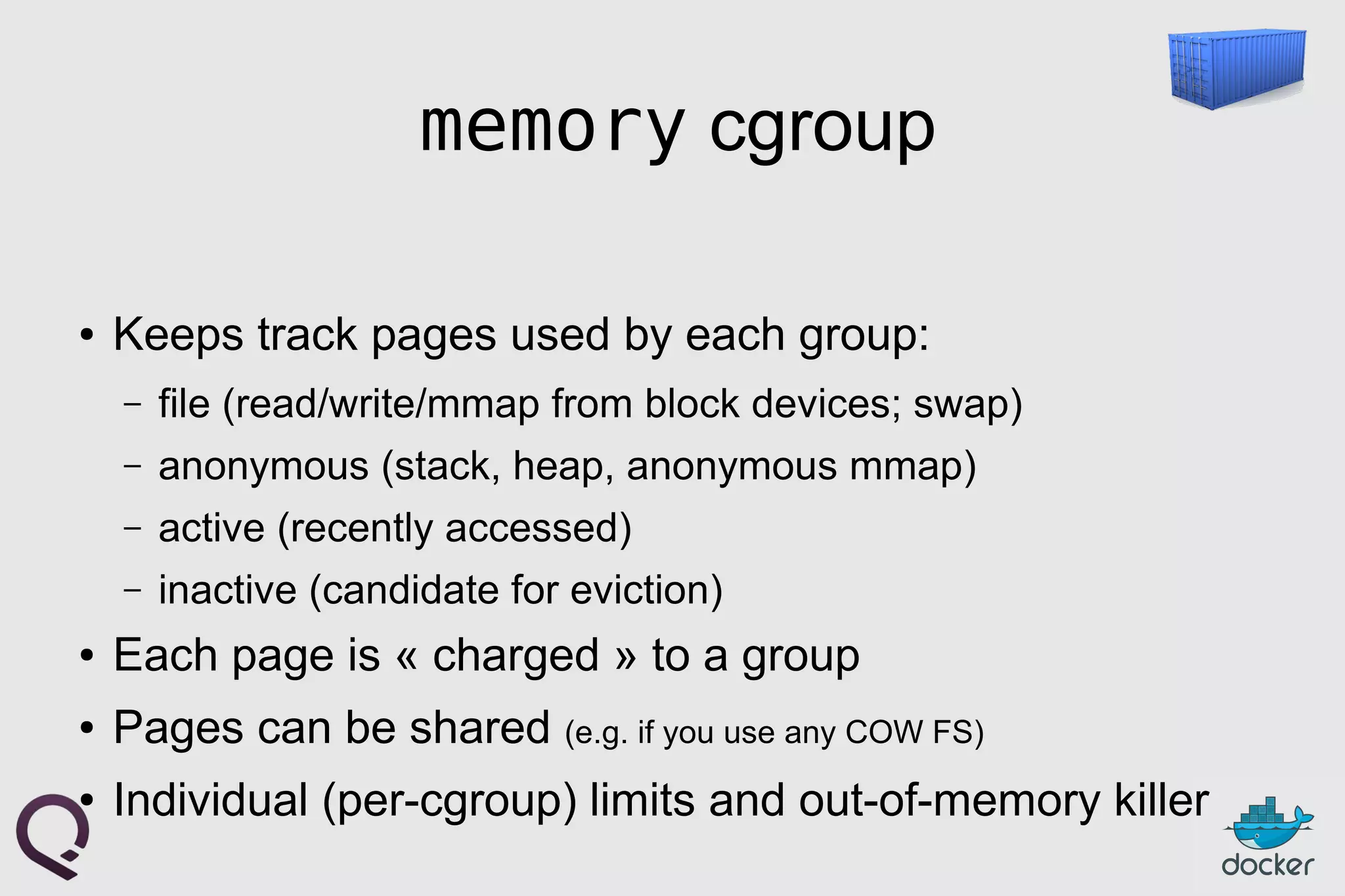




















![FROM ubuntu
RUN apt-get -y update
RUN apt-get install -y g++
RUN apt-get install -y erlang-dev erlang-manpages erlang-base-hipe ...
RUN apt-get install -y libmozjs185-dev libicu-dev libtool ...
RUN apt-get install -y make wget
RUN wget http://.../apache-couchdb-1.3.1.tar.gz | tar -C /tmp -zxf-
RUN cd /tmp/apache-couchdb-* && ./configure && make install
RUN printf "[httpd]nport = 8101nbind_address = 0.0.0.0" >
/usr/local/etc/couchdb/local.d/docker.ini
EXPOSE 8101
CMD ["/usr/local/bin/couchdb"]
docker build -t jpetazzo/couchdb .](https://image.slidesharecdn.com/2014-03-13-docker-relateiq-140313224114-phpapp01/75/Docker-Introduction-and-what-s-new-in-0-9-Docker-Palo-Alto-at-RelateIQ-58-2048.jpg)