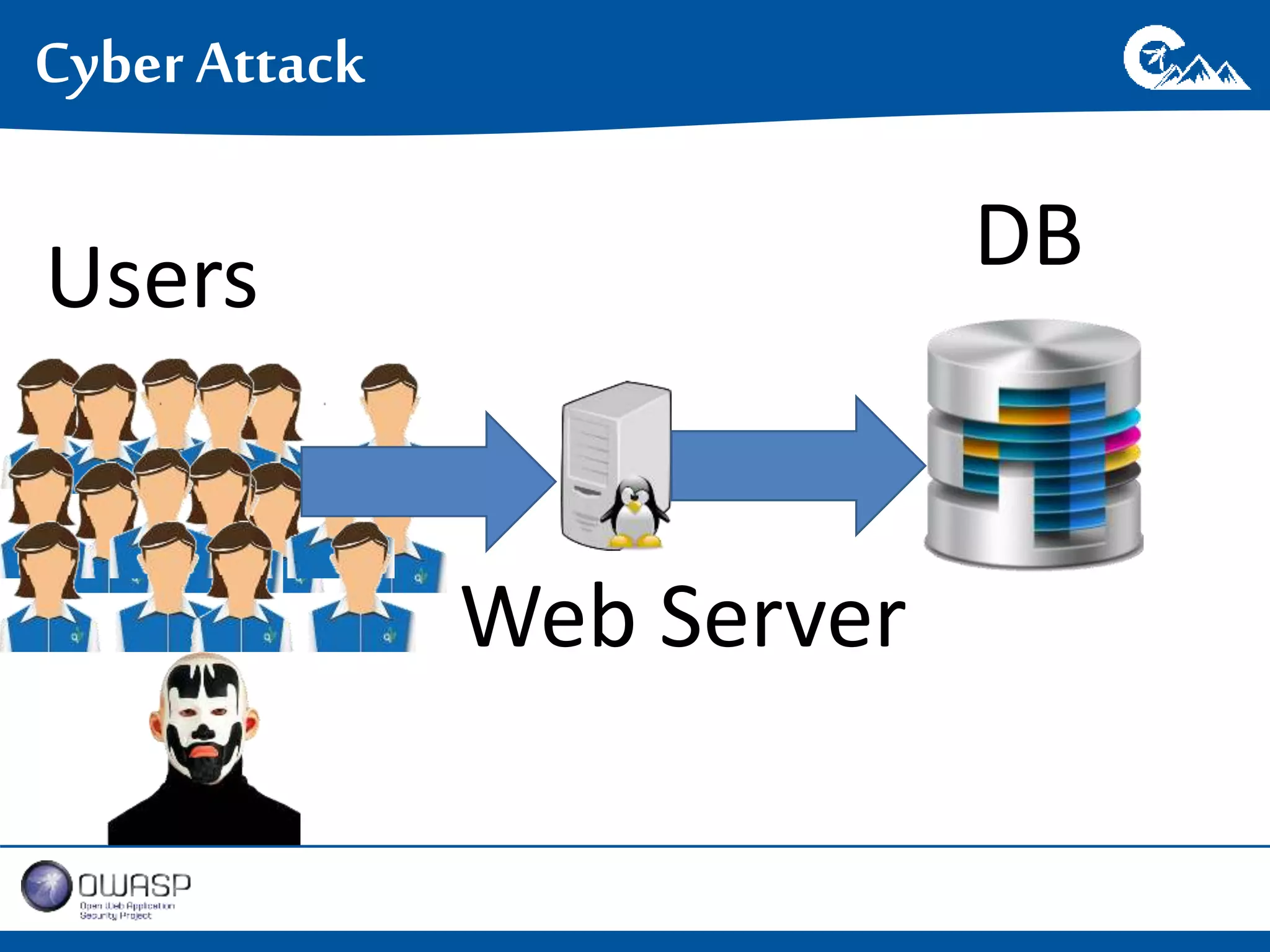
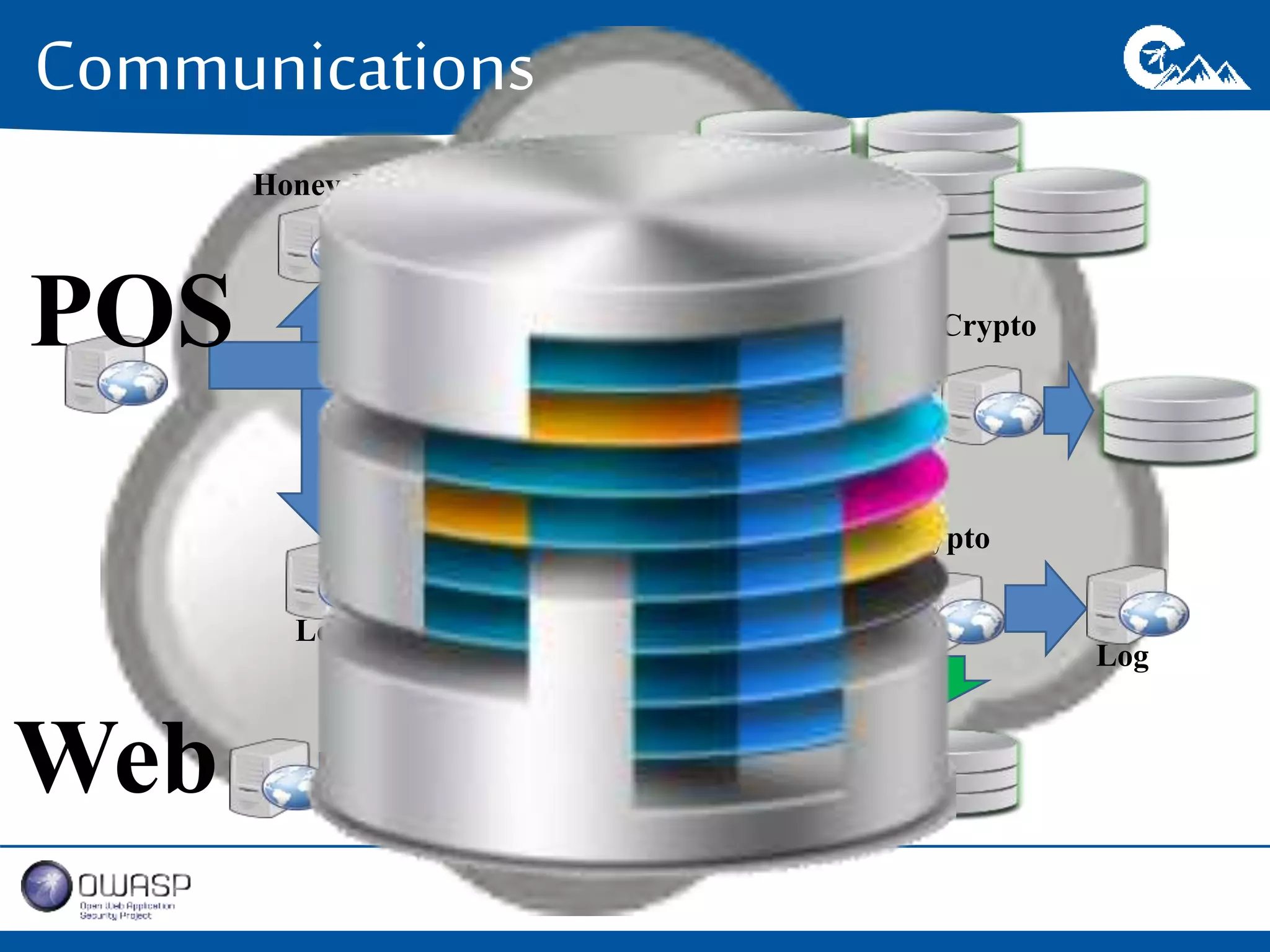
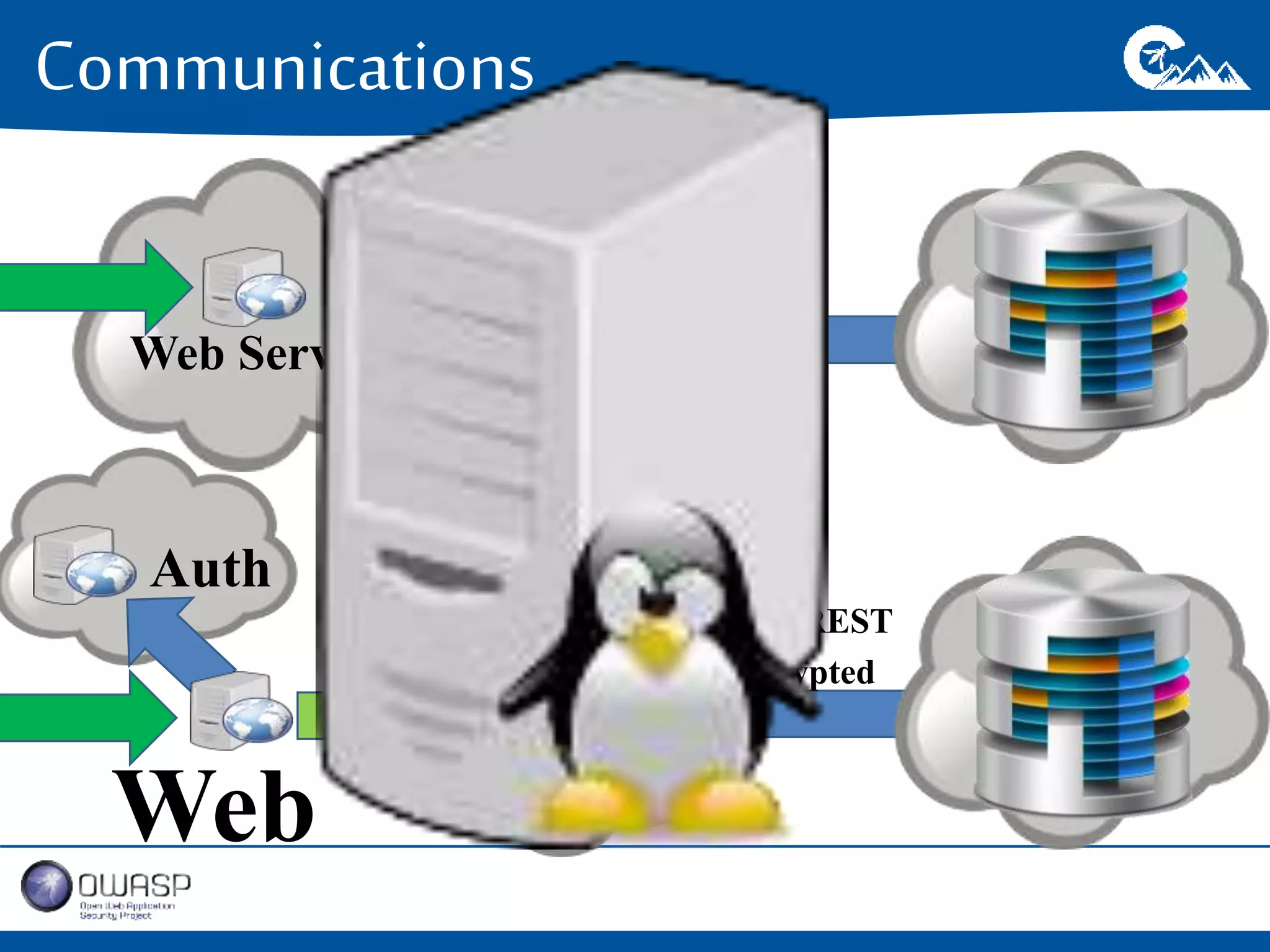
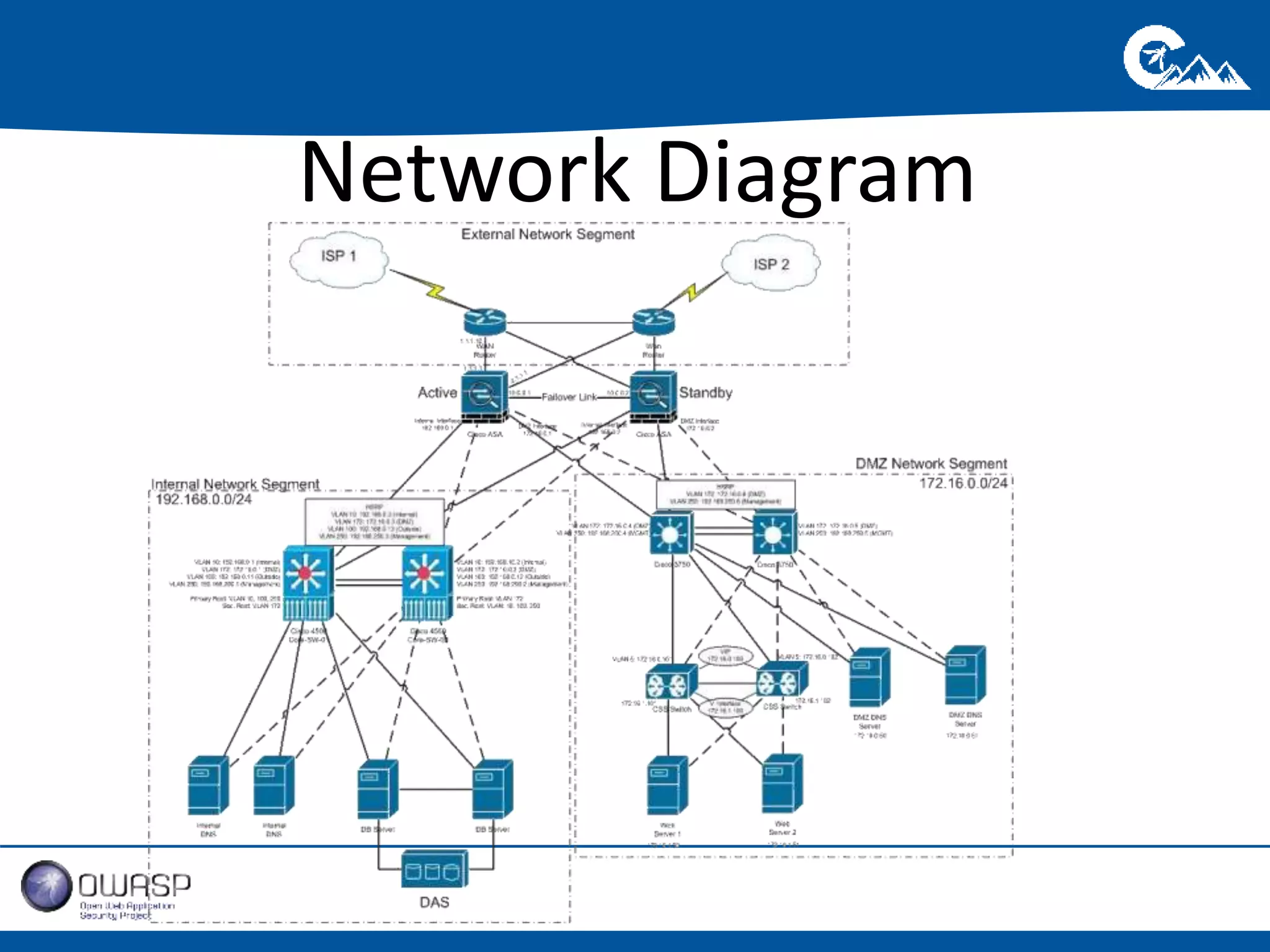
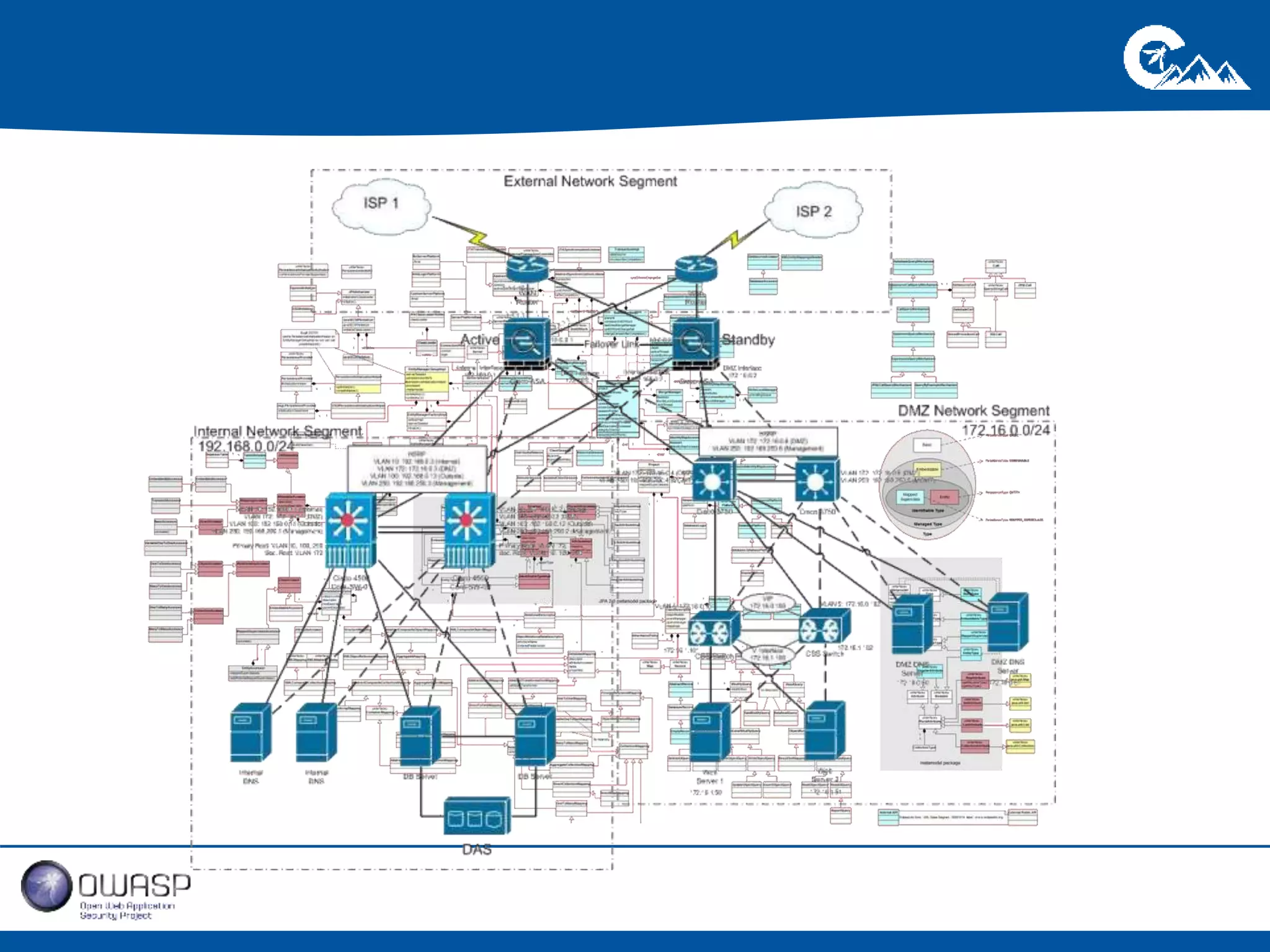
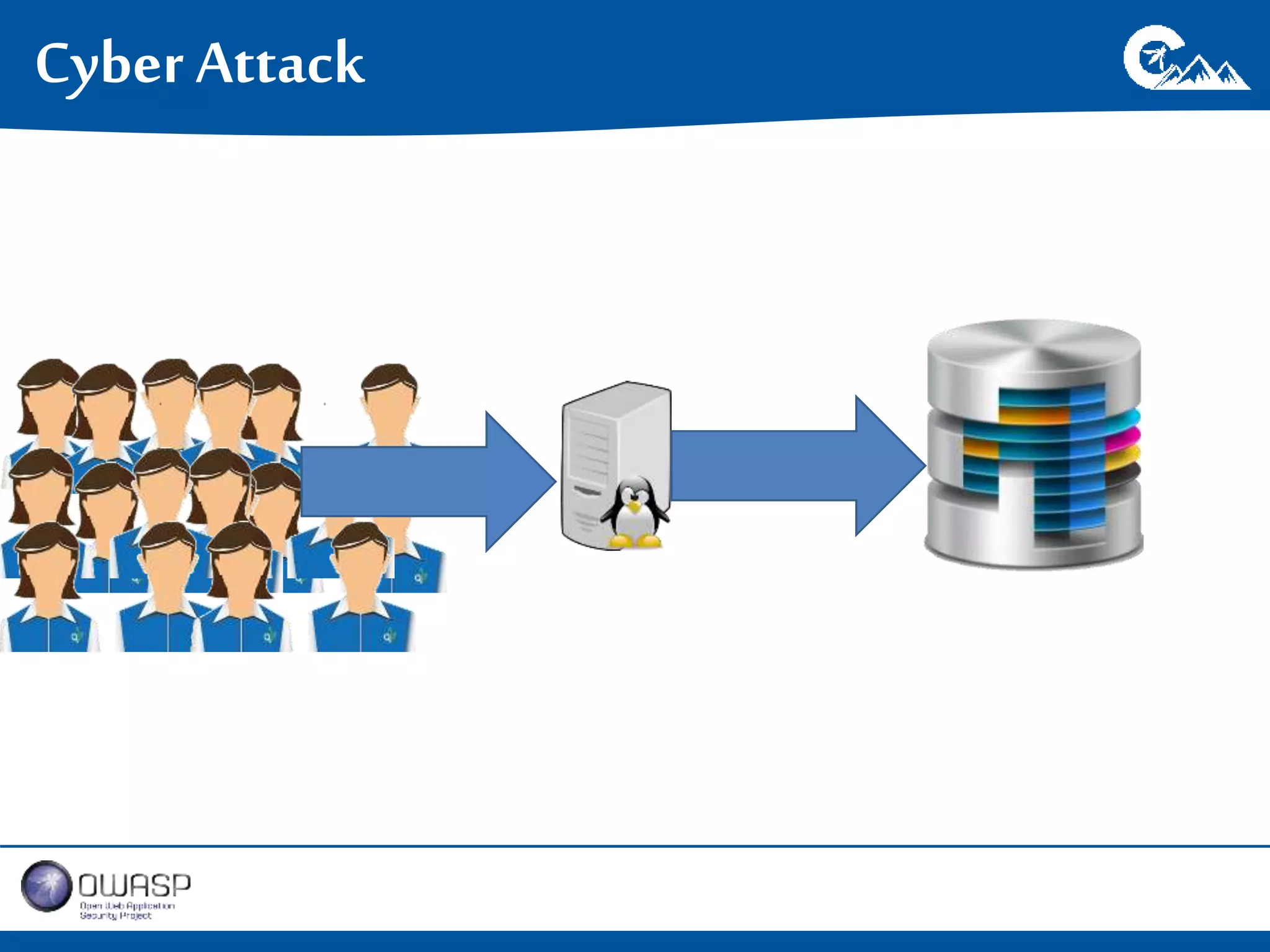
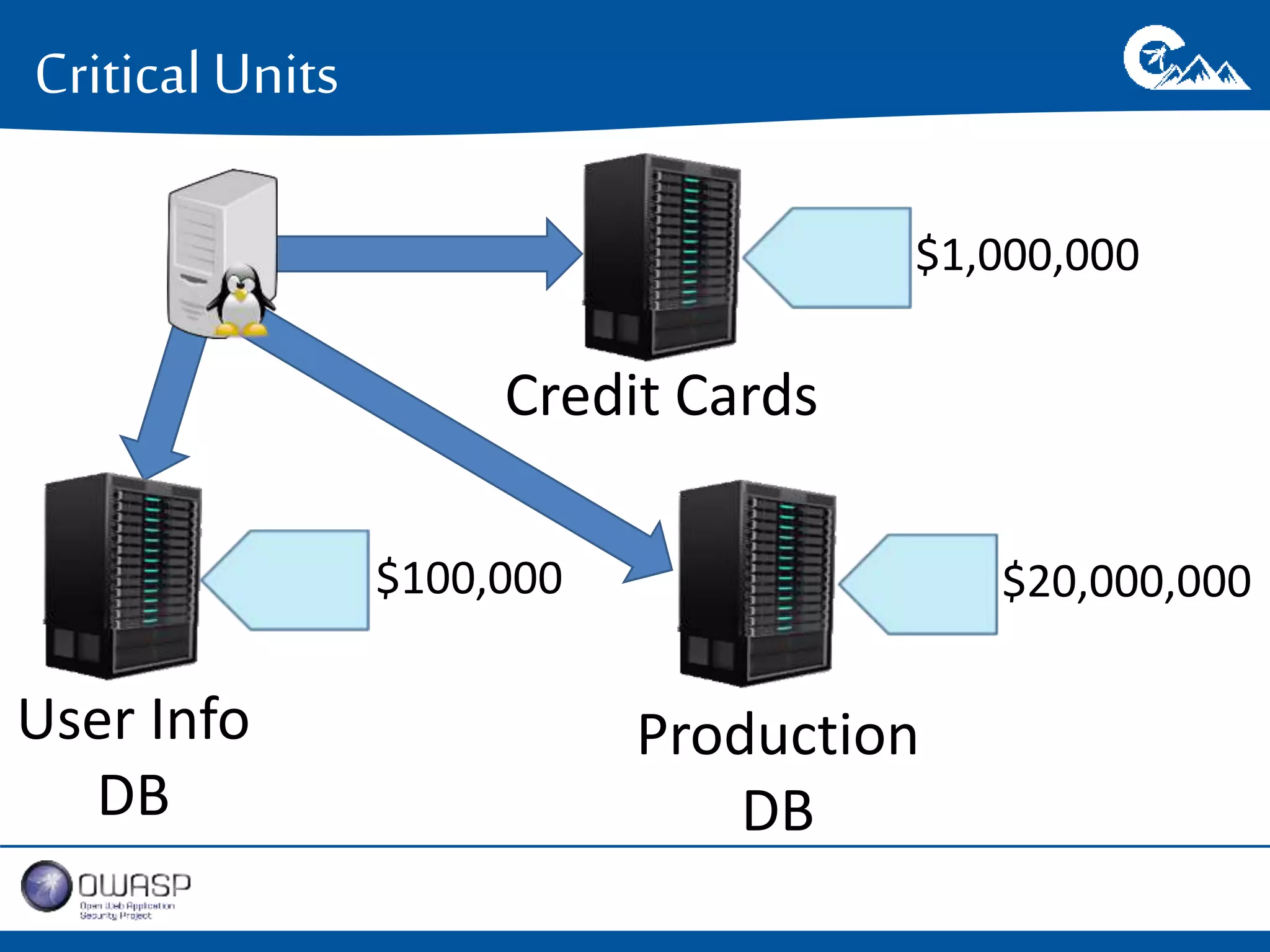
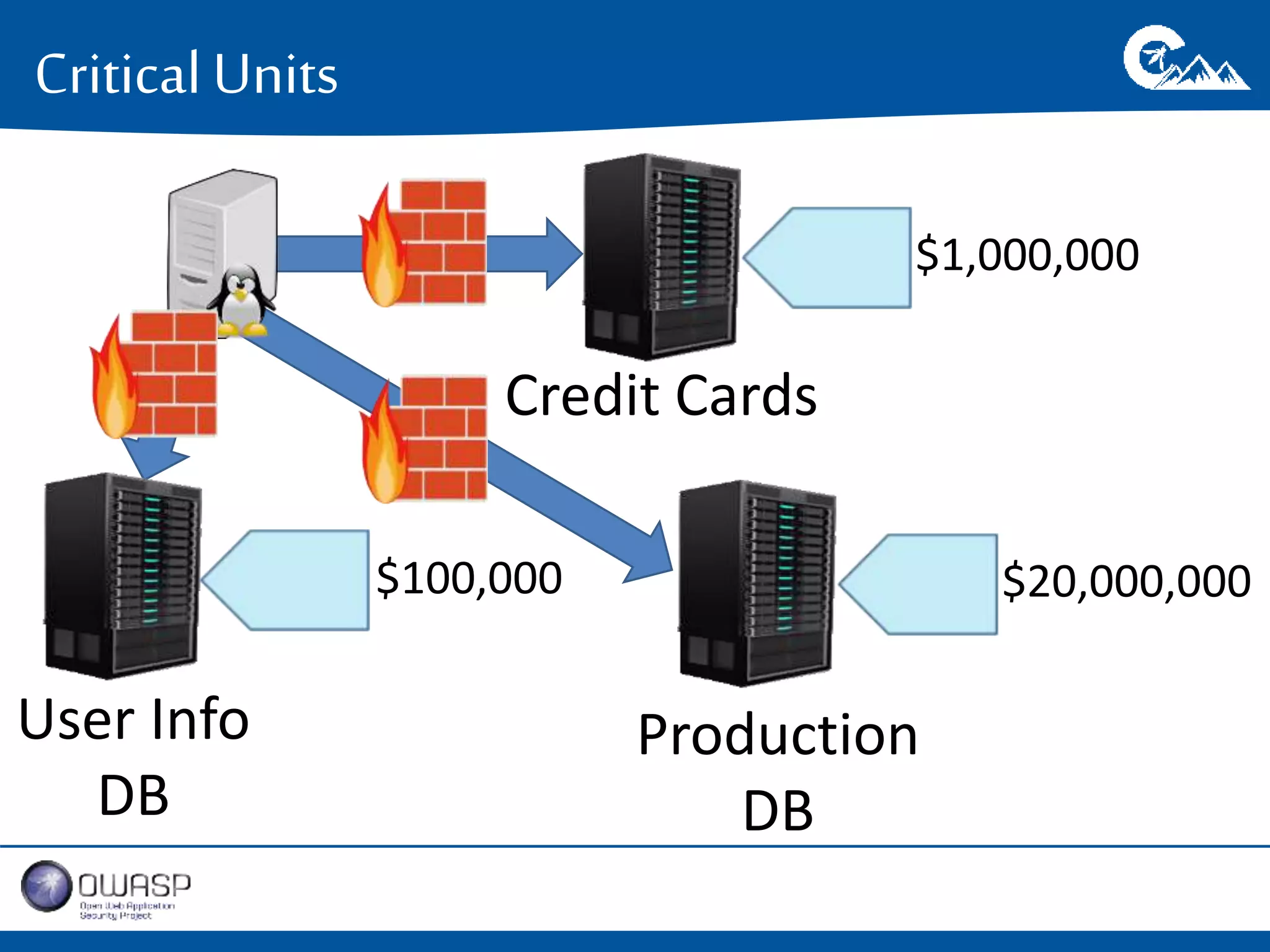
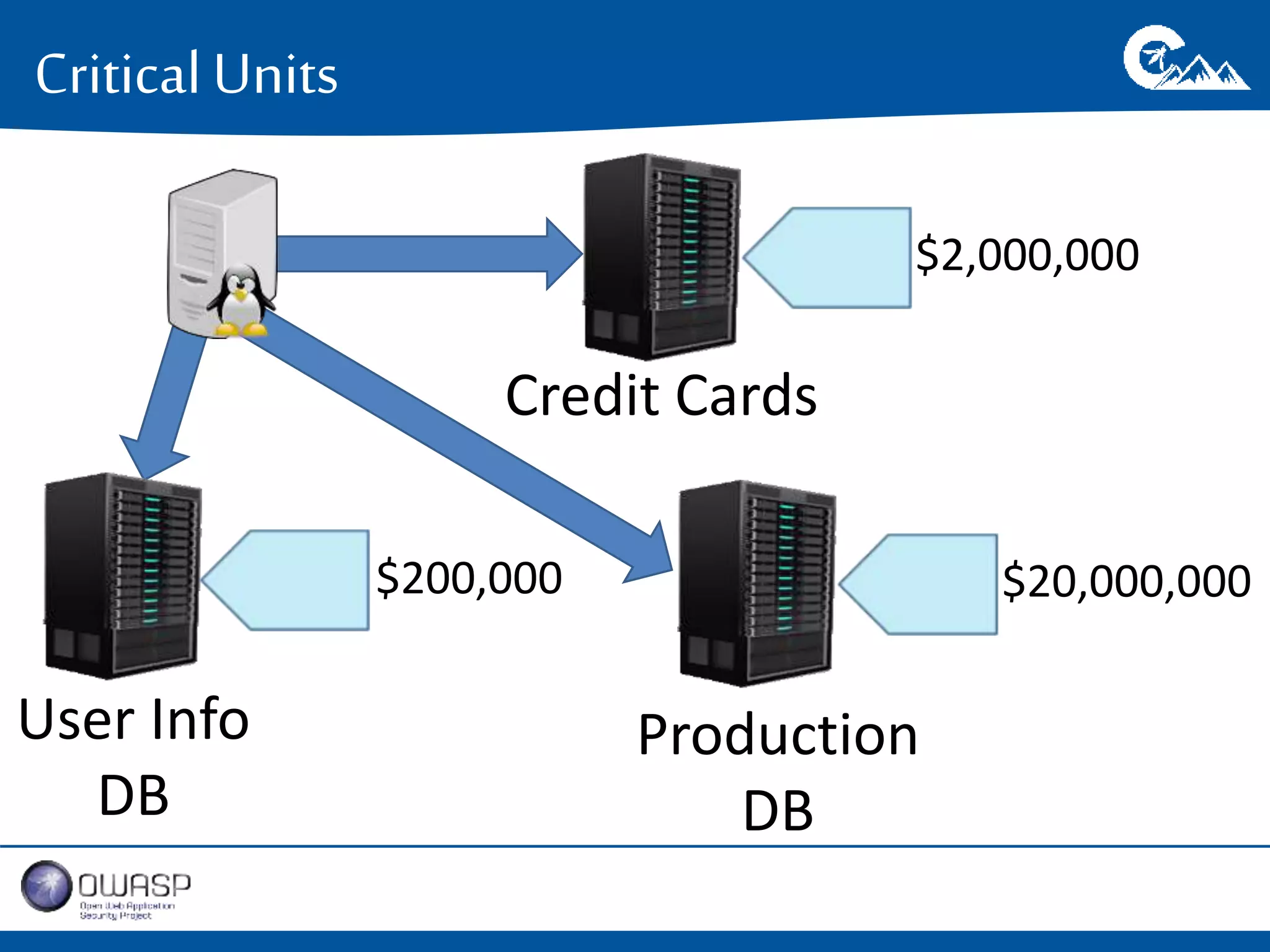
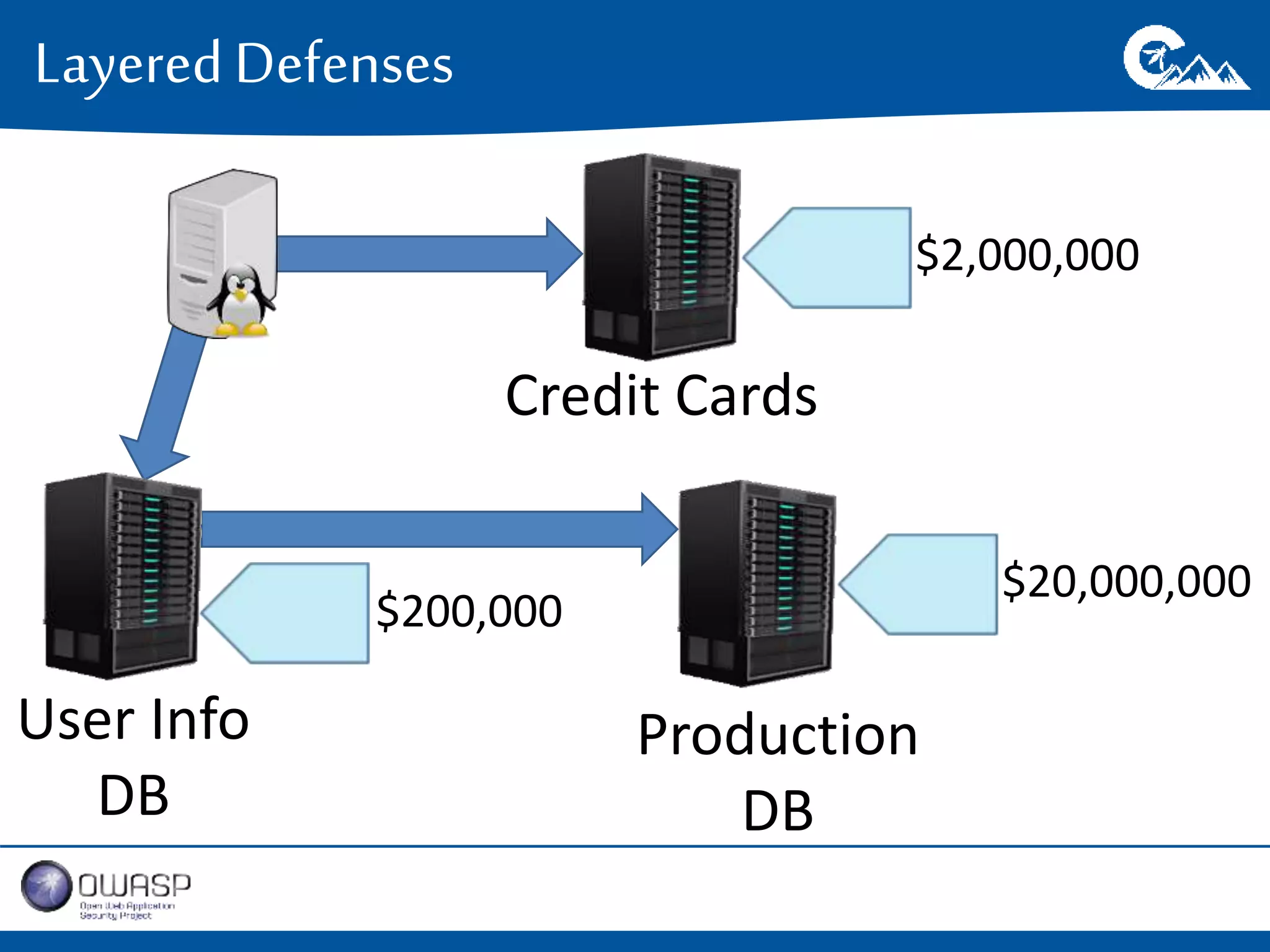
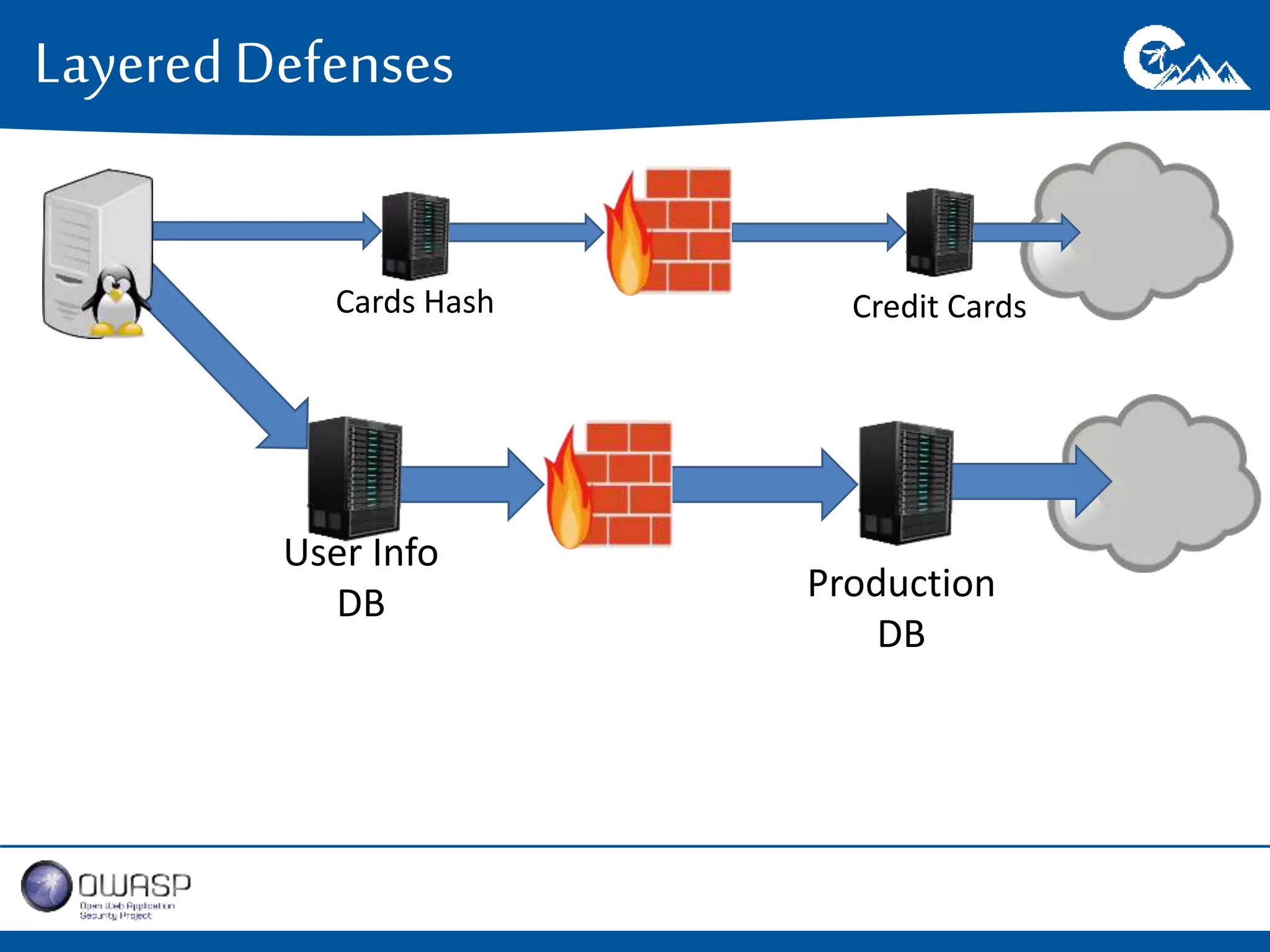
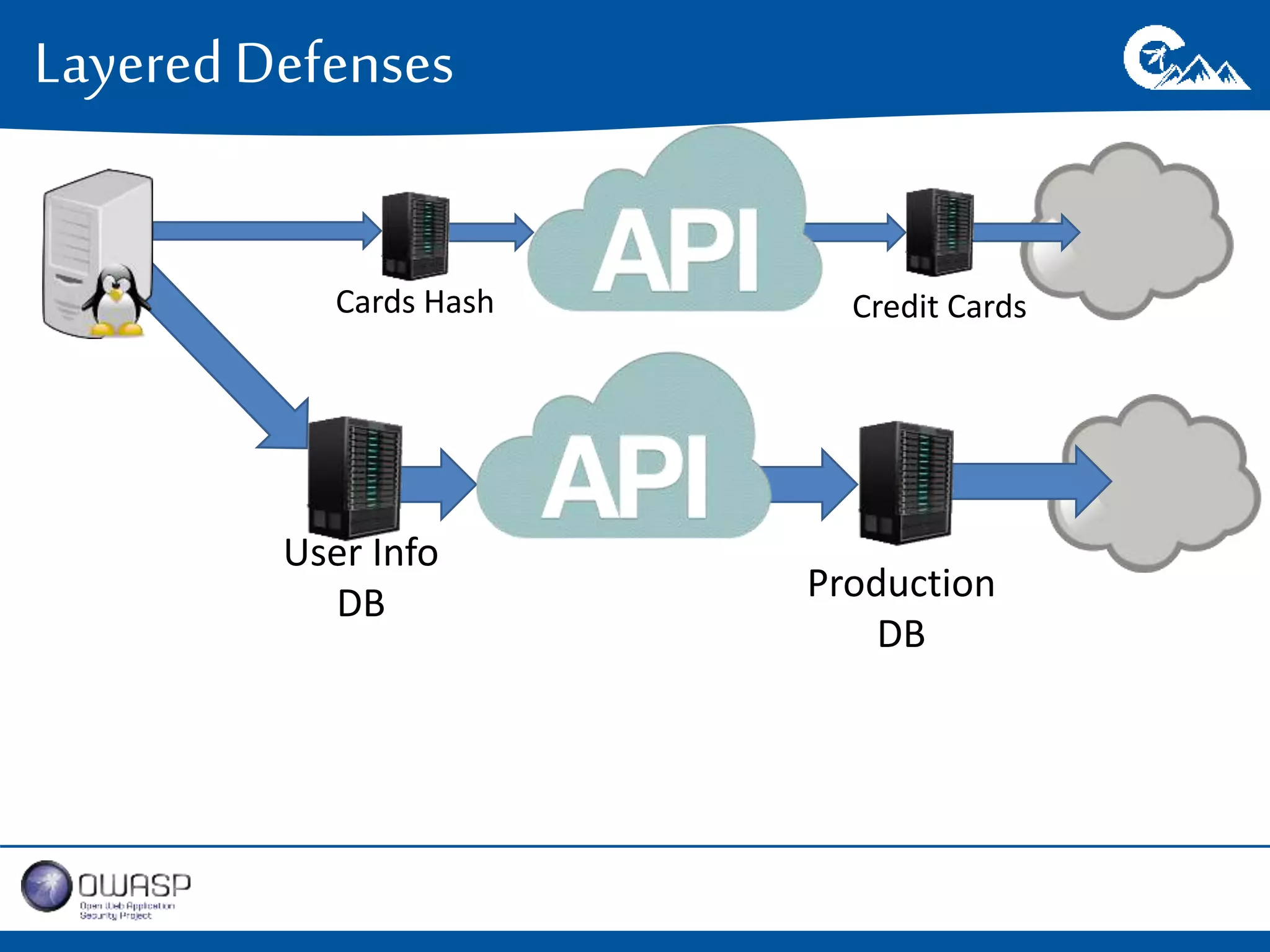
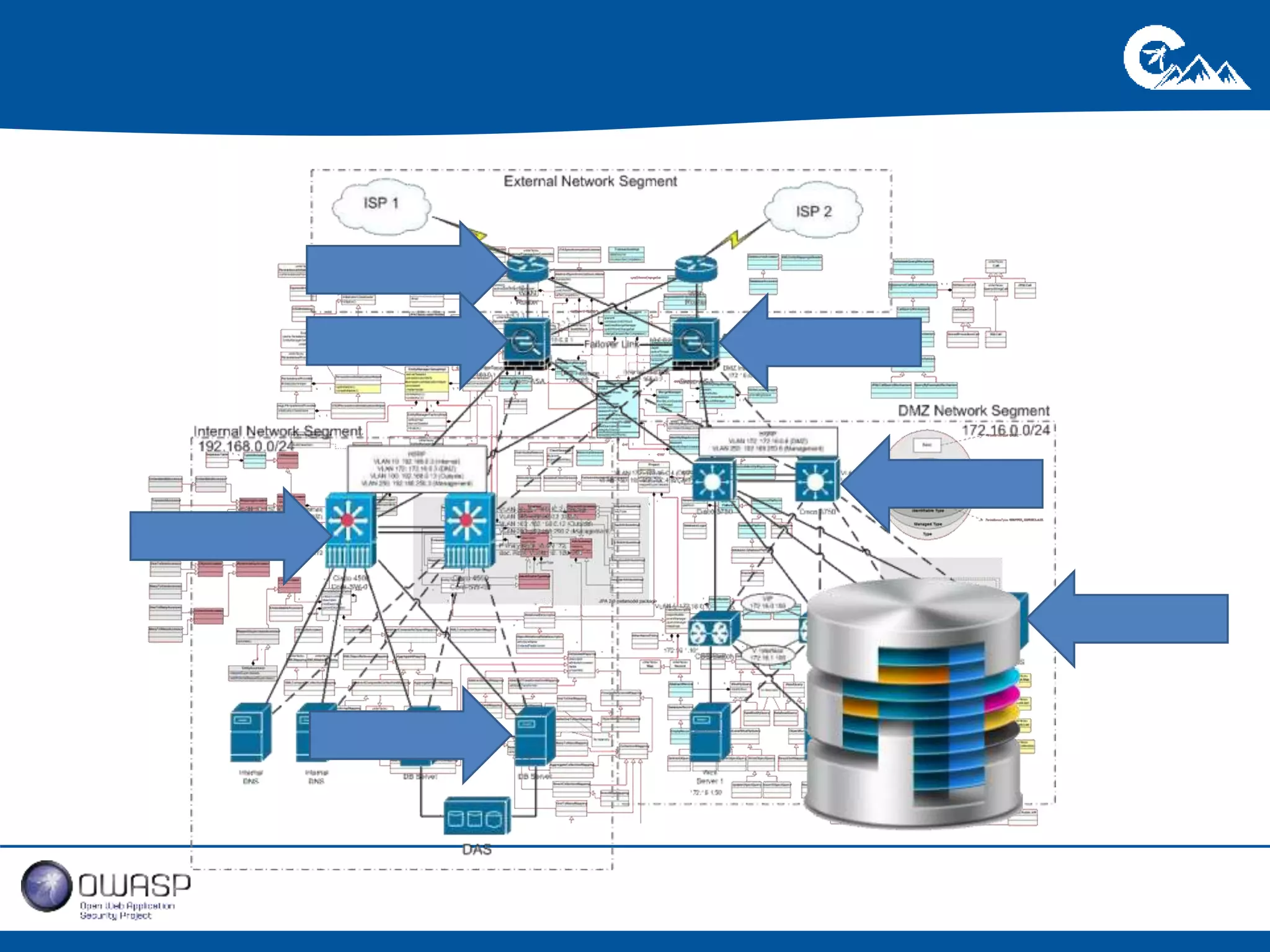
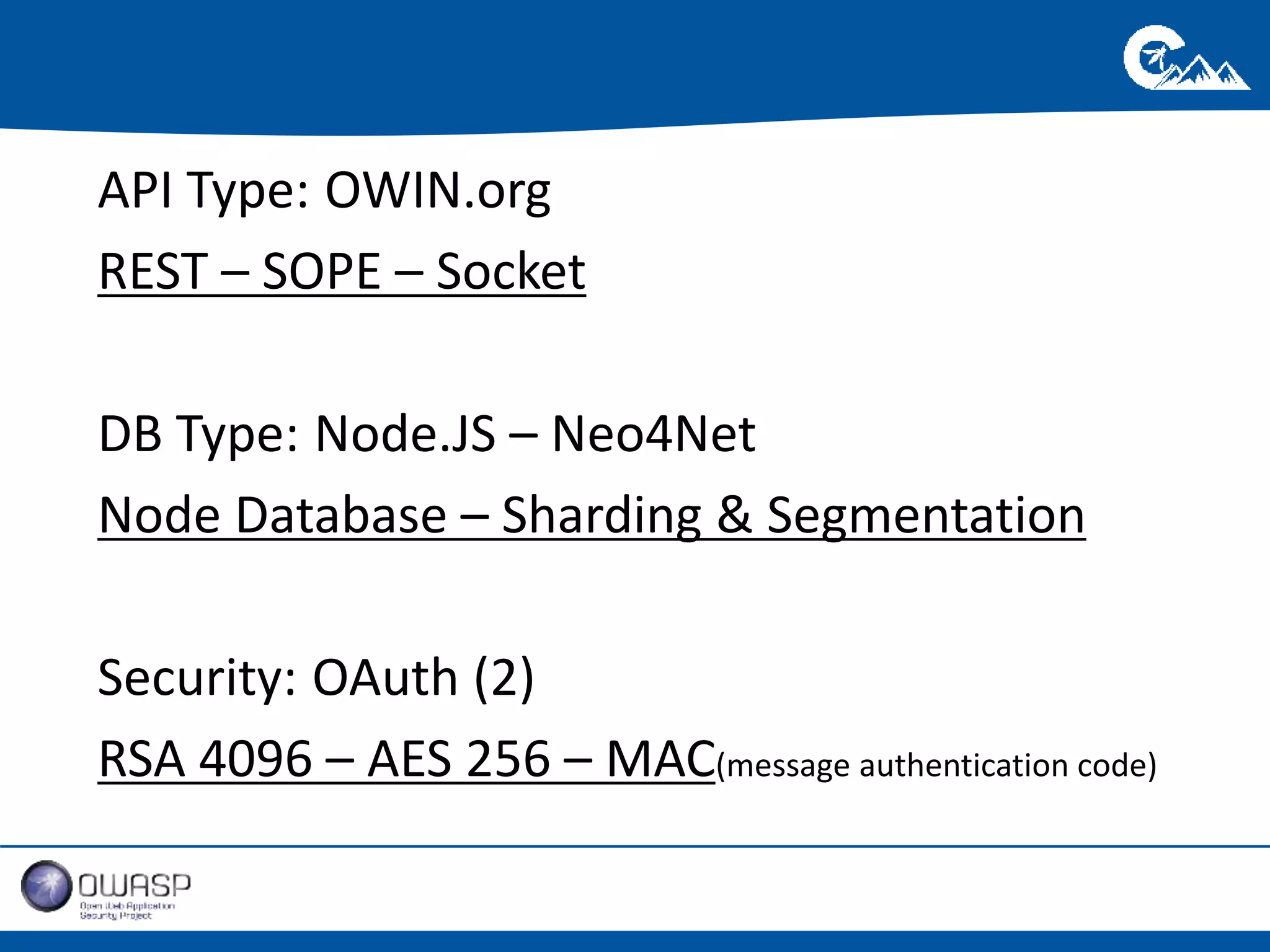
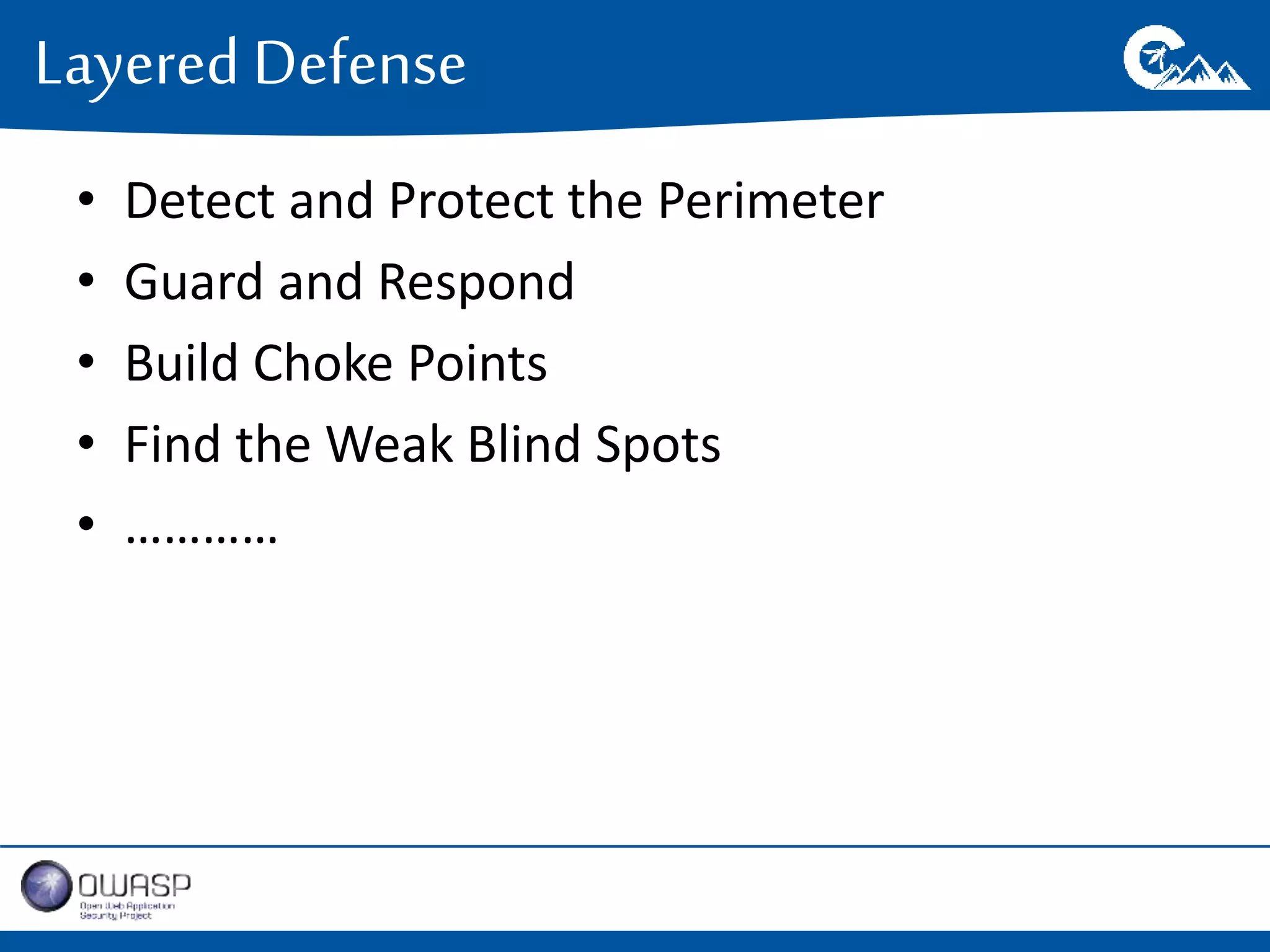
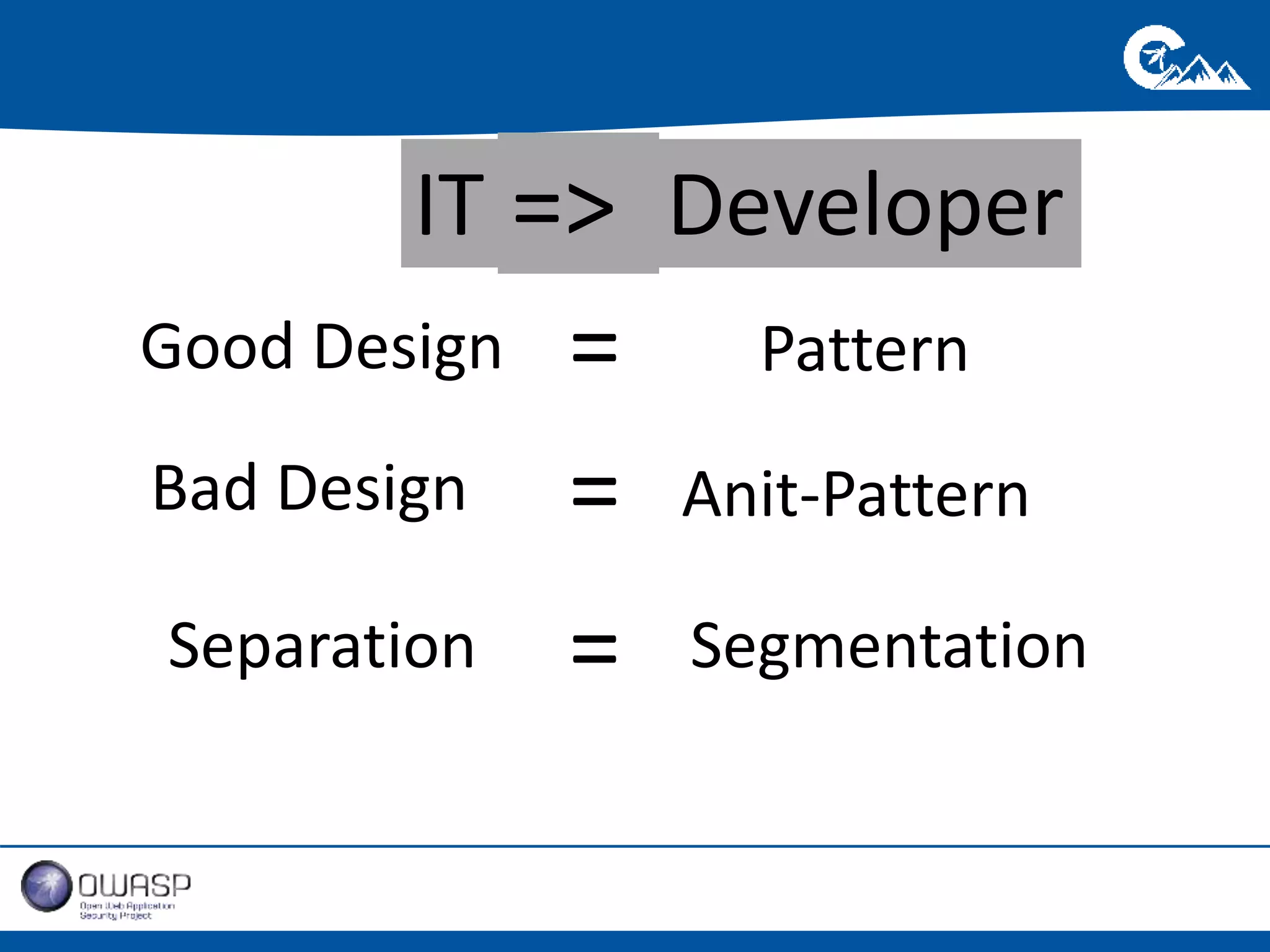
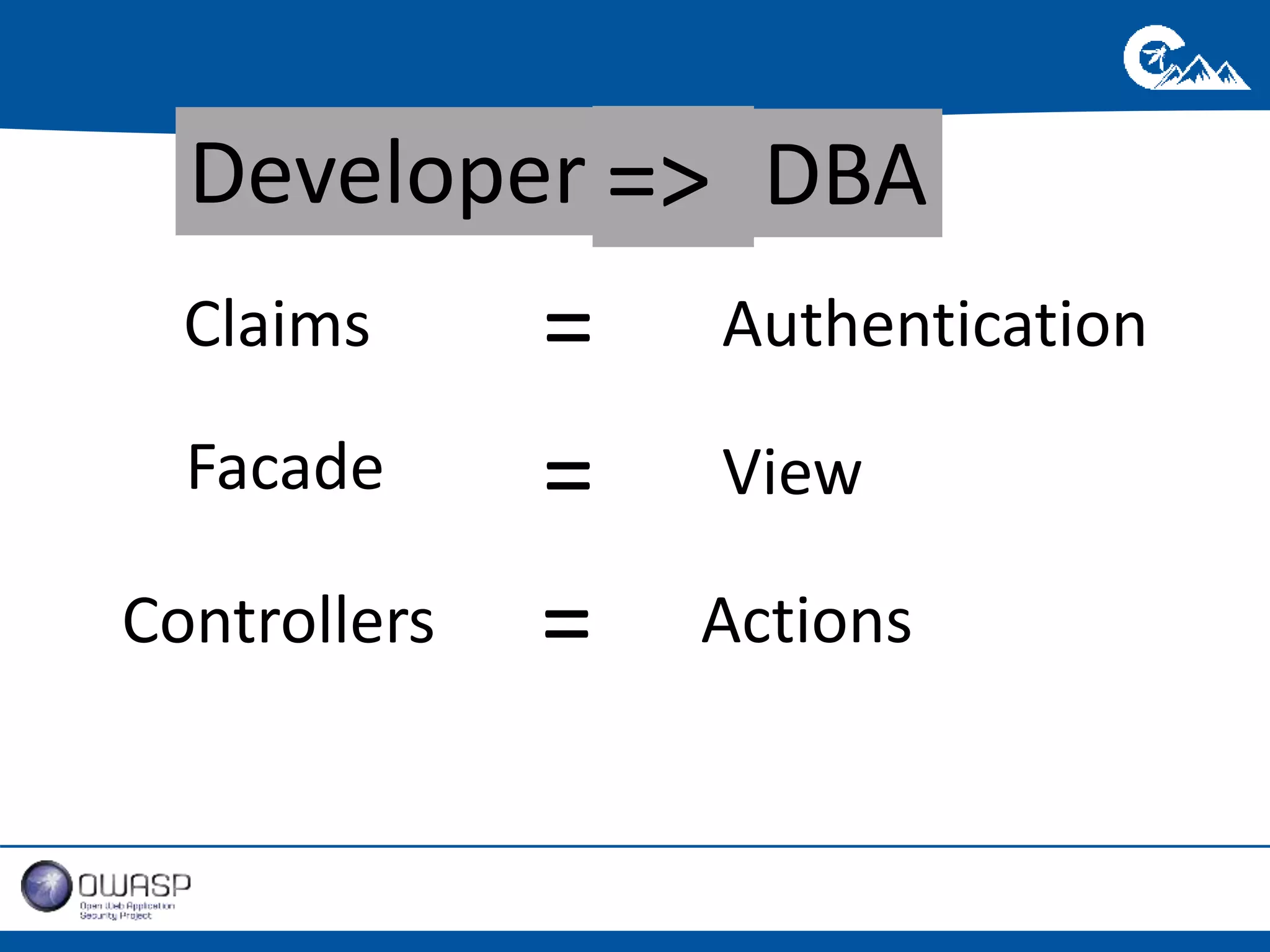
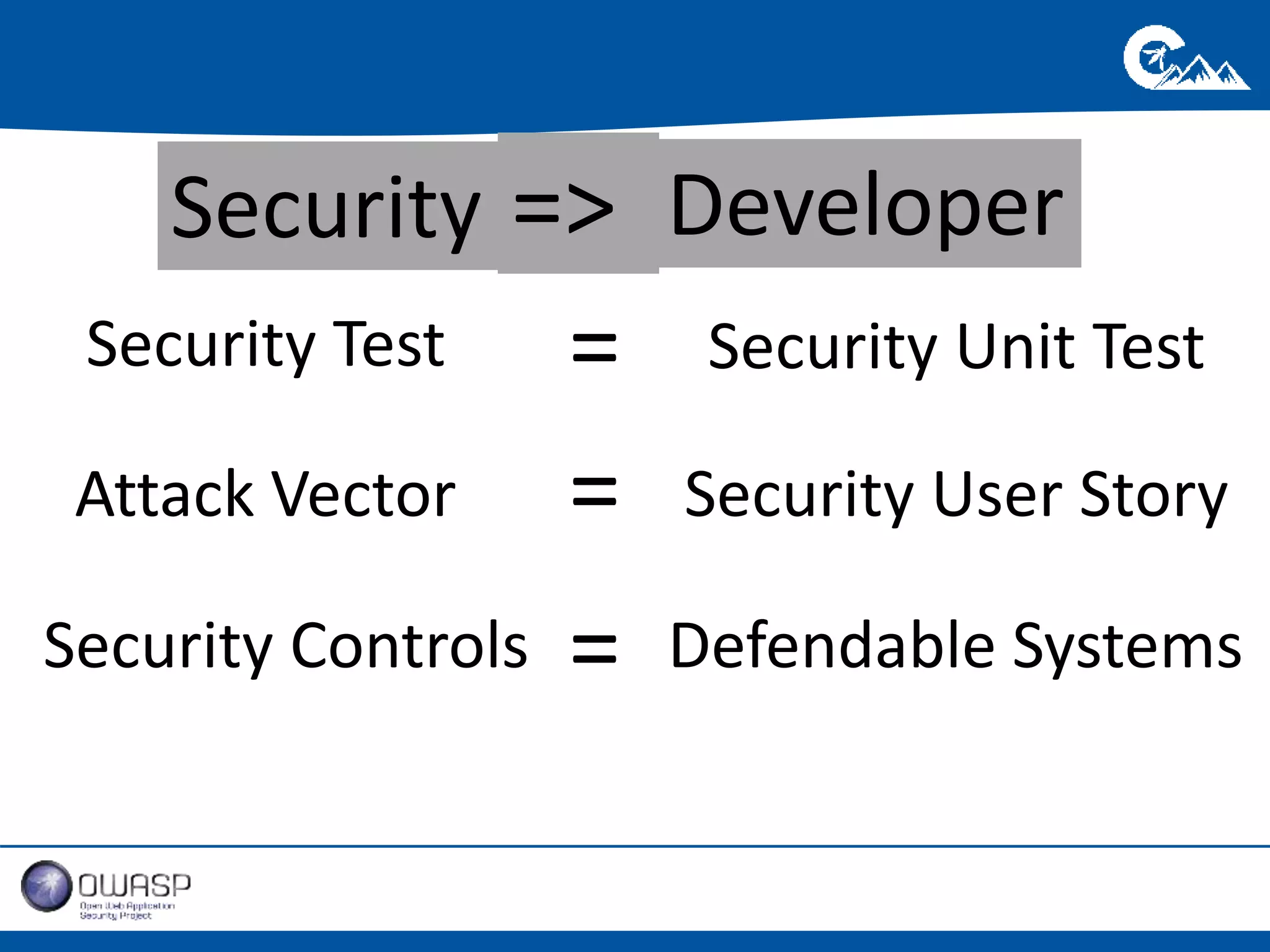
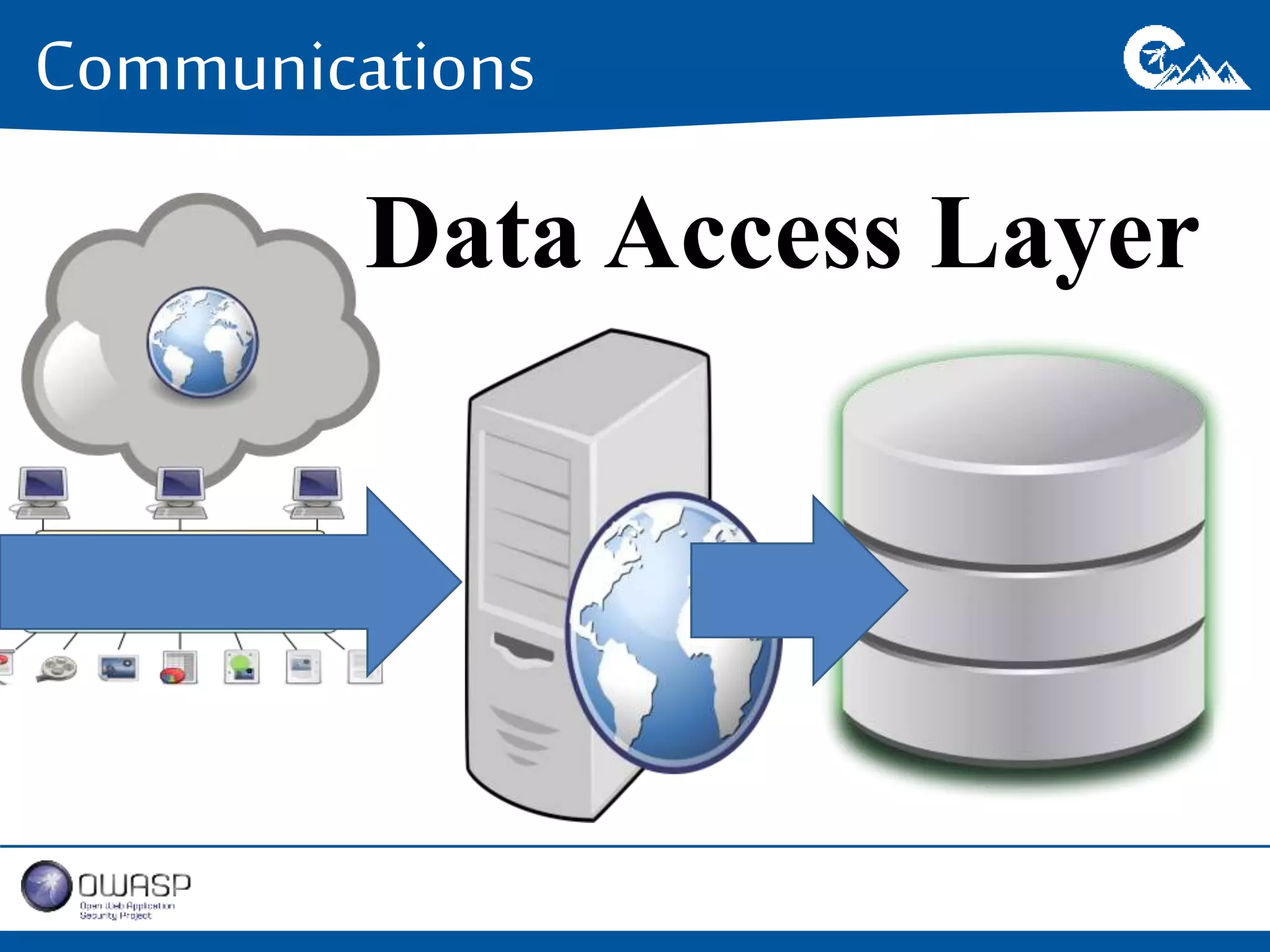
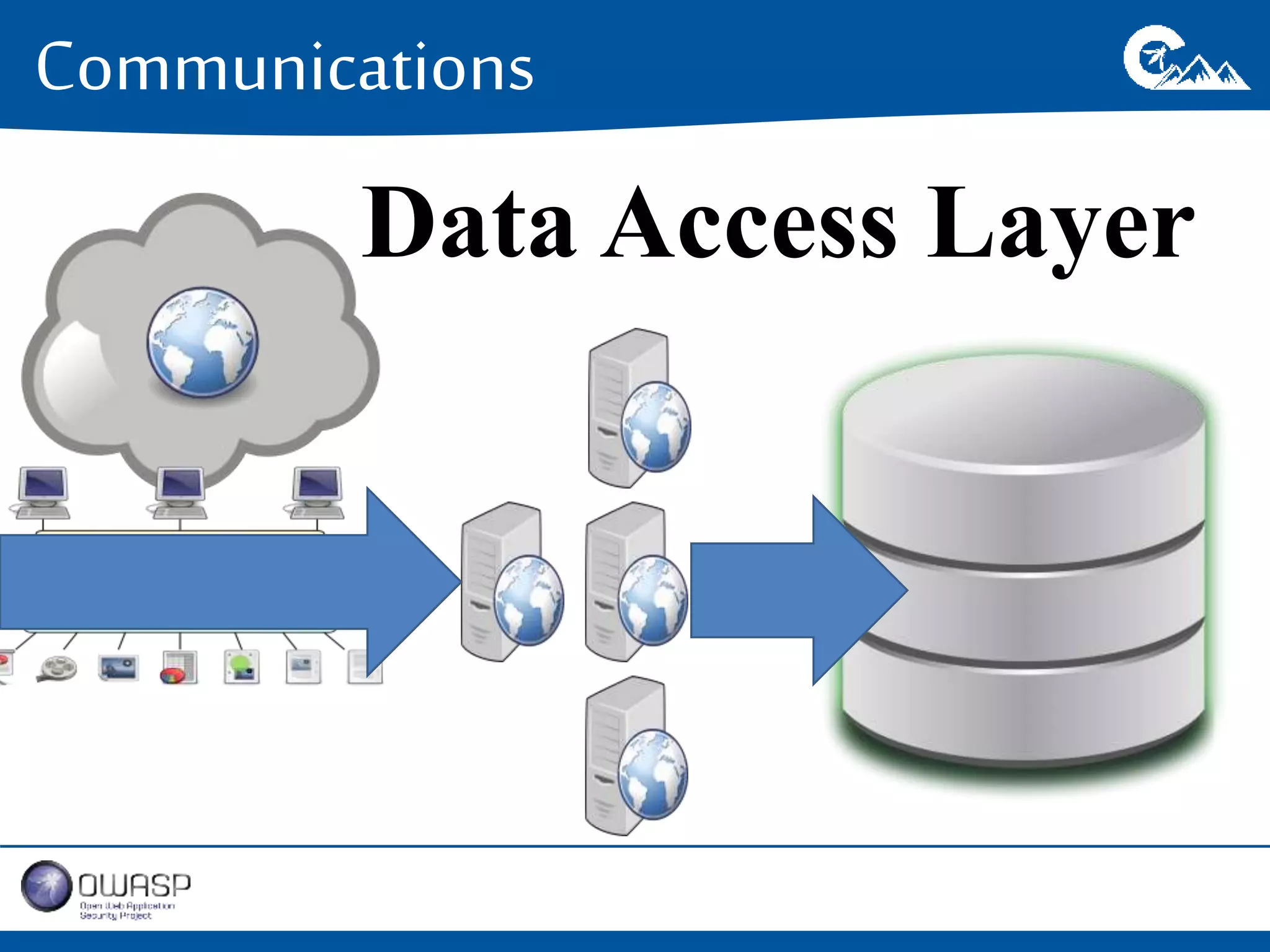
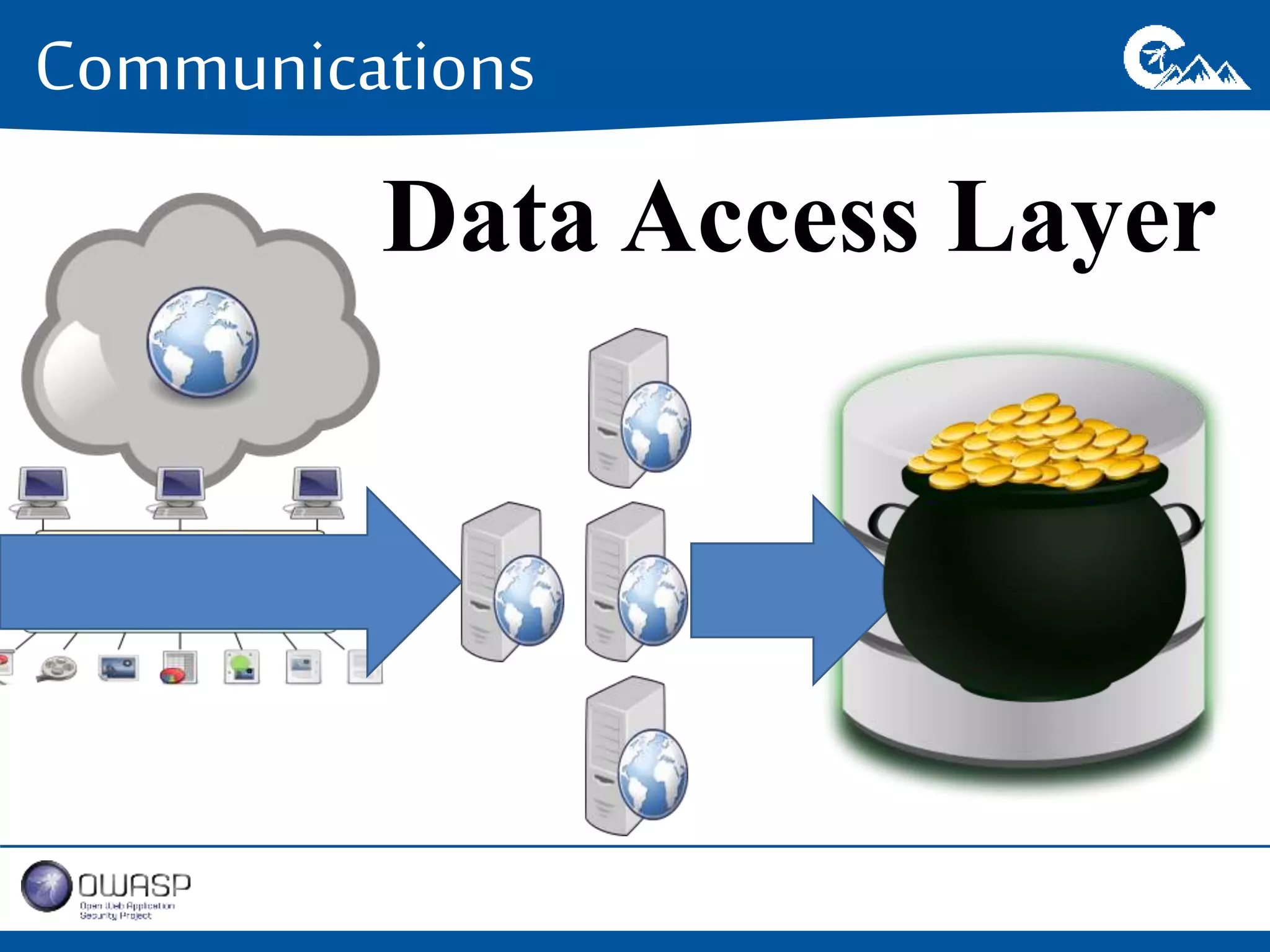
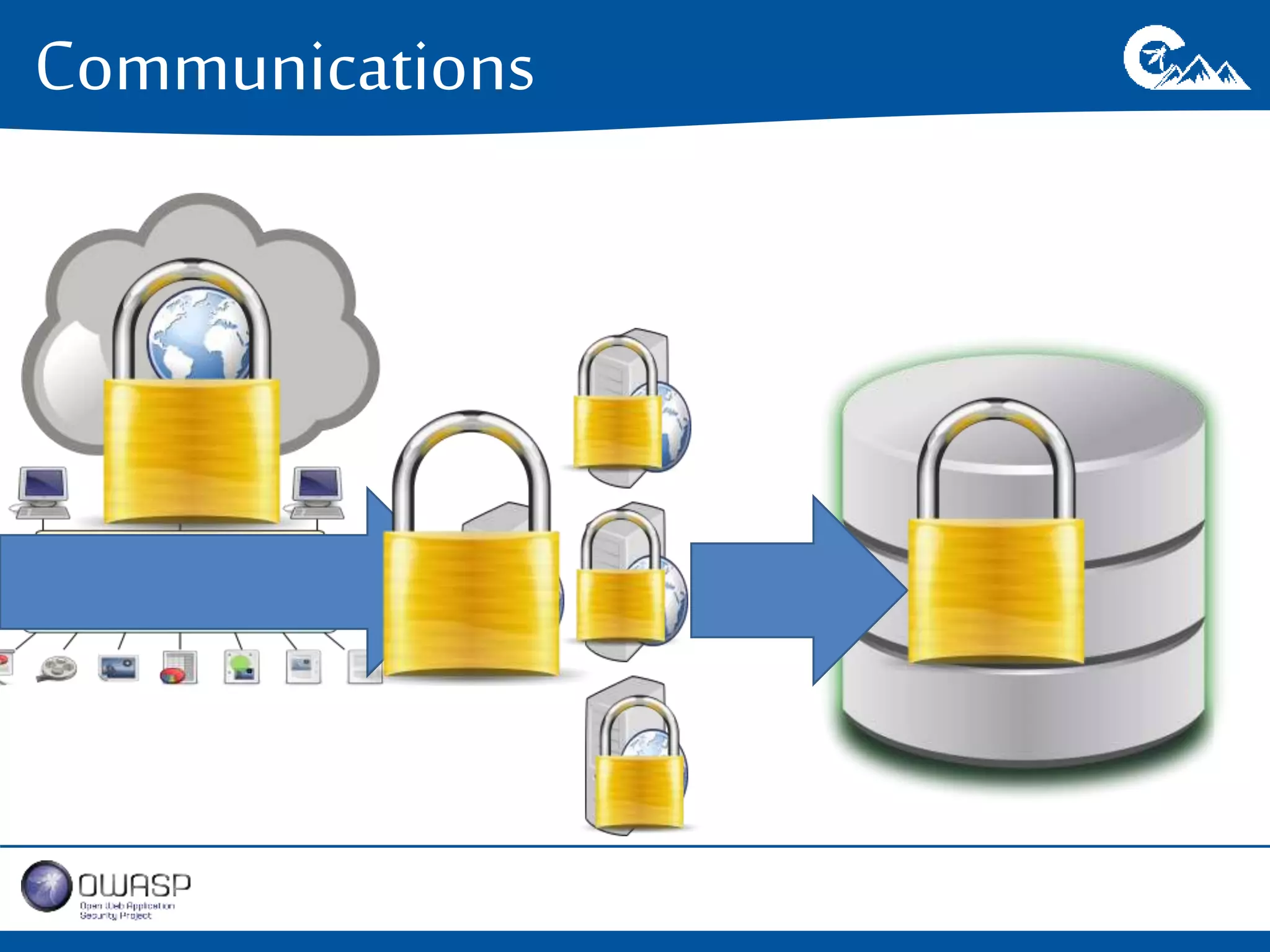
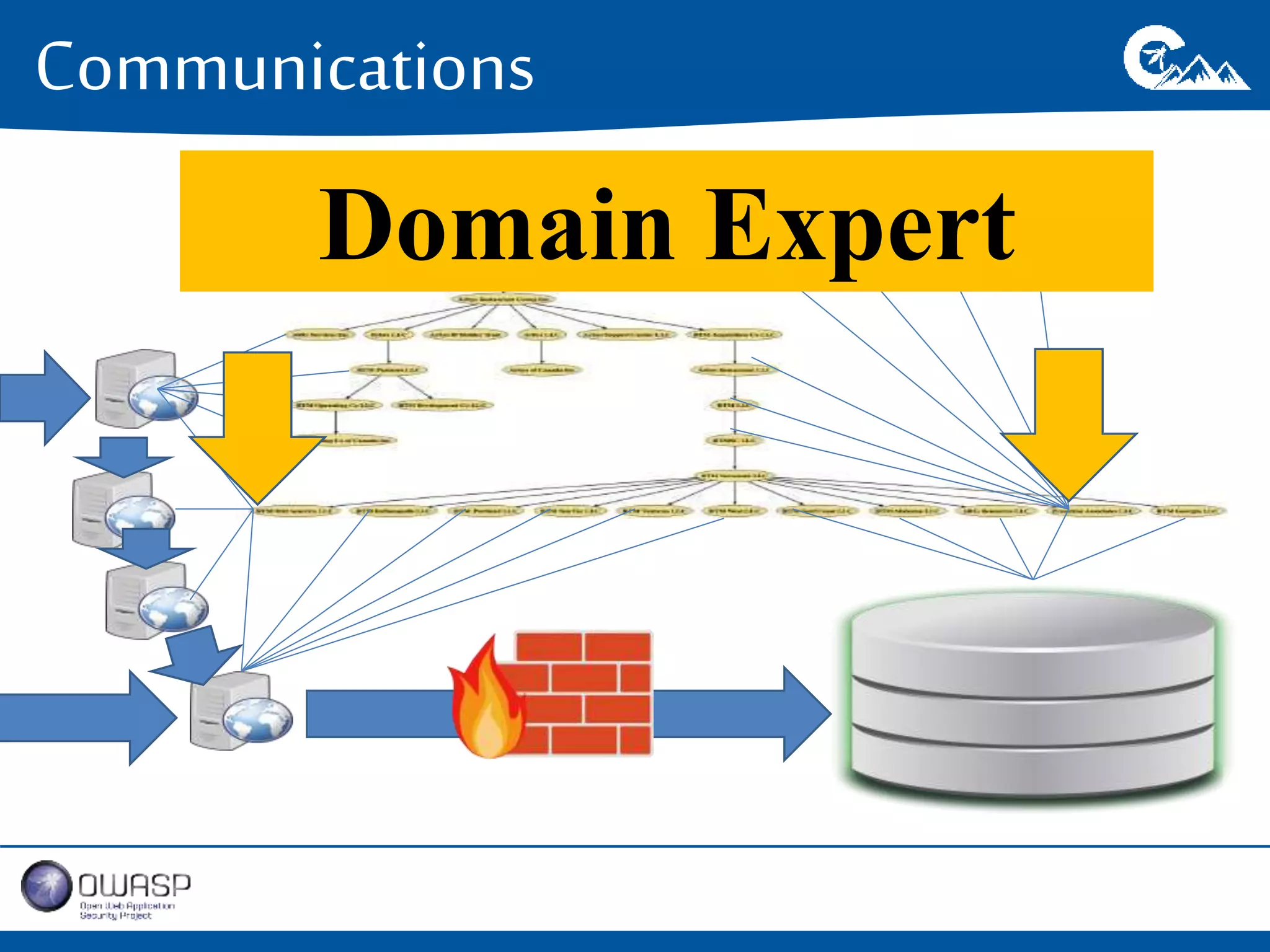
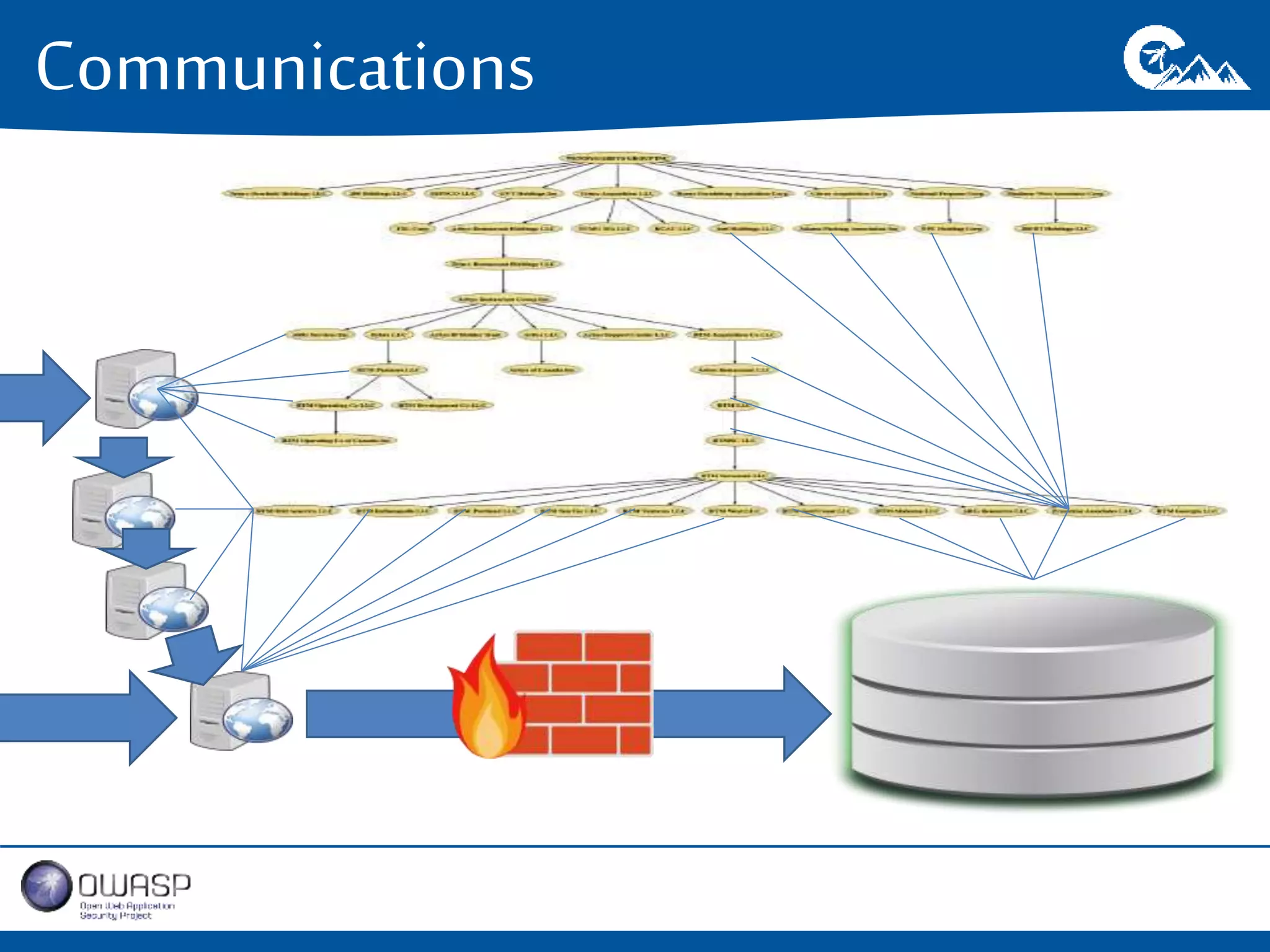
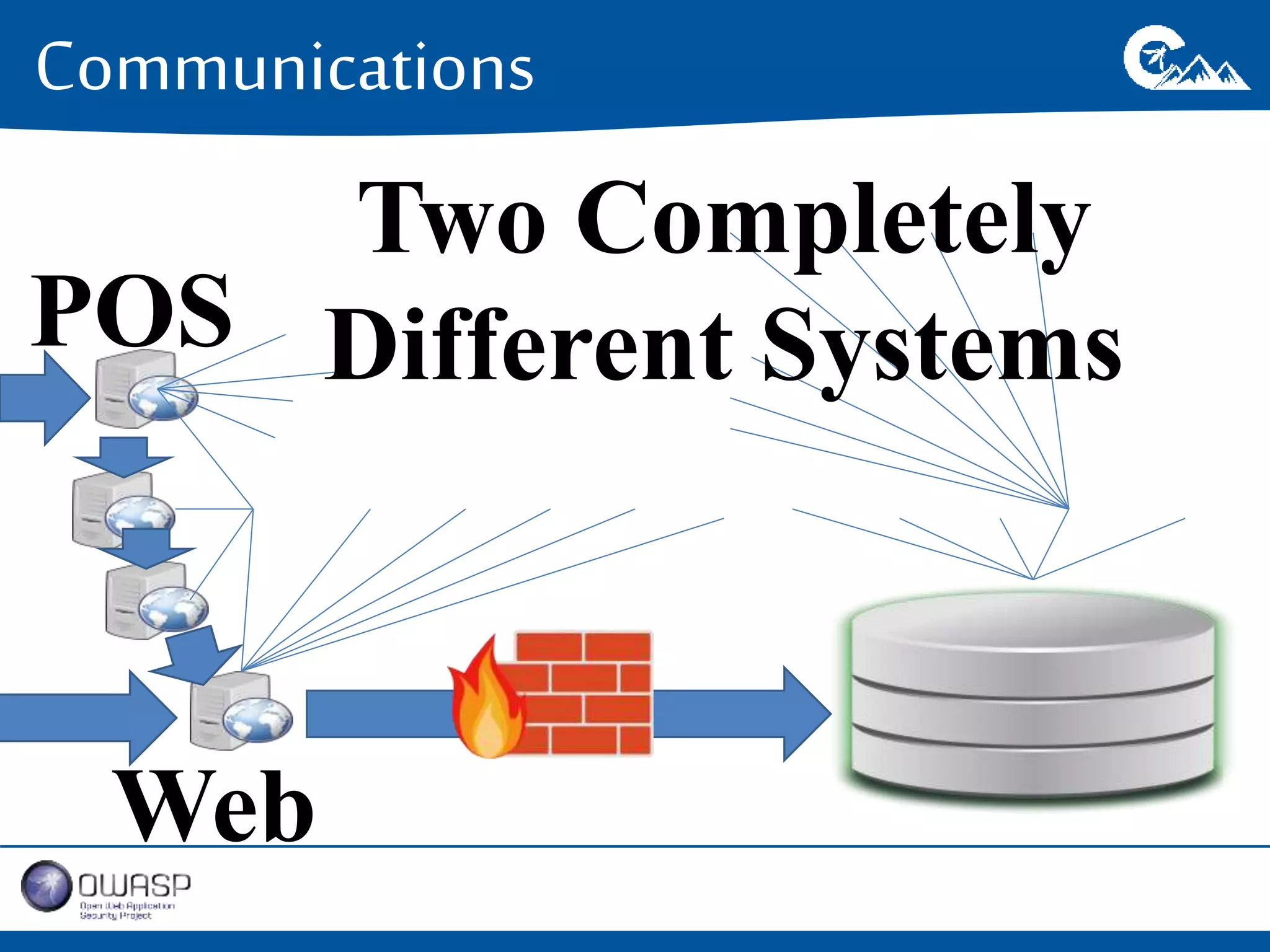
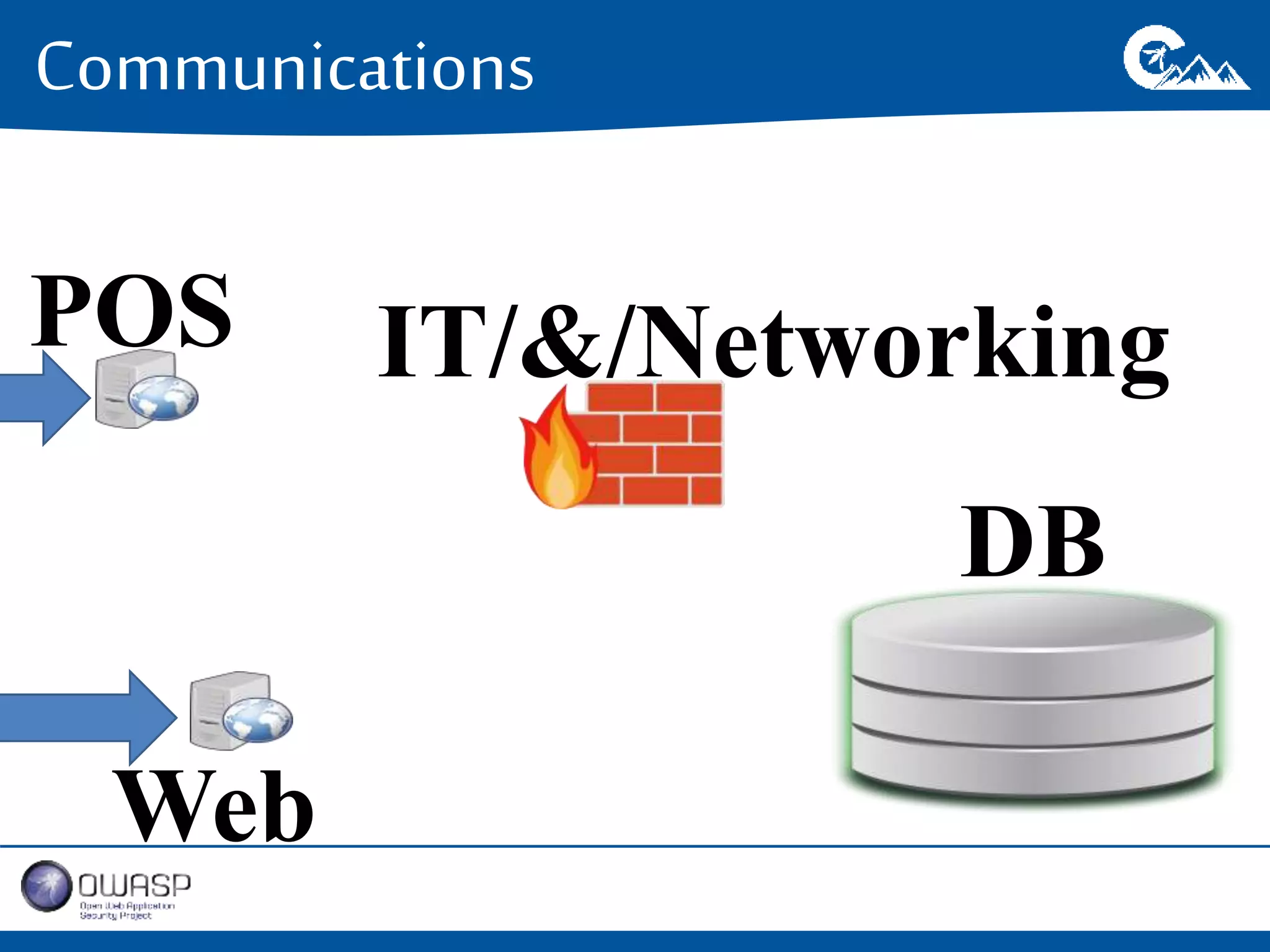
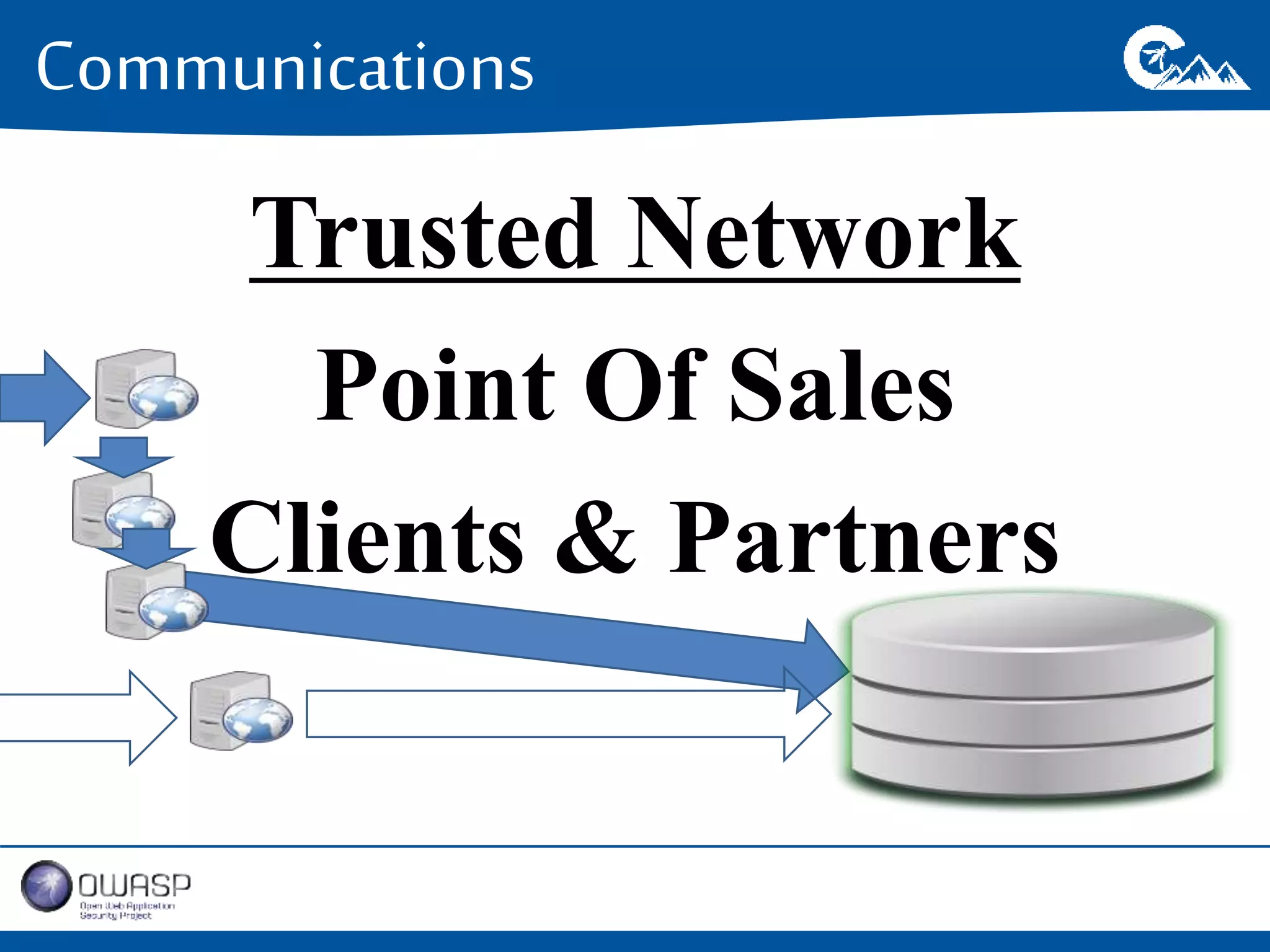
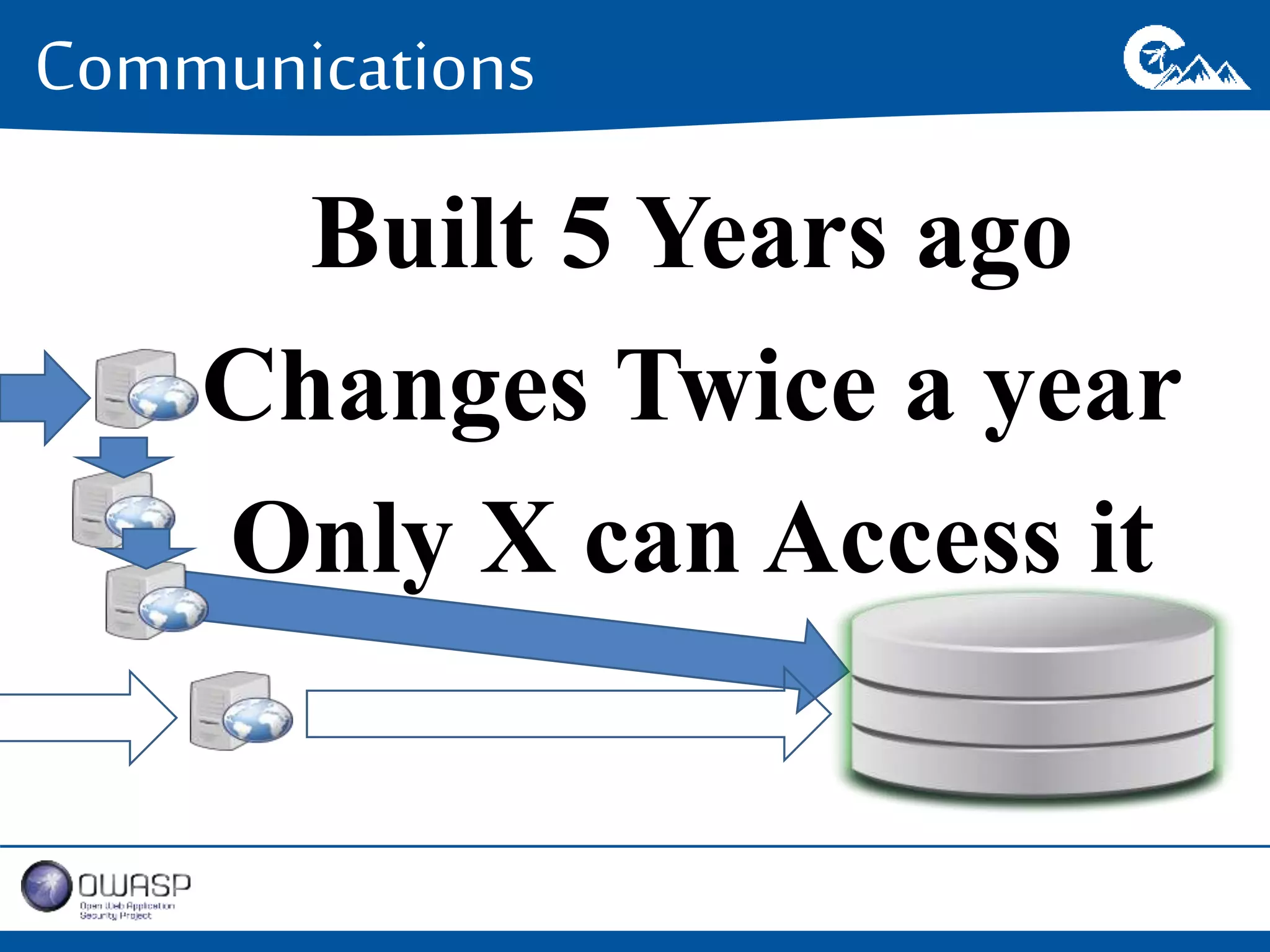
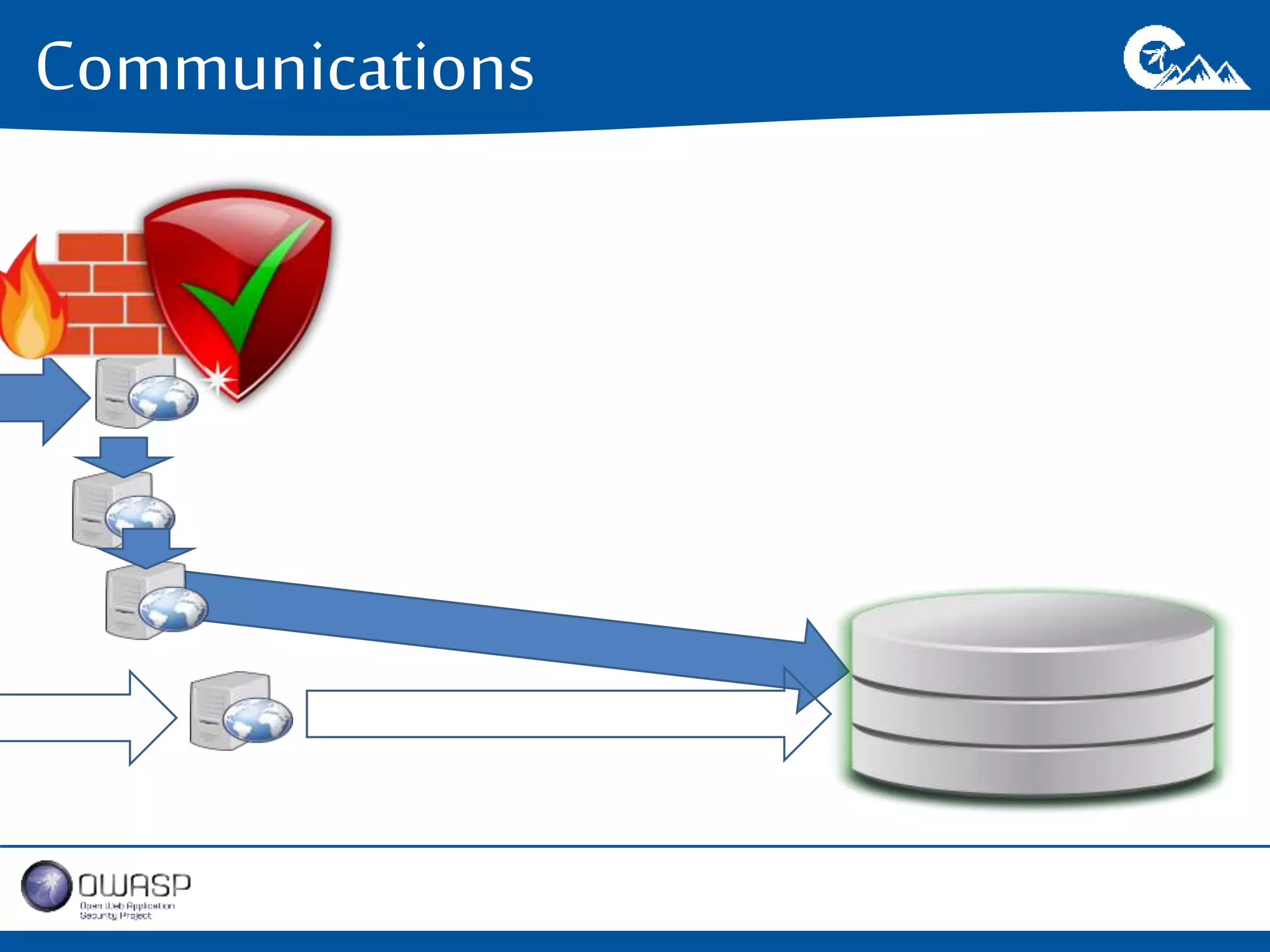
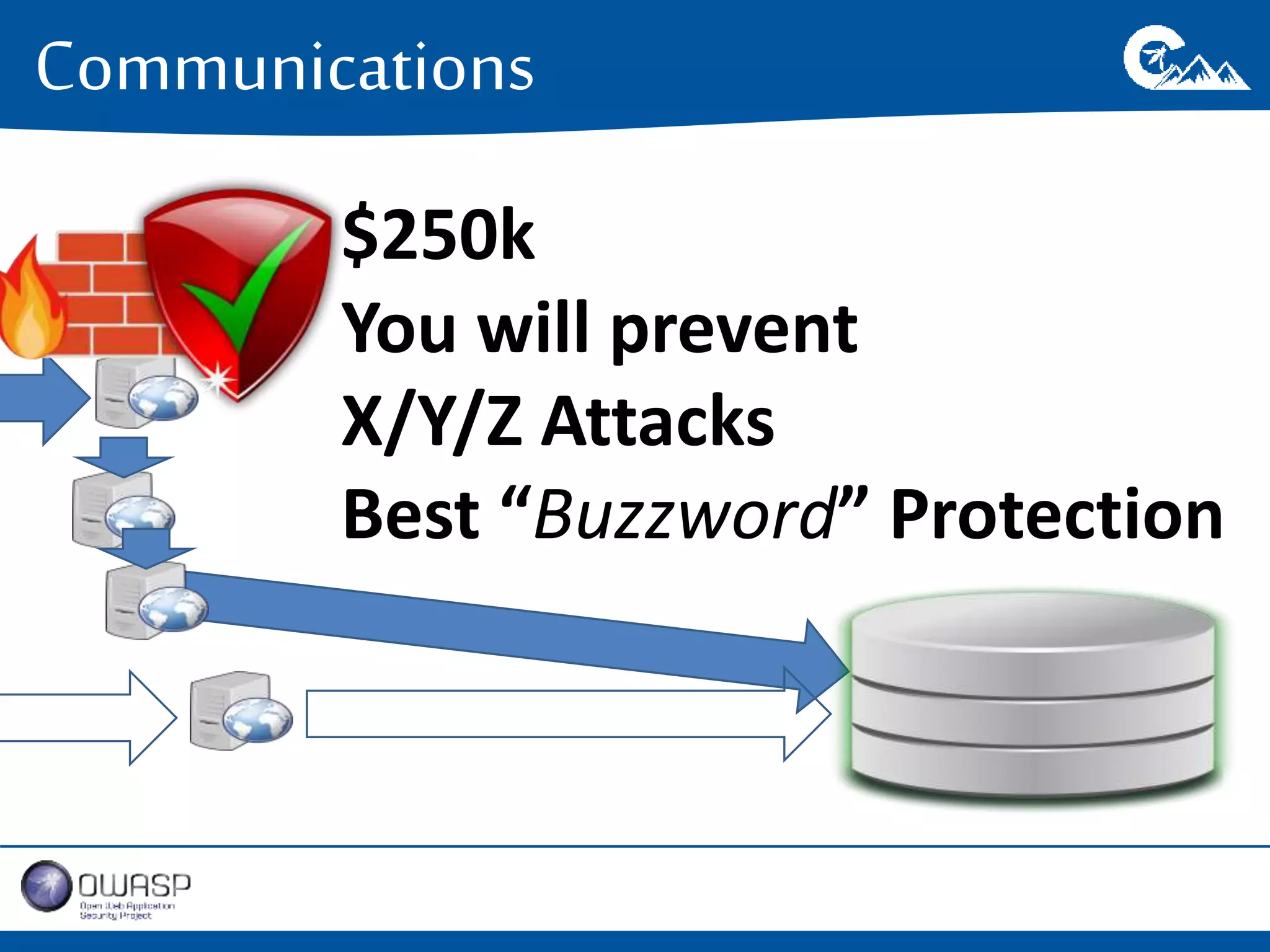
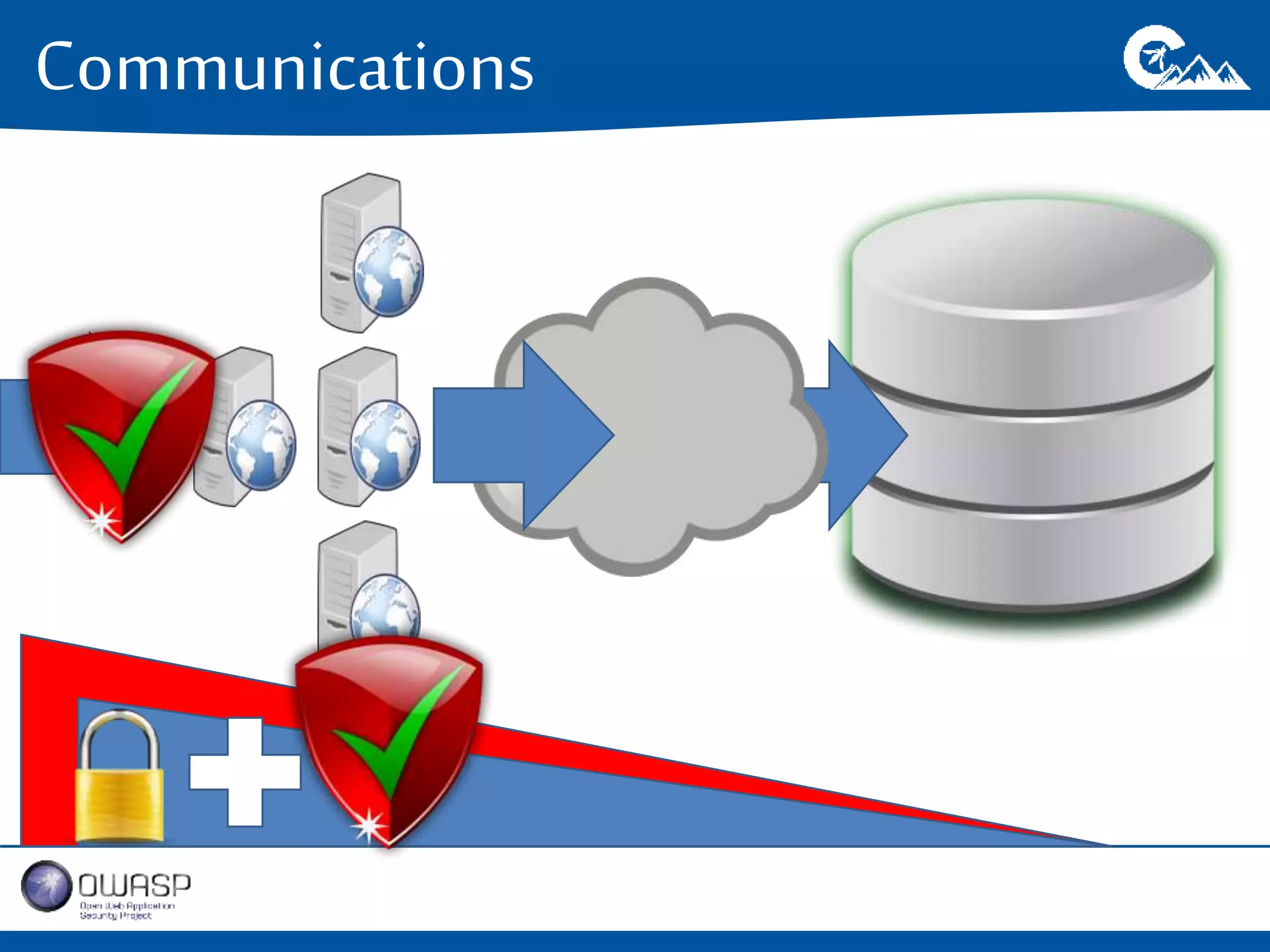
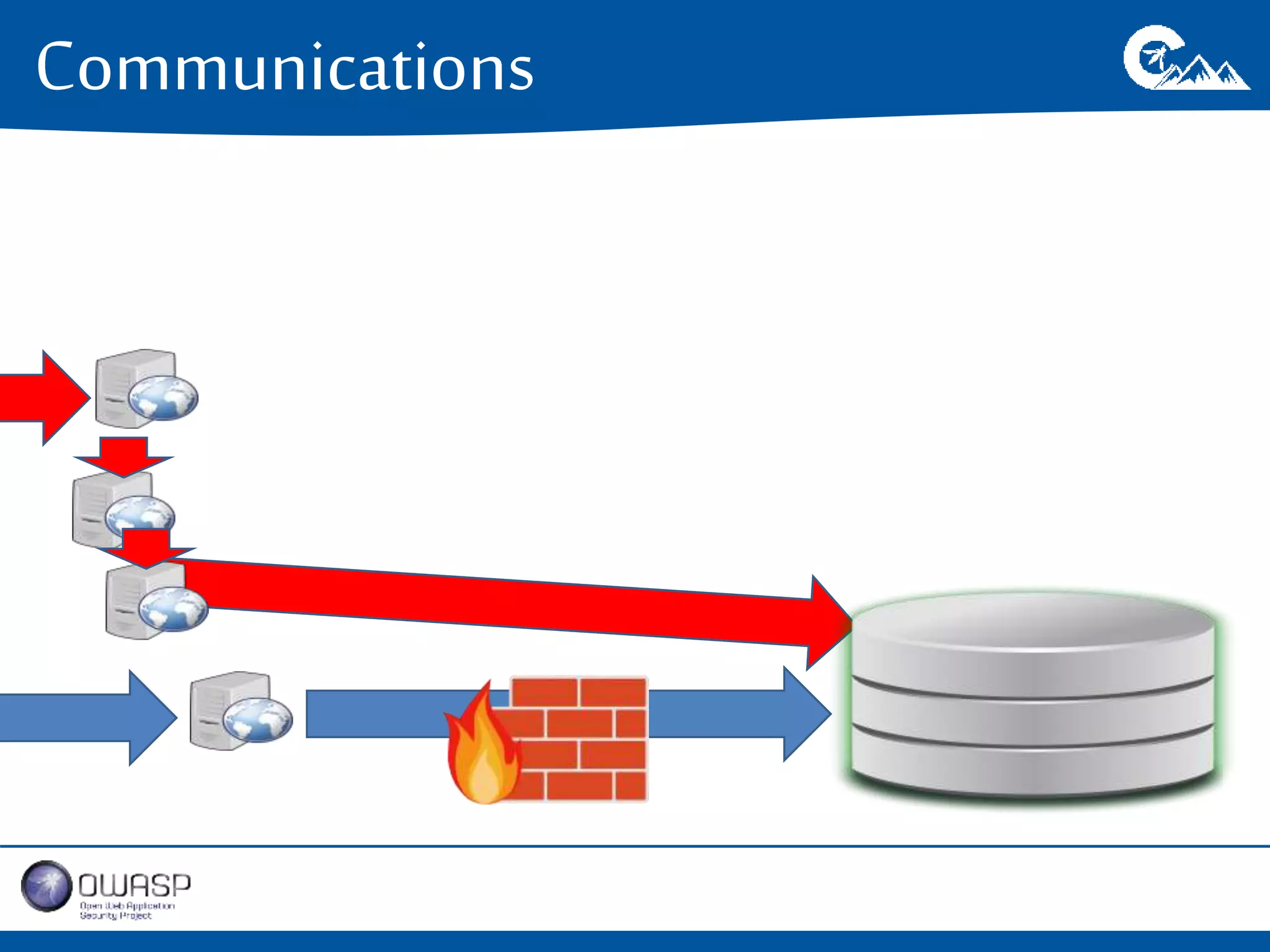
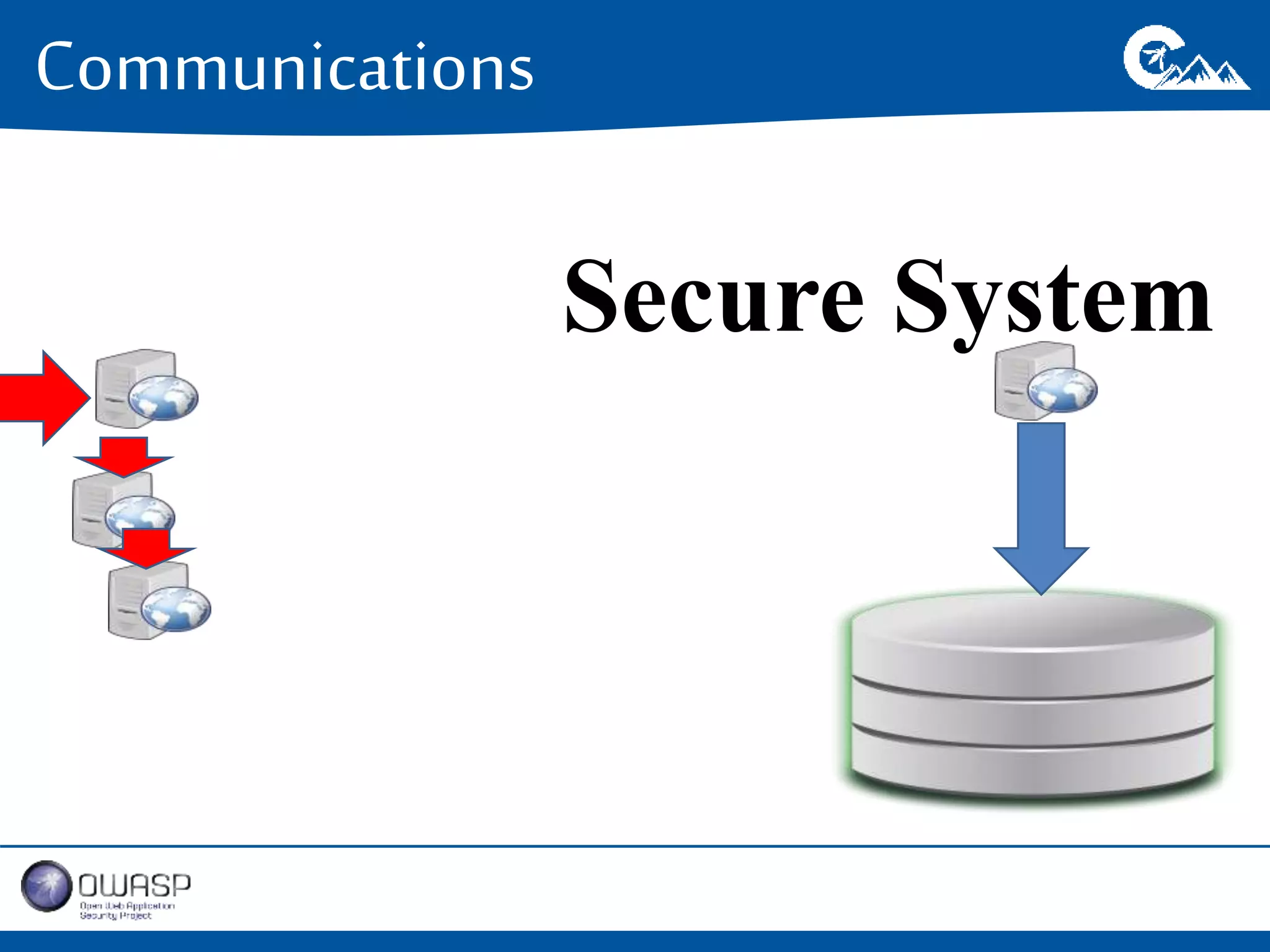
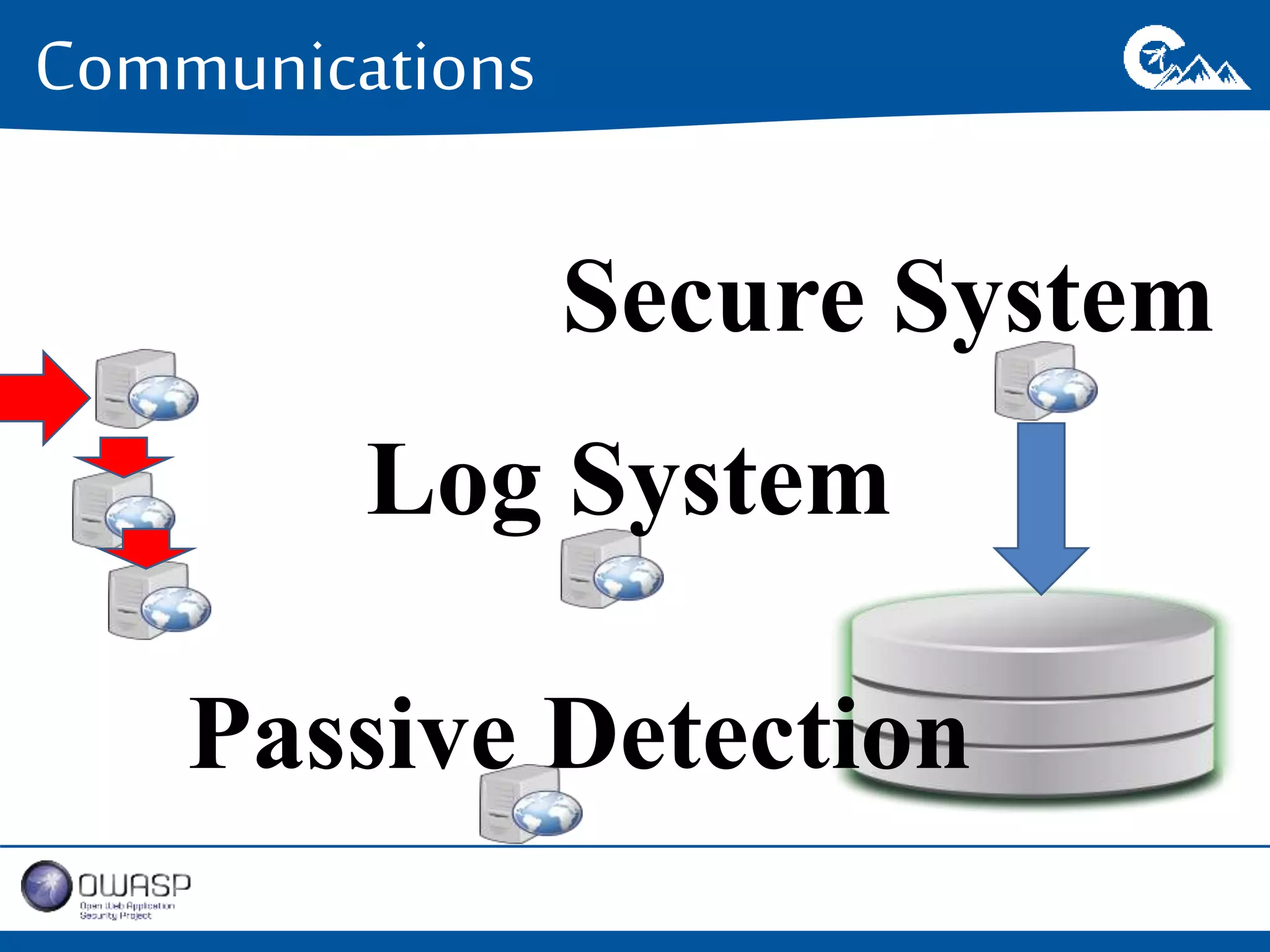
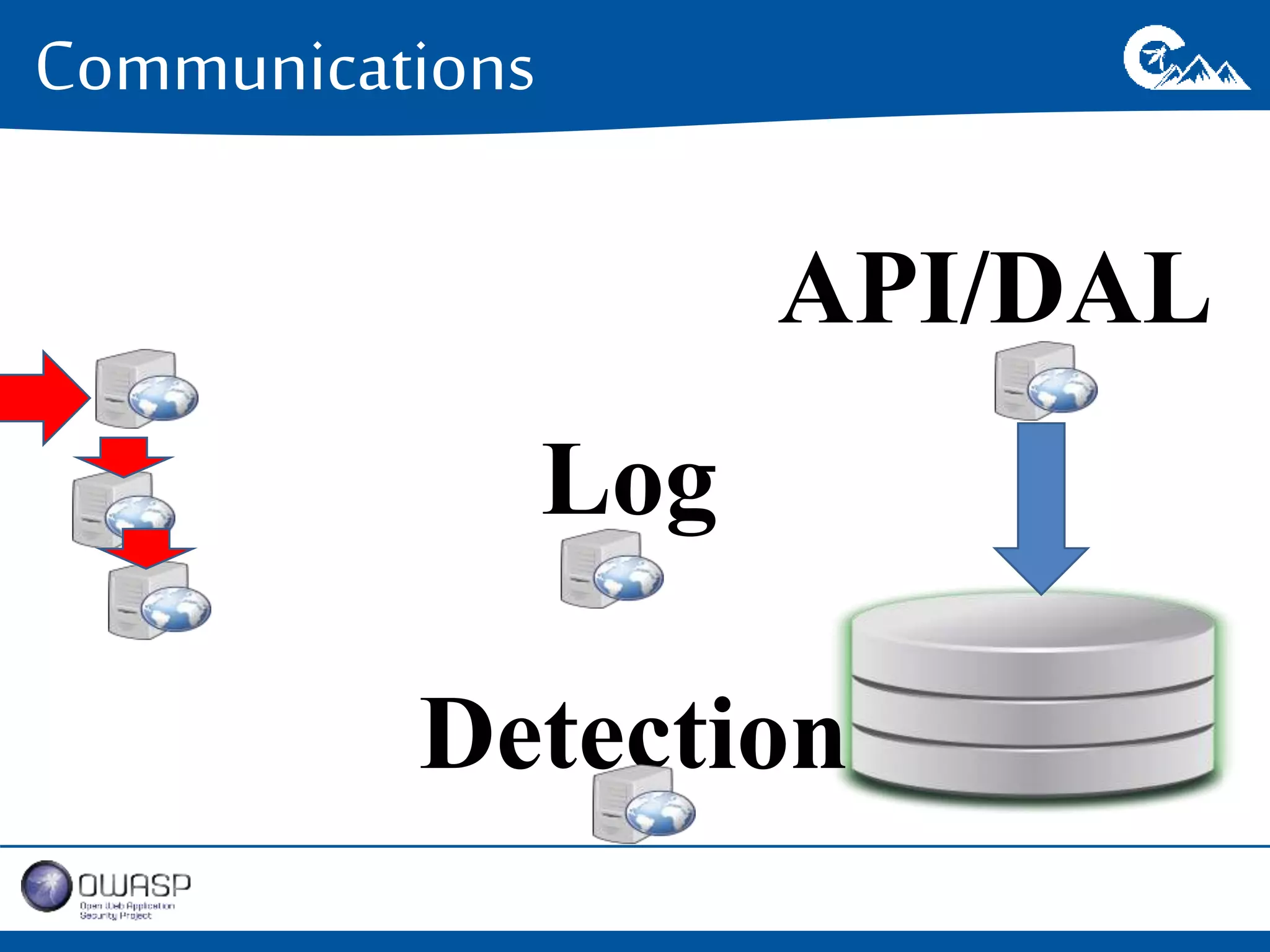
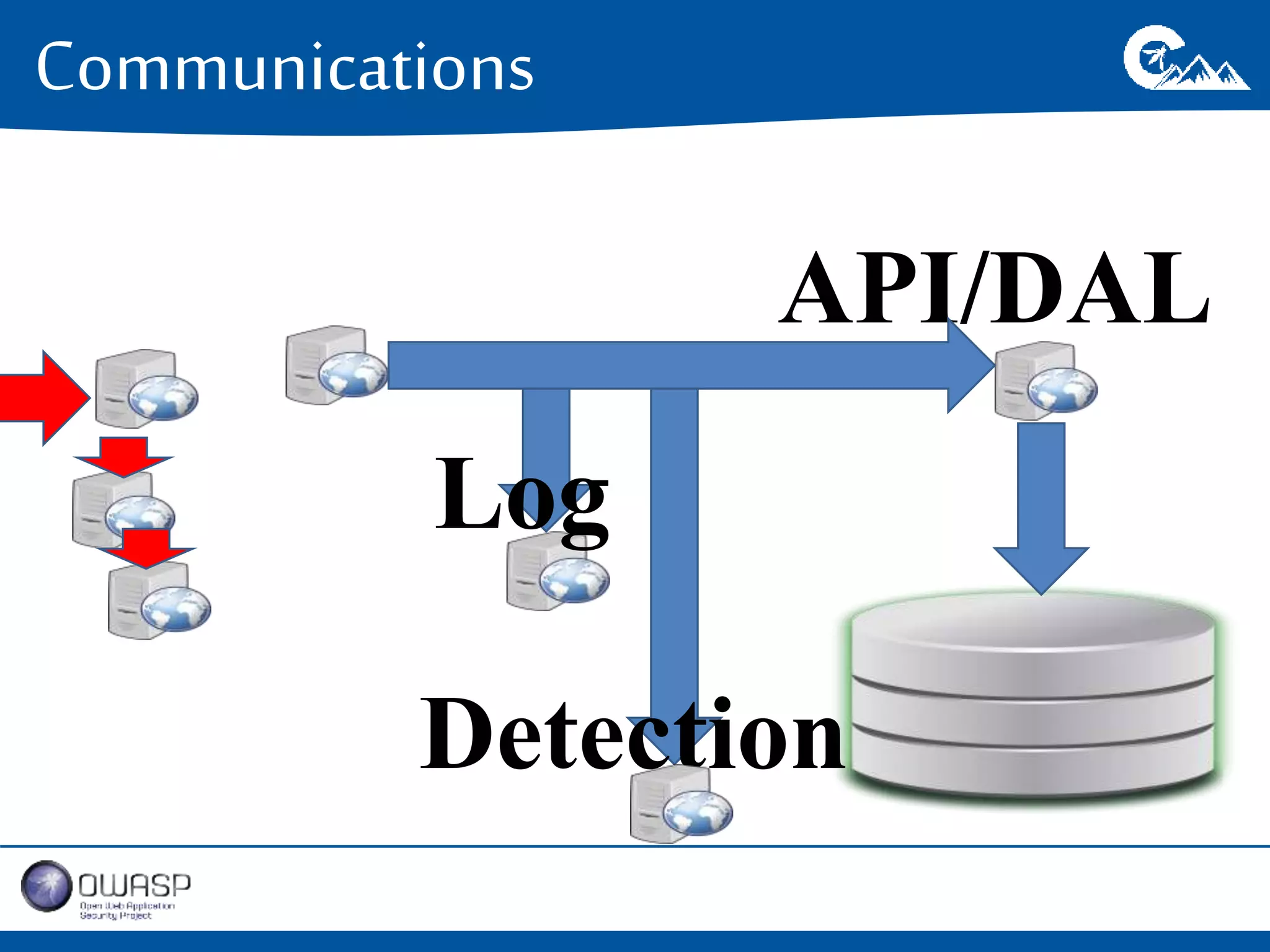
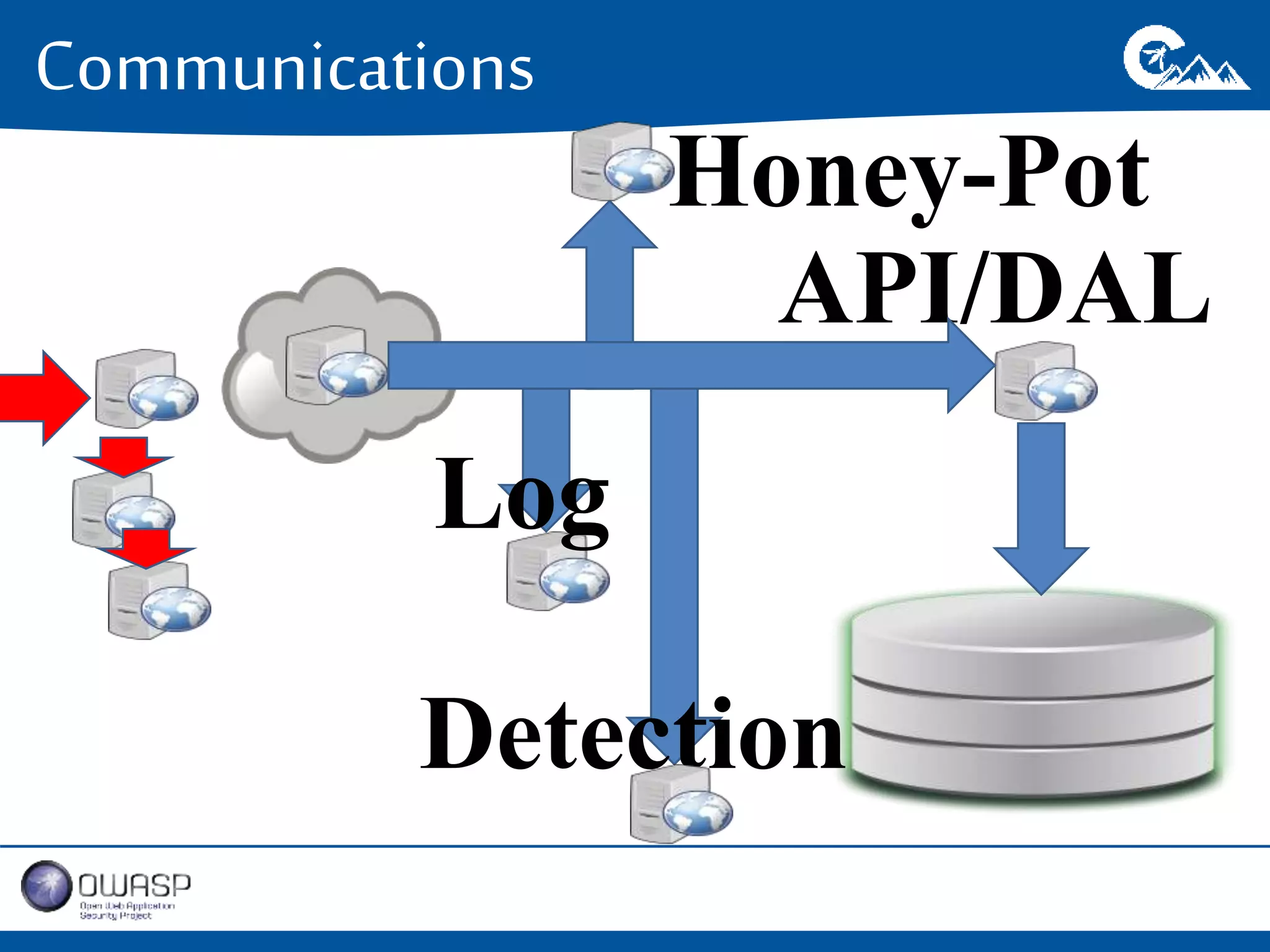
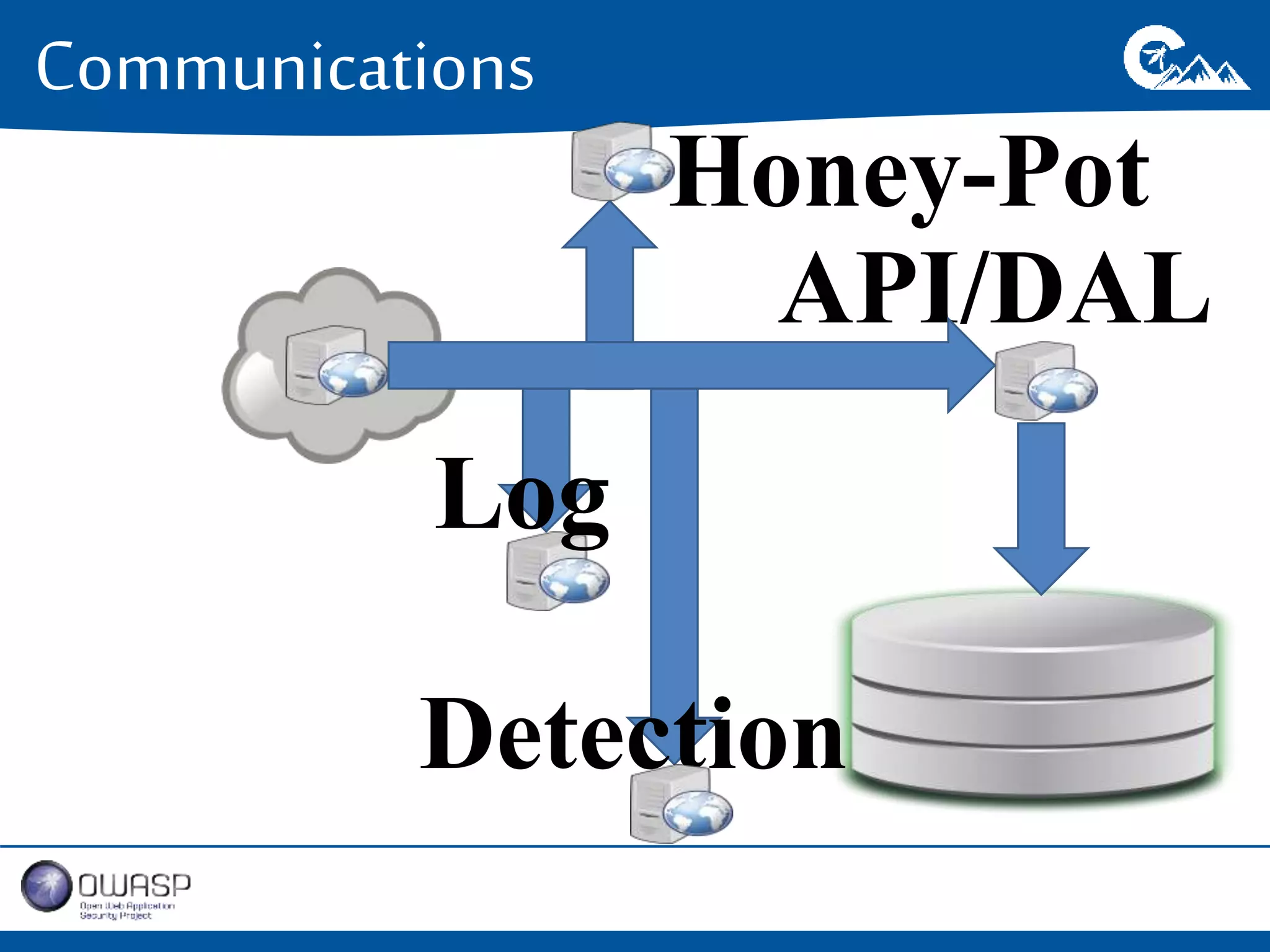
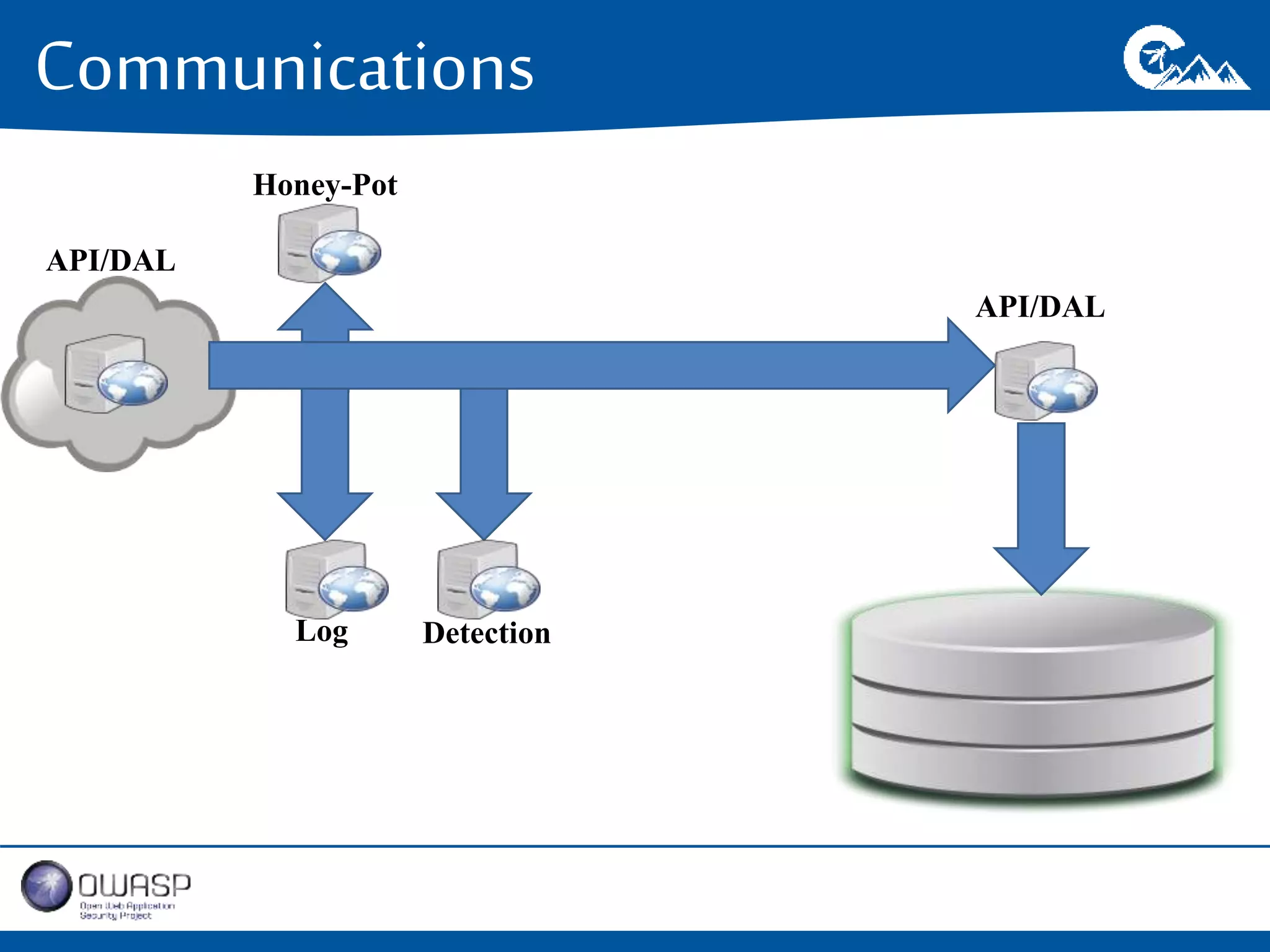
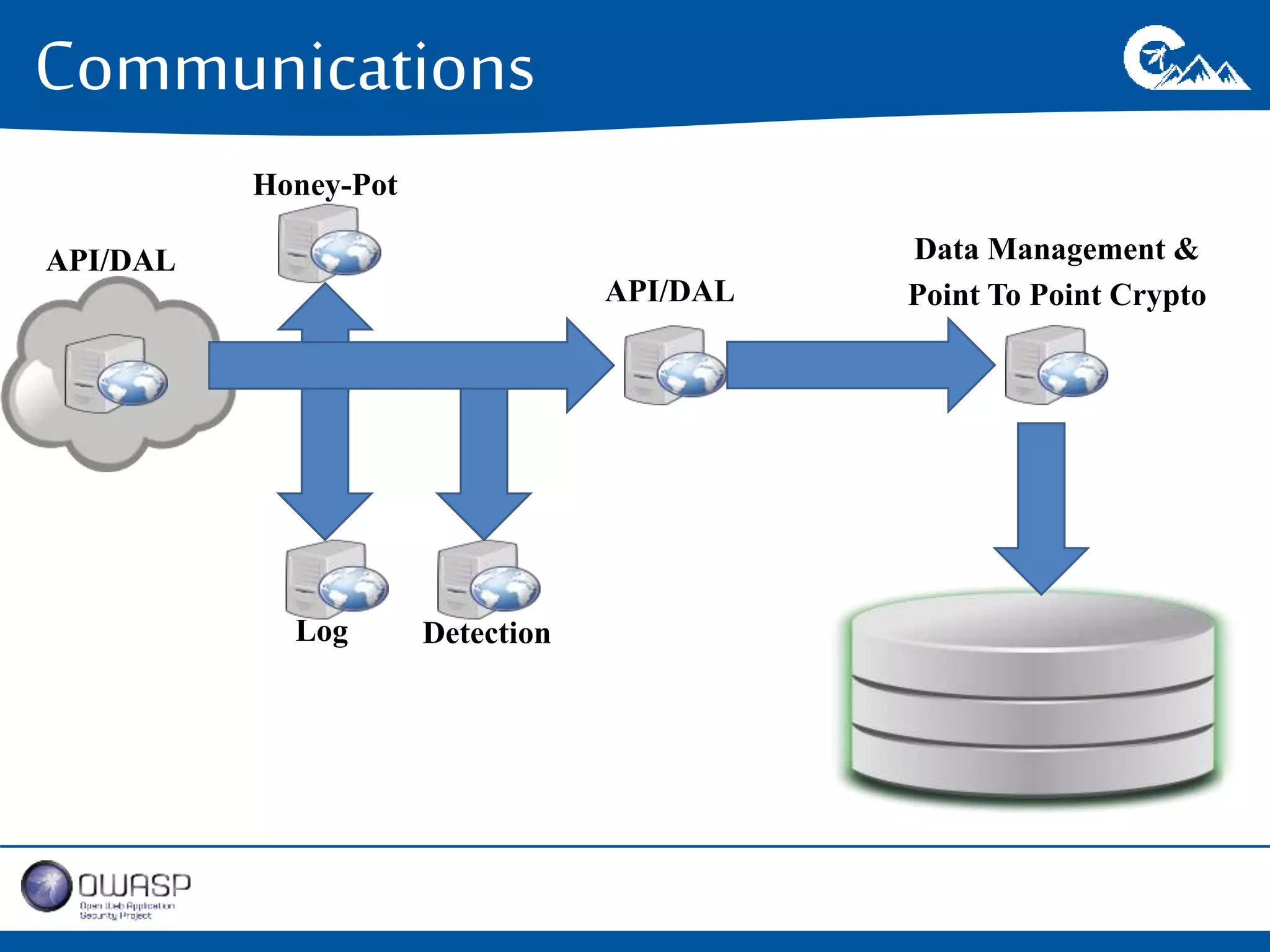
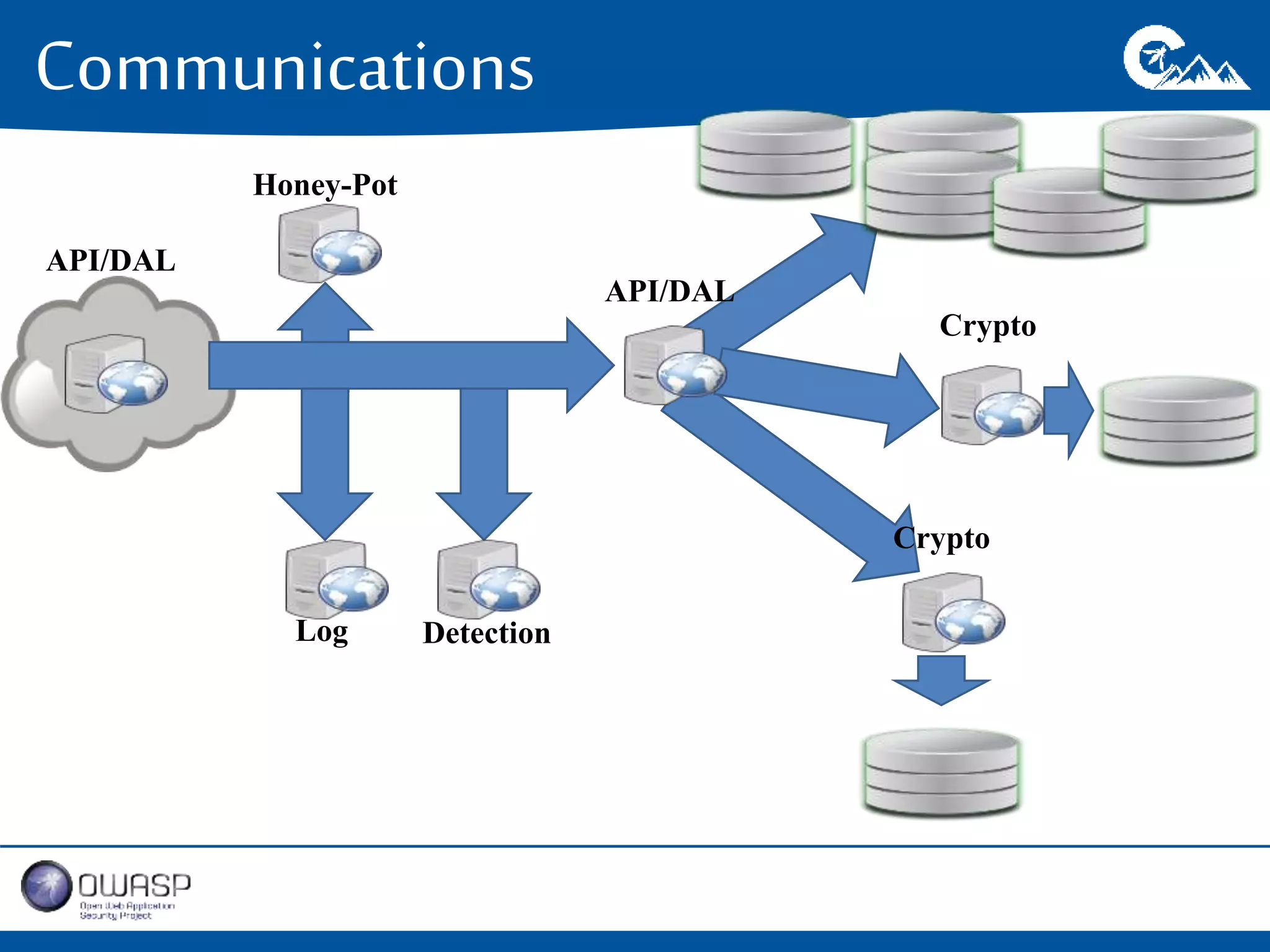
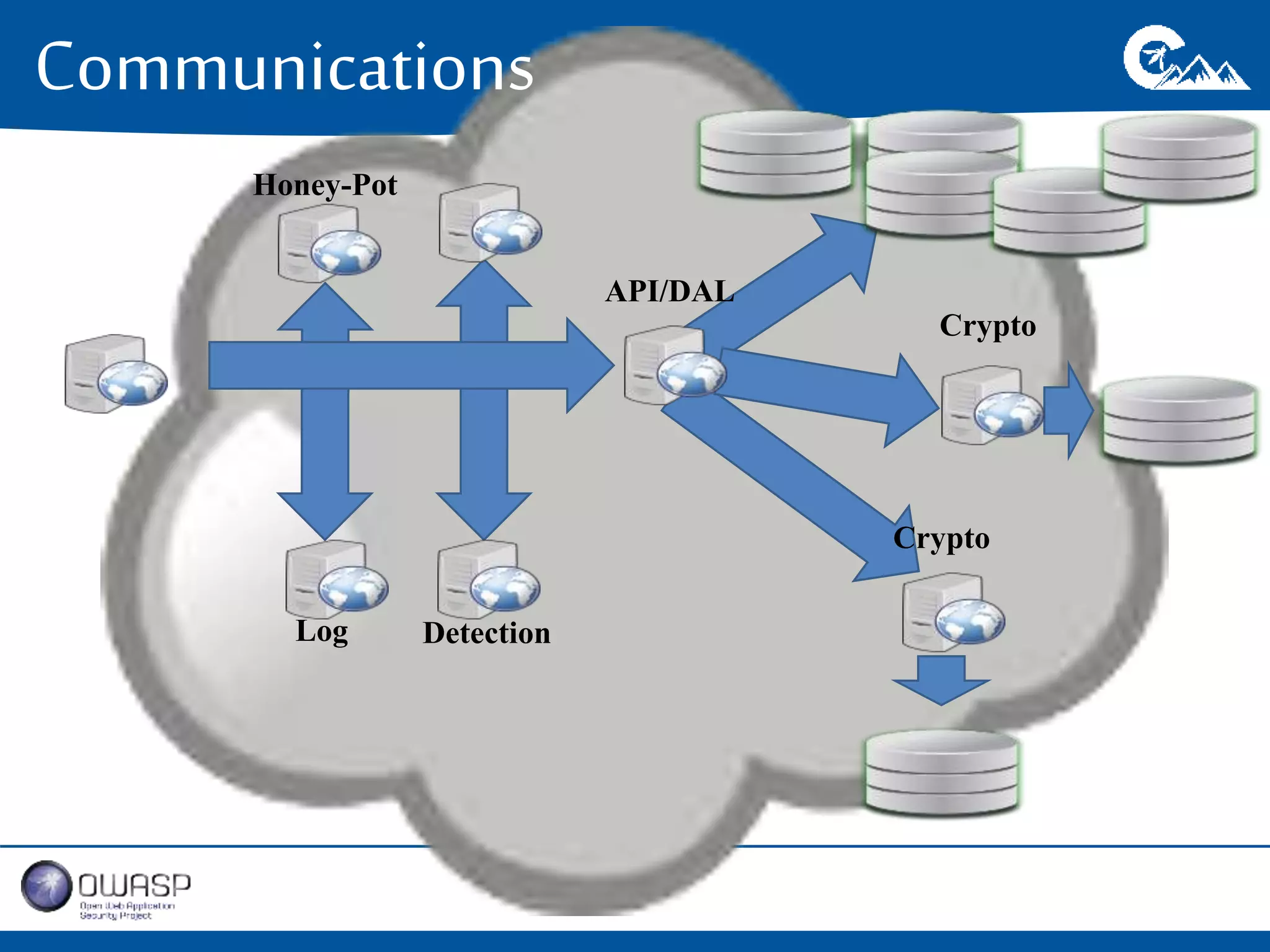
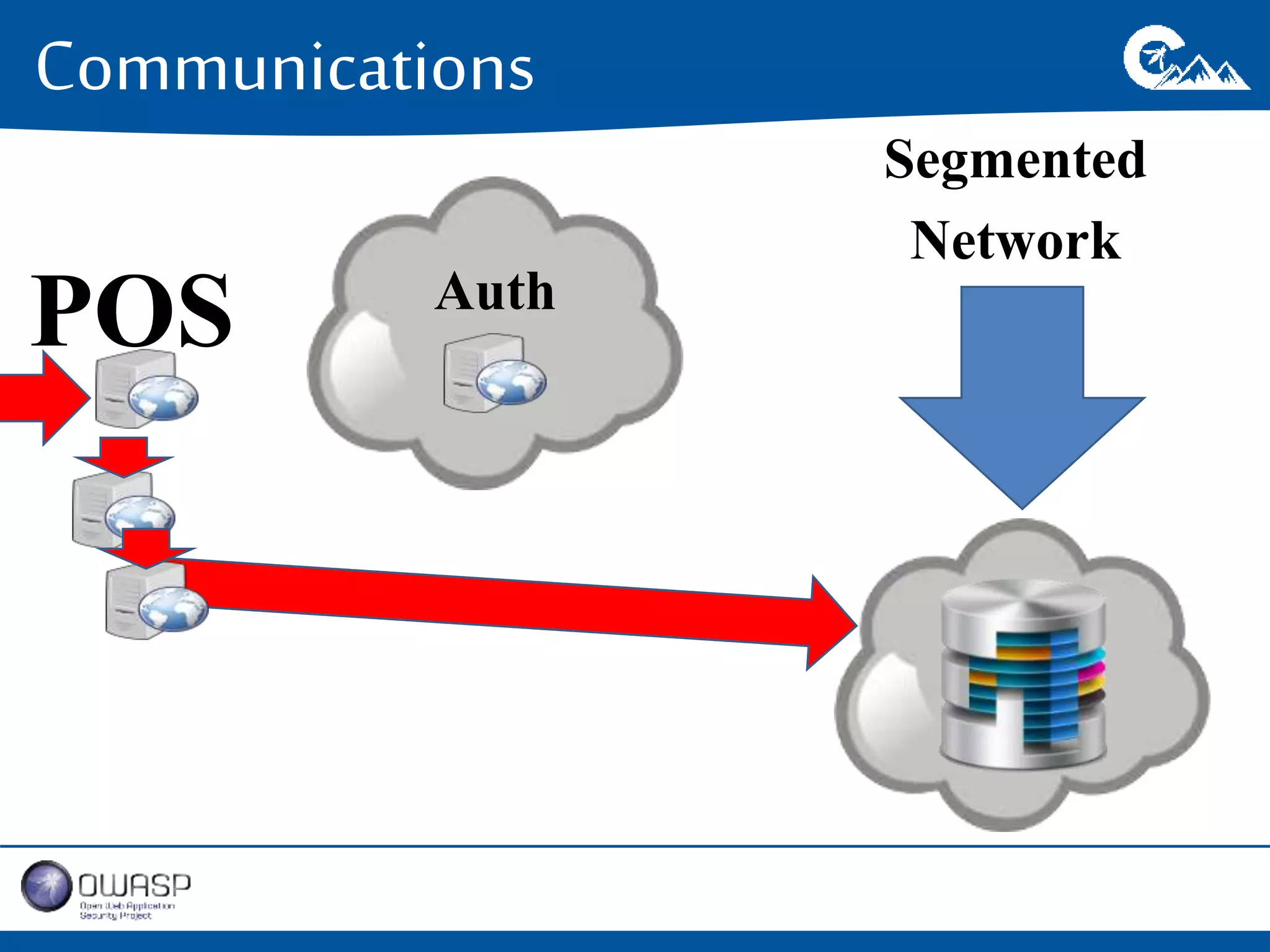
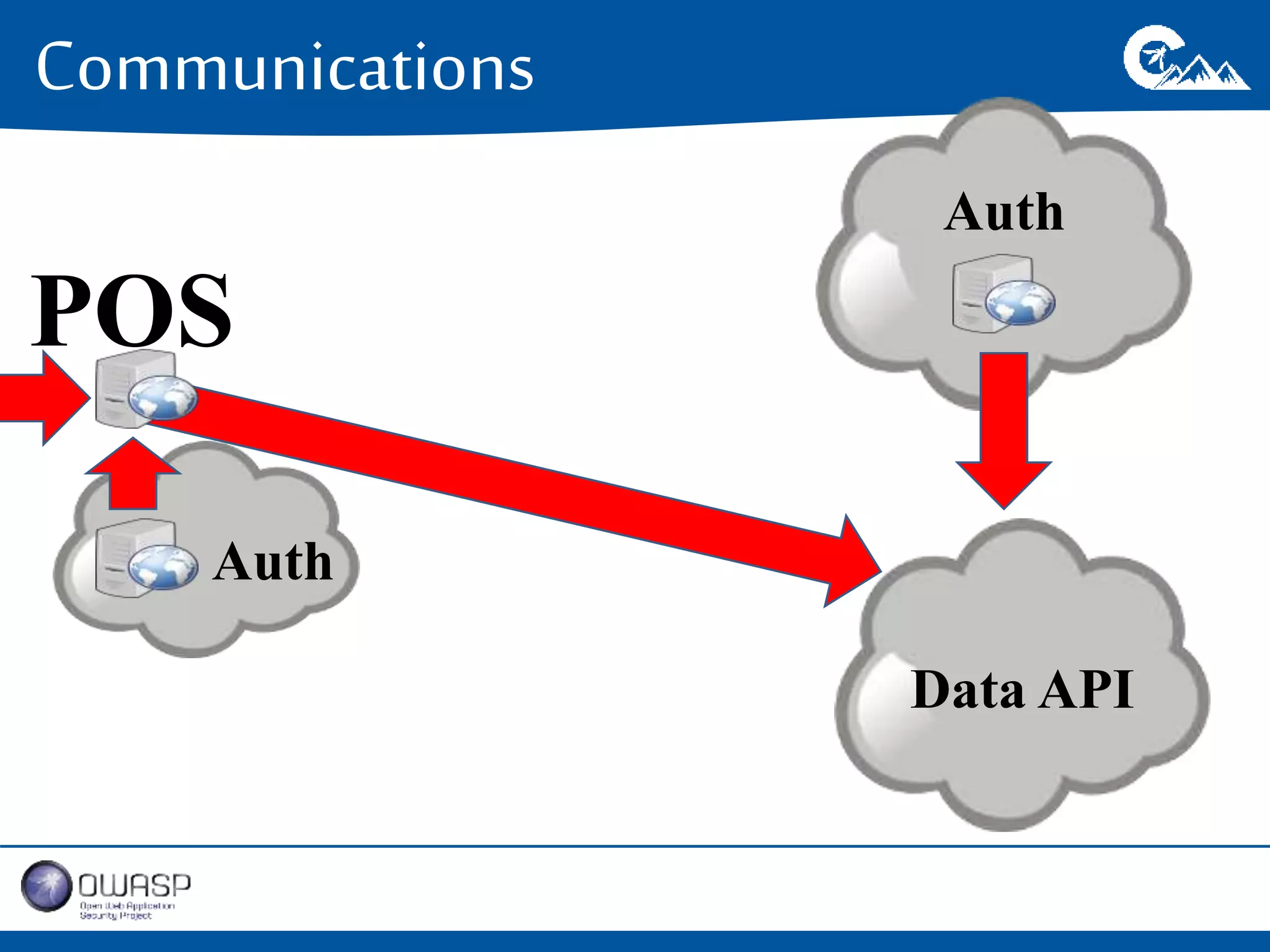
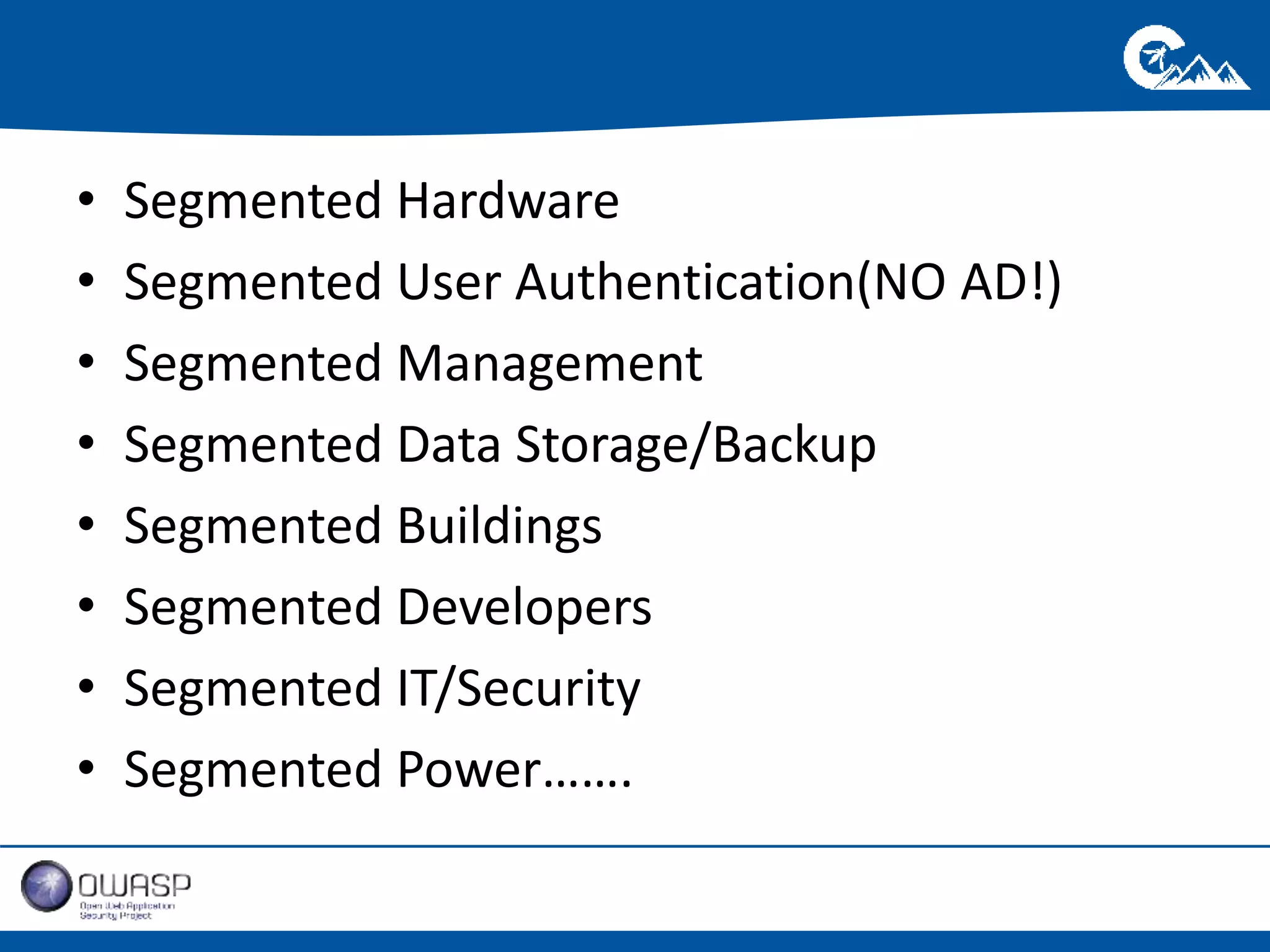
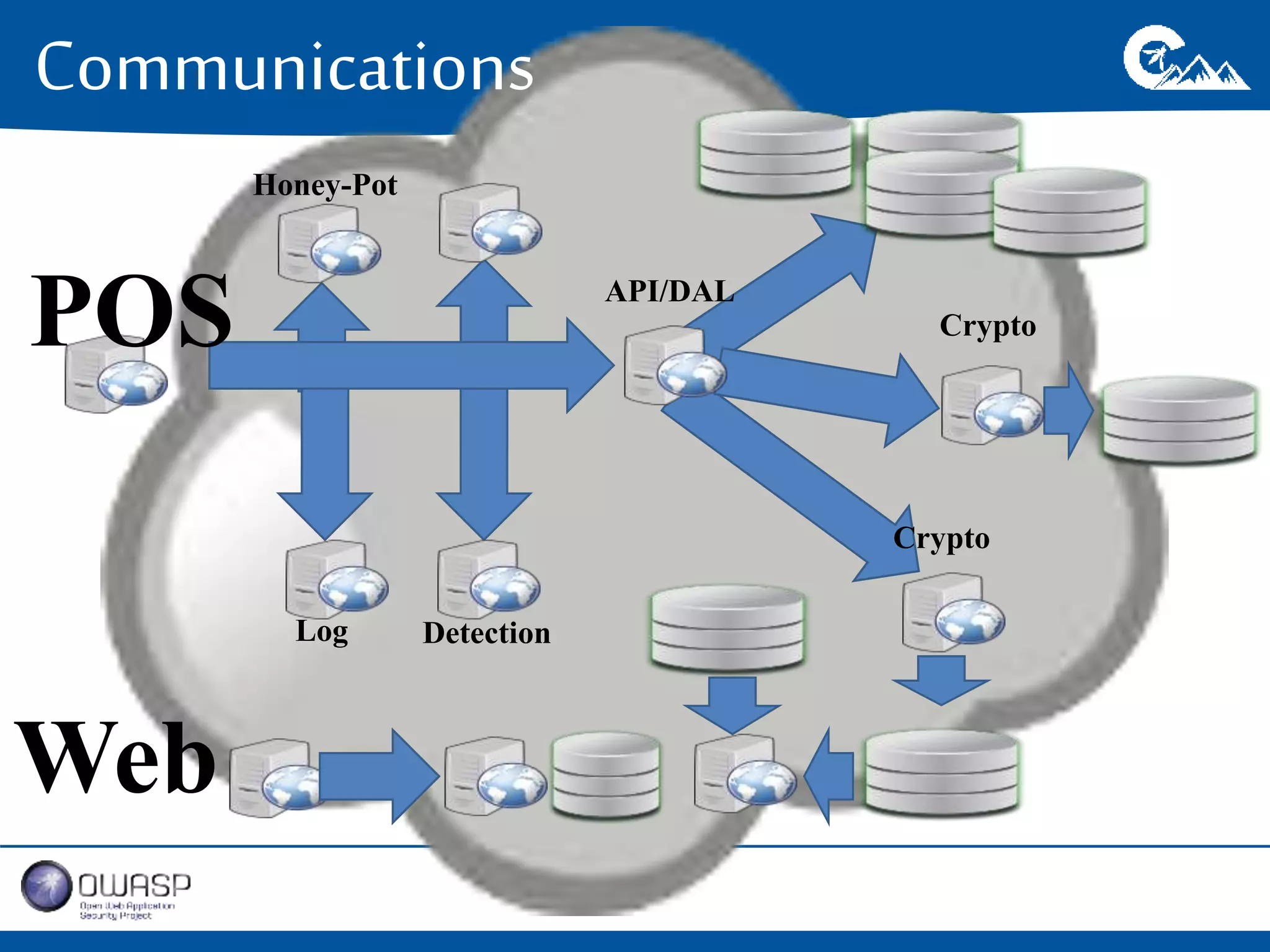
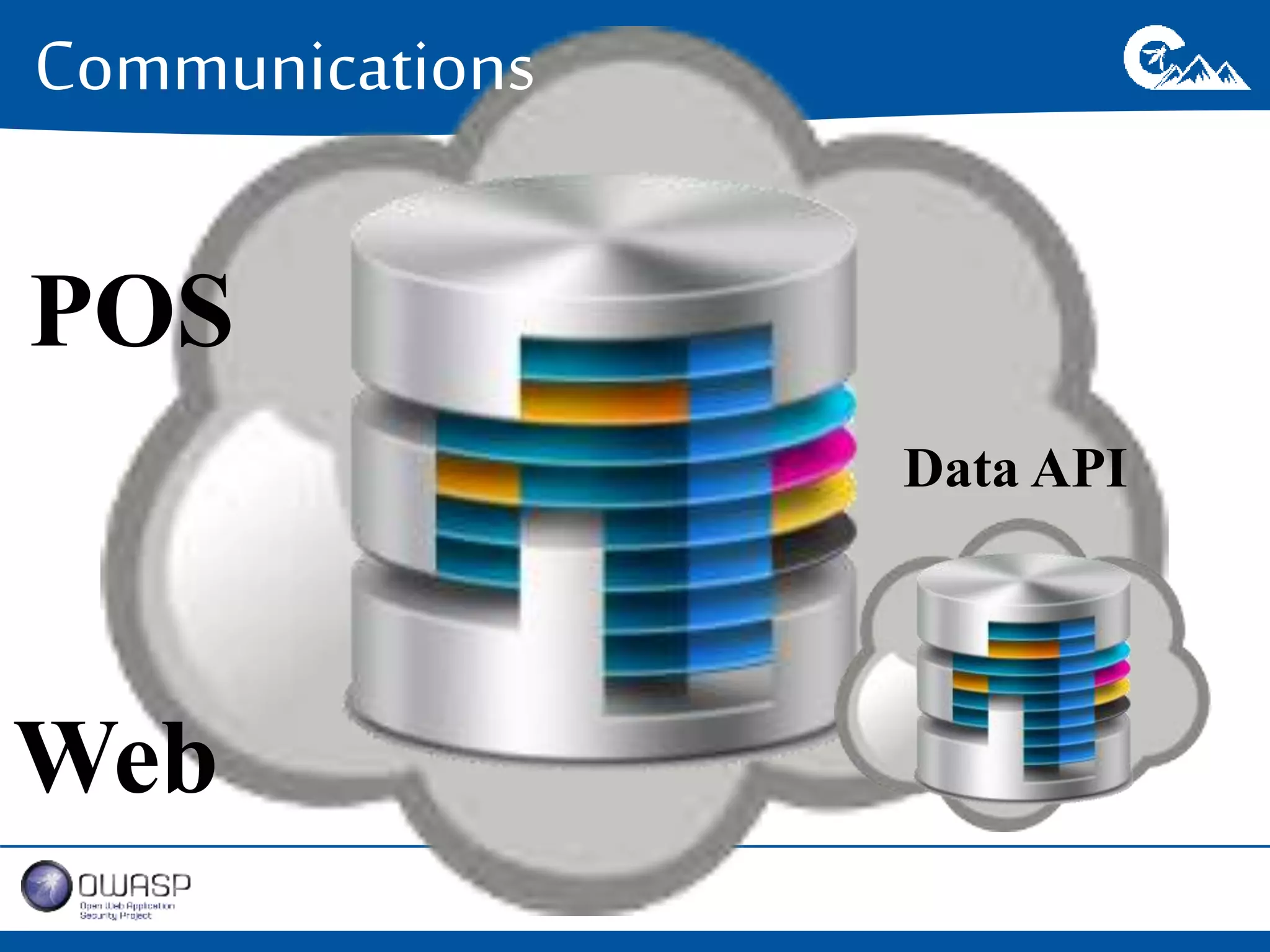
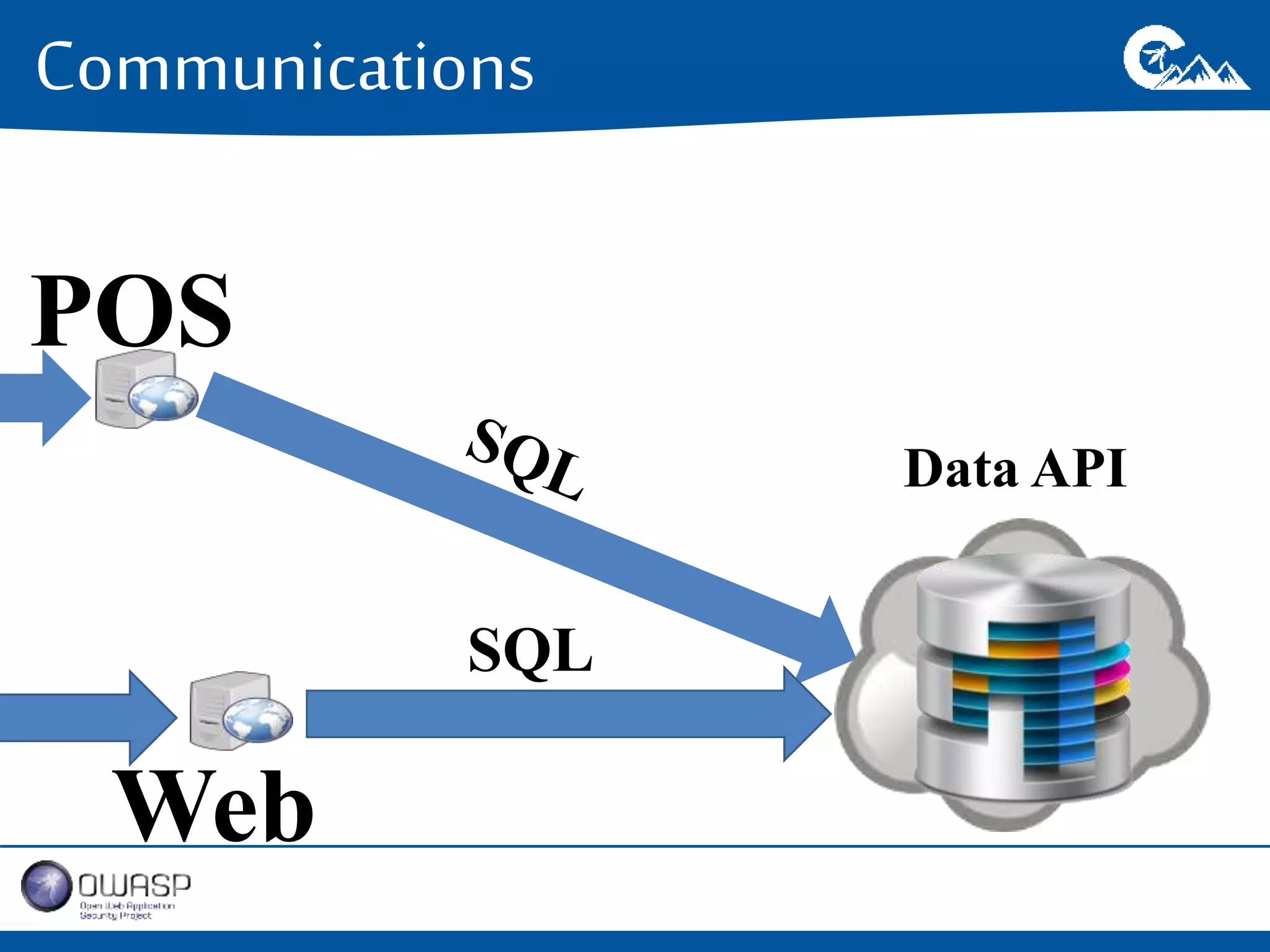
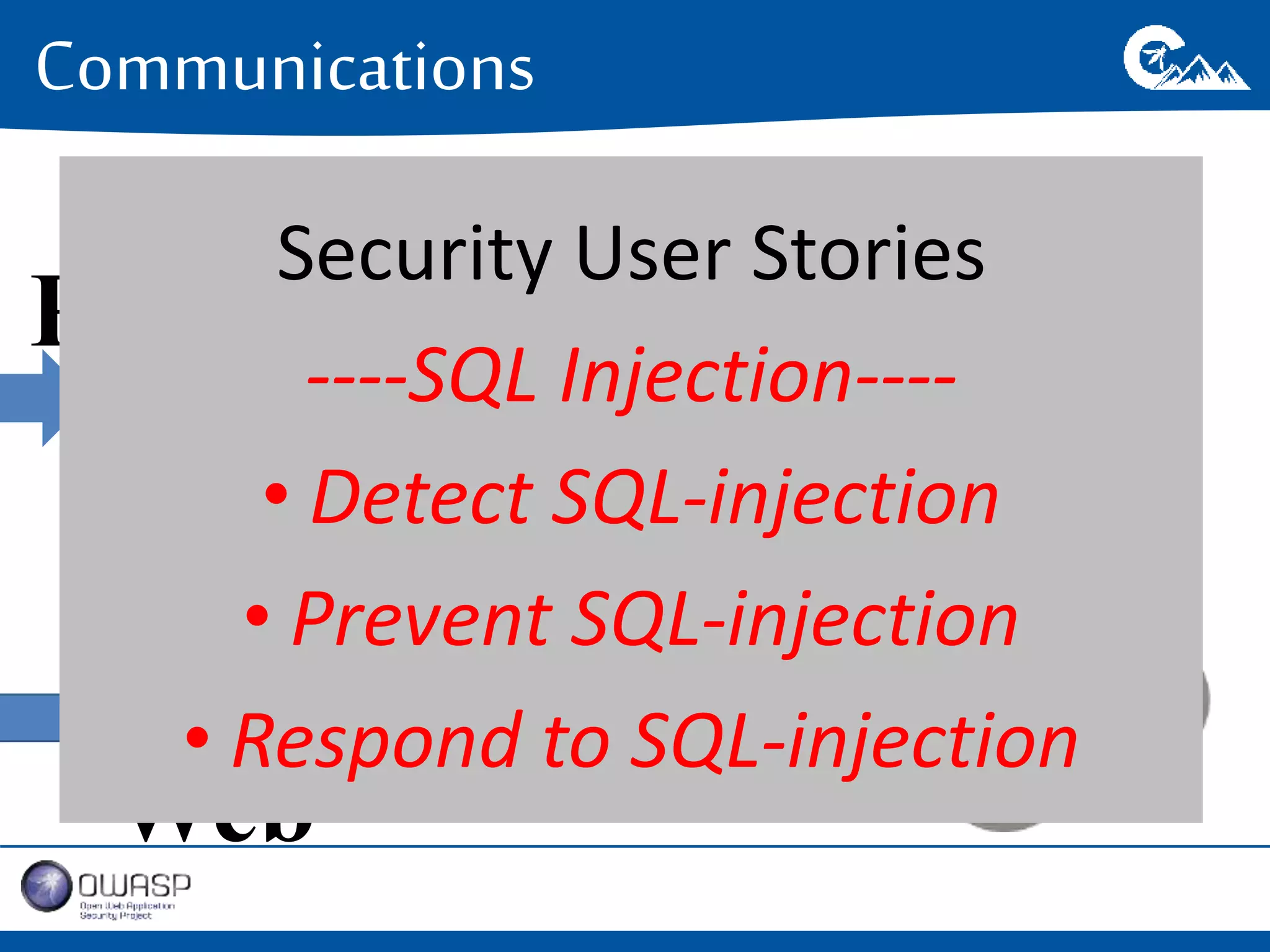
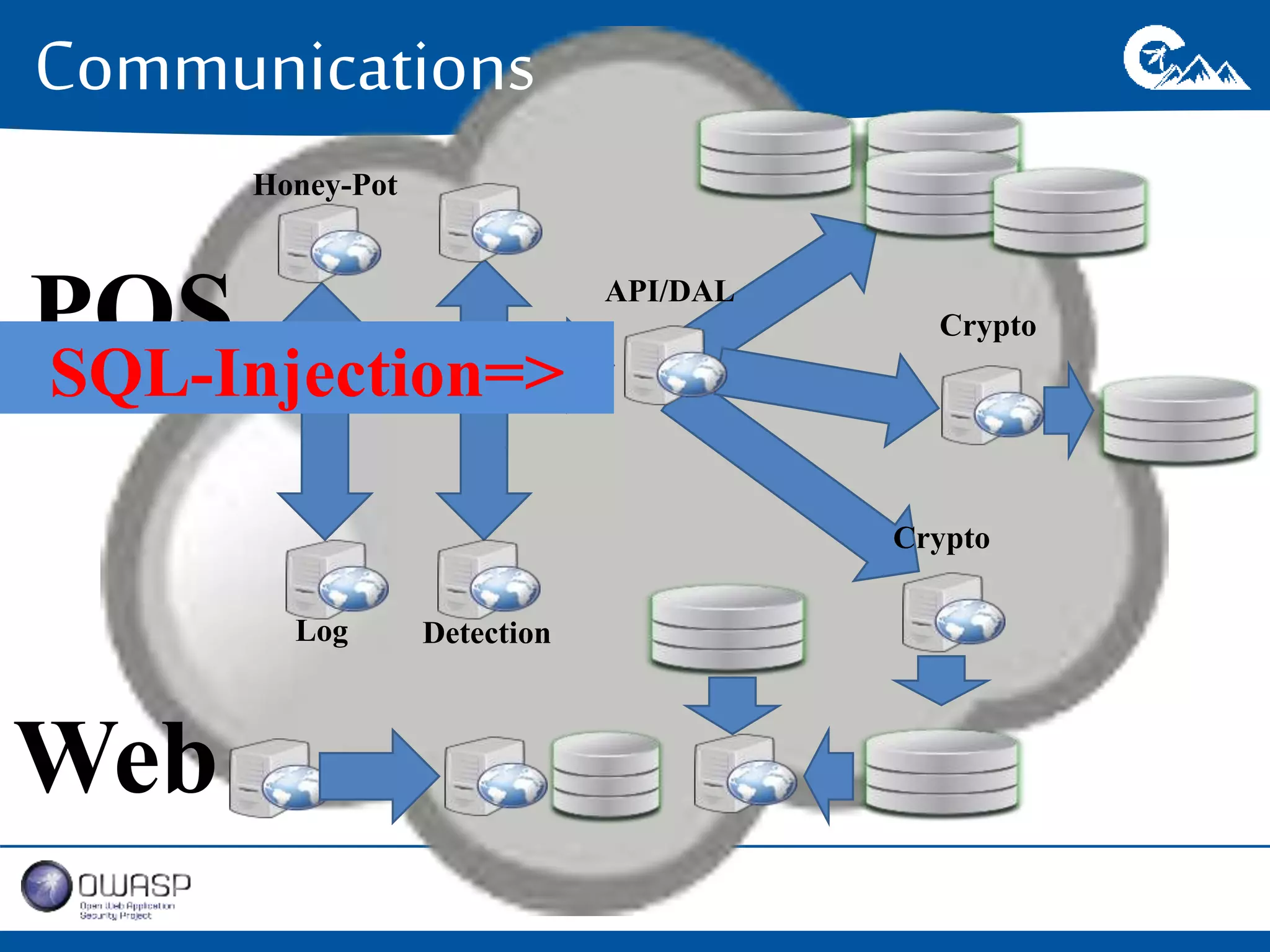
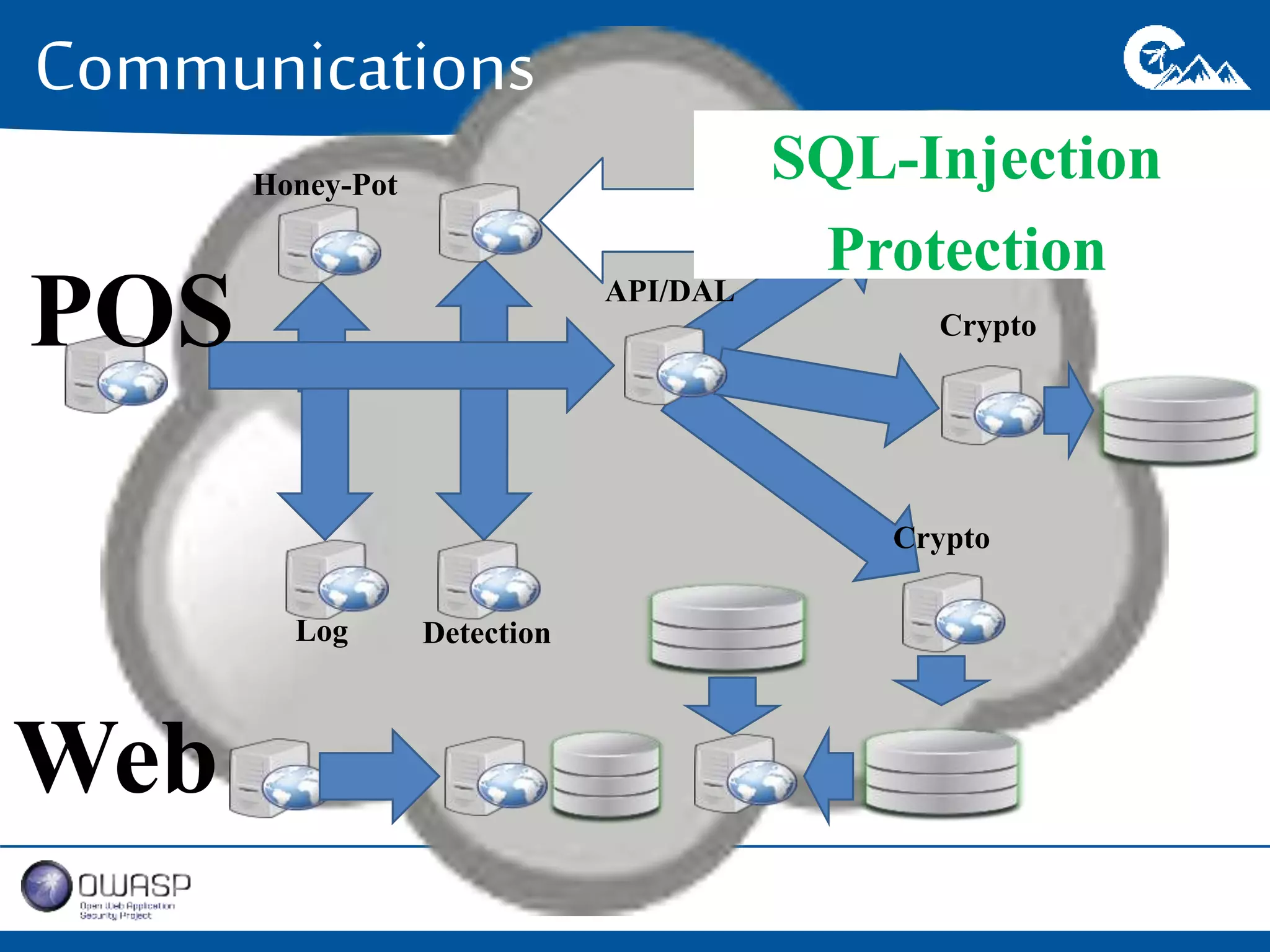
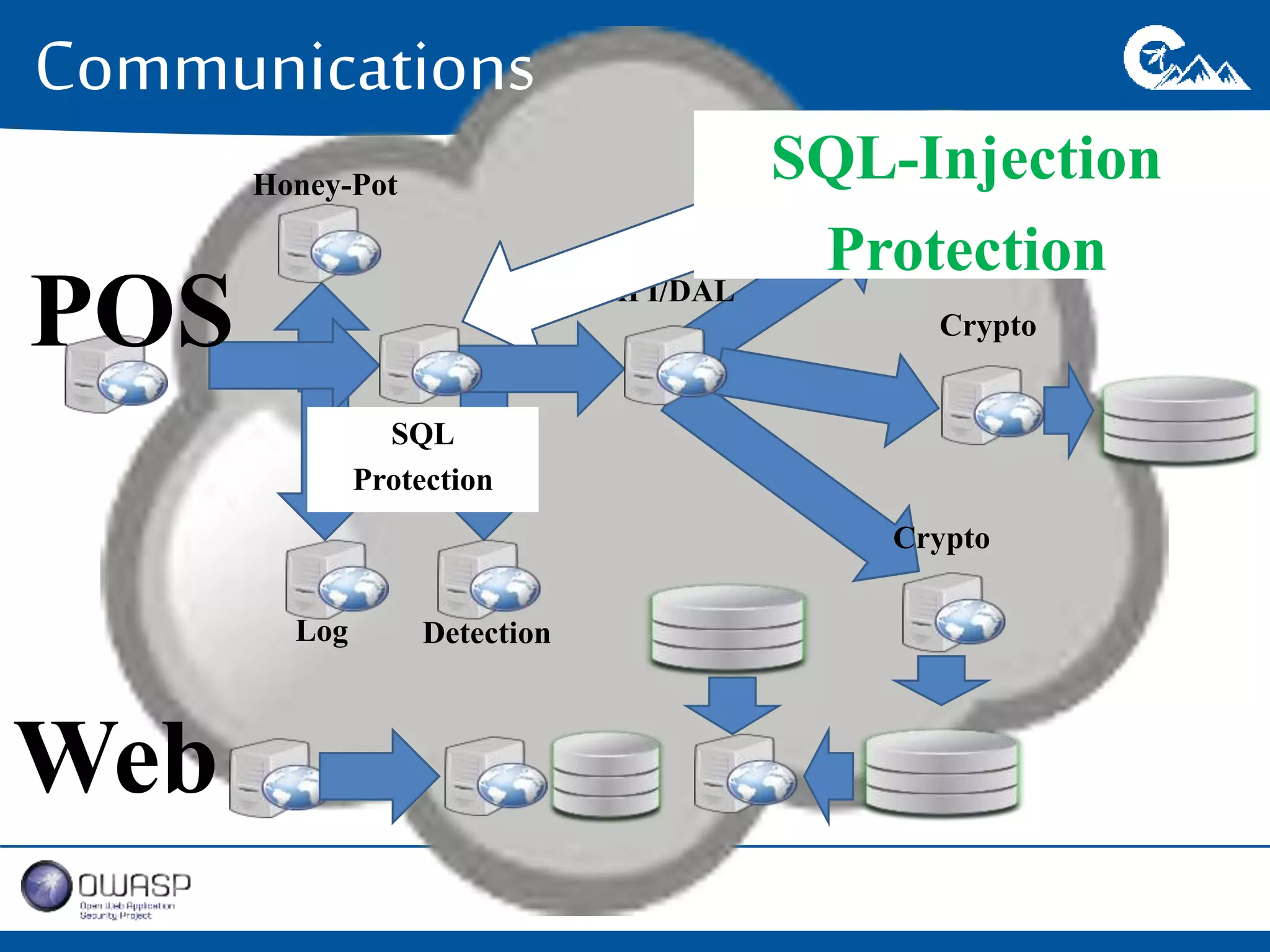
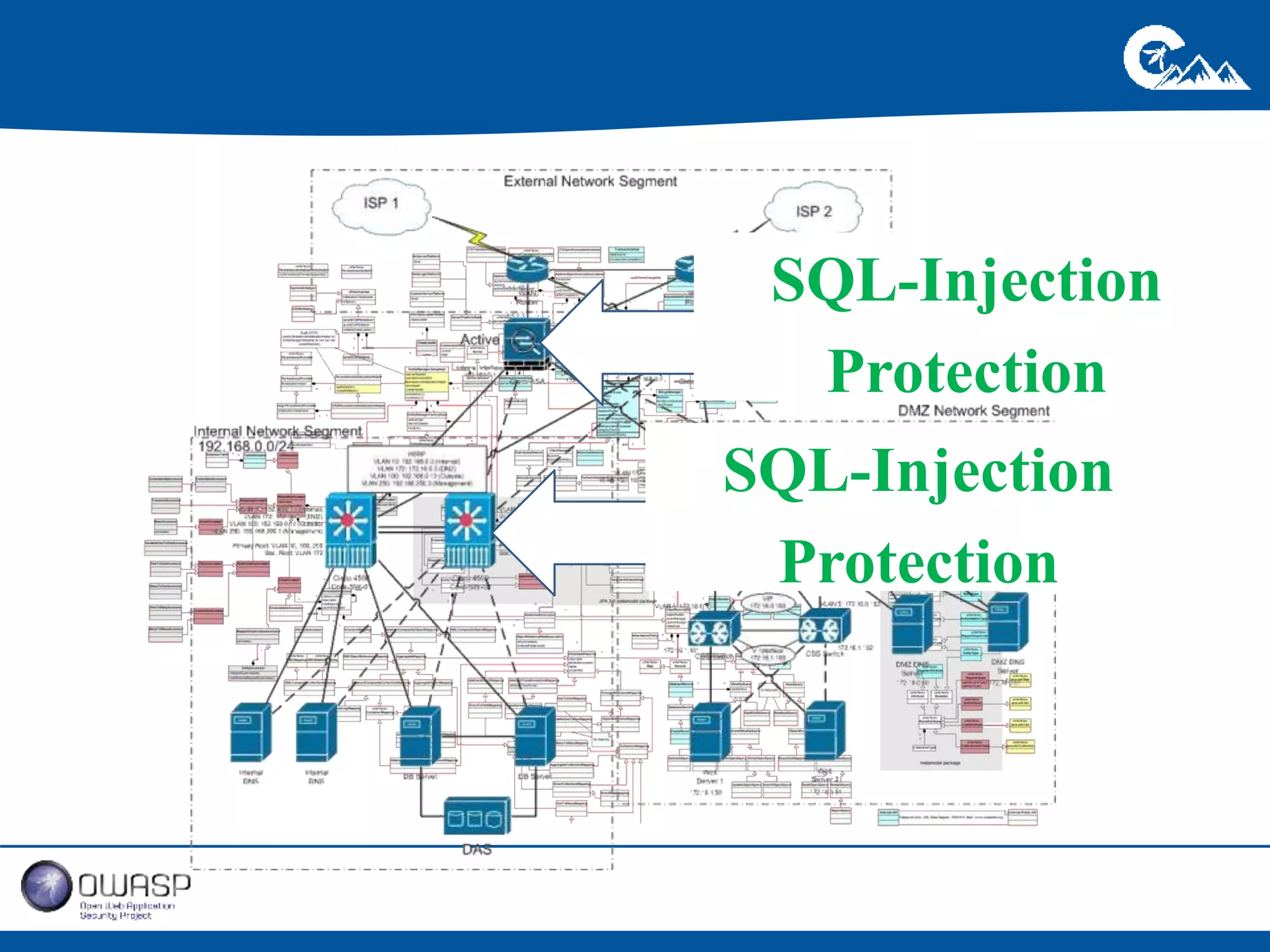
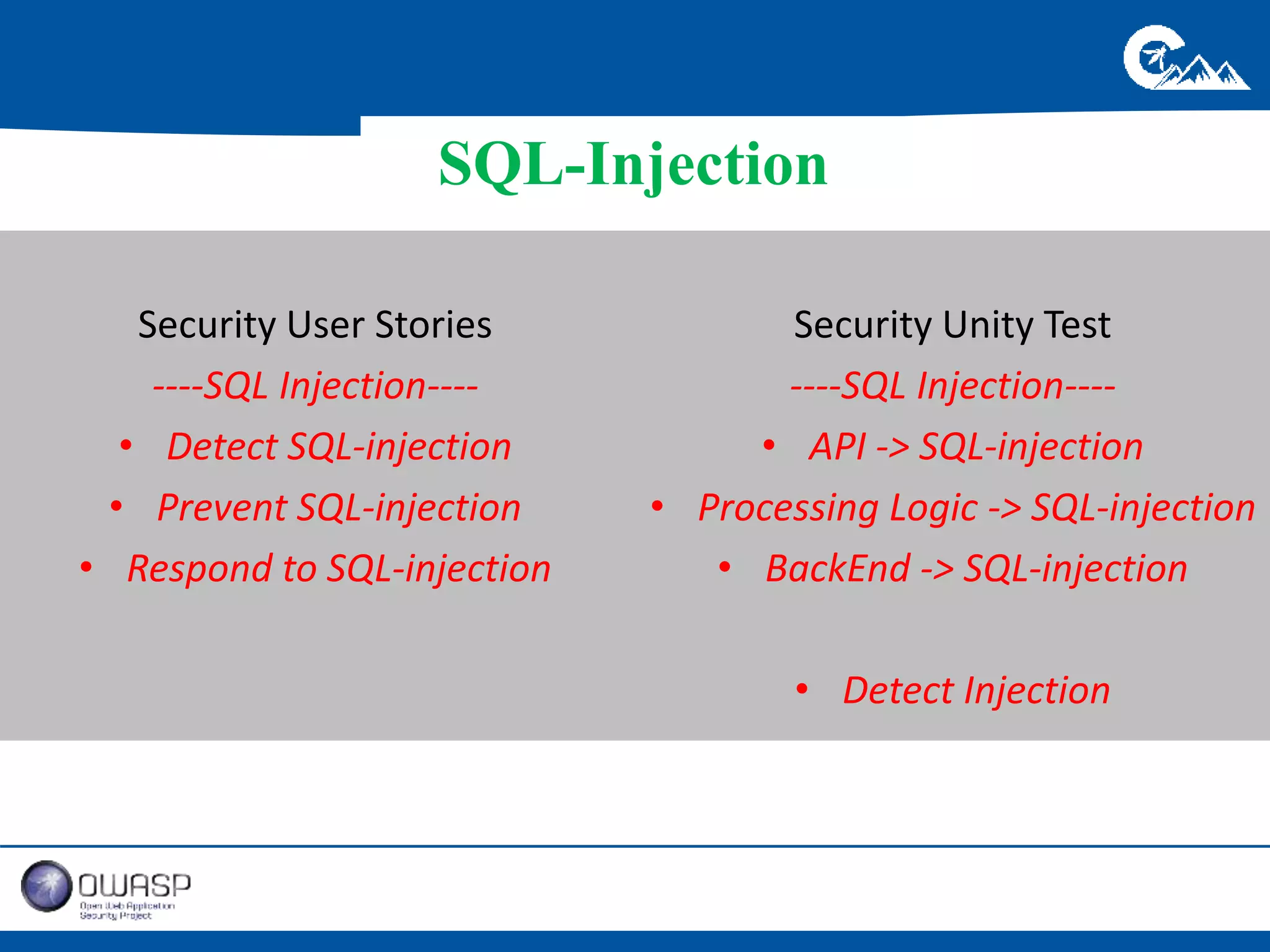
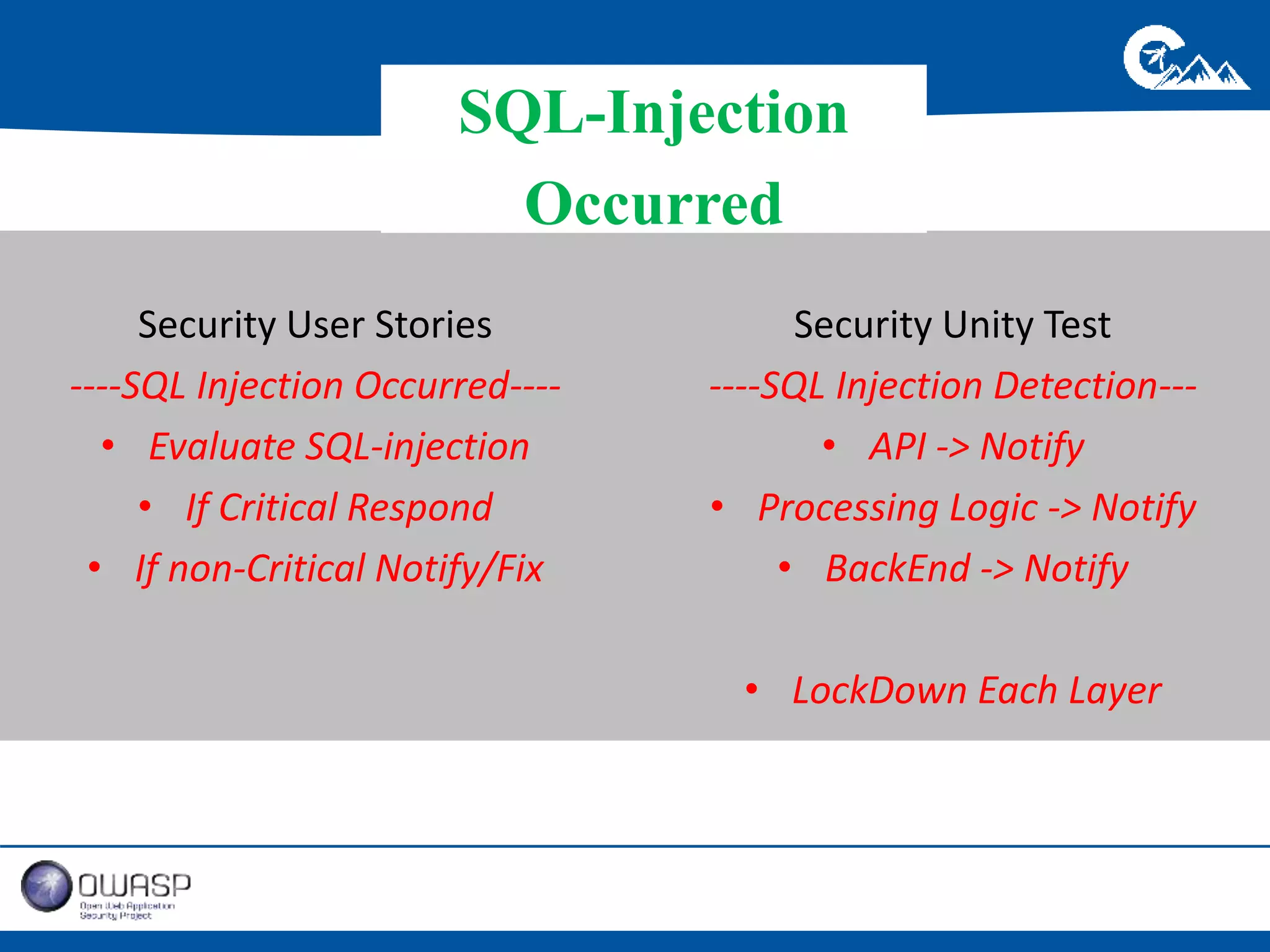
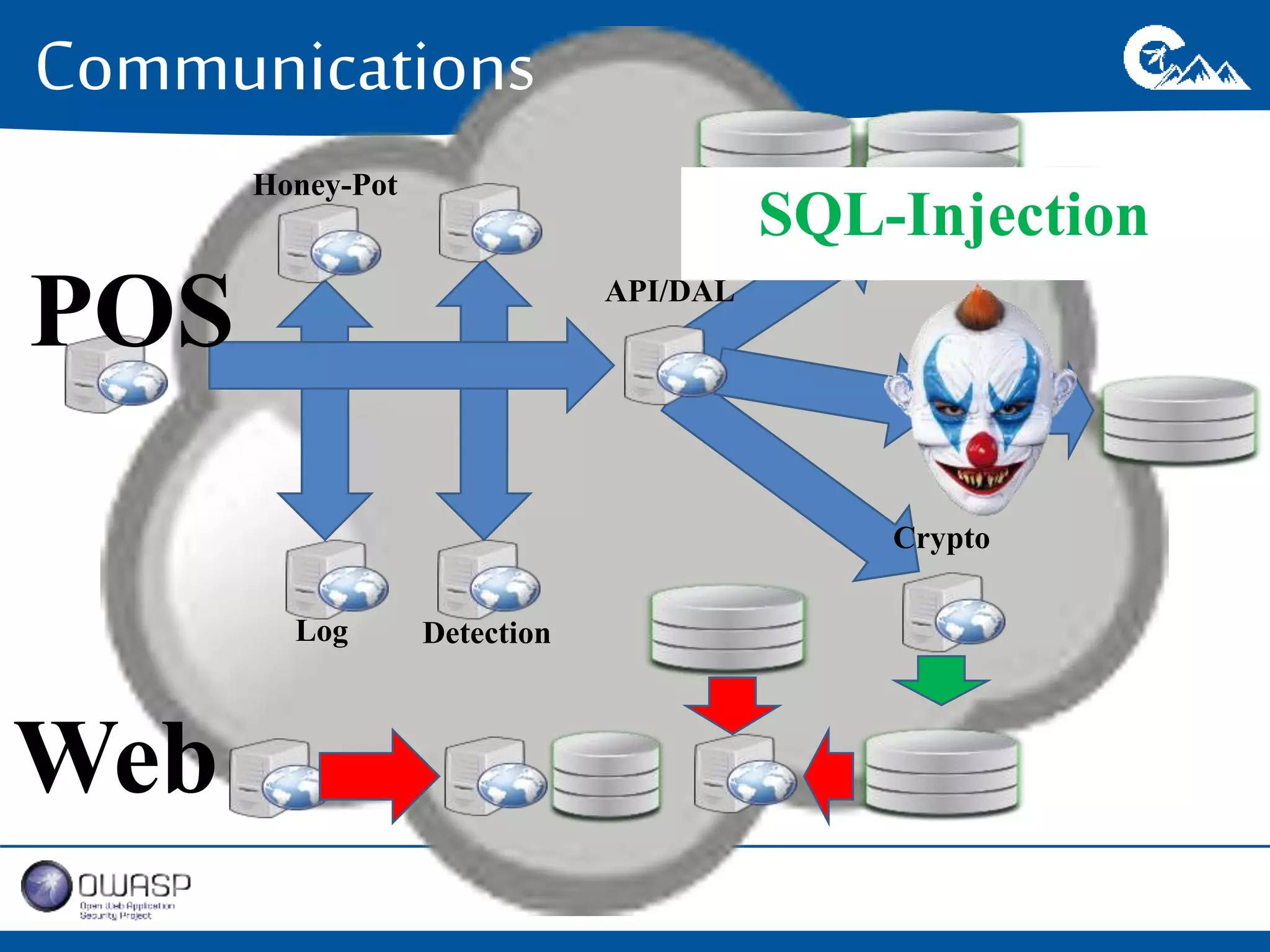
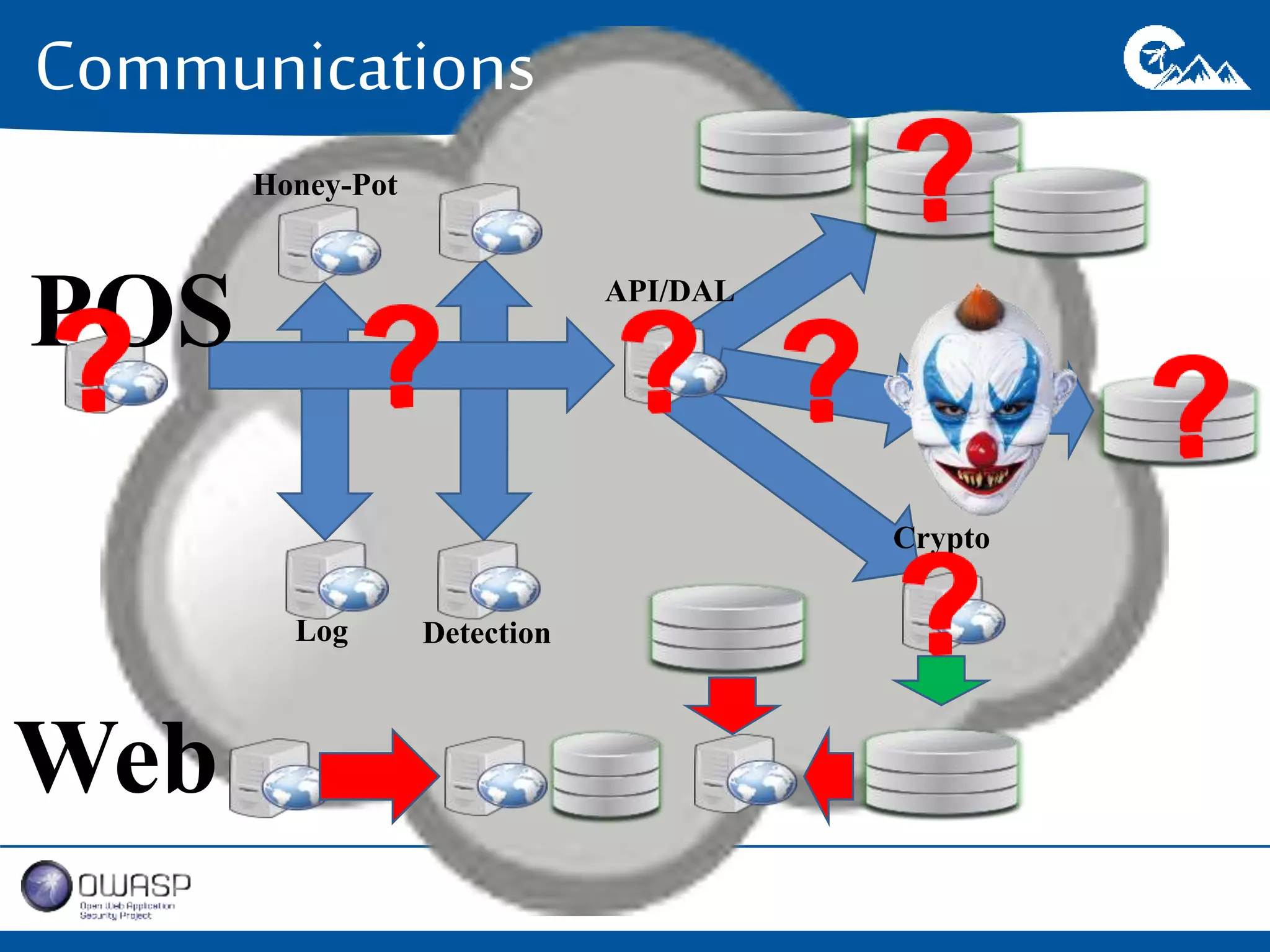
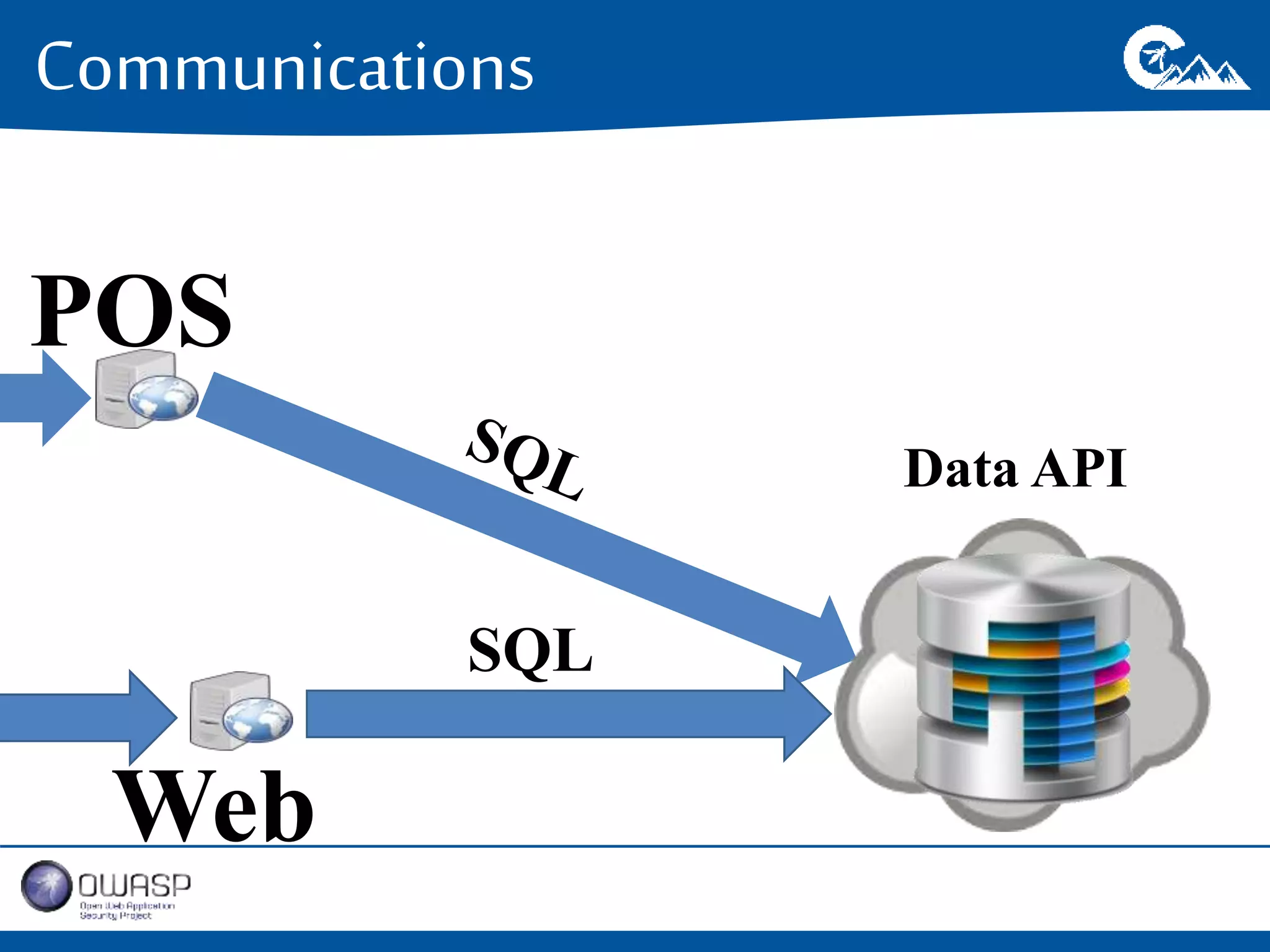
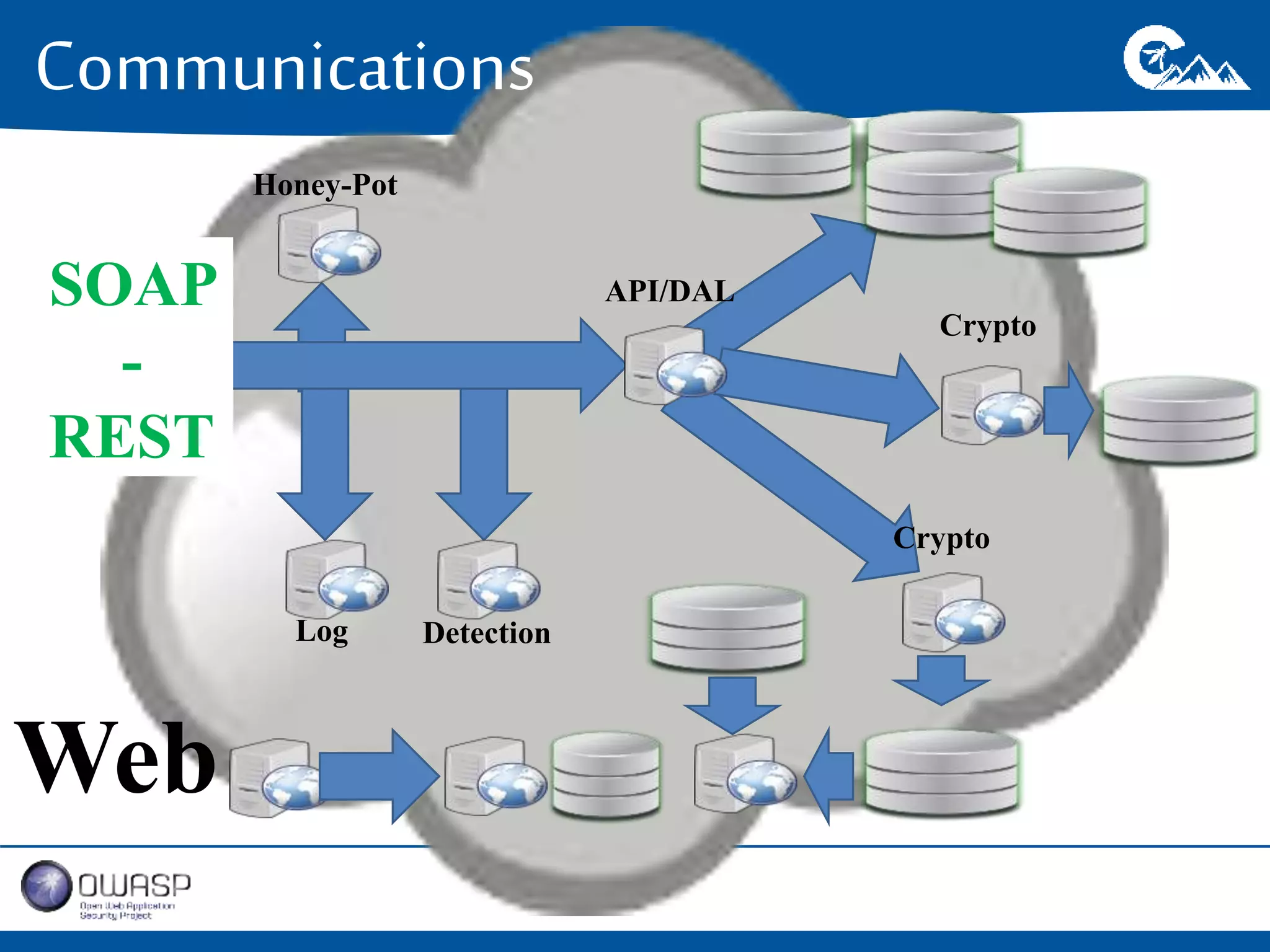
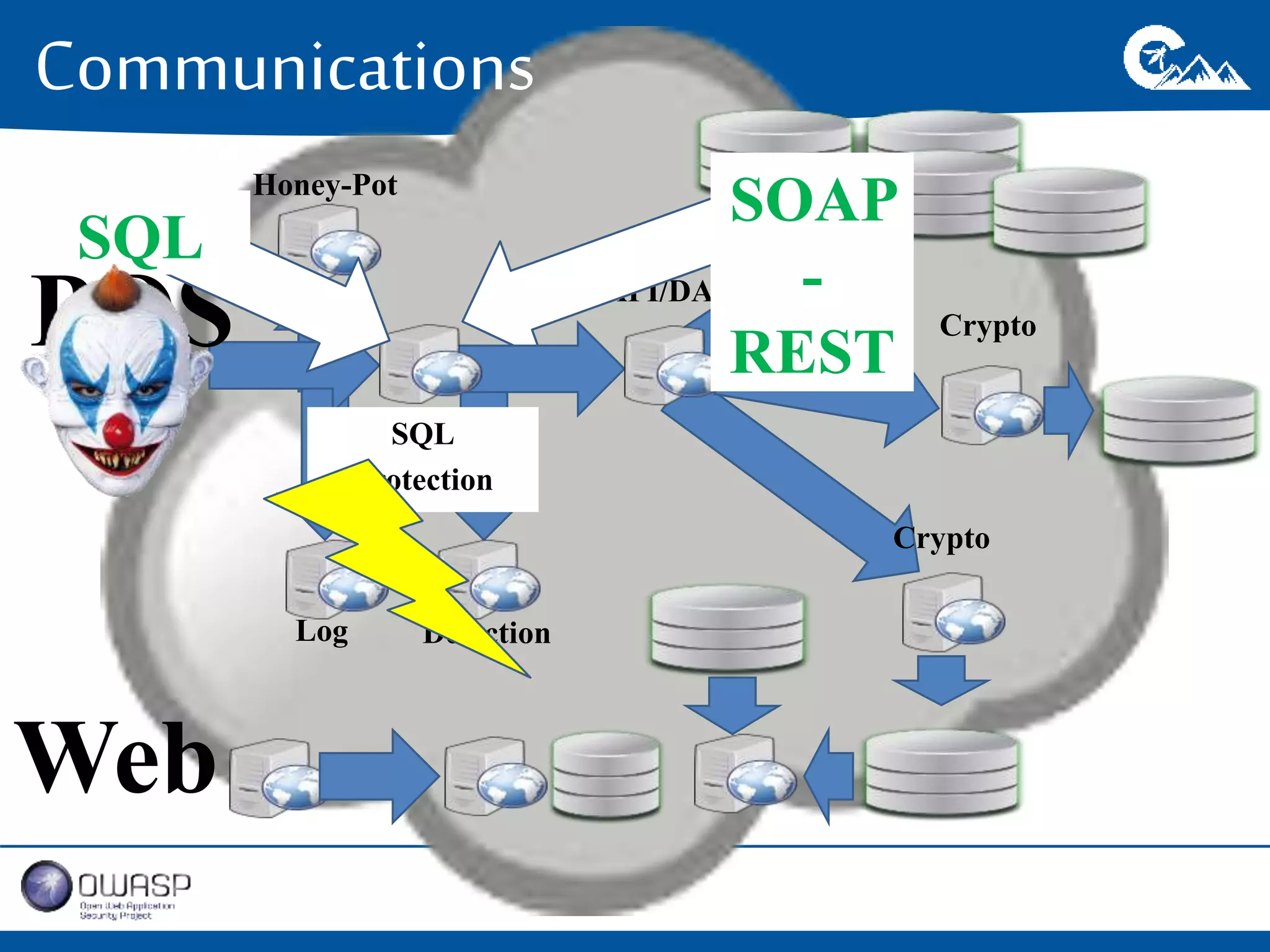
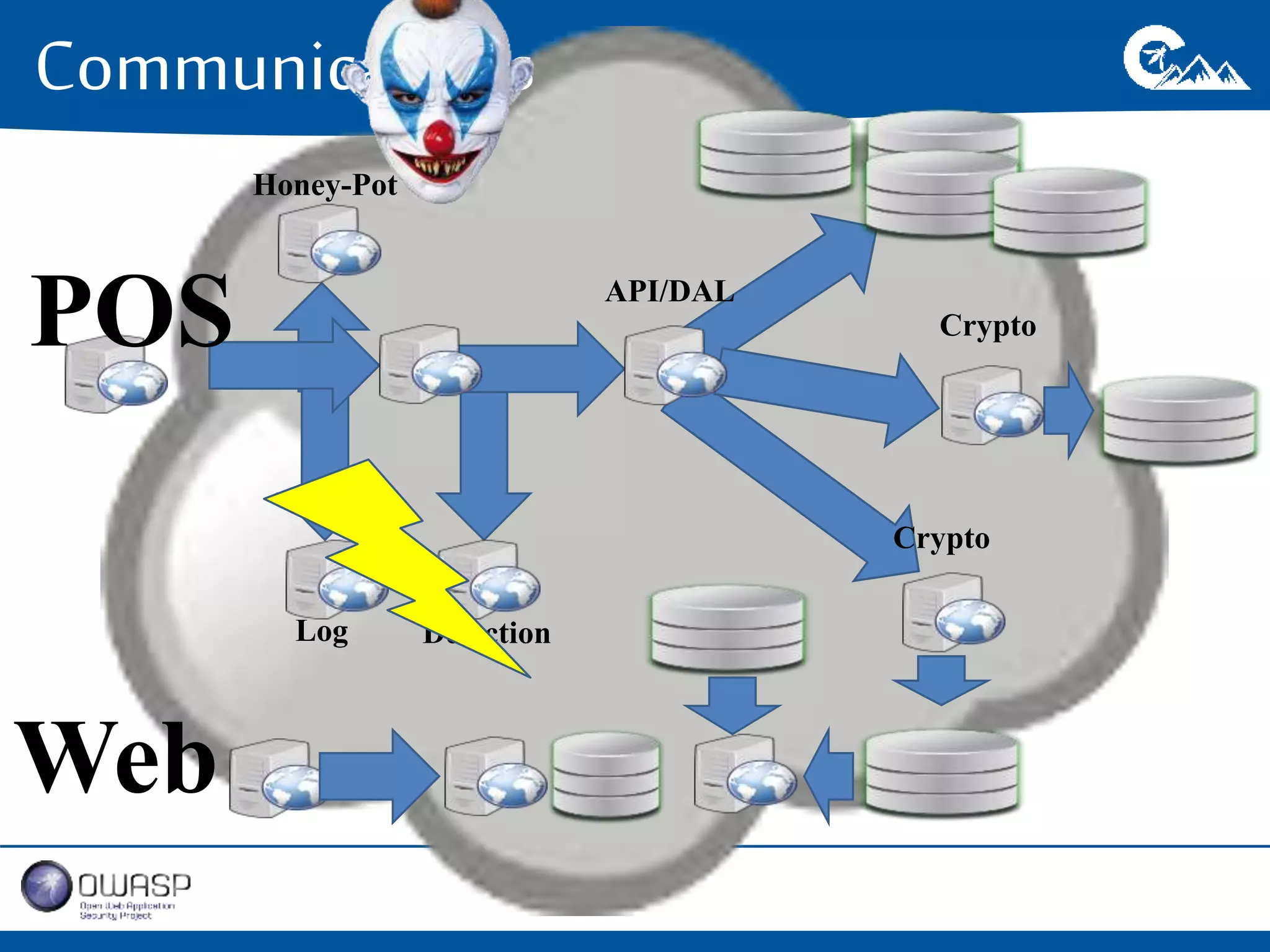
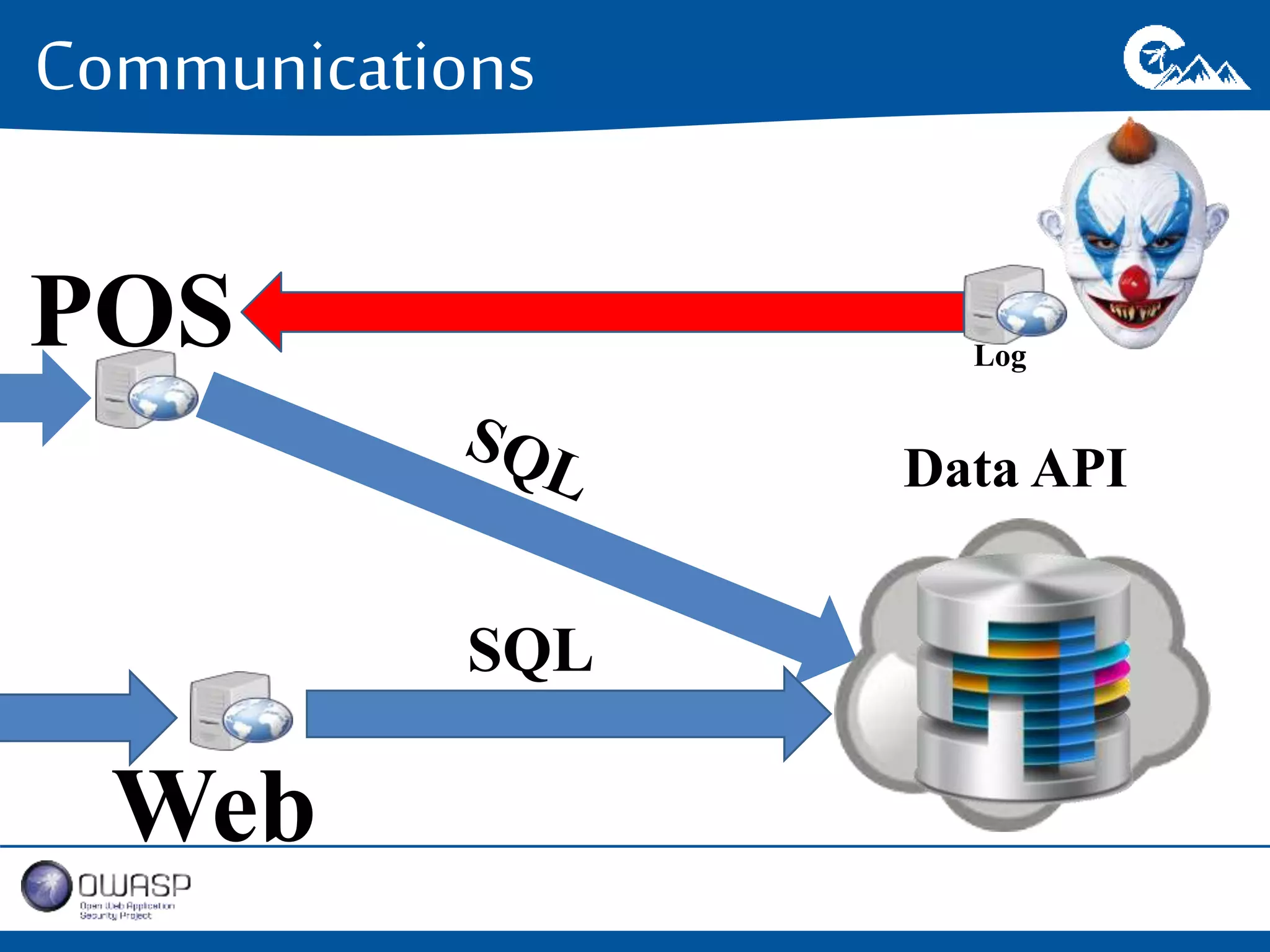
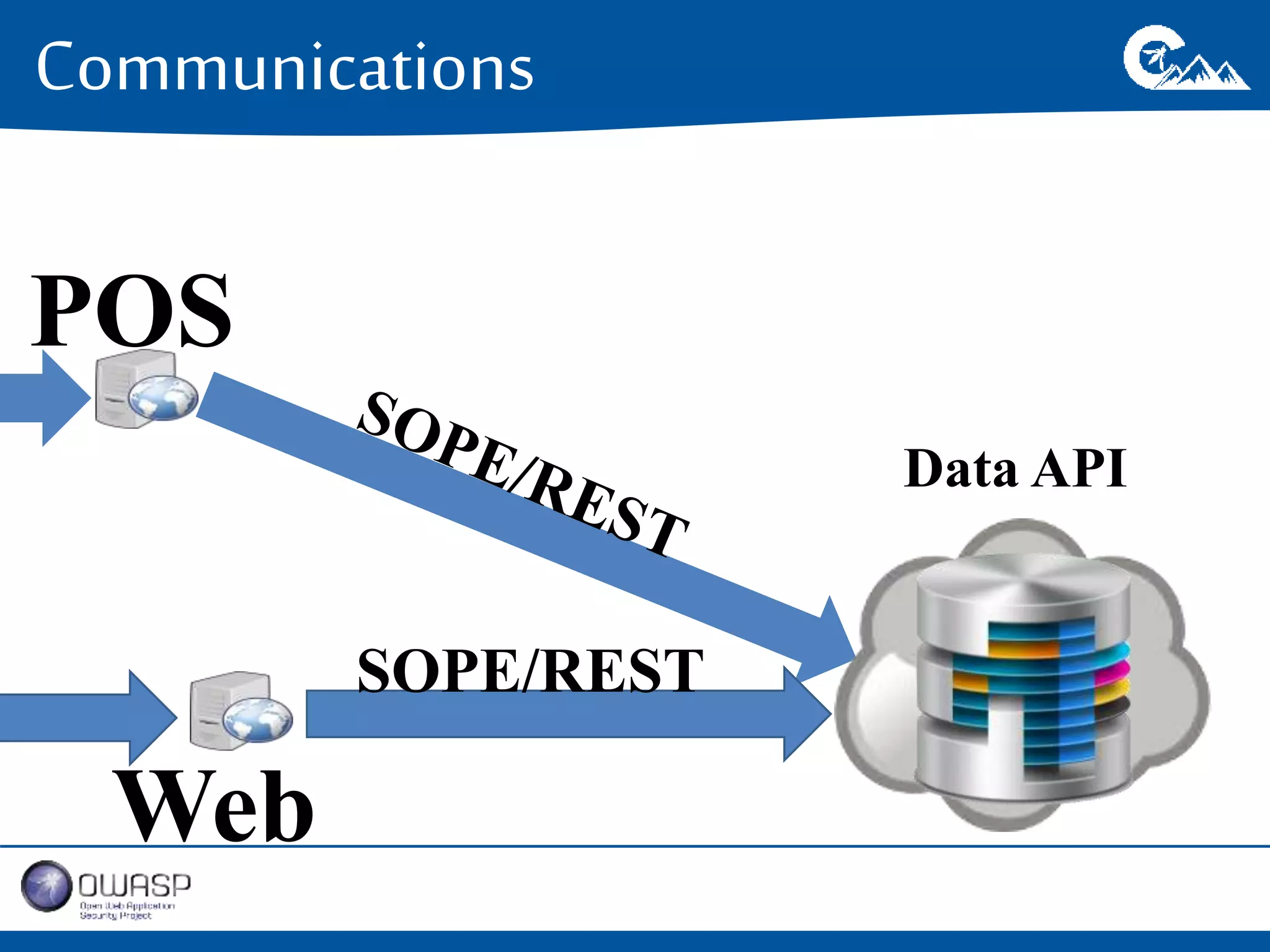
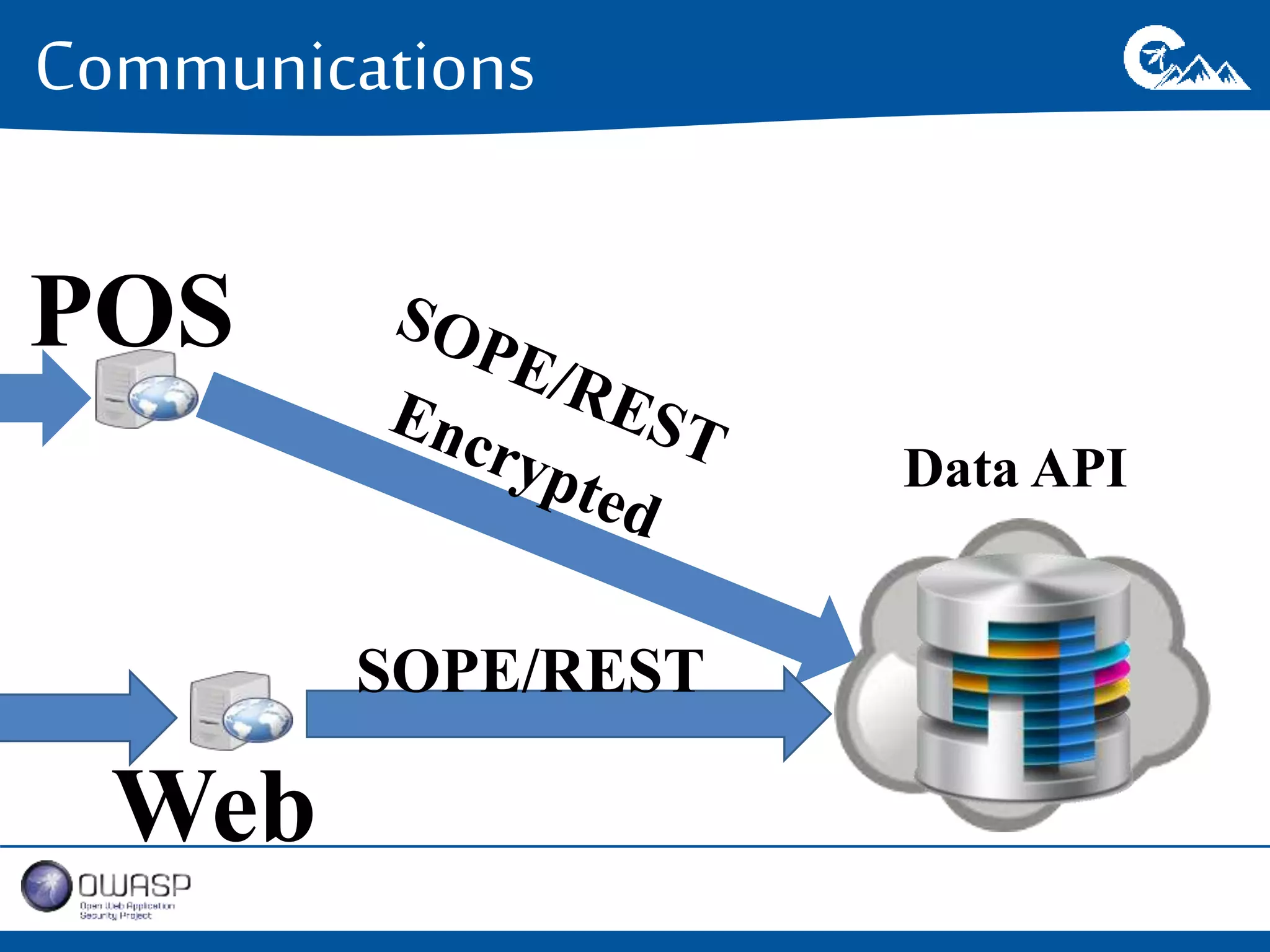
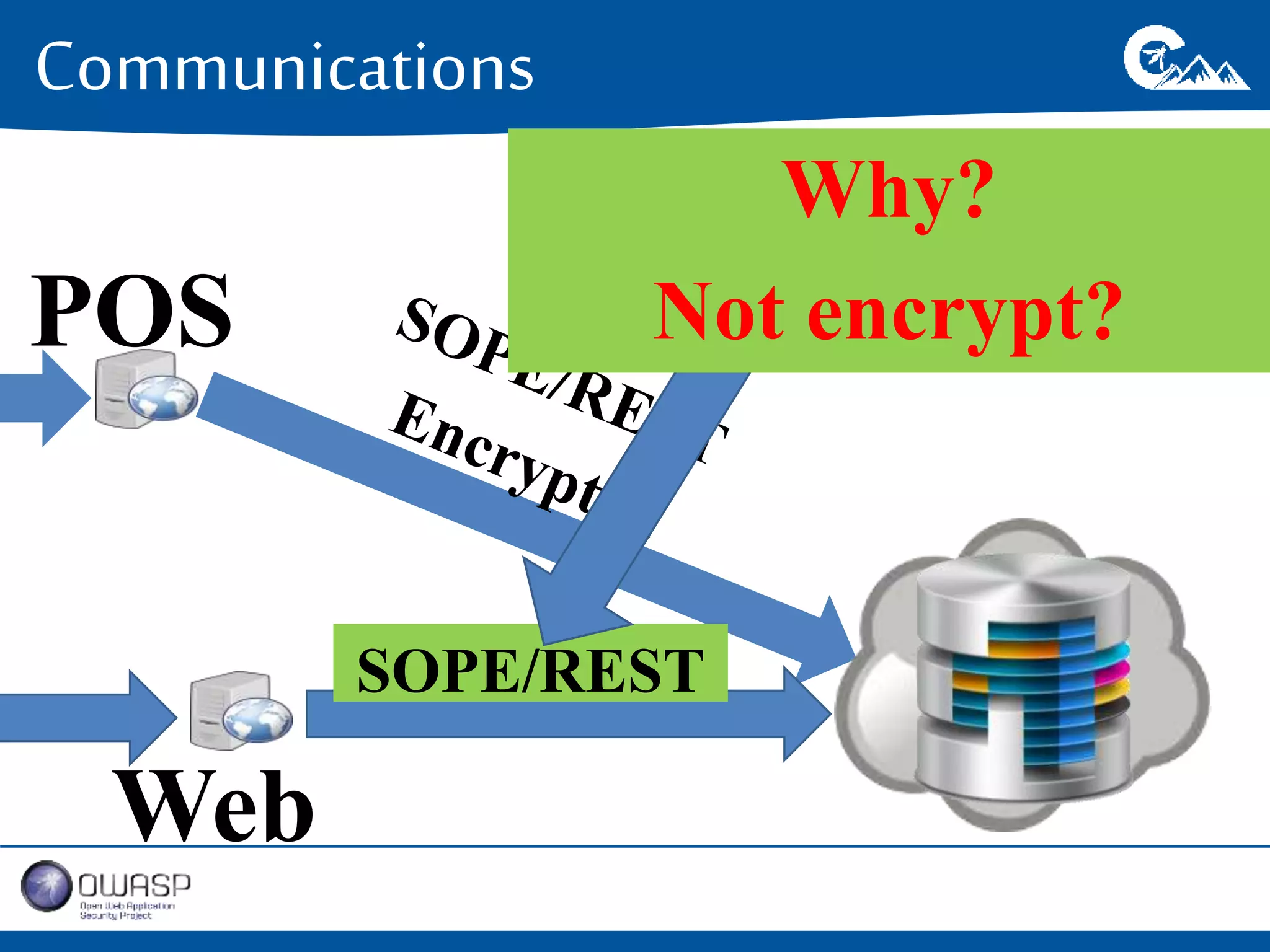
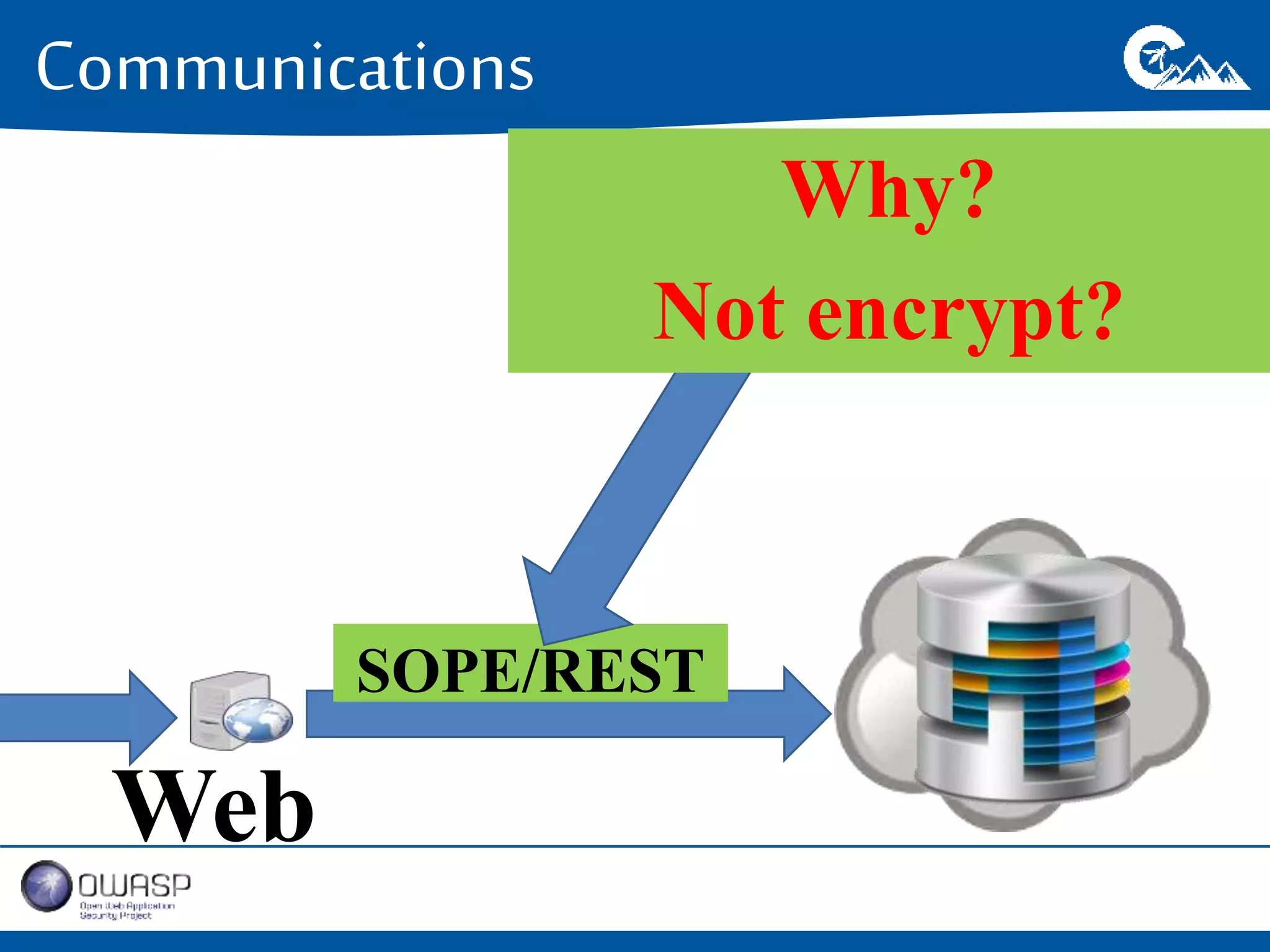
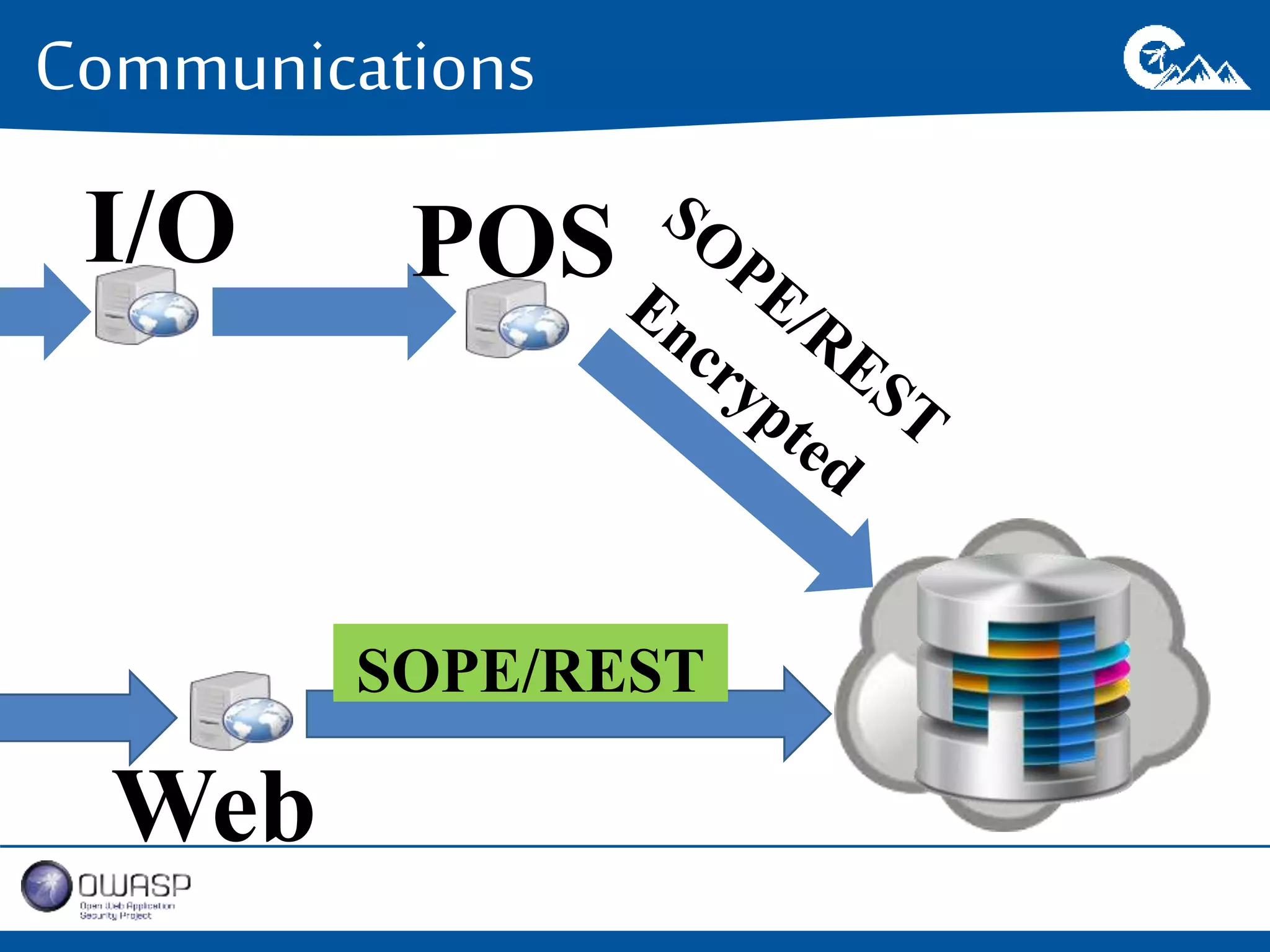
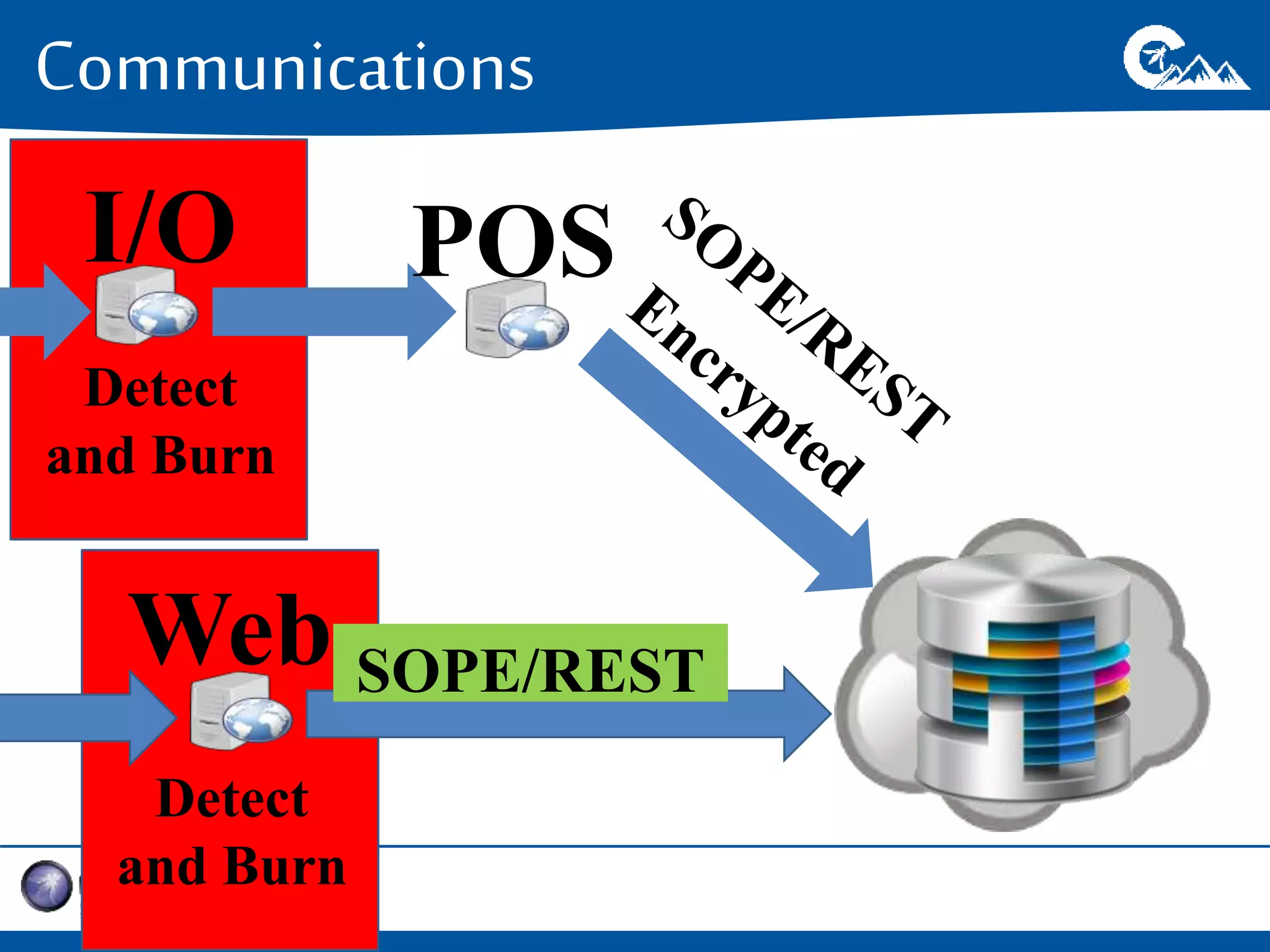
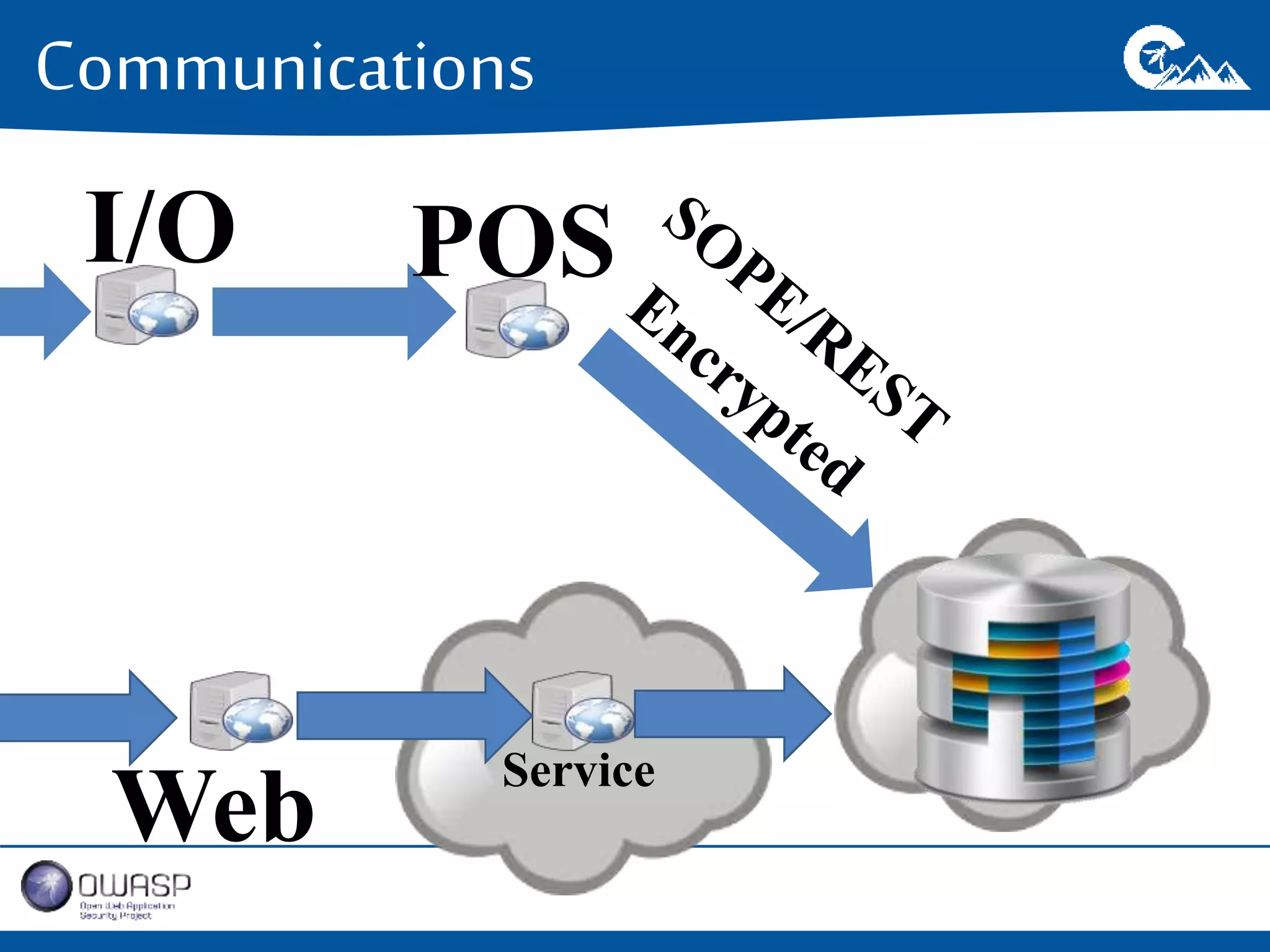
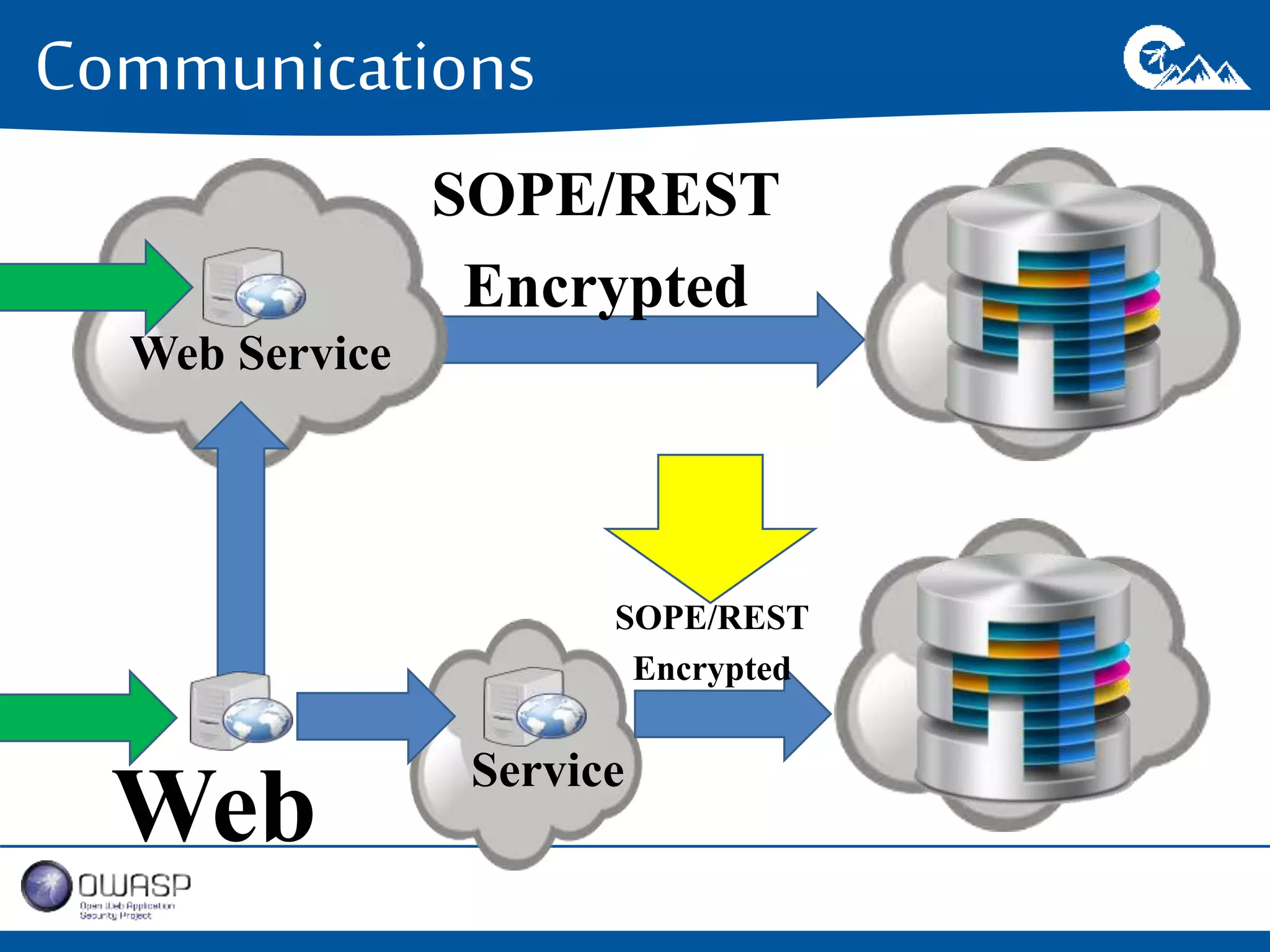
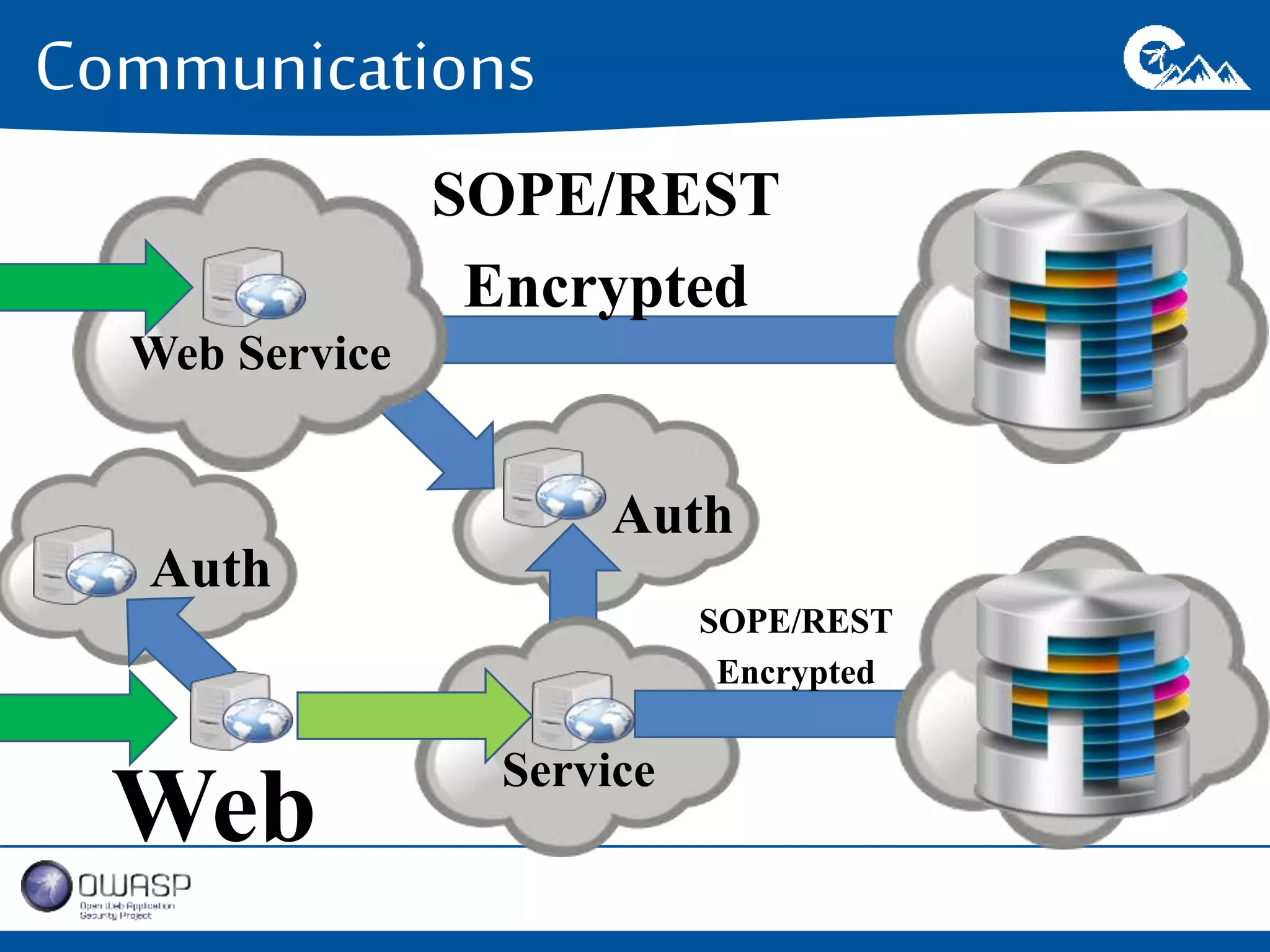
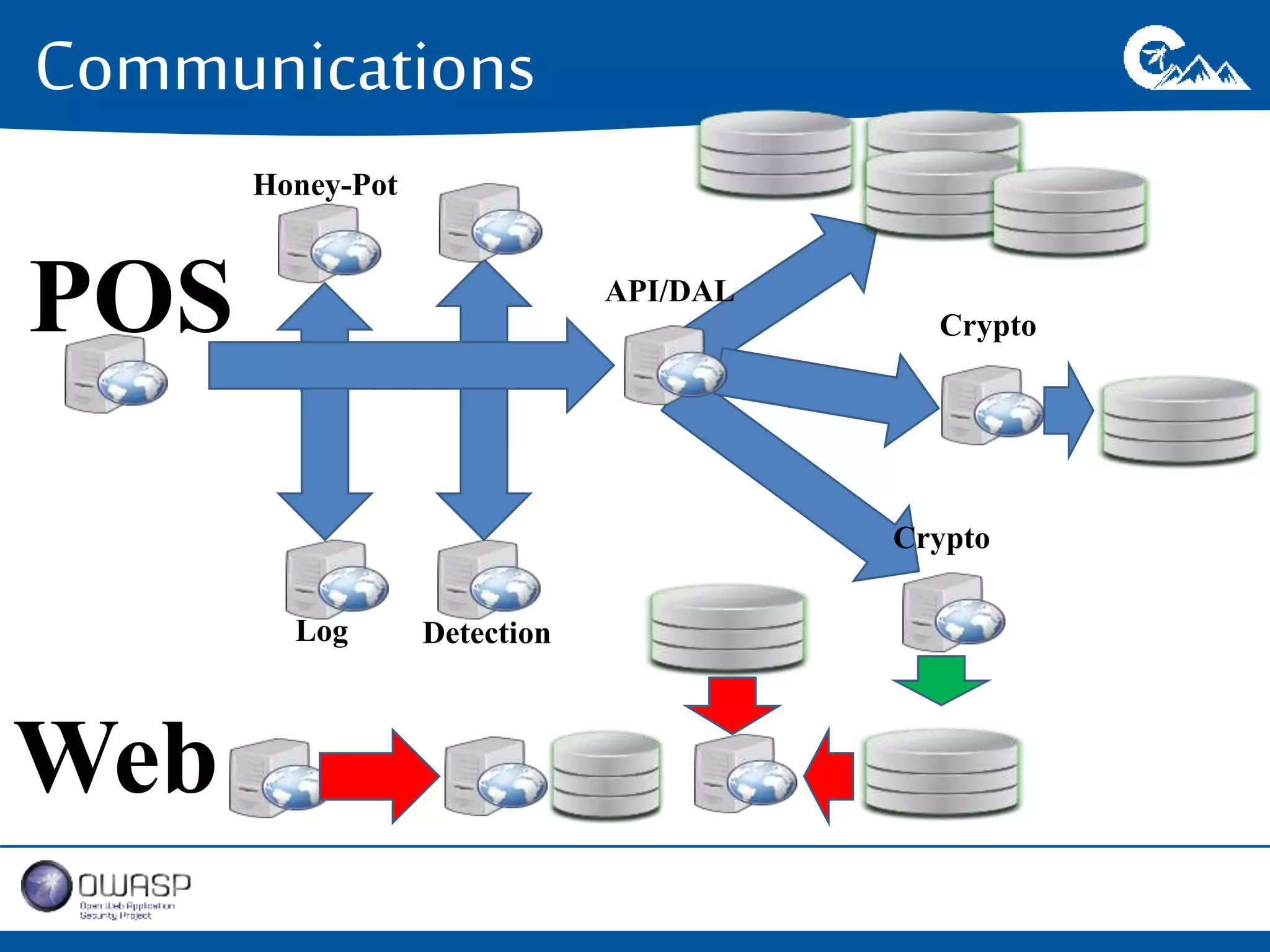
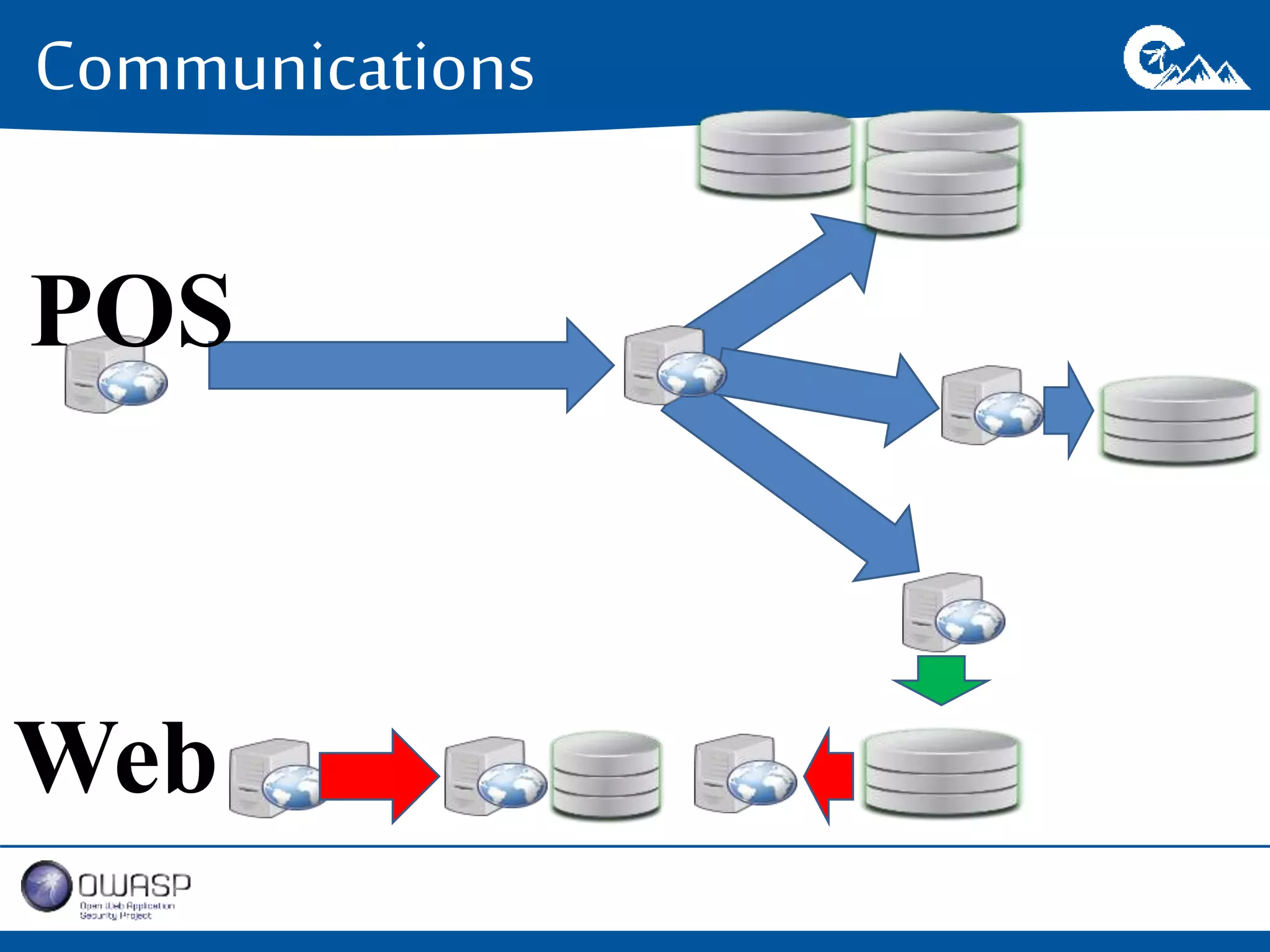
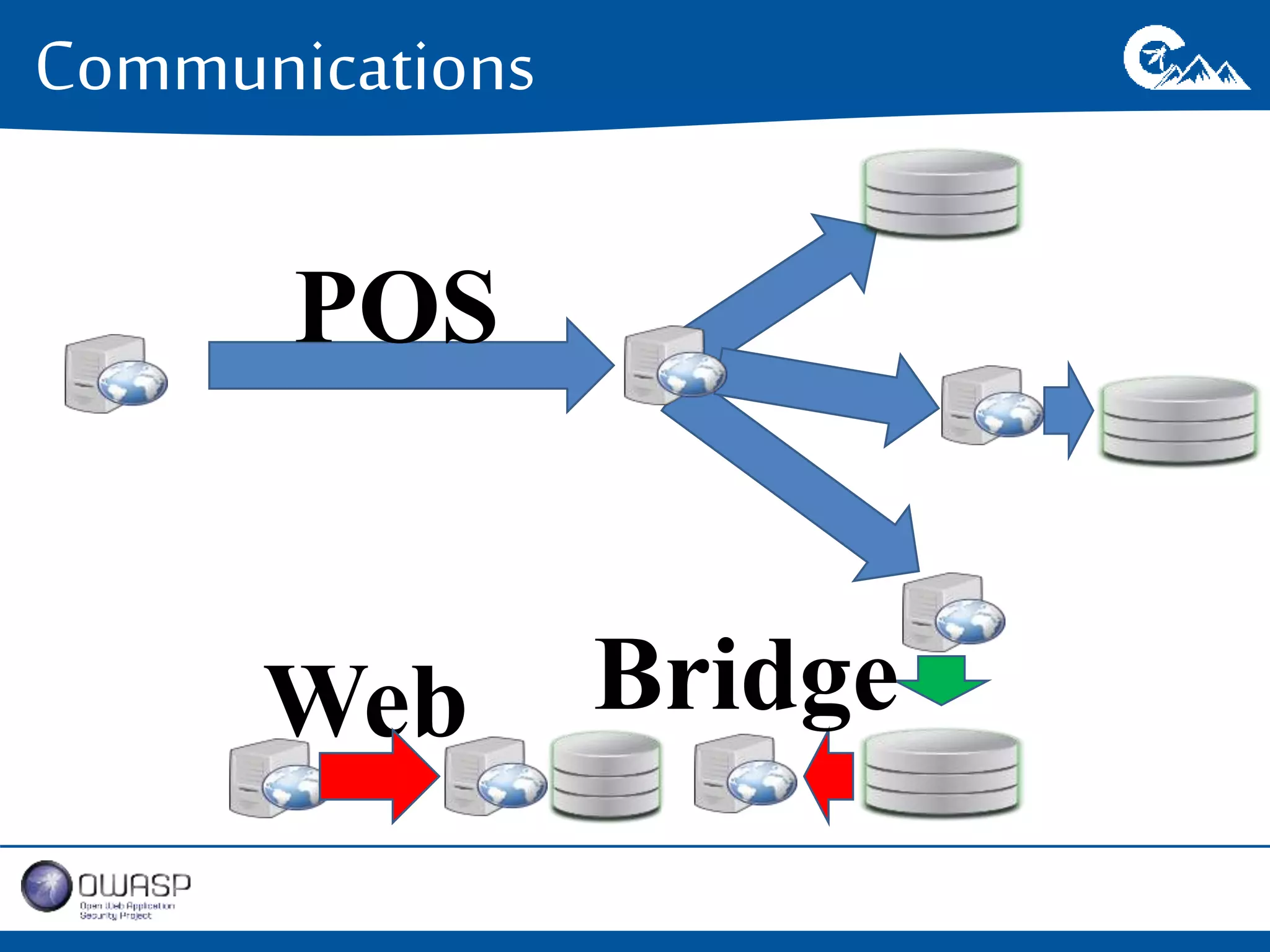
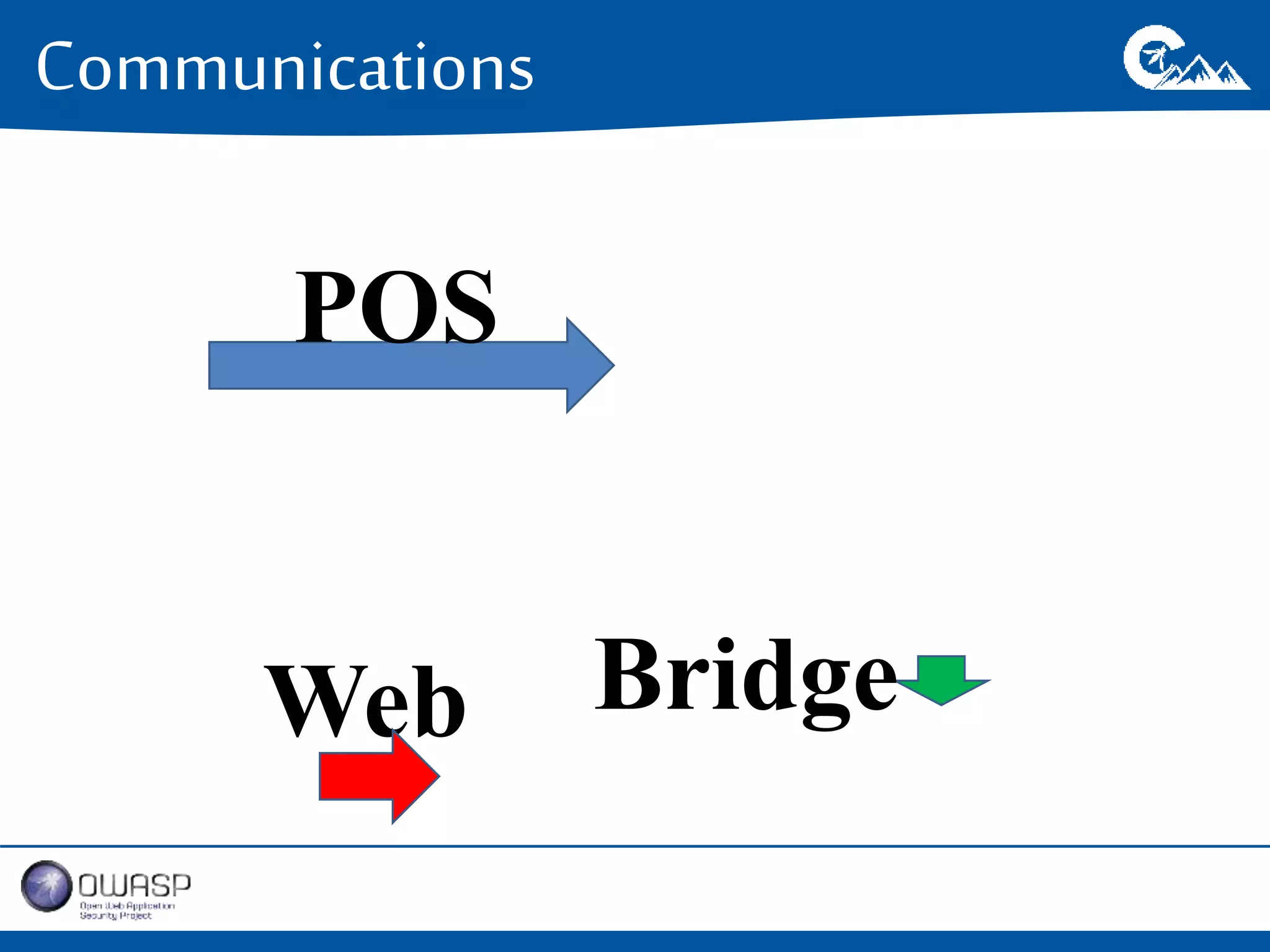
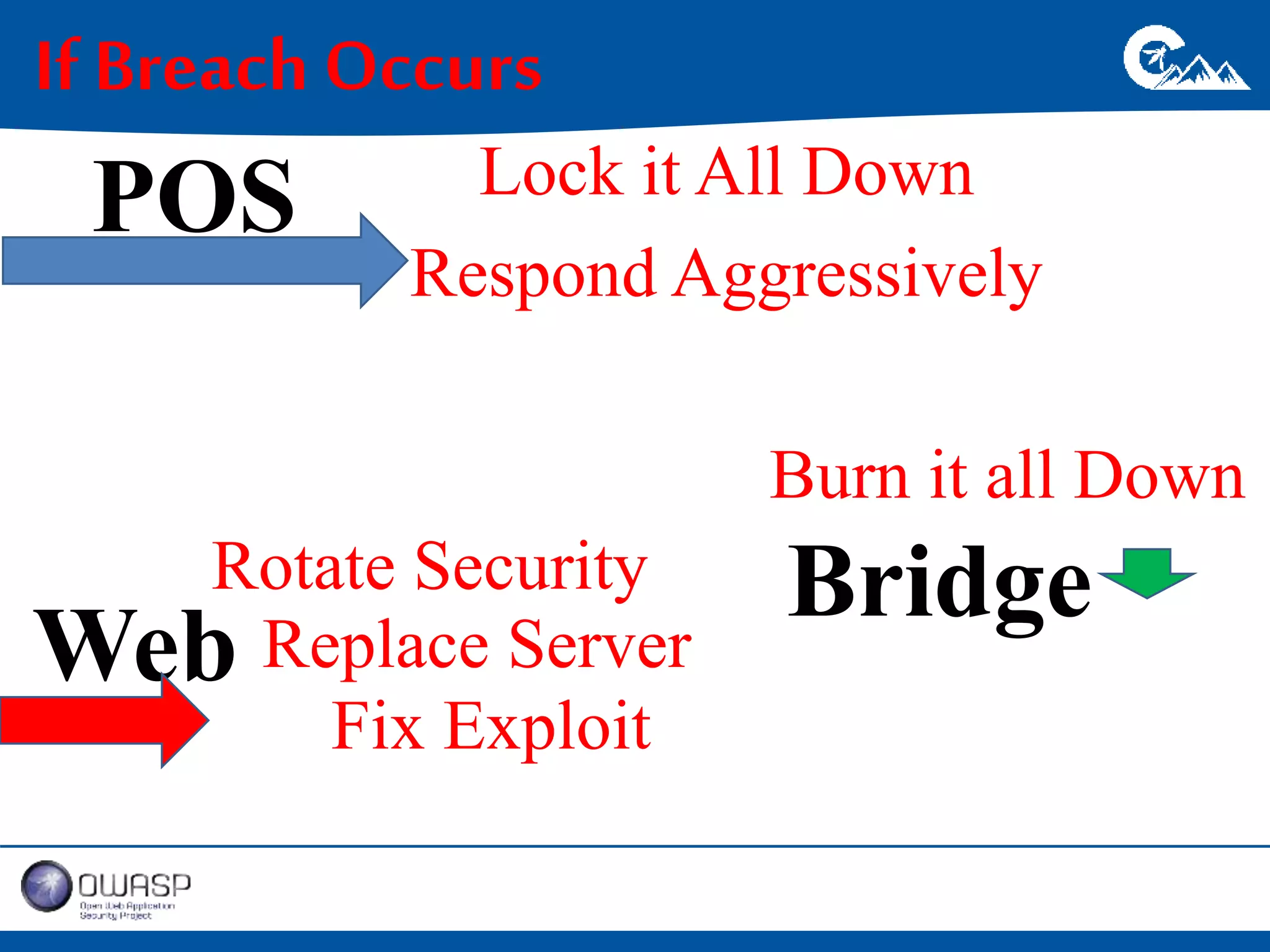
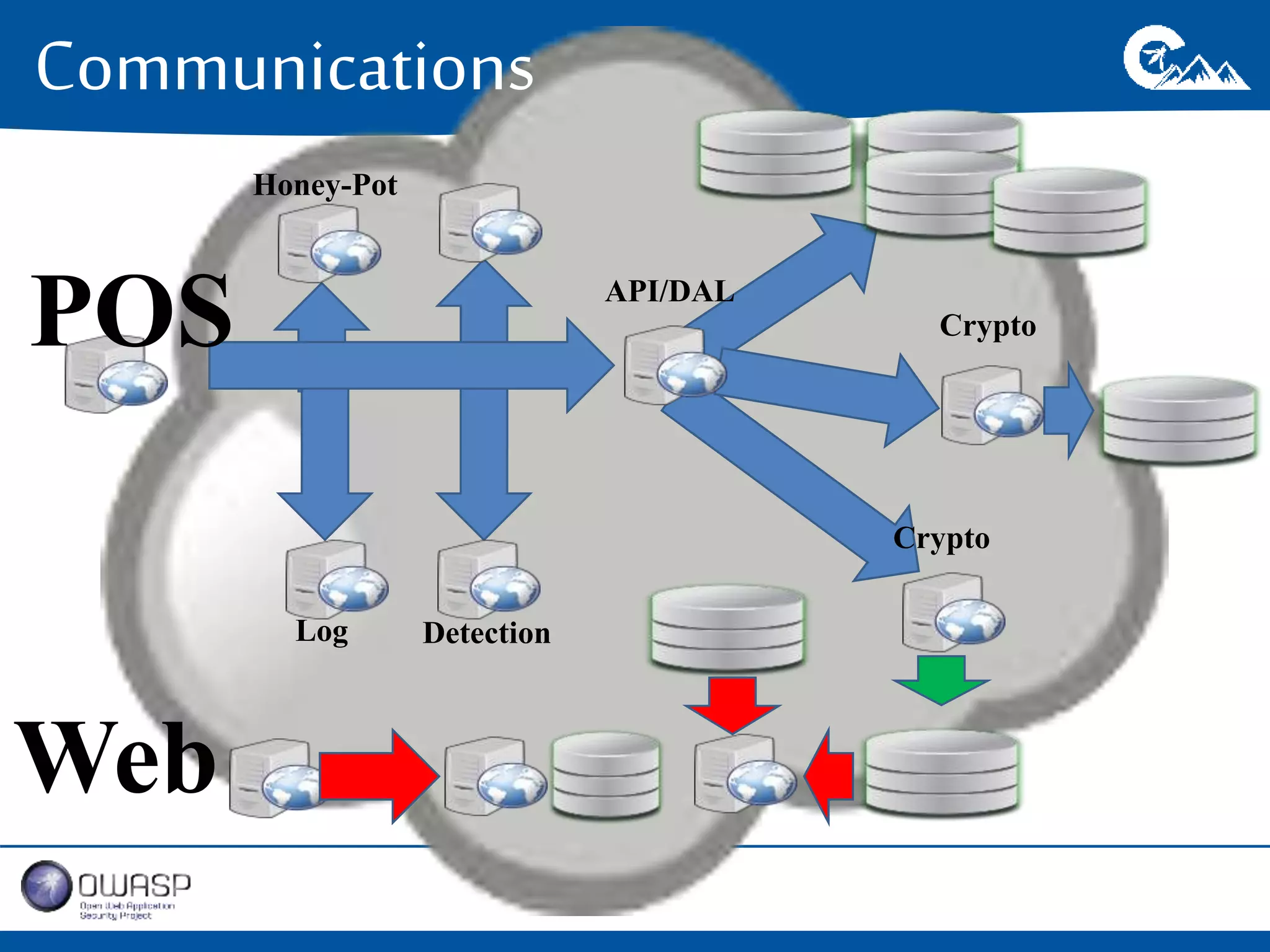
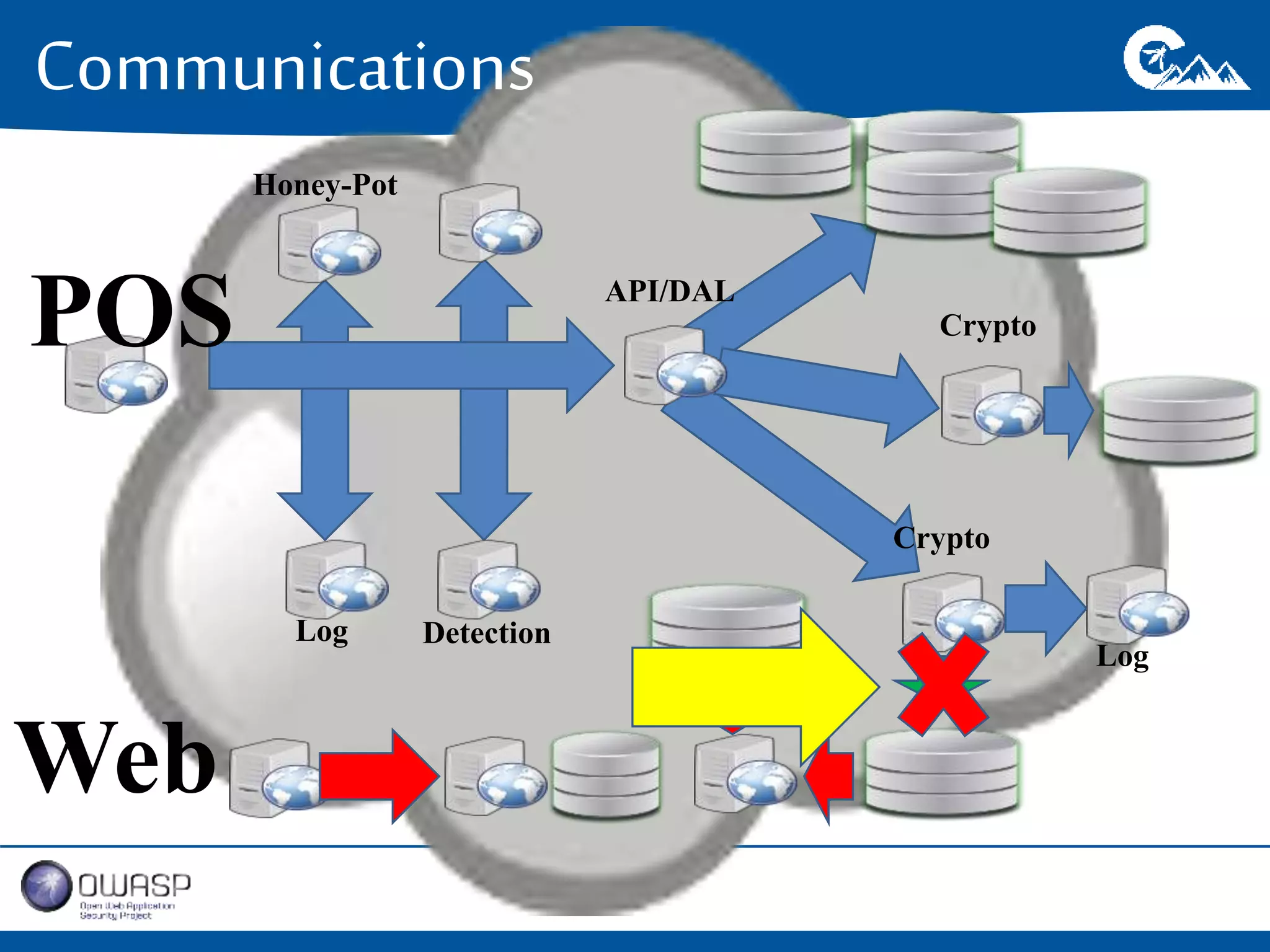
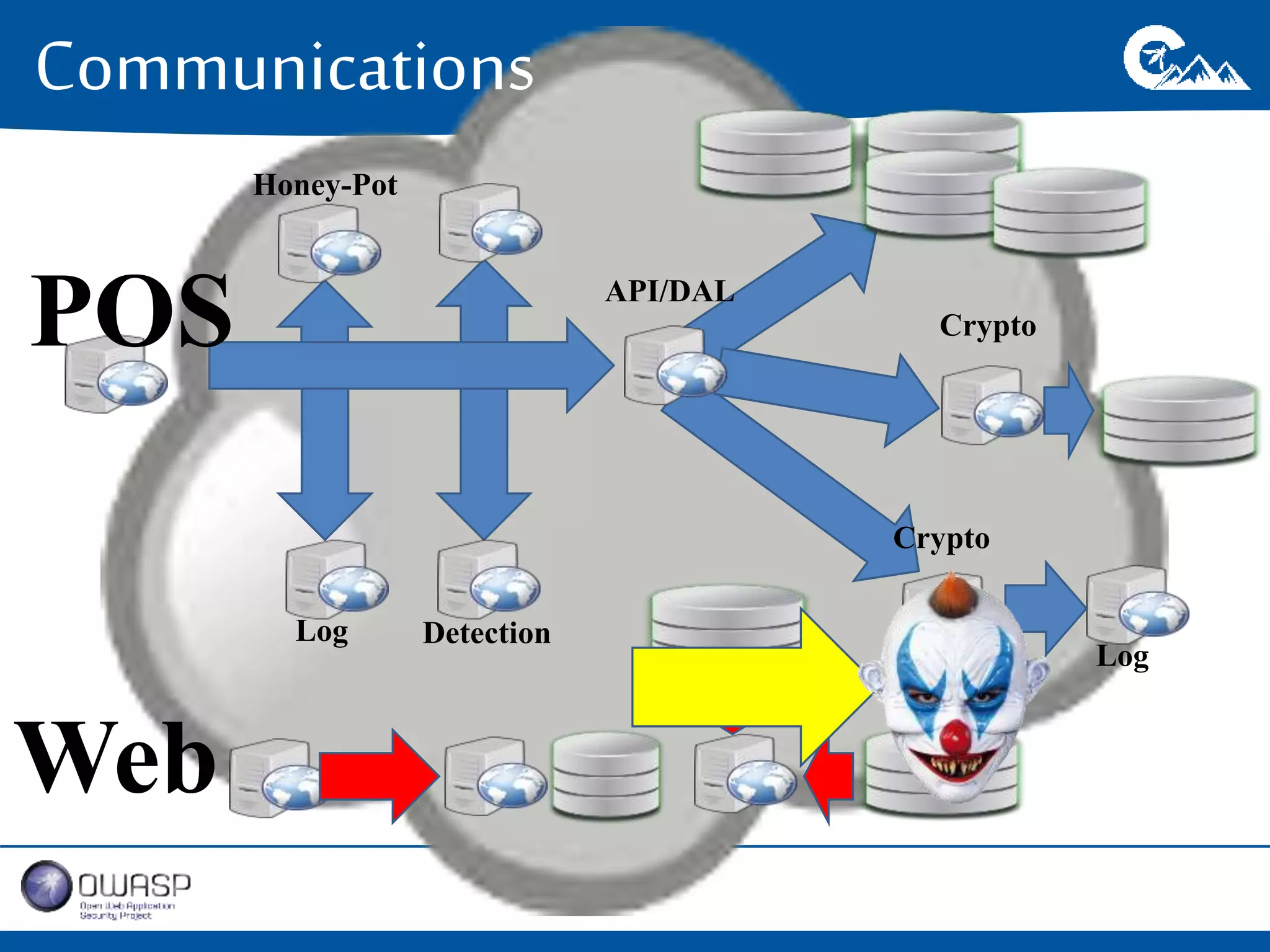
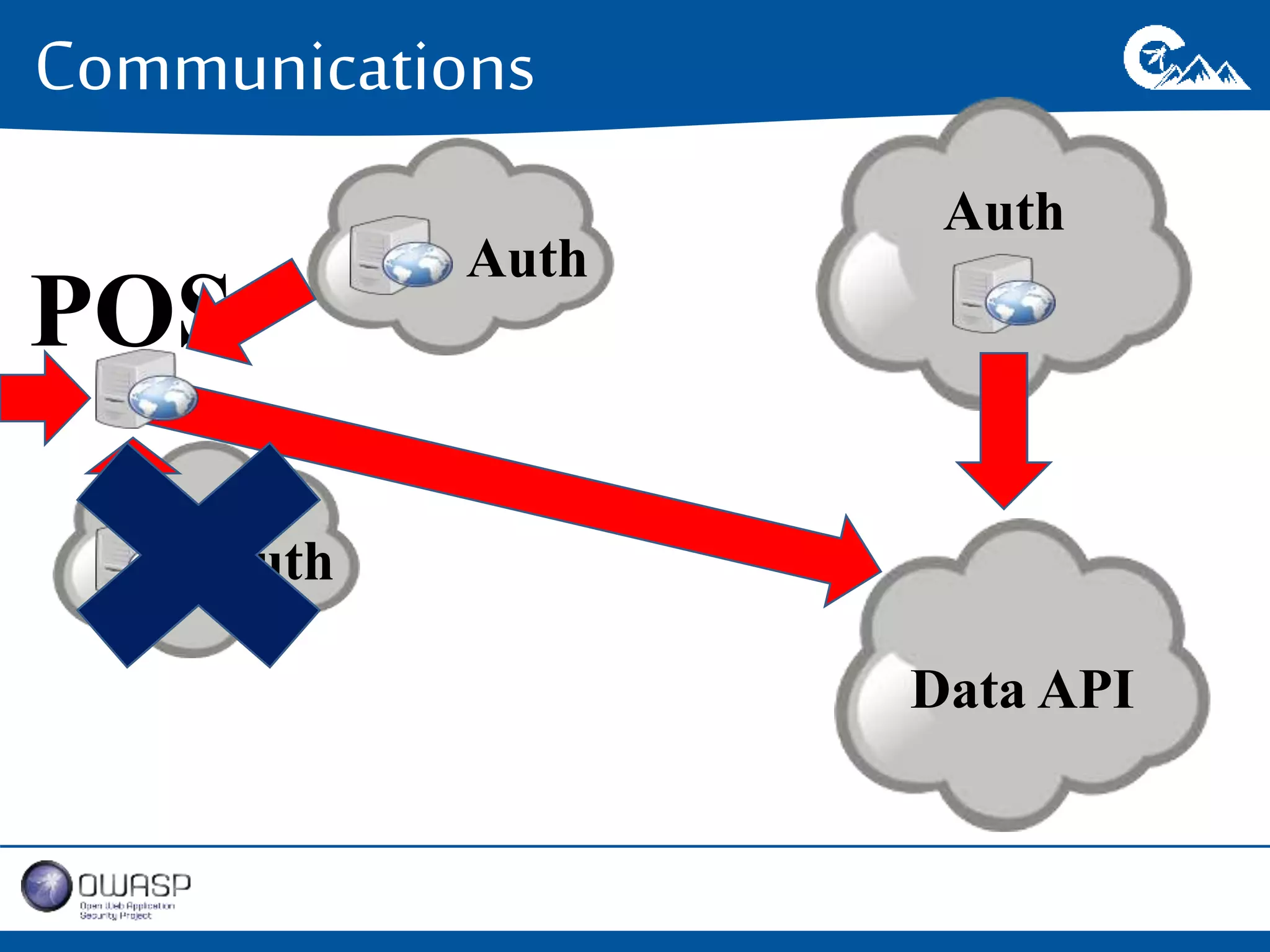
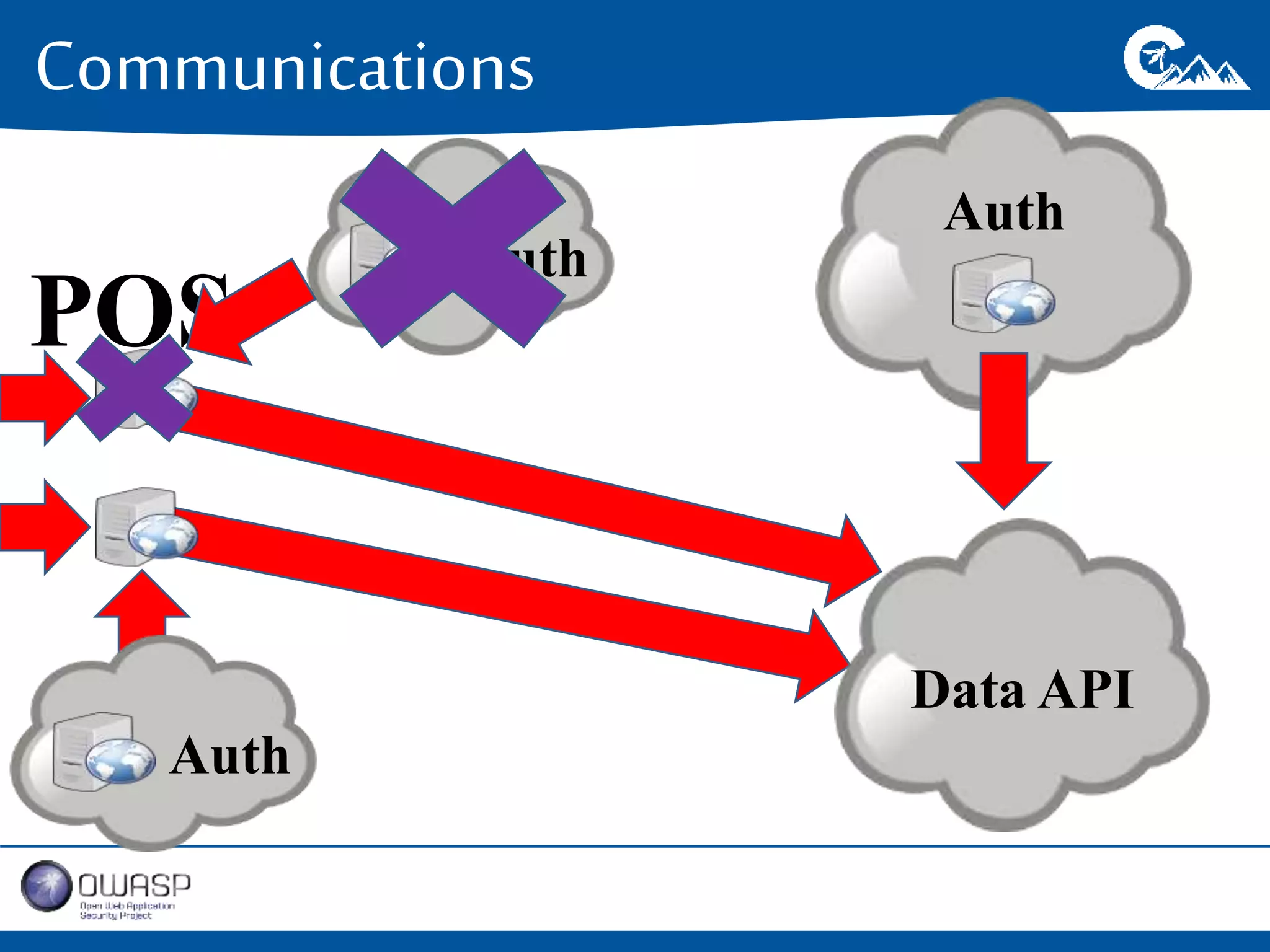
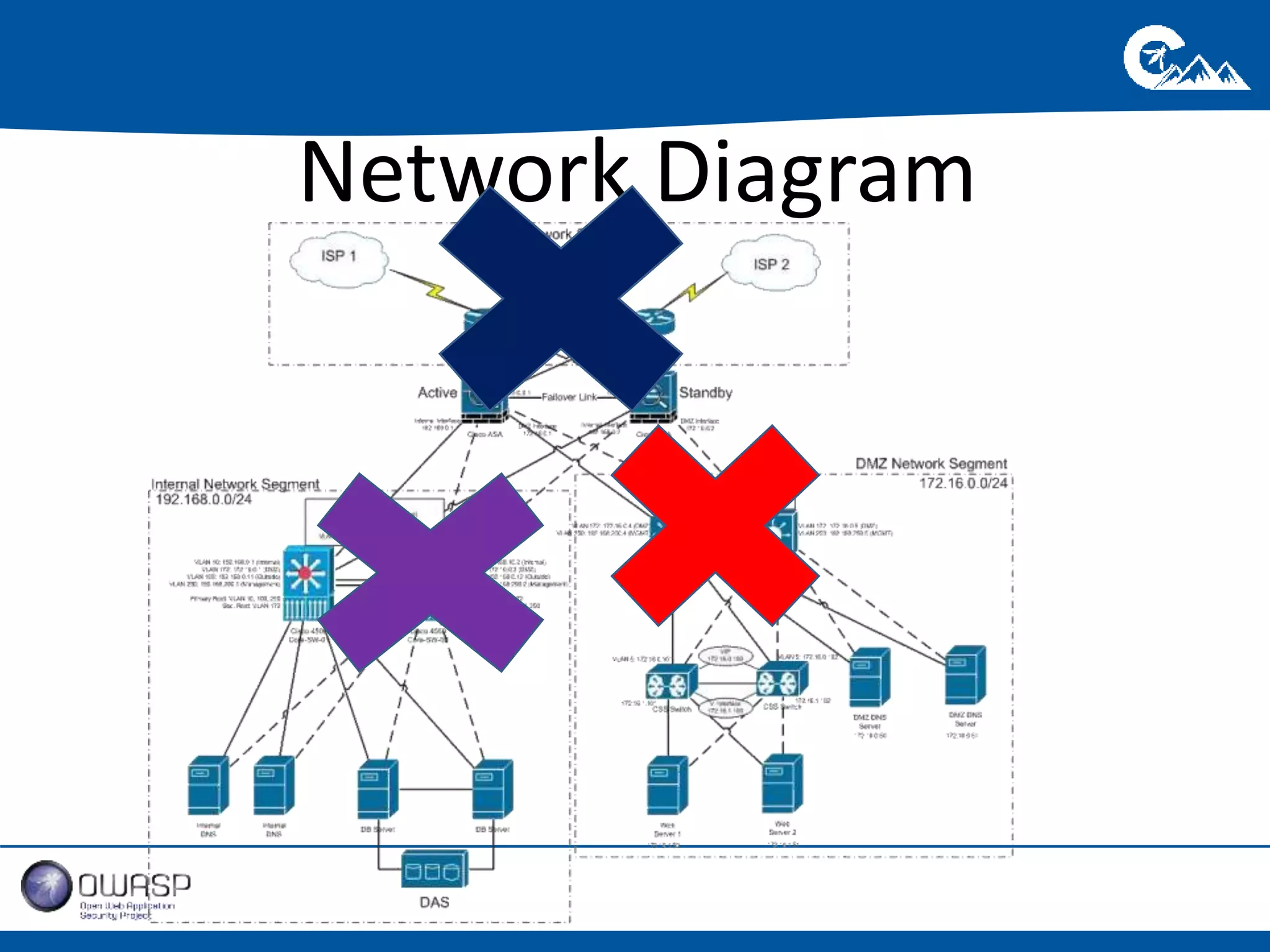
This document outlines a presentation on securing .NET/C# applications. It discusses designing defendable systems through layered defenses, segmentation, and establishing a common security language between different teams. Examples are provided of strong versus weak software designs. The importance of security user stories and testing is emphasized to prevent vulnerabilities like SQL injection.