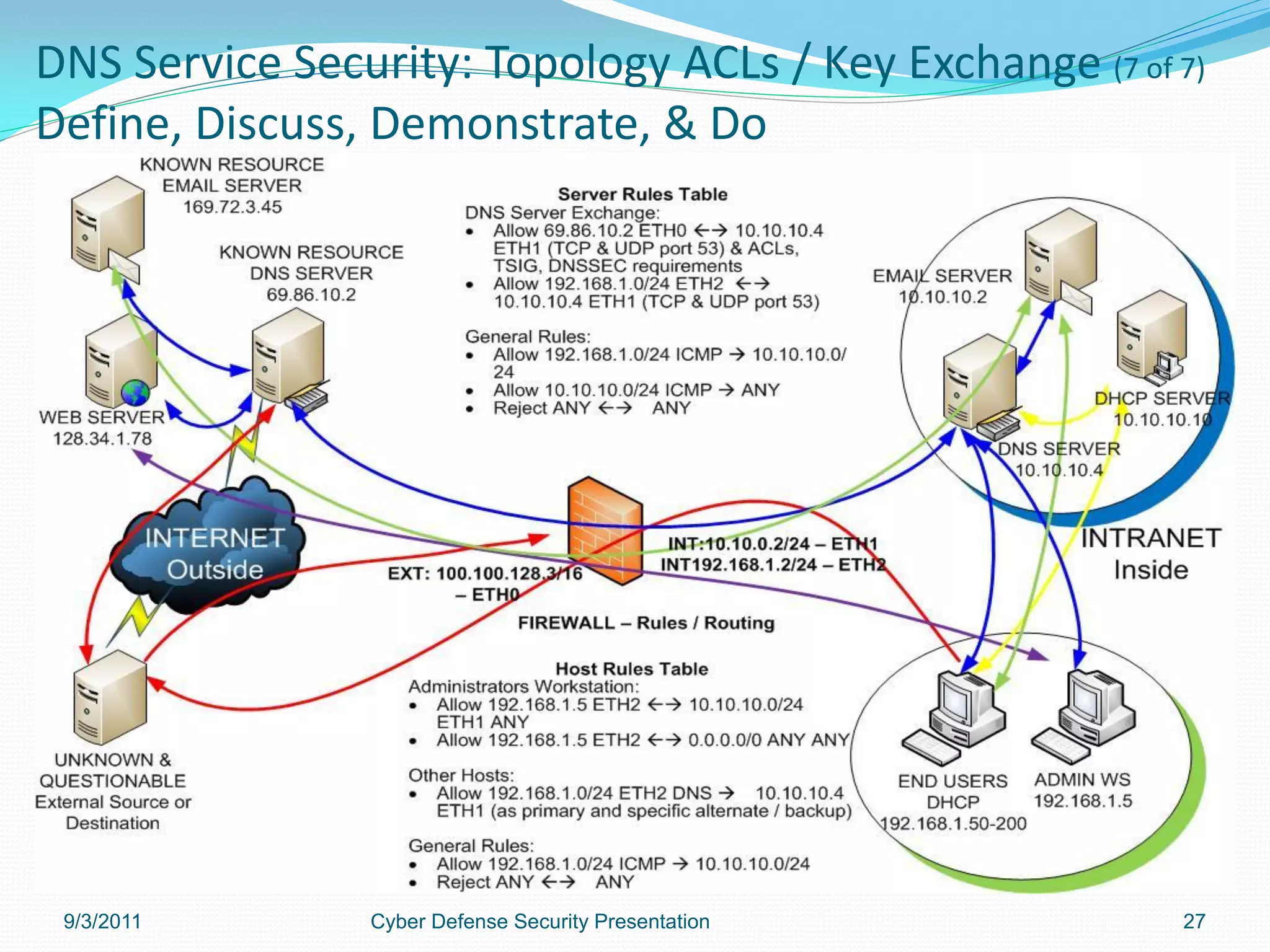
This document provides an overview and agenda for a presentation on securing and hardening DNS servers. It discusses configuring DNS servers at both the local system level and network level. At the local level, it recommends partitioning the file system, using chroot jails, firewalls, and access control configurations. At the network level, it discusses topics like limiting services, securing NTP, and managing DNS zones and records. The overall goal is to understand the high-level requirements for securing a DNS server and limiting access to the DNS service.







![DNS Service: Security Considerations
Define, Discuss, Demonstrate, & Do (1 of 3)
Where will the application physically reside on the local OS?
Partition type, quotas, & ACLs
Manage space allocation
Prevent hard links programs; facilitate precise control over mount options
limits user access or influence
Allow minimal privileges via mount options
Chroot Jail DNS application
If service compromised, limits user rights & privileges escalation - If local user
compromised limits influence on application
Function?
Runs a process with root directory other than /
$ /usr/sbin/chroot /home/user_name/existing_directory
Challenge is to include interdependent binaries / libraries files into the “Jail” environment
Once setup, change to location and start service or application
How will you manage DNS’s local functional influence? Must manages
applications ability to influence overall system functionality!
SELinux (Alt. AppArmor)
http://web.mit.edu/rhel-doc/5/RHEL-5-manual/Deployment_Guide-en-US/ch-
selinux.html http://www.nsa.gov/research/selinux/index.shtml
http://hackinglinux.blogspot.com/2007/05/selinux-tutorial.html
PAM – Pluggable Authentication Modules (Access Control)
http://www.linuxdocs.org/HOWTOs/User-Authentication-HOWTO/x101.html
How will you manage access to the service ?
TCPWrappers: /etc/hosts.allow & /etc/host.deny;
daemon_list:client_list:[:command]
Firewall local and remote settings: IPTables
Disable all on unneeded services!
Enable application auditing
Log Management – monitor activity and events types!
9/3/2011 Cyber Defense Security Presentation 17](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-17-2048.jpg)
![DNS Service: Security Considerations
Define, Discuss, Demonstrate, & Do (2 of 3)
DNS Service Access Control: Sample exploit
http://unixwiz.net/techtips/iguide-kaminsky-dns-vuln.html
Access Control Lists (ACLs)
TSIG Transactions – shared hashed key
DNSSEC: Relies on public/private key authentication. DNSSEC
specifications (RFC 4033, RFC 4034and RFC 4035 augmented with
others) answer three questions: Authentication - the DNS
responding really is the DNS that the request was sent to. Integrity -
the response is complete and nothing is missing or changed. Proof
of non-existence - if the DNS returns a status that the name does
not exist (NXDOMAIN) this response can be proven to have come
from the authoritative server. RHEL # dns-keygen edit
/etc/rndc.key [insert key] or RHEL/Fedora # rndc-confgen >
/etc/rndc.conf; rndc status
Use DNSSEC to verify recursive DNS results
Default DNS BIND configuration in RHEL 6
options {
dnssec-enable yes;
dnssec-validate yes;
};
In /etc/named.conf will set a “trust anchor” trust the root DNSKEY
managed-keys {
/* not the real root key */
“.” initial-key 257 3 5 “BNY4wrWM1nCfJ+CXd0rVXyYmobt7sEEf
K3clRbGaTwSJxrGkxJWoZu6I7PzJu/E9
gx4UC1zGAHlXKdE4zYIpRhaBKnvcC2U9
mZhkdUpd1Vso/HAdjNe8L”;
};
Testing the validating recursive DNS server
# dig www.example.com +dnssec
9/3/2011 Cyber Defense Security Presentation 18](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-18-2048.jpg)

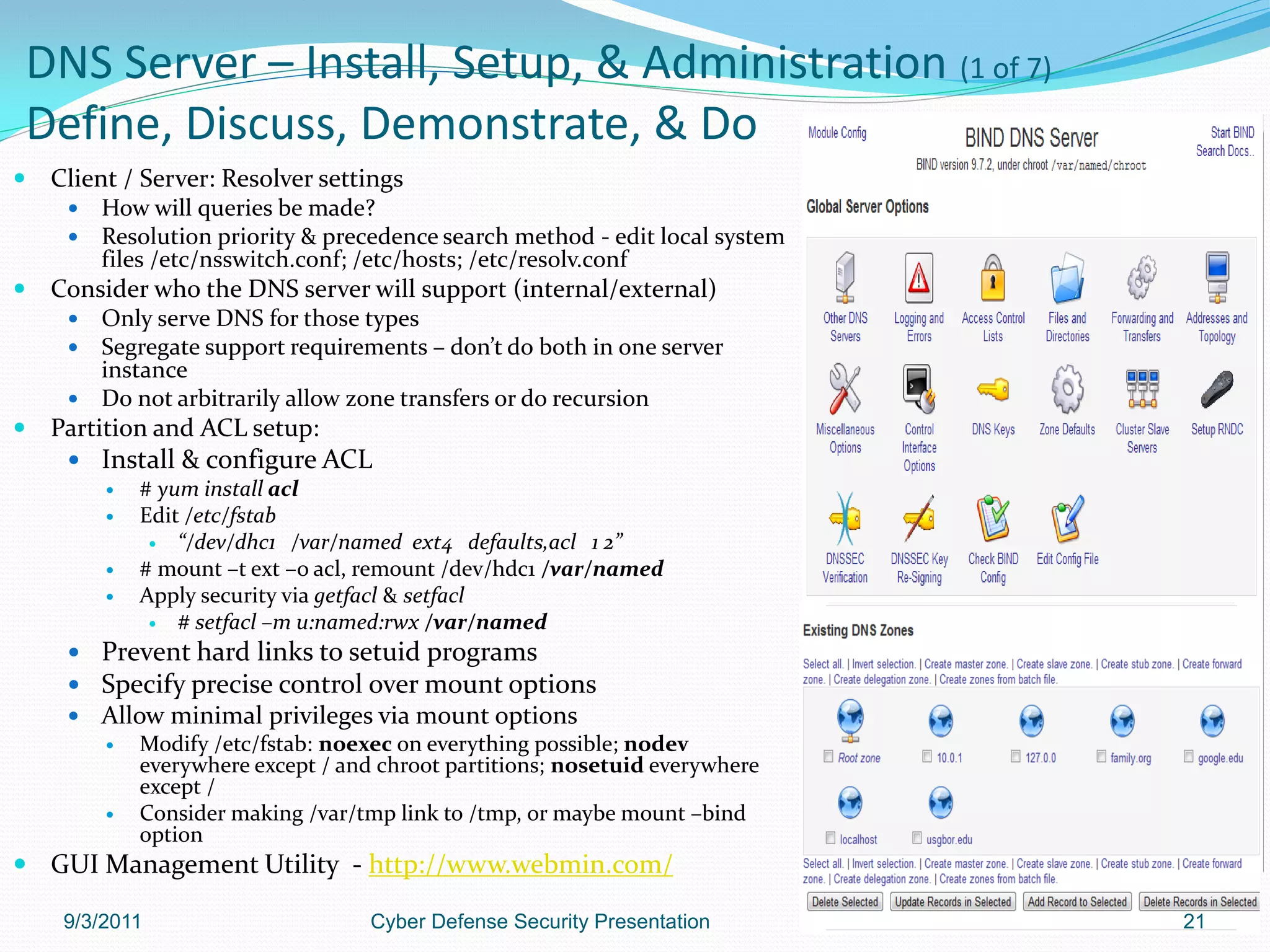
![DNS Server – Install, Setup, & Administration (2 of 7)
Define, Discuss, Demonstrate, & Do
Identify type of server and location
Master, Slave, Caching, or Forwarding
Server setup:
Install – bind, bind-utils, bind-chroot [jail application], caching-
nameserver [RHEL - install for cache server function], system-
config-bind
Network interface configuration:
Define & apply static IP address to interface
Modify /etc/sysconfig/network-scripts/ifcfg-ethX; PEERDNS=no
Modify /etc/host; place host name to IP address of resources for DNS
lookups [optional]
Modify /etc/resolv.conf; insert at beginning of file nameserver 127.0.0.1
Security considerations
Chroot / Jail application due to ever changing & challenging security issues
# yum install bind-chroot /var/named/chroot/etc/named.conf
Copy dependent binaries & libraries into chroot directory and manage links
Edit /etc/sysconfig/named directory and change it to /var/named/chroot
Modify /etc/sysconfig/named file and set ROOTDIR shell variable to
/var/named/chroot, e.g., ROOTDIR=“/var/named/chroot”
Test - do inode comparison
# ls /var/named/chroot/var/named
# ls –ldi /var/named/chroot/var/named
# ls –ldi /var/named
# service named start
# ls –ldi /var/named/chroot/var/named [should now reflect the
/var/named inode]
9/3/2011 Cyber Defense Security Presentation 22](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-22-2048.jpg)
![DNS Server – Install, Setup, & Administration (3 of 7)
Define, Discuss, Demonstrate, & Do
More security considerations http://www.puschitz.com/SecuringLinux.shtml
Modify / edit Firewall & SELinux settings: allow TCP & UDP port 53
Secure transaction exchange:
TSIGs signatures – hashed key exchange to support secure record exchange / replication
Time synchronization is critical –if TSIG exchange fails check time
Split Horizon server / Proxy Server place in DMZ; internal versus external name
resolution can support two different query types, not recommended
Logs /var/log/messages [assume DNS chroot]
# mk /var/named/chroot/var/log
# chmod 744 /var/named/chroot/var/log/bind
# chown named /var/named/chroot/var/log/bind
# ls –ld /var/named/chroot/var/log/bind
NTP Time services must be properly configured and secured
9/3/2011 Cyber Defense Security Presentation 23](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-23-2048.jpg)
![DNS Server – Install, Setup, & Administration (4 of 7)
Define, Discuss, Demonstrate, & Do
Server Service
Init & start – # chkconfig named on; service named start
Service modification – # service network [stop | start | restart ]
RHEL configuration test - # service named configtest
Documentation –
http://www.zytrax.com/books/dns/
file:///usr/share/doc/bind-9.7.2/arm/Bv9ARM.html
Server configuration:
Edit/etc/named.conf
See /usr/share/doc/bind*/sample/ for example named configuration
files
RHEL and Fedora have distinctions [see page 786 for details]
Determine type/role of DNS server(s) per topology design or
requirements Master, Slave, or Caching
Modify settings
Create Zones: root domains, local global domains, & reverse lookup
domain
Configure security – exchange methods & keys
Populate domains with appropriate static records, e.g., name
server (NS), mail server (MX), host records (A/AAAA), services
records (IP and service port specific), reverse loop up record
(PTR) etc.
Restart services
Zones information located in /var/named
9/3/2011 Cyber Defense Security Presentation 24](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-24-2048.jpg)
![DNS: Server – Install, Setup, & Administration (5 of 7)
Define, Discuss, Demonstrate, & Do
Only common references below, e.g., change below files system locations to jailed DNS file
locations
Caching-Only Server yum install –y caching-nameserver
# cp /etc/named.caching-nameserver.conf /etc/named.conf
Slave zone files # ls /var/named/slaves
Manually pull Master file to Slave # dig –t axfr zone_name.com @servername
RHEL6 /var/named not writable zone modifications /var/named/dynamic and then update
/etc/named.conf
Local System Security Settings
ACL
Define an ACL directive acl “local-net” { 127.0.0.1; 192.168.1.0/24; };
Place in named.conf allow-transfer { local-net; }; allow-query { local-net; };
User Access
DNS files owned by application “named user” and not root!
# chown root:named /etc/named/*; chown root:named /var/named/*;
IPTables – Firewall security settings – general settings provided
# iptables –I INPUT 5 –p udp –m udp –dport 53 –j ACCEPT
# iptables –I INPUT 5 –p tcp –m tcp –dport 53 –j ACCEPT
# iptables –I INPUT 5 –p udp –m udp –dport 953 –j ACCEPT [rndc key exchange]
# service iptables save; service iptables restart
SELinux
# getsebool –a | grep named_dis
# setsebool –P named_disable_trans=1
# chcon –t named_conf_t /etc/named.conf
# ls –Z /etc | grep named.conf
9/3/2011 Cyber Defense Security Presentation 25](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-25-2048.jpg)
![DNS: Server Key Exchange Setup (6 of 7)
Define, Discuss, Demonstrate, & Do [RHEL]
Only common references below, e.g., change below files system locations to jailed DNS file locations
Modify named.conf and insert include “/etc/rndc.key”;
Create key # dns-keygen
[Fedora $ /usr/sbin/dnssec-keygen –a hmac –md5 –b 512 –n HOST keyname ]
$ cat Kkeyname.+243+14321.private similar as below see page 803
Create key file # vi /etc/rndc.key
key “rndckey” {
algorithm hmac-md5;
secret
“aresrntynratbYjhjdslo863eWEDvOVCmdvfvb”; [not a real key]
};
Create config file # rndc-confgen > /etc/rndc.conf
Edit /etc/rndc.conf paste in key content listed above
Edit named.conf & add
controls {
inet 127.0.0.1 port 953
allow {127.0.0.1; } keys { “rndc.key”; };
};
include “etc/rndc.key
Change ownership of files
# chown root:named /etc/rndc.*
# chmod 400 /etc/rndc.*; service named configtest; service named restart; rndc status
# chcon –t named_conf_t rndc.key rndc.conf;
Logs /var/log/bind; /var/log/messages
9/3/2011 Cyber Defense Security Presentation 26](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-26-2048.jpg)
![DNS Server – Helpful Hints for Setup & Administration (1 of 4)
Define, Discuss, Demonstrate, & Do
GUI - system-config-network; system-config-network-tui CLI Configure Service & Status
CLI Query Resolver # service --status-all state of service
on system
$ dig fully_qualify_domain_hostname; dig –x
ip_address; dig –t MX # service service_name [stop | start |
fully_qualify_domain_hostname restart| status]
$ host ip_address; hostname; nslookup FQDN or # chkconfig service_name [on | off]
IP_ADD; ping FQDN or IP_ADD; whois domain_name # service service_name configtest
(lookup info for hostname or ip address) # netstat -tupl (internet services on a
CLI Configure Interface & Routes system); netstat –tup (active
$ ifconfig interface up|down connections to/from system); netstat -
Check out $ ethtool eth0 must be installed
tanp | grep LISTEN
Server: static configuration per node w/ host FQDN, host IP, Troubleshooting methodology: start
subnet mask, default gateway, & DNS server IP with local host remote host or service
$ ip Check local interface (hostname,
# ip addr add 1.2.3.4/24 brd + dev eth0 (add or delete IP & ifconfig, iwconfig, ping, netstat)
subnet mask) Check local gateway, route or shout?
# ip route add default via 1.2.3.254 (add or delete default (ping, route, traceroute)
gateway – change default to network address to create a static Check local services ACLs, firewall,
route)
proxy, DNS, file share, etc. (netstat, dig,
# ip link set dev eth0 up (bring interface up or down) hosts, nslookup)
# ip addr show; ip -s link; ip route show; hostname –i;
Check remote host services or resources
ip or route commands (ping, finger, jwhois, lynx, nmap, mtr,
# route add default gw 192.168.1.1 [destination address] eth0 browsers)
[interface on the same network as destination gateway
address] Key file locations: /sbin;
Edit related files: etc/sysconfig/network-scripts; /etc/sysconfig/network;
http://lartc.org/howto/lartc.rpdb.multiple-links.html /etc/sysconfig/network-scripts;
http://www.itsyourip.com/Linux/howto-add-a-persistent-
/etc/init.d/network “start, restart, or
static-route-in-redhat-enterprise-linux/ stop”
9/3/2011 Cyber Defense Security Presentation 28](https://image.slidesharecdn.com/dnshardeninglinuxos-13210988160215-phpapp01-111112055844-phpapp01/75/Dns-Hardening-Linux-Os-28-2048.jpg)