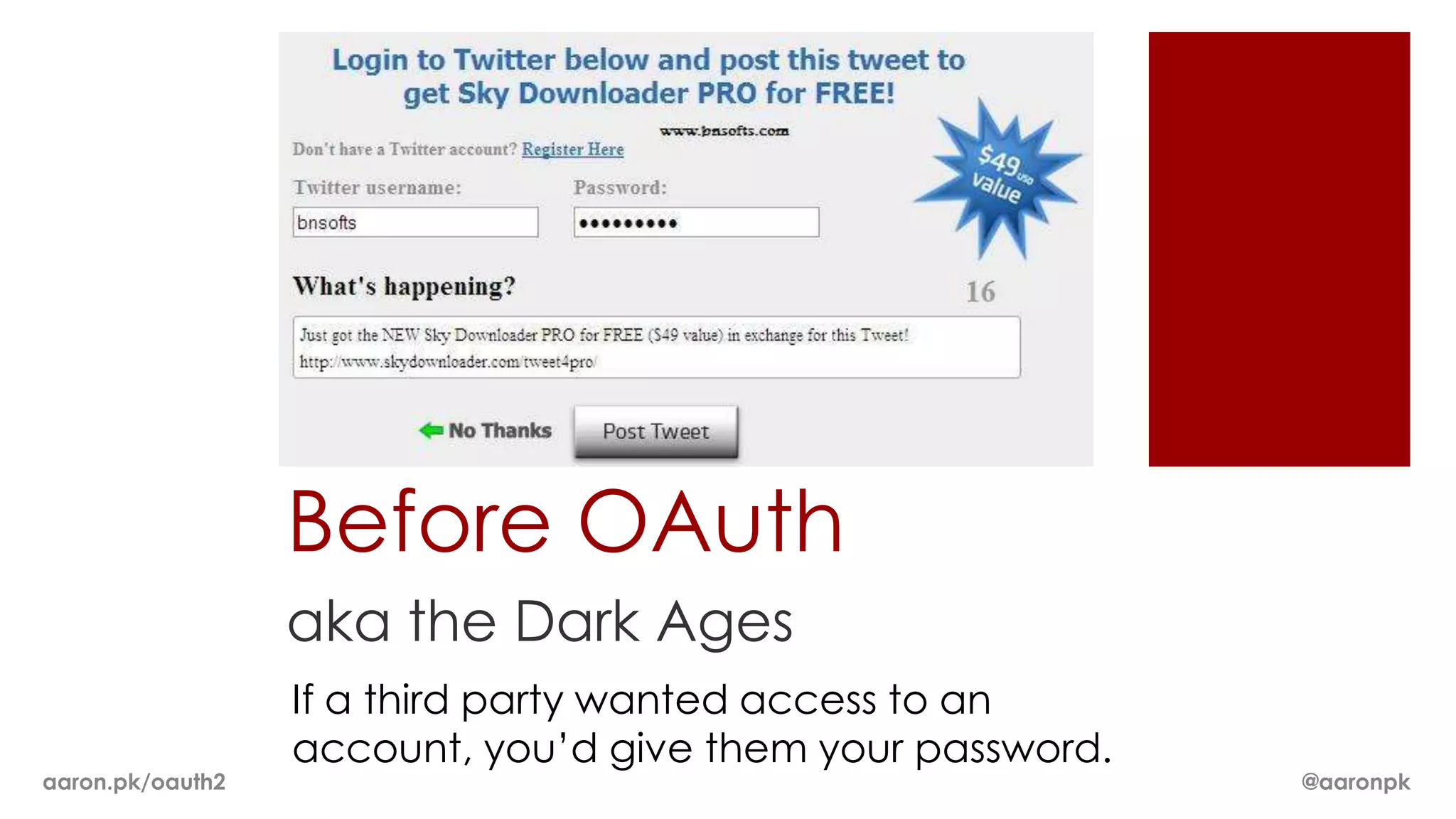
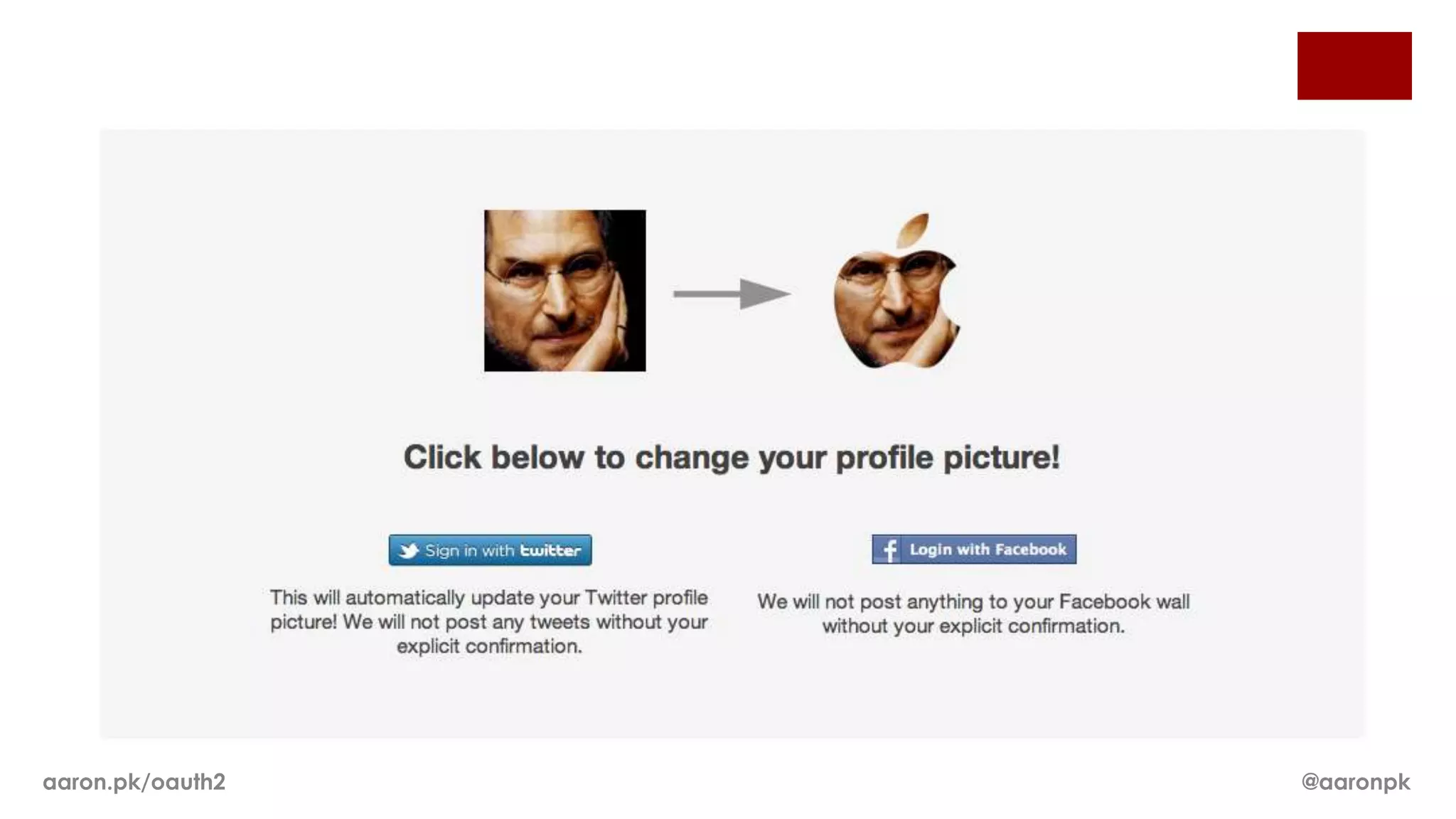
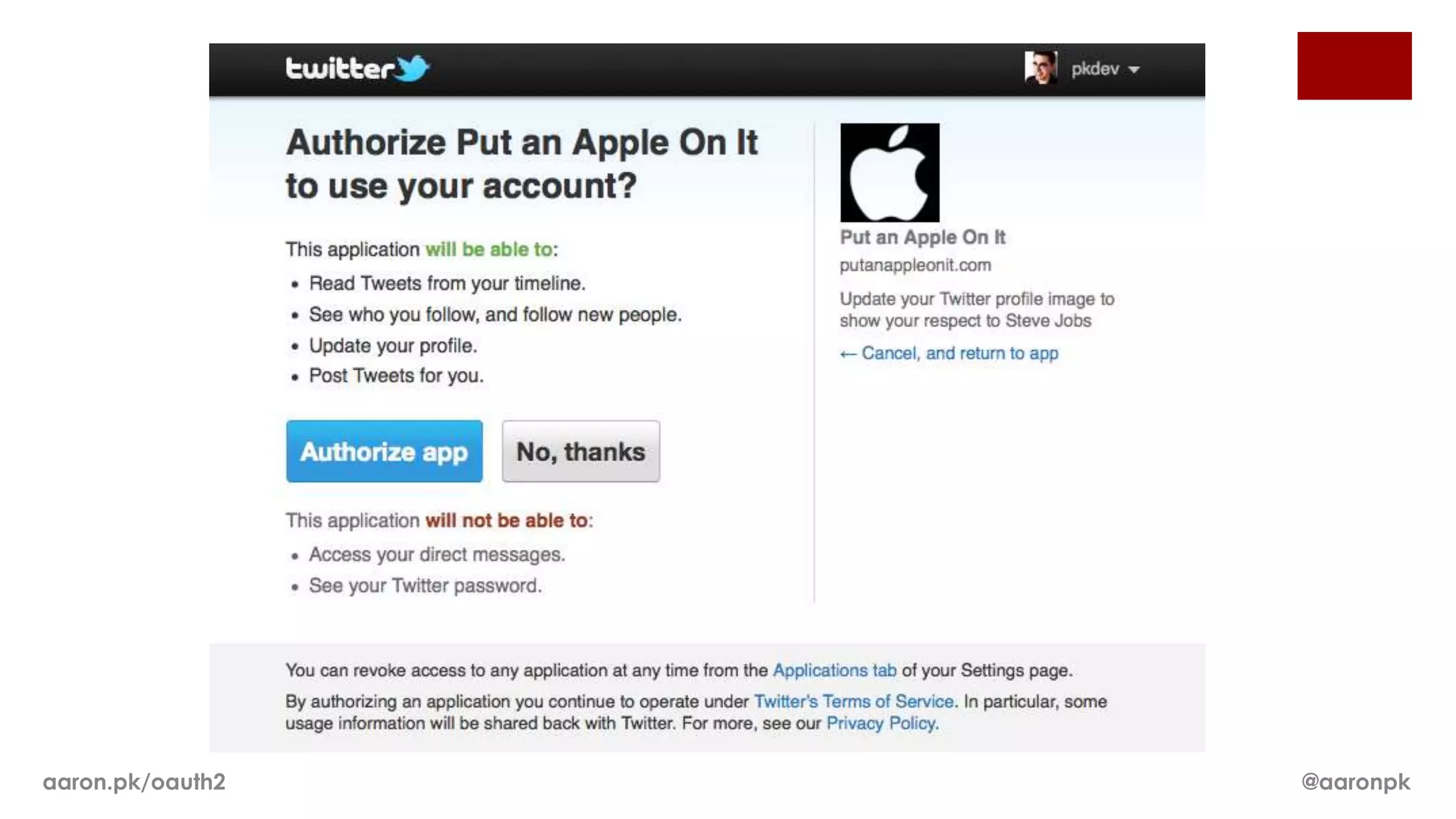
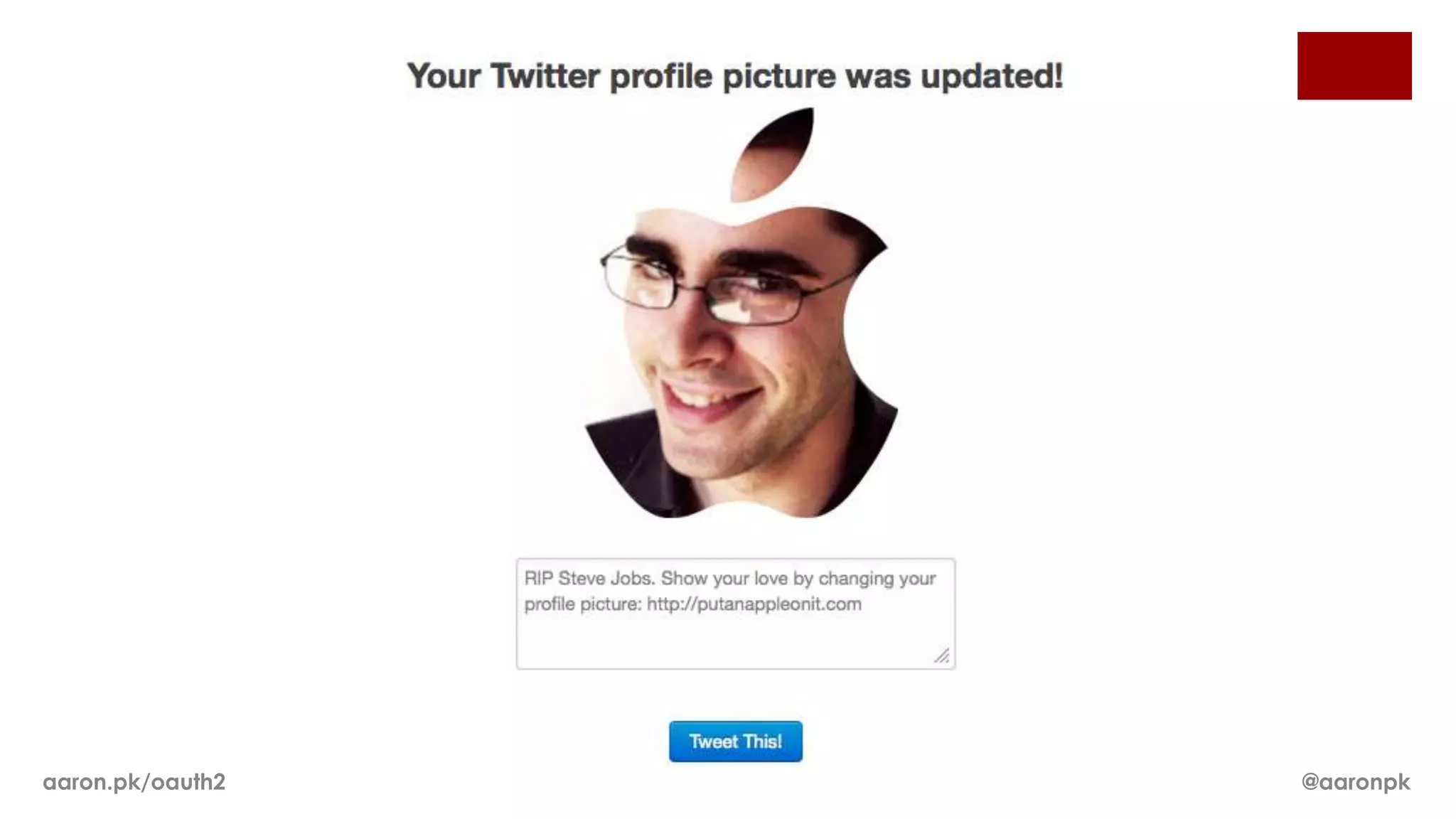
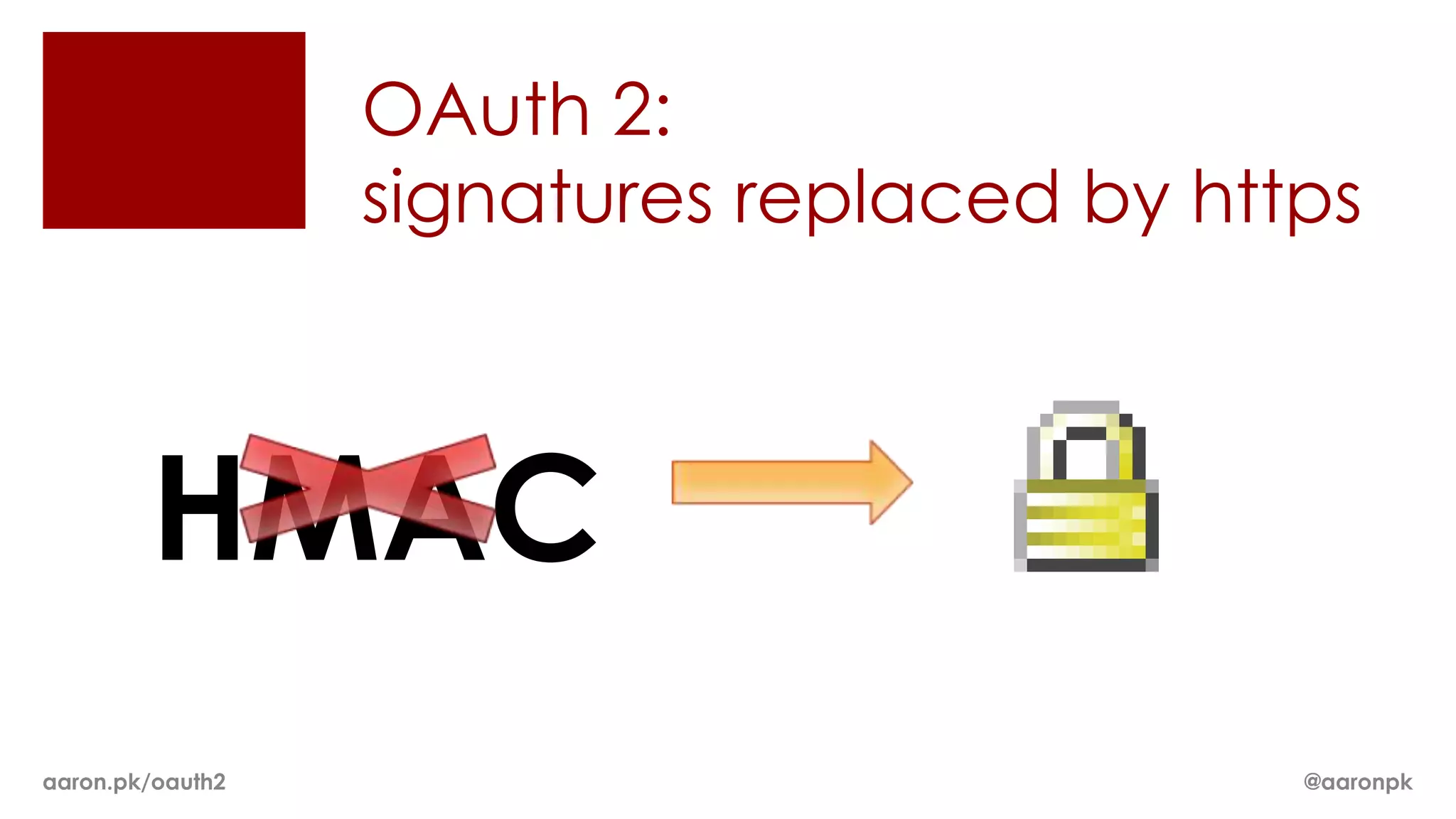
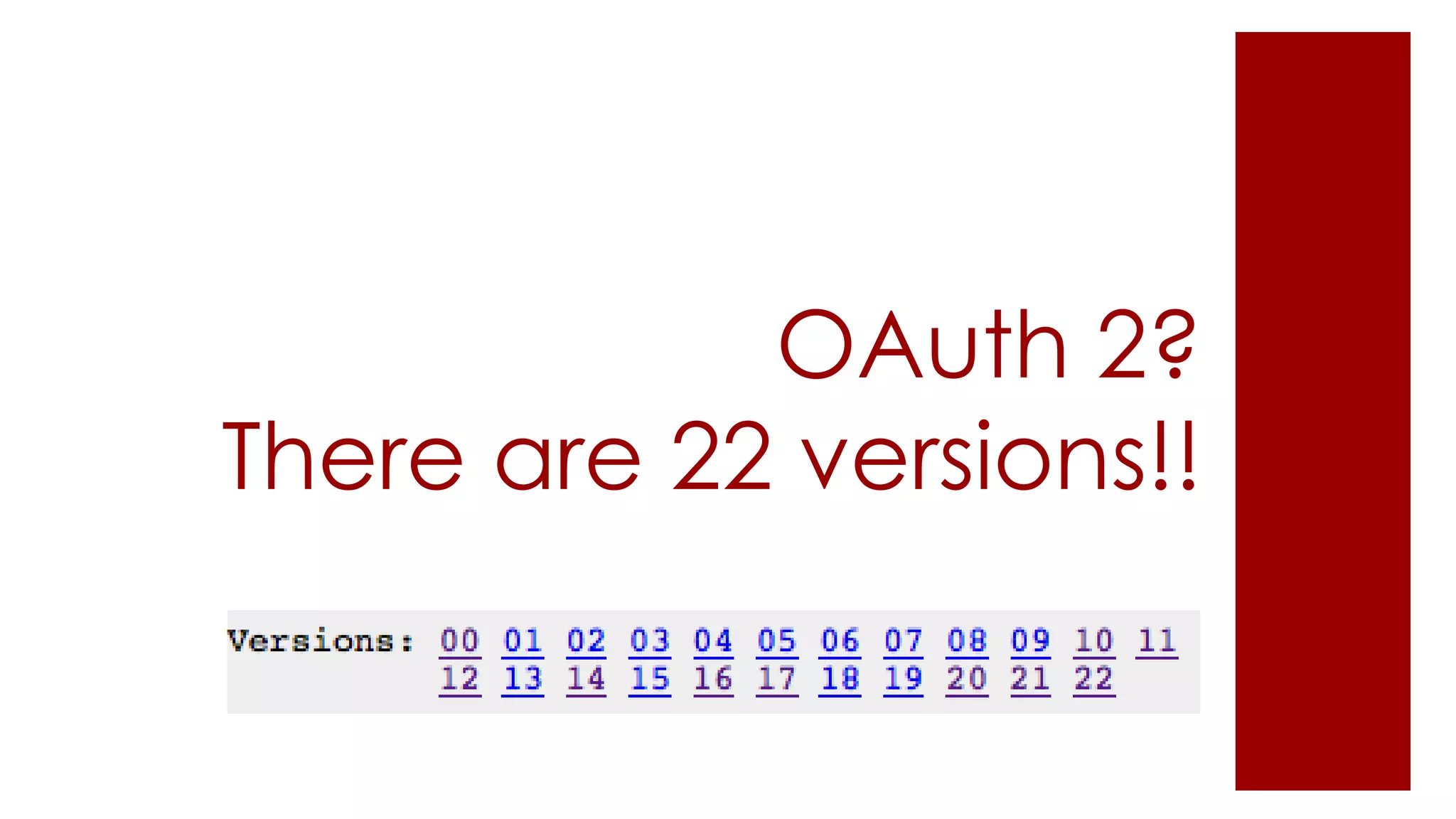
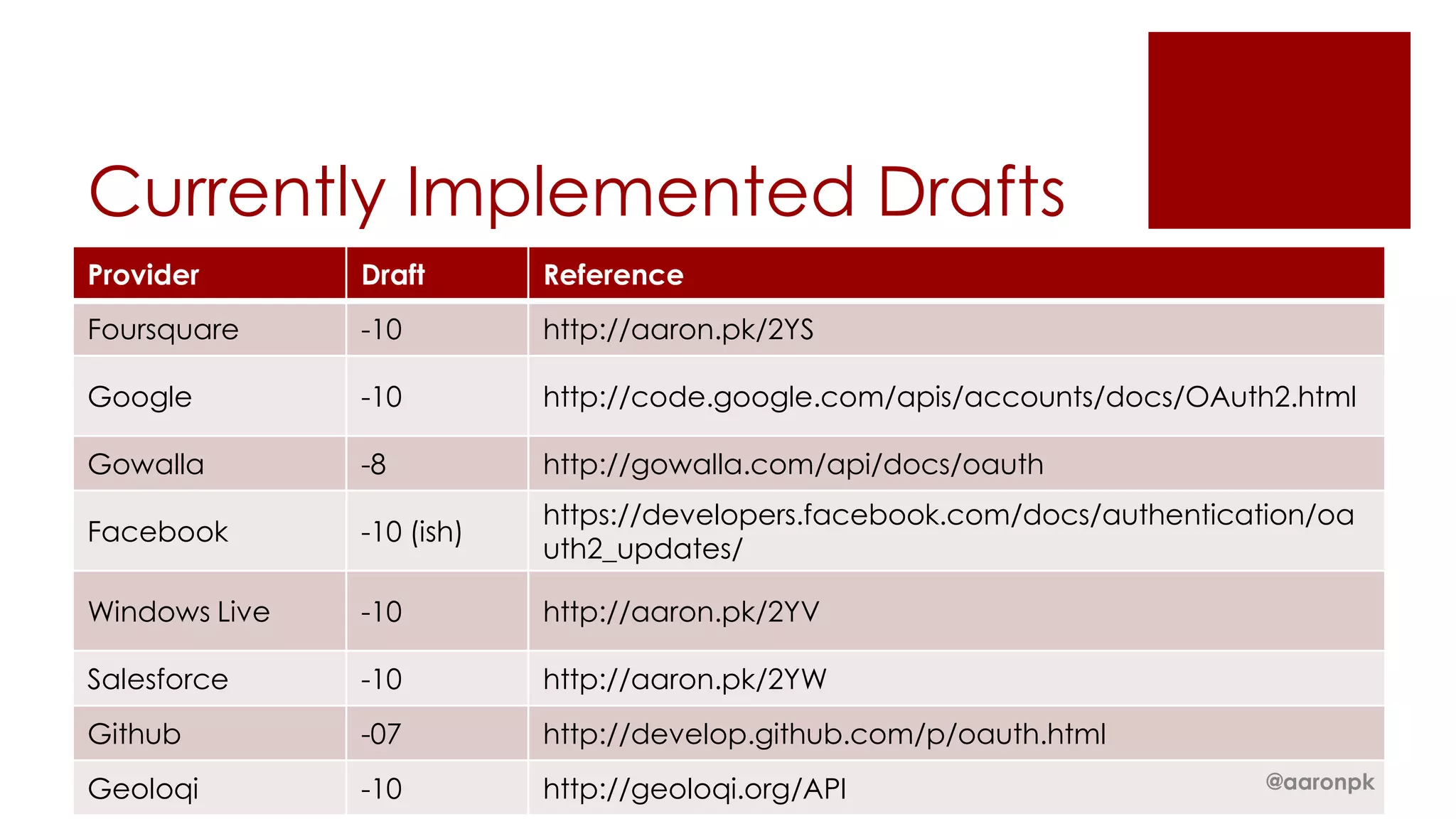
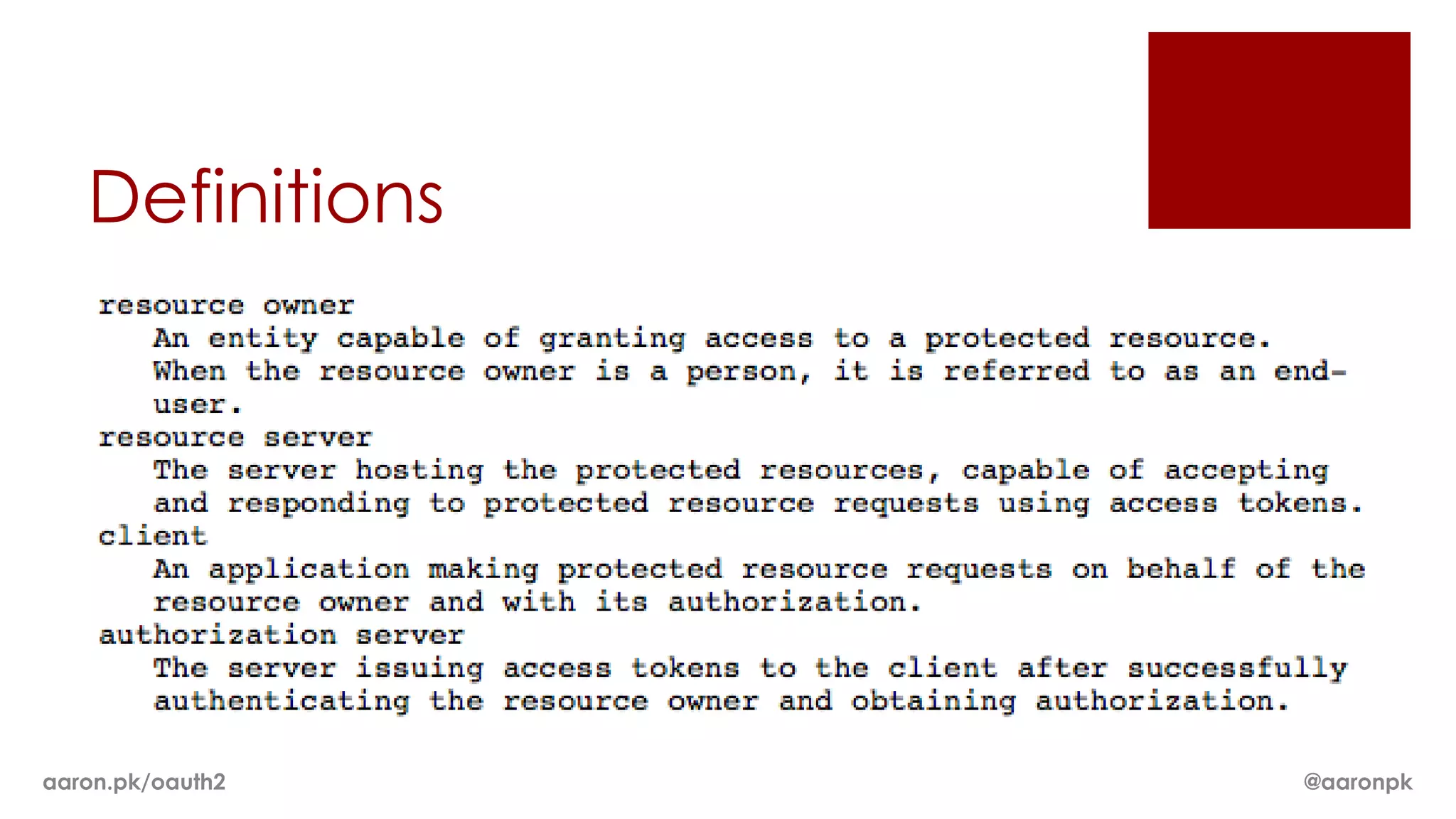
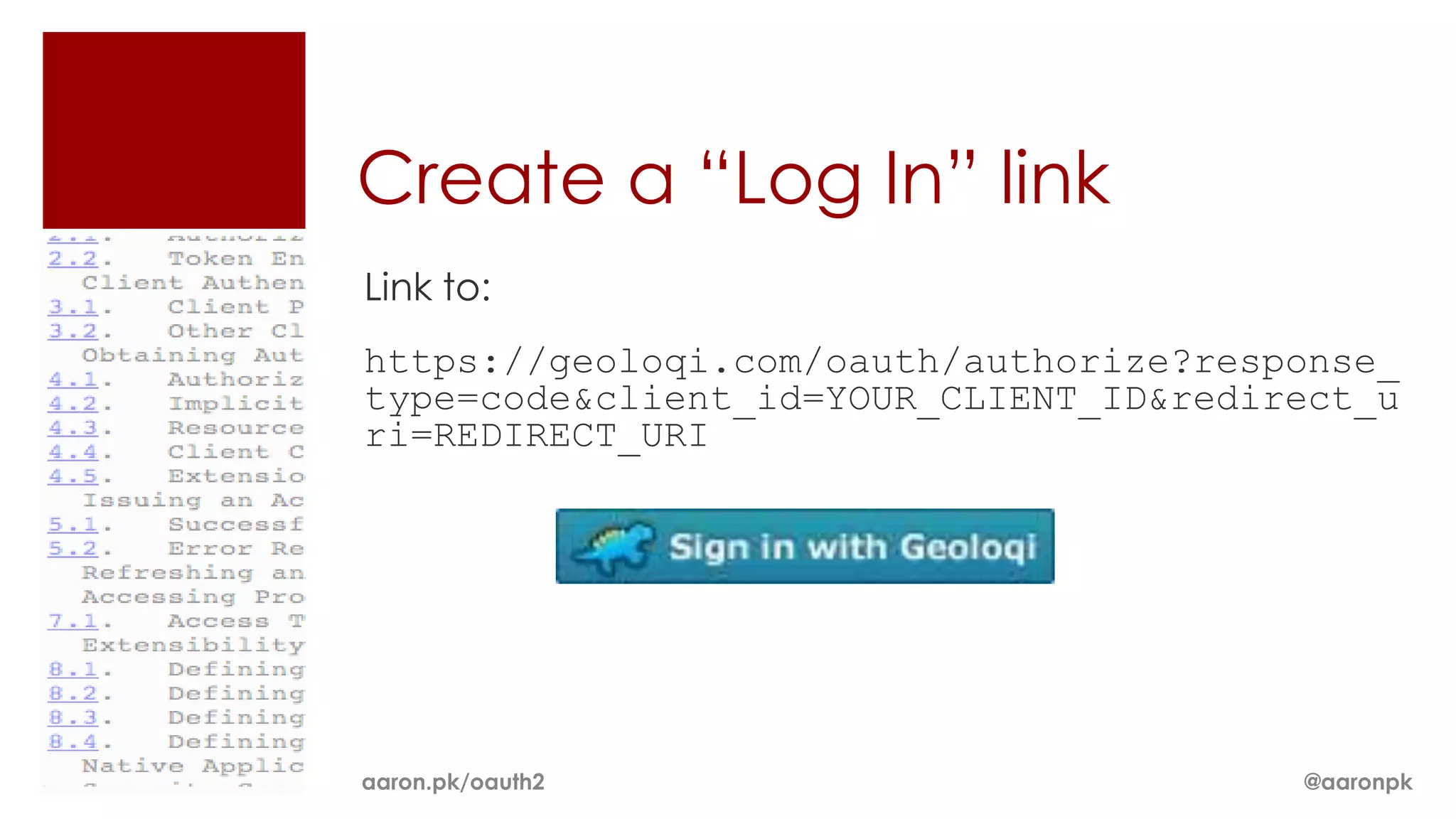
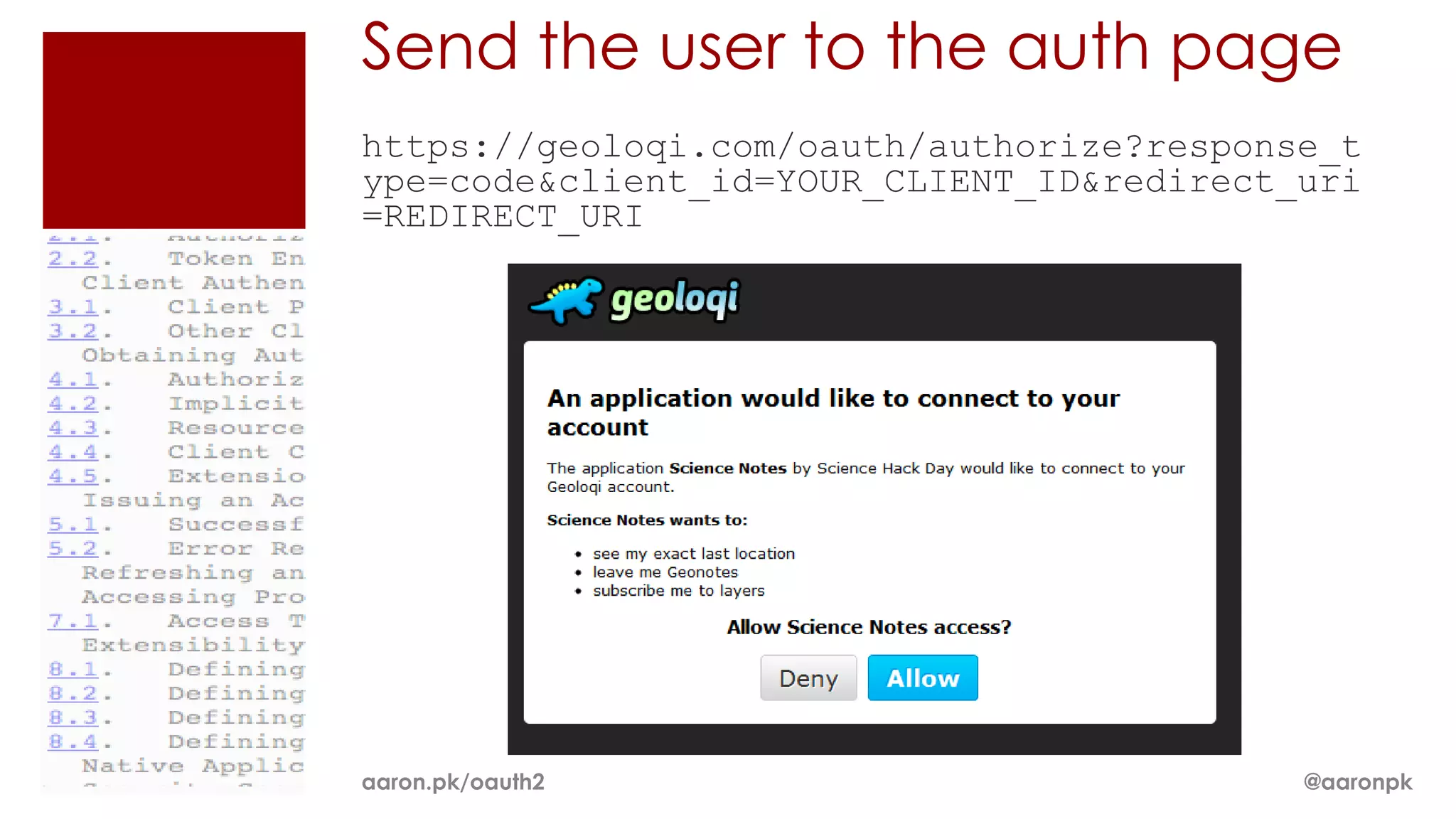
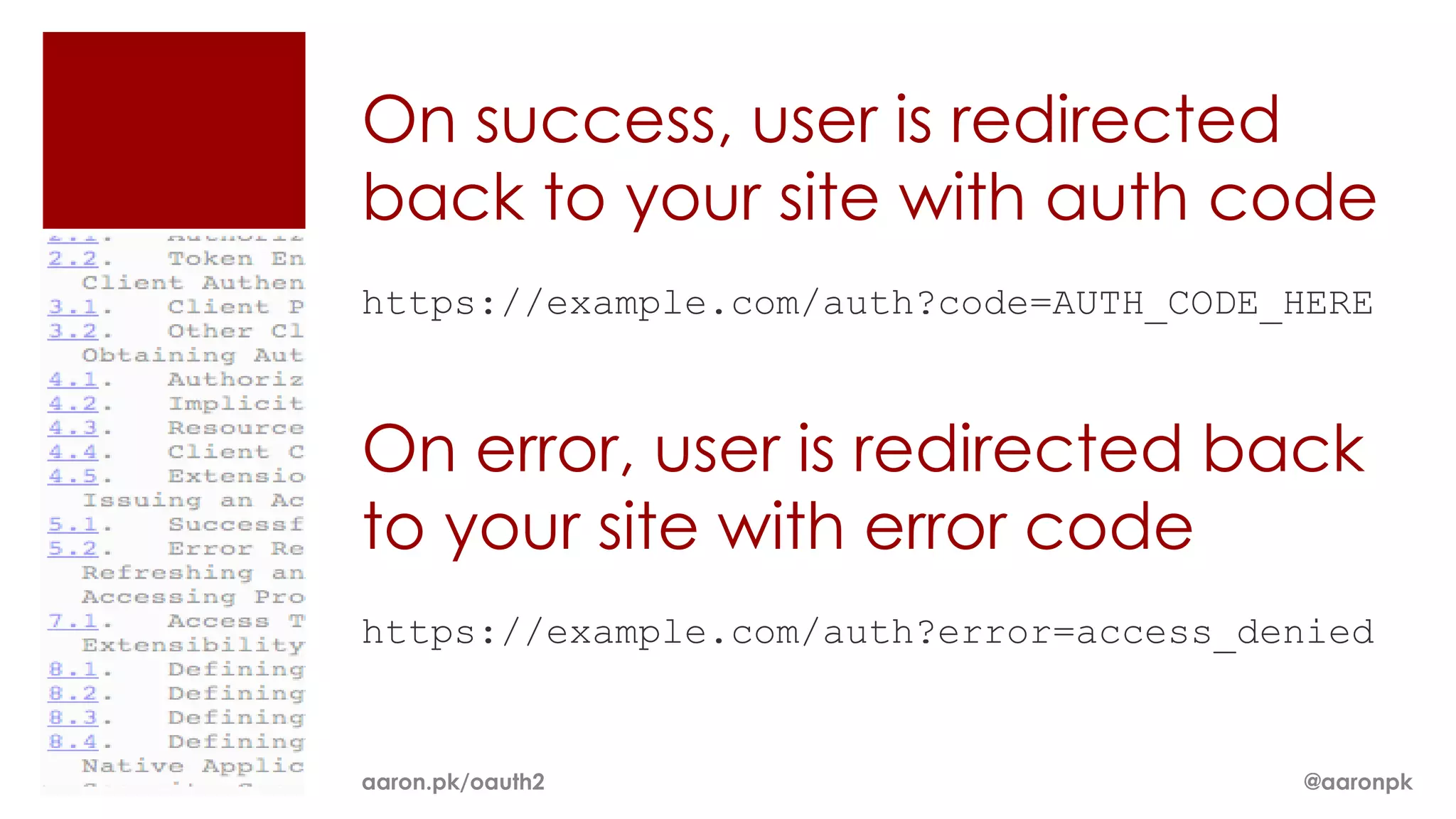
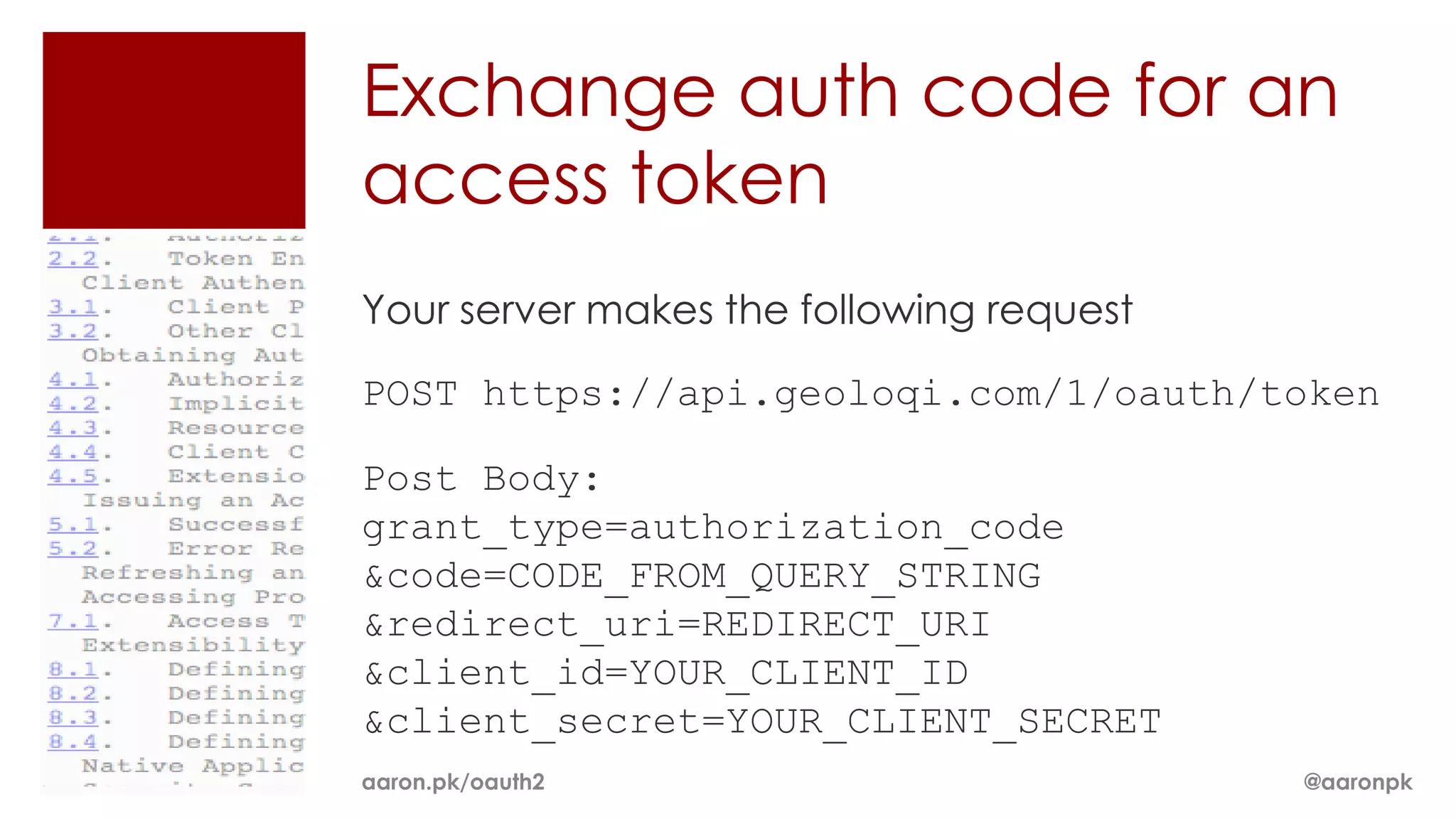
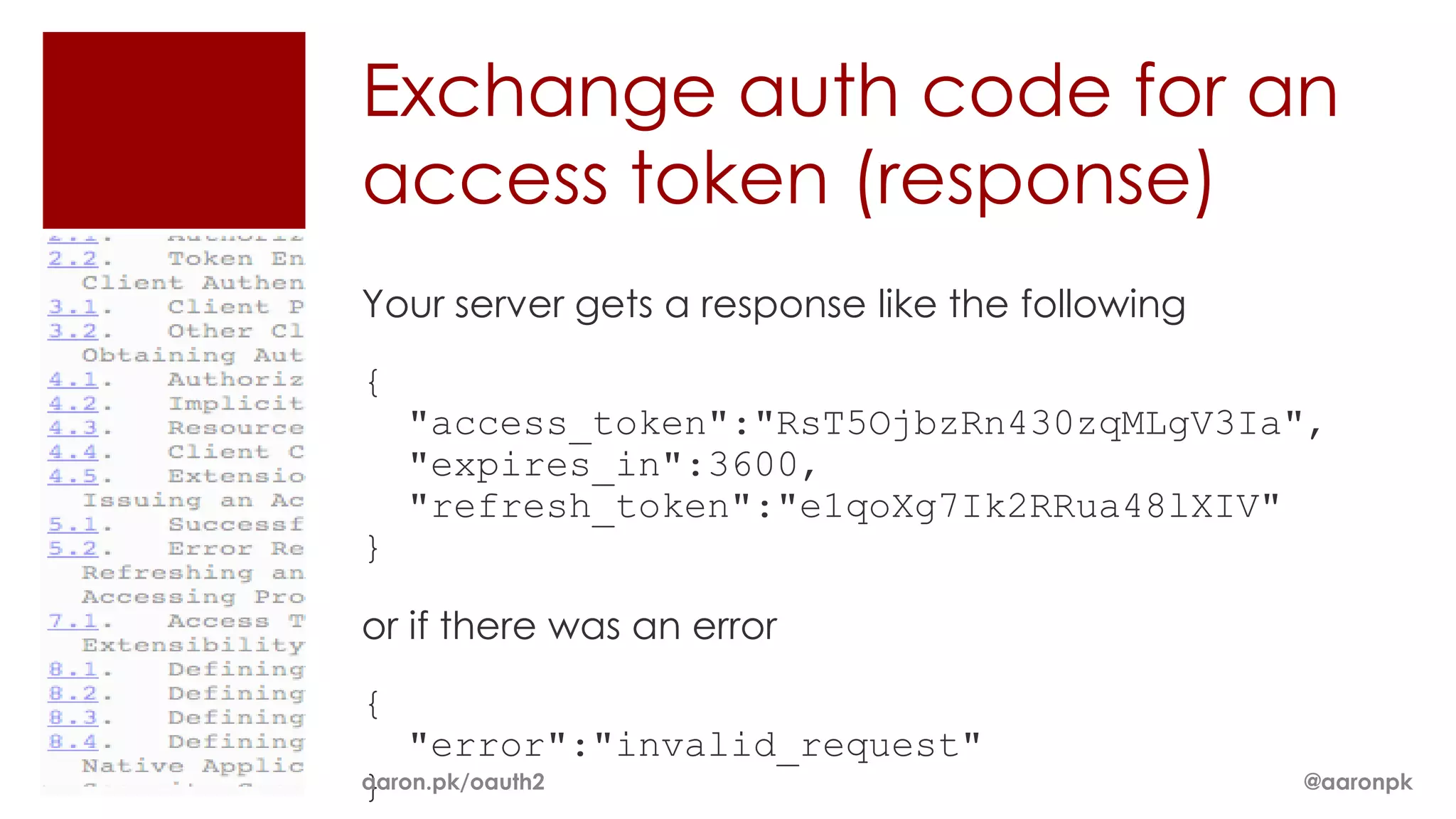
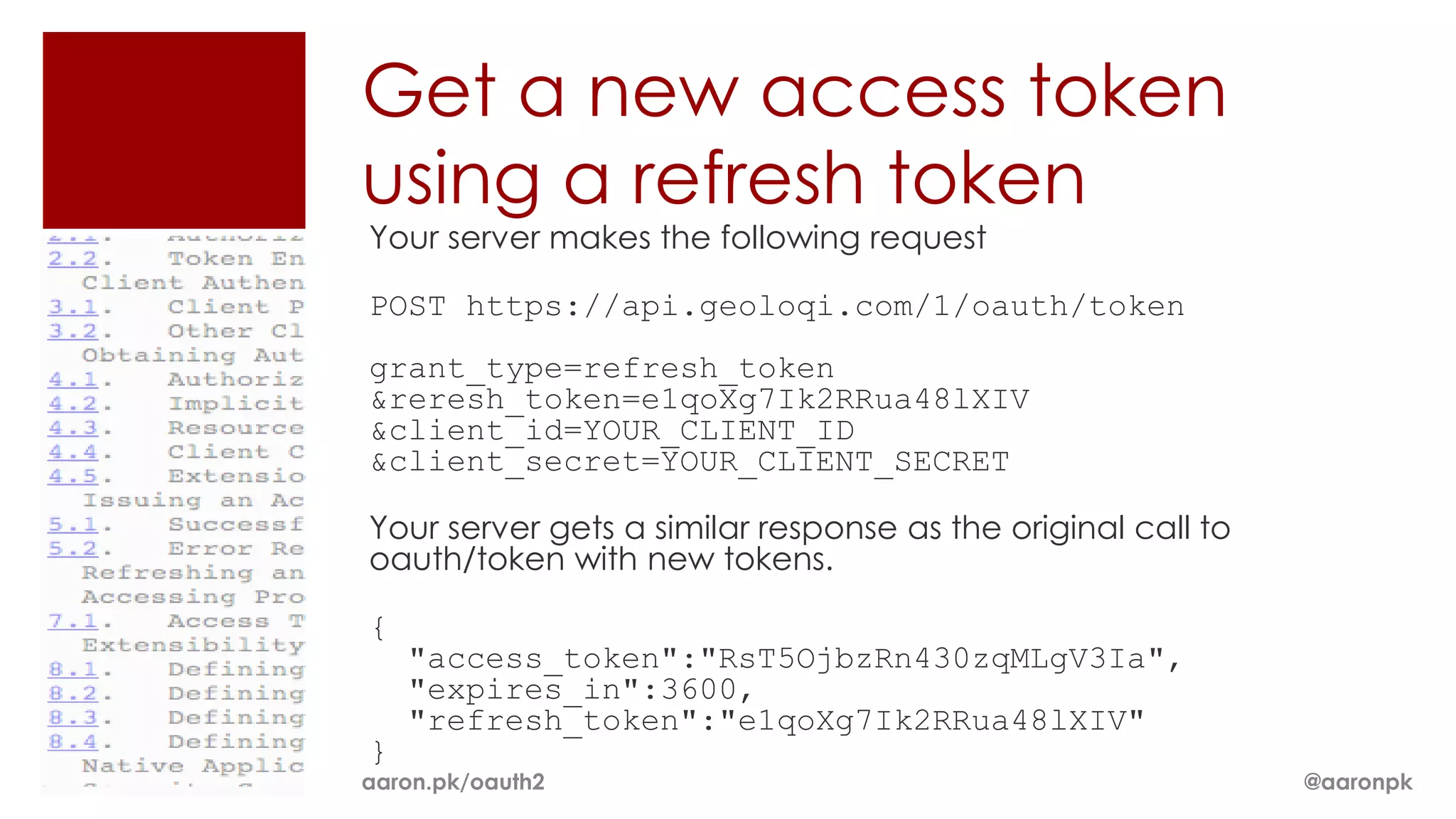
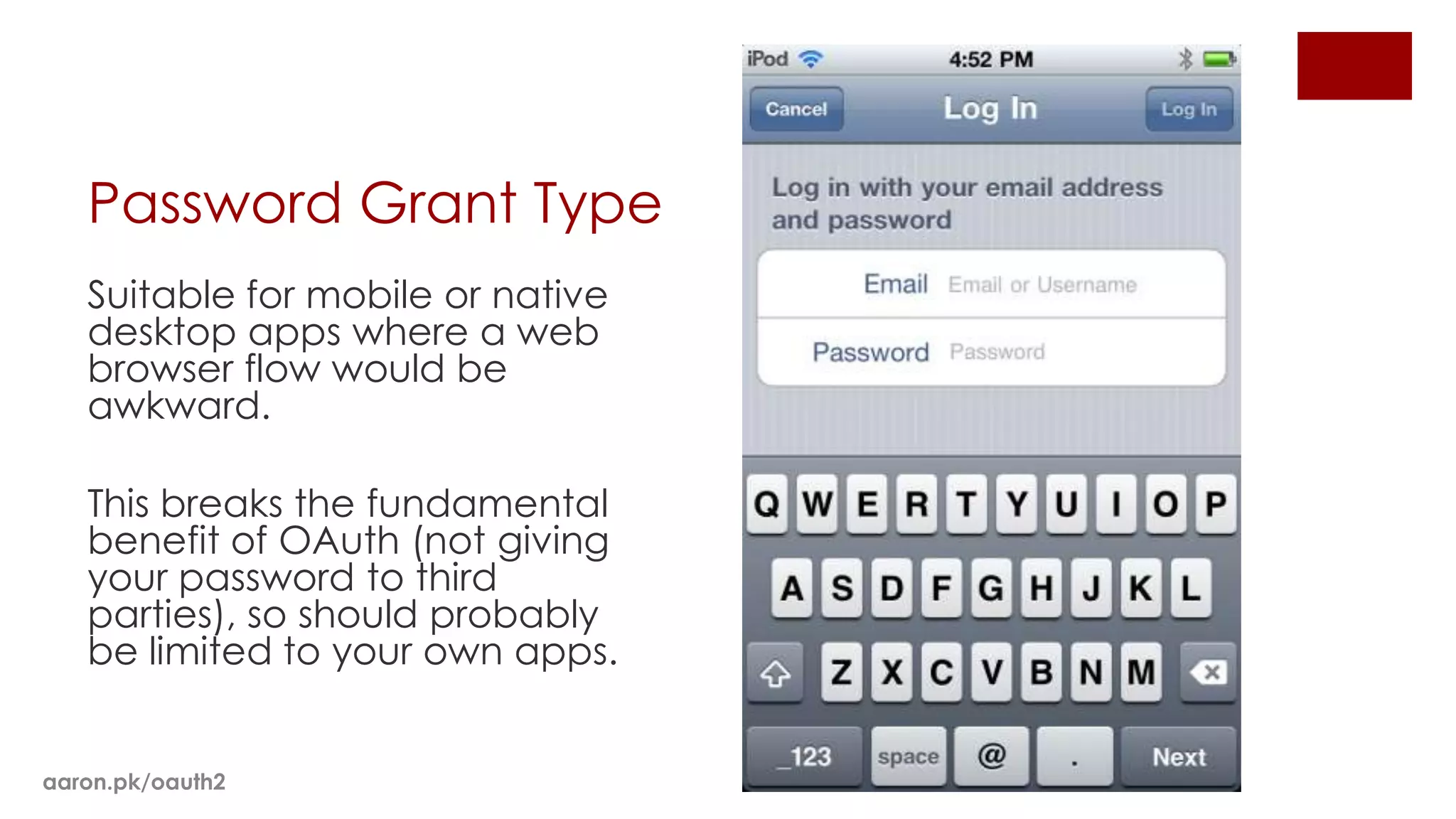
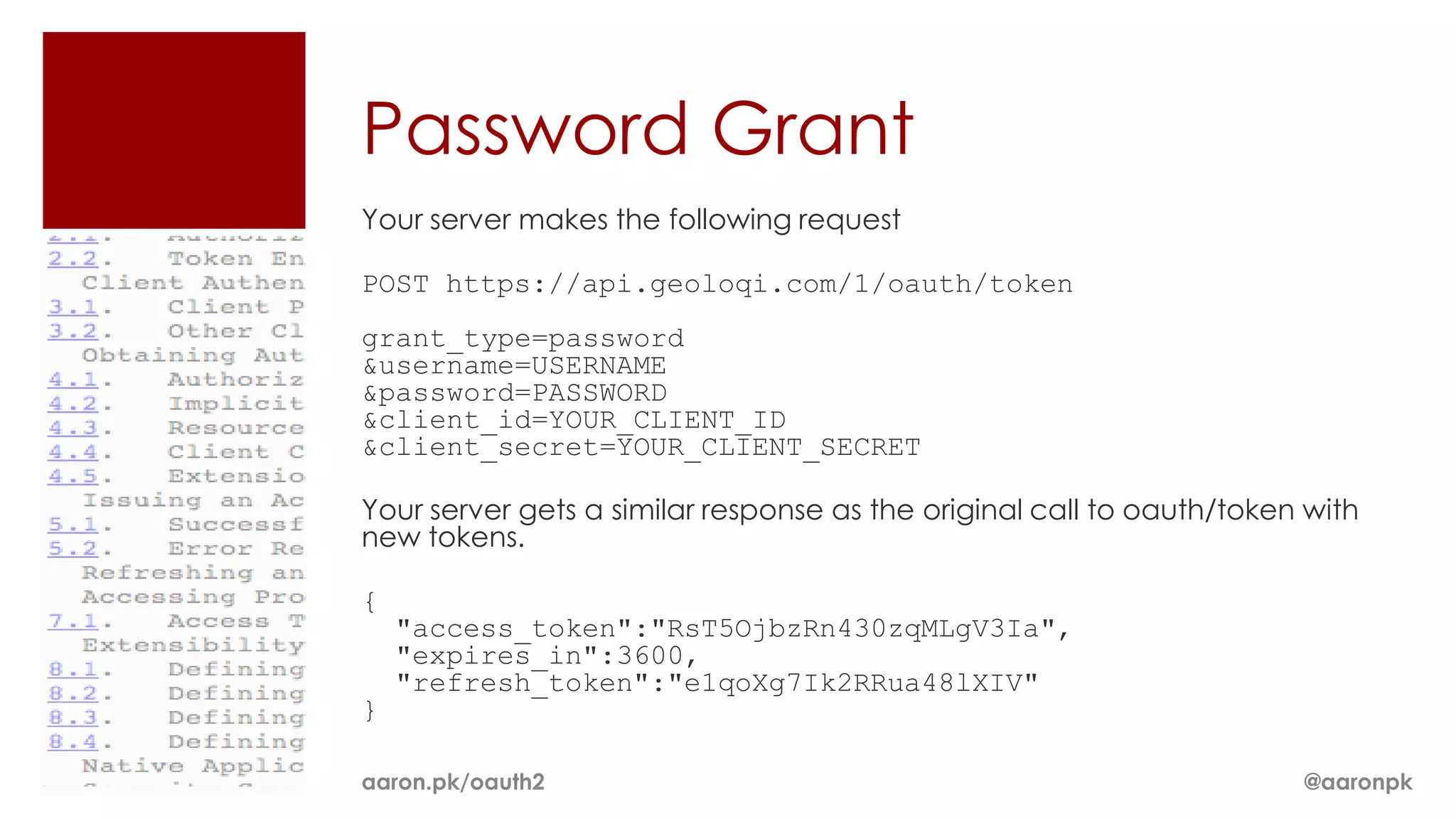
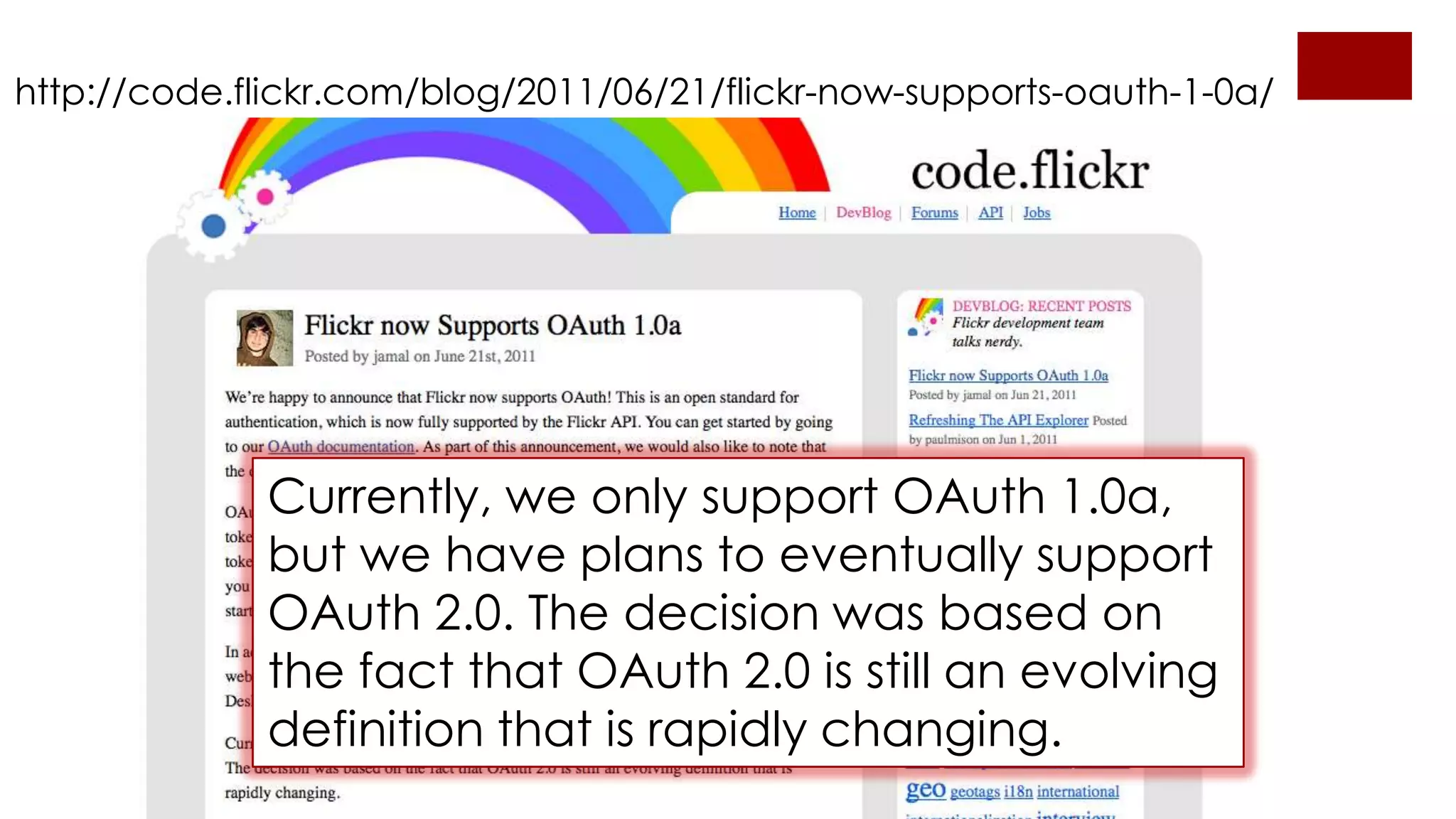
The document provides an overview of OAuth 2.0 and how it works. It describes how OAuth 1.0 had many different implementations by sites like Flickr, Google, and Facebook. OAuth 2.0 standardized the process and replaced signatures with HTTPS. It then outlines the key parts of OAuth 2.0, including authorization, accessing resources with an access token, refreshing expired tokens, and different authorization methods like authorization codes, passwords, and implicit grants. It concludes with security recommendations for clients using bearer tokens.