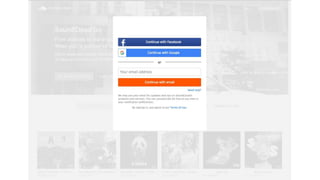
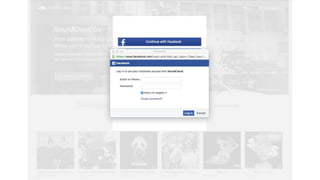
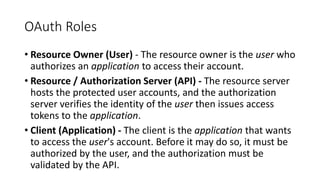
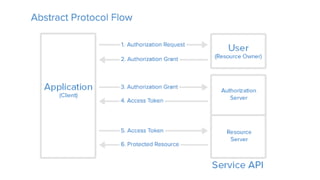
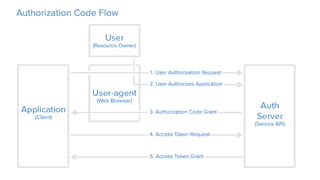
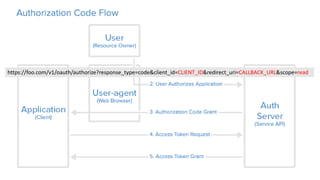
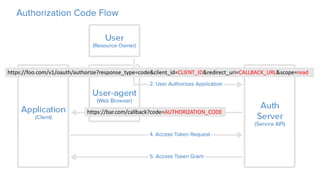
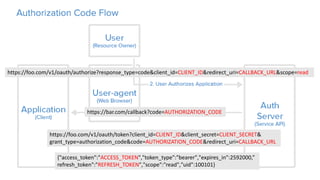
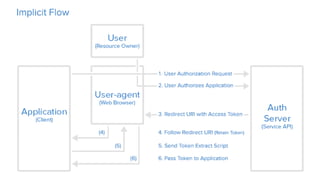
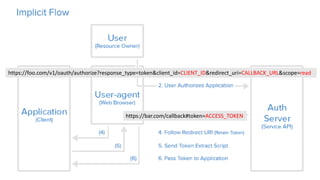
OAuth is an open standard for authorization that allows users to share private resources stored on one server with another server. It provides a process for users to authorize third-party access to their server resources without sharing credentials. OAuth has gone through several versions to address security issues and limitations of previous versions. OAuth involves resource owners, clients, and an authorization server, and defines common flows for authorization like authorization code flow and refresh token flow.