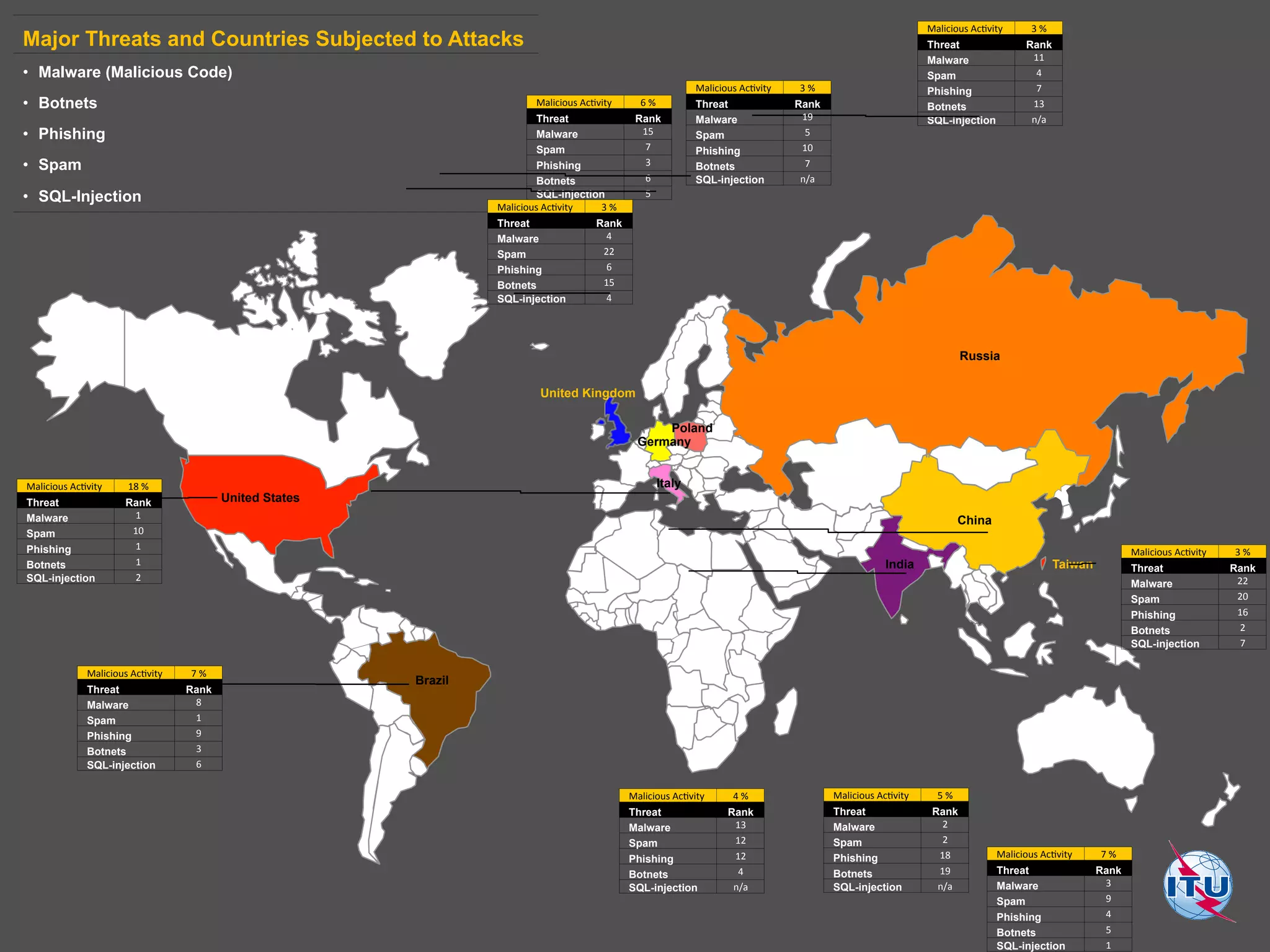
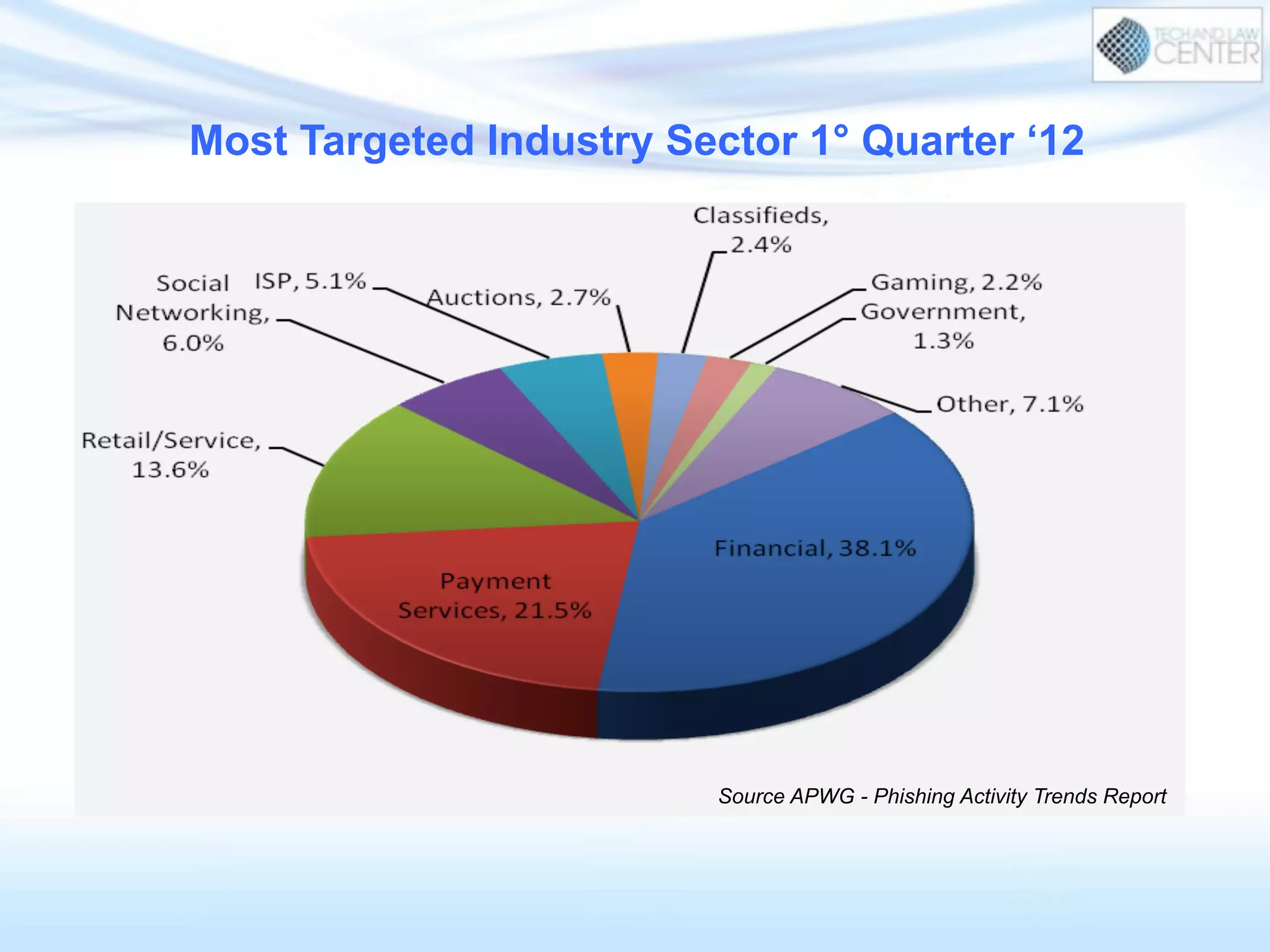
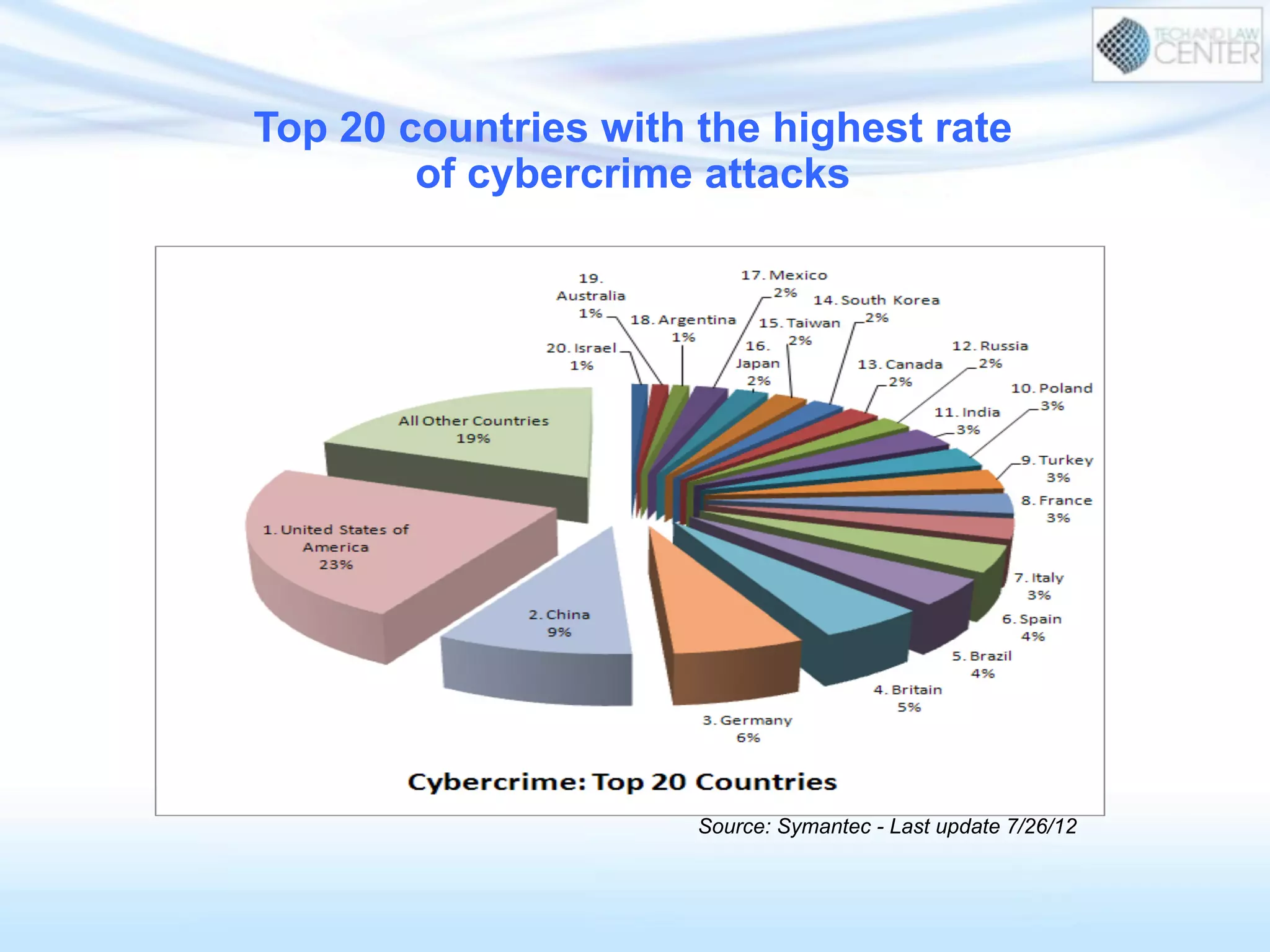
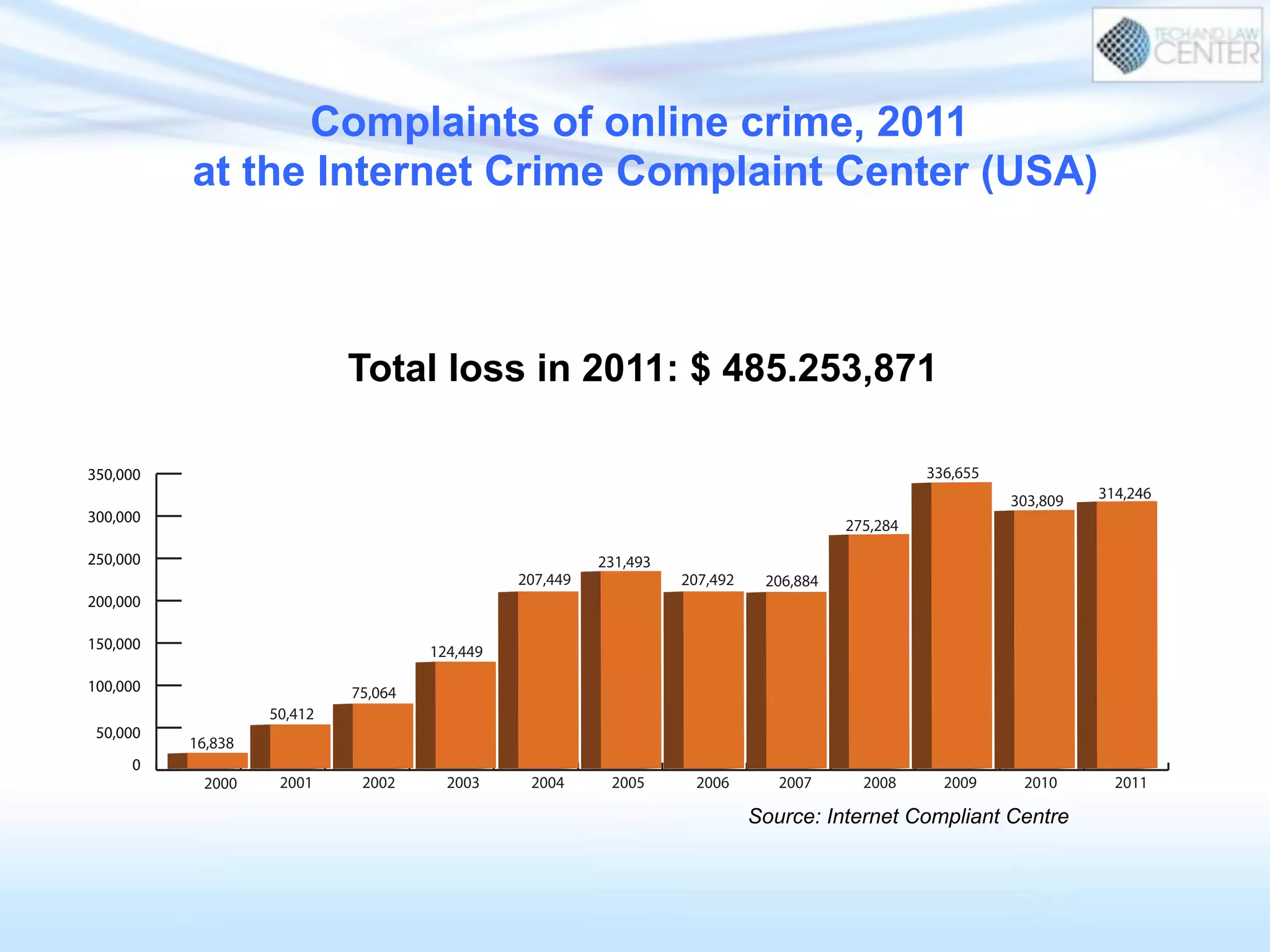
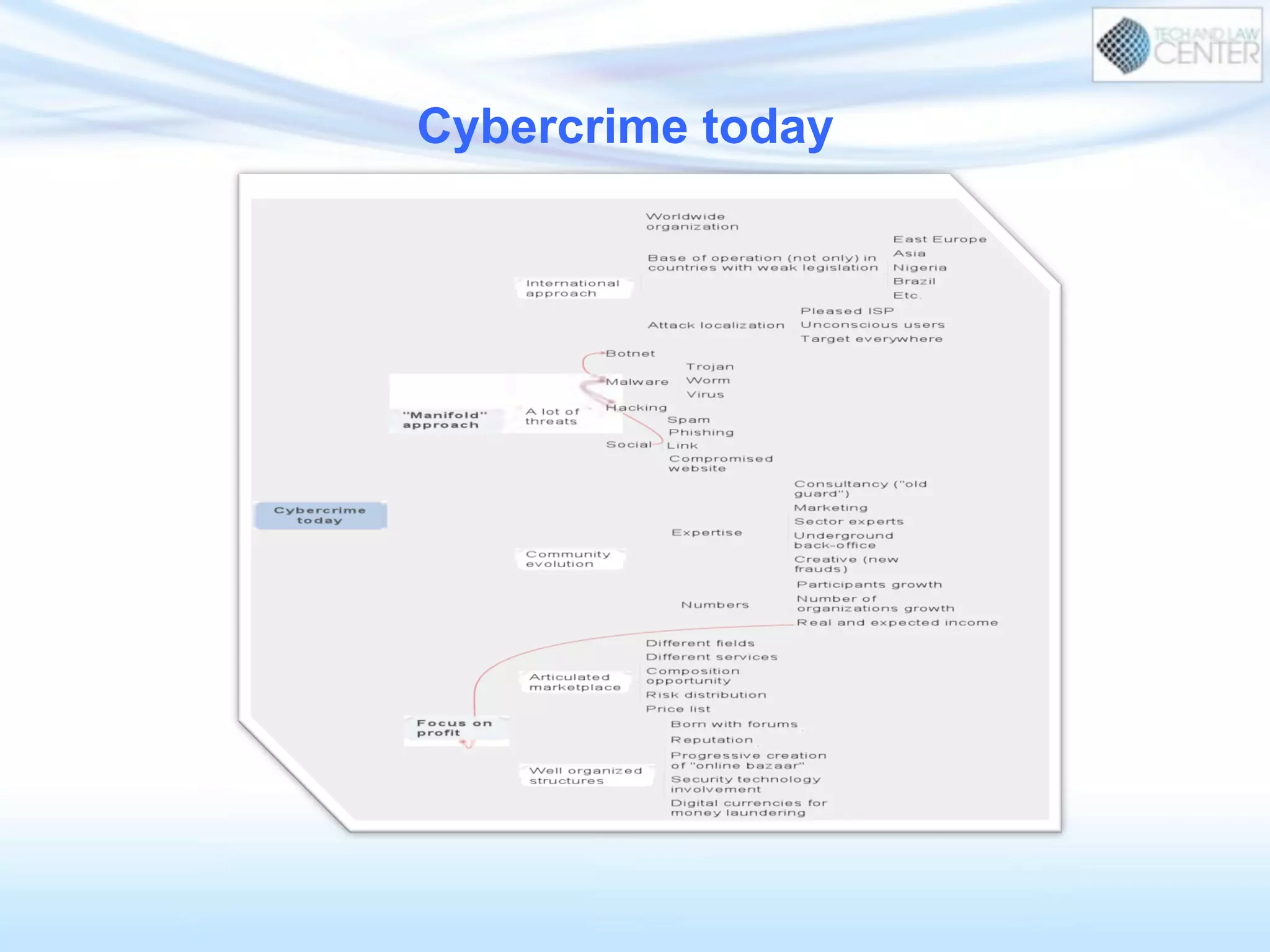
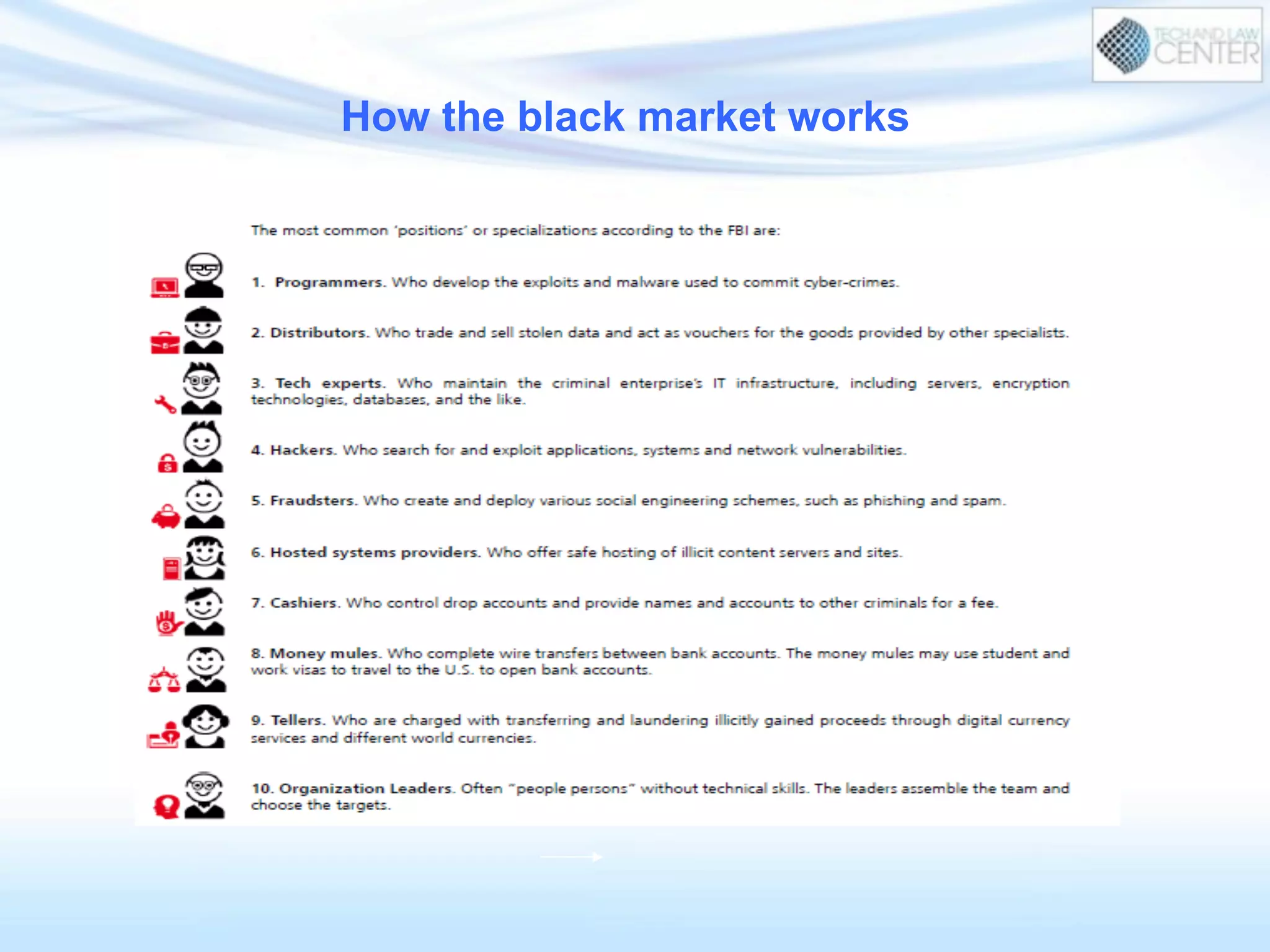
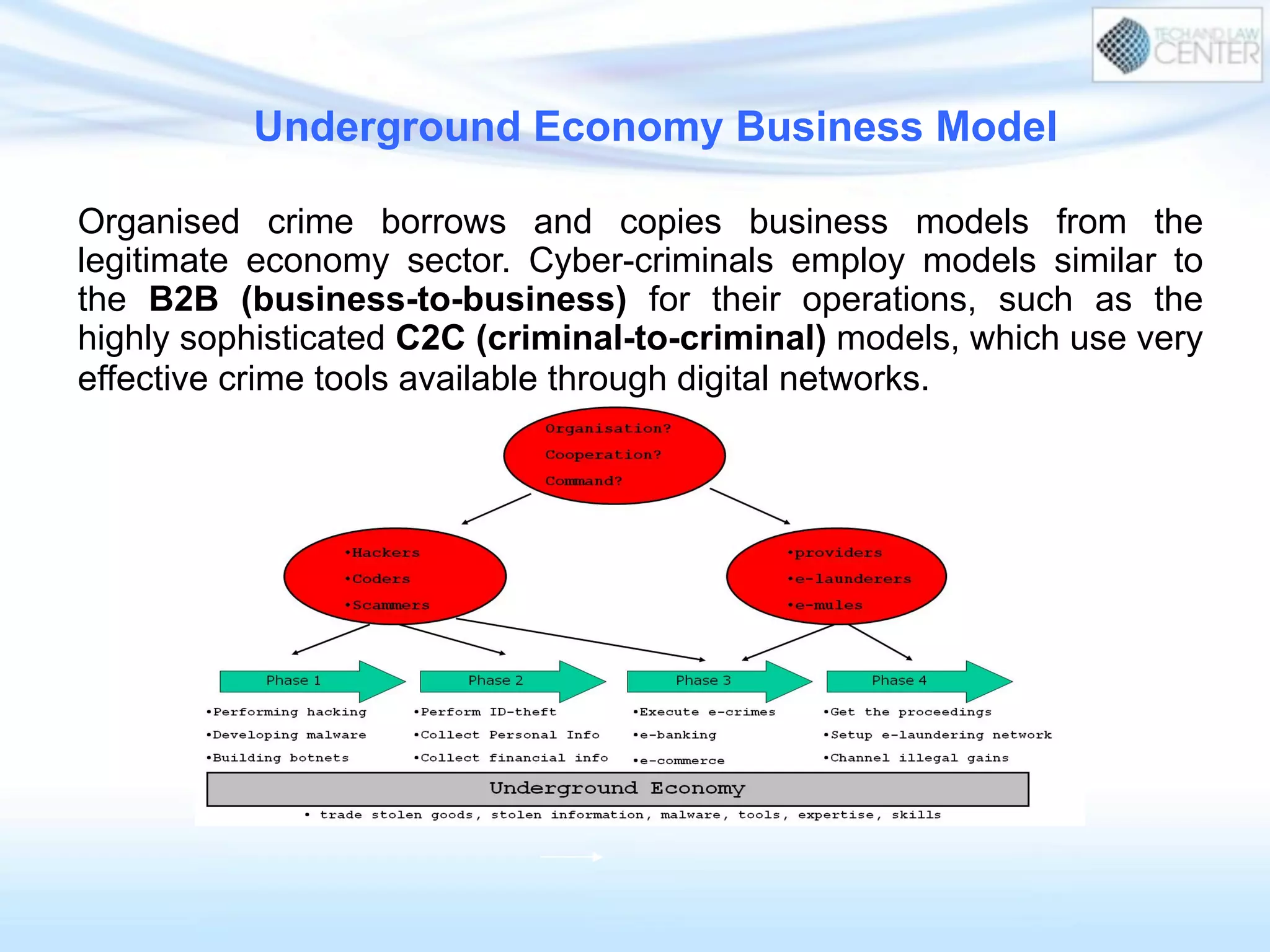
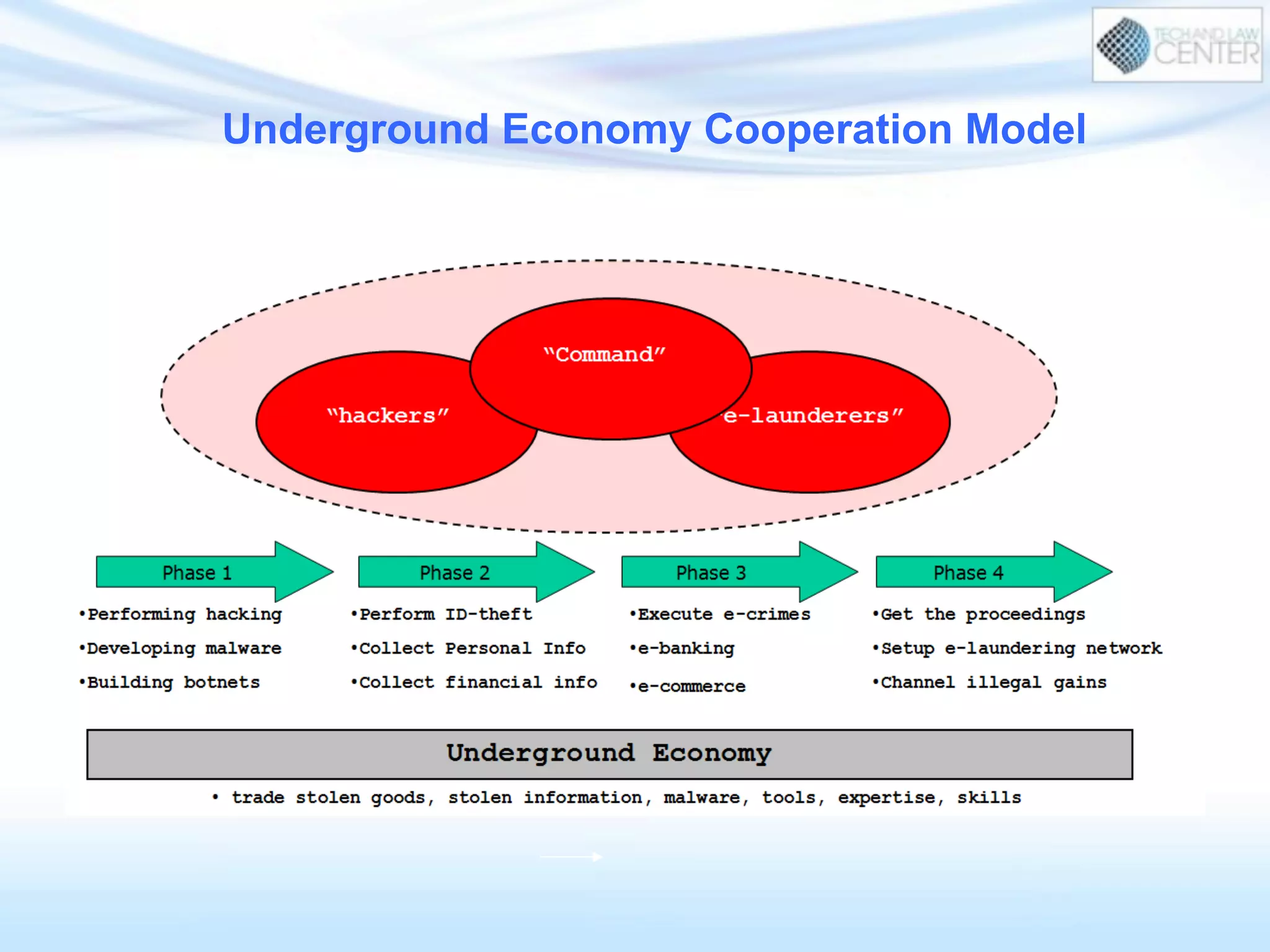
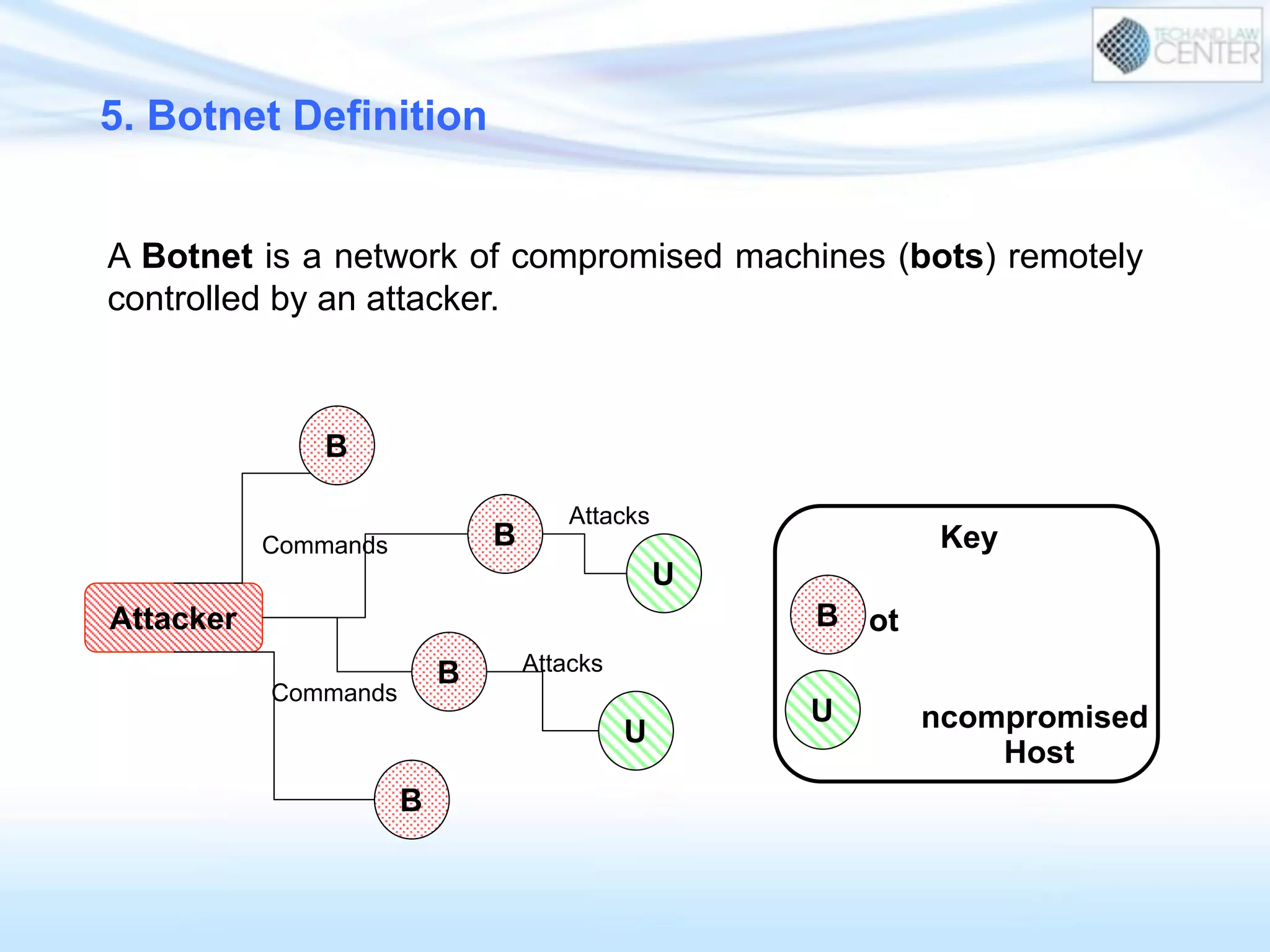
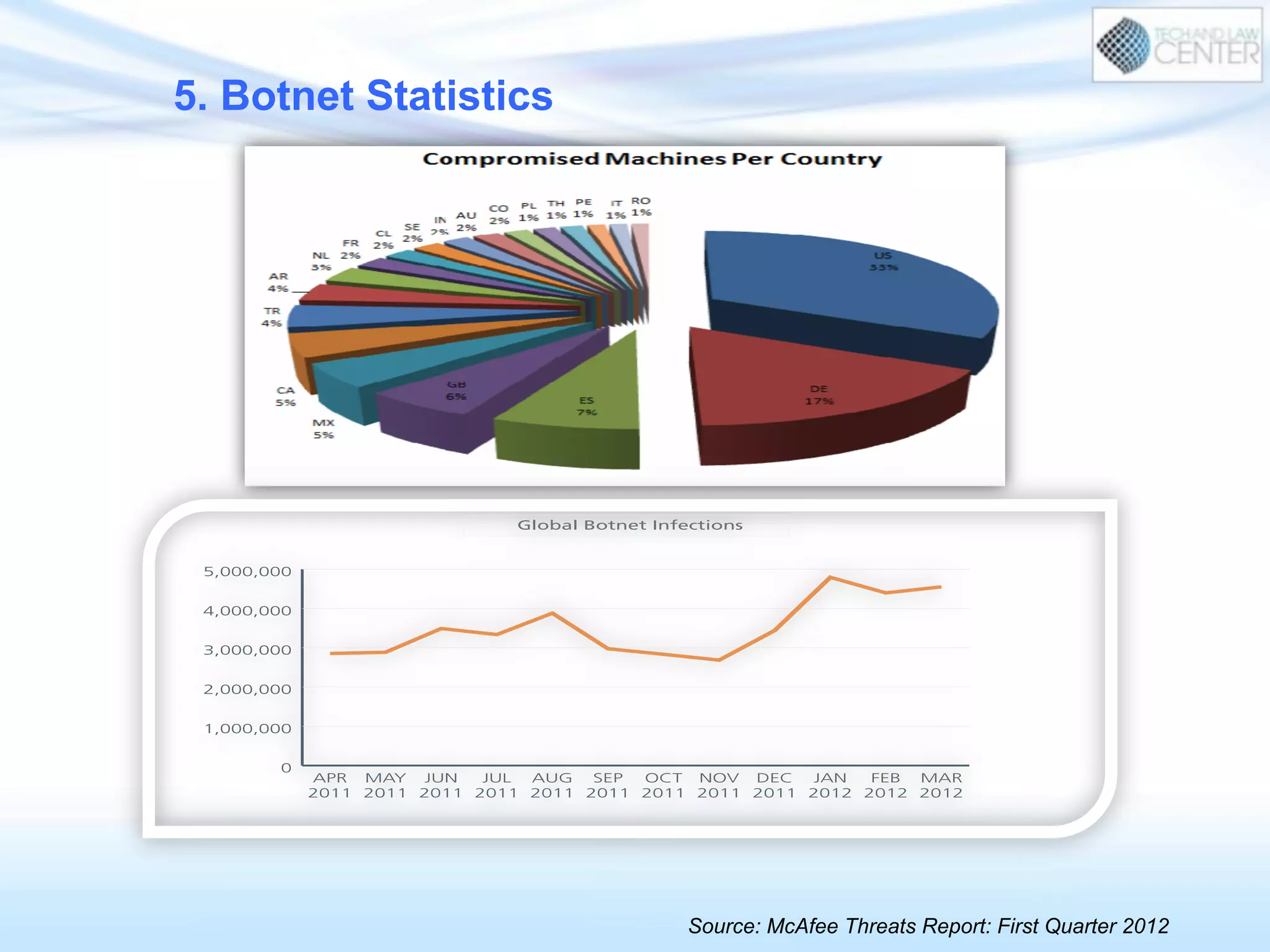
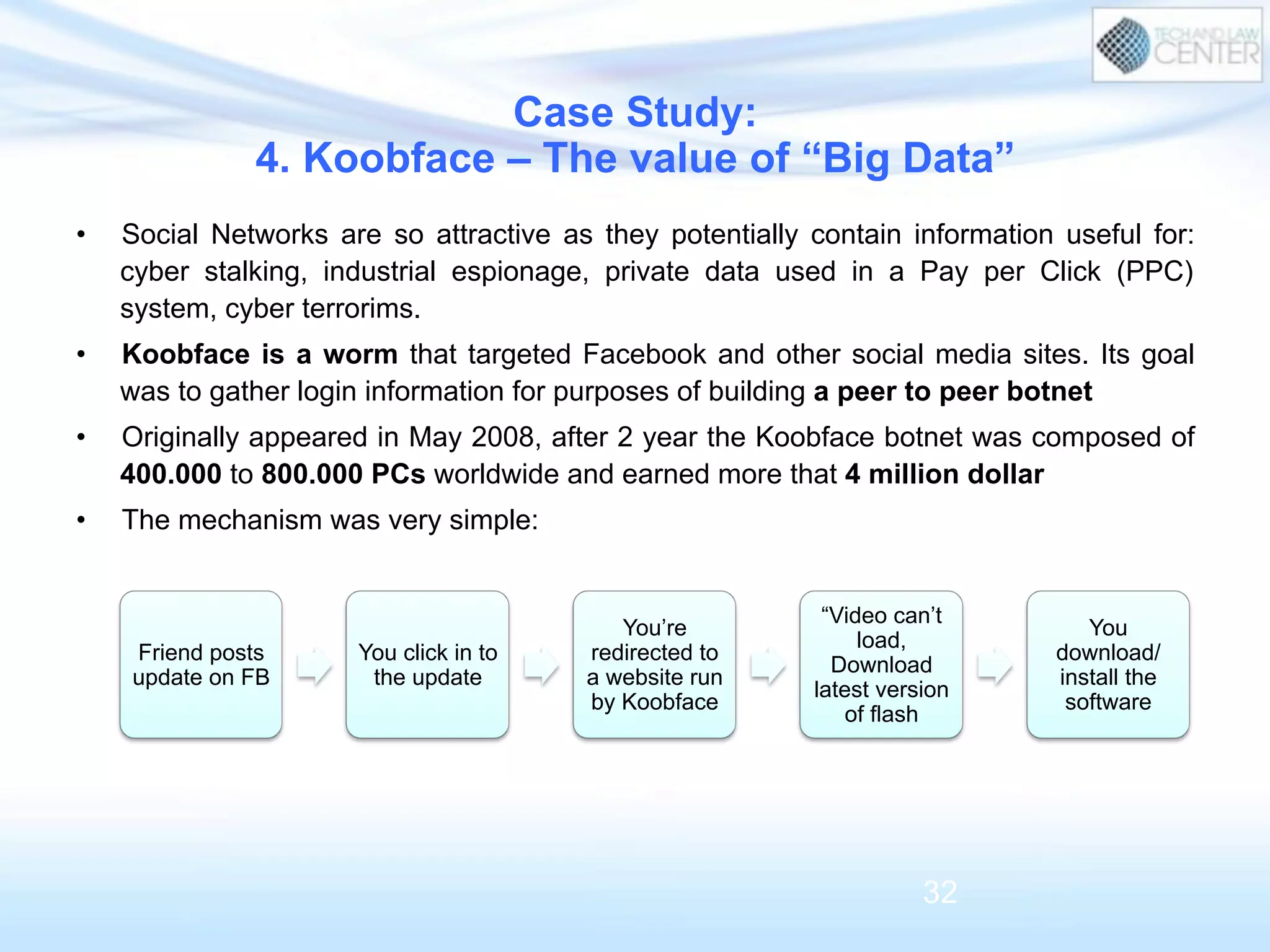
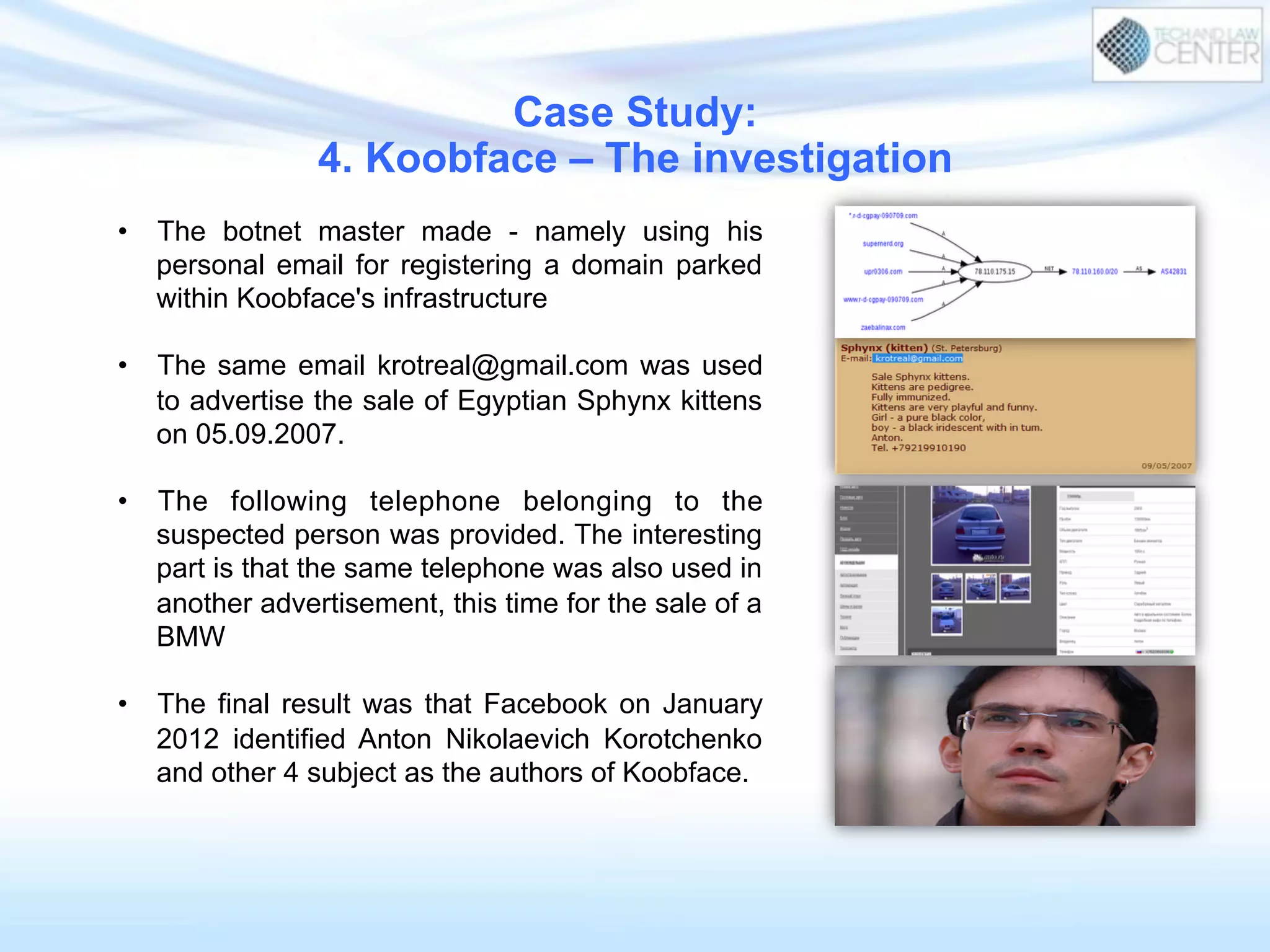
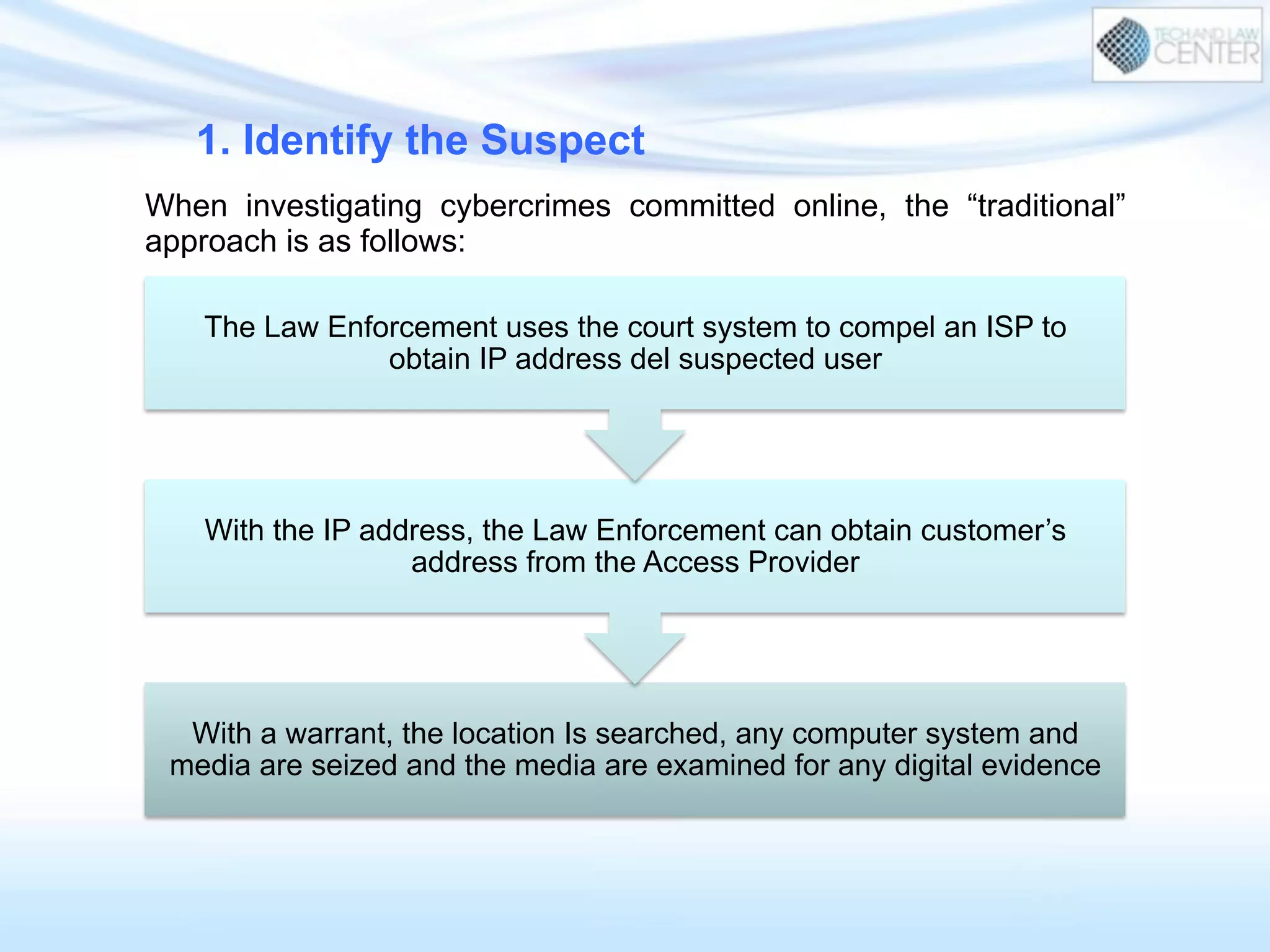
The document discusses cybercrime and digital investigation. It begins with defining cybercrime and listing its common forms. It then discusses the underground economy of cybercrime, describing how criminal networks operate similarly to legitimate businesses. Several specific cybercrimes are examined in depth, including malware, data theft, identity theft, phishing, and botnets. The document also profiles some case studies of major cybercriminal groups and hacking incidents to illustrate how crimes are committed. It aims to outline the scope and techniques of cybercrime threats.








































![1. Jurisdiction – “The Patriot Act” issue
• The Patriot Act is extraterritorial in
application (Section 215 and
Section 505).
• Under this Act, U.S. authorities are
entitled to subpoena personal data
related to non-US citizen from any
company that has “minimum
contacts” with the U.S.
The Director of the Federal Bureau of
Investigation or a designee of the Director
(whose rank shall be no lower than Assistant
Special Agent in Charge) may make an
application for an order requiring the
production of any tangible property (including
books, records, papers, documents, and other
items) for an investigation for protecting
against international terrorism or clandestine
intelligence activities, provided that such
investigation of a United States person is not
conducted solely upon the basis of activities
protected by the first amendment of the
Constitution [...]
Patriot Act, Sec. 215. Access To Records And
Other Items Under The FISA](https://image.slidesharecdn.com/20121001lisbondigitalforensics-130922063431-phpapp02/75/Cybercrime-Digital-Investigation-and-Public-Private-Partnership-by-Francesca-Bosco-e-Giuseppe-Vaciago-77-2048.jpg)