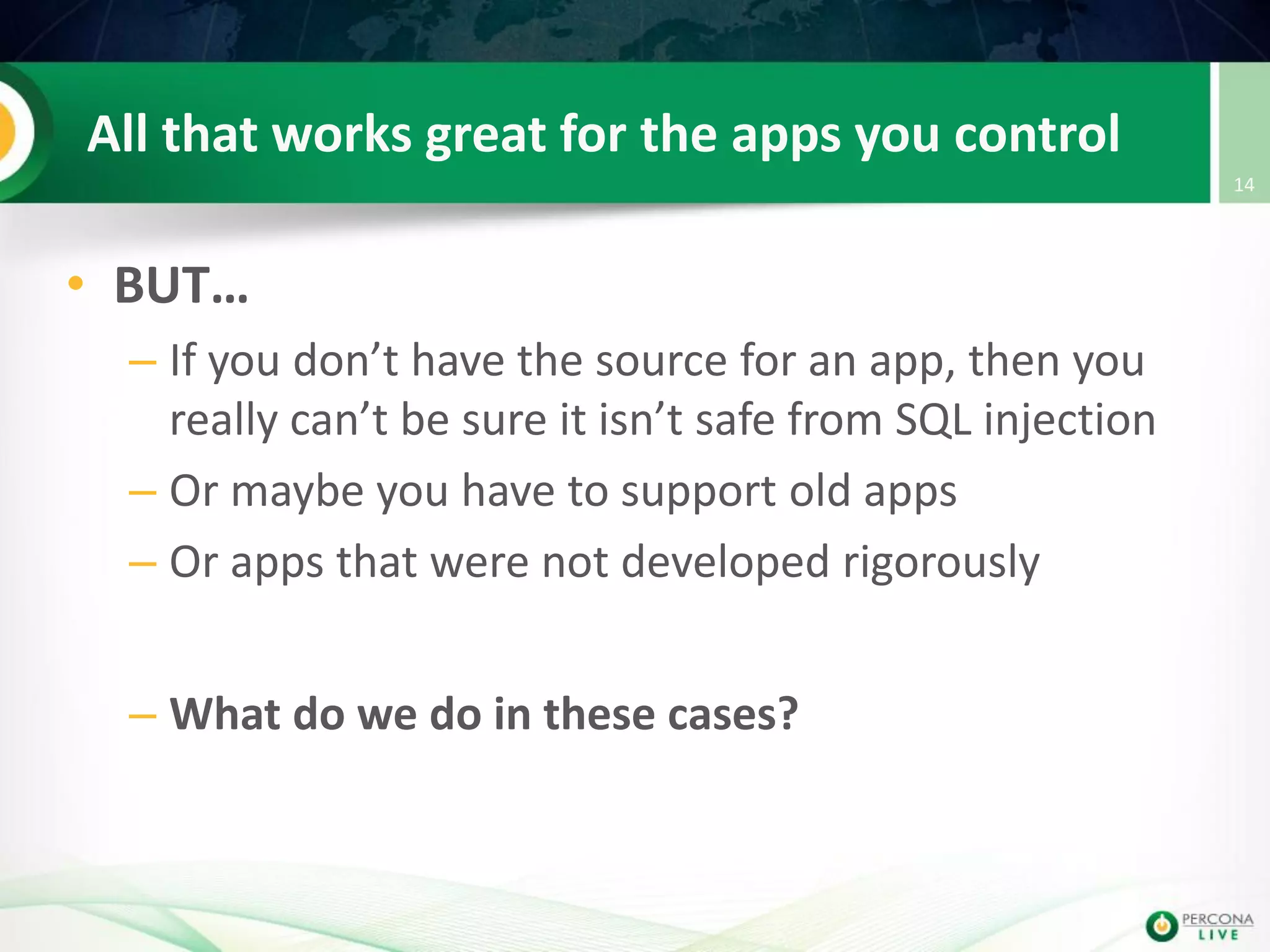
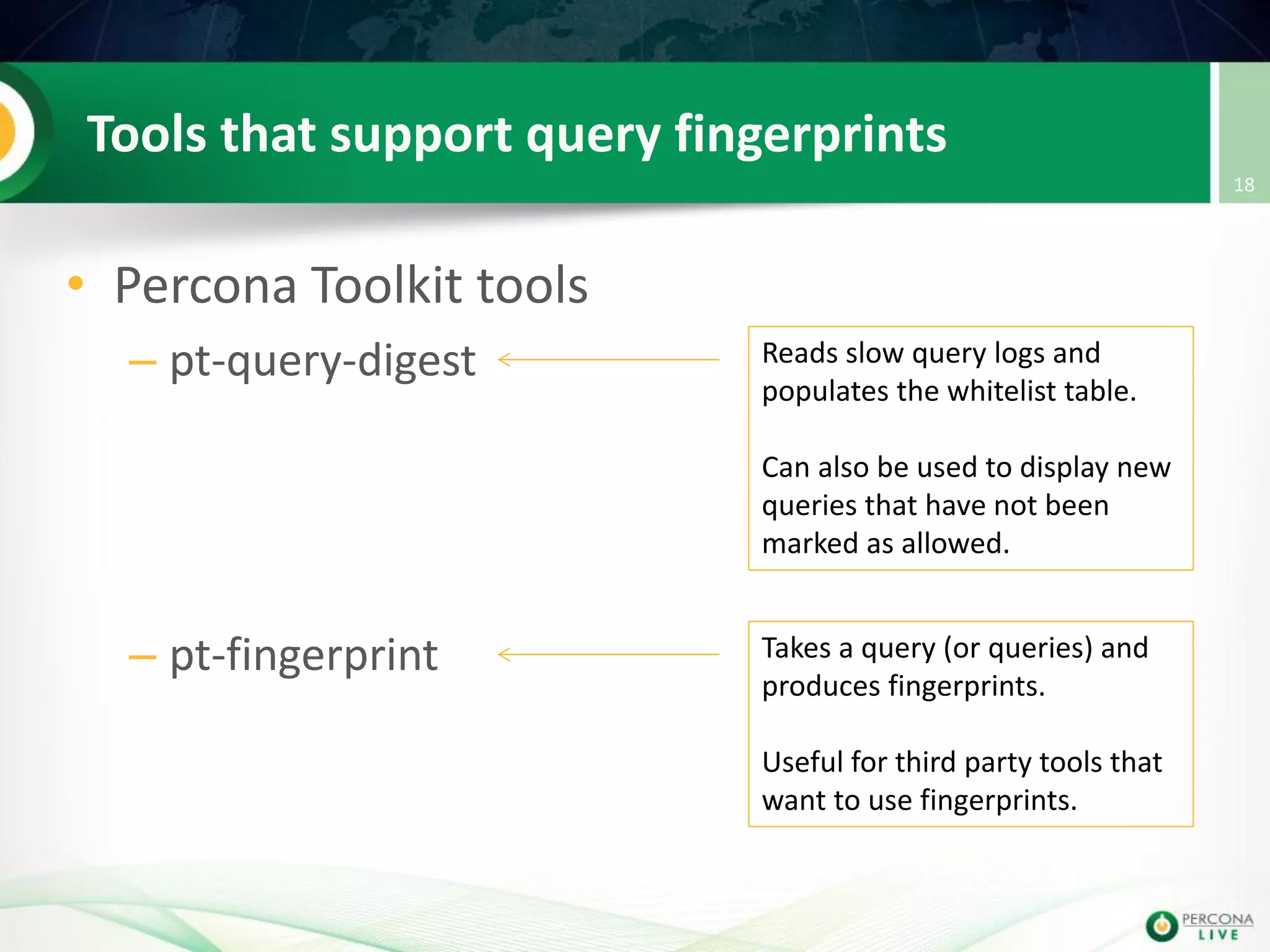
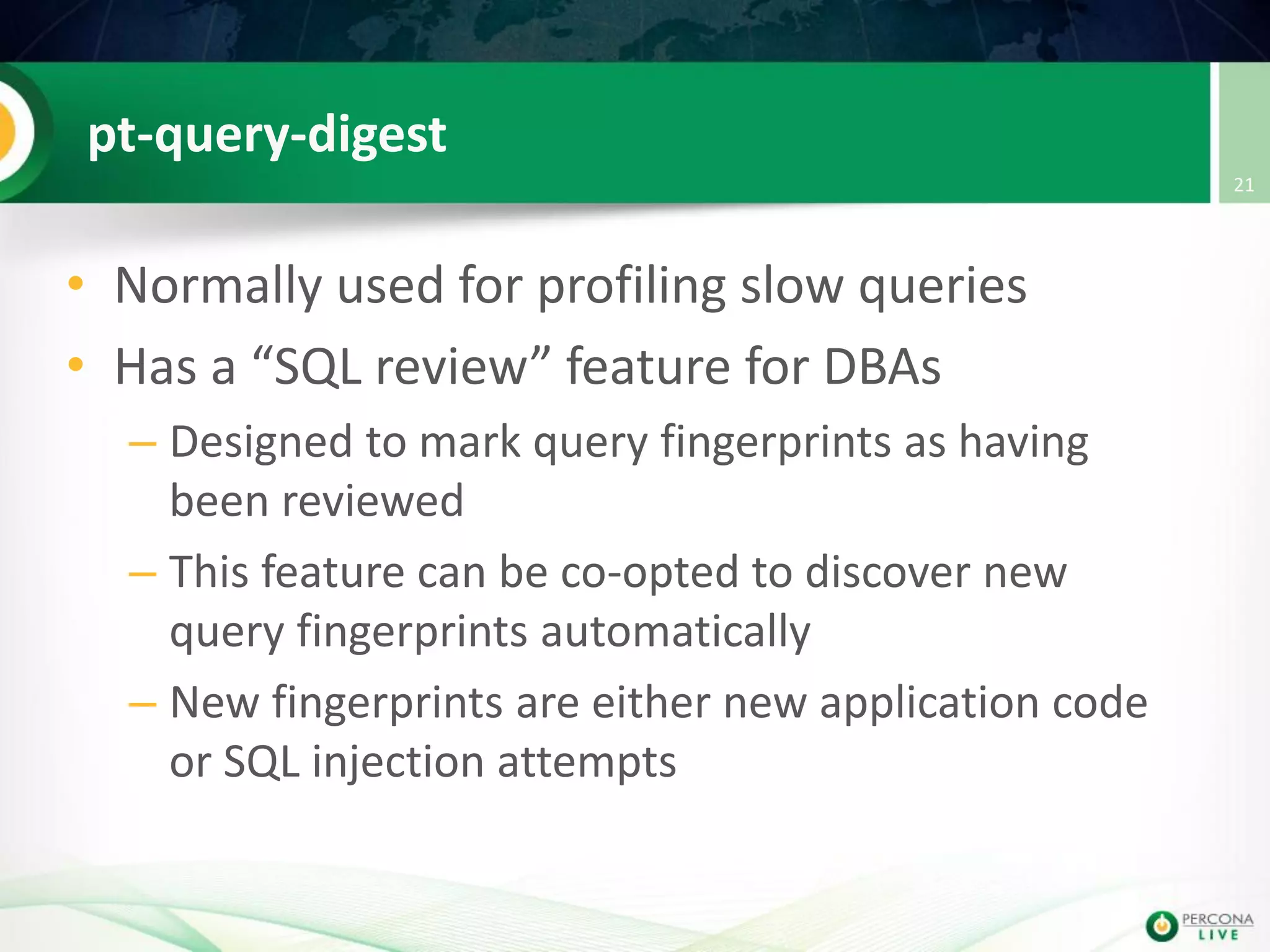
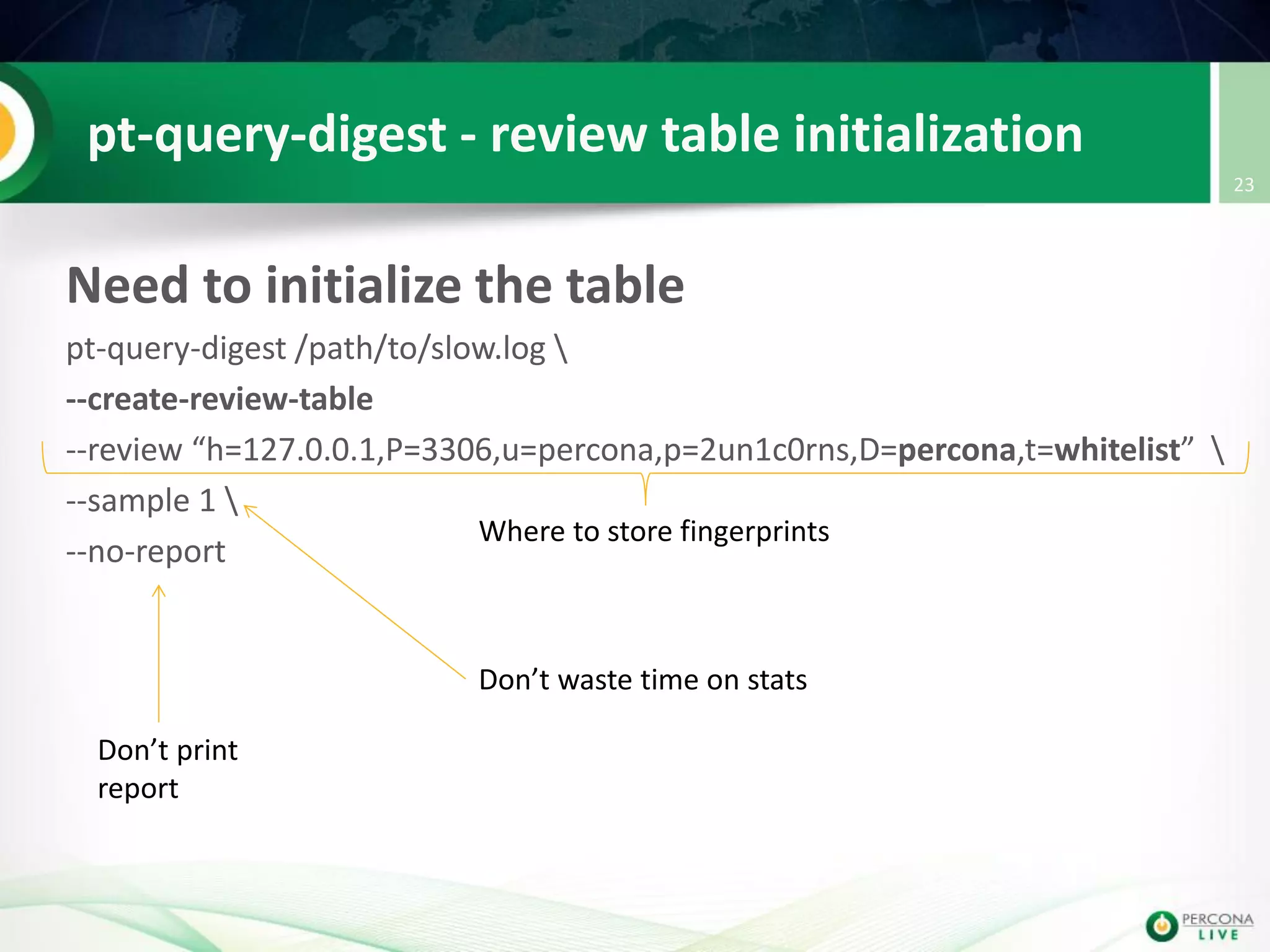
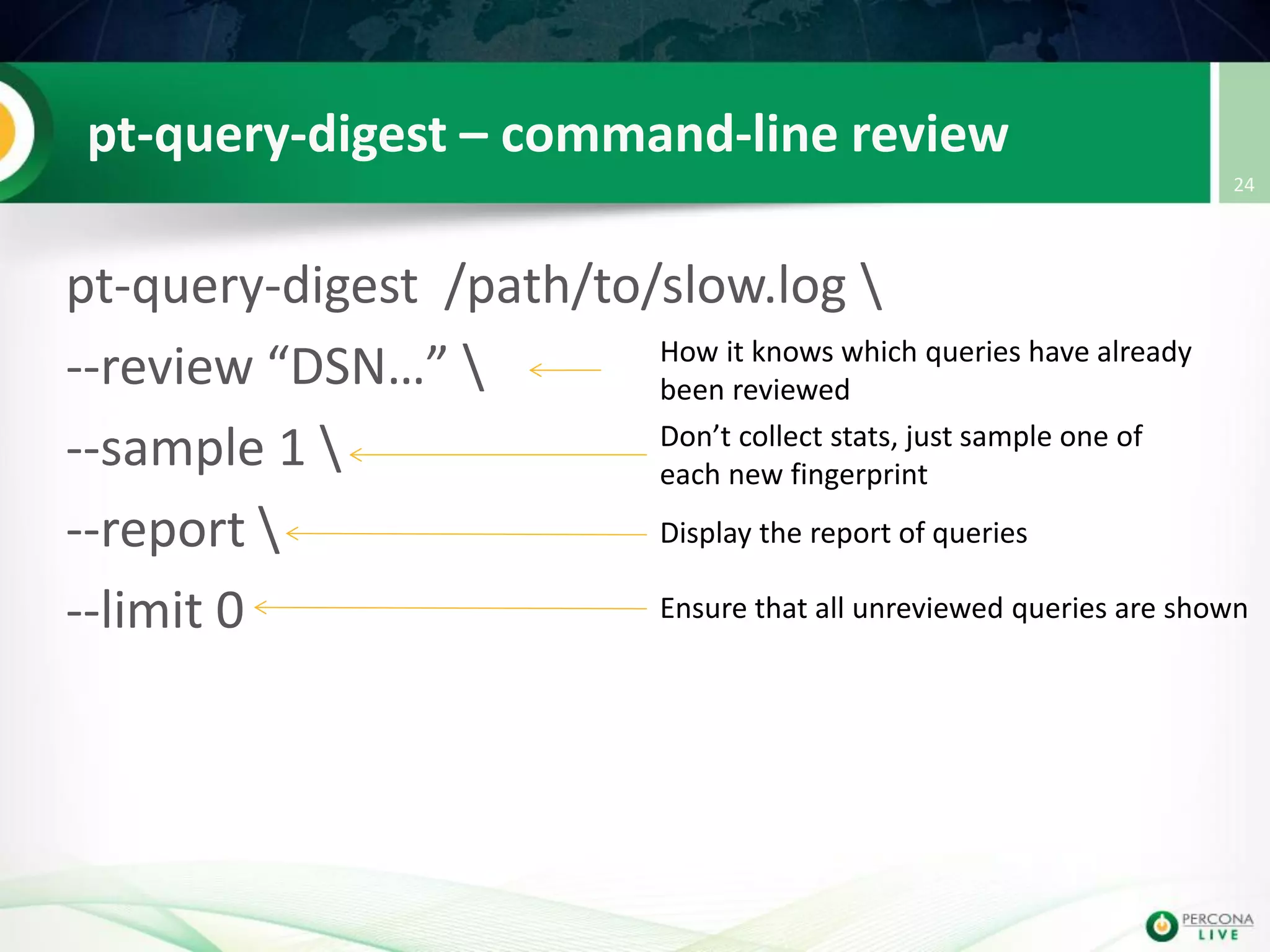
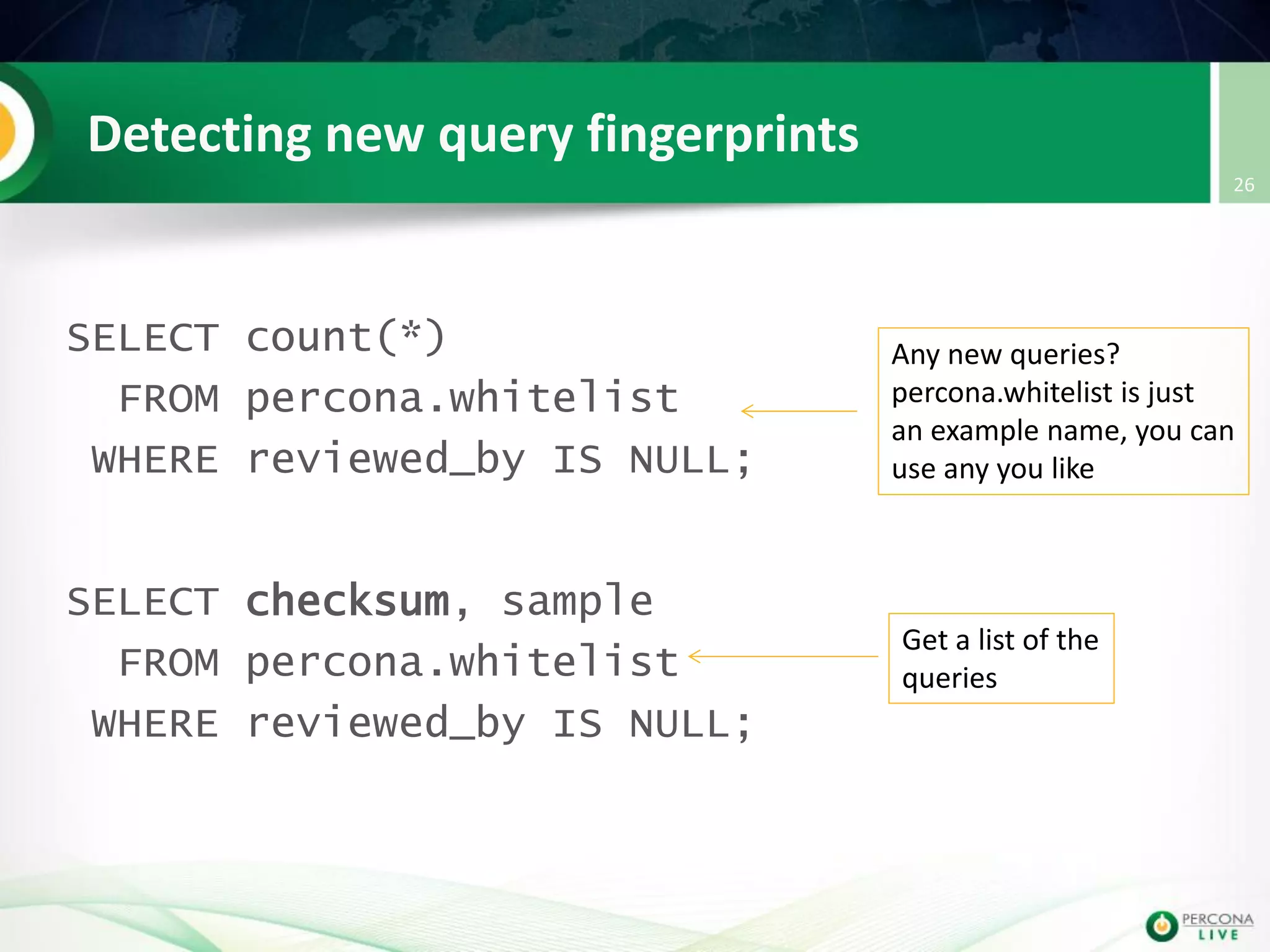
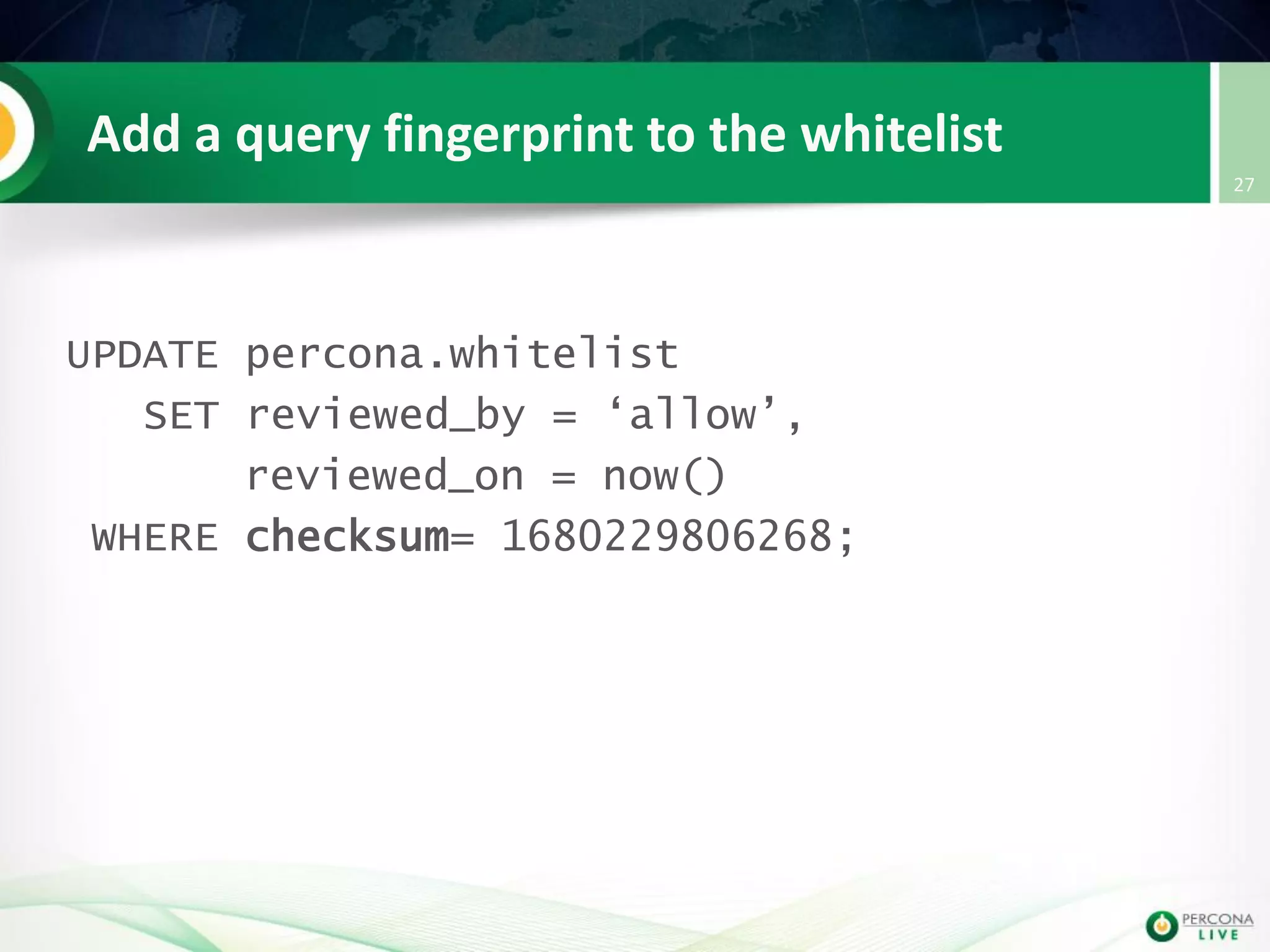
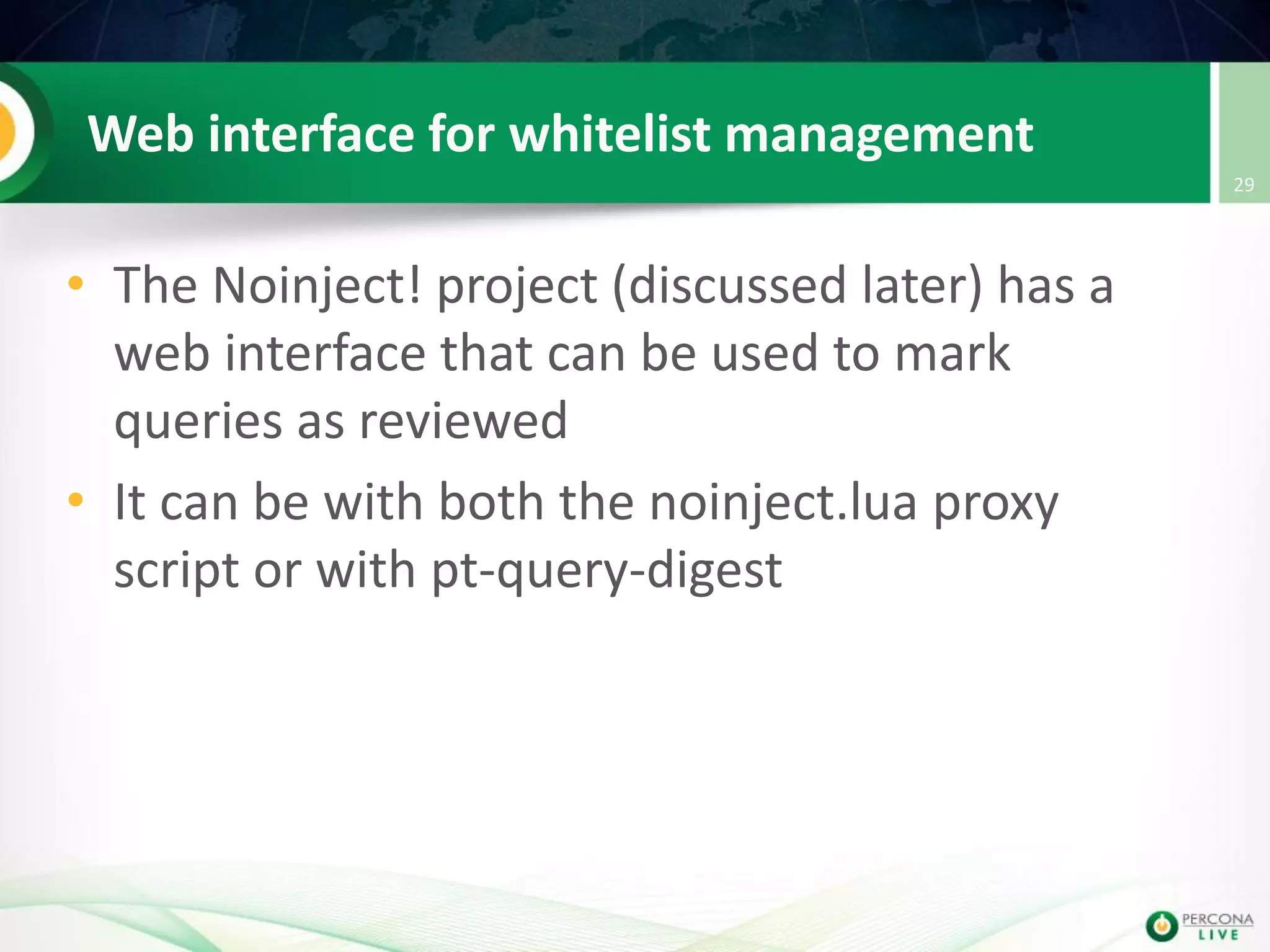
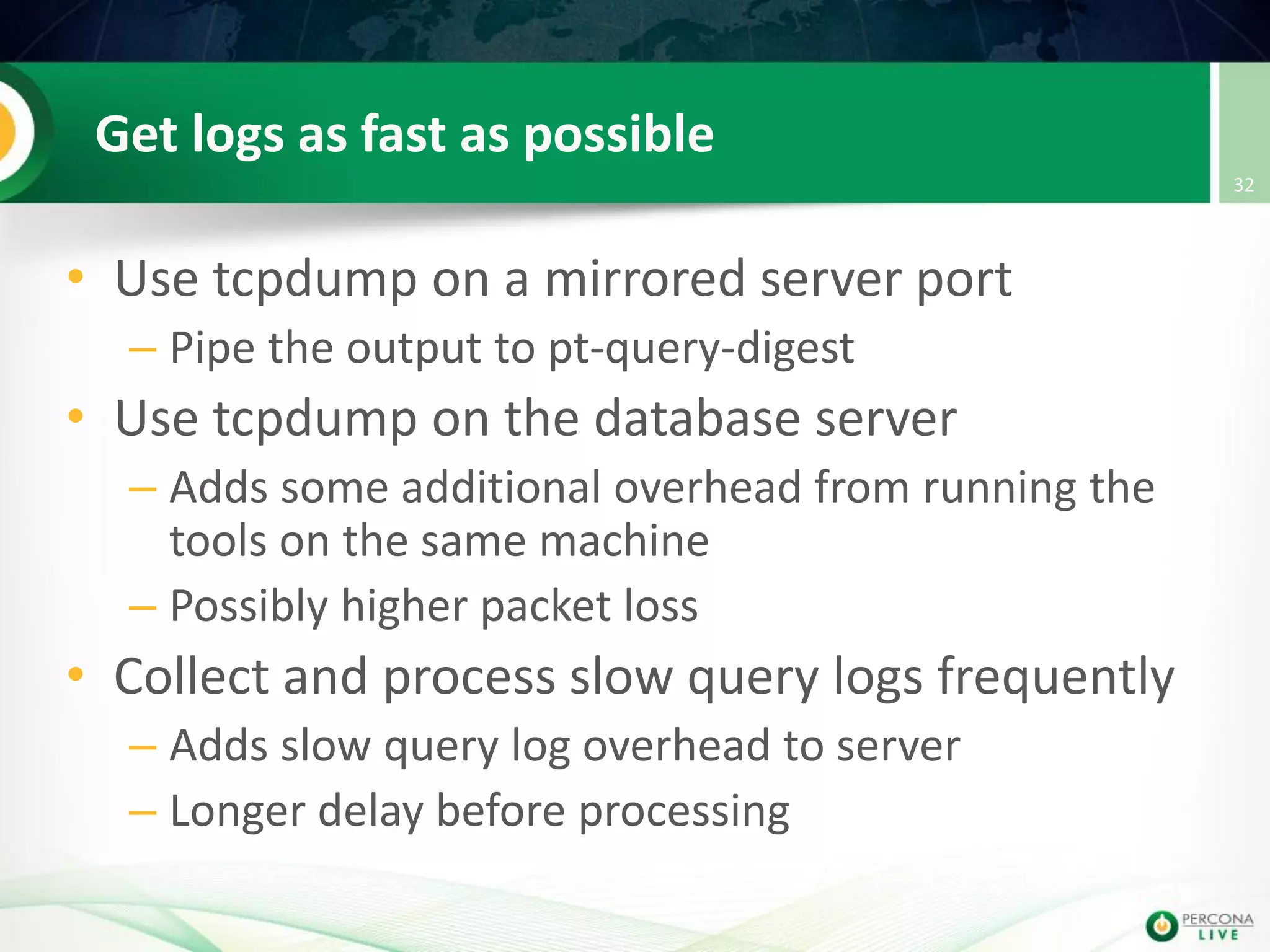
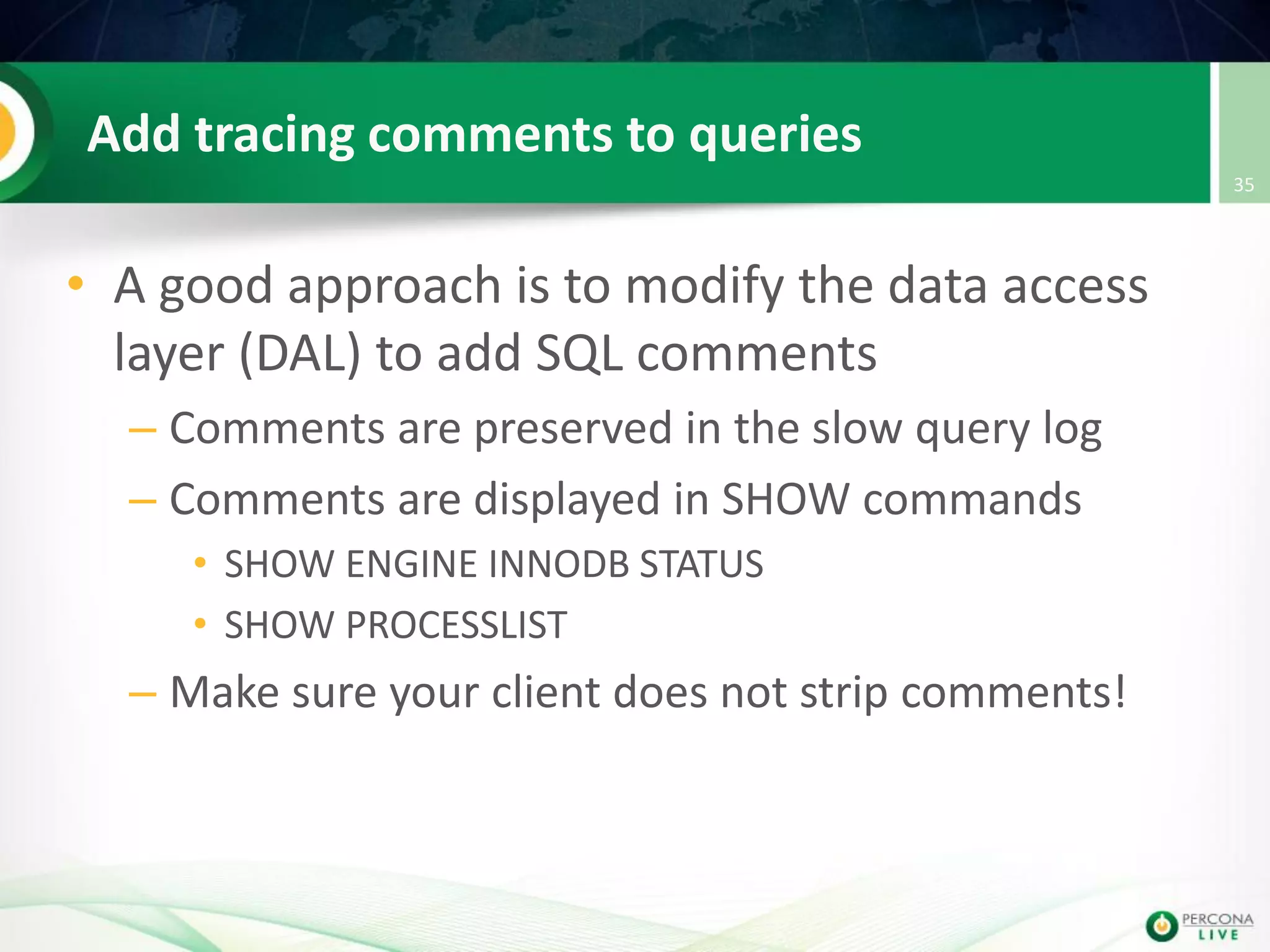
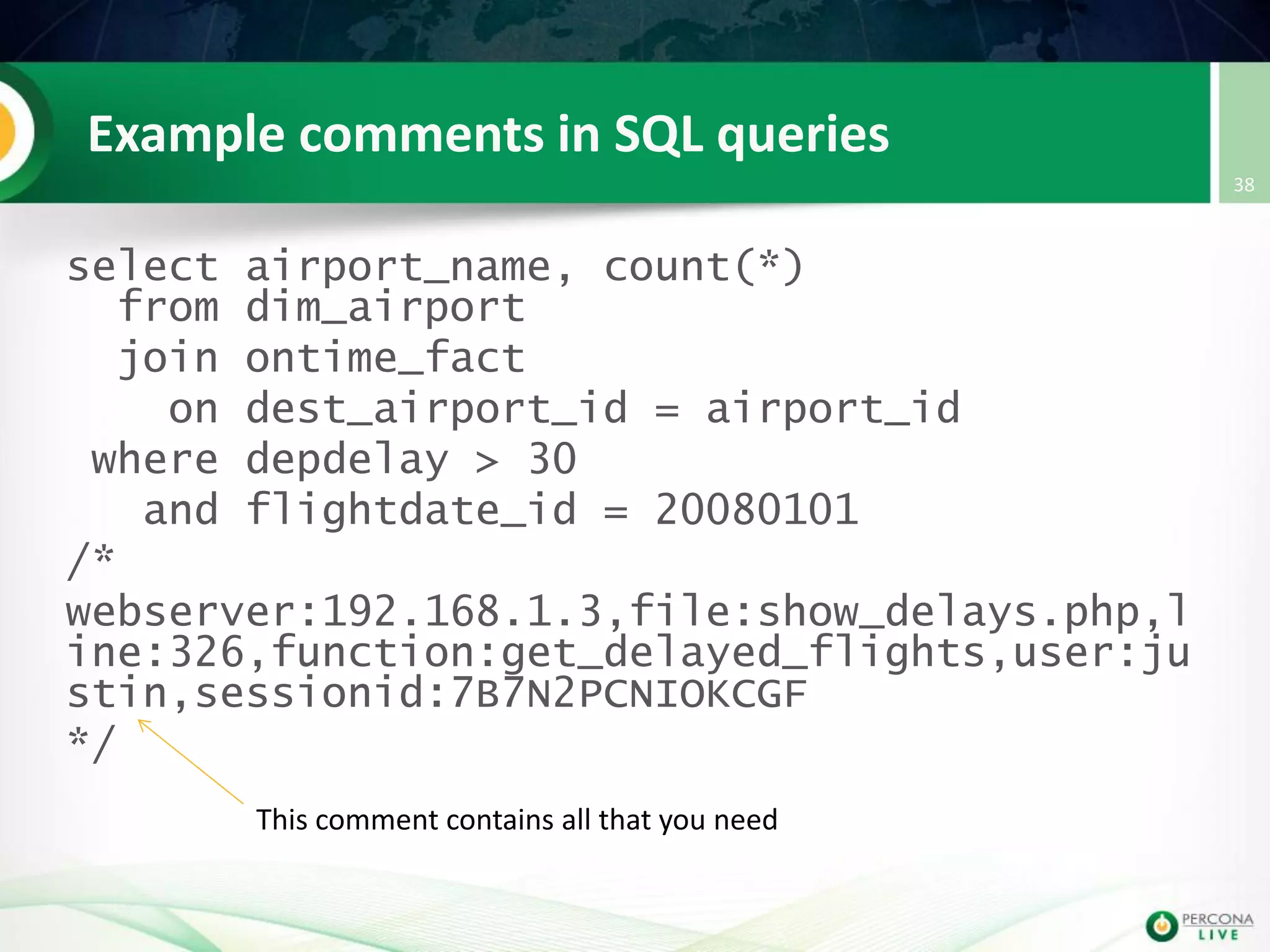
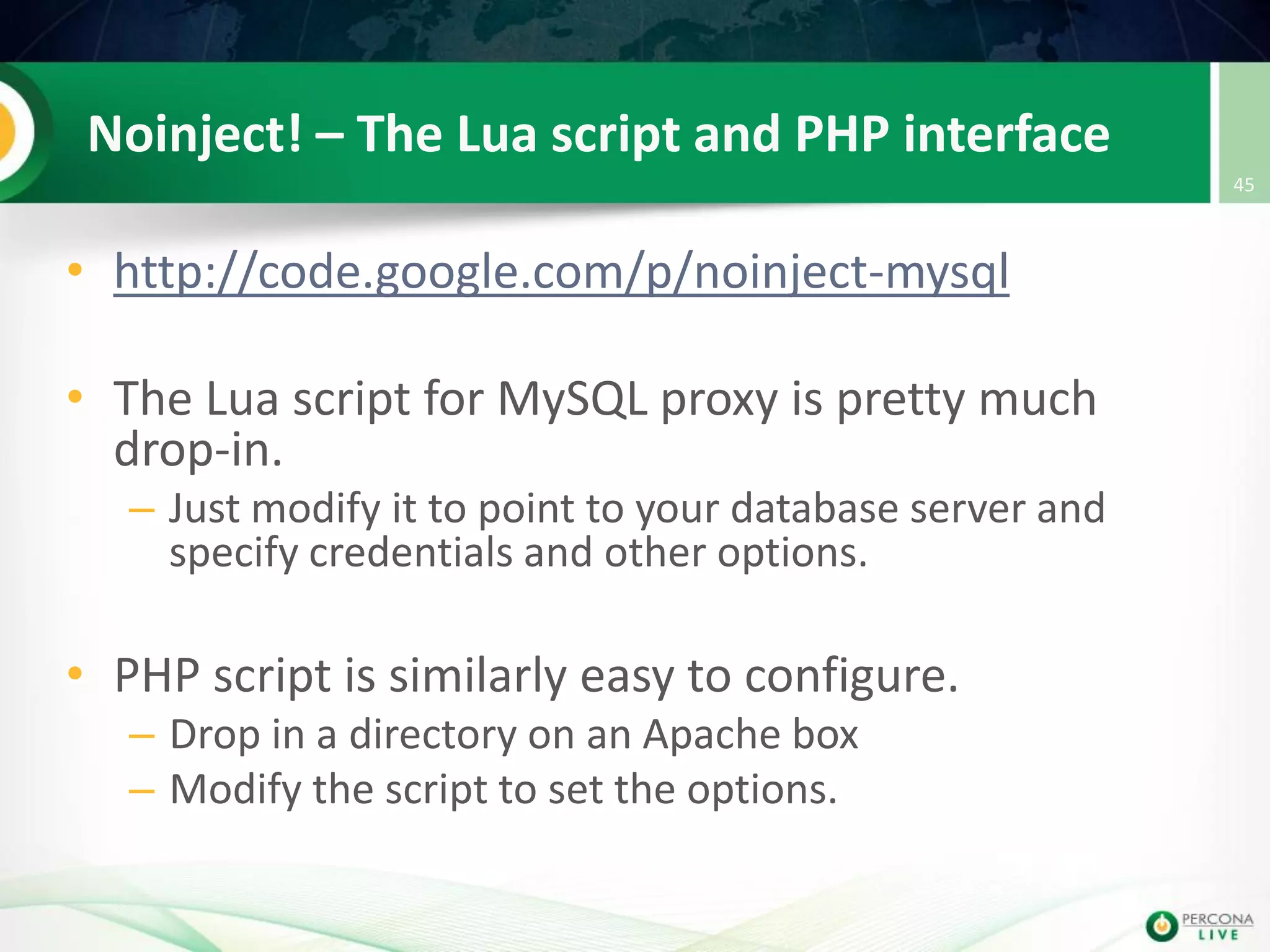
This document discusses techniques for detecting and preventing SQL injection using the Percona Toolkit and Noinject!. It begins by introducing SQL injection and how attackers can modify SQL queries without changing server code. It then discusses using query fingerprints to detect new queries that may indicate injection attempts. The Percona Toolkit tools pt-query-digest and pt-fingerprint are used to generate and store fingerprints in a whitelist. Pt-query-digest can detect new fingerprints that have not been reviewed. The Noinject! proxy script uses fingerprints to inspect queries in real-time and block any that do not match whitelisted patterns. The document concludes by discussing limitations and ways to improve the fingerprinting approach.




![What is SQL injection – interpolation (strings)
$username = $_GET[‘username’];
$sql =
“select 1
from users.users
where admin_flag=true
and username = ‘“ . $username . “’”;
$ wget http://host/path.php?username=bob
$ wget http://host/path.php?user_id=“' or '1'='1”
and username = ‘’ or ‘1’ = ‘1’
7
SQL injection!](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-7-2048.jpg)
![Escape strings, or use prepared statements!
#escape string values
$username = mysqli_real_escape_string($_GET[‘username’]);
$sql = “select … and username = ‘“ . $username . “’”;
#prepared statement
$username = GET[‘username’];
$stmt = mysqli_stmt_init($conn);
$sql = “select … and username = ?”
mysqli_stmt_prepare($stmt, $sql);
mysqli_stmt_bind_param($stmt, “s”, $username);
mysqli_stmt_execute($stmt);
mysqli_stmt_close($stmt);
8](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-8-2048.jpg)
![What is SQL injection – interpolation (ints)
$user_id = $_GET[‘user_id’];
$sql =
“select 1
from users.users
where admin_flag=true
and user_id = “ . $user_id;
…
$ wget http://host/path.php?user_id=1
$ wget http://host/path.php?user_id=“1 or 1=1”
9
SQL injection!](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-9-2048.jpg)
![Use type checking, or prepared statements!
#check that integers really are integers!
$user_id = GET[‘user_id’];
if(!is_numeric(user_id)) $user_id = “NULL”;
$sql = “select … and user_id = “ . $user_id;
#prepared statement
$user_id = GET[‘user_id’];
$sql = “select … and user_id = ?”
…
mysqli_stmt_bind_param($stmt, “i”, $user_id);
mysqli_stmt_execute($stmt);
10](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-10-2048.jpg)

![Don’t use user input in the query
#avoid using user input directly in ANY way
$sql = “select * from listings where deleted = 0 and sold
= 0 and open = 1”;
if(!empty($_GET[‘ob’])) {
$sql .= “ ORDER BY “ . $_GET[‘ob’];
}
wget … ?ob=post_date
wget … ?ob=“post_date union all (select * from listings)”
12
Now we can see all listings
Bad!](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-12-2048.jpg)
![Use whitelisting instead
#avoid using user input directly in ANY way
$sql = “select * from listings where deleted = 0 and sold
= 0 and open = 1”;
$allowed = array(‘post_date’,’neighborhood’,’etc’);
if(!empty($_GET[‘ob’]) && is_string($_GET[‘ob’])) {
if(in_array($_GET[‘ob’], $allowed)) {
$sql .= “ ORDER BY “ . $_GET[‘ob’];
}
}
wget … ?ob=post_date
wget … ?ob=“post_date union all (select * from listings)”
13
in_array() is the keeper of the gate](https://image.slidesharecdn.com/noinject-130424183128-phpapp02/75/Noinject-13-2048.jpg)