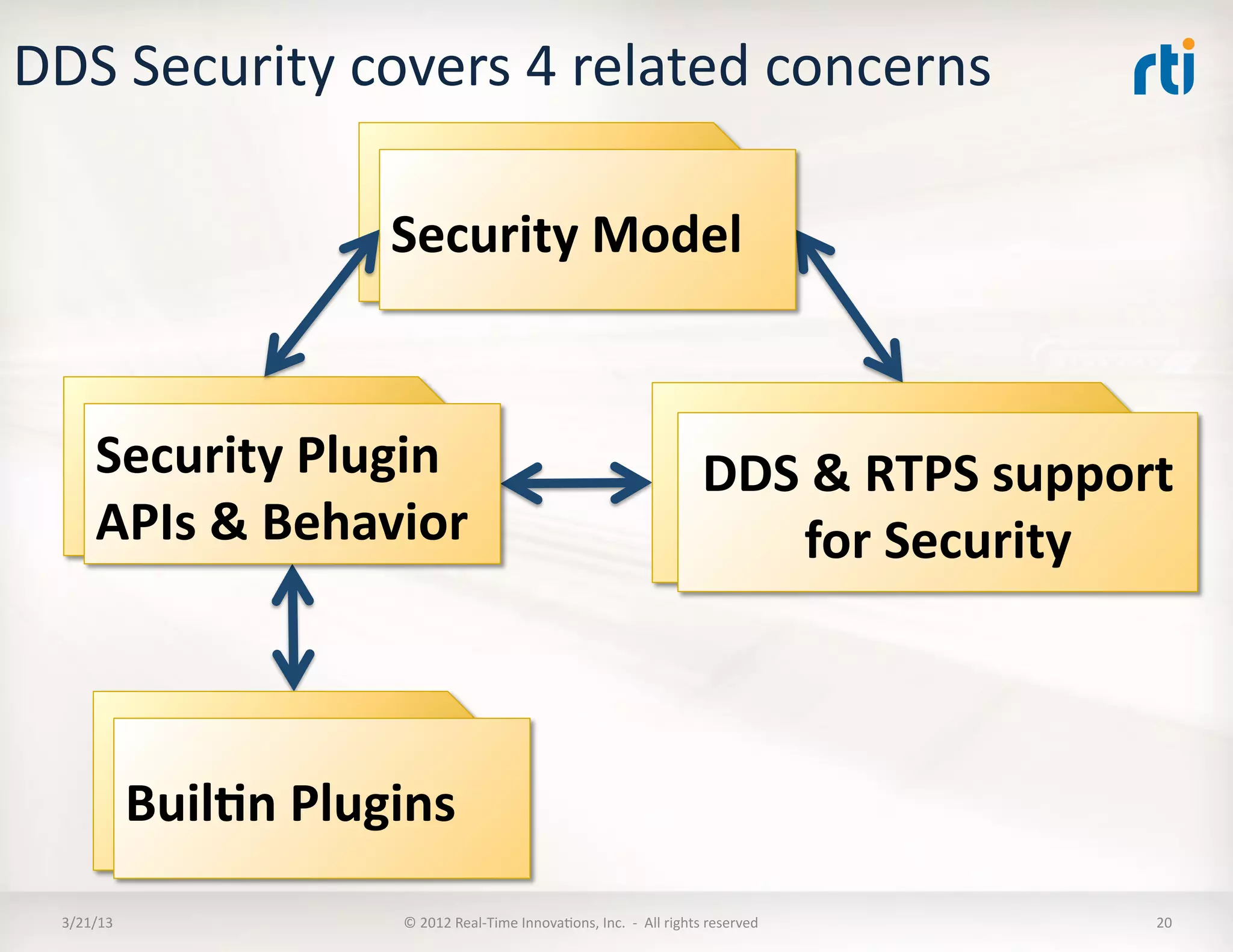
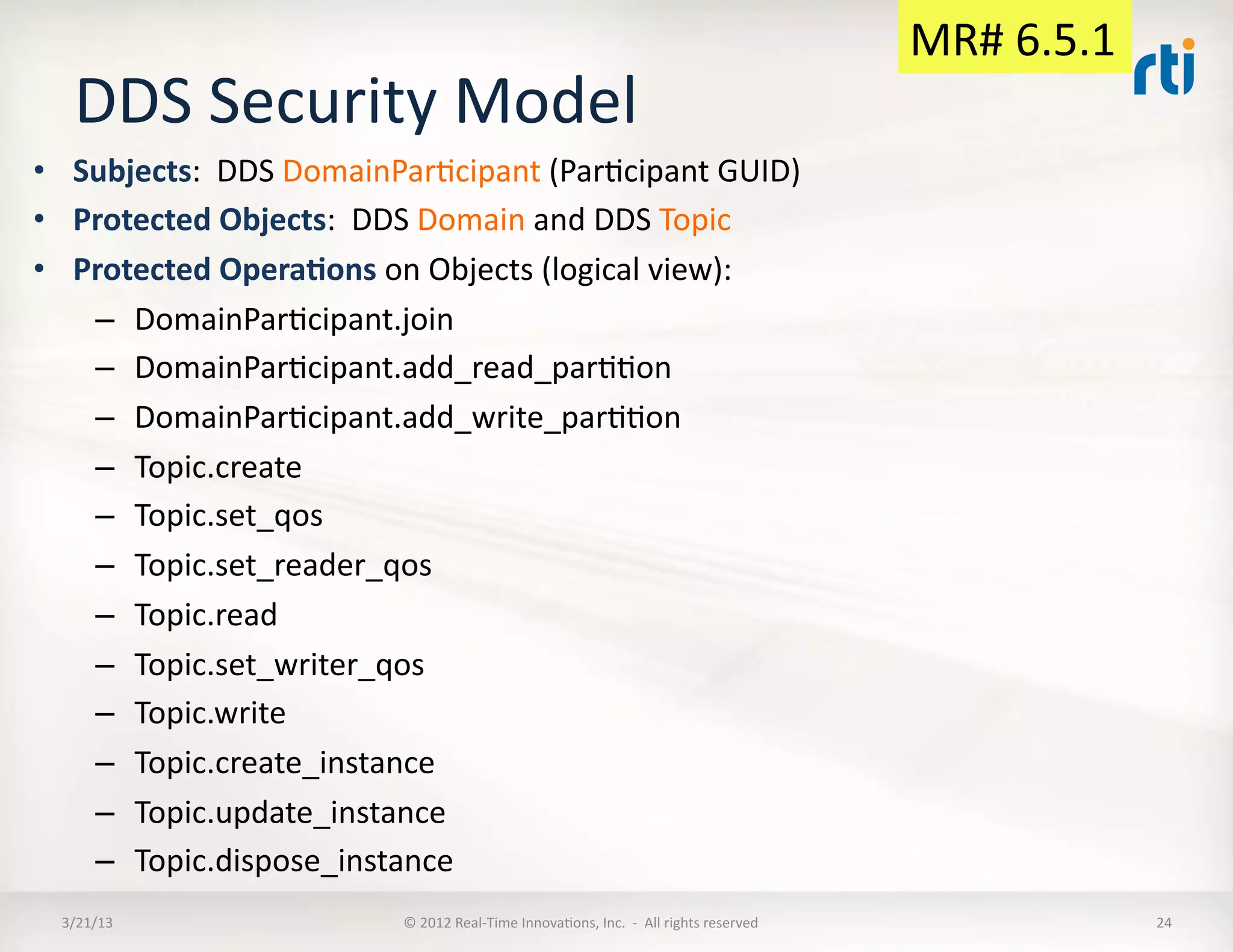
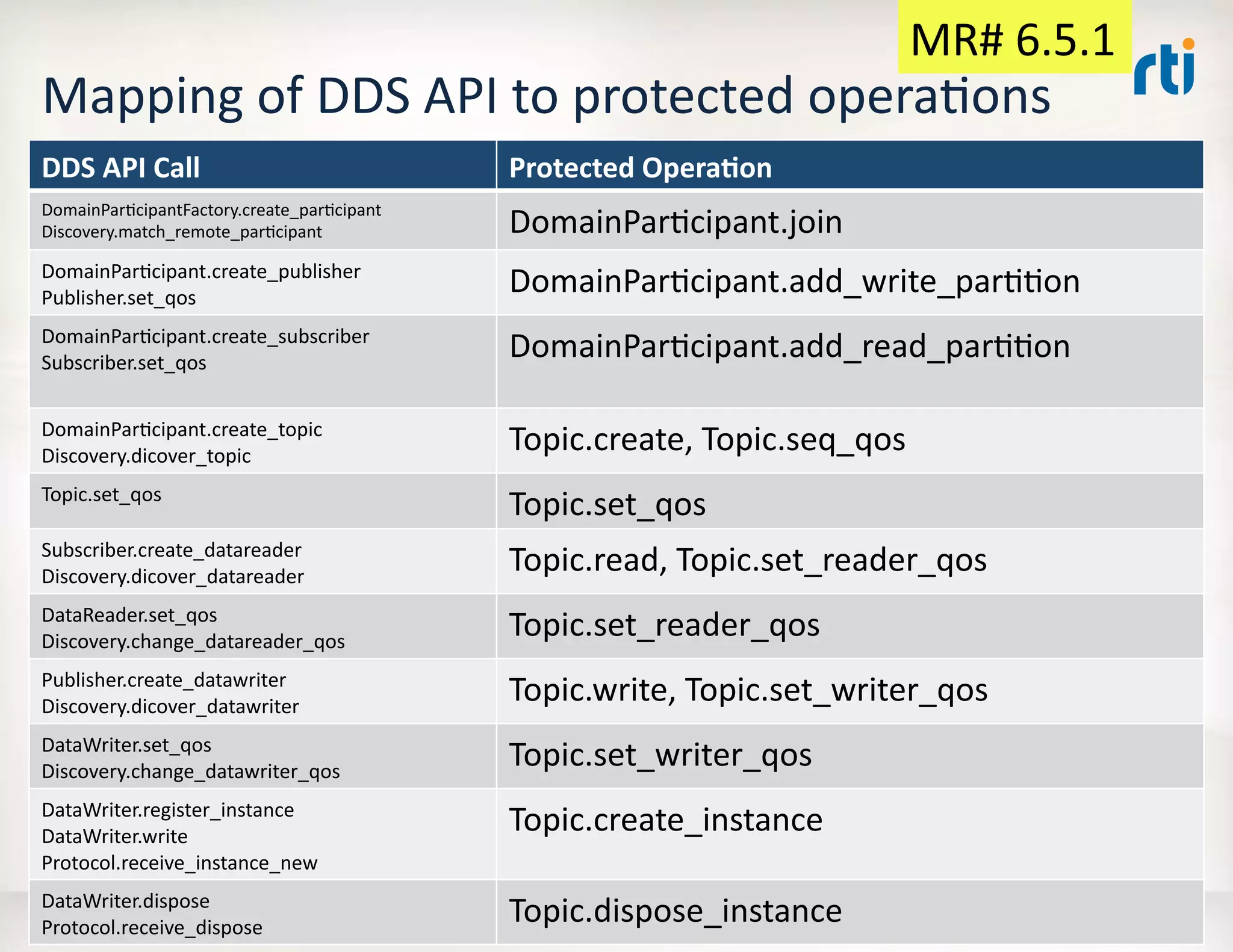
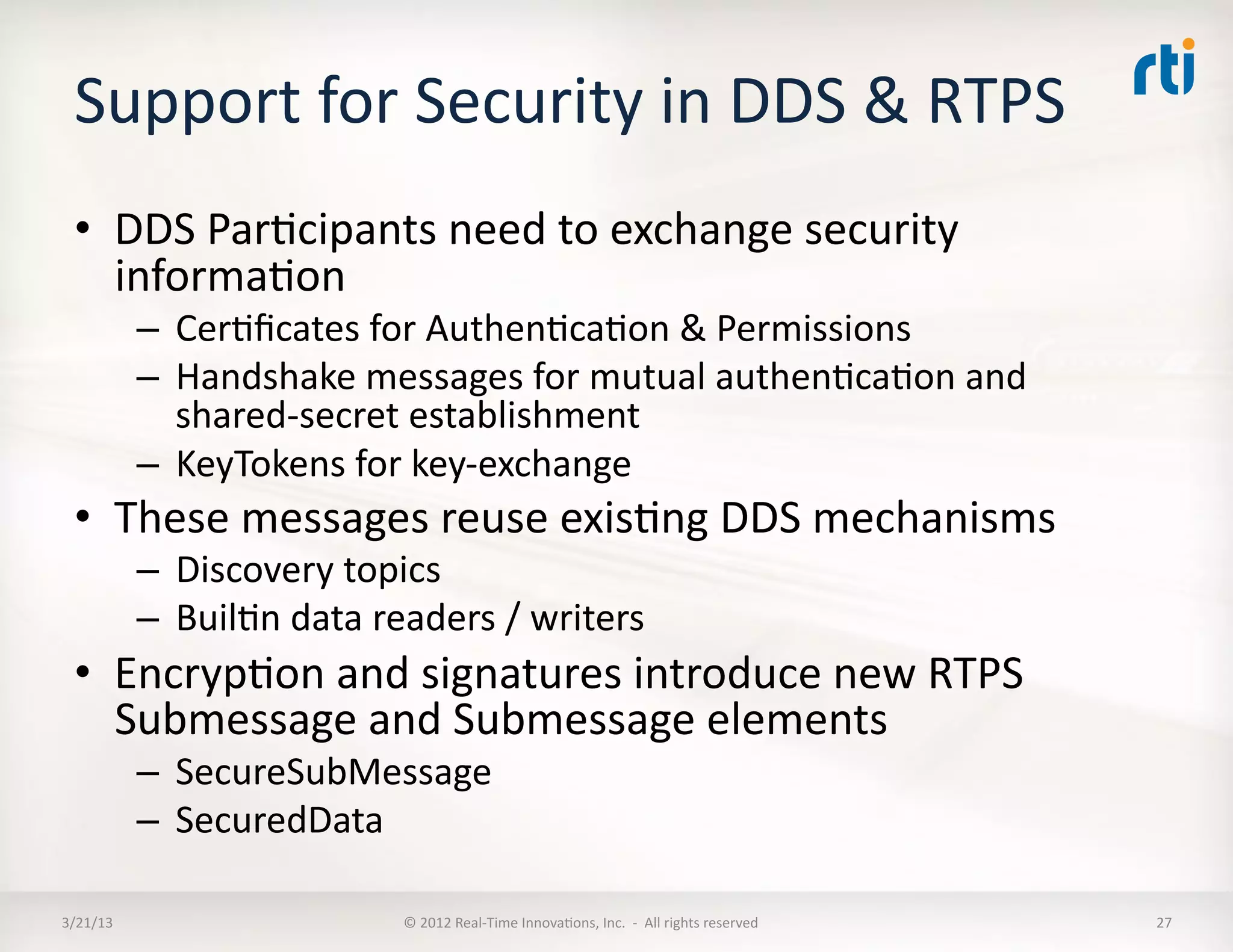
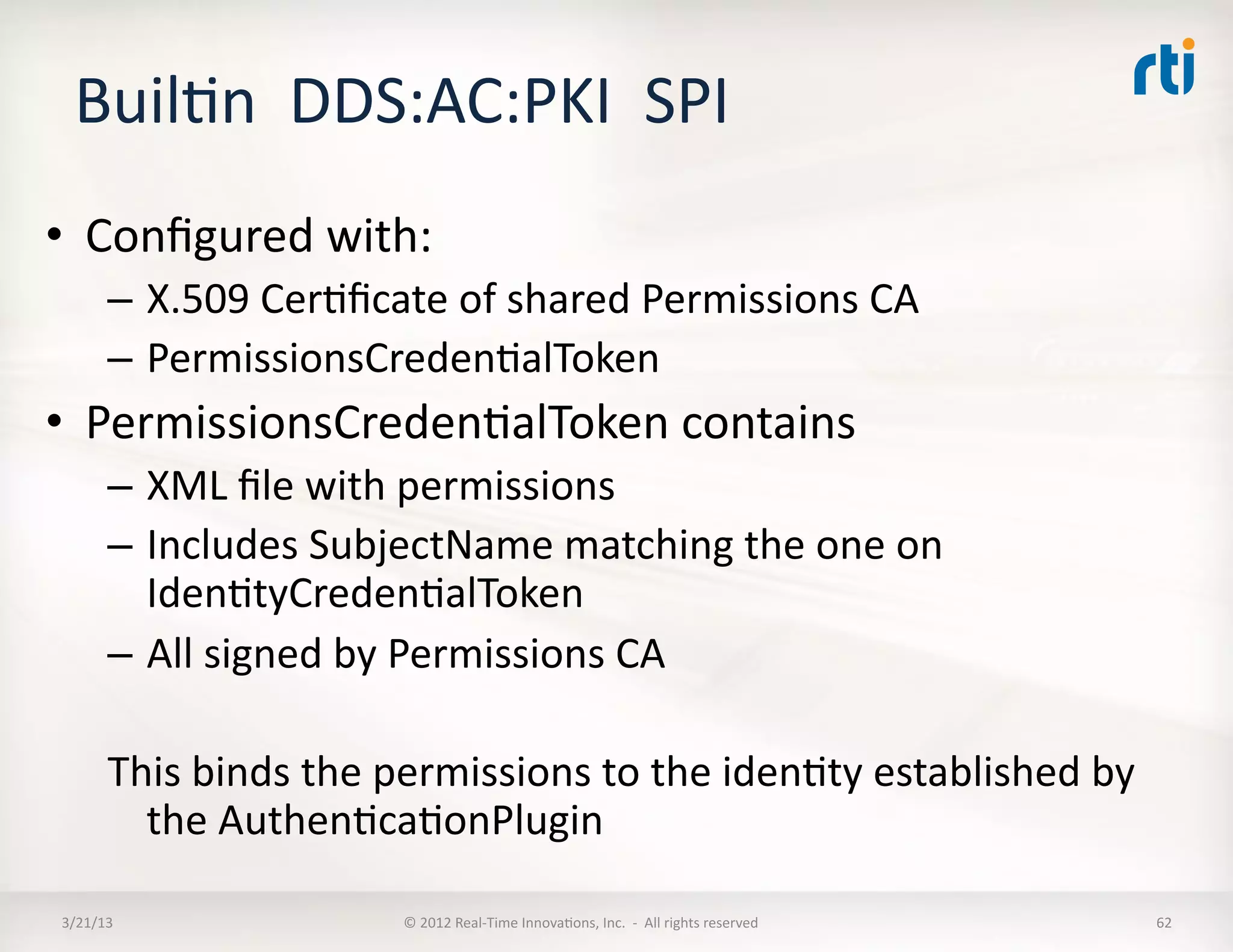
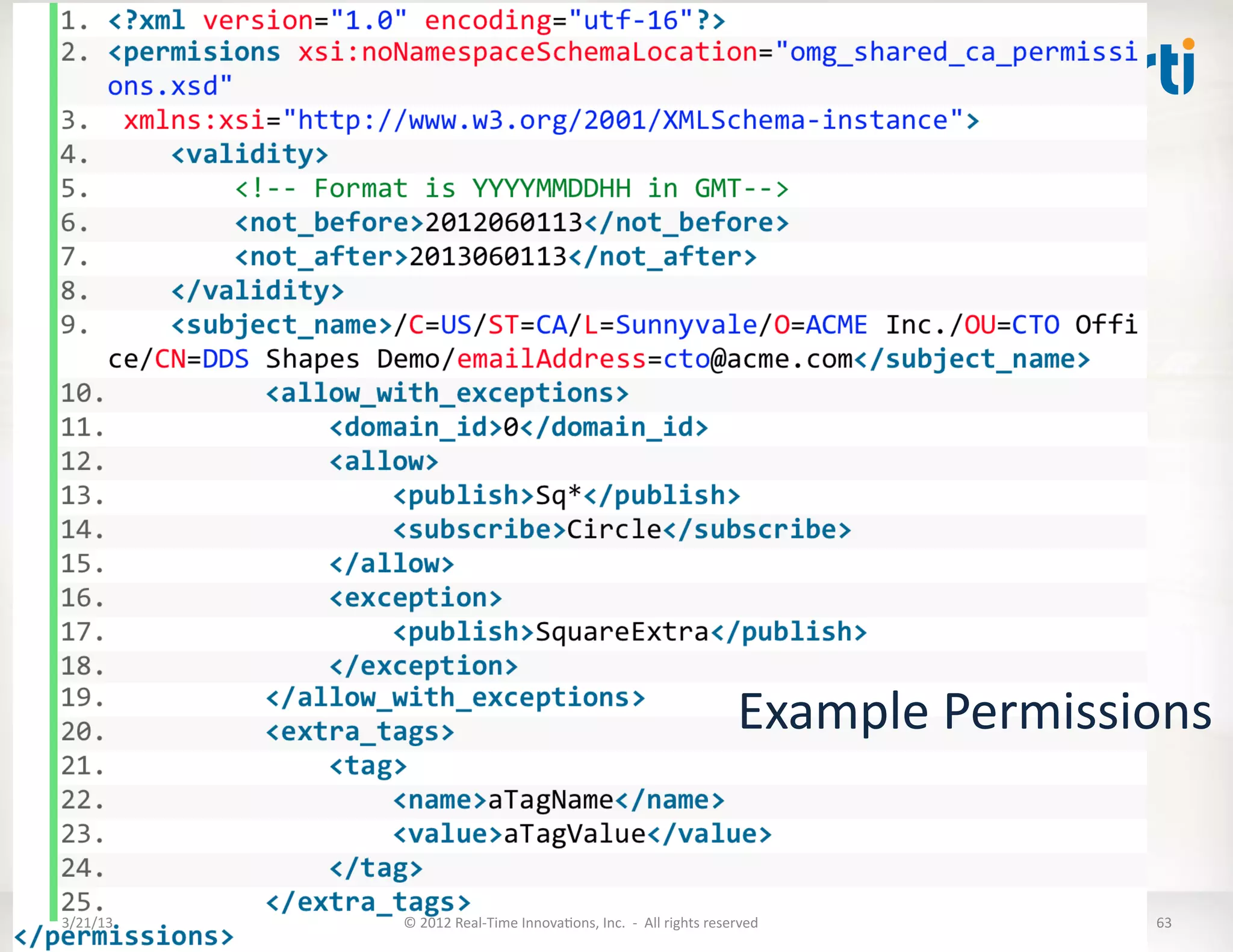
The document outlines a revised submission for a DDS (Data Distribution Service) security specification, detailing the integration of security protocols, specifically the use of MIKEY and SRTP for secure communication. It emphasizes a platform-independent security model, the roles of participants, and the required operations for protecting data within DDS systems. The document also addresses potential security threats and mandates for implementing access controls, secure communication, and interoperability standards.



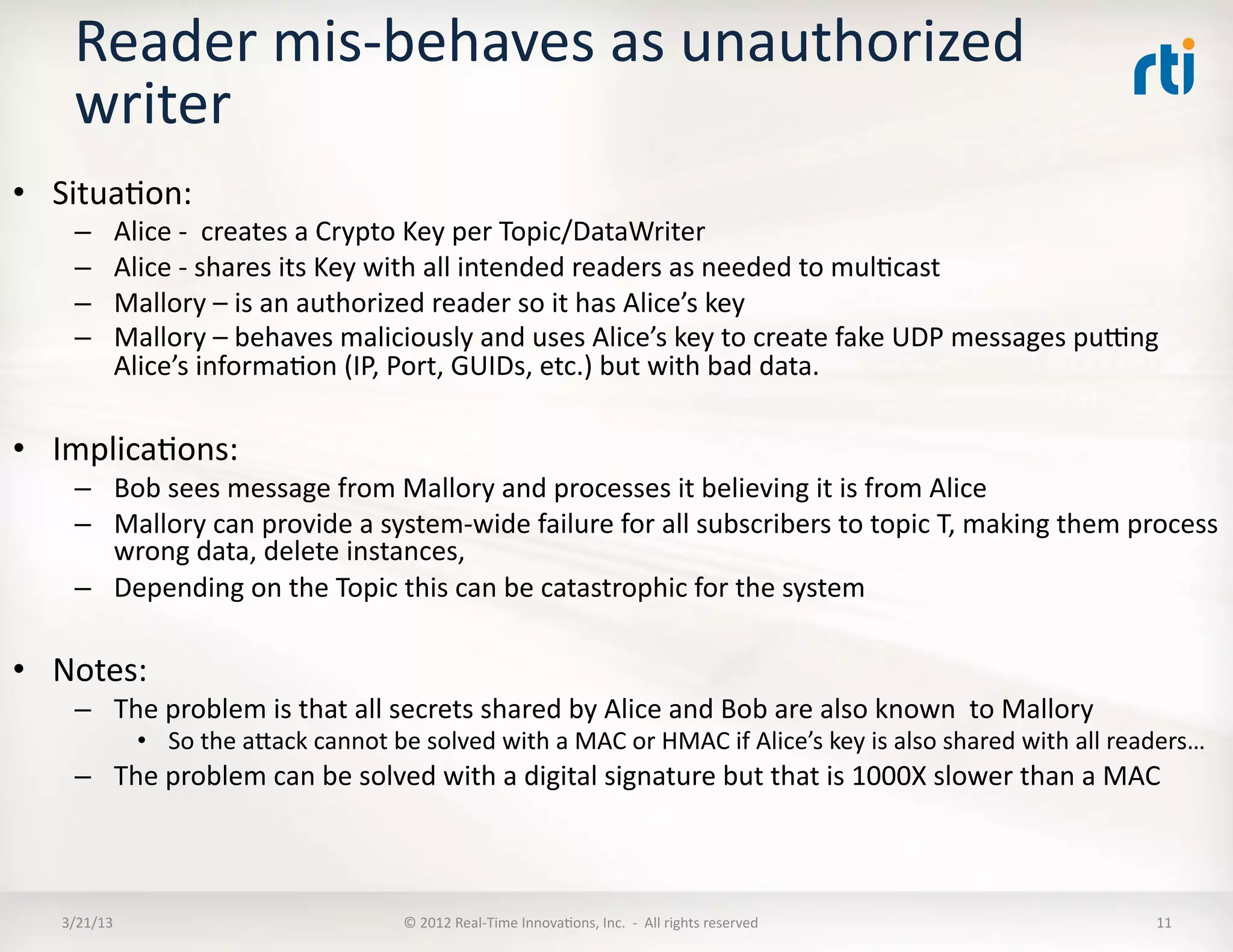

![Mandatory
Requirements
6.5.1:
Security
Model
The
Security
Model
for
DDS
shall
…
6.5.1.1
…
support
mechanisms
that
establish
the
ability
for
a
DDS
ParKcipant
to
run
in
a
plaoorm
6.5.1.2
…
support
mechanisms
to
configure
and
access
the
credenKals
of
the
underlying
DDS
ParKcipants
…
6.5.1.3
…
allow
specificaKon
of
authorizaKon
policies,
controlling
[1]
Joining
a
DDS
Domain
[2]
Access
to
DDS
Discovery
Data
[3]
Publishing
a
DDS
Topic,
[4]
Subscribing
to
a
DDS
Topic
[5]
Publishing
on
a
DDS
ParKKon,
[6]
Subscribing
on
a
DDS
ParKKon
6.5.1.4
…
include
the
concept
of
data
tagging
6.5.1.5
…
support
mechanism
for
ensuring
data
integrity,
including
[1]
traceability,
pedigree,
and
tamper
[2]
digital
signatures
[3]
data
encrypKon
[4]
use
of
different
keys
for
data
from
different
DataWriters
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
14](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-14-2048.jpg)
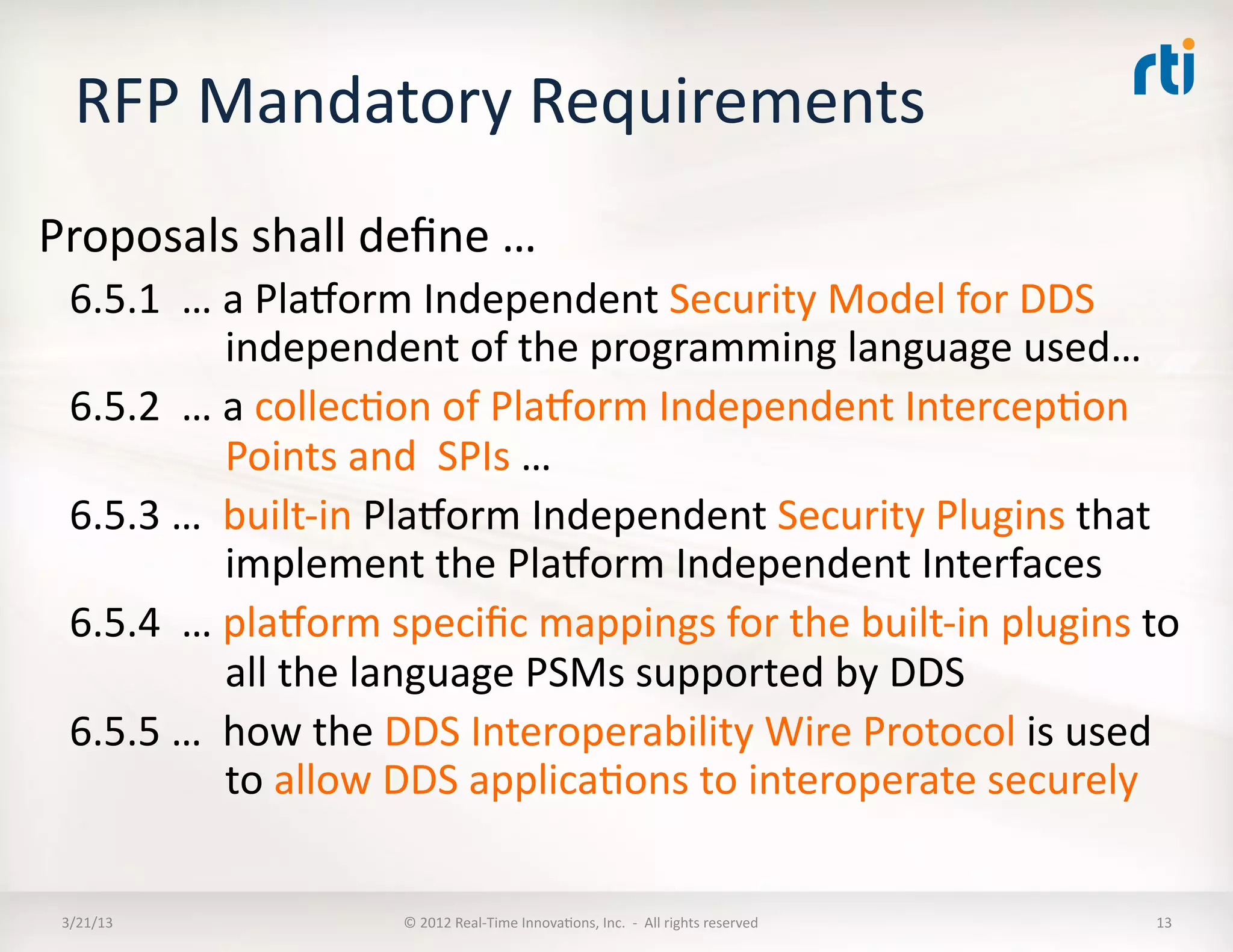
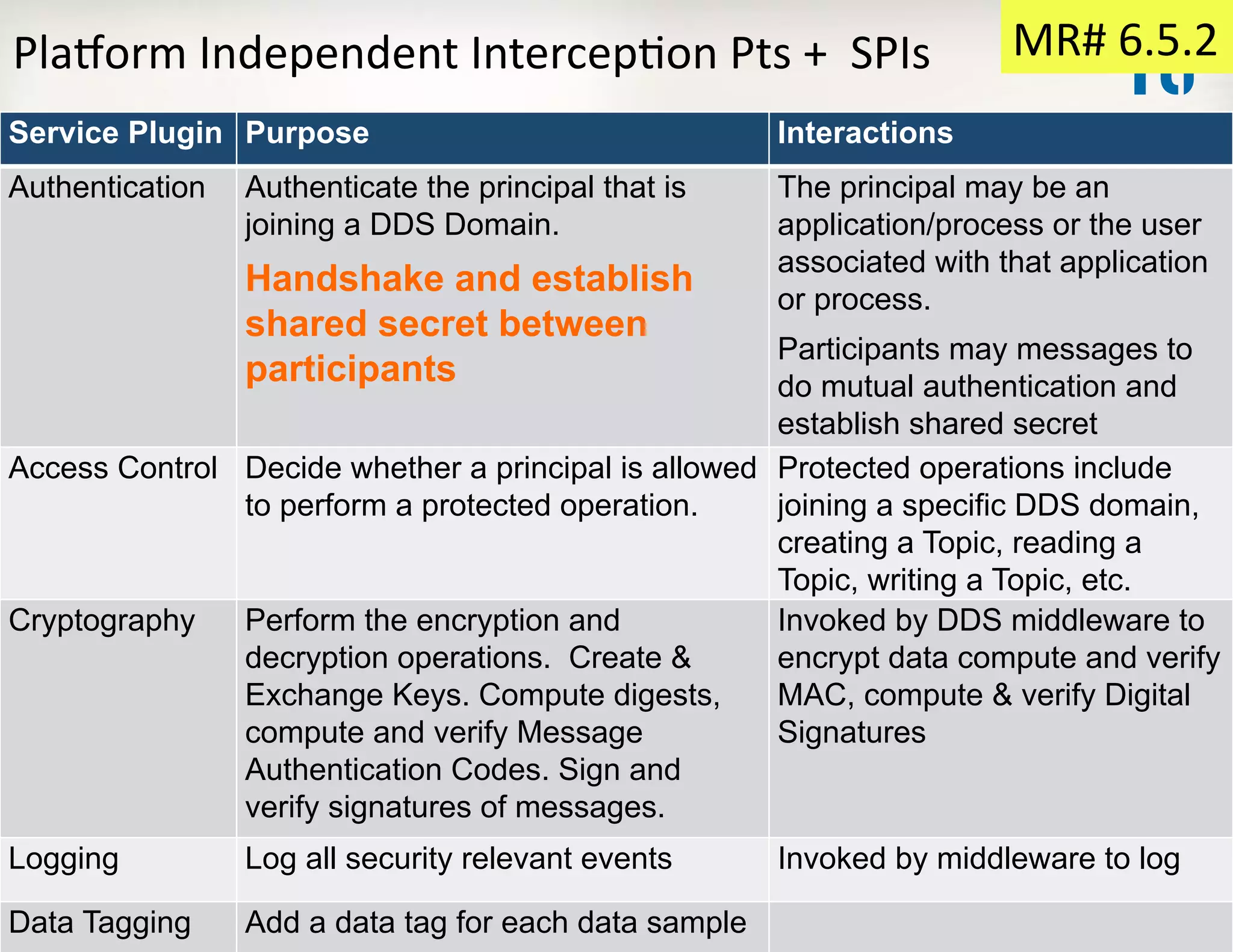
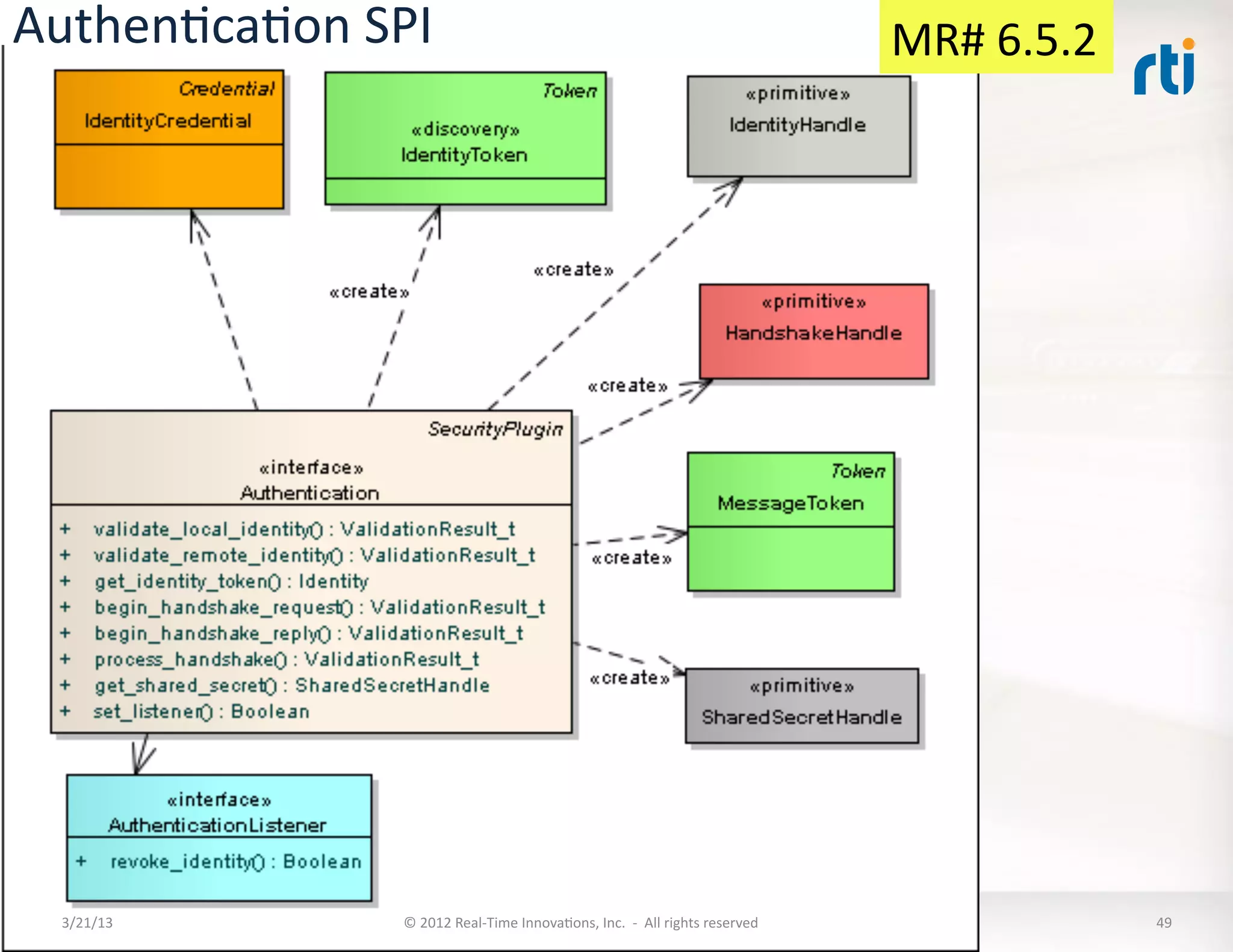
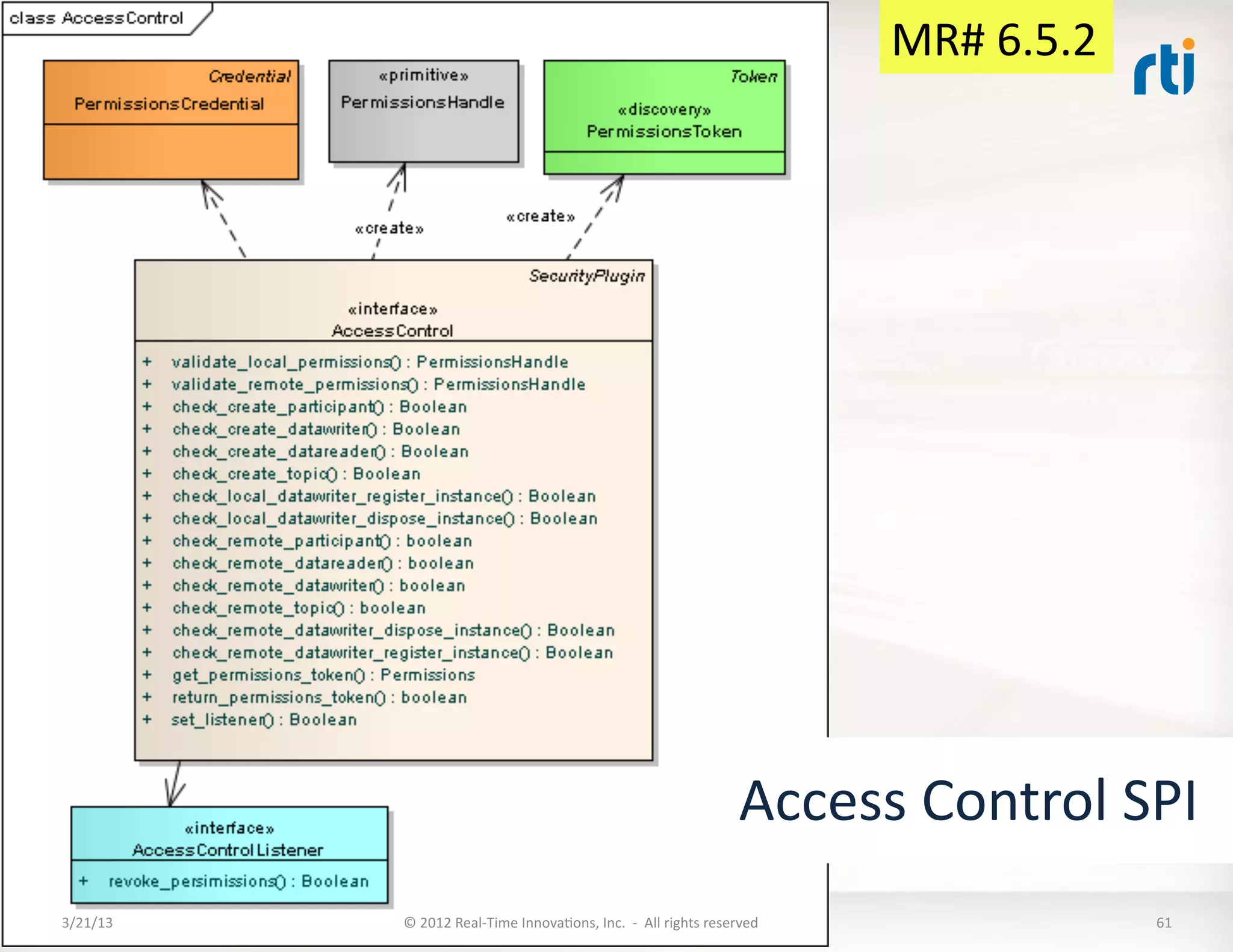
![Mandatory
Requirements
6.5.2:
Set
of
IntercepKon
Points
and
SPIs
The
Plugin
SPIs
shall
…
6.5.2.1
…
allow
applicaKons
to
exchange
credenKals
with
a
DDS
ParKcipant
[1]
exchanging
credenKals
for
authenKcaKon
[2]
delegaKon
of
authority
for
authenKcaKon
6.5.2.2
…
allow
an
external
plugin
to
perform
all
the
authorizaKon
funcKons
[1]
full
support
of
the
authorizaKon
policies
[3]
support
delegaKon
of
authority
[4]
support
delegaKon
of
authority
separately
for
each
DDS
Topic
6.5.2.3
…
allow
an
external
plugin
to
perform
all
the
tagging
and
tag-‐accessing
funcKons
6.5.2.4
…
allow
an
external
plugin
to
perform
all
the
encrypKon
and
decrypKon
funcKons
6.5.2.5
…
external
plugin
to
perform
all
the
digital
signing
and
verificaKon
funcKons
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
15](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-15-2048.jpg)




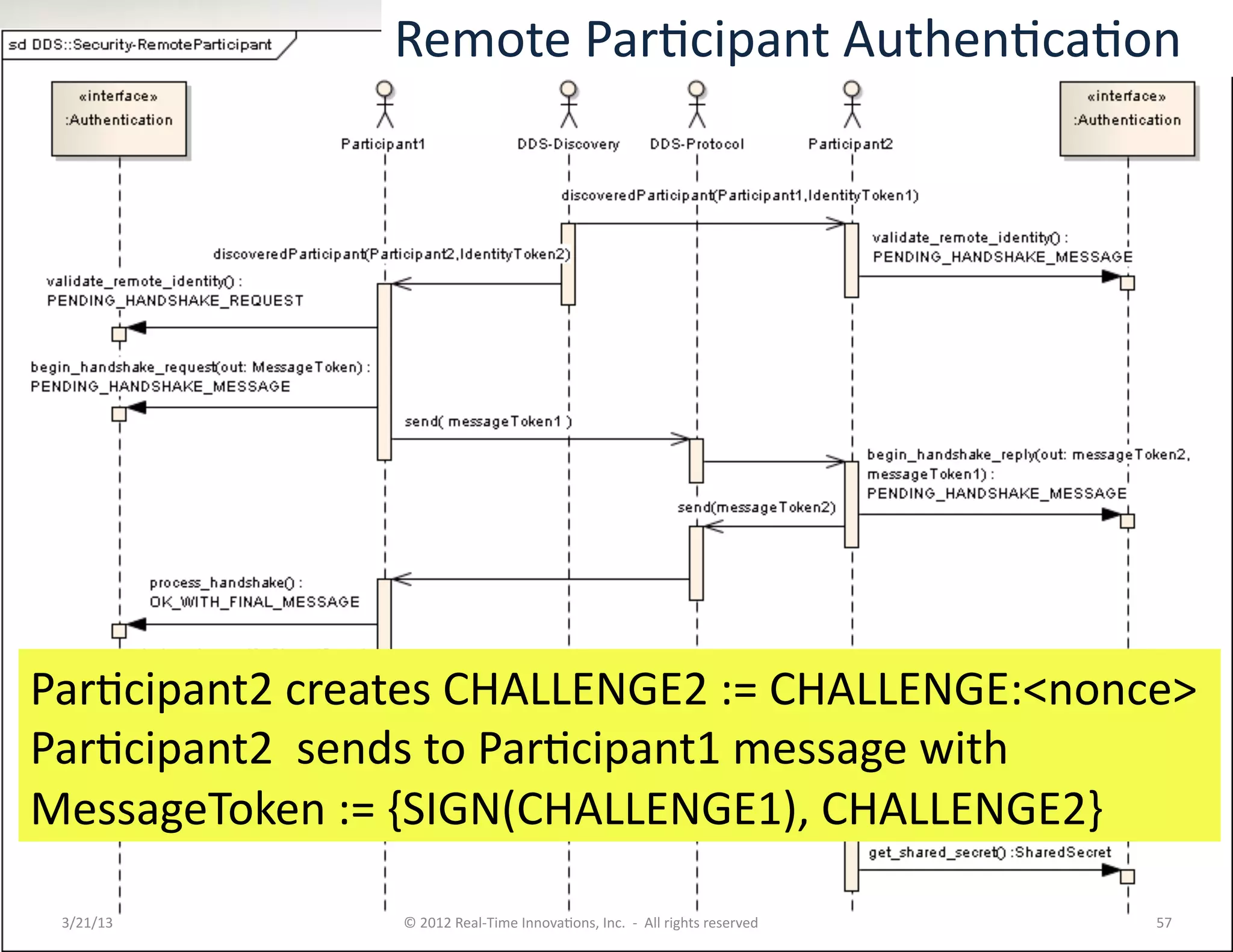
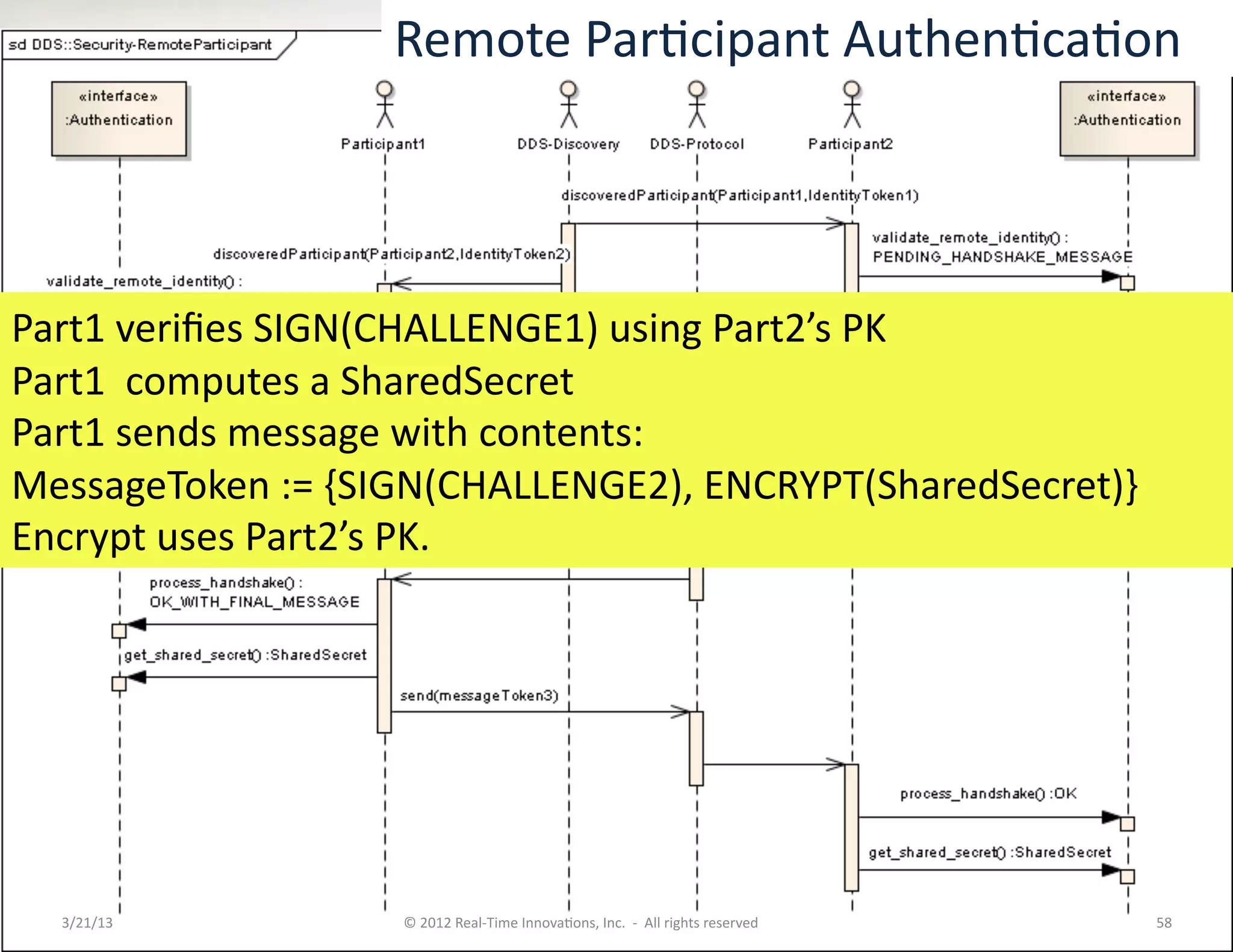
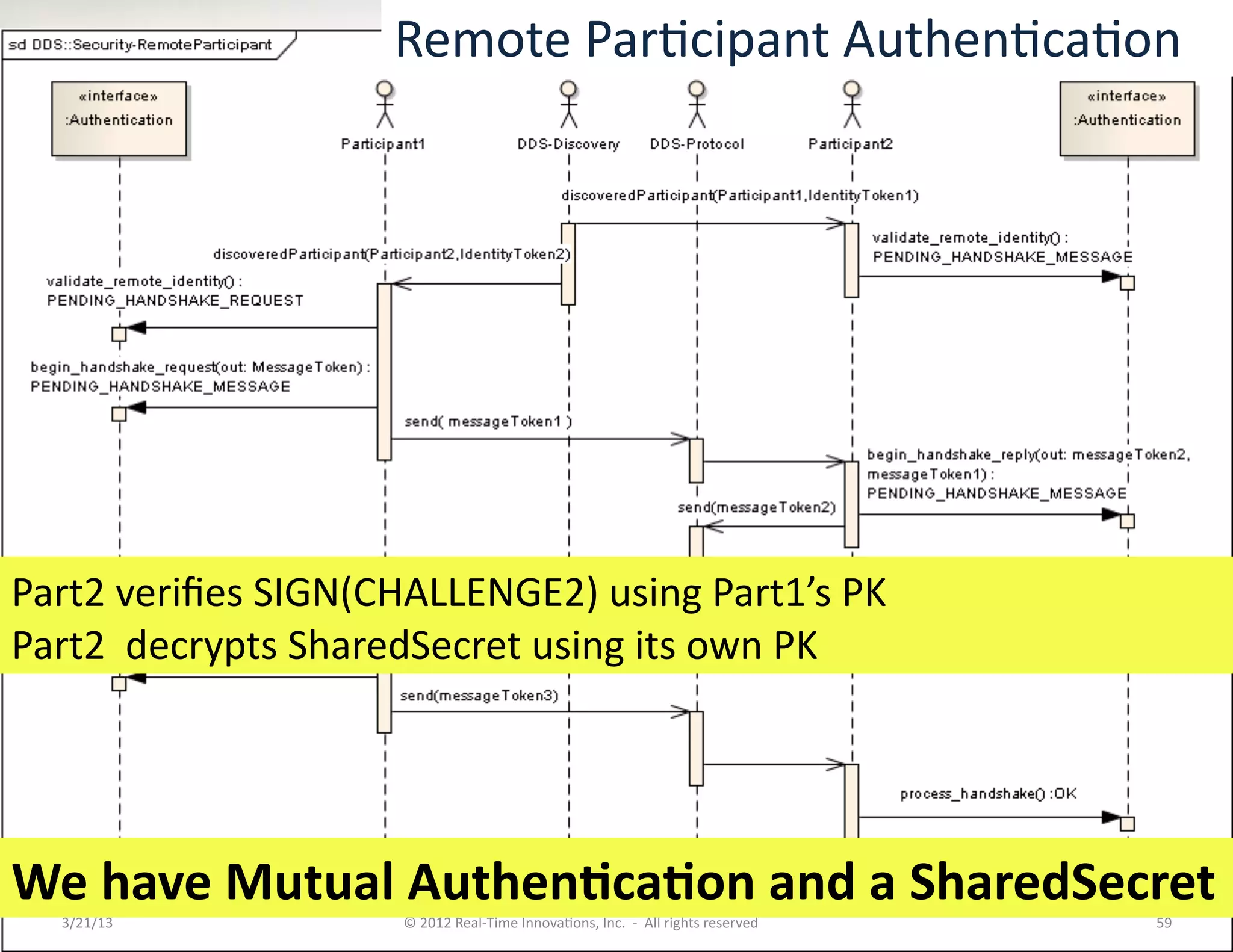
![Security
Model
Example:
UNIX
FileSystem
(simplified)
• Subjects:
Users,
specifically
processes
execuKng
on
behalf
of
a
specific
userid
• Protected
Objects:
Files
and
Directories
• Protected
OperaKons
on
Objects:
– Directory.list,
Directory.createFile,
Directory.createDir,
Directory.removeFile,
Directory.removeDir,
Directory.renameFile
– File.view,
File.modify,
File.execute
• Access
Control
Model:
– A
subject
is
given
a
userId
and
a
set
of
groupId
– Each
object
is
assigned
a
OWNER
and
a
GROUP
– Each
Object
is
given
a
combinaKon
of
READ,
WRITE,
EXECUTE
permissions
for
the
assigned
OWNER
and
GROUP
– Each
protected
operaKon
is
mapped
to
a
check,
for
example
•
File.view
is
allowed
if
and
only
if
– File.owner
==
Subject.userId
AND
File.permissions(OWNER)
includes
READ
– OR
File.group
IS-‐IN
Subject.groupId[]
AND
File.permissions(GROUP)
includes
READ
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
23](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-23-2048.jpg)

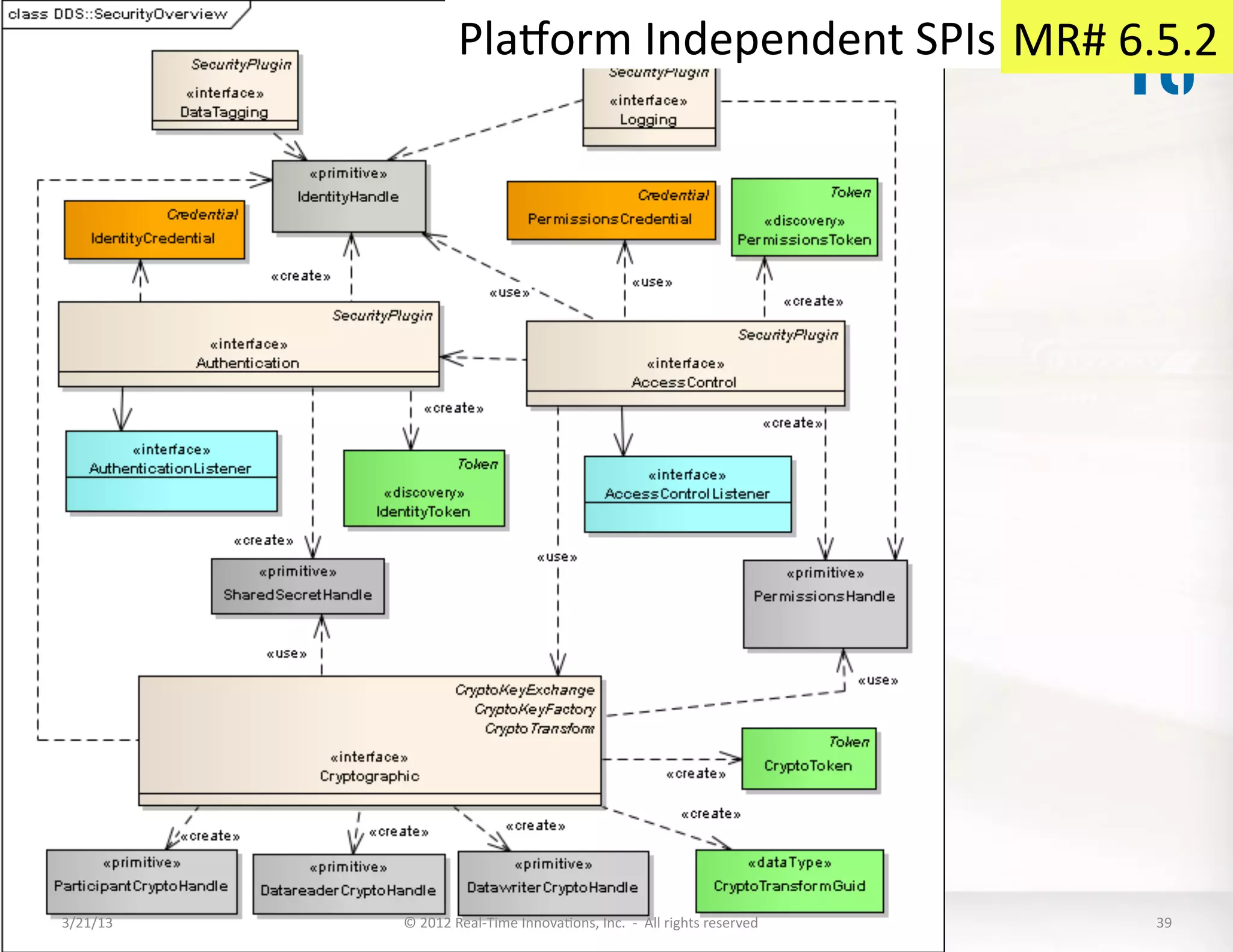
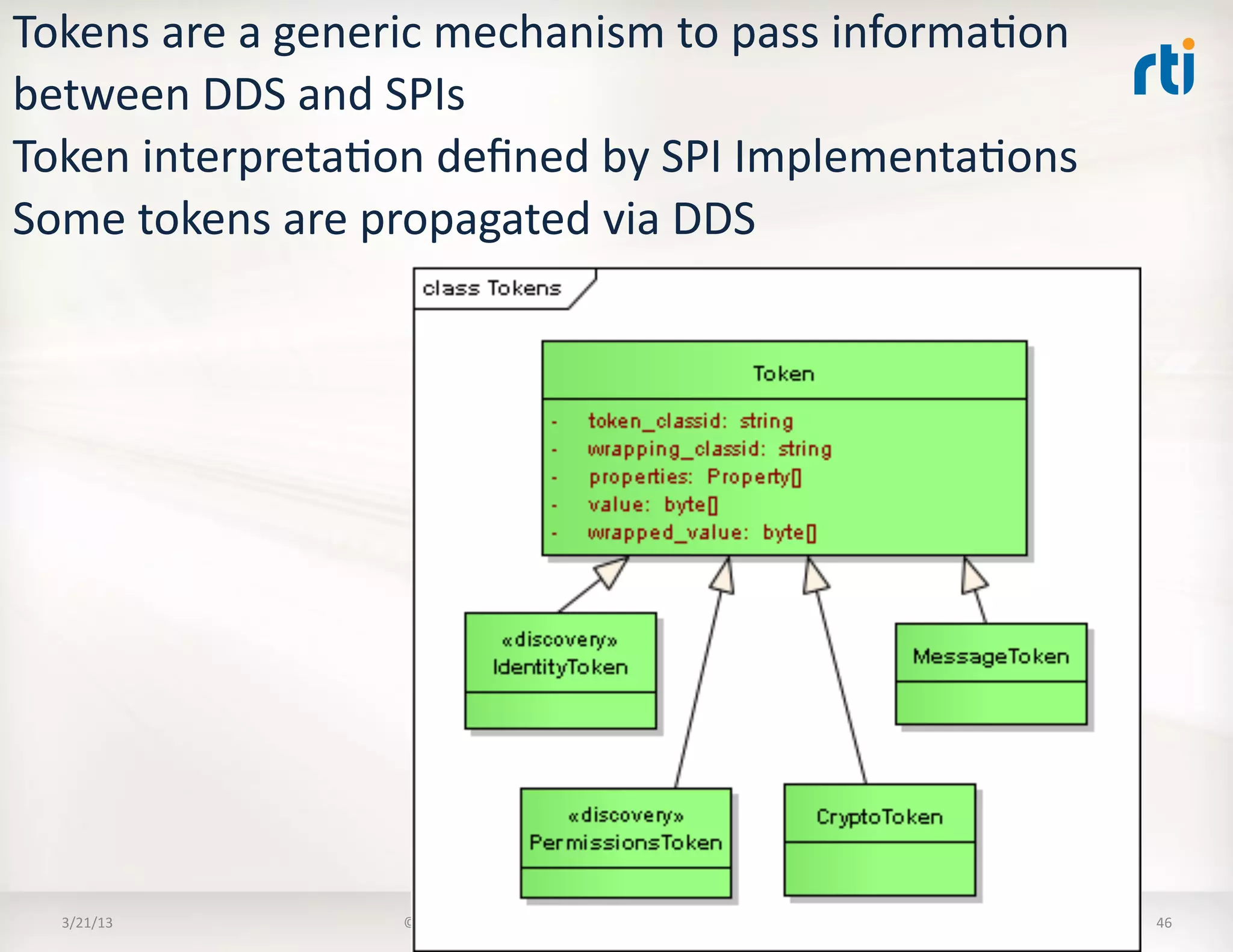
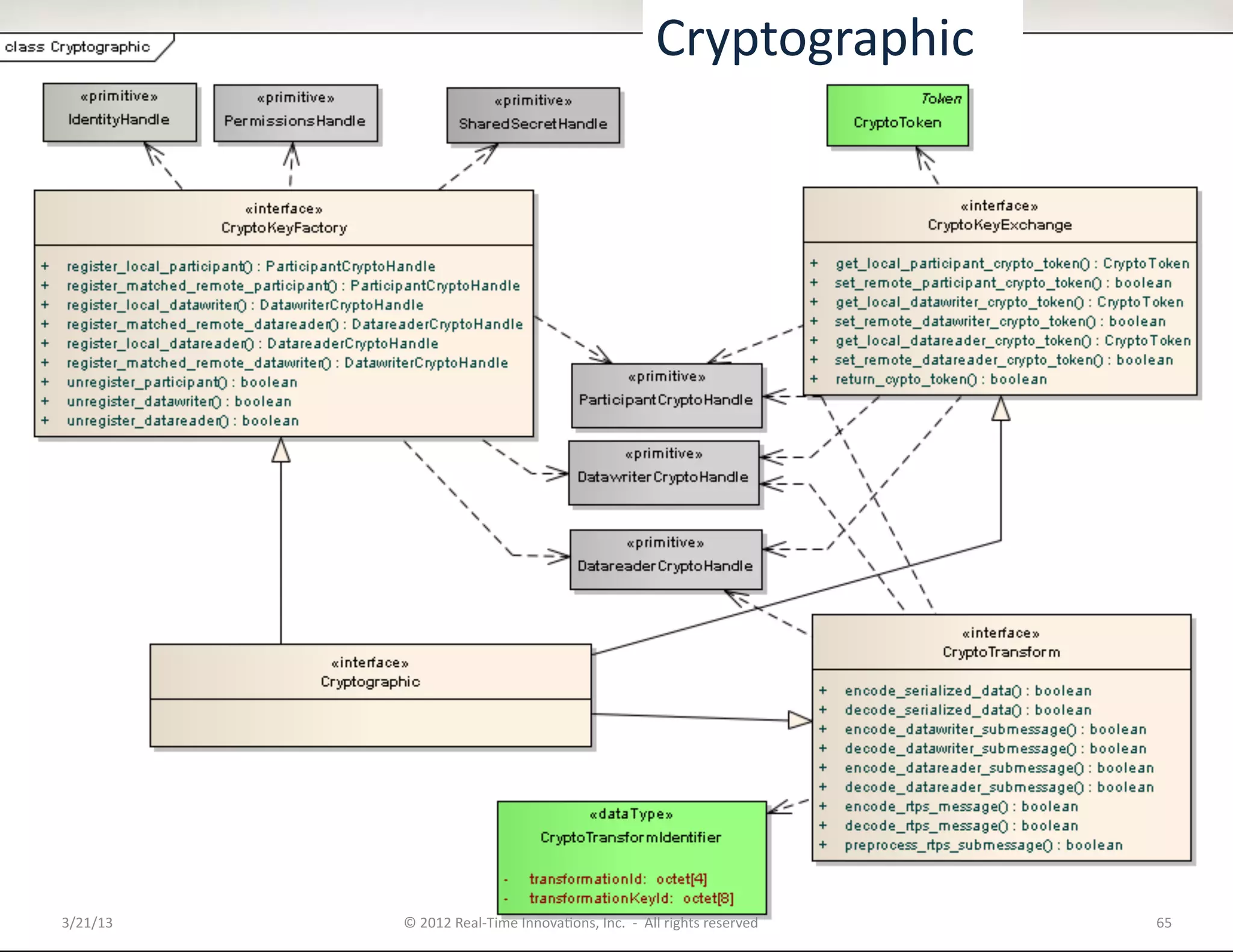
![Security
informaKon
exchanged
via
BuilKnParKcipantMessageWriter
typedef
Token
CryptoToken;
sequence<CryptoToken>
CryptoTokenSeq;
4
addiKonal
kinds:
KIND_SECURITY_AUTH_HANDSHAKE
KIND_SECURITY_PARTICIPANT_CRYPTO_TOKENS
struct
CryptoTokensMsg
{
KIND_SECURITY_DATAWRITER_CRYPTO_TOKENS
octet
sending_guid[16];
KIND_SECURITY_DATAREADER_CRYPTO_TOKENS
octet
receiving_guid[16];
CryptoTokenSeq
crypto_tokens;
};
typedef
Token
HandshakeTokenMsg;
typedef
CryptoTokensMsg
Par:cipantCryptoTokensMsg;
typedef
CryptoTokensMsg
DatawriterCryptoTokensMsg;
typedef
CryptoTokensMsg
DatareaderCryptoTokensMsg;
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
29](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-29-2048.jpg)
![BuilKnParKcipantMessageWriter
typedef
octet
GuidPrefix_t[12];
typedef
octet
Par:cipantMessageDataKind[4];
struct
Par:cipantMessageData
{
GuidPrefix_t
par:cipantGuidPrefix;
//@Key
Par:cipantMessageDataKind
kind;
//@Key
sequence<octet>
data;
};
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
30](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-30-2048.jpg)
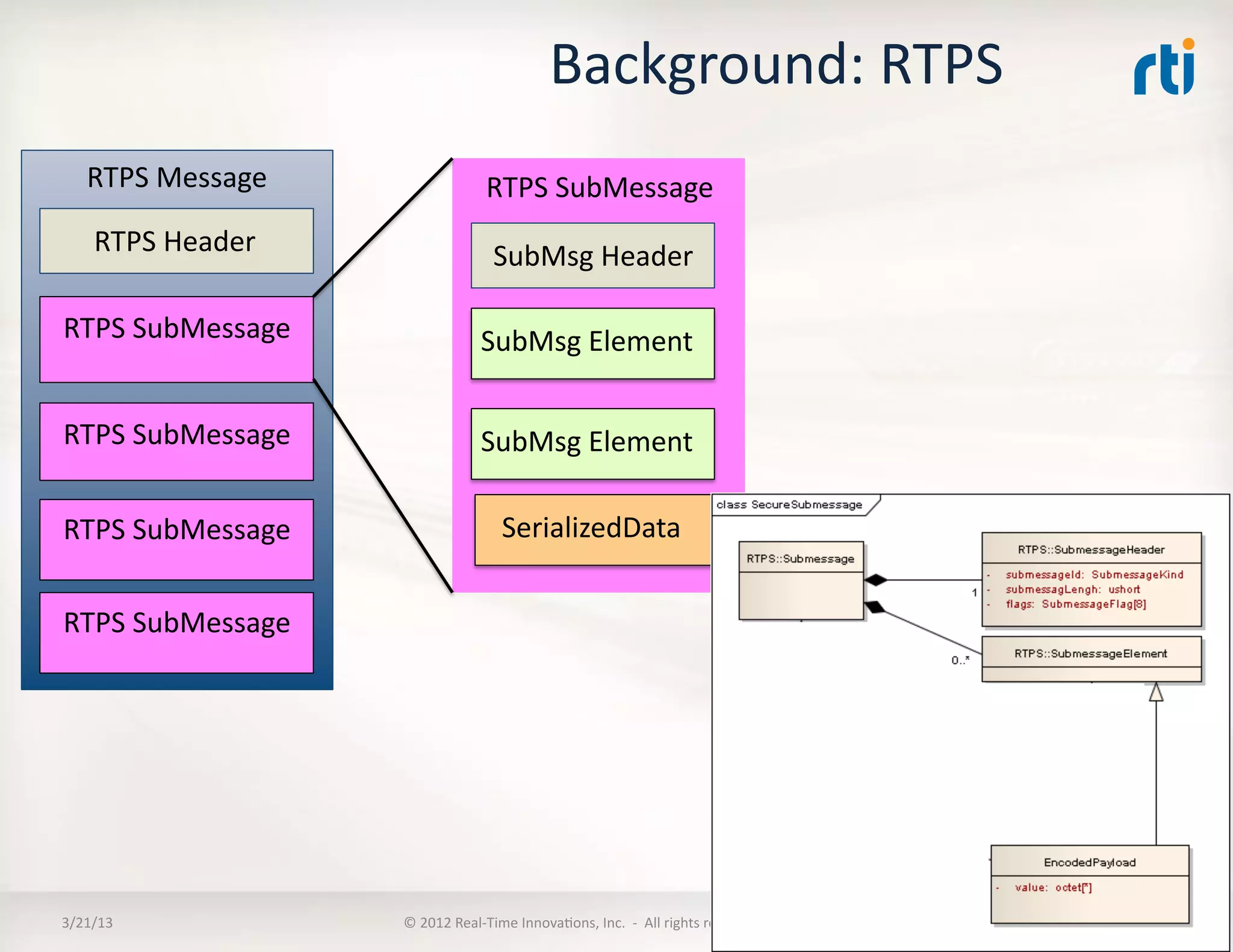
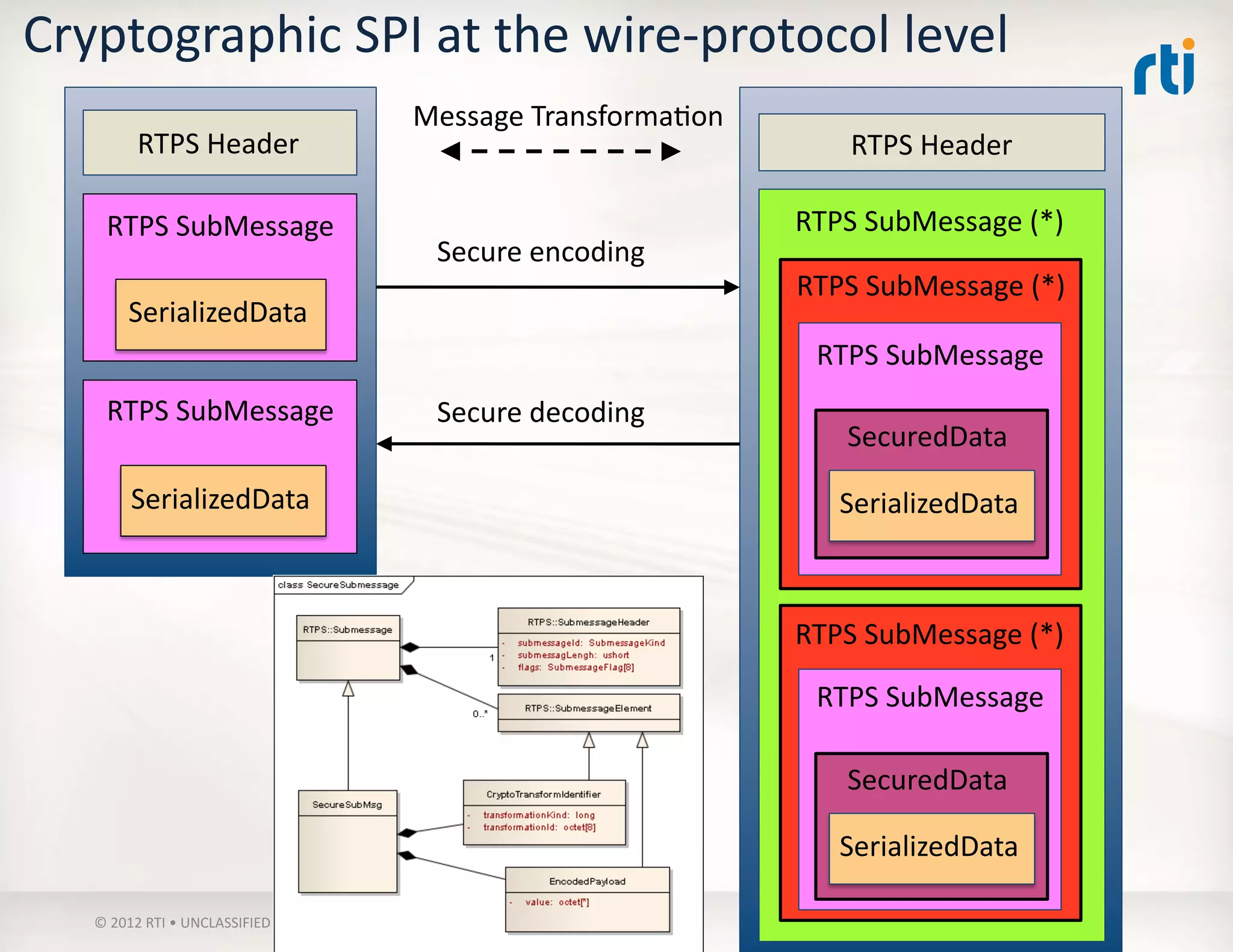
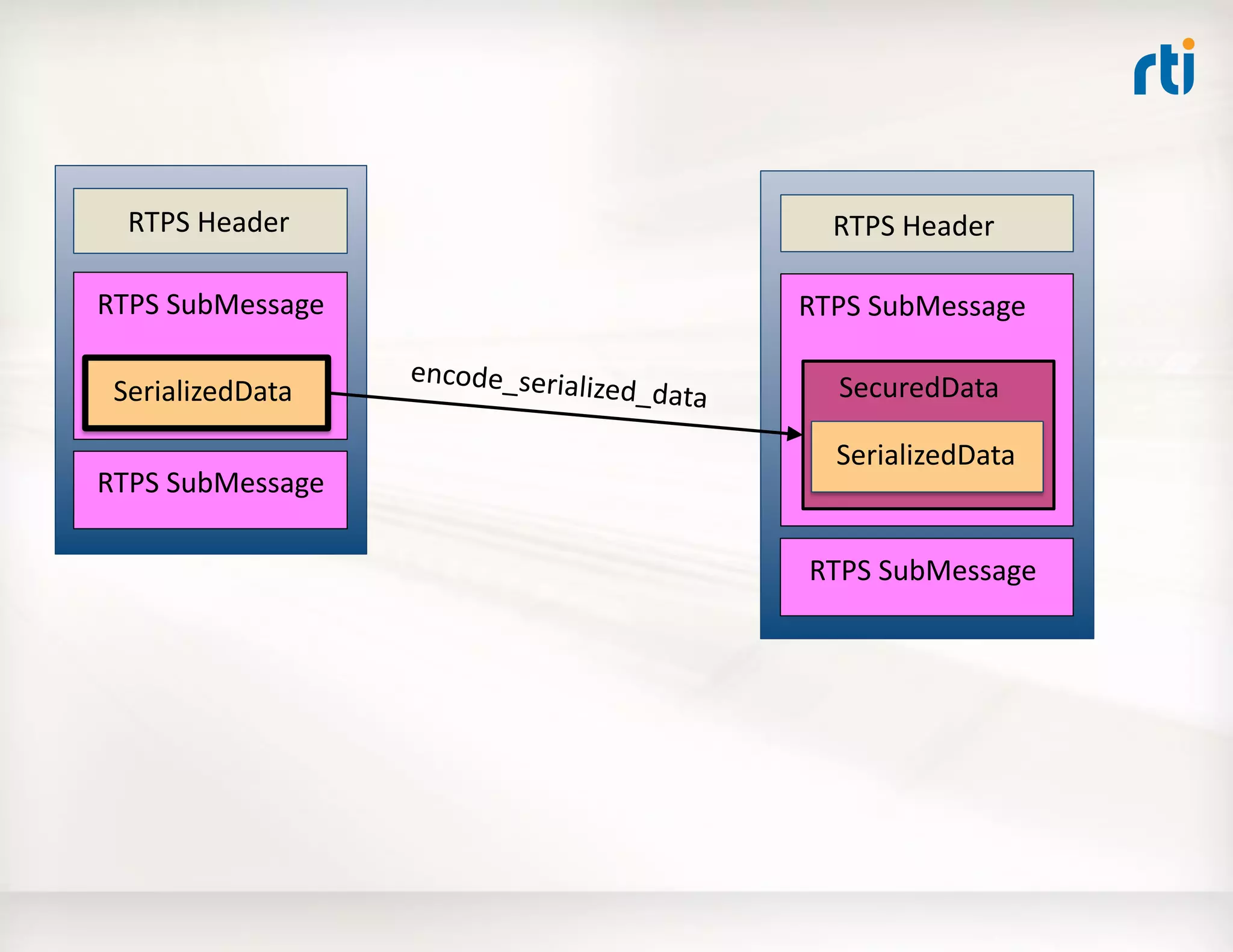
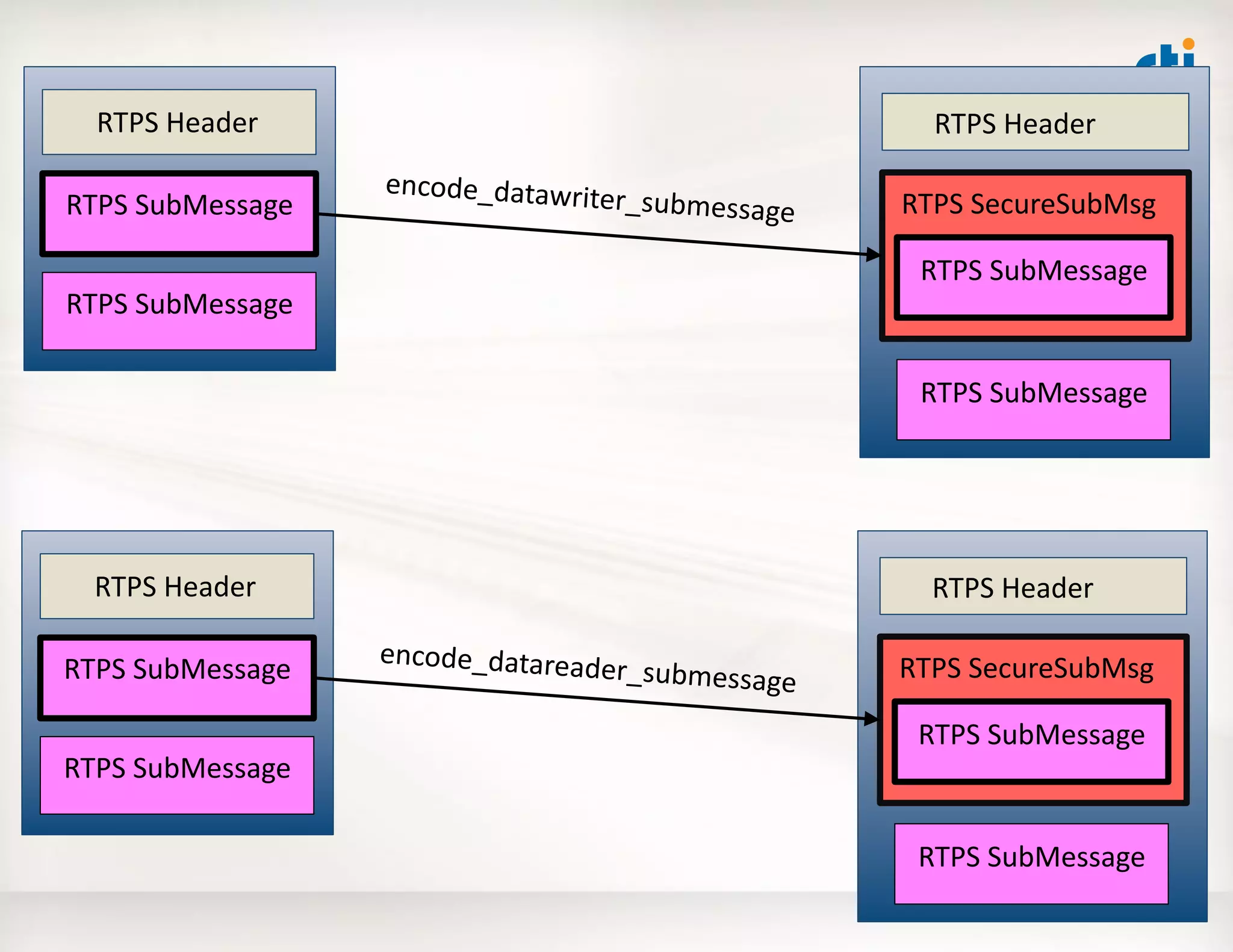
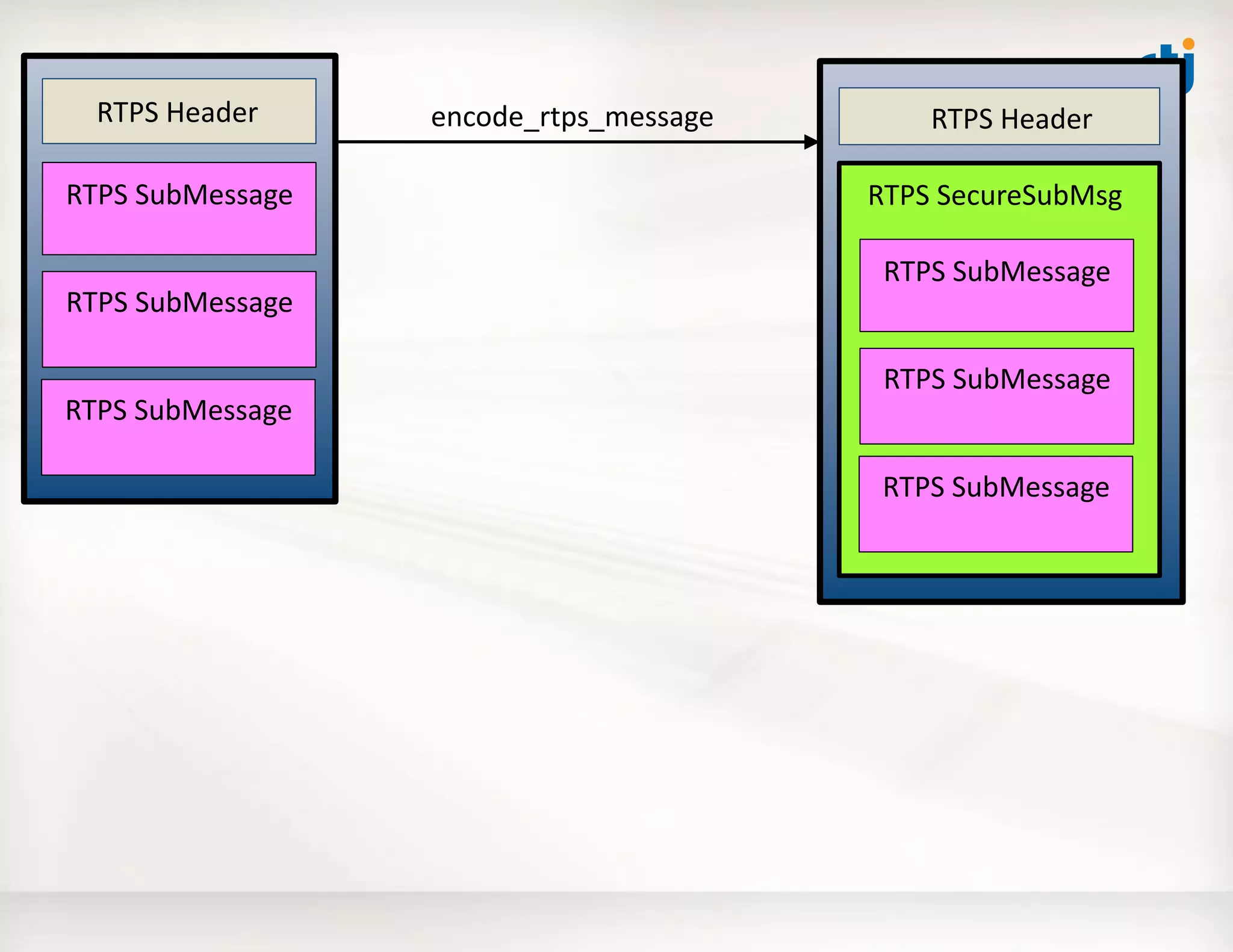
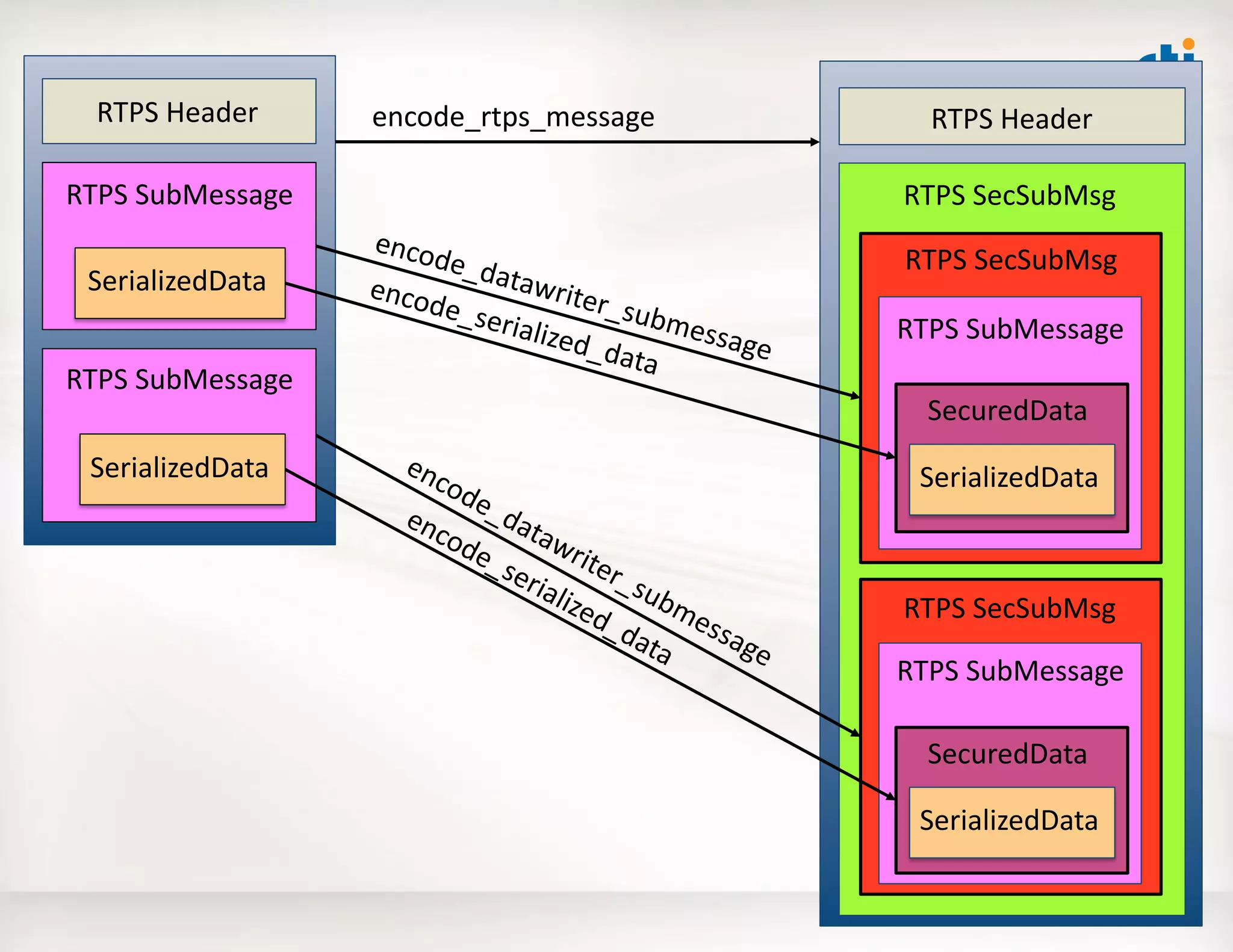
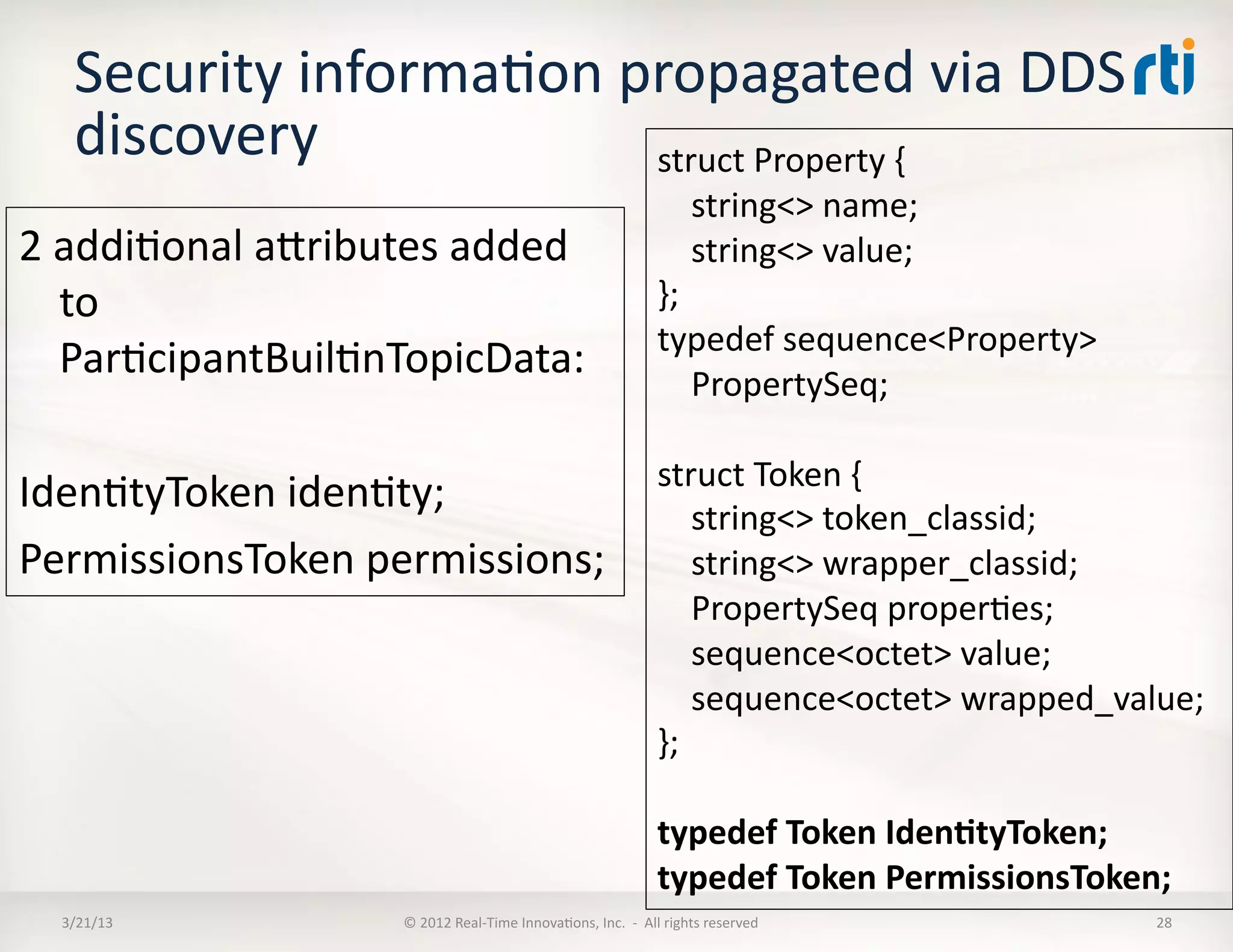
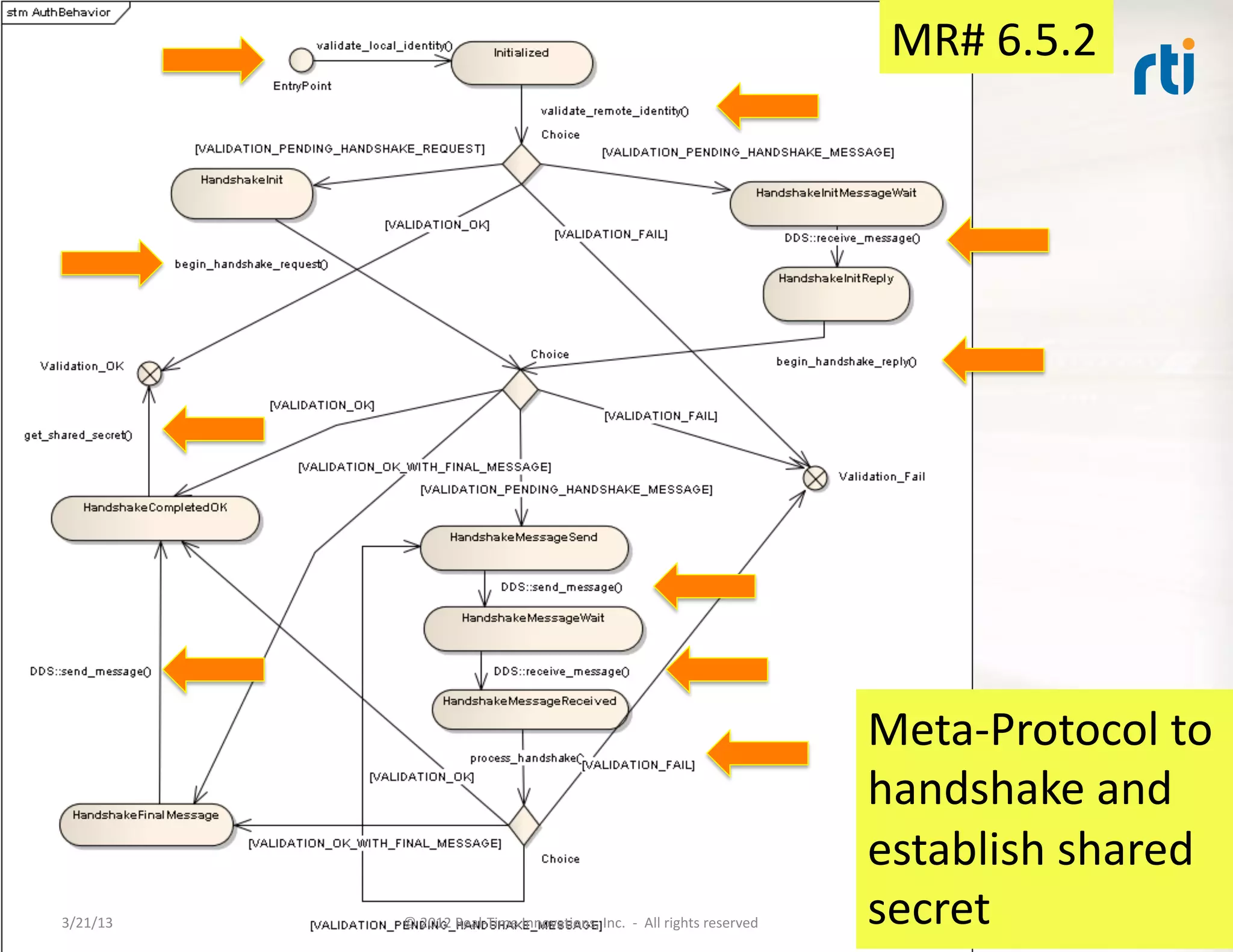
![Use
of
DDS
Interoperability
Protocol
MR#
6.5.5
• Uses:
Buil%nPar%cipantMessageWriter/Reader
– Msg
kind:
KIND_SECURITY_AUTH_HANDSHAKE
• data:
MessageToken
– Msg
kind:
KIND_SECURITY_KEY_TOKEN
• Data:
KeyToken
• Discovery
propagates
addiKonal
security
info
– Buil:nPar:cipantTopicData
• Iden:tyToken
[PID_SEC_IDENTITY_TOKEN]
• PermissionsToken
[PID_SEC_PERMISSIONS_TOKEN]
– Buil:nPublica:onTopicData
• DataTags
[PID_SEC_DATA_TAGS]
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
42](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-42-2048.jpg)








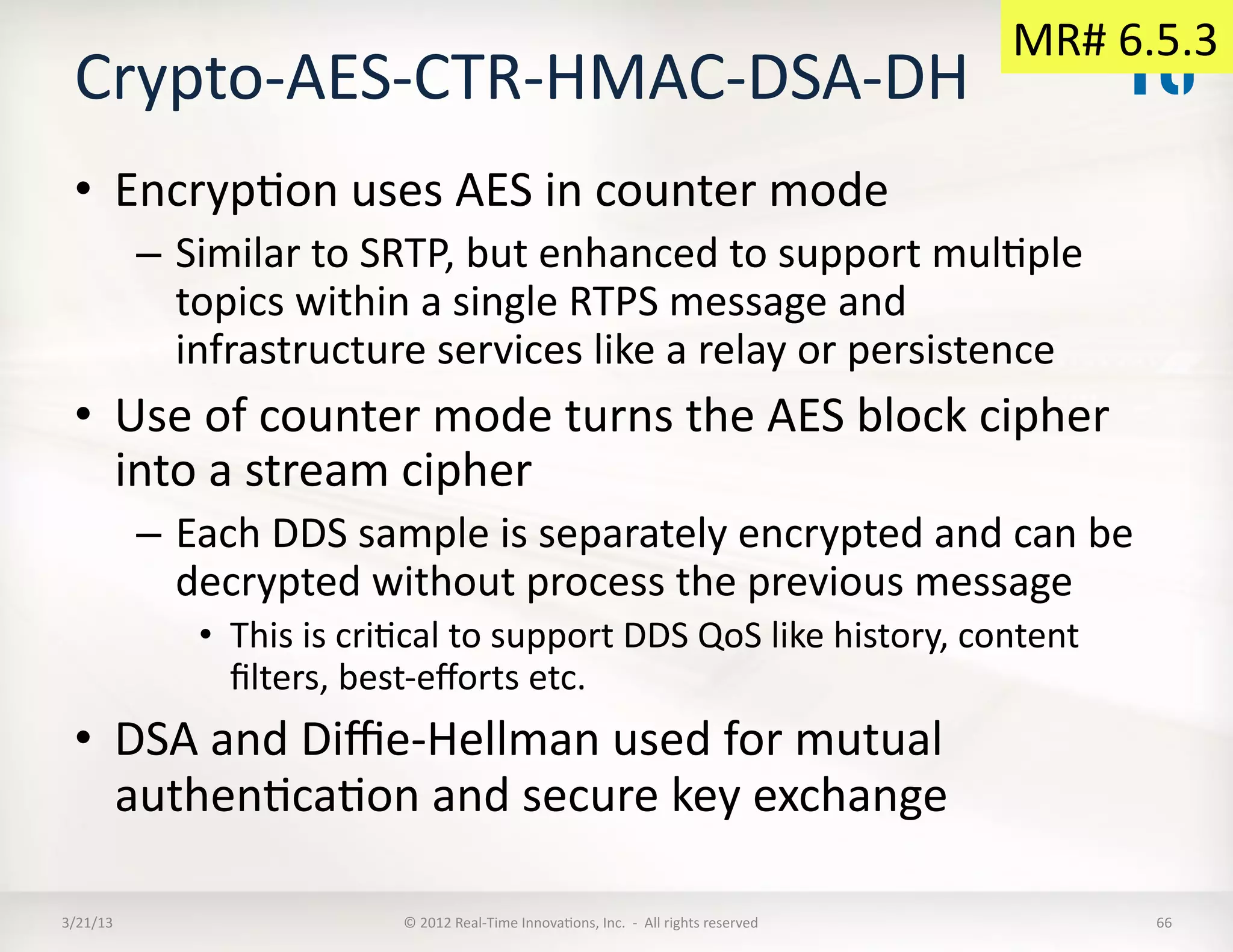
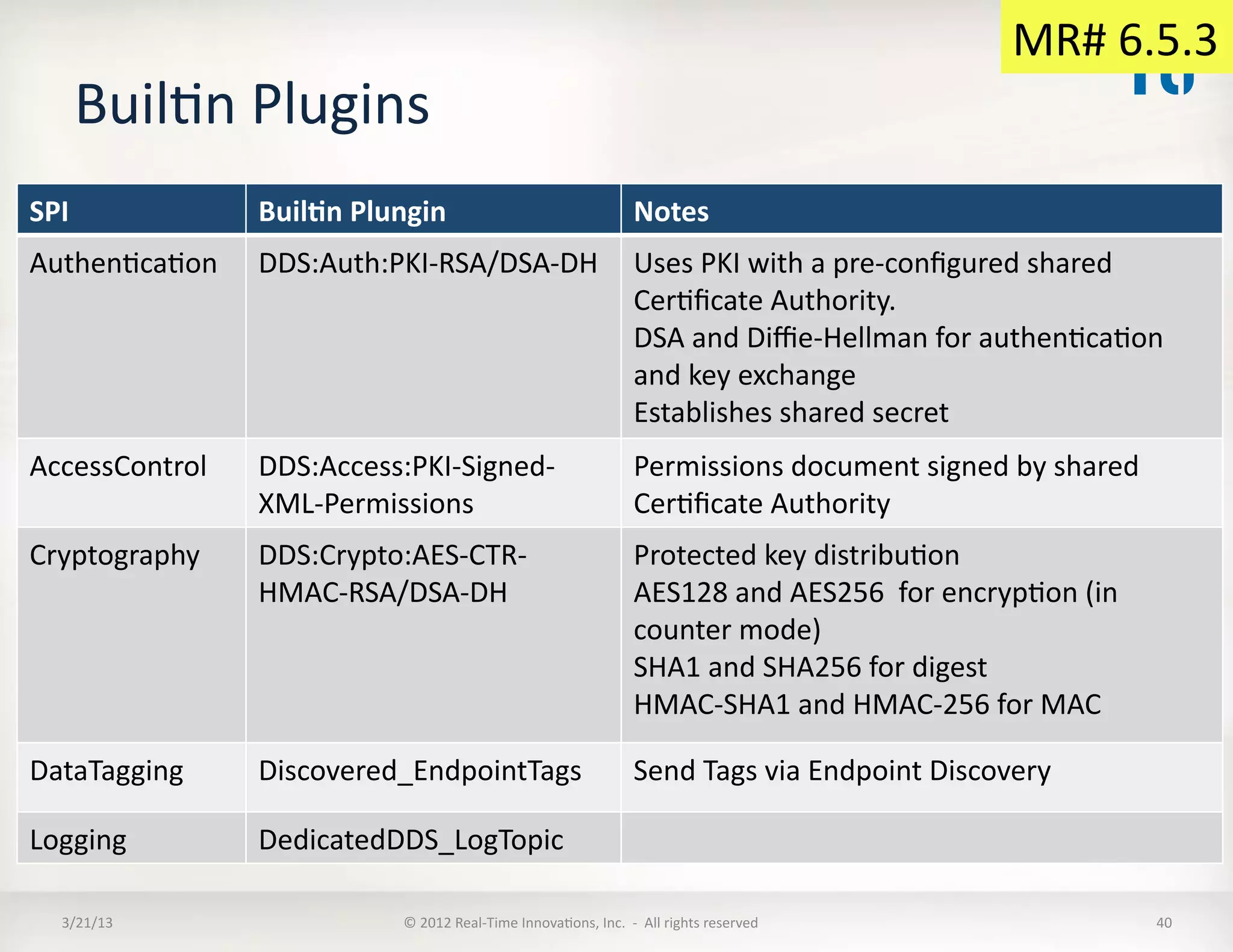
![BuilKn
DDS:Crypto-‐AES-‐CTR-‐HMAC-‐DSA-‐
DH
SPI
• Shared
secret
used
to
create
a
KeyExchangeKey
• KeyExchangeKey
used
to
send
following
Master
Key
Material
using
the
BuilKnPublicaKonWriter:
– MasterKey
– MasterSalt
– MasterHMACSalt
• Based
on
this
the
following
Key
Material
is
computed:
– SessionSalt
:=
HMAC(MasterKey,"SessionSalt"
+
MasterSalt
+
SessionId
+
0x00)
[
Truncated
to
128
bits]
– SessionKey
:=
HMAC(MasterKey,"SessionKey"
+
MasterSalt
+
SessionId
+
0x01)
– SessionHMACKey
:=
HMAC(MasterKey,"SessionHMACKey"
+
MasterHMACSalt
+
SessionId)
Note:
SessionId
goes
on
the
EncryptedMessage
Envelope
• EncrypKon
uses
AES
in
Counter
(CTR)
mode
– The
session
counter
is
sent
on
EncryptedMessage
Envelope.
3/21/13
©
2012
Real-‐Time
InnovaKons,
Inc.
-‐
All
rights
reserved
67](https://image.slidesharecdn.com/ddssecuritysubmissionmars20130310-130321105738-phpapp02/75/OMG-DDS-Security-4th-Revised-Submission-67-2048.jpg)