The document outlines the DDS Security Specification version 1.0, detailing its scope, conformance, and usage terms. It includes provisions for copyright, licensing, and security implementation guidelines, including plugin architecture and various security plugin models. The document serves as a comprehensive framework for implementing security features in DDS systems, supported by normative references and additional technical information.




















![8 DDS Security, v1.0
Data Distribution Service (DDS)
An OMG distributed data communications specification that allows Quality of Service policies to be
specified for data timeliness and reliability. It is independent of the implementation language.
Digital signature
The result of a cryptographic transformation of data that, when properly implemented with supporting
infrastructure and policy, provides the services of:
1. origin authentication
2. data integrity
3. signer non-repudiation
Extended IDL
Extended Interface Definition Language (IDL) used to describe data types in a way that can be
represented in a machine neutral format for network communications. This syntax was introduced as
part of the DDS-XTYPES specification [3].
Hashing algorithm
A one-way algorithm that maps an input byte buffer of arbitrary length to an output fixed-length byte
array in such a way that:
(a) Given the output it is computationally infeasible to determine the input.
(b) It is computationally infeasible to find any two distinct inputs that map to the same output.
Information Assurance
The practice of managing risks related to the use, processing, storage, and transmission of information
or data and the systems and processes used for those purposes.
Integrity
Protection against unauthorized modification or destruction of information.
Key management
The handling of cryptographic material (e.g., keys, Initialization Vectors) during their entire life cycle
of the keys from creation to destruction.
Message authentication code (MAC)
A cryptographic hashing algorithm on data that uses a symmetric key to detect both accidental and
intentional modifications of data.
Non-Repudiation
Assurance that the sender of data is provided with proof of delivery and the recipient is provided with
proof of the sender's identity, so neither can later deny having received or processed the data.
Public key
A cryptographic key used with a public key cryptographic algorithm that is uniquely associated with an
entity and that may be made public. The public key is associated with a private key. The public key
may be known by anyone and, depending on the algorithm, may be used to:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-22-320.jpg)









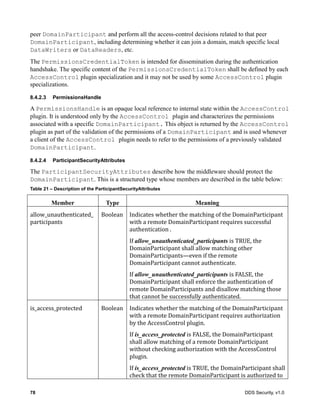
![DDS Security, v1.0 19
The DDS Security specification extends the DDS-RTPS definition of Property_t to contain the
additional boolean attribute “propagate” used to indicate whether a property is intended for local use
only or should be propagated by DDS discovery.
The DDS-Security specification uses Property_t sequences as a generic data type to configure the
security plugins, pass metadata and provide an extensible mechanism for vendors to configure the
behavior of their plugins without breaking portability or interoperability.
Property_t objects with names that start with the prefix “dds.sec.” are reserved by this
specification, including future versions of this specification. Plugin implementers can also use this
mechanism to pass metadata and configure the behavior of their plugins. In order to avoid collisions
with the value of the “name” attribute, implementers shall use property names that start with a prefix to
an ICANN domain name they own, in reverse order. For example, the prefix would be “com.acme.”
for plugins developed by a hypothetical vendor that owns the domain “acme.com”.
The names and interpretation of the expected properties shall be specified by each plugin
implementation.
Table 1 – Property_t class
Property_t
Attributes
name String
value String
propagate Boolean
7.2.1.1 IDL Representation for Property_t
The Property_t type may be used for information exchange over the network. When a
Property_t is sent over the network it shall be serialized using Extended CDR format according to
the Extended IDL representation [3] below.
@Extensibility (EXTENSIBLE_EXTENSIBILITY)
struct Property_t {
string name;
string value;
@non-serialized boolean propagate;
};
typedef sequence< Property_t > PropertySeq;
7.2.2 BinaryProperty_t
BinaryProperty_t is a data type that holds a string and an octet sequence. The string is
considered the property “name” and the octet sequence the property “value” associated with that name.
Sequences of BinaryProperty_t are used as a generic data type to configure the plugins, pass
metadata and provide an extensible mechanism for vendors to configure the behavior of their plugins
without breaking portability or interoperability.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-33-320.jpg)
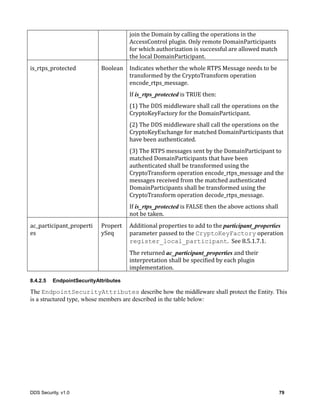
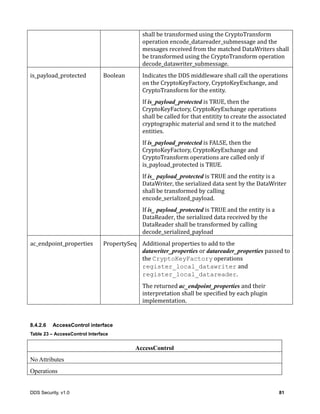
![20 DDS Security, v1.0
BinaryProperty_t also contains the boolean attribute “propagate”. Similar to Property_t
this attribute is used to indicate weather the corresponding binary property is intended for local use
only or shall be propagated by DDS discovery.
BinaryProperty_t objects with a “name” attribute that start with the prefix “dds.sec.” are
reserved by this specification, including future versions of this specification.
Plugin implementers may use this mechanism to pass metadata and configure the behavior of their
plugins. In order to avoid collisions with the value of the “name”, attribute implementers shall use
property names that start with a prefix to an ICANN domain name they own, in reverse order. For
example, the prefix would be “com.acme.” for plugins developed by a hypothetical vendor that owns
the domain “acme.com”.
The valid values of the “name” attribute and the interpretation of the associated “value” shall be
specified by each plugin implementation.
Table 2 – BinaryProperty_t class
BinaryProperty_t
Attributes
name String
value OctetSeq
propagate Boolean
7.2.2.1 IDL Representation for BinaryProperty_t
The BinaryProperty_t type may be used for information exchange over the network. When a
BinaryProperty_t is sent over the network, it shall be serialized using Extended CDR format
according to the Extended IDL representation [3] below.
@Extensibility (EXTENSIBLE_EXTENSIBILITY)
struct BinaryProperty_t {
string name;
OctetSeq value;
@non-serialized boolean propagate;
};
typedef sequence< BinaryProperty_t > BinaryPropertySeq;
7.2.3 DataHolder
DataHolder is a data type used to hold generic data. It contains various attributes used to store data
of different types and formats. DataHolder appears as a building block for other types, such as
Token and GenericMessageData.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-34-320.jpg)
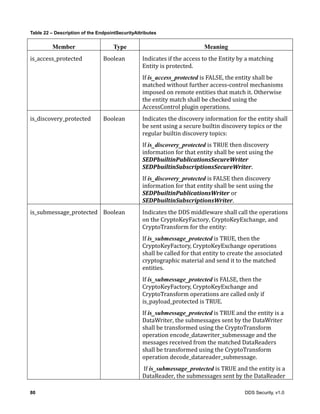
![DDS Security, v1.0 21
Table 3 – DataHolder class
DataHolder
Attributes
class_id String
properties PropertySeq
binary_properties BinaryPropertySeq
7.2.3.1 IDL representation for DataHolder
The DataHolder type may be used for information exchange over the network. When a
DataHolder is sent over the network, it shall be serialized using Extended CDR format according to
the Extended IDL representation [3] below.
@Extensibility (EXTENSIBLE_EXTENSIBILITY)
struct DataHolder {
string class_id;
PropertySeq properties;
BinaryPropertySeq binary_properties;
};
typedef sequence<DataHolder> DataHolderSeq;
7.2.4 Token
The Token class provides a generic mechanism to pass information between security plugins using
DDS as the transport. Token objects are meant for transmission over the network using DDS either
embedded within the builtin topics sent via DDS discovery or via special DDS Topic entities defined in
this specification.
The Token class is structurally identical to the DataHolder class and therefore has the same
structure for all plugin implementations. However, the contents and interpretation of the Token
objects shall be specified by each plugin implementation.
There are multiple specializations of the Token class. They all share the same format, but are used for
different purposes. This is modeled by defining specialized classes.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-35-320.jpg)
![22 DDS Security, v1.0
Figure 3 – Token Model
7.2.4.1 Attribute: class_id
When used as a Token class, the class_id attribute in the DataHolder identifies the kind of Token.
Strings with the prefix “dds.sec.” are reserved for this specification, including future versions of
the specification. Implementers of this specification can use this attribute to identify non-standard
tokens. In order to avoid collisions, the class_id they use shall start with a prefix to an ICANN domain
name they own, using the same rules specified in 7.2.1 for property names.
7.2.4.2 IDL Representation for Token and Specialized Classes
The Token class is used to hold information exchanged over the network. When a Token is sent over
the network, it shall be serialized using Extended CDR format according to the Extended IDL
representation below:
typedef DataHolder Token;
typedef Token HandshakeMessageToken;
typedef Token IdentityToken;
typedef Token PermissionsToken;
typedef Token AuthenticatedPeerCredentialToken;
typedef Token PermissionsCredentialToken;
typedef Token CryptoToken;
typedef Token ParticipantCryptoToken;
typedef Token DatawriterCryptoToken;
typedef Token DatareaderCryptoToken;
typedef sequence<HandshakeMessageToken> HandshakeMessageTokenSeq;
typedef sequence<CryptoToken> CryptoTokenSeq;
typedef CryptoTokenSeq ParticipantCryptoTokenSeq;
class Tokens
CryptoToken
Token
«discovery»
IdentityToken
«discovery»
PermissionsToken
MessageTokenPermissionsCredentialToken
DataHolder
- class_id: string
- string_properties: Property[]
- binary_properties: BinaryProperty[]
- string_values: string[]
- binary_value1: byte[]
- binary_value2: byte[]
- longlong_values: LongLong[]](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-36-320.jpg)

![24 DDS Security, v1.0
purpose data type called ParticipantGenericMessage, which is defined by the following
extended IDL:
typedef octet[16] BuiltinTopicKey_t;
@Extensibility (EXTENSIBLE_EXTENSIBILITY)
struct MessageIdentity {
BuiltinTopicKey_t source_guid;
long long sequence_number;
};
typedef string<> GenericMessageClassId;
@Extensibility (EXTENSIBLE_EXTENSIBILITY)
struct ParticipantGenericMessage {
/* target for the request. Can be GUID_UNKNOWN */
MessageIdentity message_identity;
MessageIdentity related_message_identity;
BuiltinTopicKey_t destination_participant_key;
BuiltinTopicKey_t destination_endpoint_key;
BuiltinTopicKey_t source_endpoint_key;
GenericMessageClassId message_class_id;
DataHolderSeq message_data;
};
7.2.7 Additional DDS Return Code: NOT_ALLOWED_BY_SEC
The DDS specification defines a set of return codes that may be returned by the operations on the DDS
API (see sub clause 7.1.1 of the DDS specification).
The DDS Security specification add an additional return code NOT_ALLOWED_BY_SEC, which
shall be returned by any operation on the DDS API that fails because the security plugins do not allow
it.
7.3 Securing DDS Messages on the Wire
OMG DDS uses the Real-Time Publish-Subscribe (RTPS) on-the-wire protocol [2] for communicating
data. The RTPS protocol includes specifications on how discovery is performed, the metadata sent
during discovery, and all the protocol messages and handshakes required to ensure reliability. RTPS
also specifies how messages are put together.
7.3.1 RTPS Background (Non-Normative)
In a secure system where efficiency and message latency are also considerations, it is necessary to
define exactly what needs to be secured. Some applications may require only the data payload to be
confidential and it is acceptable for the discovery information, as well as, the reliability meta-traffic
(HEARTBEATs, ACKs, NACKs, etc.) to be visible, as long as it is protected from modification. Other
applications may also want to keep the metadata (sequence numbers, in-line QoS) and/or the reliability
traffic (ACKs, NACKs, HEARTBEATs) confidential. In some cases, the discovery information (who is
publishing what and its QoS) may need to be kept confidential as well.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-38-320.jpg)

![DDS Security, v1.0 27
To support different deployment scenarios, this specification uses a “message transformation”
mechanism that gives the Security Plugin Implementations fine-grain control over which parts of the
RTPS Message need to be encrypted and/or signed.
The Message Transformation performed by the Security Plugins transforms an RTPS Message into
another RTPS Message. A new RTPS Header may be added and the content of the original RTPS
Message may be encrypted, protected by a Secure Message Authentication Code (MAC), and/or
signed. The MAC and/or signature can also include the RTPS Header to protect its integrity.
7.3.3 Constraints of the DomainParticipant BuiltinTopicKey_t (GUID)
The DDS and the DDS Interoperability Wire Protocol specifications state that DDS
DomainParticipant entities are identified by a unique 16-byte GUID.
This DomainParticipant GUID is communicated as part of DDS Discovery in the
ParticipantBuiltinTopicData in the attribute participant_key of type
BuiltinTopicKey_t defined as:
typedef octet BuiltinTopicKey_t[16];
Allowing a DomainParticipant to select its GUID arbitrarily would allow hostile applications to
perform a “squatter” attack, whereby a DomainParticipant with a valid certificate could
announce itself into the DDS Domain with the GUID of some other DomainParticipant. Once
authenticated the “squatter” DomainParticipant would preclude the real DomainParticipant
from being discovered, because its GUID would be detected as a duplicate of the already existing
one.
To prevent the aforementioned “squatter” attack, this specification constrains the GUID that can be
chosen by a DomainParticipant, so that it is tied to the Identity of the DomainParticipant.
This is enforced by the Authentication plugin.
7.3.4 Mandatory use of the KeyHash for encrypted messages
The RTPS Data and DataFrag submessages can optionally contain the KeyHash as an inline Qos
(see sub clause 9.6.3.3, titled “KeyHash (PID_KEY_HASH)”) of the DDS-RTPS specification version
2.3. In this sub clause it is specified that when present, the key hash shall be computed either as the
serialized key or as an MD5 on the serialized key.
The key values are logically part of the data and therefore in situations where the data is considered
sensitive the key should also be considered sensitive.
For this reason the DDS Security specification imposes additional constraints in the use of the key
hash. These constraints apply only to the Data or DataFrag RTPS SubMessages where the
SerializedPayload SubmessageElement is encrypted by the operation
encode_serialized_payload of the CryptoTransform plugin:
(1) The KeyHash shall be included in the Inline Qos.
(2) The KeyHash shall be computed as the 128 bit MD5 Digest (IETF RFC 1321) applied to the
CDR Big- Endian encapsulation of all the Key fields in sequence. Unlike the rule stated in sub
clause 9.6.3.3 of the DDS specification, the MD5 hash shall be used regardless of the
maximum-size of the serialized key.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-41-320.jpg)


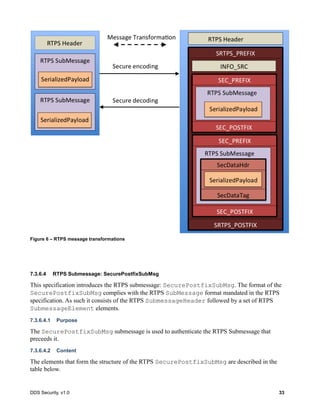
![30 DDS Security, v1.0
Figure 5 – Secure Submessage and Secured Payload Model
7.3.6.2.1 Purpose
The SecureSubMsg submessage is used to wrap one or more regular RTPS submessages in such a
way that their contents are secured via encryption, message authentication, and/or digital signatures.
7.3.6.2.2 Content
The elements that form the structure of the RTPS SecureSubMsg are described in the table below.
class SecureSubmessages
RTPS::SubmessageHeader
- submessageId: SubmessageKind
- submessagLengh: ushort
- flags: SubmessageFlag[8]
SecureBodySubMsg
RTPS::Submessage
«interface»
CryptoTransformIdentifier
- transformationKind: long
- transformationId: octet[8]
SecureDataBody
RTPS::SubmessageElement
SecurePrefixSubMsg
SecurePostfixSubMsg
SecureRTPSPrefixSubMsg
SecureRTPSPostfixSubMsg
SecureDataHeader
- transformationId: CryptoTransformIdentifier
- value: octet[*]
SecureDataTag
- common_mac: char[]
- receiver_specific_macs: ReceiverSpecificMAC[]
1
0..*
«use»
«use»](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-44-320.jpg)
![32 DDS Security, v1.0
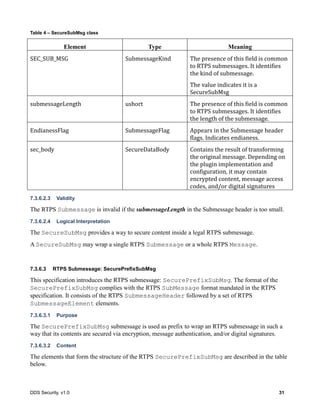
Table 5 – SecurePrefixSubMsg class
Element Type Meaning
SEC_PREFIX SubmessageKind The presence of this field is common to RTPS
submessages. It identifies the kind of
submessage.
The value indicates it is a SecurePrefixSubMsg
submessageLength ushort The presence of this field is common to RTPS
submessages. It identifies the length of the
submessage.
EndianessFlag SubmessageFlag Appears in the Submessage header flags.
Indicates endianess.
transformation_id CryptoTransformIdentifier Identfies the kind of transformation performed
on the RTPS Sububmessage that follows it.
plugin_sec_header octet[] Provides further information on the
transformation performed. The contents are
specific to the Plugin Implementation and the
value of the transformation_id
7.3.6.3.3 Validity
The RTPS Submessage is invalid if the submessageLength in the Submessage header is too small.
7.3.6.3.4 Logical Interpretation
The SecurePrefixSubMsg provides a way to prefix secure content inside a legal RTPS
submessage.
A SecurePrefixSubMsg shall be followed by a single RTPS Submessage which itself shall be
followed by a SecurePostfixSubMsg.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-46-320.jpg)
![34 DDS Security, v1.0
Table 6 – SecurePostfixSubMsg class
Element Type Meaning
SEC_POSTFIX SubmessageKind The presence of this field is common to RTPS
submessages. It identifies the kind of submessage.
The value indicates it is a SecurePostfixSubMsg.
submessageLength ushort The presence of this field is common to RTPS
submessages. It identifies the length of the
submessage.
EndianessFlag SubmessageFlag Appears in the Submessage header flags. Indicates
endianess.
plugin_sec_tag octet[] Provides information on the results of the
transformation performed, typically a list of
authentication tags. The contents are specific to the
Plugin Implementation and the value of the
transformation_id contained on the related
SecurePrefixSubMsg.
7.3.6.4.3 Validity
The RTPS Submessage is invalid if the submessageLength in the Submessage header is too small.
The RTPS Submessage is invalid if there is no SecurePrefixSubMsg. Immediately before the
RTPS submessage that preceeds the SecurePostfixSubMsg. This SecurePrefixSubMsg is
referred to as the related the SecurePrefixSubMsg.
7.3.6.4.4 Logical Interpretation
The SecurePostfixSubMsg provides a way to authenticate the validity and origin of the RTPS
SubMessage that preceeds the SecurePrefixSubMsg. The Cryptographic transformation applied is
identified in the related SecurePrefixSubMsg.
7.3.6.5 RTPS Submessage: SecureRTPSPrefixSubMsg
This specification introduces the RTPS submessage: SecureRTPSPrefixSubMsg. The format of
the SecurePrefixSubMsg complies with the RTPS SubMessage format mandated in the RTPS
specification. It consists of the RTPS SubmessageHeader followed by a set of RTPS
SubmessageElement elements.
7.3.6.5.1 Purpose
The SecureRTPSPrefixSubMsg submessage is used as prefix to wrap a complete RTPS message
in such a way that its contents are secured via encryption, message authentication, and/or digital
signatures.
7.3.6.5.2 Content
The elements that form the structure of the RTPS SecureRTPSPrefixSubMsg are described in the
table below.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-48-320.jpg)
![DDS Security, v1.0 35
Table 7 – SecureRTPSPrefixSubMsg class
Element Type Meaning
SRTPS_PREFIX SubmessageKind The presence of this field is common to RTPS
submessages. It identifies the kind of
submessage.
The value indicates it is a
SecureRTPSPrefixSubMsg.
submessageLength ushort The presence of this field is common to RTPS
submessages. It identifies the length of the
submessage.
EndianessFlag SubmessageFlag Appears in the Submessage header flags.
Indicates endianess.
transformation_id CryptoTransformIdentifier Identfies the kind of transformation performed
on the RTPS Subumessages that follow up to
the SRTPS_POSTFIX submessage.
plugin_sec_header octet[] Provides further information on the
transformation performed. The contents are
specific to the Plugin Implementation and the
value of the transformation_id.
7.3.6.5.3 Validity
The RTPS Submessage is invalid if the submessageLength in the Submessage header is too small.
The SecureRTPSPrefixSubMsg shall immediately follow the RTPS Header.
7.3.6.5.4 Logical Interpretation
The SecureRTPSPrefixSubMsg provides a way to prefix a list of RTPS Submessages so that they
can be secured.
A SecureRTPSPrefixSubMsg shall be followed by a list of RTPS Submessages which
themselves shall be followed by a SecureRTPSPostfixSubMsg.
7.3.6.6 RTPS Submessage: SecureRTPSPostfixSubMsg
This specification introduces the RTPS submessage: SecureRTPSPostfixSubMsg. The format of
the SecureRTPSPostfixSubMsg complies with the RTPS SubMessage format mandated in the
RTPS specification. As such it consists of the RTPS SubmessageHeader followed by a set of RTPS
SubmessageElement elements.
7.3.6.6.1 Purpose
The SecureRTPSPostfixSubMsg submessage is used to authenticate the RTPS Submessages that
appear between the preceeding SecureRTPSPostfixSubMsg and the
SecureRTPSPostfixSubMsg.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-49-320.jpg)
![36 DDS Security, v1.0
7.3.6.6.2 Content
The elements that form the structure of the SecureRTPSPostfixSubMsg are described in the table
below.
Table 8 – SecurePostfixSubMsg class
Element Type Meaning
SRTPS_POSTFIX SubmessageKind The presence of this field is common to RTPS
submessages. It identifies the kind of
submessage.
The value indicates it is a
SecureRTPSPostfixSubMsg.
submessageLength ushort The presence of this field is common to RTPS
submessages. It identifies the length of the
submessage.
EndianessFlag SubmessageFlag Appears in the Submessage header flags.
Indicates endianess.
plugin_sec_tag octet[] Provides information on the results of the
transformation performed, typically a list of
authentication tags. The contents are specific
to the Plugin Implementation and the value of
the transformation_id contained on the related
SecureRTPSPrefixSubMsg.
7.3.6.6.3 Validity
The RTPS Submessage is invalid if the submessageLength in the Submessage header is too small.
The RTPS SecureRTPSPostfixSubMsg is invalid if there is no SecureRTPSPrefixSubMsg
following the RTPS Header. This SecureRTPSPrefixSubMsg is referred to as the related
SecureRTPSPrefixSubMsg.
7.3.6.6.4 Logical Interpretation
The SecureRTPSPostfixSubMsg provides a way to authenticate the validity and origin of the list
of RTPS Submessages between the related SecureRTPSPrefixSubMsg and the
SecureRTPSPrefixSubMsg. The Cryptographic transformation applied is identified in the related
SecureRTPSPrefixSubMsg.
7.3.7 Mapping to UDP/IP PSM
The DDS-RTPS specification defines the RTPS protocol in terms of a platform-independent model
(PIM) and then maps it to a UDP/IP transport PSM (see clause 9, “Platform Specific Model (PSM):
UDP/IP” of the DDS-RTPS specification [2]).
Sub clause 7.3.7 does the same thing for the new RTPS submessage elements and submessages
introduced by the DDS Security specification.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-50-320.jpg)
![DDS Security, v1.0 37
7.3.7.1 Mapping of the EntityIds for the Builtin DataWriters and DataReaders
Sub clause 7.4 defines a set of builtin Topics and corresponding DataWriter and DataReader entities
that shall be present on all compliant implementations of the DDS Security specification. The
corresponding EntityIds used when these endpoints are used on the UDP/IP PSM are given in the table
below.
Table 9 – EntityId values for secure builtin data writers and data readers
Entity EntityId_t name EntityId_t value
SEDPbuiltinPublicationsSecure
Writer
ENTITYID_SEDP_BUILTIN_PUBLICATIO
NS_SECURE_WRITER
{{ff, 00, 03}, c2}
SEDPbuiltinPublicationsSecure
Reader
ENTITYID_SEDP_BUILTIN_PUBLICATIO
NS_SECURE_READER
{{ff, 00, 03}, c7}
SEDPbuiltinSubscriptionsSecur
eWriter
ENTITYID_SEDP_BUILTIN_SUBSCRIPTI
ONS_SECURE_WRITER
{{ff, 00, 04}, c2}
SEDPbuiltinSubscriptionsSecur
eReader
ENTITYID_ SEDP_BUILTIN_
SUBSCRIPTIONS_SECURE_READER
{{ff, 00, 04}, c7}
BuiltinParticipantMessageSecu
reWriter
ENTITYID_P2P_BUILTIN_PARTICIPANT_
MESSAGE_SECURE_WRITER
{{ff, 02, 00}, c2}
BuiltinParticipantMessageSecu
reReader
ENTITYID_P2P_BUILTIN_PARTICIPANT_
MESSAGE_SECURE_READER
{{ff, 02, 00}, c7}
BuiltinParticipantStatelessMes
sageWriter
ENTITYID_P2P_BUILTIN_PARTICIPANT_
STATELESS_WRITER
{{00, 02, 01}, c3}
BuiltinParticipantStatelessMes
sageReader
ENTITYID_P2P_BUILTIN_PARTICIPANT_
STATELESS_READER
{{00, 02, 01}, c4}
BuiltinParticipantVolatileMess
ageSecureWriter
ENTITYID_P2P_BUILTIN_PARTICIPANT_
VOLATILE_SECURE_WRITER
{{ff, 02, 02}, c3}
BuiltinParticipantVolatileMess
ageSecureReader
ENTITYID_P2P_BUILTIN_PARTICIPANT_
VOLATILE_SECURE_READER
{{ff, 02, 02}, c4}
7.3.7.2 Mapping of the CryptoTransformIdentifier Type
The UDP/IP PSM maps the CryptoTransformIdentifier to the following extended IDL
structure:
@Extensibility(FINAL_EXTENSIBILITY)
struct CryptoTransformIdentifier {
octet transformation_kind[4];](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-51-320.jpg)
![38 DDS Security, v1.0
octet transformation_key_id[4];
};
7.3.7.3 Mapping of the SecureDataHeader SubmessageElement
A SecureDataHeader SubmessageElement contains the information that identifies a
cryptographic transformation. The SecuredDataHeader shall start with the
CryptoTransformIdentifier and be followed by a plugin-specific plugin_sec_header
returned by the encoding transformation.
The UDP/IP wire representation for the SecuredDataHeader shall be:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
| octet transformation_kind[4] |
+---------------+---------------+---------------+---------------+
| |
+ octet transformation_key_id[4] +
| |
+---------------+---------------+---------------+---------------+
| |
~ octet plugin_sec_header[] ~
| |
+---------------+---------------+---------------+---------------+
7.3.7.4 Mapping of the SecureDataTag SubmessageElement
A SecureDataTag SubmessageElement contains the information that authenticates the result
of a cryptographic transformation. The SecuredDataTag contains a plugin-specific plugin_sec_tag
returned by the encoding transformation.
The UDP/IP wire representation for the SecureDataTag shall be:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
| |
~ octet plugin_sec_tag[] ~
| |
+---------------+---------------+---------------+---------------+
7.3.7.5 SecureBodySubMsg Submessage
7.3.7.5.1 Wire Representation
The UDP/IP wire representation for the SecureBodySubMsg shall be:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-52-320.jpg)


![DDS Security, v1.0 41
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
| SRTPS_POSTFIX |X|X|X|X|X|X|X|E| octetsToNextHeader |
+---------------+---------------+---------------+---------------+
| |
+ SecureDataTag sec_data_tag +
| |
+---------------+---------------+---------------+---------------+
7.3.7.9.2 Submessage Id
The SecureRTPSPostfixSubMsg shall have the submessageId set to the value 0x34 and referred
by the symbolic name SRTPS_POSTFIX.
7.3.7.9.3 Flags in the Submessage Header
The SecureRTPSPostfixSubMsg only uses the EndiannessFlag.
7.4 DDS Support for Security Plugin Information Exchange
In order to perform their function, the security plugins associated with different DDS
DomainParticipant entities need to exchange information representing things such as Identity
and Permissions of the DomainParticipant entities, authentication challenge messages, tokens
representing key material, etc.
DDS already has several mechanisms for information exchange between DomainParticipant
entities. Notably the builtin DataWriter and DataReader entities used by the Simple Discovery
Protocol (see sub clause 8.5 of the DDS Interoperability Wire Protocol [2]) and the
BuiltinParticipantMessageWriter and BuiltinParticipantMessageReader (see sub clause 9.6.2.1 of the
DDS Interoperability Wire Protocol [2]).
Where possible, this specification tries to reuse and extend existing DDS concepts and facilities so that
they can fulfill the needs of the security plugins, rather than defining entirely new ones. This way, the
Security Plugin implementation can be simplified and it does not have to implement a separate
messaging protocol.
7.4.1 Secure builtin Discovery Topics
7.4.1.1 Background (Non-Normative)
DDS discovery information is sent using builtin DDS DataReaders and DataWriters. These are
regular DDS DataReaders and DataWriters, except they are always present in the system and
their Topic names, associated data types, QoS, and RTPS EntityIds are all specified as part of the
DDS and RTPS specifications, so they do not need to be discovered.
The DDS specification defines three discovery builtin Topic entities: the DCPSParticipants used to
discover the presence of DomainParticipants, the DCPSPublications used to discover
DataWriters, and the DCPSSubscriptions used to discover DataReaders (see sub clause 8.5 of
the DDS Interoperability Wire Protocol [2]).](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-55-320.jpg)

![DDS Security, v1.0 43
imply that compliance to the DDS-XTYPES is required to comply with DDS Security. All that is
required is to serialize the specific data types defined here according to the format described in the
DDS-XTYPES specification.
7.4.1.3 Extension to RTPS Standard DCPSParticipants Builtin Topic
The DDS specification specifies the existence of the DCPSParticipants builtin Topic and a
corresponding builtin DataWriter and DataReader to communicate this Topic. These
endpoints are used to discover DomainParticipant entities.
The data type associated with the DCPSParticipants builtin Topic is ParticipantBuiltinTopicData,
defined in sub clause 7.1.5 of the DDS specification [1].
The DDS Interoperability Wire Protocol specifies the serialization of ParticipantBuiltinTopicData.
The format used is what the DDS Interoperability Wire Protocol calls a ParameterList whereby each
member of the ParticipantBuiltinTopicData is serialized using CDR but preceded in the stream by the
serialization of a short ParameterID identifying the member, followed by another short containing the
length of the serialized member, followed by the serialized member. See sub clause 8.3.5.9 of the DDS
Interoperability Wire Protocol [2]. This serialization format allows the ParticipantBuiltinTopicData to
be extended without breaking interoperability.
This DDS Security specification adds several new members to the ParticipantBuiltinTopicData
structure. The member types and the ParameterIDs used for the serialization are described below.
Table 10 – Additional parameter IDs in ParticipantBuiltinTopicData
Member name Member type Parameter ID name Parameter ID value
identity_token IdentityToken
(see 7.2.4)
PID_IDENTITY_TOKEN 0x1001
permissions_token PermissionsToken
(see 7.2.4)
PID_PERMISSIONS_TOKEN 0x1002
property PropertyQosPolicy PID_PROPERTY_LIST
(See Table 9.12 of DDS-
RTPS)
0x0059
(See Table 9.12 of
DDS-RTPS)
@extensibility(MUTABLE_EXTENSIBILITY)
struct ParticipantBuiltinTopicDataSecure: ParticipantBuiltinTopicData {
@ID(0x1001) IdentityToken identity_token;
@ID(0x1002) PermissionsToken permissions_token;
};
Only the Property_t and BinaryProperty_t elements having the propagate member set to
TRUE are serialized. Furthermore as indicated by the @non-serialized annotation the
serialization of the Property_t and BinaryProperty_t elements shall omit the serialization of
the propagate member. That is they are serialized as if the type definition did not contain the
propagate member. This is consistent with the data-type definition for Property_t specific in the DDS-
RTPS specification (see Table 9.12 of DDS-RTPS). Even if it is not present in the serialized data, the
receiver will set the propagate member to TRUE.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-57-320.jpg)
![44 DDS Security, v1.0
Note that according to DDS-RTPS the PID_PROPERTY_LIST is associated with a single
PropertySeq rather than the PropertyQosPolicy, which is a structure that contains two
sequences. This does not cause any interoperability problems because the containing
ParticipantBuiltinTopicData has mutable extensibility.
The DDS Interoperability Wire Protocol specifies that the ParticipantBuiltinTopicData shall contain
the attribute called availableBuiltinEndpoints that is used to announce the builtin endpoints that are
available in the DomainParticipant. See clause 8.5.3.2 of the DDS Interoperability Wire Protocol
[2]. The type for this attribute is an array of BuiltinEndpointSet_t. For the UDP/IP PSM the
BuiltinEndpointSet_t is mapped to a bitmap represented as type long. Each builtin endpoint is
represented as a bit in this bitmap with the bit values defined in Table 9.4 (clause 9.3.2) of the DDS
Interoperability Wire Protocol [2].
This DDS Security specification reserves additional bits to indicate the presence of the corresponding
built-in end points listed in clause 7.4.5. These bits shall be set on the availableBuiltinEndpoints. The
bit that encodes the presence of each individual endpoint is defined in Table 11 below.
Table 11 – Mapping of the additional builtin endpoints added by DDS security to the availableBuiltinEndpoints
Builtin Endpoint Bit in the ParticipantBuiltinTopicData
availableBuiltinEndpoints
SEDPbuiltinPublicationsSecureWriter
SEDPbuiltinPublicationsSecureReader
See clause 7.4.1.4
(0x00000001 << 16)
(0x00000001 << 17)
SEDPbuiltinSubscriptionsSecureWriter
SEDPbuiltinSubscriptionsSecureReader
See clause 7.4.1.5
(0x00000001 << 18)
(0x00000001 << 19)
BuiltinParticipantMessageSecureWriter
BuiltinParticipantMessageSecureReader
See clause 7.4.2
(0x00000001 << 20)
(0x00000001 << 21)
BuiltinParticipantStatelessMessageWriter
BuiltinParticipantStatelessMessageReader
See clause 7.4.3
(0x00000001 << 22)
(0x00000001 << 23)
BuiltinParticipantVolatileMessageSecureWriter
BuiltinParticipantVolatileMessageSecureReader
See clause 7.4.4
(0x00000001 << 24)
(0x00000001 << 25)](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-58-320.jpg)


![DDS Security, v1.0 47
7.4.2 New ParticipantMessageSecure builtin Topic
The DDS Interoperability Wire Protocol specifies the BuiltinParticipantMessageWriter and
BuiltinParticipantMessageReader (see sub clauses 8.4.13 and 9.6.2.1 of the DDS Interoperability
Wire Protocol[2]). These entities are used to send information related to the LIVELINESS QoS. This
information could be considered sensitive and therefore secure DDS systems need to provide an
alternative protected way to send liveliness information.
The data type associated with these endpoints is ParticipantMessageData defined in sub clause 9.6.2.1
of the DDS Interoperability Wire Protocol specification [2].
To support coexistence and interoperability with non-secure DDS applications, implementations of the
DDS Security specification shall use the same standard BuiltinParticipantMessageWriter and
BuiltinParticipantMessageReader to communicate liveliness information on Topic entities that are
not considered sensitive.
Implementations of the DDS Security specification shall have an additional
ParticipantMessageSecure builtin Topic and associated builtin DataReader and DataWriter
entities to communicate the liveliness information for Topic entities that are considered sensitive.
The data type associated with the ParticipantMessageSecure Topic shall be the same as the
ParticipantMessageData structure.
The QoS associated with the ParticipantMessageSecure Topic shall be the same as for the
ParticipantMessageSecure Topic as defined in sub clause 8.4.13 of the DDS Interoperability Wire
Protocol [2].
The builtin DataWriter for the ParticipantMessageSecure Topic shall be referred to as the
BuiltinParticipantMessageSecureWriter. The builtin DataReader for the
ParticipantMessageSecure Topic shall be referred to as the
BuiltinParticipantMessageSecureReader.
The RTPS EntityId_t associated with the BuiltinParticipantMessageSecureWriter and
BuiltinParticipantMessageSecureReader shall be as specified in 7.4.5.
7.4.3 New ParticipantStatelessMessage builtin Topic
To perform mutual authentication between DDS DomainParticipant entities, the security plugins
associated with those participants need to be able to send directed messages to each other. As described
in 7.4.3.1 below, the mechanisms provided by existing DDS builtin Topic entities are not adequate
for this purpose. For this reason, this specification introduces a new ParticipantStatelessMessage
builtin Topic and corresponding builtin DataReader and DataWriter entities to read and write
the Topic.
7.4.3.1 Background: Sequence Number Attacks (non normative)
DDS has a builtin mechanism for participant-to-participant messaging: the
BuiltinParticipantMessageWriter and BuiltinParticipantMessageReader (see sub clause 9.6.2.1 of the
DDS Interoperability Wire Protocol [2]). However this mechanism cannot be used for mutual
authentication because it relies on the RTPS reliability protocol and suffers from the sequence-number
prediction vulnerability present in unsecured reliable protocols:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-61-320.jpg)
![48 DDS Security, v1.0
The RTPS reliable protocol allows a DataWriter to send to a DataReader Heartbeat
messages that advance the first available sequence number associated with the DataWriter. A
DataReader receiving a Heartbeat from a DataWriter will advance its first available
sequence number for that DataWriter and ignore any future messages it receives with sequence
numbers lower than the first available sequence number for the DataWriter. The reliable
DataReader will also ignore duplicate messages for that same sequence number.
The behavior of the reliability protocol would allow a malicious application to prevent other
applications from communicating by sending Heartbeats pretending to be from other
DomainParticipants that contain large values of the first available sequence number. All the
malicious application needs to do is learn the GUIDs of other applications, which can be done from
observing the initial discovery messages on the wire, and use that information to create fake
Heartbeats.
Stated differently: prior to performing mutual authentication and key exchange, the applications cannot
rely on the use of encryption and message access codes to protect the integrity of the messages.
Therefore, during this time window, they are vulnerable to this kind of sequence-number attack. This
attack is present in most reliable protocols. Stream-oriented protocols such as TCP are also vulnerable
to sequence-number-prediction attacks but they make it more difficult by using a random initial
sequence number on each new connection and discarding messages with sequence numbers outside the
window. This is something that RTPS cannot do given the data-centric semantics of the protocol.
In order to avoid this vulnerability, the Security plugins must exchange messages using writers and
readers sufficiently robust to sequence number prediction attacks. The RTPS protocol specifies
endpoints that meet this requirement: the RTPS StatelessWriter and StatelessReader (see
8.4.7.2 and 8.4.10.2 of the DDS Interoperability Wire Protocol [2]) but there are no DDS builtin
endpoints that provide access to this underlying RTPS functionality.
7.4.3.2 BuiltinParticipantStatelessMessageWriter and BuiltinParticipantStatelessMessageReader
The DDS Security specification defines two builtin Endpoints: the
BuiltinParticipantStatelessMessageWriter and the BuiltinParticipantStatelessMessageReader. These
two endpoints shall be present in compliant implementations of this specification. These endpoints are
used to write and read the builtin ParticipantStatelessMessage Topic.
The BuiltinParticipantStatelessMessageWriter is an RTPS Best-Effort StatelessWriter (see sub
clause 8.4.7.2 of the DDS Interoperability Wire Protocol [2]).
The BuiltinParticipantStatelessMessageReader is an RTPS Best-Effort StatelessReader (see
sub clause 8.4.10.2 of the DDS Interoperability Wire Protocol [2]).
The data type associated with these endpoints is ParticipantStatelessMessage defined
below (see also 7.2.5):
typedef ParticipantStatelessMessage ParticipantGenericMessage;
The RTPS EntityId_t associated with the BuiltinParticipantStatelessMessageWriter and
BuiltinParticipantStatelessMessageReader shall be as specified in 7.4.5.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-62-320.jpg)
![DDS Security, v1.0 49
7.4.3.3 Contents of the ParticipantStatelessMessage
The ParticipantStatelessMessage is intended as a holder of information that is sent point-
to-point from a DomainParticipant to another.
The message_identity uniquely identifies each individual ParticipantStatelessMessage:
The source_guid field within the message_identity shall be set to match the
BuiltinTopicKey_t of the BuiltinParticipantStatelessMessageWriter that writes the message.
The sequence_number field within the message_identity shall start with the value set to one and be
incremented for each different message sent by the BuiltinParticipantStatelessMessageWriter.
The related_message_identity uniquely identifies another ParticipantStatelessMessage that
is related to the message being processed. It shall be set to either the tuple {GUID_UNKNOWN, 0} if
the message is not related to any other message, or else set to match the message_identity of the
related ParticipantStatelessMessage.
The destination_participant_key shall contain either the value GUID_UNKNOWN (see sub clause
9.3.1.5 of the DDS Interoperability Wire Protocol [2]) or else the BuiltinTopicKey_t of the
destination DomainParticipant.
The destination_endpoint_key provides a mechanism to specify finer granularity on the intended
recipient of a message beyond the granularity provided by the destination_participant_key. It can
contain either GUID_UNKNOWN or else the GUID of a specific endpoint within destination
DomainParticipant. The targeted endpoint is the one whose Endpoint (DataWriter or
DataReader) BuiltinTopic_t matches the destination_endpoint_key.
The contents message_data depend on the value of the message_class_id and are defined in this
specification in the sub clause that introduces each one of the pre-defined values of the
GenericMessageClassId. See 7.4.3.5 and 7.4.3.6.
7.4.3.4 Destination of the ParticipantStatelessMessage
If the destination_participant_key member is not set to GUID_UNKNOWN, the message written is
intended only for the BuiltinParticipantStatelessMessageReader belonging to the
DomainParticipant with a matching Participant Key.
This is equivalent to saying that the BuiltinParticipantStatelessMessageReader has an implied content
filter with the logical expression:
“destination_participant_key == GUID_UNKNOWN
|| destination_participant_key == BuiltinParticipantStatelessMessageReader.participant.key”
Implementations of the specification can use this content filter or some other mechanism as long as the
resulting behavior is equivalent to having this content filter.
If the destination_endpoint_key member is not set to GUID_UNKNOWN, the message written targets
the specific endpoint within the destination DomainParticipant with a matching Endpoint Key.
7.4.3.5 Reserved values of ParticipantStatelessMessage GenericMessageClassId
This specification, including future versions of this specification reserves GenericMessageClassId
values that start with the prefix “dds.sec.” (without quotes) .](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-63-320.jpg)
![50 DDS Security, v1.0
The specification defines and uses the following specific values for the GenericMessageClassId:
#define GMCLASSID_SECURITY_AUTH_HANDSHAKE
“dds.sec.auth”
Additional values of the GenericMessageClassId may be defined with each plugin implementation.
7.4.3.6 Format of data within ParticipantStatelessMessage
Each value for the GenericMessageClassId uses different schema to store data within the
generic attributes in the message_data.
7.4.3.6.1 Data for message class GMCLASSID_SECURITY_AUTH_HANDSHAKE
If GenericMessageClassId is GMCLASSID_SECURITY_AUTH_HANDSHAKE the
message_data attribute shall contain the HandshakeMessageTokenSeq containing one element.
The specific contents of the HandshakeMessageToken element shall be defined by the
Authentication Plugin.
The destination_participant_key shall be set to the BuiltinTopicKey_t of the destination
DomainParticipant.
The destination_endpoint_key shall be set to GUID_UNKNOWN. This indicates that there is no
specific endpoint targeted by this message: It is intended for the whole DomainParticipant.
The source_endpoint_key shall be set to GUID_UNKNOWN.
7.4.4 New ParticipantVolatileMessageSecure builtin Topic
7.4.4.1 Background (Non-Normative)
In order to perform key exchange between DDS DomainParticipant entities, the security plugins
associated with those participants need to be able to send directed messages to each other using a
reliable and secure channel. These messages are intended only for Participants that are currently in the
system and therefore need a DURABILITY Qos of kind VOLATILE.
The existing mechanisms provided by DDS are not adequate for this purpose:
The new ParticipantStatelessMessage is not suitable because it is a stateless best-effort channel not
protected by the security mechanisms in this specification and therefore requires the message data
to be explicitly encrypted and signed prior to being given to the
ParticipantStatelessMessageWriter.
The new ParticipantMessageSecure is not suitable because its QoS has DURABILITY kind
TRANSIENT_LOCAL (see sub clause 8.4.13 of the DDS Interoperability Wire Protocol [2]) rather
than the required DURABILITY kind VOLATILE.
For this reason, implementations of the DDS Security specification shall have an additional builtin
Topic ParticipantVolatileMessageSecure and corresponding builtin DataReader and
DataWriter entities to read and write the Topic.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-64-320.jpg)
![DDS Security, v1.0 51
7.4.4.2 BuiltinParticipantVolatileMessageSecureWriter and
BuiltinParticipantVolatileMessageSecureReader
The DDS Security specification defines two new builtin Endpoints: The
BuiltinParticipantVolatileMessageSecureWriter and the
BuiltinParticipantVolatileMessageSecureReader. These two endpoints shall be present in compliant
implementations of this specification. These endpoints are used to write and read the builtin
ParticipantVolatileSecureMessage Topic.
The BuiltinParticipantVolatileMessageSecureWriter is an RTPS Reliable StatefulWriter (see sub
clause 8.4.9.2 of the DDS Interoperability Wire Protocol [2]). The DDS DataWriter Qos associated
with the DataWriter shall be as defined in the table below. Any policies that are not shown in the
table shall be set corresponding to the DDS defaults.
Table 14 – Non-default Qos policies for BuiltinParticipantVolatileMessageSecureWriter
DataWriter Qos policy Policy Value
RELIABILITY kind= RELIABLE
HISTORY kind= KEEP_ALL
DURABILITY kind= VOLATILE
The BuiltinParticipantVolatileMessageSecureReader is an RTPS Reliable StatefulReader (see sub
clause 8.4.11.2 of the DDS Interoperability Wire Protocol [2]). The DDS DataReader Qos
associated with the DataReader shall be as defined in the table below. Any policies that are not
shown in the table shall be set corresponding to the DDS defaults.
Table 15 – Non-default Qos policies for BuiltinParticipantVolatileMessageSecureReader
DataReader Qos policy Policy Value
RELIABILITY kind= RELIABLE
HISTORY kind= KEEP_ALL
DURABILITY kind= VOLATILE
The data type associated with these endpoints is ParticipantVolatileSecureMessage
defined as:
typedef ParticipantVolatileSecureMessage ParticipantGenericMessage;
The RTPS EntityId_t associated with the BuiltinParticipantVolatileMessageSecureWriter and
BuiltinParticipantVolatileMessageSecureReader shall be as specified in 7.4.5.
7.4.4.3 Contents of the ParticipantVolatileSecureMessage
The ParticipantVolatileSecureMessage is intended as a holder of secure information that
is sent point-to-point from a DomainParticipant to another.
The destination_participant_key shall contain either the value GUID_UNKNOWN (see sub clause
9.3.1.5 of the DDS Interoperability Wire Protocol [2] or else the BuiltinTopicKey_t of the
destination DomainParticipant.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-65-320.jpg)



![56 DDS Security, v1.0
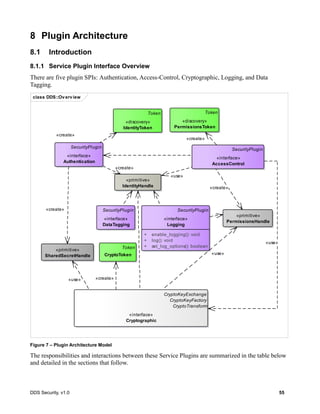
Table 16 – Purpose of each Security Plugin
Service Plugin Purpose Interactions
Authentication Authenticate the principal that is
joining a DDS Domain.
Support mutual authentication
between participants and establish a
shared secret.
The principal may be an
application/process or the user associated
with that application or process.
AccessControl Decide whether a principal is
allowed to perform a protected
operation.
Protected operations include joining a
specific DDS domain, creating a Topic,
reading a Topic, writing a Topic, etc.
Cryptography Generate keys. Perform Key
Exchange. Perform the encryption
and decryption operations. Compute
digests, compute and verify
Message Authentication Codes.
Sign and verify signatures of
messages.
This plugin implements 3
complementary interfaces:
CryptoKeyFactory, CryptoKeyExchange,
and CryptoTransform.
Logging Log all security relevant events. This plugin is accessible to all other
plugins such that they can log the
relevant events.
DataTagging Add a data tag for each data sample.
8.1.2 Plugin Instantiation
The Security Plugins shall be configurable separately for each DomainParticipant even when
multiple DomainParticipants are constructed within the same Operating System Process and share the
same Address Space.
A collection of the 5 SPIs intended to be used with the same DomainParticipant is referred to as
a DDS-Security Plugin Suite.
The mechanism used to instantiate the security Service Plugins and associate them with each
DomainParticipant is not defined by the DDS-Security specification.
Implementations of this specification may use vendor-specific configurations to facilitate linking the
Plugin Suite, including providing dynamic loading and linking facilities as well as initializing the
Plugin Suite.
Likewise implementations of this specification may use vendor-specific configurations to bind a Plugin
Suite to the DomainParticipant. However it is required for the Plugin Suite to be initialized and
bound by the time the DomainParticipant is enabled. Therefore this process shall complete either
during the DomainParticipantFactory create_domain_participant or else during the
DomainParticipant enable operations defined in [1]. Note that some of the Plugin Suite
Authentication and AccessControl operations shall also be called during
create_domain_participant or during enable.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-70-320.jpg)


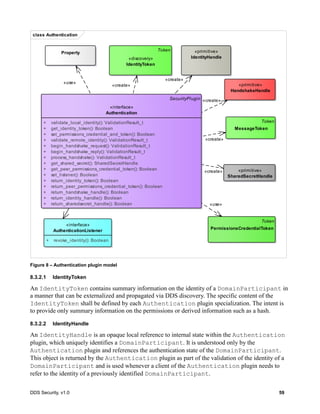

![DDS Security, v1.0 61
Figure 9 – Authentication plugin interaction state machine
8.3.2.7.1 Reliability of the Authentication Handshake
In order to be sufficiently robust to avert sequence number attacks (7.4.3.1), the Authentication
Handshake uses the BuiltinParticipantStatelessMessageWriter and
BuiltinParticipantStatelessMessageReader endpoints (7.4.3) with GenericMessageClassId set
to GMCLASSID_SECURITY_AUTH_HANDSHAKE (7.4.3.5). These stateless endpoints send
messages best-effort without paying attention to any sequence number information to remove
duplicates or attempt ordered delivery. Despite this, the Authentication Handshake needs to be able to
withstand the message loss that may occur on the network.
In order to operate robustly in the presence of message loss and sequence number attacks DDS
Security implementations shall follow the rules below:
1. The DDS security implementation shall pass to the AuthenticationPlugin any message received
by the BuiltinParticipantStatelessMessageReader that has a GenericMessageClassId
set to GMCLASSID_SECURITY_AUTH_HANDSHAKE.
2. Any time the state-machine indicates that a message shall be sent using the
BuiltinParticipantStatelessMessageWriter and a reply message needs to be received by the
stm AuthBehavior
HandshakeInit
HandshakeInitReply
Choice
Initialized
EntryPoint
Validation_OK
Validation_Failed
HandshakeMessageSend
Choice
HandshakeCompletedOK
HandshakeMessageWait
HandshakeInitMessageWait
HandshakeFinalMessage
HandshakeMessageReceived
[VALIDATION_FAILED]
begin_handshake_reply()
[VALIDATION_PENDING_HANDSHAKE_REQUEST] [VALIDATION_PENDING_HANDSHAKE_MESSAGE]
[VALIDATION_OK] [VALIDATION_FAILED]
validate_remote_identity()
begin_handshake_request()
DDS::send_message()
process_handshake()
[VALIDATION_OK]
[VALIDATION_PENDING_HANDSHAKE_MESSAGE]
[VALIDATION_OK_WITH_FINAL_MESSAGE]
get_shared_secret()
DDS::receive_message()
DDS::receive_message()
DDS::send_message()
validate_local_identity()](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-75-320.jpg)

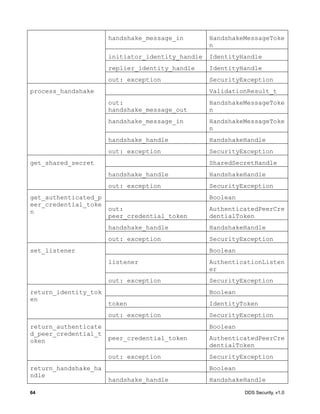
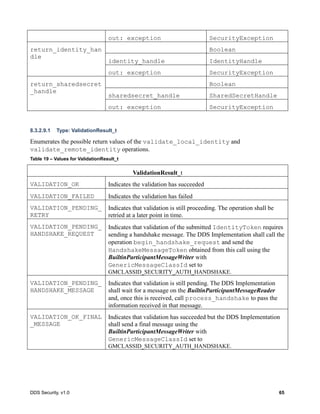
![66 DDS Security, v1.0
8.3.2.9.2 Operation: validate_local_identity
Validates the identity of the local DomainParticipant. The operation returns as an output
parameter the IdentityHandle, which can be used to locally identify the local Participant to the
Authentication Plugin.
In addition to validating the identity, this operation also returns the DomainParticipant
BuiltinTopicKey_t that shall be used by the DDS implementation to uniquely identify the
DomainParticipant on the network.
This operation shall be called before the DomainParticipant is enabled. It shall be called either
by the implementation of DomainParticipantFactory create_domain_participant or
DomainParticipant enable [1].
If an error occurs, this method shall return VALIDATION_FAILED and fill the
SecurityException.
The method shall return either VALIDATION_OK if the validation succeeds, or
VALIDATION_FAILED if it fails, or VALIDATION_PENDING_RETRY if the verification has not
finished.
If VALIDATION_PENDING_RETRY has been returned, the operation shall be called again after a
configurable delay to check the status of verification. This shall continue until the operation returns
either VALIDATION_OK (if the validation succeeds), or VALIDATION_FAILED. This approach
allows non-blocking interactions with services whose verification may require invoking remote
services.
Parameter (out) local_identity_handle: A handle that can be used to locally refer to the
Authenticated Participant in subsequent interactions with the Authentication plugin. The nature
of the handle is specific to each Authentication plugin implementation. The handle will only be
meaningful if the operation returns VALIDATION_OK.
Parameter (out) adjusted_participant_key: The BuiltinTopicKey_t that the DDS
implementation shall use to uniquely identify the DomainParticipant on the network. The
returned adjusted_participant_key shall be the one that eventually appears in the participant_key
attribute of the ParticipantBuiltinTopicData sent via discovery.
Parameter domain_id: The DDS Domain Id of the DomainParticipant.
Parameter participant_qos: The DomainParticipantQos of the DomainParticipant.
Parameter candidate_participant_key: The BuiltinTopicKey_t that the DDS implementation
would have used to uniquely identify the DomainParticipant if the Security plugins were not
enabled.
Parameter exception: A SecurityException object.
Return: The operation shall return
VALIDATION_OK if the validation was successful.
VALIDATION_FAILED if it failed.
VALIDATION_PENDING_RETRY if verification has not completed and the operation should be
retried later.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-80-320.jpg)








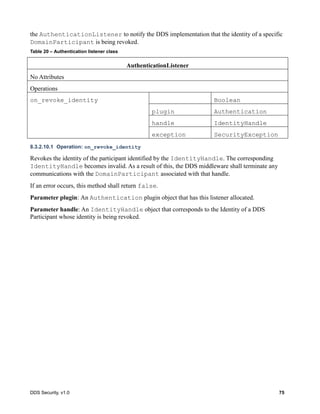

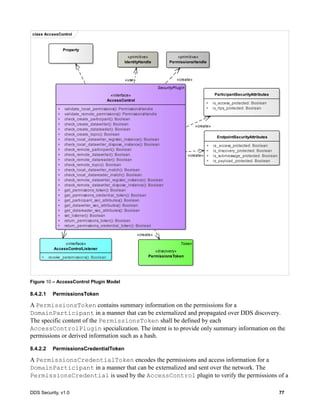
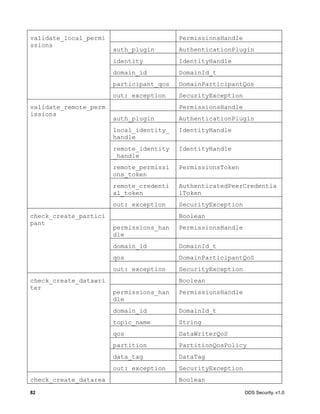
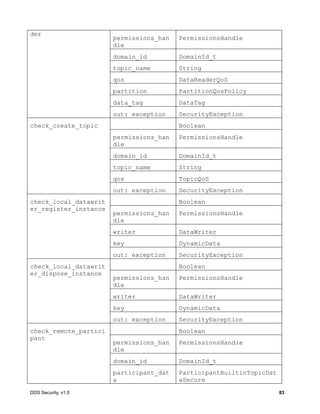
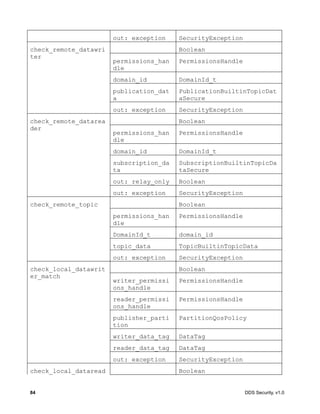
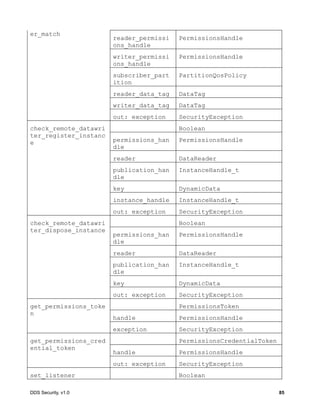
![DDS Security, v1.0 87
8.4.2.6.1 Operation: validate_local_permissions
Validates the permissions of the local DomainParticipant. The operation returns a
PermissionsHandle object, if successful. The PermissionsHandle can be used to locally
identify the permissions of the local DomainParticipant to the AccessControl plugin.
This operation shall be called before the DomainParticipant is enabled. It shall be called either
by the implementation of DomainParticipantFactory create_domain_participant or
DomainParticipant enable [1].
If an error occurs, this method shall return HandleNIL.
Parameter auth_plugin: The Authentication plugin, which validated the identity of the local
DomainParticipant. If this argument is nil, the operation shall return HandleNIL.
Parameter identity: The IdentityHandle returned by the authentication plugin from a successful
call to validate_local_identity.
Parameter domain_id: The DDS Domain Id of the DomainParticipant.
Parameter participant_qos: The DomainParticipantQos of the DomainParticipant.
Parameter exception: A SecurityException object, which provides details, in case this operation
returns HandleNIL.
8.4.2.6.2 Operation: validate_remote_permissions
Validates the permissions of the previously authenticated remote DomainParticipant, given the
PermissionsToken object received via DDS discovery and the
PermissionsCredentialToken obtained as part of the authentication process. The operation
returns a PermissionsHandle object, if successful.
If an error occurs, this method shall return HandleNIL.
Parameter auth_plugin: The Authentication plugin, which validated the identity of the remote
DomainParticipant. If this argument is nil, the operation shall return HandleNIL.
Parameter local_identity_handle: The IdentityHandle returned by the authentication plugin.
Parameter remote_identity_handle: The IdentityHandle returned by a successful call to the
validate_remote_identity operation on the Authentication plugin.
Parameter remote_permissions_token: The PermissionsToken of the remote
DomainParticipant received via DDS discovery inside the permissions_token member of the
ParticipantBuiltinTopicData. See 7.4.1.3.
Parameter remote_credential_token: The AuthenticatedPeerCredentialToken of the
remote DomainParticipant returned by the operation
get_authenticated_peer_credential_token on the Authentication plugin.
Parameter exception: A SecurityException object, which provides details, in case this
operation returns HandleNIL.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-101-320.jpg)
![88 DDS Security, v1.0
8.4.2.6.3 Operation: check_create_participant
Enforces the permissions of the local DomainParticipant. When the local
DomainParticipant is created, its permissions must allow it to join the DDS Domain specified
by the domain_id. Optionally the use of the specified value for the DomainParticipantQoS must
also be allowed by its permissions. The operation returns a Boolean value.
This operation shall be called before the DomainParticipant is enabled. It shall be called either
by the implementation of DomainParticipantFactory create_domain_participant or
DomainParticipant enable [1].
If an error occurs, this method shall return false.
Parameter permissions_handle: The PermissionsHandle object associated with the local
DomainParticipant. If this argument is nil, the operation shall return false.
Parameter domain_id: The domain id where the local DomainParticipant is about to be
created. If this argument is nil, the operation shall return false.
Parameter qos: The QoS policies of the local DomainParticipant. If this argument is nil, the
operation shall return false.
Parameter exception: A SecurityException object, which provides details in case this operation
returns false.
8.4.2.6.4 Operation: check_create_datawriter
Enforces the permissions of the local DomainParticipant. When the local
DomainParticipant creates a DataWriter for topic_name with the specified
DataWriterQos associated with the data_tag, its permissions must allow this. The operation
returns a Boolean object.
If an error occurs, this method shall return false.
Parameter permissions_handle: The PermissionsHandle object associated with the local
DomainParticipant. If this argument is nil, the operation shall return false.
Parameter domain_id: The DomainId_t of the local DomainParticipant to which the local
DataWriter will belong.
Parameter topic_name: The topic name that the DataWriter is supposed to write. If this argument
is nil, the operation shall return false.
Parameter qos: The QoS policies of the local DataWriter. If this argument is nil, the operation
shall return false.
Parameter partition: The PartitionQosPolicy of the local Publisher to which the
DataWriter will belong.
Parameter data_tag: The data tags that the local DataWriter is requesting to be associated with its
data. This argument can be nil if it is not considered for access control.
Parameter exception: A SecurityException object, which provides details in case this operation
returns false.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-102-320.jpg)










![DDS Security, v1.0 99
8.5 Cryptographic Plugin
The Cryptographic plugin defines the types and operations necessary to support encryption,
digest, message authentication codes, and key exchange for DDS DomainParticipants,
DataWriters and DDS DataReaders.
Users of DDS may have specific cryptographic libraries they use for encryption, as well as, specific
requirements regarding the algorithms for digests, message authentication, and signing. In addition,
applications may require having only some of those functions performed, or performed only for certain
DDS Topics and not for others. Therefore, the plugin API has to be general enough to allow flexible
configuration and deployment scenarios.
8.5.1 Cryptographic Plugin Model
The Cryptographic plugin model is presented in the figure below. It combines related
cryptographic interfaces for key creation, key exchange, encryption, message authentication, hashing,
and signature.
Figure 11 – Cryptographic Plugin Model
class Cryptographic
«interface»
Cryptographic
«interface»
CryptoKeyFactory
+ register_local_participant(): ParticipantCryptoHandle
+ register_matched_remote_participant(): ParticipantCryptoHandle
+ register_local_datawriter(): DatawriterCryptoHandle
+ register_matched_remote_datareader(): DatareaderCryptoHandle
+ register_local_datareader(): DatareaderCryptoHandle
+ register_matched_remote_datawriter(): DatawriterCryptoHandle
+ unregister_participant(): Boolean
+ unregister_datawriter(): Boolean
+ unregister_datareader(): Boolean
«primitive»
ParticipantCryptoHandle
«primitive»
DatawriterCryptoHandle
«primitive»
DatareaderCryptoHandle
«interface»
CryptoKeyExchange
+ create_local_participant_crypto_tokens(): Boolean
+ set_remote_participant_crypto_tokens(): Boolean
+ create_local_datawriter_crypto_tokens(): Boolean
+ set_remote_datawriter_crypto_tokens(): Boolean
+ create_local_datareader_crypto_tokens(): Boolean
+ set_remote_datareader_crypto_tokens(): Boolean
+ return_cypto_tokens(): Boolean
«interface»
CryptoTransform
+ encode_serialized_payload(): Boolean
+ encode_datawriter_submessage(): Boolean
+ encode_datareader_submessage(): Boolean
+ encode_rtps_message(): Boolean
+ decode_rtps_message(): Boolean
+ preprocess_secure_submessage(): Boolean
+ decode_datawriter_submessage(): Boolean
+ decode_datareader_submessage(): Boolean
+ decode_serialized_payload(): Boolean
Token
CryptoToken
«primitive»
IdentityHandle
«primitive»
PermissionsHandle
«dataType»
CryptoTransformIdentifier
- transformation_kind_id: octet[4]
- transformation_key_id: octet[4]
«primitive»
SharedSecretHandle
Property
SubmessageElement
SecureDataTag
- common_mac: char[]
- receiver_specific_macs: ReceiverSpecificMAC[]
«use»](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-113-320.jpg)
![100 DDS Security, v1.0
8.5.1.1 CryptoToken
This class represents a generic holder for key material. A CryptoToken object contains all the
information necessary to construct a set of keys to be used to encrypt and/or sign plain text
transforming it into cipher-text or to reverse those operations.
The format and interpretation of the CryptoToken depends on the implementation of the
Cryptographic plugin. Each plugin implementation shall fully define itself, so that applications are able
to interoperate. In general, the CryptoToken will contain one or more keys and any other necessary
material to perform crypto-transformation and/or verification, such as, initialization vectors (IVs),
salts, etc.
8.5.1.2 ParticipantCryptoHandle
The ParticipantCryptoHandle object is an opaque local reference that represents the key
material used to encrypt and sign whole RTPS Messages. It is used by the operations
encode_rtps_message and decode_rtps_message.
8.5.1.3 DatawriterCryptoHandle
The DatawriterCryptoHandle object is an opaque local reference that represents the key
material used to encrypt and sign RTPS submessages sent from a DataWriter. This includes the RTPS
submessages Data, DataFrag, Gap, Heartbeat, and HeartbeatFrag, as well as, the
SerializedPayload submessage element that appears in the Data and DataFrag submessages.
It is used by the operations encode_datawriter_submessage,
decode_datawriter_submessage, encode_serialized_payload, and
decode_serialized_payload.
8.5.1.4 DatareaderCryptoHandle
The DatareaderCryptoHandle object is an opaque local reference that represents the key
material used to encrypt and sign RTPS Submessages sent from a DataReader. This includes the
RTPS Submessages AckNack and NackFrag.
It is used by the operations encode_datareader_submessage,
decode_datareader_submessage.
8.5.1.5 CryptoTransformIdentifier
The CryptoTransformIdentifier object used to uniquely identify the transformation applied
on the sending side (encoding) so that the receiver can locate the necessary key material to perform the
inverse transformation (decoding). The generation of CryptoTransformIdentifier is
performed by the Cryptographic plugin.
To enable interoperability and avoid misinterpretation of the key material, the structure of the
CryptoTransformIdentifier is defined for all Cryptographic plugin implementations as
follows:
typedef octet CryptoTransformKind[4];
typedef octet CryptoTransformKeyId[4];
struct CryptoTransformIdentifier {
CryptoTransformKind transformation_kind;](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-114-320.jpg)
![DDS Security, v1.0 101
CryptoTransformKeyId transformation_key_id;
};
Table 25 – CryptoTransformIdentifier class
CryptoTransformIdentifier
Attributes
transformation_kind CryptoTransformKind
transformation_key_id CryptoTransformKeyId
8.5.1.5.1 Attribute: transformation_kind
Uniquely identifies the type of cryptographic transformation.
Values of transformation_kind having the first two octets set to zero are reserved by this
specification, including future versions of this specification.
Implementers can use the transformation_kind attribute to identify non-standard cryptographic
transformations. In order to avoid collisions, the first two octets in the transformation_kind
shall be set to a registered RTPS VendorId [36]. The RTPS VendorId used shall either be one
reserved to the implementer of the Cryptographic Plugin, or else the implementer of the
Cryptographic Plugin shall secure permission from the registered owner of the RTPS
VendorId to use it.
8.5.1.5.2 Attribute: transformation_key_id
Uniquely identifies the key material used to perform a cryptographic transformation within the scope
of all Cryptographic Plugin transformations performed by the DDS DomainParticipant that
creates the key material.
In combination with the sending DomainParticipant GUID, the transformation_key_id
attribute allows the receiver to select the proper key material to decrypt/verify a message that has been
encrypted and/or signed. The use of this attribute allows a receiver to be robust to dynamic changes in
keys and key material in the sense that it can identify the correct key or at least detect that it does not
have the necessary keys and key material.
The values of the transformation_key_id are defined by the Cryptographic plugin
implementation and understood only by that plugin.
8.5.1.6 SecureSubmessageCategory_t
Enumerates the possible categories of RTPS submessages.
Table 26 – SecureSubmessageCategory_t
SecureSubmessageCategory_t
INFO_SUBMESSAGE Indicates an RTPS Info submessage: InfoSource, InfoDestination, or
InfoTimestamp.
DATAWRITER_SUMBES
SAGE
Indicates an RTPS submessage that was sent from a DataWriter: Data,
DataFrag, HeartBeat, Gap.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-115-320.jpg)

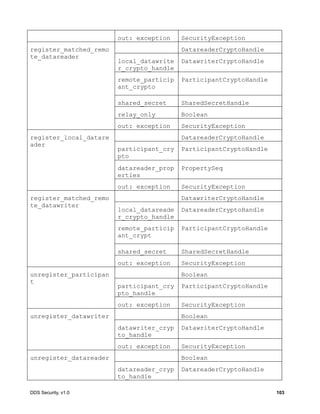





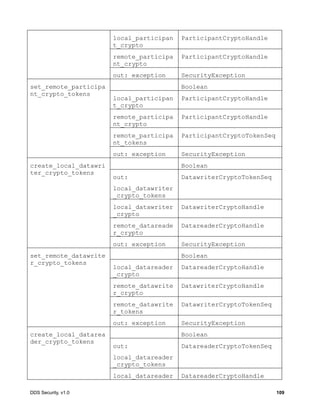
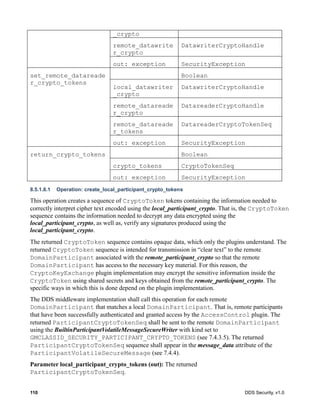




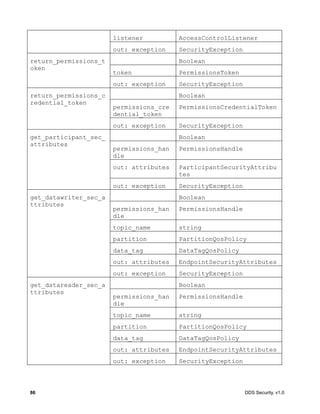
![DDS Security, v1.0 115
create_local_participant_crypto_tokens
create_local_datawriter_crypto_tokens
create_local_datareader_crypto_tokens
Parameter exception: A SecurityException object, which provides details in case this operation
returns false.
8.5.1.9 CryptoTransform interface
This interface groups the operations related to encrypting/decrypting, as well as, computing and
verifying both message digests (hashes) and Message Authentication Codes (MAC).
MACs may be used to verify both the (data) integrity and the authenticity of a message. The
computation of a MAC (also known as a keyed cryptographic hash function), takes as input a secret
key and an arbitrary-length message to be authenticated, and outputs a MAC. The MAC value protects
both a message's data integrity, as well as, its authenticity by allowing verifiers (who also possess the
secret key) to detect any changes to the message content.
A Hash-based Message Authentication Code (HMAC) is a specialized way to compute MACs. While
an implementation of the plugin is not forced to use HMAC, and could use other MAC algorithms, the
API is chosen such that plugins can implement HMAC if they so choose.
The operations in the CryptoTransform Plugin are defined to be quite generic, taking an input
byte array to transform and producing the transformed array of bytes as an output. The DDS
implementation is only responsible for calling the operations in the CryptoTransform plugin at the
appropriate times as it generates and processes the RTPS messages, substitutes the input bytes with the
transformed bytes produced by the CryptoTransform operations, and proceeds to generate/send or
process the RTPS message as normal but with the replaced bytes. The decision of the kind of
transformation to perform (encrypt and/or produce a digest and/or a MAC and/or signature) is left to
the plugin implementation.
Table 29 – CryptoTransform interface
CryptoTransform
No Attributes
Operations
encode_serialized_pa
yload
Boolean
out:
encoded_buffer
octet[]
out:
extra_inline_qos
octet[]
plain_buffer octet[]
sending_datawrit
er_crypto
DatawriterCryptoHandle
out: exception SecurityException](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-129-320.jpg)
![116 DDS Security, v1.0
encode_datawriter_su
bmessage
Boolean
out:
encoded_rtps_sub
message
octet[]
plain_rtps_subme
ssage
octet[]
sending_datawrit
er_crypto
DatawriterCryptoHandle
receiving_datare
ader_crypto_list
DatareaderCryptoHandle[]
out: exception SecurityException
encode_datareader_su
bmessage
Boolean
out:
encoded_rtps_sub
message
octet[]
plain_rtps_subme
ssage
octet[]
sending_dataread
er_crypto
DatareaderCryptoHandle
receiving_datawr
iter_crypto_list
DatawriterCryptoHandle[]
out: exception SecurityException
encode_rtps_message Boolean
out:
encoded_rtps_mes
sage
octet[]
plain_rtps_messa
ge
octet[]
sending_crypto ParticipantCryptoHandle
receiving_crypto
_list
ParticipantCryptoHandle[]
out: exception SecurityException
decode_rtps_message Boolean
out:
plain_buffer
octet[]
encoded_buffer octet[]](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-130-320.jpg)
![DDS Security, v1.0 117
receiving_crypto ParticipantCryptoHandle
sending_crypto ParticipantCryptoHandle
out: exception SecurityException
preprocess_secure_su
bmsg
Boolean
out:
datawriter_crypt
o
DatawriterCryptoHandle
out:
datareader_crypt
o
DatareaderCryptoHandle
out:
secure_submessag
e_category
DDS_SecureSumessageCatego
ry_t
in:
encoded_rtps_sub
message
octet[]
receiving_crypto ParticipantCryptoHandle
sending_crypto ParticipantCryptoHandle
out: exception SecurityException
decode_datawriter_su
bmessage
Boolean
out:
plain_rtps_subme
ssage
octet[]
encoded_rtps_sub
message
octet[]
receiving_datare
ader_crypto
DatareaderCryptoHandle
sending_datawrit
er_crypto
DatawriterCryptoHandle
out: exception SecurityException
decode_datareader_su
bmessage
Boolean
out:
plain_rtps_subme
ssage
octet[]
encoded_rtps_sub
message
octet[]](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-131-320.jpg)
![118 DDS Security, v1.0
8.5.1.9.1 Operation: encode_serialized_payload
This operation shall be called by the DDS implementation as a result of the application calling the
write operation on the DataWriter associated with the DatawriterCryptoHandle specified in the
sending_datawriter_crypto parameter.
The operation receives the data written by the DataWriter in serialized form wrapped inside the
RTPS SerializedPayload submessage element and shall output an RTPS SecuredPayload
submessage element and a extra_inline_qos containing InlineQos formatted as a ParameterList,
see section 7.3.1.
If the returned extra_inline_qos is not empty, the parameters contained shall be added to the list of
inlineQos parameters present in the (Data or DataFrag) submessage. If the (Data or DataFrag)
submessage did not already have an inlineQos, then the inlineQos submessage element shall be added
and the submessage flags modified accordingly.
The DDS implementation shall call this operation for all outgoing RTPS Submessages with
submessage kind Data and DataFrag. The DDS implementation shall substitute the
SerializedPayload submessage element within the aforementioned RTPS submessages with the
SecuredPayload produced by this operation.
The implementation of encode_serialized_payload can perform any desired cryptographic
transformation of the SerializedPayload using the key material in the
sending_datawriter_crypto, including encryption, addition of a MAC, and/or signature. The
encode_serialized_payload shall include in the extra_inline_qos or the SecuredPayload
the CryptoTransformIdentifier and the additional information needed to identify the key
used and decode the SecuredPayload submessage element.
receiving_datawr
iter_crypto
DatawriterCryptoHandle
sending_dataread
er_crypto
DatareaderCryptoHandle
out: exception SecurityException
decode_serialized_pa
yload
Boolean
out:
plain_buffer
octet[]
encoded_buffer octet[]
inline_qos octet[]
receiving_datare
ader_crypto
DatareaderCryptoHandle
sending_datawrit
er_crypto
DatawriterCryptoHandle
out: exception SecurityException](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-132-320.jpg)
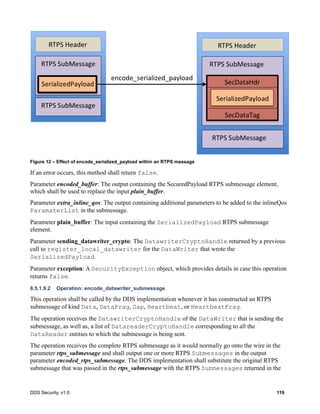




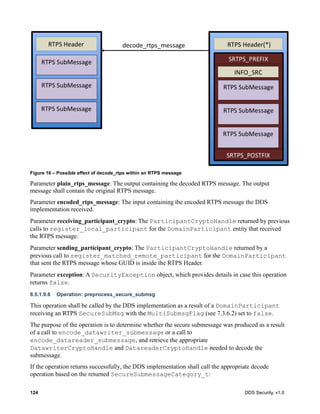



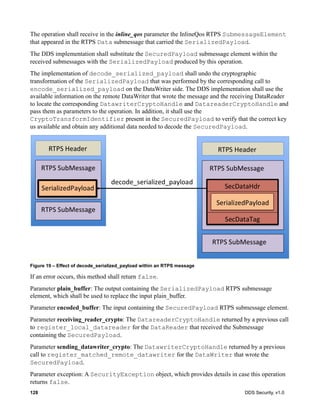
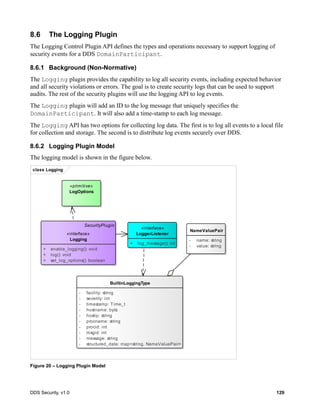

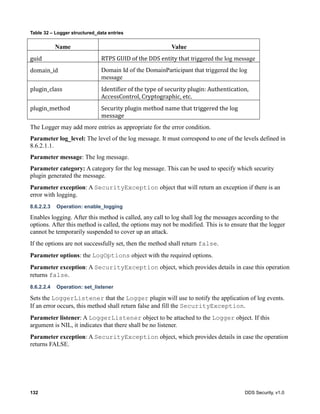



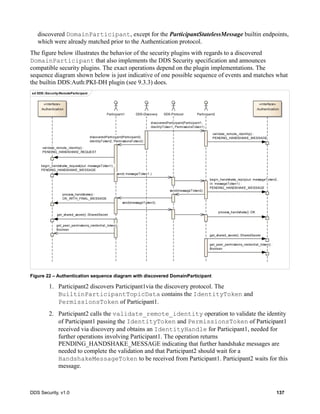

![DDS Security, v1.0 139
12. Participant1 sends the HandshakeMessageToken (messageToken3) to Participant2
using the BuiltinParticipantMessageWriter.
13. Participant2 receives the HandshakeMessageToken (messageToken3) on the
BuiltinParticipantMessageReader. Participant2 determines this message originated from a
remote DomainParticipant (Participant1) for which it had already called the
operation begin_handshake_reply where the call had returned
PENDING_HANDSHAKE_MESSAGE.
14. Participant2 calls the process_handshake operation, passing the received
HandshakeMessageToken (messageToken3). The Authentication plugin processes the
messageToken2, verifies it is a valid reply to the messageToken2 it had sent and returns
OK, indicating authentication is complete and no more messages need to be sent or
received.
15. Participant1, having completed the authentication of Participant2, calls the operation
get_shared_secret to retrieve the SharedSecret, which is used with the other
Plugins to create Tokens to exchange with Participant2.
16. Participant1, having completed the authentication of Participant2, calls the operation
get_authenticated_peer_credential_token to retrieve the
AuthenticatedPeerCredentialToken associated with Participant2, which is
used with the AccessControl plugin to determine the permissions that Participant1 will
grant to Participant2.
17. Participant2, having completed the authentication of Participant1, calls the operation
get_shared_secret to retrieve the SharedSecret, which is used with the other
Plugins to create Tokens to exchange with Participant1.
18. Participant2, having completed the Authentication of Participant1, calls the operation
get_authenticated_peer_credential_token to retrieve the
AuthenticatedPeerCredentialToken associated with Participant2 which is used
with the AccessControl plugins to determine the permissions that Participant2 will
grant to Participant1.
8.8.3 DDS Entities impacted by the AccessControl operations
There are six types of DDS Entities: DomainParticipant, Topic, Publisher,
Subscriber, DataReader, and DataWriter. All these except the DomainParticipant are
defined as the DDS Domain Entities (subclause 2.2.2.1.2 of DDS [1]).
The Domain Entities created by a DomainParticipant can be grouped into four categories:
DDS-RTPS Protocol [2] Builtin Entities. These are domain entities used to read and write the
four builtin Topics: DCPSParticipants, DCPSTopics, DCPSPublications,
DCPSSubscriptions.
Builtin Secure Entities. These are the Domain Entities related to the Builtin Secure
Endpoints defined in Section 7.4.5. These Entities are used to read and write the four
builtin secure topics: DCPSPublicationsSecure, DCPSSubscriptionsSecure,
ParticipantMessageSecure, and ParticipantVolatileMessageSecure.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-153-320.jpg)
![140 DDS Security, v1.0
Other builtin Entities defined by the DDS-Security specification not included in the
“Builtin Secure Endpoints”. These are the BuiltinParticipantStatelessMessageWriter and the
BuiltinParticipantStatelessMessageReader.
Application-defined Entities. These are any non-builtin Domain Entities.
The AccessControl plugin shall impact only the Builtin Secure Entities and the application-
defined Entities. It shall not impact the builtin entities defined by the DDS-RTPS Protocol
specification nor the BuiltinParticipantStatelessMessageWriter or the
BuiltinParticipantStatelessMessageReader.
AccessControl plugin operations can be grouped into 5 groups:
1. Group1. Operations related to DomainParticipant. These are: validate_local_permissions,
validate_remote_permissions, check_create_participant, get_permissions_token,
get_permissions_credential_token, set_listener, return_permissions_token,
return_permissions_credential_token, get_participant_sec_attributes.
2. Group2. Operations related to the creation of local Domain Entities. These are:
check_create_topic, check_create_datawriter, check_create_datareader,
get_datawriter_sec_attributes, get_datareader_sec_attributes.
3. Group3. Operations related to write activities of local Domain Entities. These are:
check_local_datawriter_register_instance and check_local_datawriter_dispose_instance.
4. Group4. Operations related to discovery and match of remote Domain Entities. These are:
check_remote_topic, check_remote_datawriter, check_remote_datareader,
check_local_datawriter_match, and check_local_datareader_match.
5. Group5. Operations related to the write activities of remote Domain Entities. These are:
check_remote_datawriter_register_instance and check_remote_datawriter_dispose_instance.
Table 33 below summarizes the DDS Entities affected by each operation group.
Table 33 – Impact of Access Control Operations to the DDS Builtin and Application-defined Entities
Entity
Category
Entity Impact by AccessControl operation in group
Group1 Group2 Group3 Group4 Group5
DomainPar
ticipant
All created Yes No No No No
DDS-RTPS
Protocol
Builtin
Entities
See RTPS Protocol
specification [2]
Yes,
indirectly
No No No No
Builtin
Secure
SEDPbuiltinPublicat
ionsSecureWriter
SEDPbuiltinPublicat
ionsSecureReader
SEDPbuiltinSubscrip
tionsSecureWriter
SEDPbuiltinSubscrip
Yes,
indirectly
Only
get_datawriter_
sec_attributes
No No No](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-154-320.jpg)








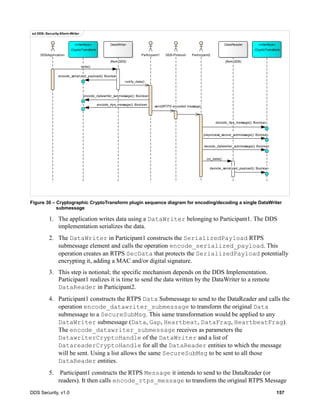

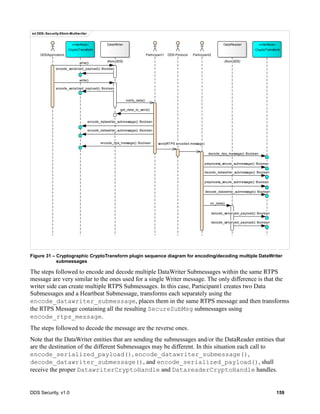
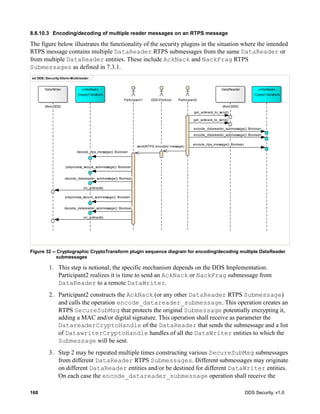

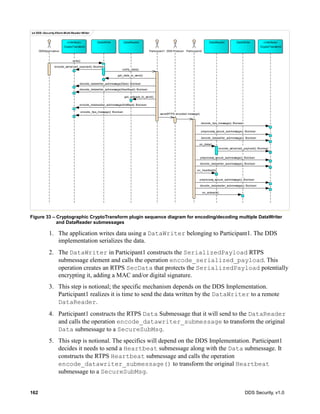




![168 DDS Security, v1.0
consumers of the builtin plugins will be users who want to secure their systems but not have complex
needs or significant legacy components. Under these conditions, ease-of-use is essential. A security
infrastructure that is too hard to configure or too complex to understand or maintain is less likely to be
used, or may be used wrongly, resulting in systems that are less secure overall.
The builtin plugins balance rich functionality and ease-of-use, providing for the most common use
cases, in a manner that is easy to understand and use correctly.
9.3 Builtin Authentication: DDS:Auth:PKI-DH
This builtin authentication plugin is referred to as the “DDS:Auth:PKI-DH”.
The DDS:Auth:PKI-DH plugin implements authentication using a trusted Certificate
Authority (CA). It performs mutual authentication between discovered participants using the RSA
or ECDSA Digital Signature Algorithms [11] and establishes a shared secret using Diffie-Hellman
(DH) or Elliptic Curve Diffie-Hellman (ECDH) Key Agreement Methods [12].
The CA could be an existing one. Or a new one could be created for the purpose of deploying
applications on a DDS Domain. The nature or manner in which the CA is selected is not important
because the way it is used enforces a shared recognition by all participating applications.
Prior to a DomainParticipant being enabled the DDS:Auth:PKI-DH plugin associated with the
DomainParticipant must be configured with three things:
1. The X.509 Certificate that defines the Shared Identity CA. This certificate
contains the Public Key of the CA.
2. The Private Key of the DomainParticipant.
3. An X.509 Certificate that chains up to the Shared Identity CA, that binds the
Public Key of the DomainParticipant to the Distinguished Name (subject name)
for the DomainParticipant.
9.3.1 Configuration
The builtin authentication plugin shall be configured using the PropertyQosPolicy of the
DomainParticipantQos. The specific properties used are described in Table 35 below.
Table 35 – Properties used to configure the builtin Authentication plugin
Property Name
(all properties have
“dds.sec.auth” prefix)
Property Value
(all these properties shall have propagate set to FALSE)
URI syntax follows IETF RFC 3986.
URI “data” schema follows IETF RFC 2397
URI “pkcs11” schema follows IETF RFC 7512
Vendors may support additional schemas
identity_ca URI to the X509 certificate [39] of the Identity CA.
Supported URI schemes: file, data, pkcs11
The file and data schemas shall refer to a X.509 v3 certificate (see X.509
v3 ITU-T Recommendation X.509 (2005) [39]) in PEM format.
Examples:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-182-320.jpg)
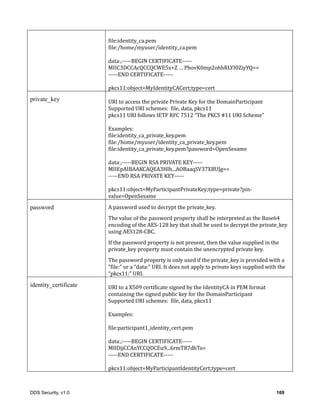
![170 DDS Security, v1.0
9.3.1.1 Identity CA Certificate
The certificate used to configure the public key of the Identity CA.
The certificate shall be the X.509 v3 Certificate [39] of the issuer of the Identity Certificates in section
9.3.1.3. The certificate can be self-signed if it is a root CA or signed by some other CA public key if it
is a subordinate CA. Regardless of this the Public Key in the Certificate shall be accepted as the one
for the Identity CA trusted to sign DomainParticipant Identity Certificates, see 9.3.1.3.
The public key of the CA shall be either a 2048-bit RSA key [44] or else a 256-bit Elliptic Curve Key
for the prime256v1 curve [41], also known as the NIST P-256 curve [42].
The Identity CA Certificate shall be provided to the plugins using the PropertyQosPolicy on the
DomainParticipantQos as specified in Table 35.
9.3.1.2 Private Key
The Private Key associated with the DomainParticipant. It may be either a 2048-bit RSA private
key or a 256-bit Elliptic Curve Key for use with the prime256v1 curve [41].
The Private Key shall be provided to the plugins using the PropertyQosPolicy on the
DomainParticipantQos as specified in Table 35.
9.3.1.3 Identity Certificate
An X.509 v3 Certificate [39] that chains up to the Identity CA (see 9.3.1.1). The Identity Certificate
binds the Public Key of the DomainParticipant to the Distinguished Name (subject name) for the
DomainParticipant.
9.3.2 DDS:Auth:PKI-DH Types
This sub clause specifies the content and format of the Credential and Token objects used by the
DDS:Auth:PKI-DH plugin.
Credential and Token attributes left unspecified in this specification shall be understood to not
have any required values in this specification. These attributes shall be handled according to the
following rules:
Plugin implementations may place data in these attributes as long as they also include a property
attribute that allows the implementation to unambiguously detect the presence and interpret these
attributes.
Attributes that are not understood shall be ignored.
Property_t and BinaryProperty_t names shall comply with the rules defined in 7.2.1 and
7.2.2, respectively.
The content of the Handle objects is not specified as it represents references to internal state that is
only understood by the plugin itself. The DDS Implementation only needs to hold a reference to the
returned Handle objects returned by the plugin operations and pass these Handle references to other
operations.
9.3.2.1 DDS:Auth:PKI-DH IdentityToken
The DDS:Auth:PKI-DH plugin shall set the attributes of the IdentityToken object as specified in
the table below:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-184-320.jpg)
![172 DDS Security, v1.0
9.3.2.3.1 HandshakeRequestMessageToken objects
The attributes in HandshakeRequestMessageToken objects shall be set as specified in the table
below. References to the DomainParticipant within the table refer to the
DomainParticipant that is creating the HandshakeRequestMessageToken.
Table 38 – HandshakeRequestMessageToken for the builtin Authentication plugin
Attribute name Attribute value
class_id “DDS:Auth:PKI-DH:1.0+Req”
binary_properties name value
c.id Contents of the certificate signed by IdentityCA that was
configured using the Participant PropertyQosPolicy with
name “dds.sec.auth.identity_certificate”
c.perm Contents of the permissions document signed by the
PermissionCA that was configured using the Participant
PropertyQosPolicy with name “dds.sec.access.permissions”
c.pdata The CDR Big Endian Serialization of the
ParticipantBultinTopicData
c.dsign_algo Digital signature algorithm identifier.
Either “RSASSA-PSS-SHA256” or “ECDSA-SHA256”
c.kagree_algo Key agreement algorithm identifier.
Either “DH+MODP-2048-256” or “ECDH+prime256v1-
CEUM”
hash_c1 SHA-256 hash of the CDR Big Endian serialization of a
BinaryPropertySeq object containing all the properties
above that start with “c.” placed in the same order as they
appear above.
Inclusion of the hash_c1 property is optional. Its only
purpose is to facilitate troubleshoot interoperability
problems.
dh1 The CDR Big Endian Serialization of a Diffie-Hellman Public
Key chosen by the Participant. This will be used for key
agreement.
challenge1 A Random Challenge generated by the Participant,
compliant with the recommendations of Section 3.2.1 of
FIPS-196 [46]
Plugin implementations may add extra properties as long as the names comply with the rules defined in
in 7.2.1. Plugin implementations shall ignore any properties they do not understand.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-186-320.jpg)
![174 DDS Security, v1.0
purpose is to facilitate troubleshoot interoperability
problems.
dh1 The value of the related HandshakeRequestMessageToken
property dh1.
Inclusion of the dh1 property is optional. Its only purpose
is to facilitate troubleshoot interoperability problems.
challenge1 Value of the related HandshakeRequestMessageToken
property challenge1.
challenge2 A Random Challenge generated by the Participant,
compliant with the recommendations of Section 3.2.1 of
FIPS-196 [46].
signature The Digital Signature of the CDR Big Endian serialization of
a BinaryPropertySeq object containing the properties:
hash_c2, challenge2, dh2, challenge1, dh1, and hash_c1,
placed in that order.
All the aforementioned properties shall appear within the
signature even if some of the optional properties do not
appear separately as properties in the
HandshakeReplyMessageToken.
Plugin implementations may add extra properties as long as the names comply with the rules defined in
7.4.3.5. Plugin implementations shall ignore any properties they do not understand.
If the value of the c. kagree_algo property is “DH+MODP-2048-256”, then:
The Diffie-Hellman Public Key shall be for the 2048-bit MODP Group with 256-bit Prime
Order Subgroup, see IETF RFC 5114 [47], section 2.3.
The Key Agreement Algorithm shall be the “dhEphem, C(2e, 0s, FFC DH) Scheme” defined
in section 6.1.2.1 of NIST Special Publication 800-56A Revision 2 [48].
Non-normative note: The OpenSSL 1.0.2 operation DH_get_2048_256() retrieves the parameters for
the 2048-bit MODP Group with 256-bit Prime Order Subgroup.
If the value of the c.kagree_algo property is “ECDH+prime256v1-CEUM”, then:
The Diffie-Hellman Public Key shall be for the NIST’s EC Curve P-256 as defined in appendix
D of FIPS 186-4 [42] also known as prime256v1 in ANSI X9.62-2005 [41].
The Key Agreement Algorithm shall be the “(Cofactor) Ephemeral Unified Model, C(2e, 0s,
ECC CDH)” defined in section 6.1.2.2 of NIST Special Publication 800-56A Revision 2 [48].
See also section 3.1 “Ephemeral Unified Model” of NIST Suite B Implementer’s Guide to
NIST SP 800-56A [49].
The digital signature shall be computed using the Private Key associated with the DomainParticipant,
which corresponds to the Public Key that appears in the Identity Certificate.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-188-320.jpg)
![DDS Security, v1.0 175
If the Participant Private Key is a RSA key, then:
The value of the c.dsign_algo property shall be “RSASSA-PSS-SHA256”.
The digital signature shall be computed using the RSASSA-PSS algorithm specified in PKCS
#1 (IETF 3447) RSA Cryptography Specifications Version 2.1 [44], using SHA256 as hash
function, and MGF1 with SHA256 (mgf1sha256) as mask generation function.
If the Participant Private Key is an EC key, then:
The value of the c.dsign_algo shall be “ECDSA-SHA256”.
The digital signature shall be computed using the ECDSA-SHA256 algorithm specified in
ANSI X9.62-2005 [41].
9.3.2.3.3 HandshakeFinalMessageToken
HandshakeFinalMessageToken objects are used to finish an authentication handshake and
communicate a SharedSecret. References to the DomainParticipant within the table refer to
the DomainParticipant that is creating the HandshakeFinalMessageToken.
The SharedSecret shall be a 256-bit random number generated using a cryptographically-strong
random number generator. Each created HandshakeFinalMessageToken shall have associated a
unique SharedSecret.
The attributes in the HandshakeFinalMessageToken objects shall be set as specified in the table
below.
Table 40 – HandshakeFinalMessageToken for the builtin Authentication plugin
Attribute name Attribute value
class_id “DDS:Auth:PKI-DH:1.0+Final”.
binary_properties name value
hash_c1 The value of the related HandshakeRequestMessageToken
property hash_c1.
Inclusion of the hash_c1 property is optional. Its only purpose
is to facilitate troubleshoot interoperability problems.
hash_c2 The value of the related HandshakeReplyMessageToken
property hash_c2.
Inclusion of the hash_c2 property is optional. Its only purpose
is to facilitate troubleshoot interoperability problems.
dh1 The value of the related HandshakeRequestMessageToken
property dh1.
Inclusion of the dh1 property is optional. Its only purpose is to
facilitate troubleshoot interoperability problems.
dh2 The value of the related HandshakeReplyMessageToken
property dh2.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-189-320.jpg)
![176 DDS Security, v1.0
Inclusion of the dh2 property is optional. Its only purpose is to
facilitate troubleshoot interoperability problems. |
challenge1 Value of HandshakeRequestMessageToken property
challenge1
challenge2 Value of HandshakeReplyMessageToken property challenge2
signature The Digital Signature of the CDR Big Endian serialization of a
BinaryPropertySeq object containing the properties: hash_c1,
challenge1, dh1, challenge2, dh2, and hash_c2, placed in that
order.
All the aforementioned properties shall appear within the
signature even if some of the optional properties do not appear
separately as properties in the HandshakeFinalMessageToken.
The Diffie Hellman public key shall be for the same algorithm and Domain Parameters that were used
for the HandshakeRequestMessageToken key received as value of the dh2 property. The
parameters and algorithm shall be determined based on the value of the
HandshakeRequestMessageToken parameter with key c.kagree_algo. In other words, it is the
Participant that creates the HandshakeRequestMessageToken the one that controls the key
agreement algorithm used.
The digital signature shall be computed using the Private Key associated with the DomainParticipant,
which corresponds to the Public Key that appears in the Identity Certificate.
If the Participant Private Key is a RSA key, then the digital signature shall be computed using the
RSASSA-PSS algorithm specified in PKCS #1 (IETF 3447) RSA Cryptography Specifications Version
2.1 [44], using SHA256 as hash function, and MGF1 with SHA256 (mgf1sha256) as mask generation
function.
If the Participant Participant Private Key is an EC key, then the digital signature shall be computed
using the ECDSA-SHA256 algorithm specified in ANSI X9.62-2005 [41].
9.3.3 DDS:Auth:PKI-DH plugin behavior
The table below describes the actions that the DDS:Auth:PKI-DH plugin performs when each of the
plugin operations is invoked.
Table 41 – Actions undertaken by the operations of the builtin Authentication plugin
validate_local_ide
ntity
This operation shall receive the participant_key associated with
the local DomainParticipant whose identity is being
validated.
The operation shall receive the DomainParticipantQos
with a PropertyQosPolicy containing the properties defined
in section 9.3.1.
The operation shall verify the validity of the X509 certificate
associated with the property named
dds.sec.auth.identity_certificate using the CA configured by the](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-190-320.jpg)




![186 DDS Security, v1.0
9.4 Builtin Access Control: DDS:Access:Permissions
This builtin AccessControl plugin is referred to as the “DDS:Access:Permissions” plugin.
The DDS:Access:Permissions implements the AccessControl plugin API using a permissions
document signed by a shared Certificate Authority (CA).
The shared CA could be an existing one (including the same CA used for the Authentication
plugin), or a new one could be created for the purpose of assigning permissions to the applications on a
DDS Domain. The nature or manner in which the CA is selected is not important because the way it is
used enforces a shared recognition by all participating applications.
Each DomainParticipant has an associated instance of the DDS:Access:Permissions plugin.
9.4.1 Configuration
The DDS:Access:Permissions plugin is configured with three documents:
The Permissions CA certificate
The Domain governance signed by the Permissions CA
The DomainParticipant permissions signed by the Permissions CA
The configuration of the builtin access control plugin shall be done using the PropertyQosPolicy
of the DomainParticipantQos. The specific properties used are described in Table 45 below.
Table 45 – Properties used to configure the builtin AccessControl plugin
Property Name
(all properties have
“dds.sec.access” prefix)
Property Value
(all these properties shall have propagate set to FALSE)
URI syntax follows IETF RFC 3986.
URI “data” schema follows IETF RFC 2397
Vendors may support additional schemas
permissions_ca URI to a X509 certificate for the PermissionsCA in PEM format.
Supported URI schemes: file, data, pkcs11
The file and data schemas shall refer to a X.509 v3 certificate (see X.509
v3 ITU-T Recommendation X.509 (2005) [39]) in PEM format.
Examples:
file:permissions_ca.pem
file:/home/myuser/ permissions_ca.pem
data:,-----BEGIN CERTIFICATE-----
MIIC3DCCAcQCCQCWE5x+Z … PhovK0mp2ohhRLYI0ZiyYQ==
-----END CERTIFICATE-----
pkcs11:object= MyPermissionsCACert;type=cert
governance URI to the shared Governance Document signed by the Permissions CA in
S/MIME format
URI schemes: file, data
Example file URIs:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-200-320.jpg)







![194 DDS Security, v1.0
The topic access rules shall be evaluated in the same order as they appear within the
<topic_access_rules> Section. If multiple rules match the first rule that matches is the only one that
applies.
9.4.1.2.5.1 Topic expression element
This element is delimited by the XML element <topic_expression>.
The value in this element identifies the set of DDS Topic names to which the rule applies. The rule
will apply to any DataReader or DataWriter associated with a Topic whose name matches the
value.
The Topic name expression syntax and matching shall use the syntax and rules of the POSIX
fnmatch() function as specified in POSIX 1003.2-1992, Section B.6 [38].
9.4.1.2.5.2 Enable Discovery protection element
This element is delimited by the XML element <enable_discovery_protection>.
This element may take the binary values TRUE or FALSE.
The setting controls the contents of the EndpointSecurityAttributes returned by the
AccessControl::get_datawriter_sec_attributes or
AccessControl::get_datareader_sec_attributes operation on an endpoint whose
associated Topic name matches the rule’s topic expression. Specifically the is_discovery_protected
attribute in the EndpointSecurityAttributes shall be set to the binary value specified in the
“enable discovery protection" element.
9.4.1.2.5.3 Enable Read Access Control element
This element is delimited by the XML element <enable_read_access_control>.
This element may take the binary values TRUE or FALSE.
The setting shall control the contents of the EndpointSecurityAttributes returned by the
AccessControl::get_datawriter_sec_attributes operation on any DataWriter
entity whose associated Topic name matches the rule’s topic expression. Specifically the
is_access_protected attribute in the EndpointSecurityAttributes shall be set to the binary
value specified in the “enable read access protection" element.
In addition, this element shall control the AccessControl::check_create_datareader
operation on any DataReader entity whose associated Topic name matches the rule’s topic
expression. Specifically:
If the value of “enable_read_access_control” element is FALSE, the operation
check_create_datareader shall return TRUE without further checking the Permissions
document.
If the value of “enable_read_access_control” element is TRUE, the operation
check_create_datareader shall return a value according to what is specified in the
Permissions document, see 9.4.1.3.
9.4.1.2.5.4 Enable Write Access Control element
This element is delimited by the XML element <enable_write_access_control>.
This element may take the binary values TRUE or FALSE.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-208-320.jpg)






![DDS Security, v1.0 201
Each grant Section contains three sections:
1. Subject name Section (subject_name element)
2. Validity Section (validity element)
3. Rules Section (allow, deny and default elements)
The contents and delimiters of each Section are described below.
9.4.1.3.2.1 Subject name Section
This Section is delimited by the XML element <subject_name>.
The subject name Section identifies the DomainParticipant to which the permissions apply. Each
subject name can only appear in a single <permissions> Section within the XML Permissions
document.
The contents of the <subject_name> element shall be the x.509 subject name for the
DomainParticipant as is given in its Authorization Certificate. A permissions Section with a
subject name that does not match the subject name given in the corresponding Authorization certificate
shall be ignored.
The X.509 subject name is a set of name-value pairs. The format of x.509 subject name shall be the
string representation of the X.509 certificate Subject name as defined in IETF RFC 4514 "Lightweight
Directory Access Protocol (LDAP): String Representation of Distinguished Names" [51].
For example:
<subject_name>emailAddress=cto@acme.com, CN=DDS Shapes Demo, OU=CTO Office,
O=ACME Inc., L=Sunnyvale, ST=CA, C=US</subject_name>
9.4.1.3.2.2 Validity Section
This Section is delimited by the XML element <validity>. The contents of this element reflect the
valid dates for the permissions. It contains both the starting date and the end date in GMT formatted as
YYYYMMDDHH.
A permissions Section with a validity date that falls outside the current date at which the permissions
are being evaluated shall be ignored.
9.4.1.3.2.3 Rules Section
This Section contains the permissions assigned to the DomainParticipant. It is described as a set
of rules.
The rules are applied in the same order that appear in the document. If the criteria for the rule matches
the domain_id join and/or publish or subscribe operation that is being attempted, then the allow or
deny decision is applied. If the criteria for a rule does not match the operation being attempted, the
evaluation shall proceed to the next rule. If all rules have been examined without a match, then the
decision specified by the “default” rule is applied. The default rule, if present, must appear after all
allow and deny rules. If the default rule is not present, the implied default decision is DENY.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-215-320.jpg)
![202 DDS Security, v1.0
The matching criteria for each rule specify the domain_id, topics (published and subscribed), the
partitions (published and subscribed), and the data-tags associated with the DataWriter and
DataReader.
For the grant to match there shall be a match of the topics, partitions, and data-tags criteria. This is
interpreted as an AND of each of the criteria. For a specific criterion to match (e.g., <topics>) it is
enough that one of the topic expressions listed matches (i.e., an OR of the expressions with the
<topics> section).
9.4.1.3.2.3.1 Format of the allow rules
Allow rules appear inside the <allow_rule> XML Element. Each rule contains the domain IDs to
which the rule applies, and the topic names that are allowed to be published and subscribed within
those domains.
9.4.1.3.2.3.1.1 Domains Section
This Section is delimited by the XML element <domain_id>.
The value in this element identifies the collection of DDS domain_id values to which the rule applies.
The syntax is the same as for the domain section of the Governance document. See subclause
9.4.1.2.4.1.
For example:
<domains>
<id>0</id>
</domains>
9.4.1.3.2.3.1.2 Publish Section
This Section defines the Topic names that the rule allows to be published.
The publish Section shall be delimited by the <publish> XML Element.
The topic names appear in the Section delimited by the <topics> XML element. Topic names may be
given explicitly or by means of Topic name expressions. Each topic name or topic-name expression
appears separately in a <topic> sub-element within the <topics> element.
The Topic name expression syntax and matching shall use the syntax and rules of the POSIX fnmatch()
function as specified in POSIX 1003.2-1992, Section B.6 [38].
The publish Section may also include one or more sections delimited by the <partitions> XML
Element. The <partition> XML Elements contain the DDS Partition names where it is allowed to
publish the specified Topic names. Partition names may be given explicitly or by means of Partition
name expressions. Each partition name or partition-name expression appears separately in a
<partition> sub-element within the <partitions> element.
The Partition name expression syntax and matching shall use the syntax and rules of the POSIX
fnmatch() function as specified in POSIX 1003.2-1992, Section B.6 [38]. If there is no <partitions>
Section then the rule allows publishing only in the "empty string" partition. See PARTITION
QosPolicy entry in Qos Policies table of section 2.2.3 (Supported Qos) of the DDS Specification
version 1.4.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-216-320.jpg)
![DDS Security, v1.0 203
The publish Section may also include one or more sections delimited by the <data_tags> XML
Element. The <data_tags> XML Elements contain a set of tags that shall be associated with the
DataWriter that publishes the data on the Topic names allowed by the rule.
Example1:
<publish>
<topics>
<topic>Circle1</topic>
</topics>
</publish>
Example2:
<publish>
<topics>
<topic>Square</topic>
</topics>
<partitions>
<partition>A_partition</partition>
</partitions>
</publish>
Example3:
<publish>
<topics>
<topic>Cir*</topic>
</topics>
<data_tags>
<tag>
<name>aTagName1</name>
<value>aTagValue1</value>
</tag>
</data_tags>
</publish>
9.4.1.3.2.3.1.3 Subscribe Section
This Section defines the Topic names that the rule allows to be subscribed.
The subscribe Section shall be delimited by the <subscribe> XML Element.
The topic names appear in the Section delimited by the <topics> XML element. Topic names may be
given explicitly or by means of Topic name expressions. Each topic name or topic-name expression
appears separately in a <topic> sub-element within the <topics> element.
The Topic name expression syntax and matching shall use the syntax and rules of the POSIX fnmatch()
function as specified in POSIX 1003.2-1992, Section B.6 [38].
The subscribe Section may also include one or more sections delimited by the <partitions> XML
Element. The <partition> XML Elements contain the DDS Partition names where it is allowed to
subscribe to the specified Topic names. Partition names may be given explicitly or by means of
Partition name expressions. Each partition name or partition-name expression appears separately in a
<partition> sub-element within the <partitions> element.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-217-320.jpg)
![204 DDS Security, v1.0
The Partition name expression syntax and matching shall use the syntax and rules of the POSIX
fnmatch() function as specified in POSIX 1003.2-1992, Section B.6 [38]. If there is no <partitions>
Section, then the rule allows subscribing only in the "empty string" partition. See PARTITION
QosPolicy entry in Qos Policies table of section 2.2.3 (Supported Qos) of the DDS Specification
version 1.4.
The subscribe Section may also include one or more sections delimited by the <data_tags> XML
Element. The <data_tags> XML Elements contain a set of tags that shall be associated with the
DataReader that subscribes the data on the Topic names allowed by the rule.
Example1:
<subscribe>
<topics>
<topic>Circle1</topic>
</topics>
</subscribe>
Example2:
<subscribe>
<topics>
<topic>Square</topic>
</topics>
<partitions>
<partition>A_partition</partition>
</partitions>
</subscribe>
Example3:
<subscribe>
<topics>
<topic>Cir*</topic>
<topics>
<data_tags>
<tag>
<name>aTagName1</name>
<value>aTagValue1</value>
</tag>
</data_tags>
</subscribe>
9.4.1.3.2.3.1.4 Example allow rule
<allow_rule>
<domains>
<id>0</id>
</domains>
<publish>
<topics>
<topic>Cir*</topic>
</topics>
<data_tags>](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-218-320.jpg)




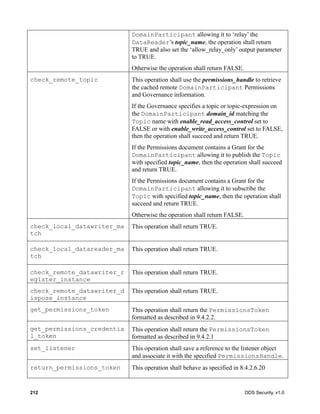
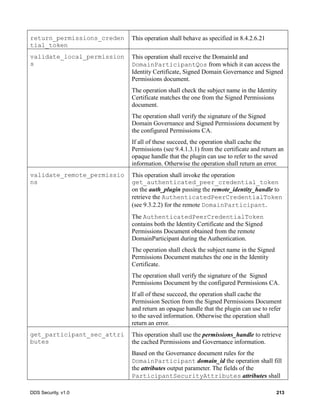
![214 DDS Security, v1.0
be set according to the following rules:
If the Governance document has the element
allow_unauthenticated_participants set to FALSE, the
attributes field allow_unauthenticated_participants shall be
set to FALSE. Otherwise the field shall be set to TRUE.
If the Governance document has the element
enable_join_access_control set to FALSE, the attributes
field is_access_protected shall be set to FALSE. Otherwise
the field shall be set to TRUE.
If the Governance document has the element
rtps_protection_kind set to NONE, the attributes field
is_rtps_protected shall be set to FALSE. Otherwise the field
shall be set to TRUE.
9.5 Builtin Crypto: DDS:Crypto:AES-GCM-GMAC
The builtin Cryptographic plugin is referred to as “DDS:Crypto:AES-GCM-GMAC” plugin.
DDS:Crypto:AES-GCM-GMAC provides authenticated encryption using Advanced Encryption
Standard (AES) in Galois Counter Mode (AES-GCM) [45]. It supports two AES key sizes: 128 bits
and 256 bits. It may also provide additional reader-specific message authentication codes (MACs)
using Galois MAC (AES-GMAC) [45].
The definition of the AES-GCM and AES-GMAC transformations shall be as specified in NIST SP
800-38D [45] specialized to 128-bit and 256-bit AES keys with 96-bit Initialization Vector. The most
relevant aspects are summarized below.
The AES-GCM authenticated encryption operation is a transformation that takes the four inputs and
produces two outputs, symbolically:
C, T = AES-GCM(K, P, AAD, IV)
The AES-GCM inputs are described in Table 49 below.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-228-320.jpg)
![DDS Security, v1.0 215
Table 49 – AES-GCM transformation inputs
Input Description
K The 128-bit key to be used with the AES-128 block cipher
or the 256-bit key to be used with the AES-256 block cipher.
P The plaintext. This is the data to encrypt and authenticate.
It may be empty in case we only want to authenticate data.
AAD Additional Autenticated Data.
This is data beyond the plaintext that will only be authenticated. I.e. it is not
encrypted.
IV Initialization Vector.
This is a 96-bit NONCE that shall not be repeated for the same key.
The AES-GCM transformation outputs are described in Table 50 below.
Table 50 – AES-GCM trasnsformation outputs
Input Description
C Ciphertext.
This is the encryption of the plaintext “P”.
T Authentication Tag.
This is a Message Authentication Code (MAC) that provides authentication for
the Ciphertext (C) and the Additional Authenticated Data (AAD).
AES-GCM uses AES in counter mode with a specific incrementing function called “inc32” used to
generate the counter blocks. As recommended in section 5.2.1.1 of NIST SP 800-38D [45] the counter
blocks shall be created from the 96-bit Initialization Vector as follows:
The initial value of the 128-bit counter block is a 128-bit string containing the IV as the leading
96 bits and zeros the remaining right-most 32 bits.
Incremental values of the 128-bit counter block used to encrypt each block are obtained using
the “inc32” function which increments the right-most 32 bits of the string, regarded as the
binary representation of a big-endian integer, modulo 2^32. The inc32 operation does not touch
the leading 96 bits.
The AES-GMAC transformation is defined as the special case where the plaintext “P” is empty (zero
length). This transformation produces only an AuthenticationTag (Message Authentication Code) on
the AAD data:
T = AES-GMAC(K, AAD, IV) = AES-GCM(K, “”, AAD, IV)
The use of (Galois) counter mode allows authenticated decryption of blocks in arbitrary order. All that
is needed to decrypt and validate the authentication tag are the Key and the Initialization Vector. This is](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-229-320.jpg)


![218 DDS Security, v1.0
A zero value for receiver_specific_key_id indicates there is no receiver-specific authentication tags and
shall occur if and only if the length of the master_receiver_specific_key is also zero.
9.5.2.1.2 Key material used by the BuiltinParticipantVolatileMessageSecureWriter and
BuiltinParticipantVolatileMessageSecureReader
The Key Material used by the BuiltinParticipantVolatileMessageSecureWriter and
BuiltinParticipantVolatileMessageSecureReader shall be derived from the SharedSecret obtained
as part of the authentication process. The attributes of the KeyMaterial_AES_GCM_GMAC shall be
set as described in Table 52 below. This uses HMAC-Based Key Derivation (HKDF) recommended in
IETF RFC 5869 [50].
Table 52 – KeyMaterial_AES_GCM_GMAC for BuiltinParticipantVolatileMessageSecureWriter and
BuiltinParticipantVolatileMessageSecureReader
Attribute name Attribute value
transformation_kind CRYPTO_TRANSFORMATION_KIND_AES128_GCM or
CRYPTO_TRANSFORMATION_KIND_AES256_GCM
master_salt HMACsha256 ( sha256(Challenge1 | KxSaltCookie | Challenge2) ,
SharedSecret)
The parameters to the above functions are defined in Table 53.
In the case where transformation_kind is
CRYPTO_TRANSFORMATION_KIND_AES128_GCM this is
truncated to the first 128 bits.
sender_key_id 0
master_sender_key HMACsha256 ( sha256(Challenge2 | KxKeyCookie | Challenge1) ,
SharedSecret )
The parameters to the above functions are defined in Table 53.
In the case where transformation_kind is
CRYPTO_TRANSFORMATION_KIND_AES128_GCM this is truncated
to the first 128 bits.
receiver_specific_key_id 0
master_receiver_specific_key Zero-length sequence
Table 53 – Terms used in KxKey and KxMacKey derivation formula for the builtin Cryptographic plugin
Term Meaning
Challenge1 The challenge that was sent in the challenge1 attribute of the
HandshakeRequestMessageToken as part of the Authentication
protocol.
This information shall be accessible from the
SharedSecretHandle.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-232-320.jpg)
![DDS Security, v1.0 219
Challenge2 The challenge that was sent in the challenge2 attribute of the
HandshakeReplyMessageToken as part of the Authentication
protocol.
This information shall be accessible from the
SharedSecretHandle.
SharedSecret The shared secret established as part of the key agreement protocol.
This information shall be accessible from the
SharedSecretHandle.
KxKeyCookie The 16 bytes in the string “key exchange key”
KxSaltCookie The 16 bytes in the string “keyexchange salt”
data1 | data2 | data3 The symbol ‘|’ is used to indicate byte string concatenation
HMACsha256(key, data) Computes the hash-based message authentication code on ‘data’
using the key specified as first argument and a SHA256 hash as
defined in [27].
9.5.2.2 DDS:Crypto:AES-GCM-GMAC CryptoTransformIdentifier
The DDS:Crypto:AES-GCM-GMAC shall set the CryptoTransformIdentifier attributes as
specified in the table below:
Table 54 – CryptoTransformIdentifier class for the builtin Cryptographic plugin
Attribute Value
transformation_kind Set to one of the following values (see section 9.5.2.1.1):
CRYPTO_TRANSFORMATION_KIND_NONE
CRYPTO_TRANSFORMATION_KIND_AES128_GMAC
CRYPTO_TRANSFORMATION_KIND_AES128_GCM
CRYPTO_TRANSFORMATION_KIND_AES256_GMAC
CRYPTO_TRANSFORMATION_KIND_AES256_GCM
The variants containing AES128 in their name indicate that
the encryption and/or authentication use AES with 128-bit
key as the underlaying cryptographic engine. These variants
shall have master_sender_key with 16 octets in length and
master_receiver_specific_key with either zero or 16 octets in
length.
The variants containing AES256 in their name indicate that
the encryption and/or authentication use AES with 256-bit
key as the underlaying cryptographic engine. These variants
shall have master_sender_key with 32 octets in length and
master_receiver_specific_key with either zero or 32 octets in
length.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-233-320.jpg)
![220 DDS Security, v1.0
The variants with name ending with GCM indicate that the
transformation is the standard authenticated encryption
operation known as AES-GCM (AES using Galois Counter
Mode) where the plaintext is encrypted and followed by an
authentication tag computed using the same secret key. These
variants may contain zero or more receiver-specific
authentication tags. If receiver_specific_key_id is set to zero
there shall be no receiver-specific tags otherwise there shall
be one or more receiver-specific tags.
The variants ending in GMAC indicate that there is no
encryption (i.e., the ciphertext matches the input plaintext) and
there is an authentication tag computed using the sender key
that is shared with all the readers. These variants may contain
zero or more receiver-specific authentication tags. If
receiver_specific_key_id is set to zero there shall be no
receiver-specific tags otherwise there shall be one or more
receiver-specific tags.
transformation_key_id This is set to a different value each time new Key Material is
produced by a DomainParticipant. The algorithm used is
implementation specific but it shall avoid repeating the values
for the same DomainParticipant.
9.5.2.3 DDS:Crypto:AES-GCM-GMAC SecureDataHeader
The DDS:Crypto:AES-GCM-GMAC CryptoTransform interface has several operations that
transform plain text into cipher text. The cipher-text created by these “encode” operations
contains a SecureDataHeader that is interpreted by the corresponding “decode” operations on the
receiving side. The SecureDataHeader structure is described by the Extended IDL below:
@Extensibility(FINAL_EXTENSIBILITY)
struct SecureDataHeader {
CryptoTransformIdentifier transform_identifier;
octet session_id[4];
octet initialization_vector_suffix[8];
};
As indicated by the IDL above, the plugin_sec_header attribute introduced in section 7.3.6.3 consists
of the session_id and the initialization_vector_suffix.
The transformation_indentifier combined with the identity of the sending DomainParticipant
uniquely identifies the KeyMaterial used to transform the plaintext into the cipher text.
The session_id combined with the KeyMaterial uniquely identifies the cryptographic keys used for
the encryption and MAC operations.
The initialization_vector_suffix combined with the session_id uniquely identifies the
Initialization Vector used as part of the AES-GCM and AES-GMAC transformations.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-234-320.jpg)
![DDS Security, v1.0 221
9.5.2.4 DDS:Crypto:AES-GCM-GMAC SecureDataBody
The DDS:Crypto:AES-GCM-GMAC CryptoTransform interface has operations that transform
plaintext into cipher text. The cipher-text created by some of these “encode” operations contains a
SecureDataBody submessage element (see 7.3.6.1) that is interpreted by the corresponding
“decode” operations on the receiving side.
The SecureDataBody structure is described by the Extended IDL below:
@Extensibility(FINAL_EXTENSIBILITY)
struct SecureDataBody {
sequence<octet> secure_data;
};
The SecureDataBody structure shall be serialized using Big Endian serialization (a.k.a. network
byte order).
9.5.2.5 DDS:Crypto:AES-GCM-GMAC SecureDataTag
The DDS:Crypto:AES-GCM-GMAC CryptoTransform interface has several operations that
transform plaintext into cipher text. The cipher-text created by these “encode” operations contains a
SecureDataTag that is interpreted by the corresponding “decode” operations on the receiving side.
The SecureDataTag structure is described by the Extended IDL below:
@Extensibility(FINAL_EXTENSIBILITY)
struct ReceiverSpecificMAC {
CryptoTransformKeyId receiver_mac_key_id;
octet receiver_mac[16];
};
@Extensibility(FINAL_EXTENSIBILITY)
struct SecureDataTag {
octet common_mac[16];
sequence<ReceiverSpecificMAC> receiver_specific_macs;
};
As indicated by the IDL above, the plugin_sec_tag attribute introduced in section 7.3.6.4 consists of
the common_mac and the receiver_specific_macs.
The receiver-specific Message Authentication Codes (MACs) are computed with a secret key that the
sender shares only with one receiver. The receiver-specific MACs provide message origin
authentication to the receiver even when the sender is communicating with multiple receivers via
multicast and shares the same encryption key will all of them.
9.5.3 DDS:Crypto:AES-GCM-GMAC plugin behavior
This plugin implements three interfaces: CryptoKeyFactory, CryptoKeyExchange, and
CryptoTransform. Each is described separately.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-235-320.jpg)
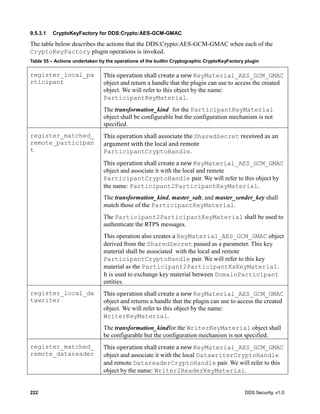
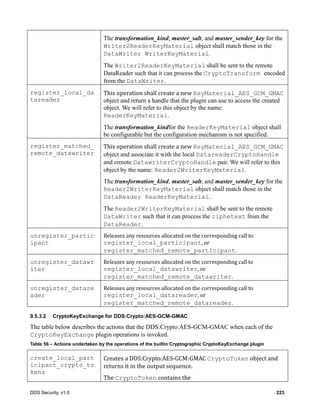
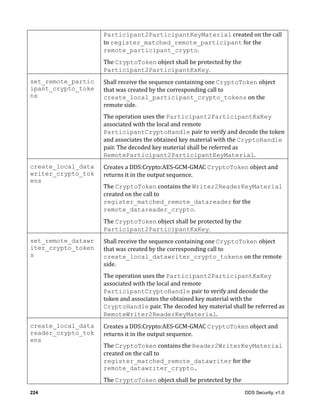
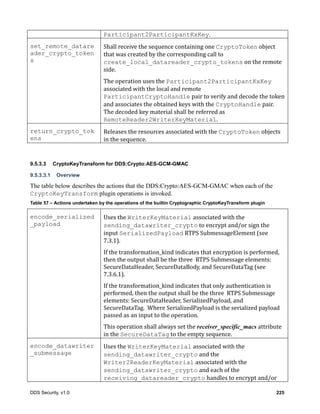
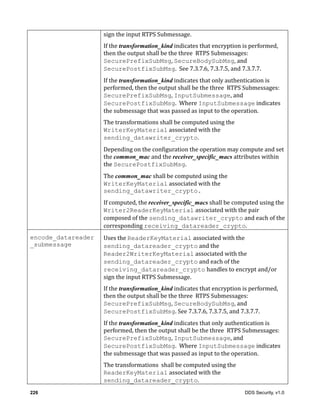

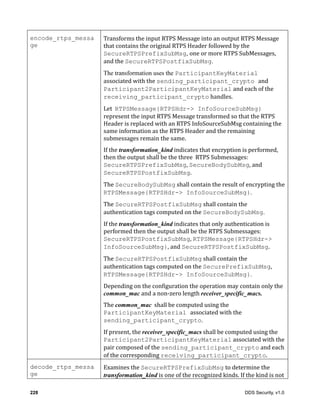

![232 DDS Security, v1.0
use the RemoteDatawriterKeyMaterial to decode the data in
the SecureDataBody, obtain a SerializedPayload and
return it. Otherwise the RTPS Submessage Element that follows the
SecureDataHeader is returned as SerializedPayload.
Upon success the returned RTPS SerializedPayload shall
match the input to the encode_serialized_data operation on
the DomainParticipant that sent the message.
9.5.3.3.2 Encode/decode operation virtual machine
The logical operation of the DDS:Crypto:AES-GCM-GMAC is described in terms of a virtual machine
as it performs the encrypt message digest operations. This is not intended to mandate implementations
should follow this approach literally, simply that the observable results for any plaintext are the same
as the virtual machine described here.
For any given cryptographic session the operation of the DDS:Crypto:AES-GCM-GMAC transforms
plaintext into ciphertext can be described in terms of a virtual machine that maintains the following
state:
Table 58 – Terms used in Key Computation and cryptographic transformations formulas for the builtin
cryptographic plugin
State variable Type Meaning
MasterKey 128 bit array for AES128
256 bit array for AES256
The master key from which session
salts, session keys and session hash
keys are derived.
MasterSalt 128 bit array for AES128
256 bit array for AES256
A random vector used in connection
with the MasterKey to create the
SessionKey.
MasterKeyId octet[4] A NONCE value associated with the
master key when it is first created used
to tag the ciphertext to ensure the
correct key is being used during
decryption. It may be used also for the
purposes of re-keying.
MasterReaderSpecificKey 128 bit array for AES128
256 bit array for AES256
The master key from which
SessionReceiverSpecificKey keys are
derived.
InitializationVectorSuffix octet[8] An initially random NONCE used to
create the Initialization Vector needed
by the cryptographic operations. This
value shall be changed each time an
encryption or MAC operation is
performed using the same key.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-246-320.jpg)
![DDS Security, v1.0 233
SessionId octet[4] An initially random value used to create
the current SessionKey, and
SessionReceiverSpecificKey from the
MasterKey, MasterReceiverSpecificKey,
and Master salts.
The SessionId is incremented each time
a new SessionKey is needed and then
used to derive the new SessionKey and
SessionReceiverSpecificKey from the
MasterKey and
MasterReceiverSpecificKey.
Knowledge of the MasterKey,
MasterSalt, and the SessionId is
sufficient to create the SessionKey.
Knowledge of the
MasterReceiverSpecificKey, MasterSalt,
and the SessionId is sufficient to create
the SessionReceiverSpecificKey.
SessionKey 128 bit array for AES128
256 bit array for AES256
The current key used for creating the
ciphertext and/or the common_mac.
It is constructed from the MasterKey,
MasterSalt, and SessionId.
SessionReceiverSpecificKey 128 bit array for AES128
256 bit array for AES256
The current key used for creating the
receiver_specific_mac.
session_block_counter 64 bit integer A counter that counts the number of
blocks that have been ciphered with the
current SessionKey.
max_blocks_per_session 64 bit integer A configurable property that limits the
number of blocks that can be ciphered
with the same SessionKey. If the
session_block_counter exceeds this
value a new SessionKey, SessionSalt,
and SessionHMACKey are computed
and the session_block_counter is reset
to zero.
All the key material with a name that starts with “Master” corresponds to the
KeyMaterial_AES_GCM_GMAC objects that were created by the CryptoKeyFactory
operations. This key material is not used directly to encrypt or compute MAC of the plaintext. Rather it
is used to create “Session” Key material by means of the algorithms described below. This has the
benefit that the ‘session’ keys used to secure the data stream data can be modified as needed to
maintain the security of the stream without having to perform explicit rekey and key-exchange
operations.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-247-320.jpg)

![DDS Security, v1.0 235
9.5.3.3.4.1 Format of the SecureDataHeader Submessage Element
The SecureDataHeader submessage element generated by the DDS:Crypto:AES-GCM-GMAC
shall take the form:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
+ SecureDataHeader: +
+ CryptoTransformIdentifier transformation_id +
| octet[4] transformation_id.transformation_kind |
| octet[4] transformation_id.transformation_key_id |
+ - - - - - - - - - - - - - - - - - - - - - - - - - - - +
+ plugin_sec_prefix: +
| octet[4] plugin_sec_prefix.session_id |
~ octet[8] plugin_sec_prefix.init_vector_suffix ~
+---------------+---------------+---------------+---------------+
9.5.3.3.4.2 Format of the SecureDataBody Submessage Element
The SecureDataBody submessage element generated by the DDS:Crypto:AES-GCM-GMAC shall
take the form:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
+ SecureDataBody: +
| long secure_data.length = N |
+ - - - - - - - - - - - - - - - - - - - - - - - - - - - - +
| sec_data[0] | sec_data[1] | sec_data[2] | sec_data[3] |
~ . . . ~
| sec_data[N-4] | sec_data[N-3] | sec_data[N-2] | sec_data[N-1] |
+---------------+---------------+---------------+---------------+
Note that the built cipher operations have 16-byte block-size and add padding when needed. Therefore
the secure data.length (“N”) will always be a multiple of 16.
Note that as specified in subclause 9.5.2.4 the secure data.length shall be serialized using Big Endian
representation.
9.5.3.3.4.3 Format of the SecureDataTag Submessage Element
The SecureDataTag submessage element generated by the DDS:Crypto:AES-GCM-GMAC shall
take the form:](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-249-320.jpg)
![236 DDS Security, v1.0
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
+ SecureDataTag ( = plugin_sec_tag): +
~ octet[16] plugin_sec_tag.common_mac ~
+ - - - - - - - - - - - - - - - - - - - - - - - - - - - +
+ plugin_sec_tag.receiver_specific_macs: +
| long plugin_sec_tag.receiver_specific_macs.length = N |
| - - - - - - - - - - - - - - - - - - - - - - - - - - - - |
| octet[4] receiver_specific_macs[0].receiver_mac_key_id |
~ octet[16] receiver_specific_macs[0].receiver_mac ~
+ - - - - - - - - - - - - - - - - - - - - - - - - - - +
+ . . . +
+ - - - - - - - - - - - - - - - - - - - - - - - - - - +
| octet[4] receiver_specific_macs[N-1].receiver_mac_key_id|
~ octet[16] receiver_specific_macs[N-1].receiver_mac ~
+---------------+---------------+---------------+---------------+
9.5.3.3.4.4 Result from encode_serialized_payload
The input to this operation is a SerializedPayload submessage element:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
~ SerializedPayload ~
+---------------+---------------+---------------+---------------+
The output in case the transformation performs authentication only shall be:
0...2...........8...............16.............24...............32
+---------------+---------------+---------------+---------------+
~ SecureDataHeader ~
+---------------+---------------+---------------+---------------+
~ SerializedPayload (unchanged from input) ~
+---------------+---------------+---------------+---------------+
~ SecureDataTag ~
+---------------+---------------+---------------+---------------+](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-250-320.jpg)







![DDS Security, v1.0 245
10 Plugin Language Bindings
10.1 Introduction
Clause 8 defines the plugin interfaces in a programming-language independent manner using UML.
Using the terminology of the DDS specification this UML definition could be considered a Platform
Independent Model (PIM) for the plugin interfaces. The mapping to each specific programming
languages platform could therefore be considered a Platform Specific Model (PSM) for that
programming language.
The mapping of the plugin interfaces to specific programming languages is defined by first defining
the interfaces using OMG-IDL version 3.5 with the additional syntax defined in the DDS-XTYPES
specification and subsequently applying the IDL to language mapping to the target language.
IDL Types lacking the DDS-XTYPES @Extensibility annotation shall be interpreted as having
the extensibility kind EXTENSIBLE_EXTENSIBILITY. This matches the DDS-XTYPES
specification implied extensibility of un-annotated types.
For consistency with the DDS specification, the DDS security specification defines language bindings
to each of the language PSMs specified for DDS, namely:
C as derived from the IDL to C mapping
C++ classic, as derived from the IDL to C++ mapping
Java classic, as derived from the IDL to Java mapping
C++ modern, aligned with the DDS-STDC++ specification, this is derived from the IDL to C++11
mapping
Java modern with the DDS-JAVA5+ specification
10.2 IDL representation of the plugin interfaces
For consistency in the resulting APIs, the mapping from the plugin interfaces defined in clause 8 and
the OMG IDL follows the same PIM to PSM mapping rules as the OMG DDS specification (see sub
clause 7.2.2 of the DDS specification version 1.2 [1]). A relevant subset of these rules is repeated here.
In these rules “PIM” refers to the UML description of the interfaces in clause 8 and PSM refers to the
OMG-IDL description of the interfaces that appears in the associated dds_security.idl file.
The PIM to PSM mapping maps the UML interfaces and classes into IDL interfaces. Plain data
types are mapped into structures.
‘Out’ parameters in the PIM are conventionally mapped to ‘inout’ parameters in the PSM in order
to minimize the memory allocation performed by the Service and allow for more efficient
implementations. The intended meaning is that the caller of such an operation should provide an
object to serve as a “container” and that the operation will then “fill in” the state of that objects
appropriately.
The resulting IDL representation of the plugin interfaces appears in the file dds_security.idl which
shall be considered part of the DDS Security specification.
10.3 C language representation of the plugin interfaces
The C language representation of the plugin interfaces shall be obtained applying the IDL to C
mapping [5] to the dds_security.idl file.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-259-320.jpg)
![246 DDS Security, v1.0
10.4 C++ classic representation of the plugin interfaces
The C++ classic (without the use of the C++ standard library) language representation of the plugin
interfaces shall be obtained using the IDL2C++ mapping [7] to the dds_security.idl file.
10.5 Java classic
The Java classic language representation of the plugin interfaces shall be obtained using the IDL2Java
mapping [6] to the dds_security.idl file.
10.6 C++11 representation of the plugin interfaces
This representation is aligned with the DDS-STDC++ PSM.
The C++ classic language representation of the plugin interfaces shall be obtained using the
IDL2C++11 mapping [8] to the dds_security.idl file with the following exceptions:
1. The IDL module DDS shall be mapped to the C++ namespace dds so it matches the namespace
used by the DDS-STD-C++ PSM.
2. The mapping shall not use any C++11-only feature of the language or the library (e.g., move
constructors, noexcept, override, std::array).
3. Arrays shall map to the dds::core::array template defined in the DDS-STD-C++ PSM.
4. The enumerations shall map to the dds::core::safe_enum template defined in the DDS-STD-
C++ PSM.
5. The IDL DynamicData native type shall be mapped to the C++ type
dds::code::xtypes::DynamicData defined in the DDS-STDC++ PSM.
10.7 Java modern aligned with the DDS-JAVA5+ PSM
The Java classic language representation of the plugin interfaces shall be obtained using the IDL2Java
mapping [6] to the dds_security.idl file with the following exceptions:
1. The IDL module DDS shall be mapped to the Java namespace org.omg.dds so it matches the
namespace used by the DDS-JAVA5+ PSM.
2. The IDL DynamicData native type shall be mapped to the type
org.omg.dds.type.dynamic.DynamicData defined in the DDS-JAVA5+ PSM.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-260-320.jpg)
![DDS Security, v1.0 247
Annex A - References
[1] DDS: Data-Distribution Service for Real-Time Systems version 1,2.
http://www.omg.org/spec/DDS/1.2/
[2] DDS-RTPS: Data-Distribution Service Interoperability Wire Protocol version 2.1,
http://www.omg.org/spec/DDS-RTPS/2.1/
[3] DDS-XTYPES: Extensible and Dynamic Topic-Types for DDS version 1.0
http://www.omg.org/spec/DDS-XTypes/
[4] OMG-IDL: Interface Definition Language (IDL) version 3.5 http://www.omg.org/spec/IDL35/
[5] IDL2C: IDL to C Language Mapping, Version 1.0. http://www.omg.org/spec/C/1.0/
[6] IDL2Java: IDL To Java Language Mapping, Version 1.3 http://www.omg.org/spec/I2JAV/1.3/
[7] IDL2C++: IDL to C++ Language Mapping (CPP), Version 1.3
http://www.omg.org/spec/CPP/1.3/PDF
[8] IDL2C++11: IDL To C++11 Language Mapping http://www.omg.org/spec/CPP11/
[9] Transport Layer Security, http://en.wikipedia.org/wiki/Transport_Layer_Security
[10] IPSec, http://en.wikipedia.org/wiki/IPsec
[11] DSA, FIPS PUB 186-4 Digital Signature Standard (DSS).
http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-4.pdf
[12] Diffie-Hellman (D-H) Key Agreement Method. IETF RFC 2631.
http://tools.ietf.org/html/rfc2631
[13] J. H. Catch et. al., “A Security Analysis of the CLIQUES Protocol Suite”,
http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.2.8964
[14] Erramilli, S.; Gadgil, S.; Natarajan, N., “Efficient assignment of multicast groups to publish-
subscribe information topics in tactical networks”, MILCOM 2008
[15] “RFC 2094 - Group Key Management Protocol (GKMP) Architecture”,
http://www.faqs.org/rfcs/rfc2094.html
[16] Raghav Bhaskar, Daniel Augot, Cedric Adjih, Paul Muhlethaler and Saadi Boudjit, “AGDH
(Asymmetric Group Diffie Hellman): An Efficient and Dynamic Group Key Agreement
Protocol for Ad hoc Networks”, Proceedings of New Technologies, Mobility and Security
(NTMS) conference, Paris, France, May 2007
[17] Qianhong Wu, Yi Mu, Willy Susilo, Bo Qin and Josep Domingo-Ferrer “Asymmetric Group
Key Agreement”, EUROCRYPT 2009
[18] “Secure IP Multicast”,
http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6552/prod_presentation0900ae
cd80473105.pdf
[19] Gerardo Pardo-Castellote. “Secure DDS: A Security Model suitable for NetCentric, Publish-
Subscribe, and Data Distribution Systems”, RTESS, Washington DC, July 2007.
http://www.omg.org/news/meetings/workshops/RT-2007/05-2_Pardo-Castellote-revised.pdf
[20] M. Baugher, D. McGrew, M. Naslund, E. Carrara, K. Norrman, “The Secure Real-time
Transport Protocol (SRTP)” IETF RFC 3711, http://tools.ietf.org/html/rfc3711
[21] Baugher, M., Weis, B., Hardjono, T. and H. Harney, "The Group Domain of Interpretation,”
IETF RFC 3547, http://tools.ietf.org/html/rfc3547, July 2003.
[22] P. Zimmerman, A. Johnston, and J. Callas, “ZRTP: Media Path Key Agreement for Secure
RTP”, Internet-Draft, March 2009
[23] F. Andreason, M. Baugher, and D. Wing, “Session description protocol (SDP) security
description for media streams,” IETF RFC 4568, July 2006
[24] D. Ignjatic, L. Dondeti, F. Audet, P. Lin, “MIKEY-RSA-R: An Additional Mode of Key
Distribution in Multimedia Internet KEYing (MIKEY)”, RFC 4738, November 2006.](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-261-320.jpg)
![248 DDS Security, v1.0
[25] M. Baugher, A. Rueegsegger, and S. Rowles, “GDOI Key Establishment for the STRP Data
Security Protocol”, http://tools.ietf.org/id/draft-ietf-msec-gdoi-srtp-01.txt, June 2008.
[26] Bruce Schneier (August 2005). "SHA-1 Broken". Retrieved 2009-01-09. "
[27] H. Krawczyk, M. Bellare, and R.Canetti, “HMAC: Keyed-Hashing for Message
Authentication” IETF RFC 2104, http://tools.ietf.org/html/rfc2104
[28] Bellare, Mihir (June 2006). "New Proofs for NMAC and HMAC: Security without Collision-
Resistance". In Dwork, Cynthia. Advances in Cryptology – Crypto 2006 Proceedings. Lecture
Notes in Computer Science 4117. Springer-Verlag.
[29] S. Turner and L. Chen, “Updated Security Considerations for the MD5 Message-Digest and the
HMAC-MD5 Algorithms” IETF RFC 6151, http://tools.ietf.org/html/rfc6151
[30] Cisco, “Implementing Group Domain of Interpretation in a Dynamic Multipoint VPN”,
http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6586/ps6660/ps6811/prod_whit
e_paper0900aecd804c363f.html
[31] CiscoIOS Secure Multicast,
http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6552/prod_white_paper0900ae
cd8047191e.html
[32] A. Mason. IPSec Overview Part Two: Modes and Transforms.
http://www.ciscopress.com/articles/article.asp?p=25477
[33] R. Canetti, P. Cheng, F. Giraud, D. Pendararkis, J. Rao, P. Rohatgi, and D. Saha, “An IPSec-
based Host Architecture for Secure Internet Multicast”, Proceedings of the 7th
Annual Network
and Distributed Systems Security Symposium, San Diego, CA, 2000
[34] T. Aurisch, and C. Karg, “Using the IPSec architecture for secure multicast communications,”
8th
International Command and Control Research and Technology Symposium (ICCRTS),
Washington D.C., 2003
[35] J. Zhang and C. Gunter. Application-aware secure multicast for power grid communications,
International Journal of Security and Networks, Vol 6, No 1, 2011
[36] List of reserved RTPS Vendor Ids. http://portals.omg.org/dds/content/page/dds-rtps-vendor-
and-product-ids
[37] PKCS #7: Cryptographic Message Syntax Version 1.5. IETF RFC 2315.
http://tools.ietf.org/html/rfc2315
[38] File expression matching syntax for fnmatch() ; POSIX fnmatch API (IEEE 1003.2-1992
Section B.6)
[39] X.509 v3. ITU-T Recommendation X.509 (2005) | ISO/IEC 9594-8:2005, Information
technology - Open Systems Interconnection - The Directory: Public-key and attribute
certificate frameworks. http://www.itu.int/itu-t/recommendations/rec.aspx?rec=X.509
[40] IETF RFC 5280: Internet X.509 Public Key Infrastructure Certificate and Certificate
Revocation List (CRL) Profile, https://tools.ietf.org/html/rfc5280
[41] ANSI X9.62. ANSI, "Public Key Cryptography For The Financial Services Industry: The
Elliptic Curve Digital Signature Algorithm (ECDSA)", ANSI X9.62, 2005
[42] FIPS 186-4: FIBS Digital Signature Standard (DSS).
http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-4.pdf
[43] PKCS#8: Asymmetric Key Packages. IETF RFC 5958. https://tools.ietf.org/html/rfc5958
[44] PKCS#1: Public-Key Cryptography Standards: RSA Cryptography Specifications Version 2.1
https://tools.ietf.org/html/rfc3447
[45] [NIST SP 800-38D] Recommendation for Block Cipher Modes of Operation: Galois/Counter
Mode (GCM) and GMAC http://csrc.nist.gov/publications/nistpubs/800-38D/SP-800-38D.pdf
[46] FIPS 196 Entity Authentication Using Public Key Cryptography
http://csrc.nist.gov/publications/fips/fips196/fips196.pdf](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-262-320.jpg)
![DDS Security, v1.0 249
[47] IETF RFC 5114 “Additional Diffie-Hellman Groups for Use with IETF
Standards” https://tools.ietf.org/html/rfc5114.
[48] [NIST SP 800-56Ar2] NIST Special Publication 800-56A Revision 2. Recommendation for
Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-56Ar2.pdf
[49] NIST Suite B Implementer’s Guide to NIST SP 800-56A
https://www.nsa.gov/ia/_files/SuiteB_Implementer_G-113808.pdf
[50] IETF RFC 5869 HMAC-based Extract-and-Expand Key Derivation Function (HKDF)
https://tools.ietf.org/html/rfc5869
[51] IETF RFC 4514 "Lightweight Directory Access Protocol (LDAP): String Representation of
Distinguished Names" https://tools.ietf.org/html/rfc4514](https://image.slidesharecdn.com/omgddssecurityformalv10-171006013721/85/DDS-Security-Specification-version-1-0-263-320.jpg)