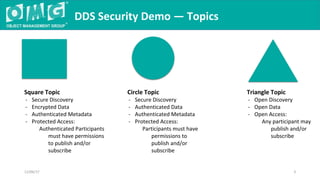
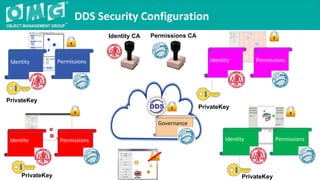
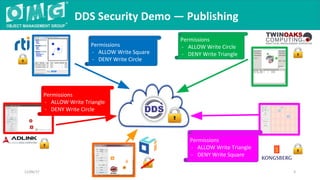
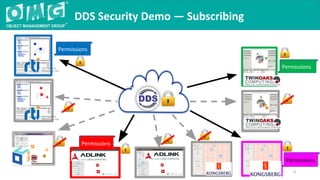
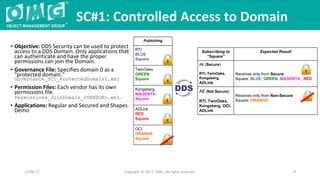
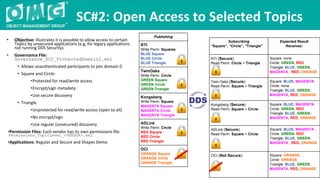
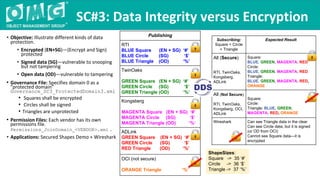
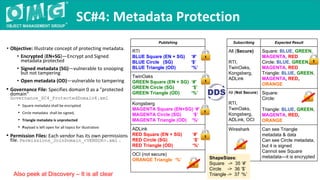
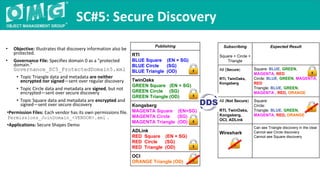
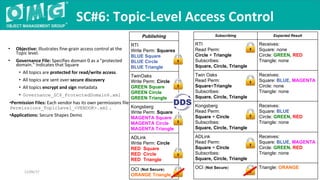
The document outlines a DDS security interoperability demonstration involving various vendor products and fundamental capabilities of DDS security protocols. It details different scenarios such as controlled access to data, metadata protection, and secure discovery, highlighting how permissions and configurations govern data publishing and subscribing. The demo emphasizes the ability of applications to function with and without security while demonstrating granular control over data integrity and access levels.