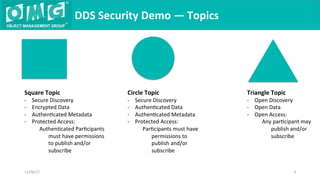
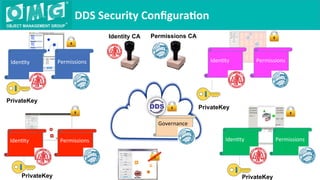
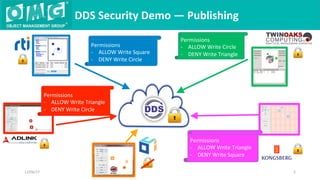
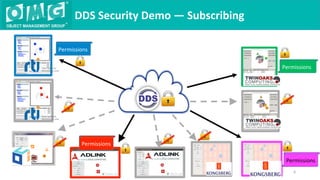
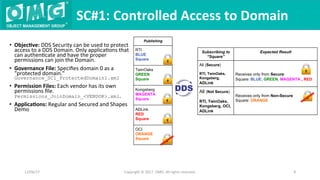
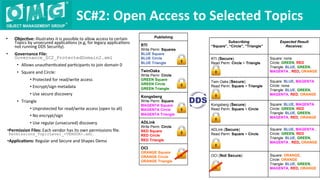
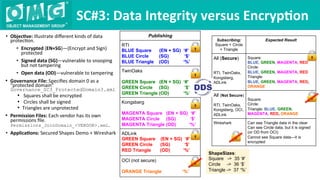
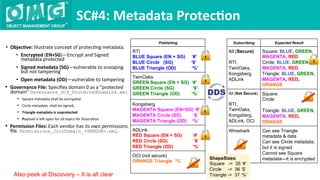
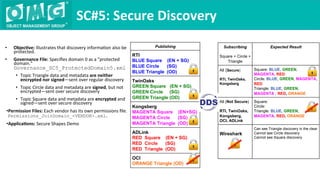
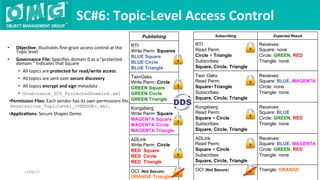
The document describes a demonstration of interoperability between 5 vendor DDS security implementations using a shapes demo application. The demo consists of 6 scenarios that illustrate different aspects of DDS security configuration and functionality, including controlling access to the domain, enabling open access to selected topics, comparing data integrity vs encryption, protecting metadata, securing discovery, and fine-grained access control at the topic level. Each scenario varies the security governance and permission files to achieve the desired access control configuration.