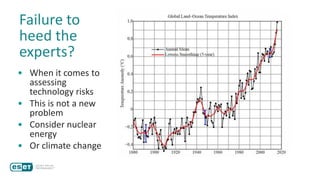
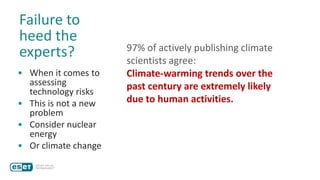
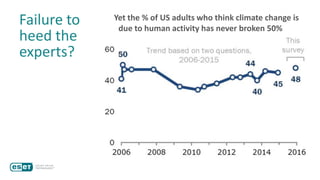
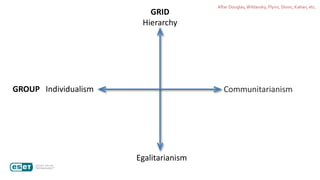
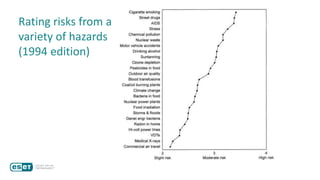
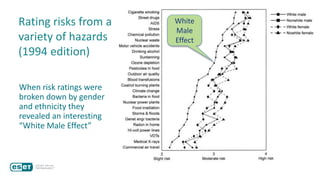
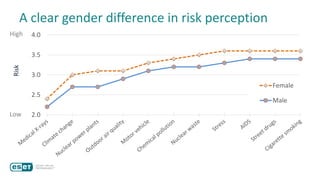
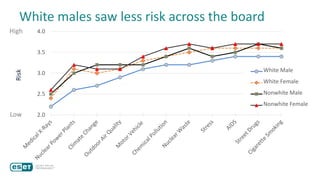
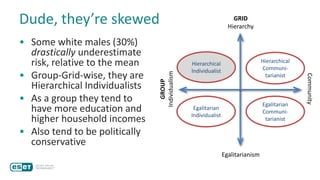
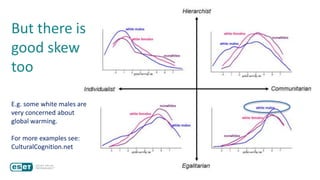
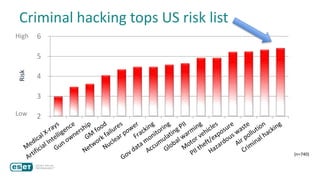
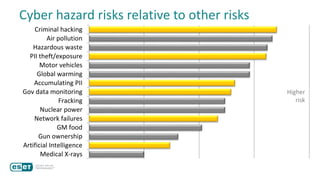
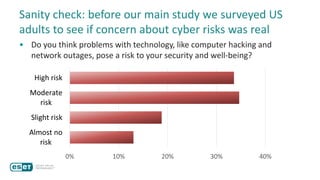
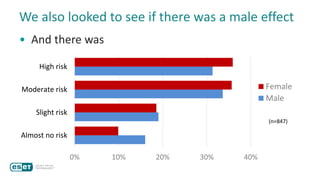
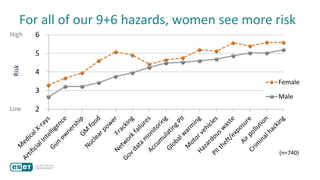
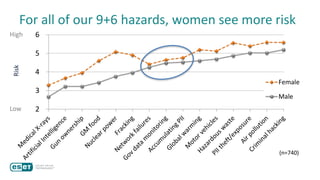
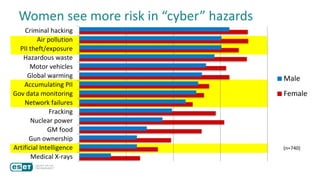
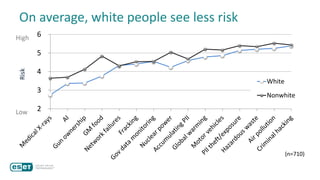
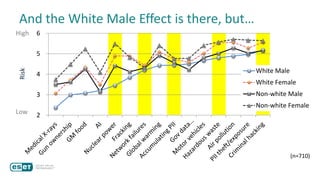
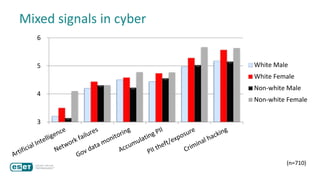
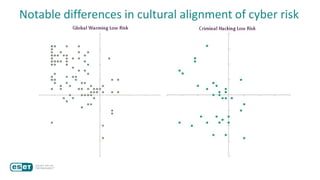
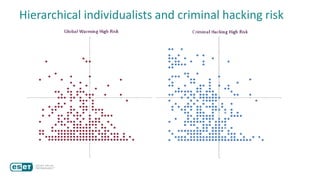
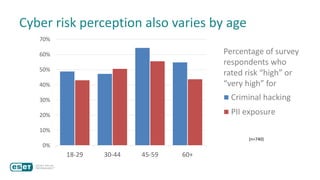
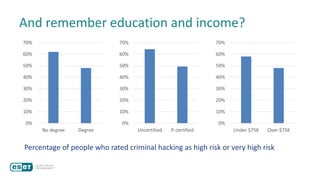
The document discusses how perceptions of cybersecurity risks are influenced by factors such as cultural theory and demographic variables, highlighting the 'white male effect' where white males generally see less risk compared to other groups. It emphasizes the importance of understanding these perceptions to improve risk communication and management in cybersecurity, suggesting that diversity in technology leadership could enhance risk assessment. Finally, the authors advocate for further research into risk perception to enhance communications about cybersecurity risks.