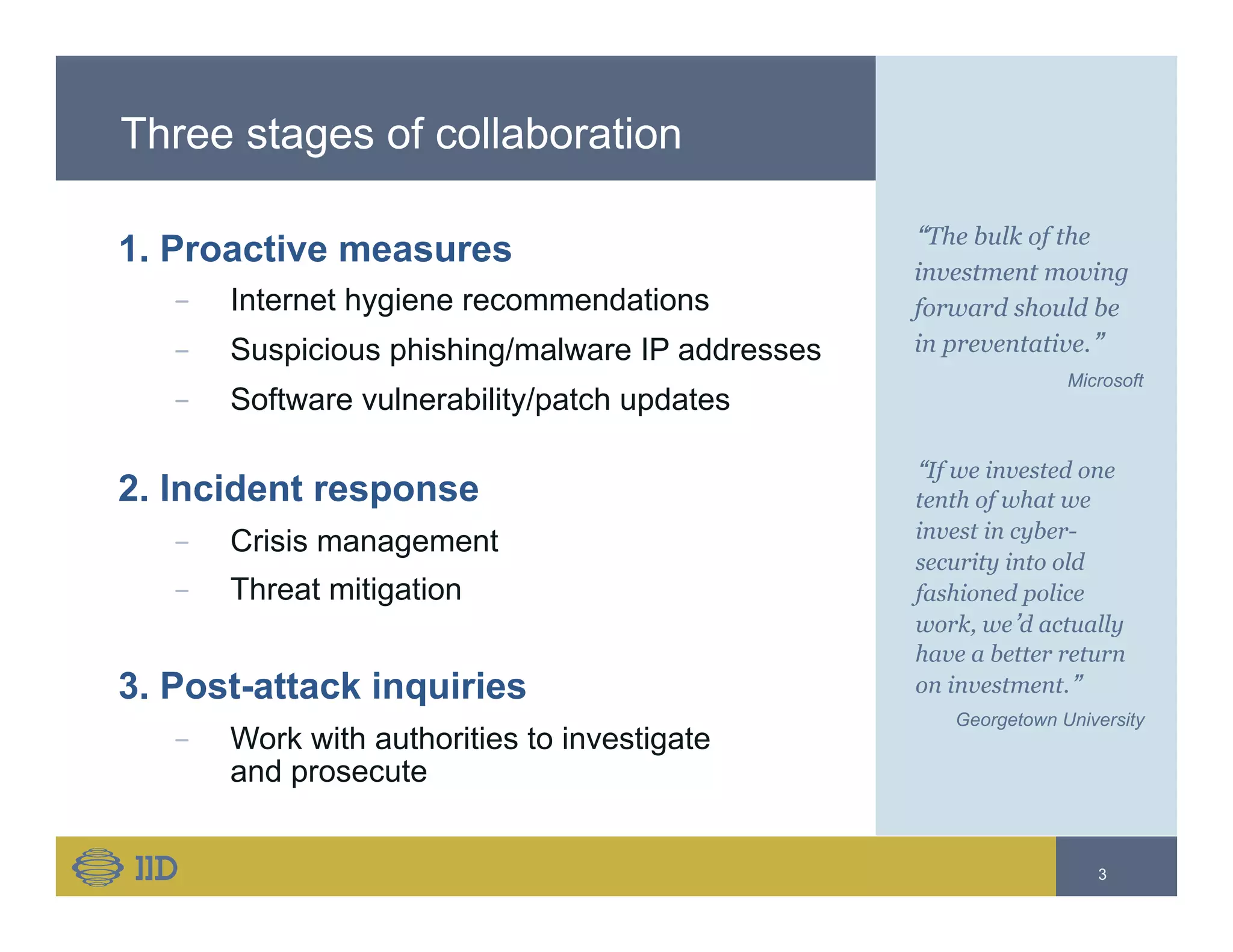
The document discusses the need for collaboration among security experts to combat cybercrime, highlighting the obstacles of trust, liability, and resource limitations. It emphasizes the importance of proactive measures, incident response, and post-attack inquiries while calling for standardized processes and trust-building among collaborators. The conclusion stresses the significance of advancing cybersecurity intelligence sharing to keep pace with evolving threats.