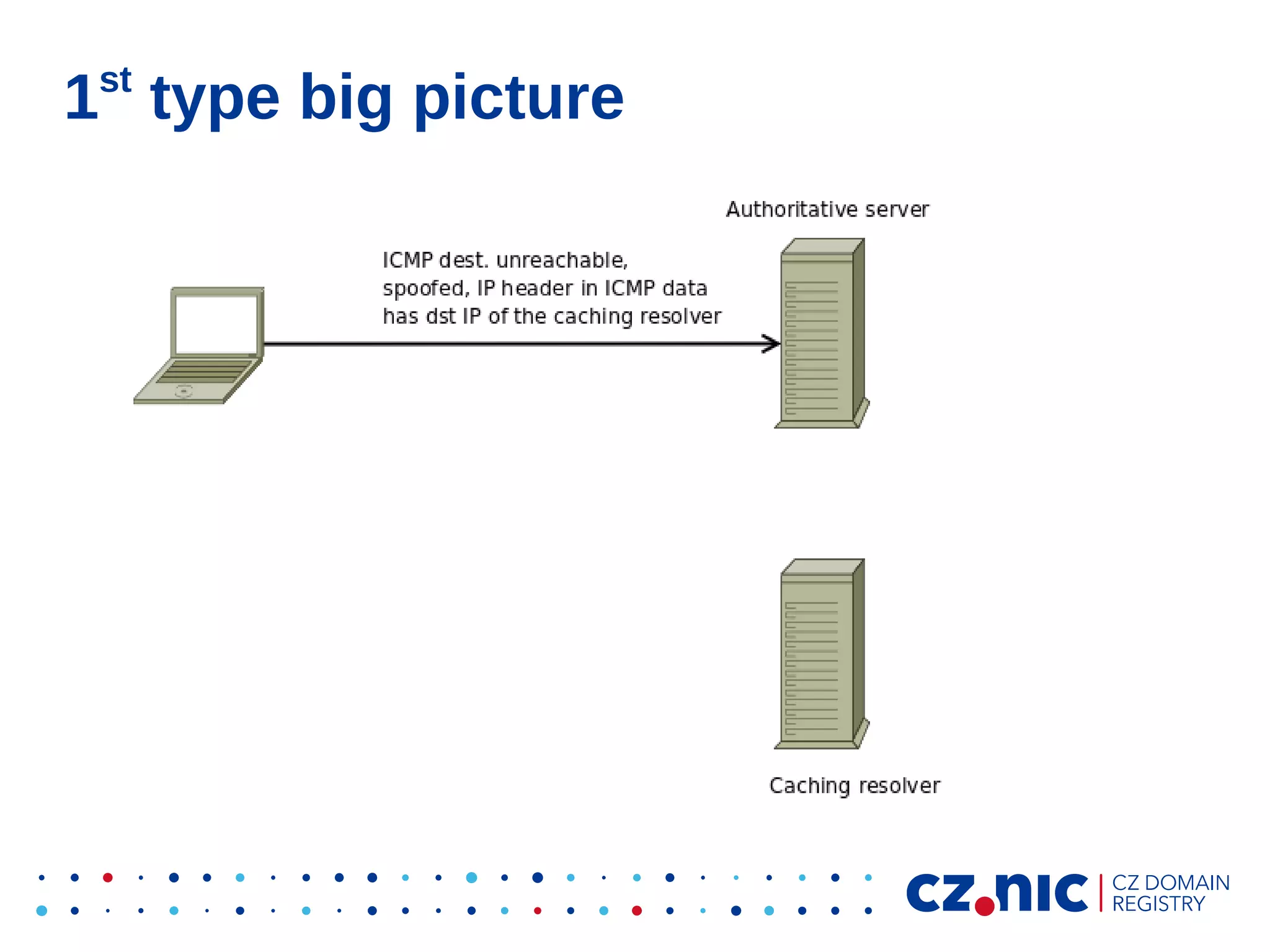
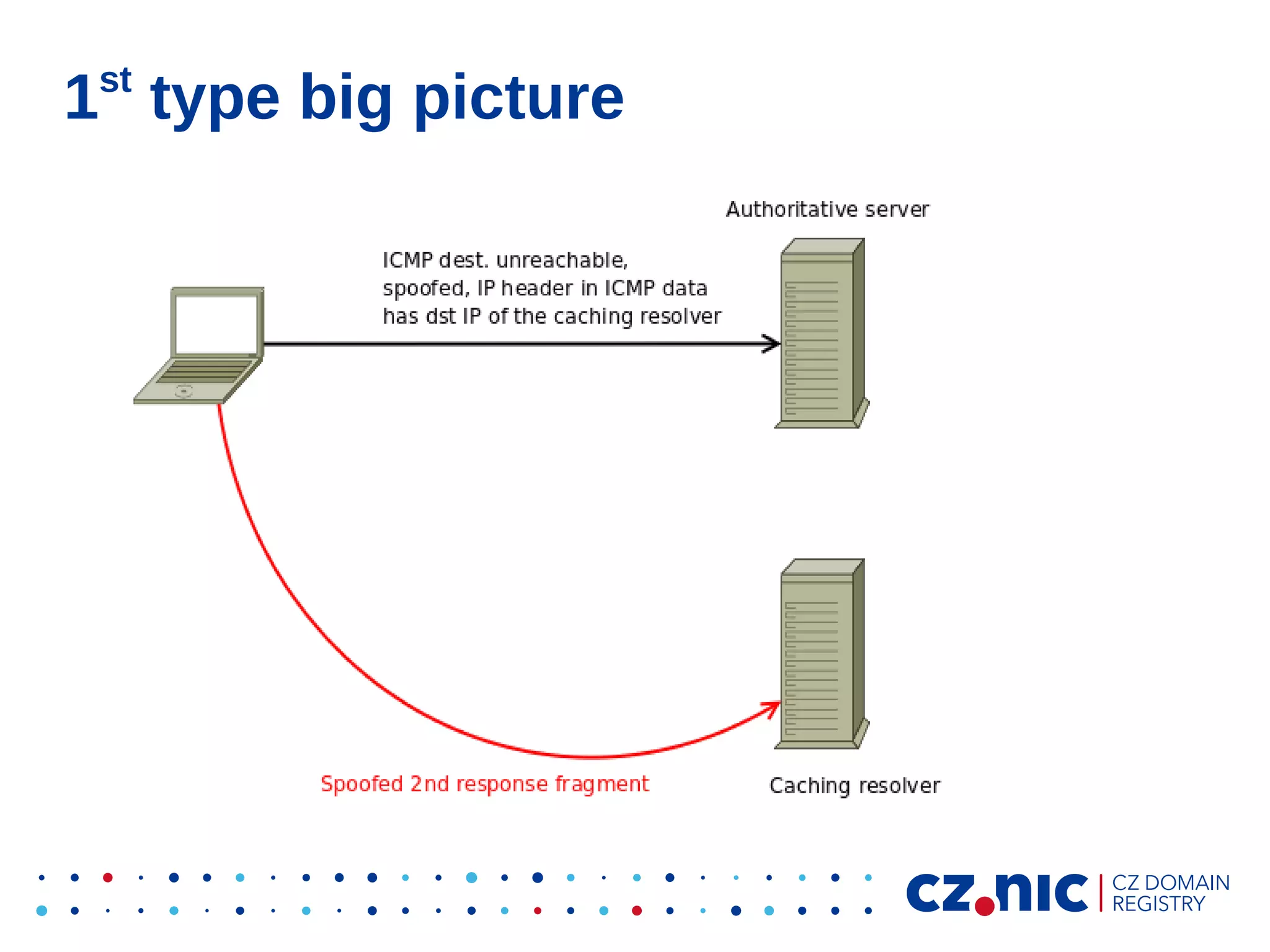
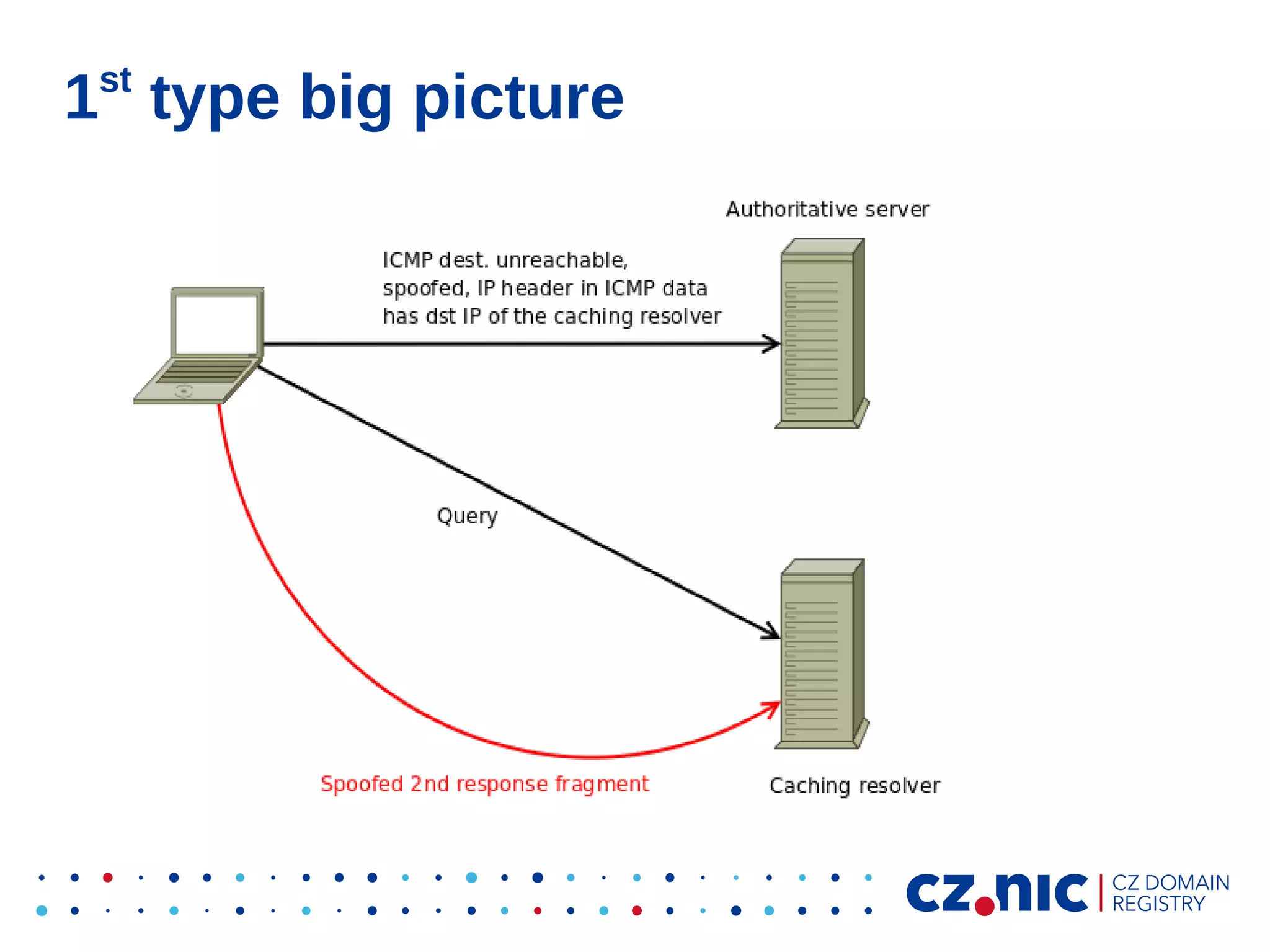
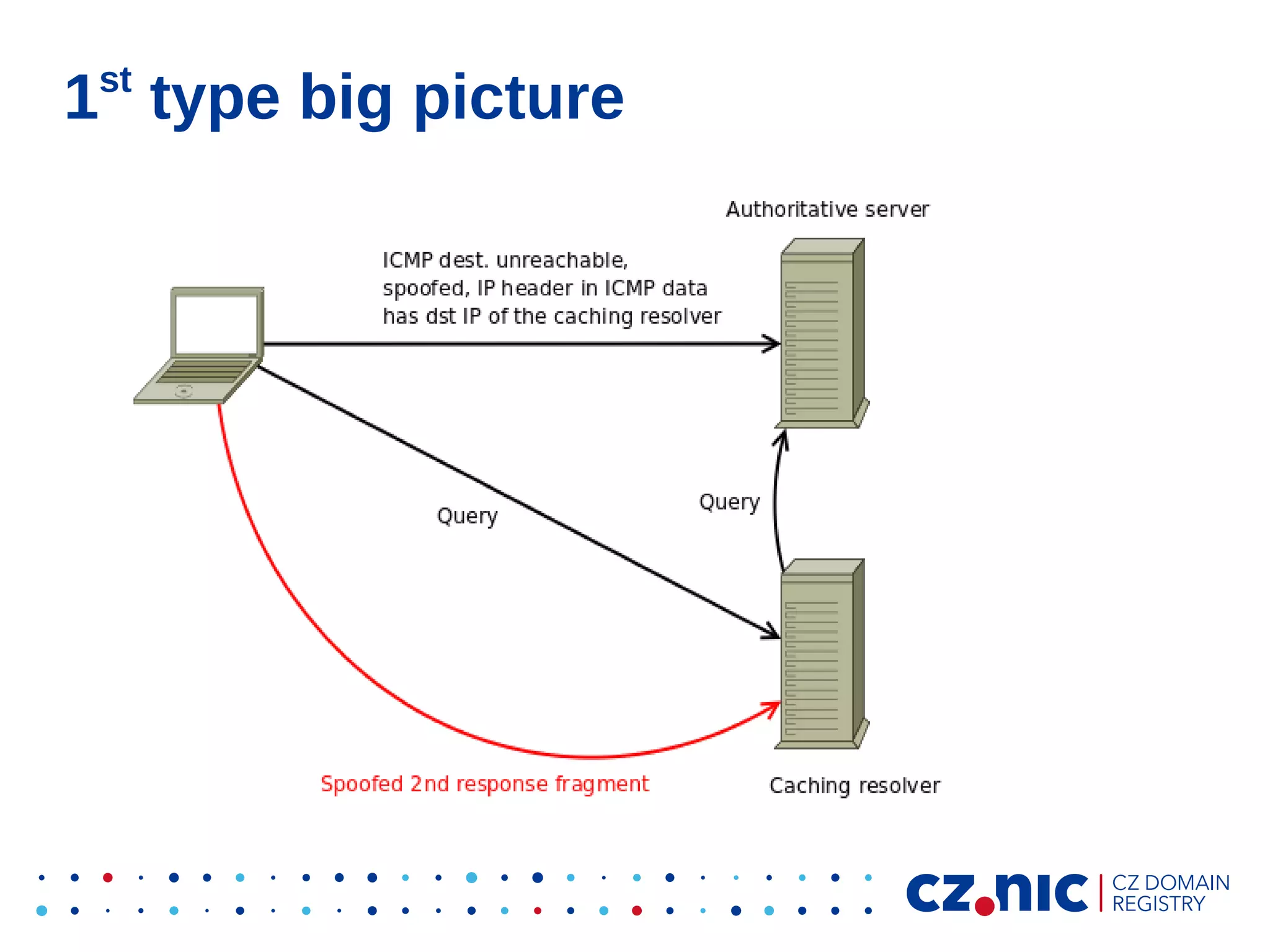
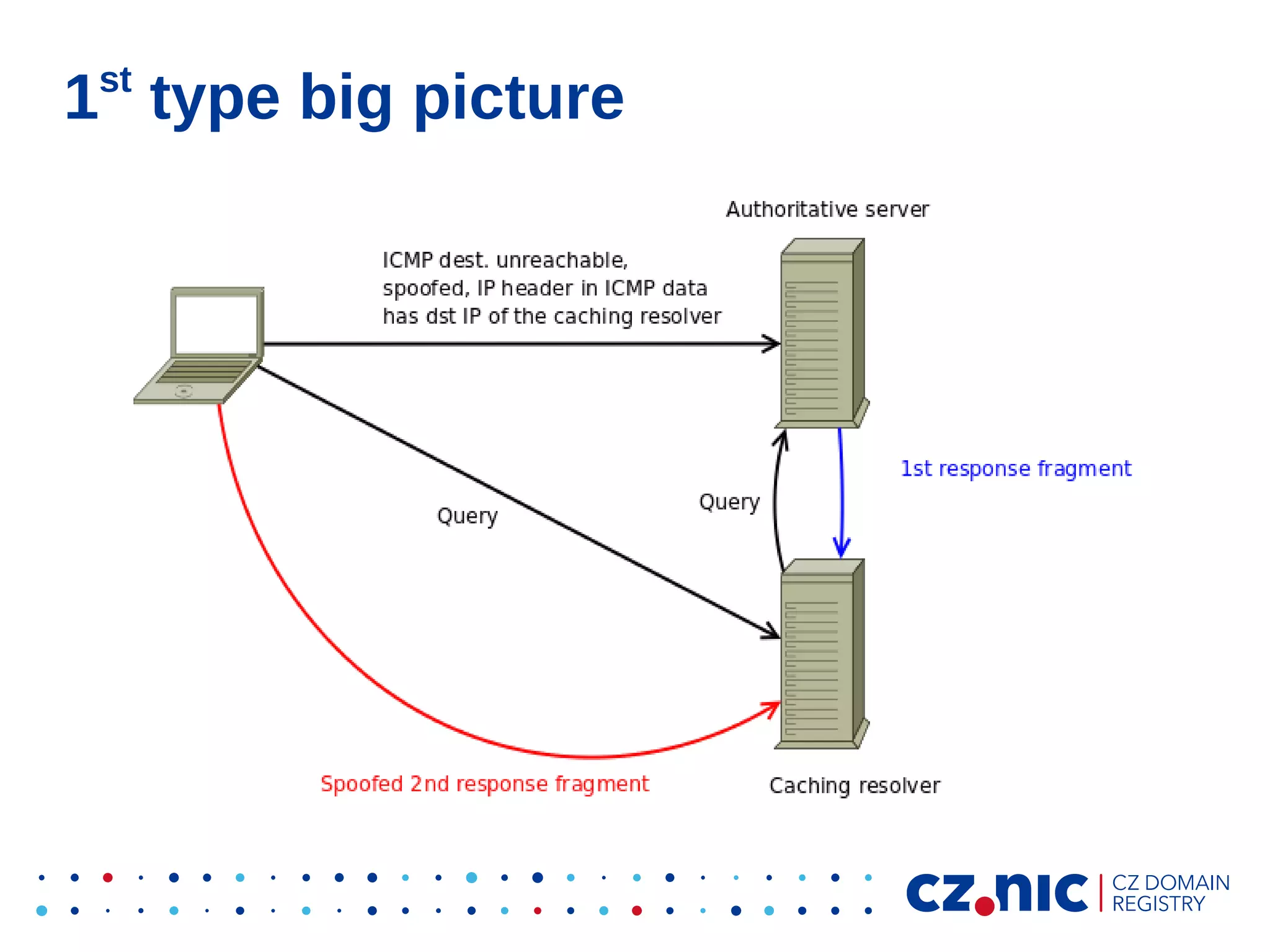
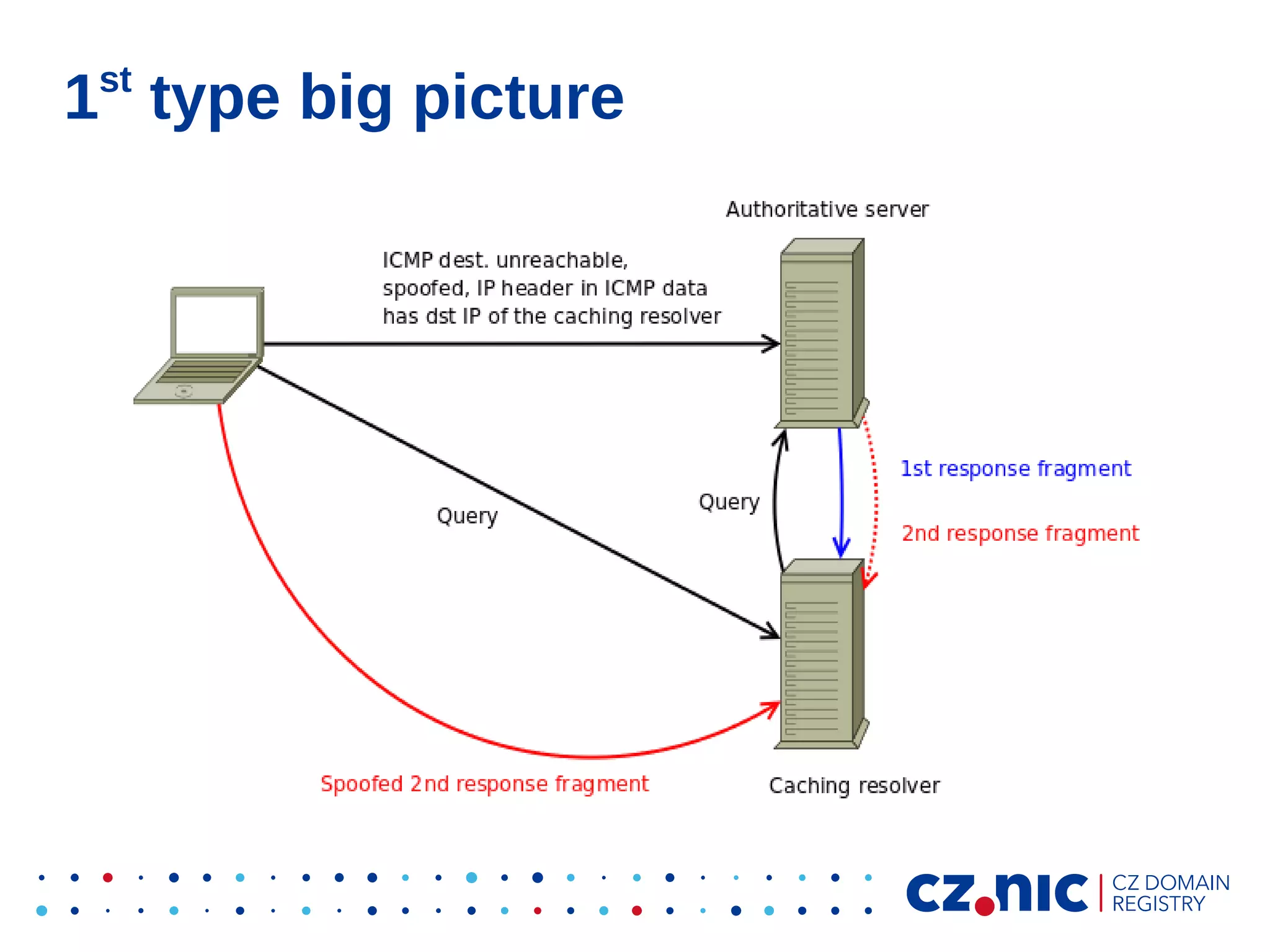
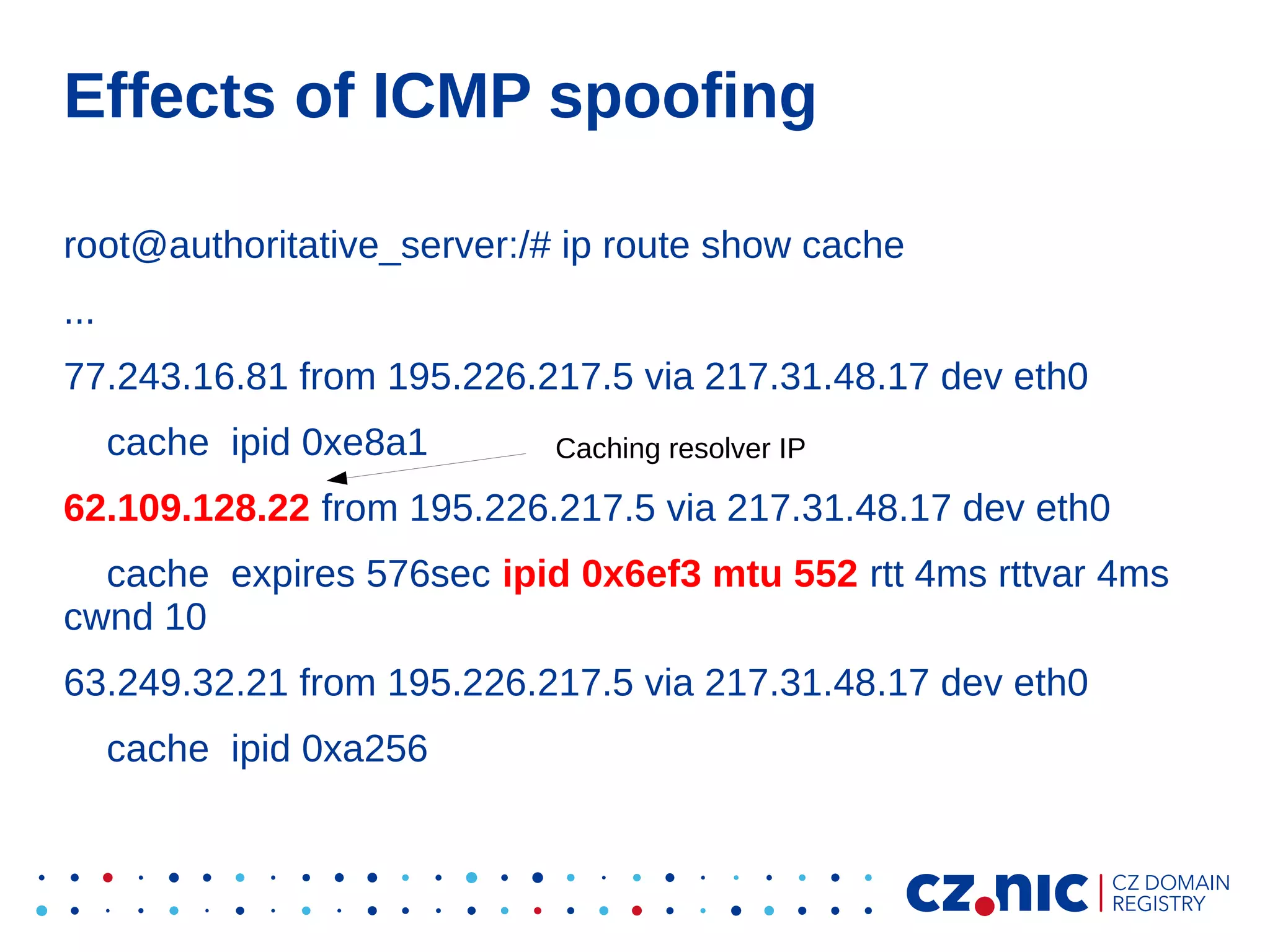
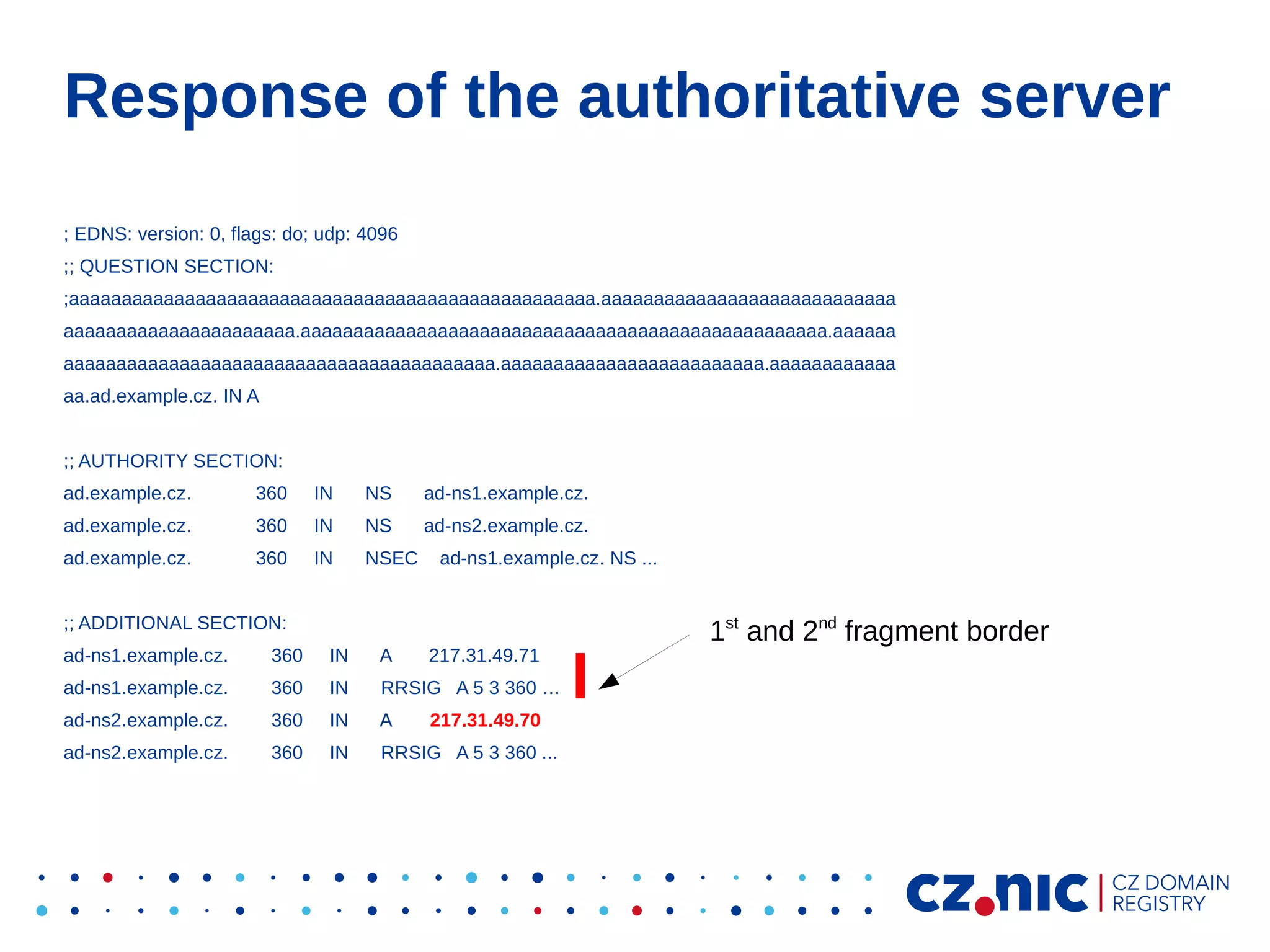
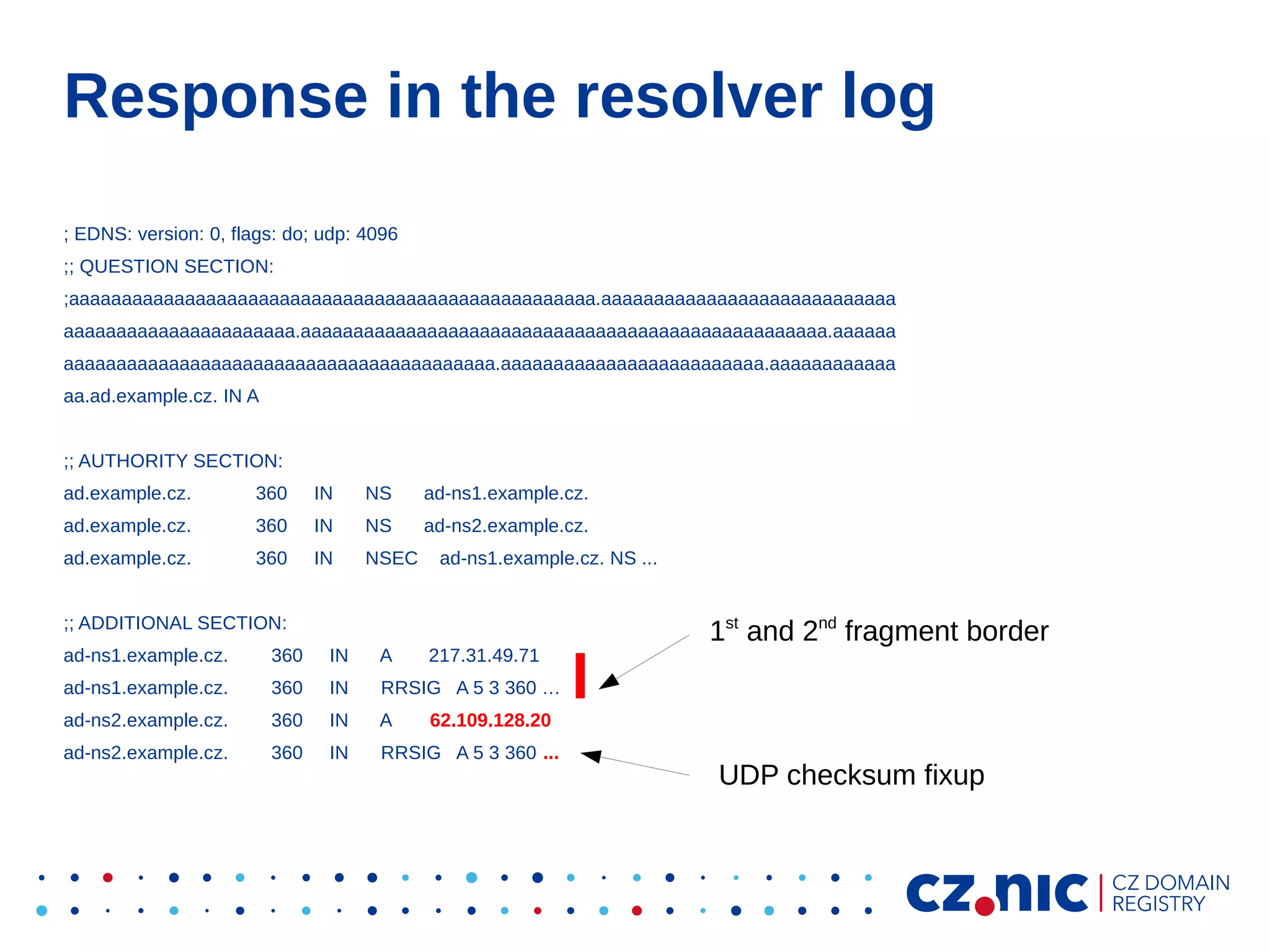
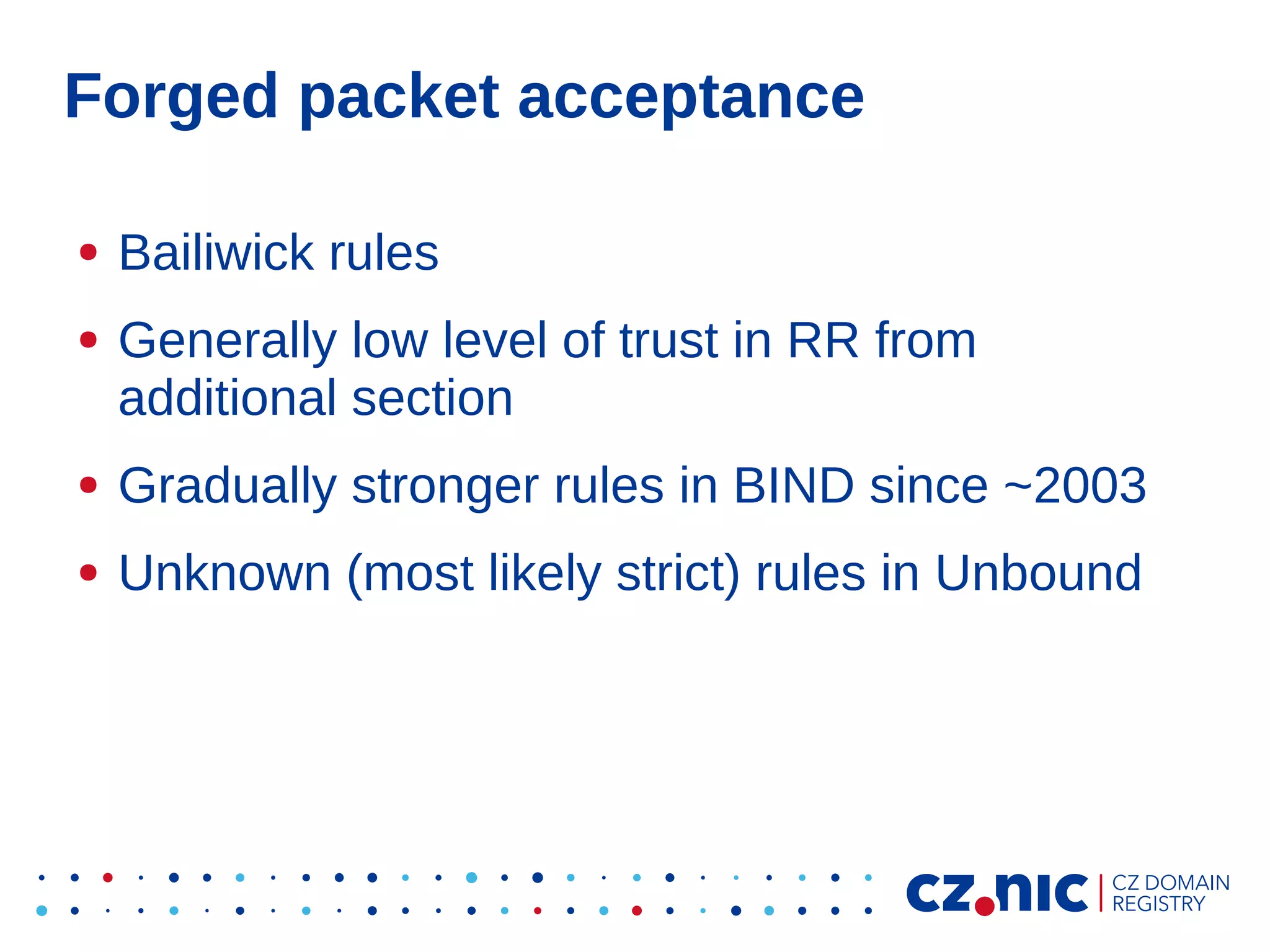
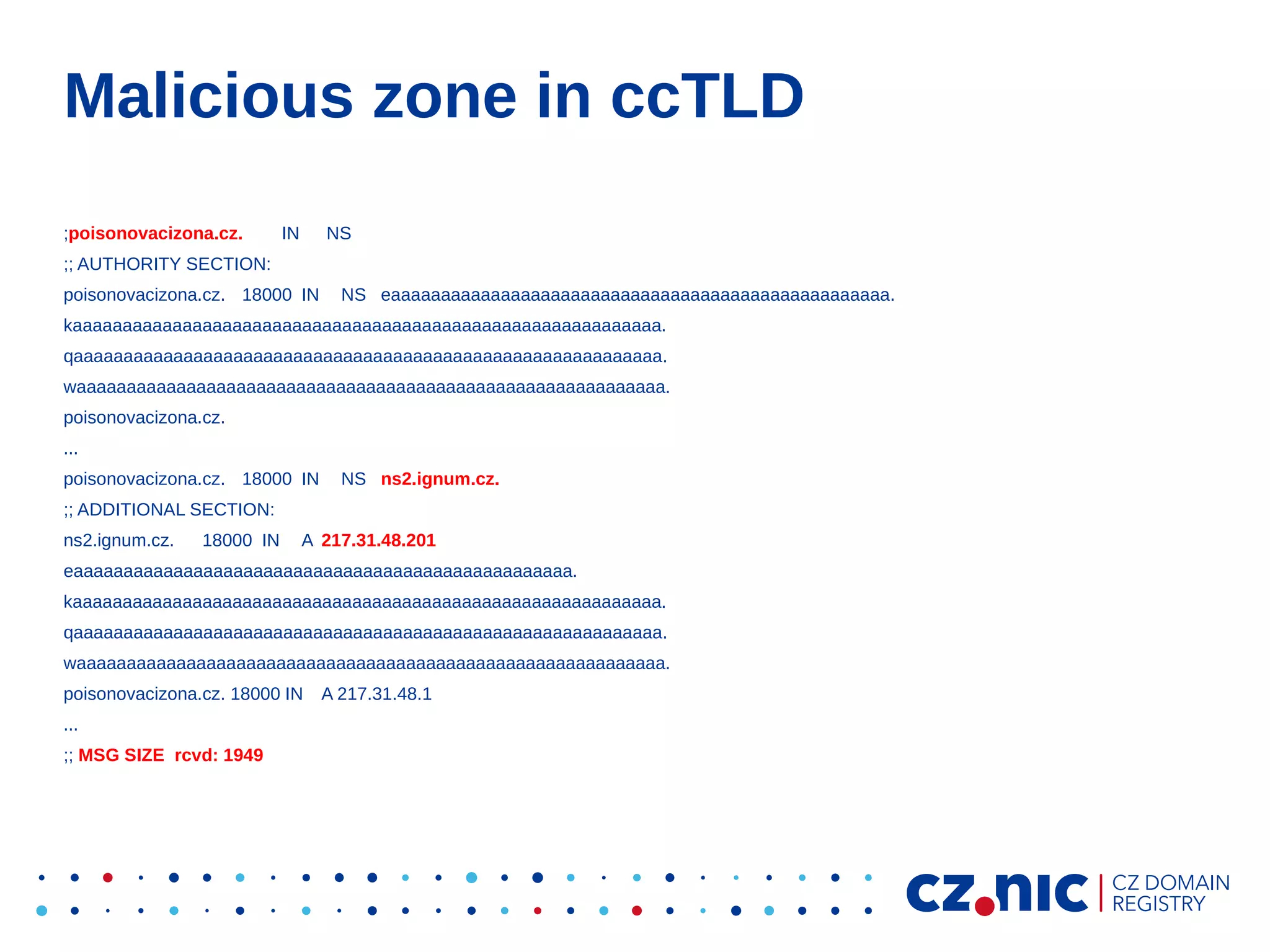
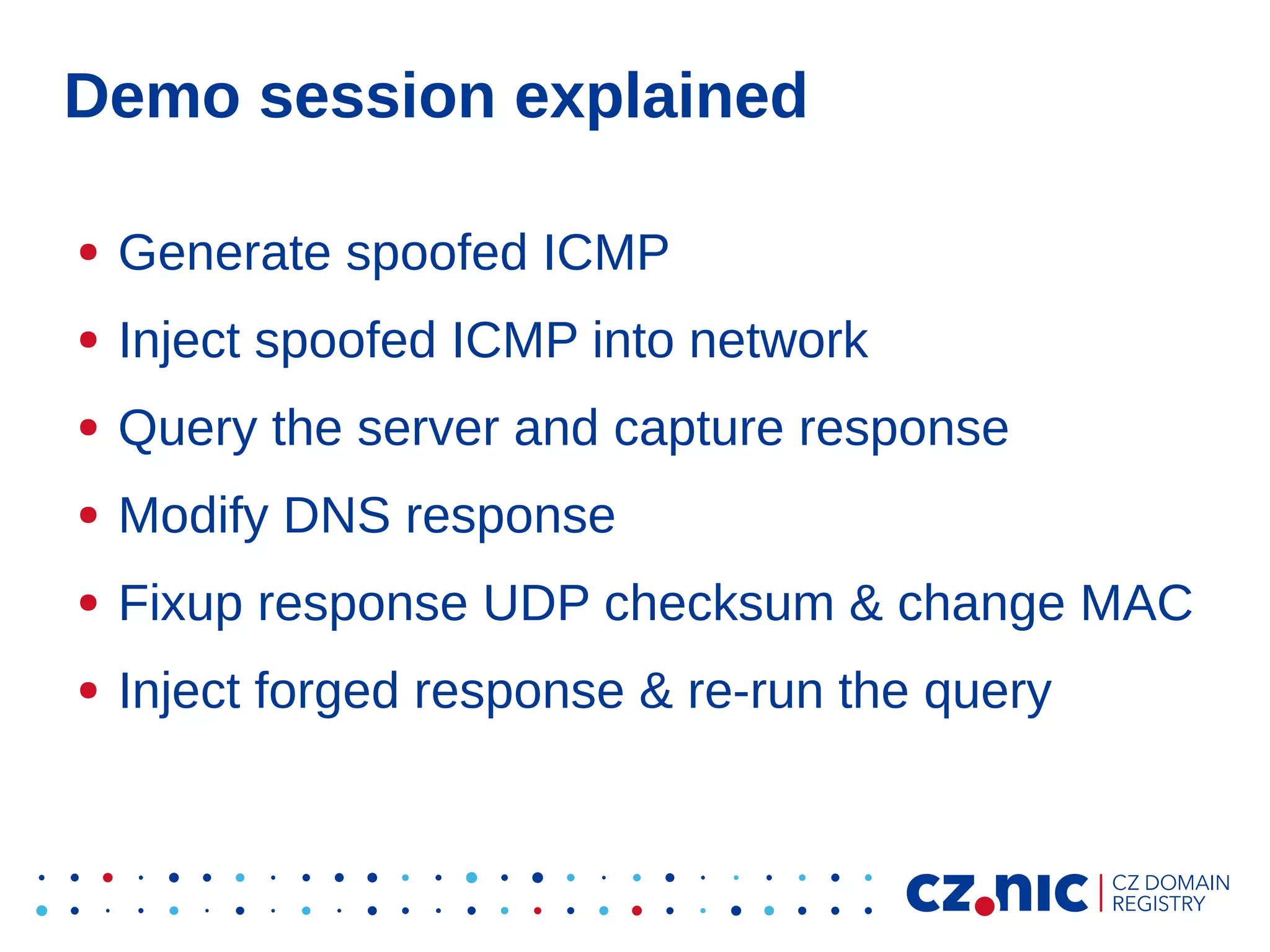
This document summarizes an IP fragmentation attack on DNS resolvers. It exploits IP fragmentation and reassembly to reduce the entropy for cache poisoning from 32 bits to 16 bits. There are two types of attacks - one triggers fragmentation through spoofed ICMP messages, while the other registers a specially crafted zone to generate oversized responses. The attacks allow modifying DNS response fragments off-path to poison caches. Defenses include DNSSEC and workaround like ignoring certain ICMP and limiting response sizes.