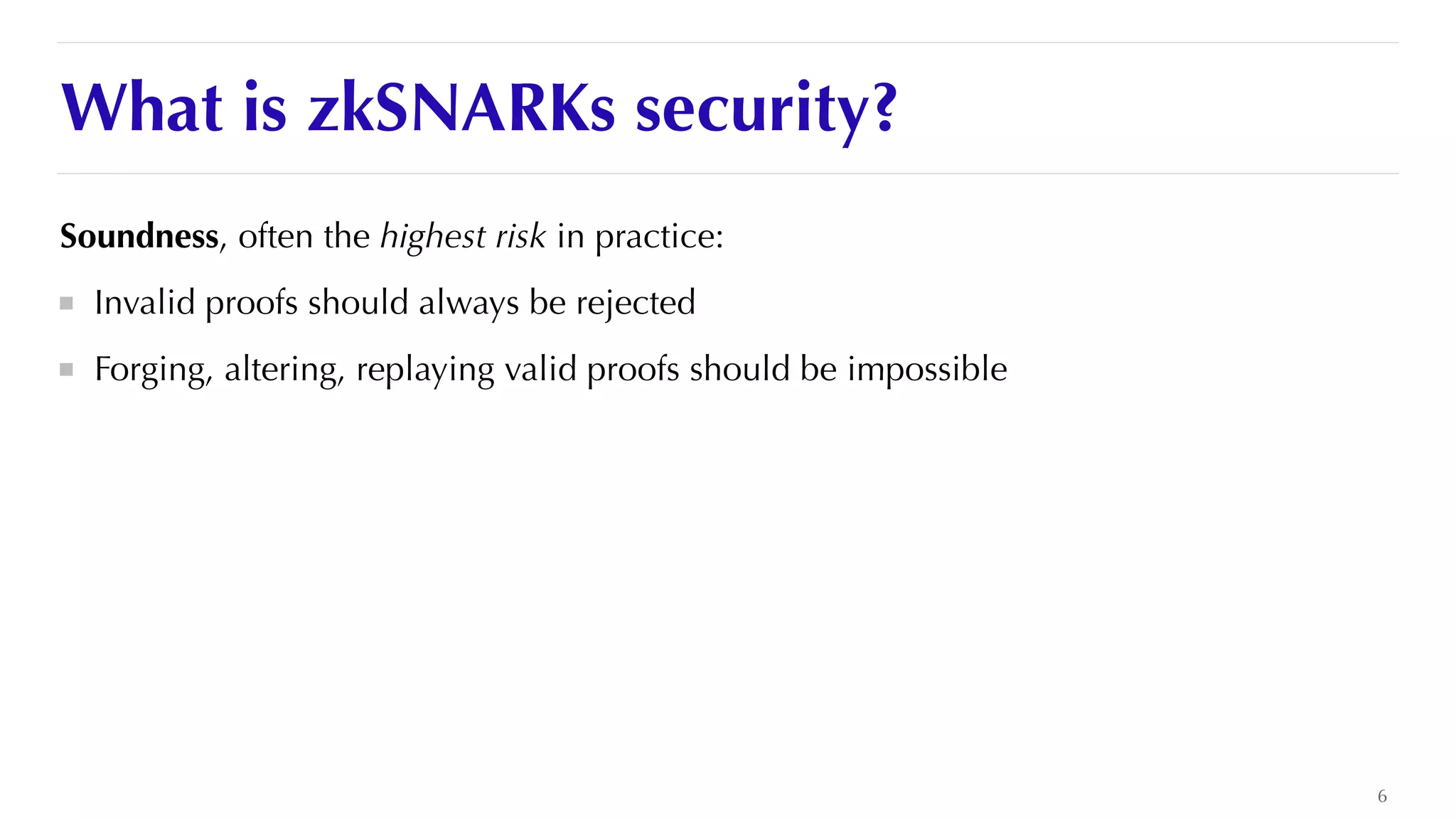
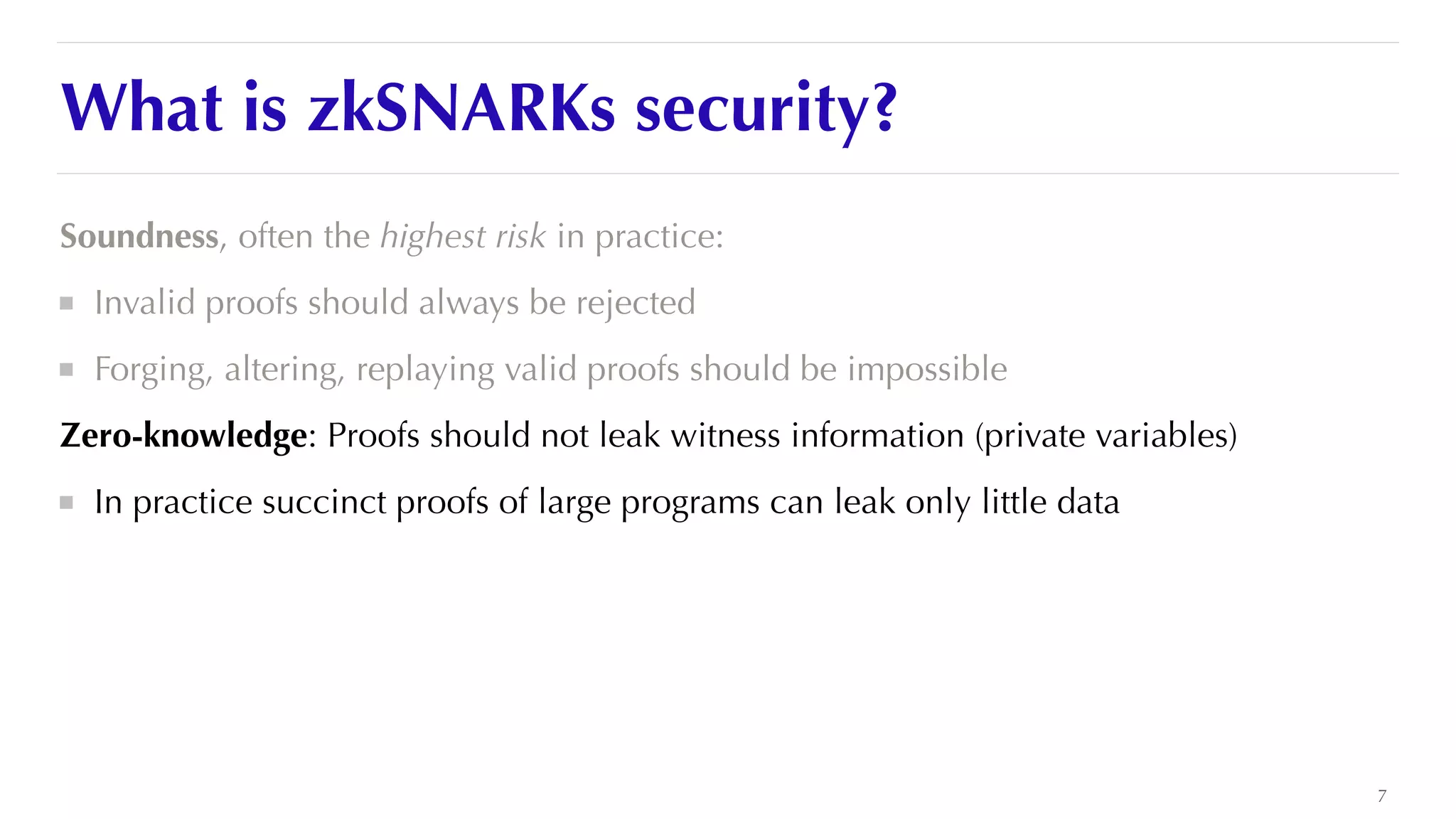
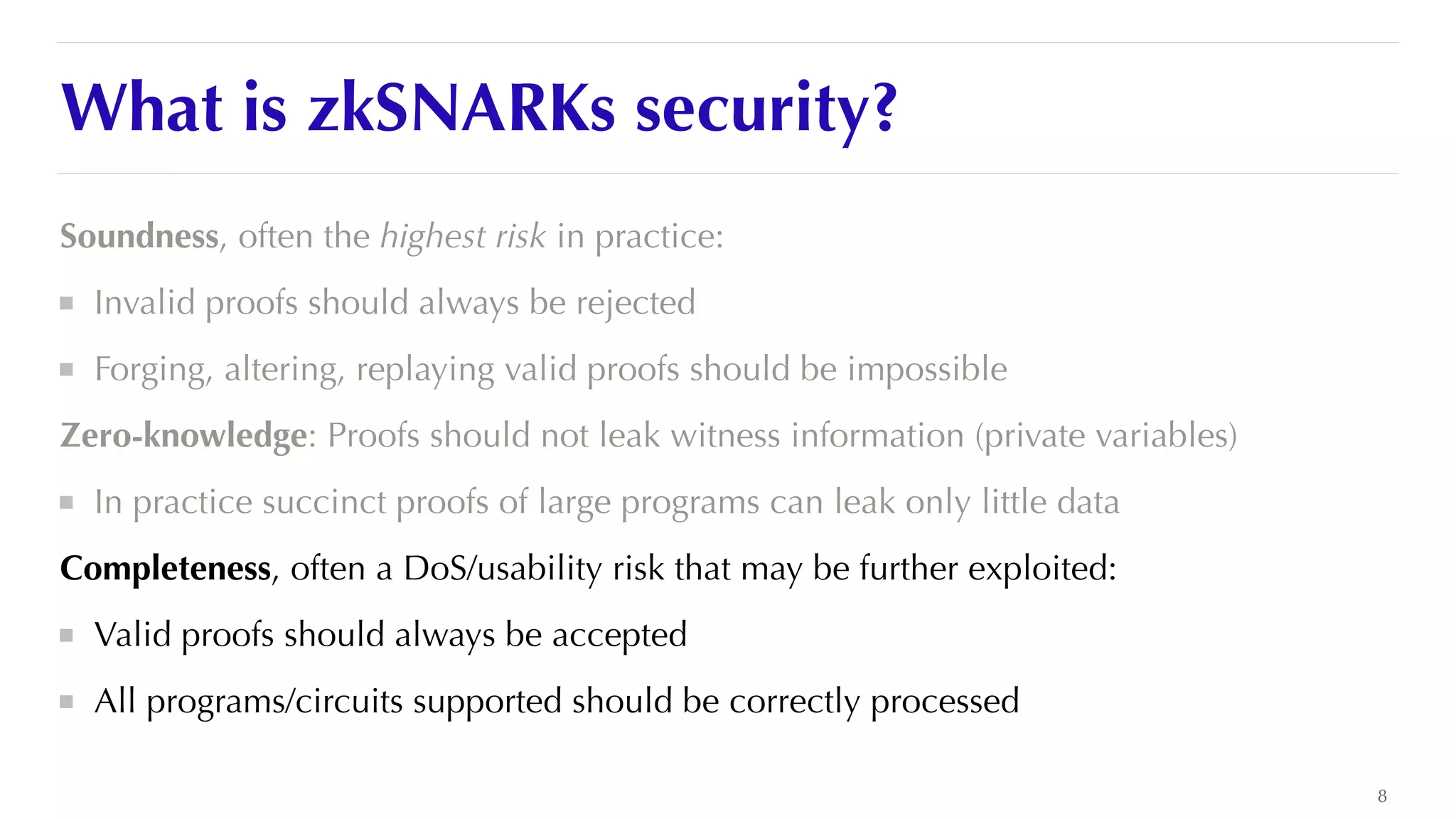
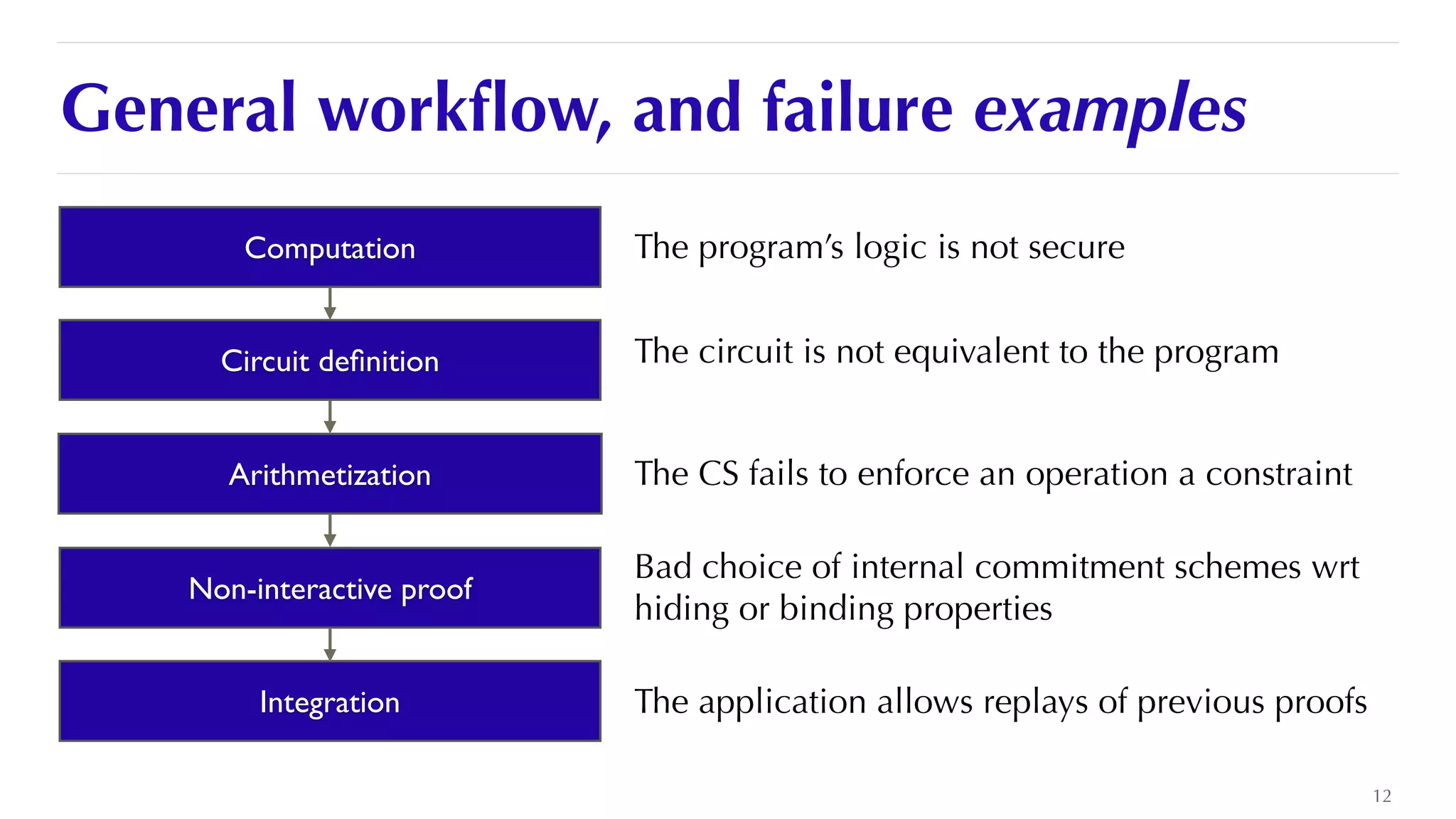
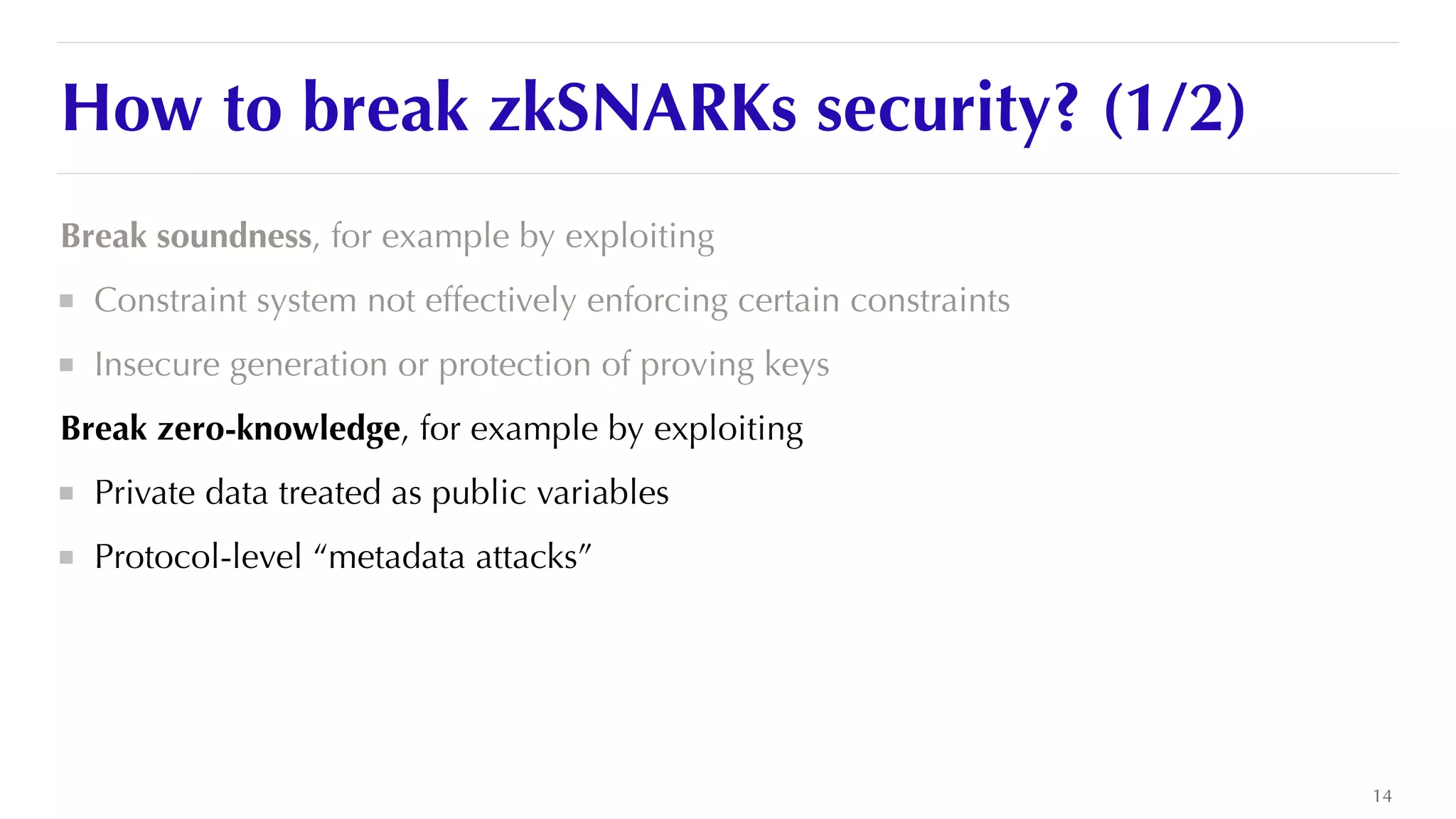
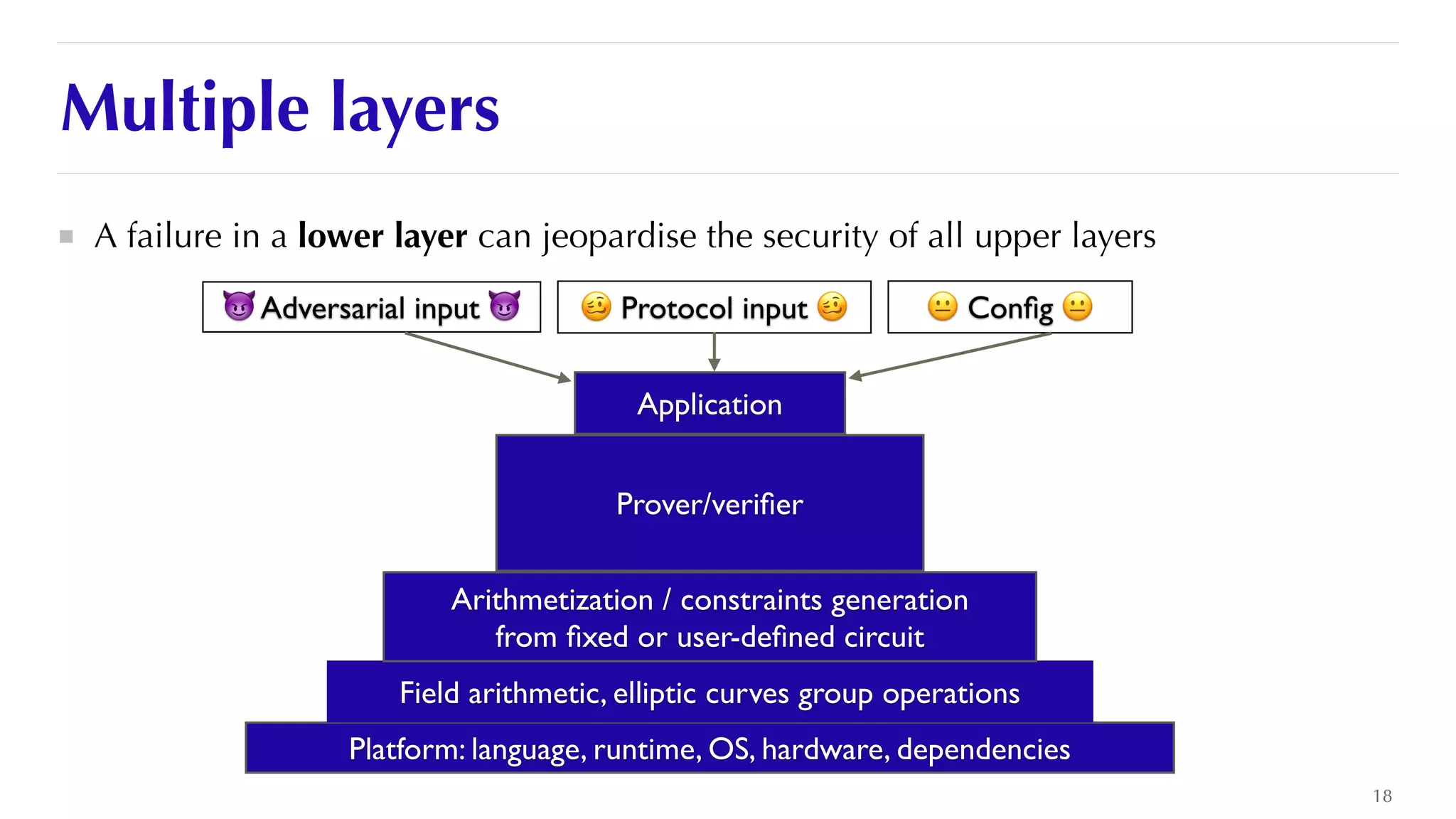
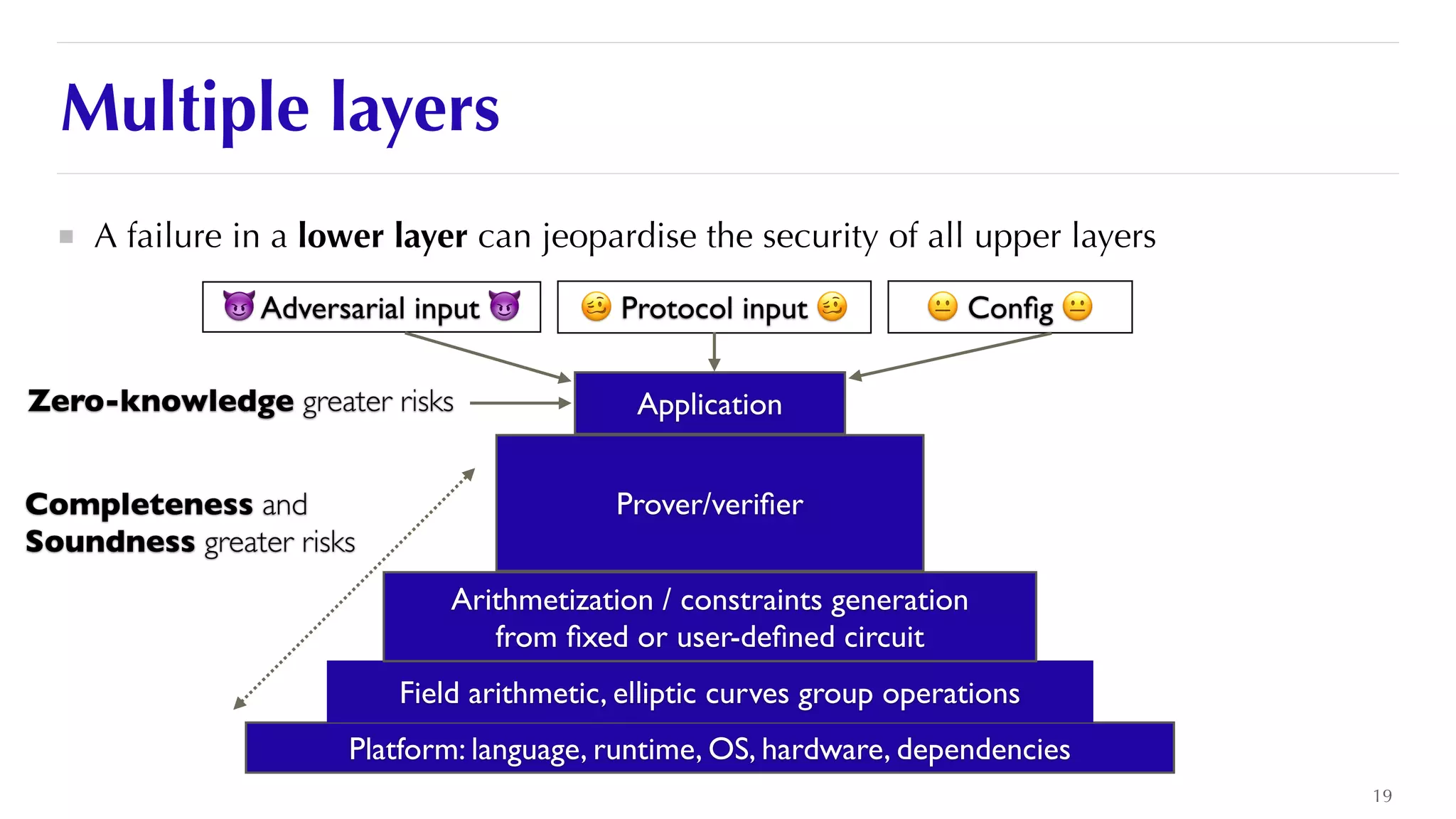
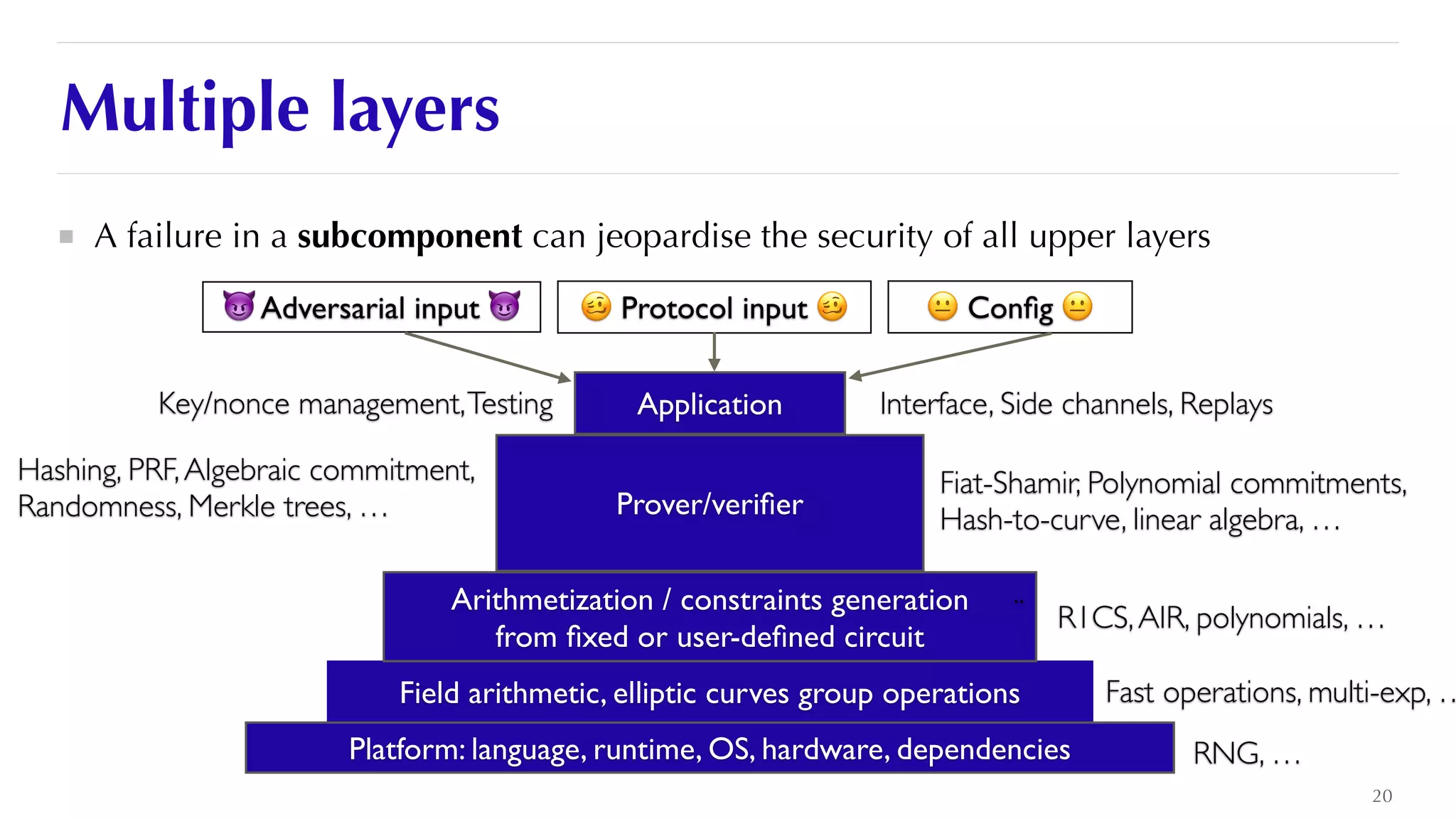
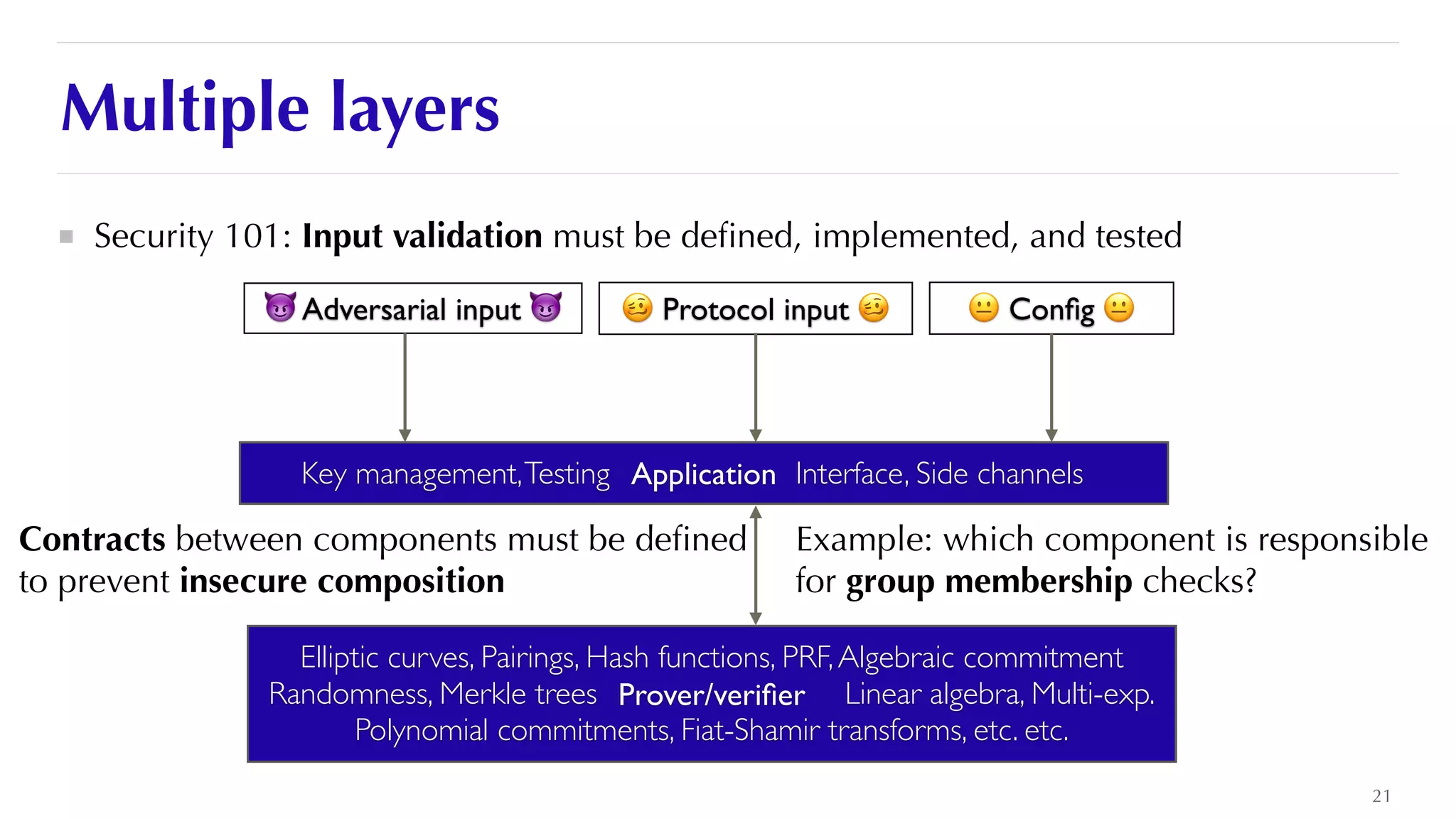
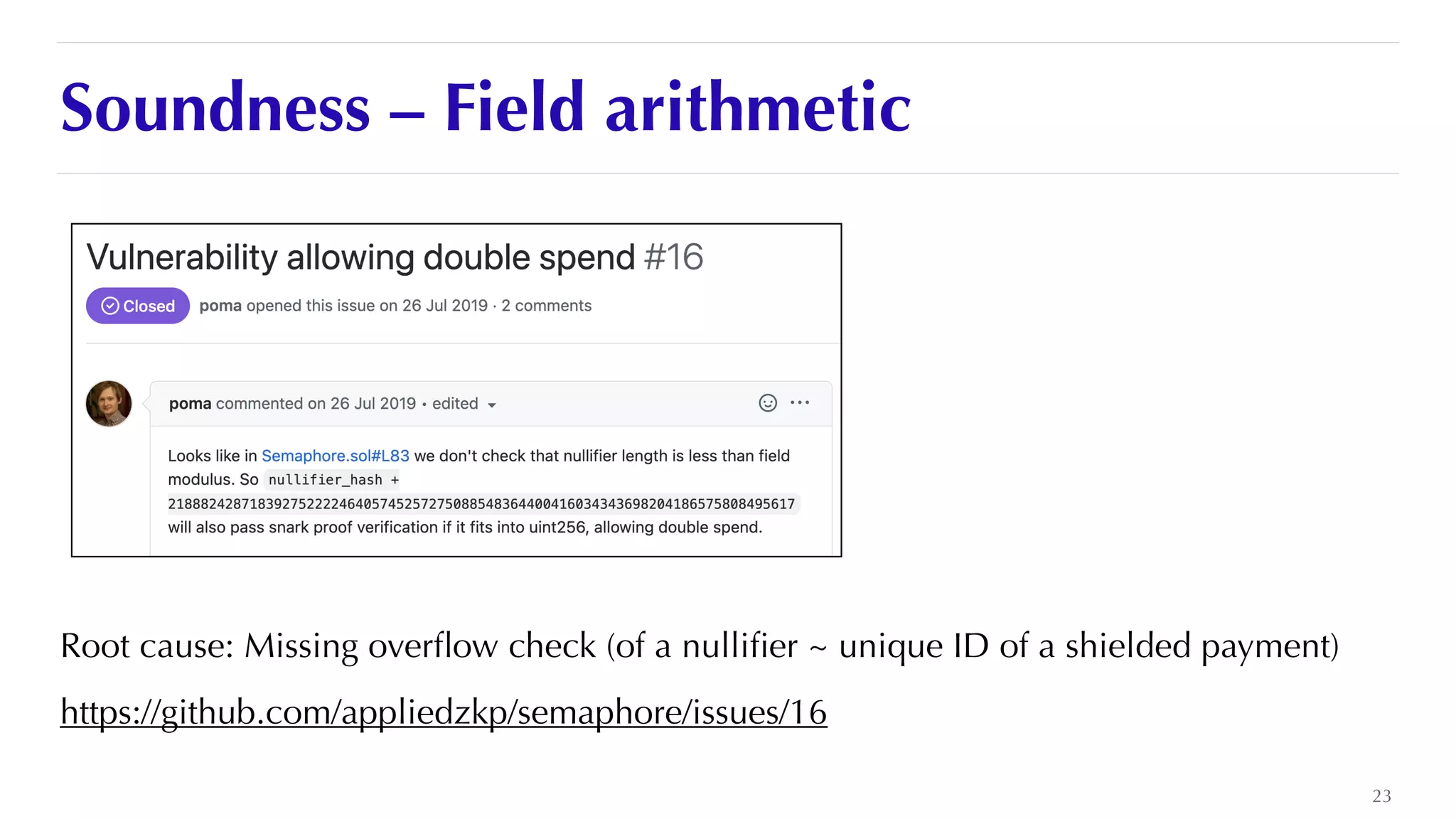
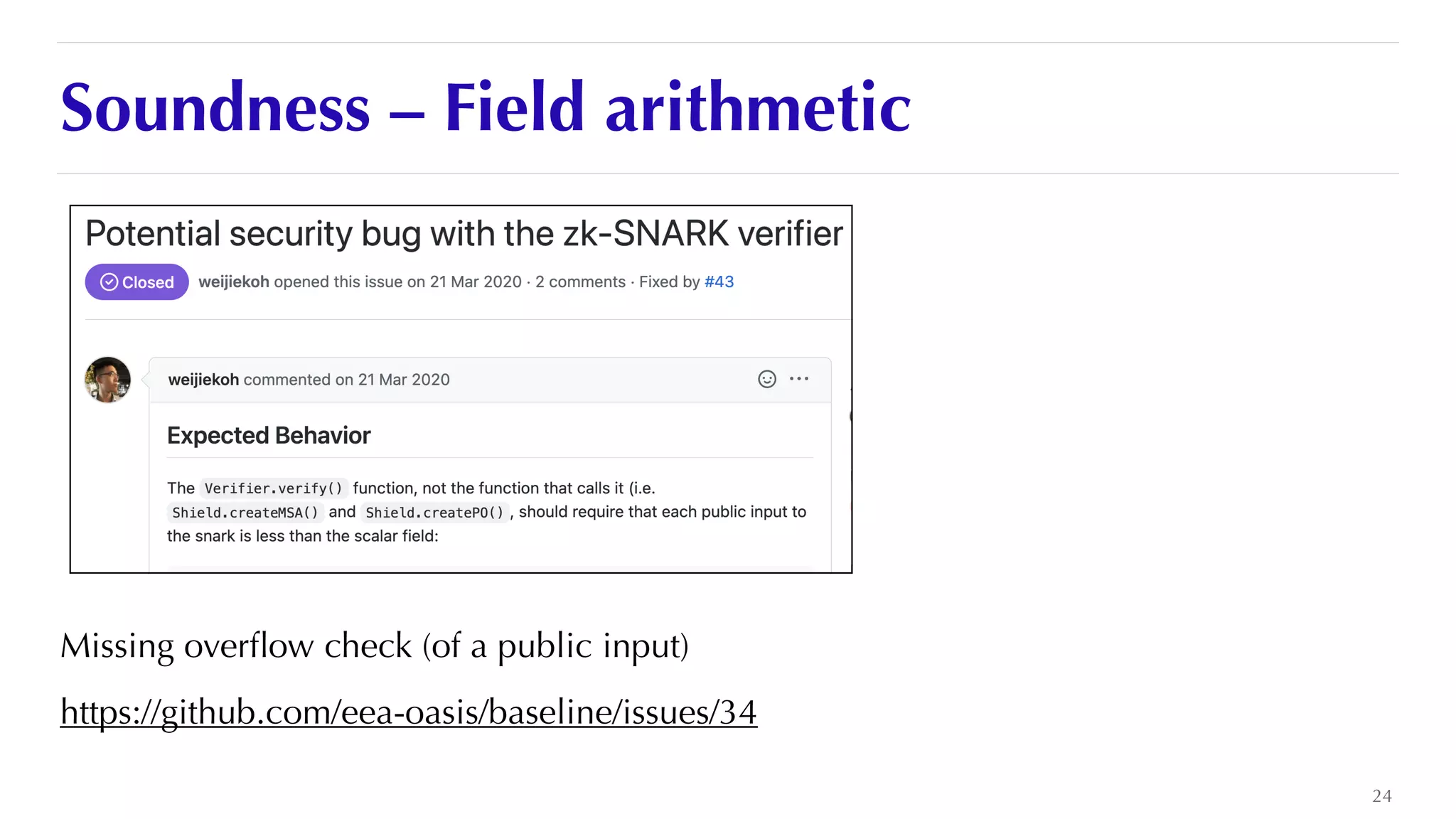
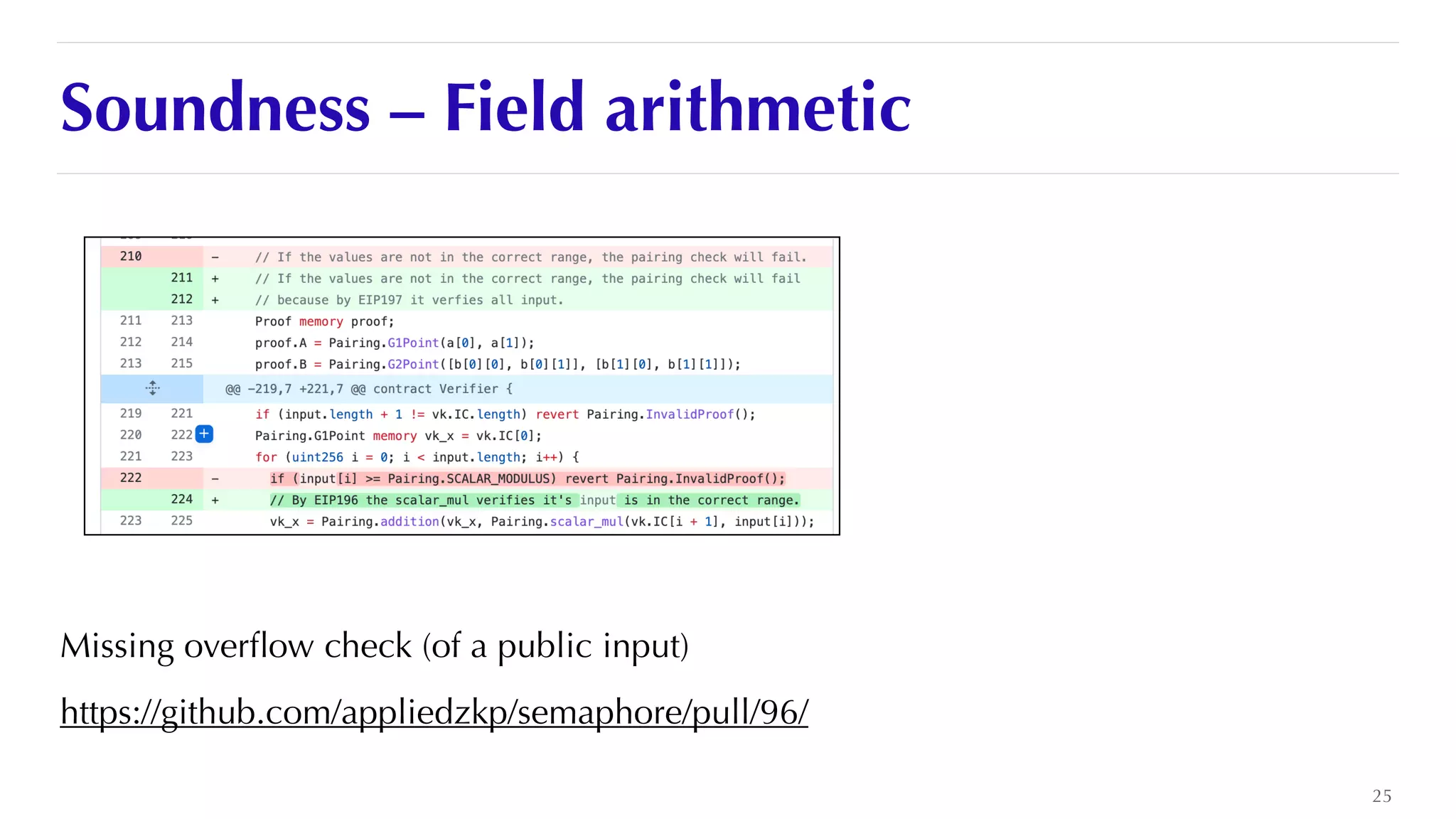
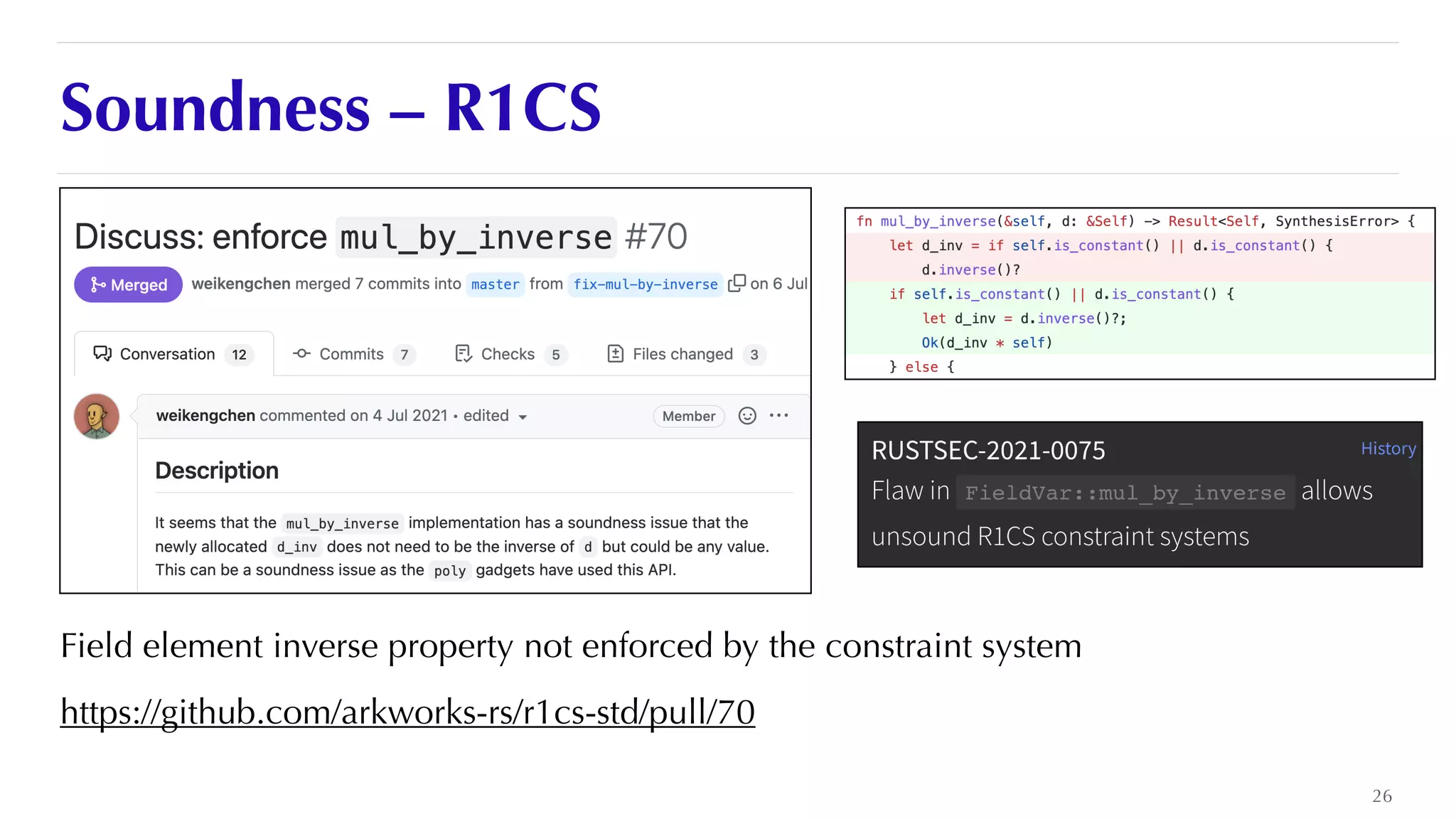
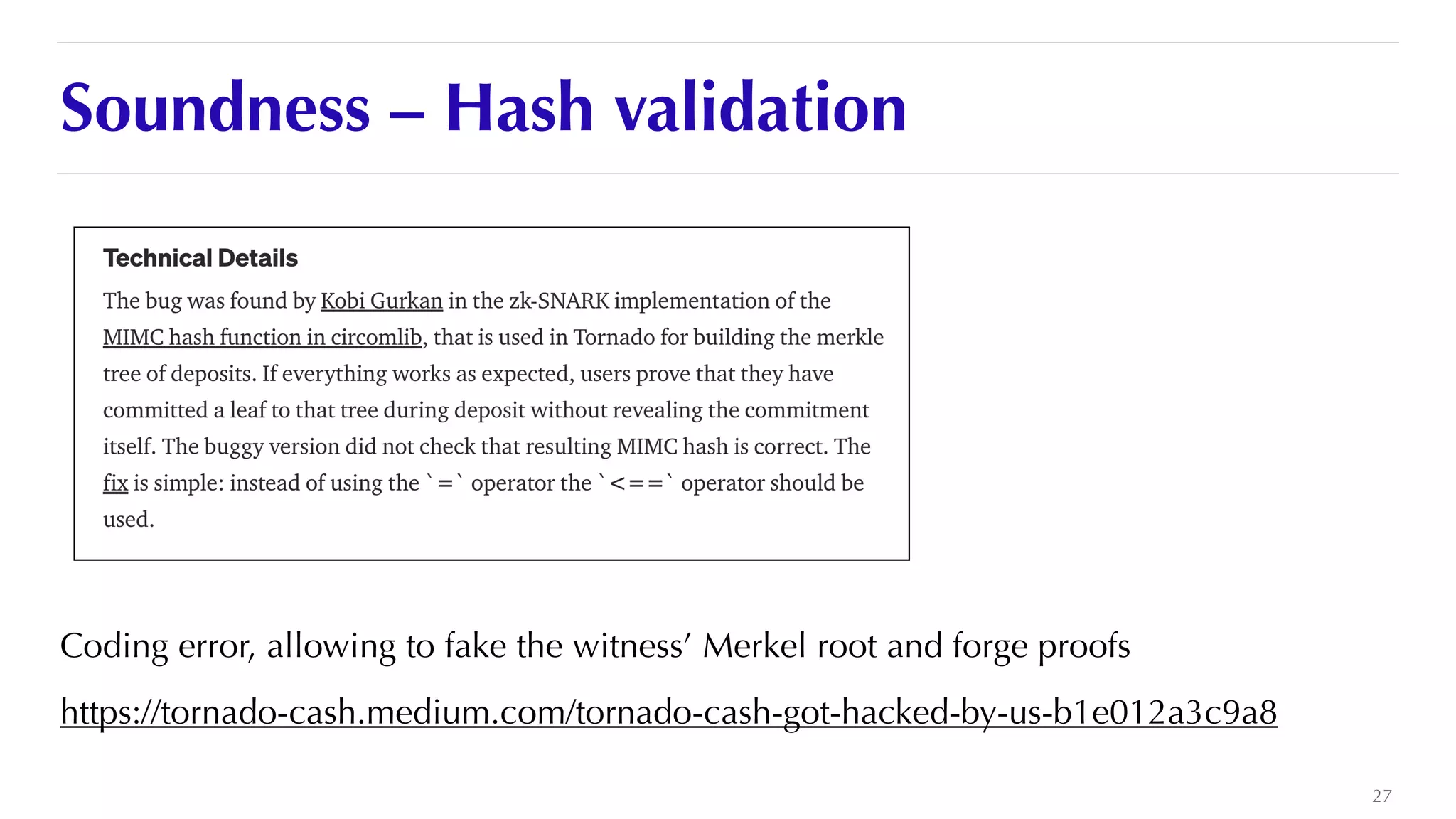
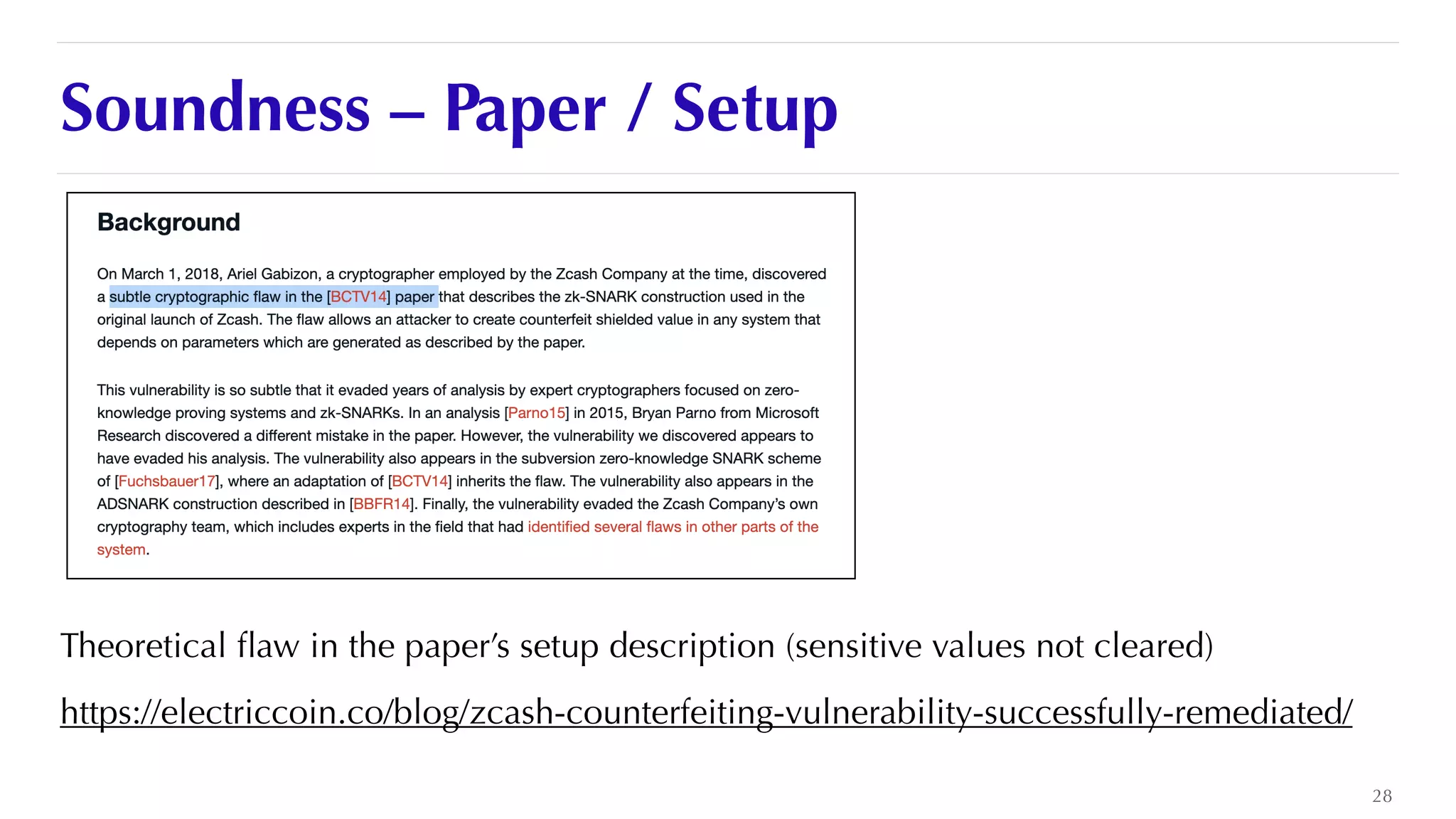
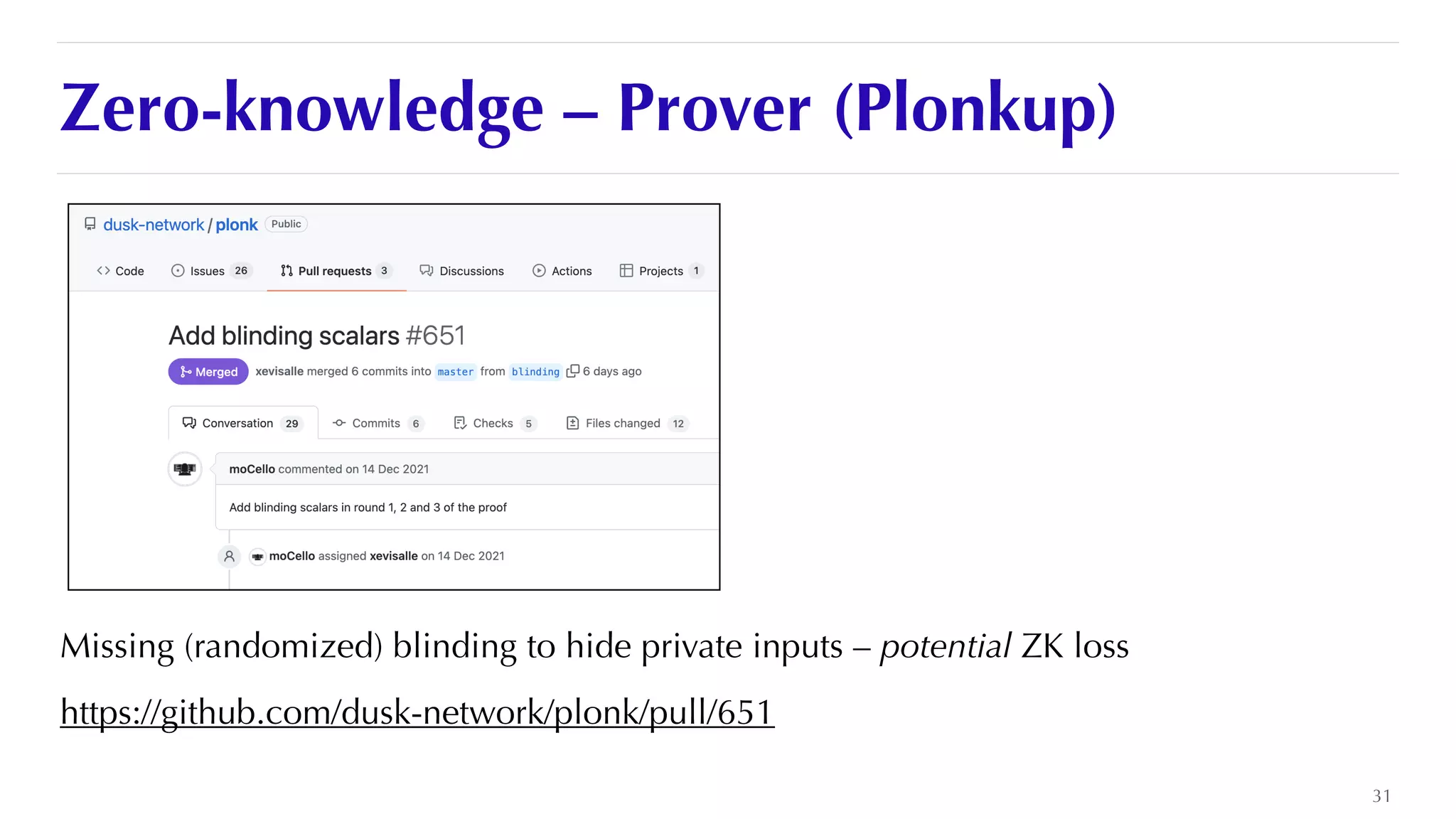
The document is a presentation by JP Aumasson focused on the security of zero-knowledge succinct non-interactive arguments (ZK-SNARKs), highlighting risks, challenges in auditing, and potential vulnerabilities. It discusses the importance of soundness, completeness, and zero-knowledge properties, while outlining how to break ZK-SNARK security. The presentation emphasizes the need for better collaboration, threat analysis, and improved auditing practices in the rapidly evolving landscape of blockchain technology.