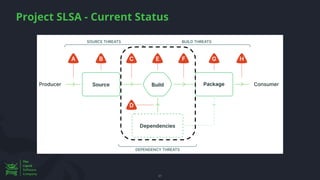
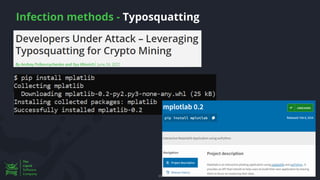
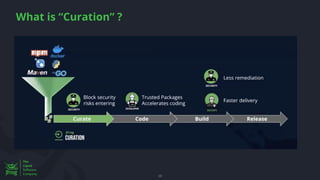
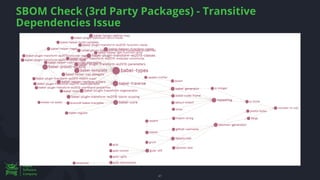
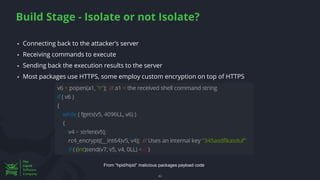
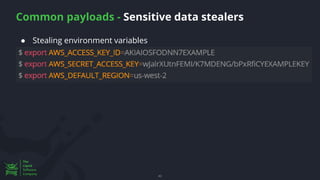
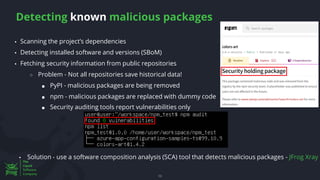
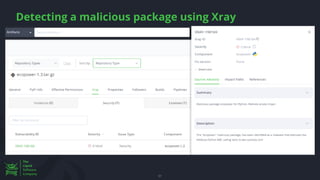
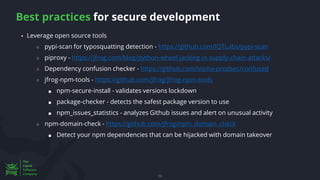
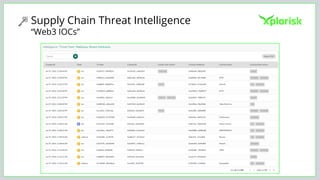
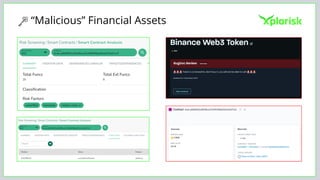
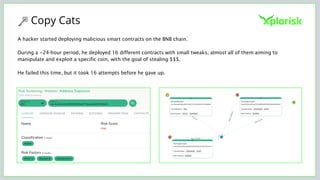
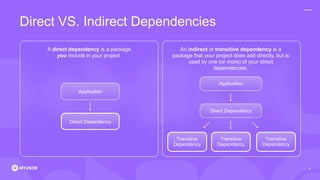
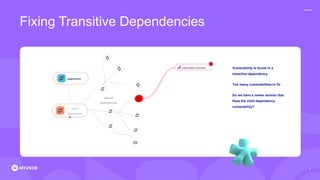
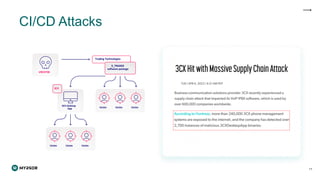
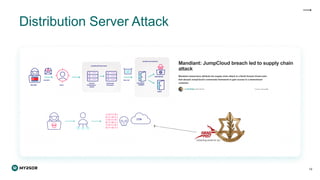
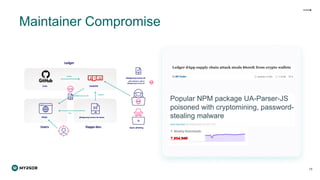
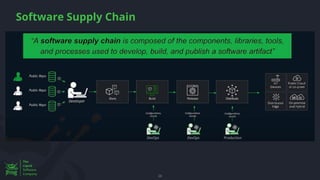
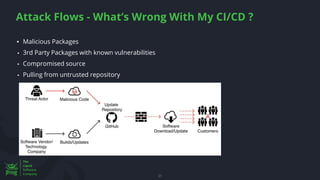
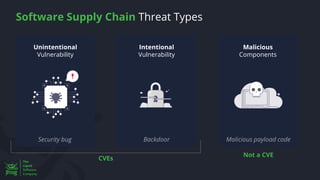
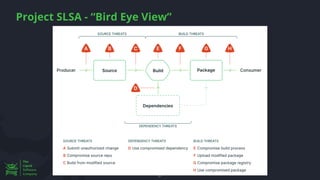
The document discusses the rising threat of software supply chain attacks, highlighting various attack types and the importance of securing dependencies in software development. It details the challenges posed by these attacks, such as vulnerabilities in third-party code, and introduces frameworks like SLSA to improve security measures. Additionally, it emphasizes best practices for development teams to mitigate risks associated with open-source dependencies and enhance overall security.




















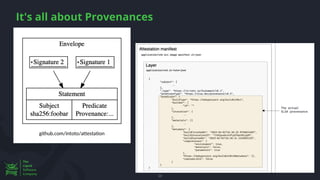
![DSSE
30
▪ Problems with JWT and TUF signatures
▪ Not just JSON
▪ No Need Canonicalization
▪ Supports a PAE (Pre-Auth-Encoding)
{'payload': 'SGVsbG8gMTIz',
'payloadType': 'http://example.com/testing',
'signatures': [{'keyid': '2a7141d6',
'sig':
'i16opxQrAEnXJ7x9kTWYd2LtZwEoRQqhYEvxoexvj2/tKXX6DZE8cbQ3eEGb8ZtuWcMk2LjD
LyhpQ2BSGcwQnA=='}]}](https://image.slidesharecdn.com/vulnerabilityalertfatigueandmaliciouscodeattacksmeetup11012024-240116081455-c8f89fc7/85/Vulnerability-Alert-Fatigue-and-Malicious-Code-Attacks-Meetup-11012024-pdf-30-320.jpg)