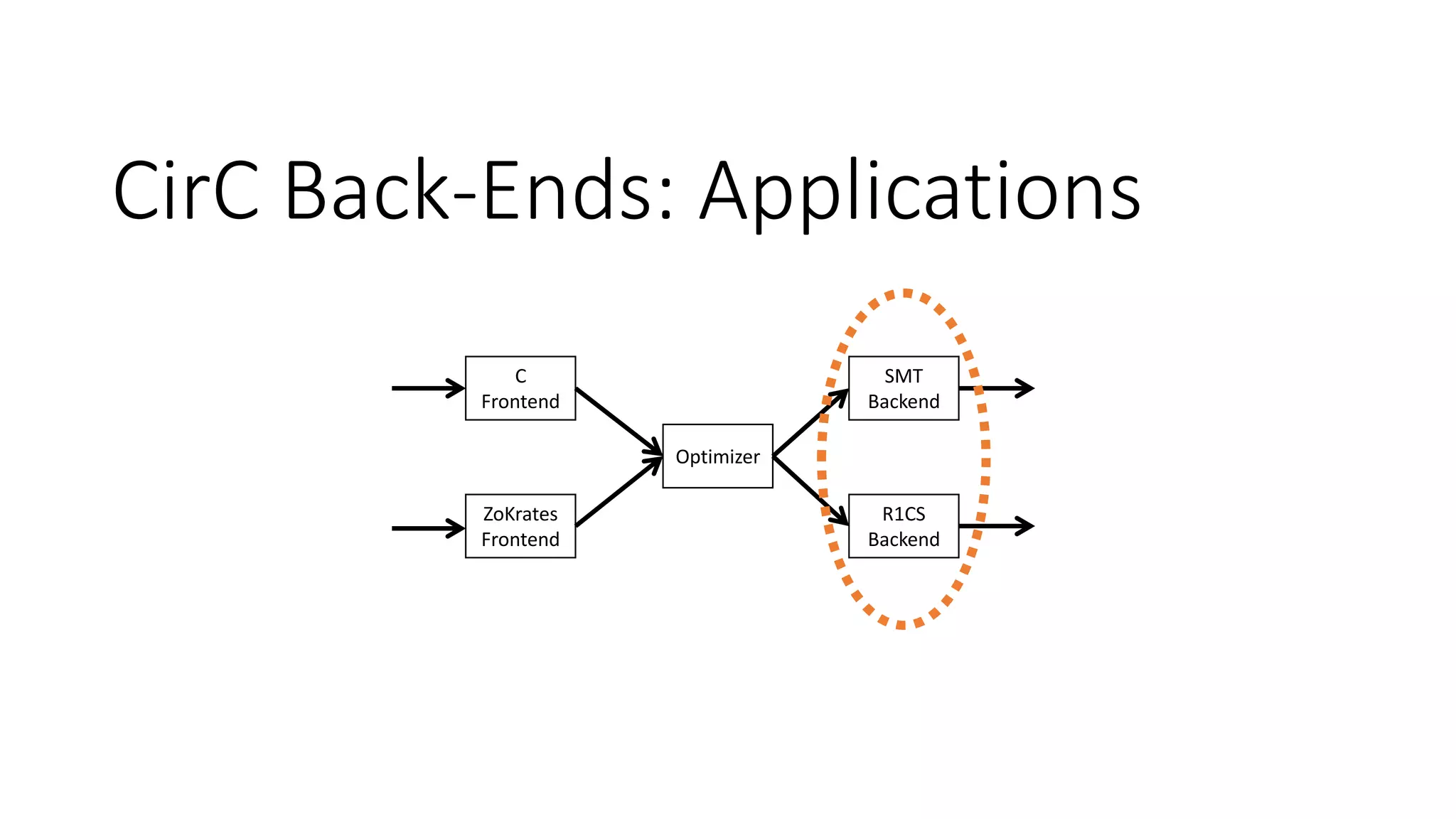
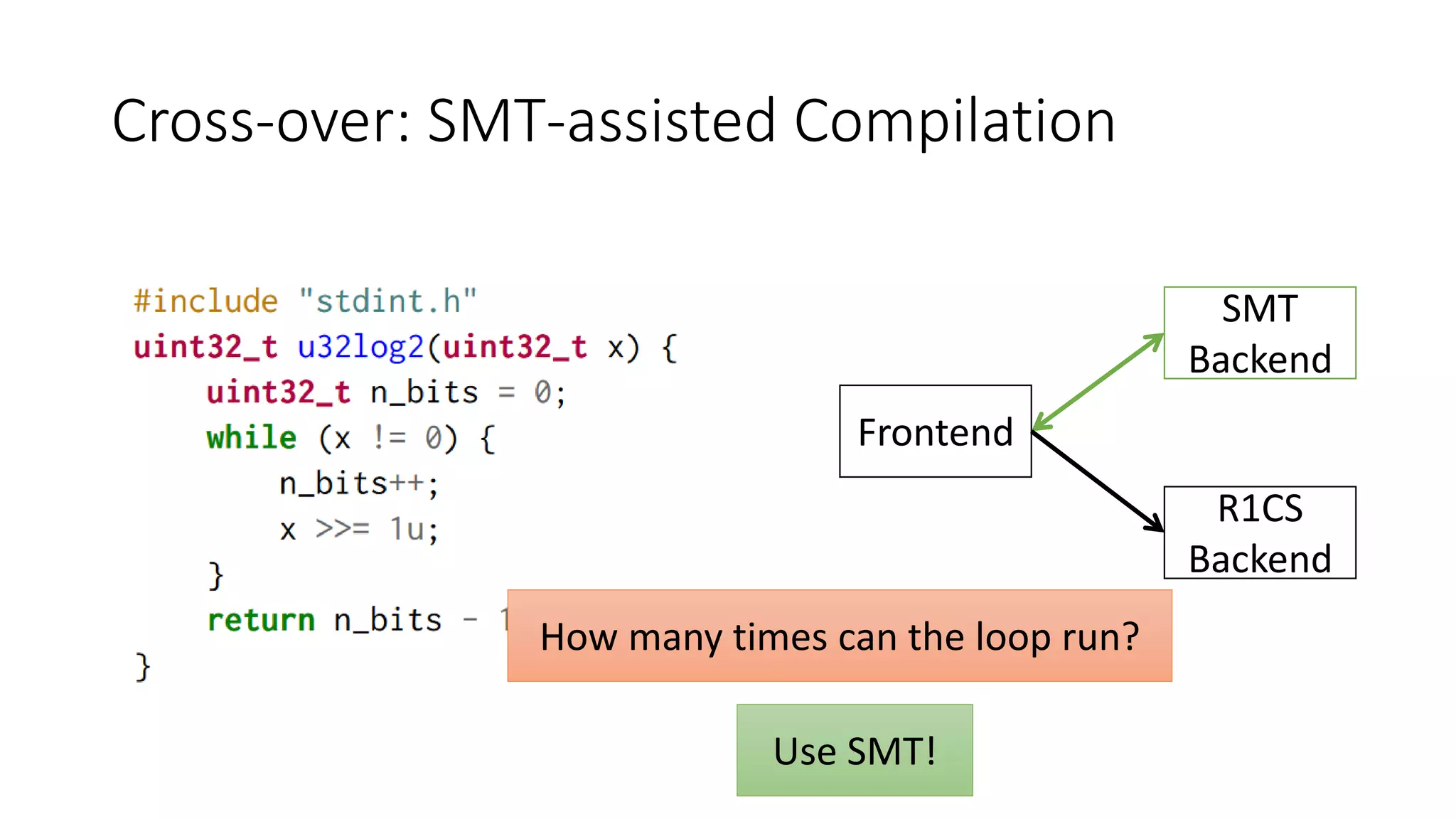
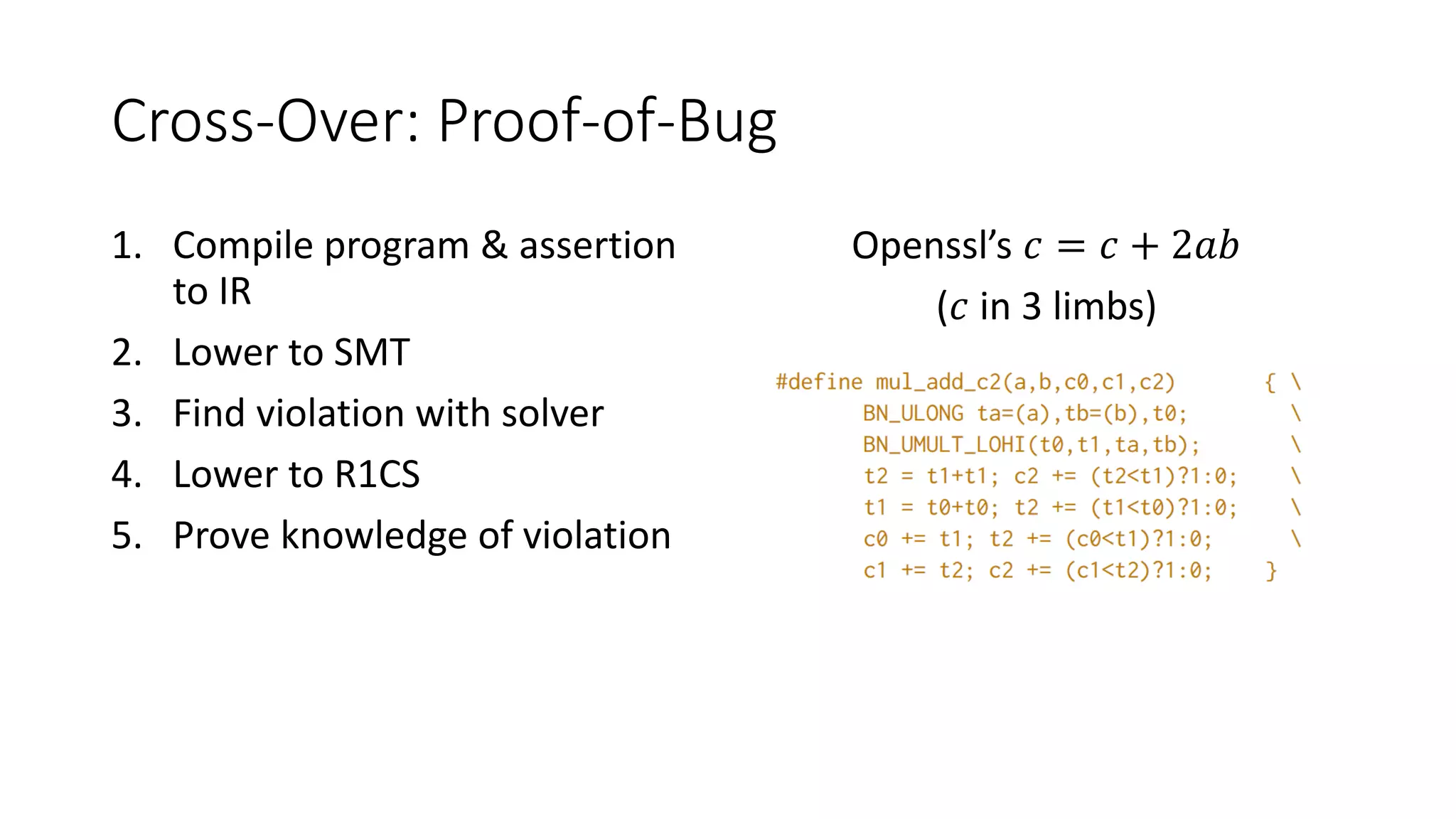
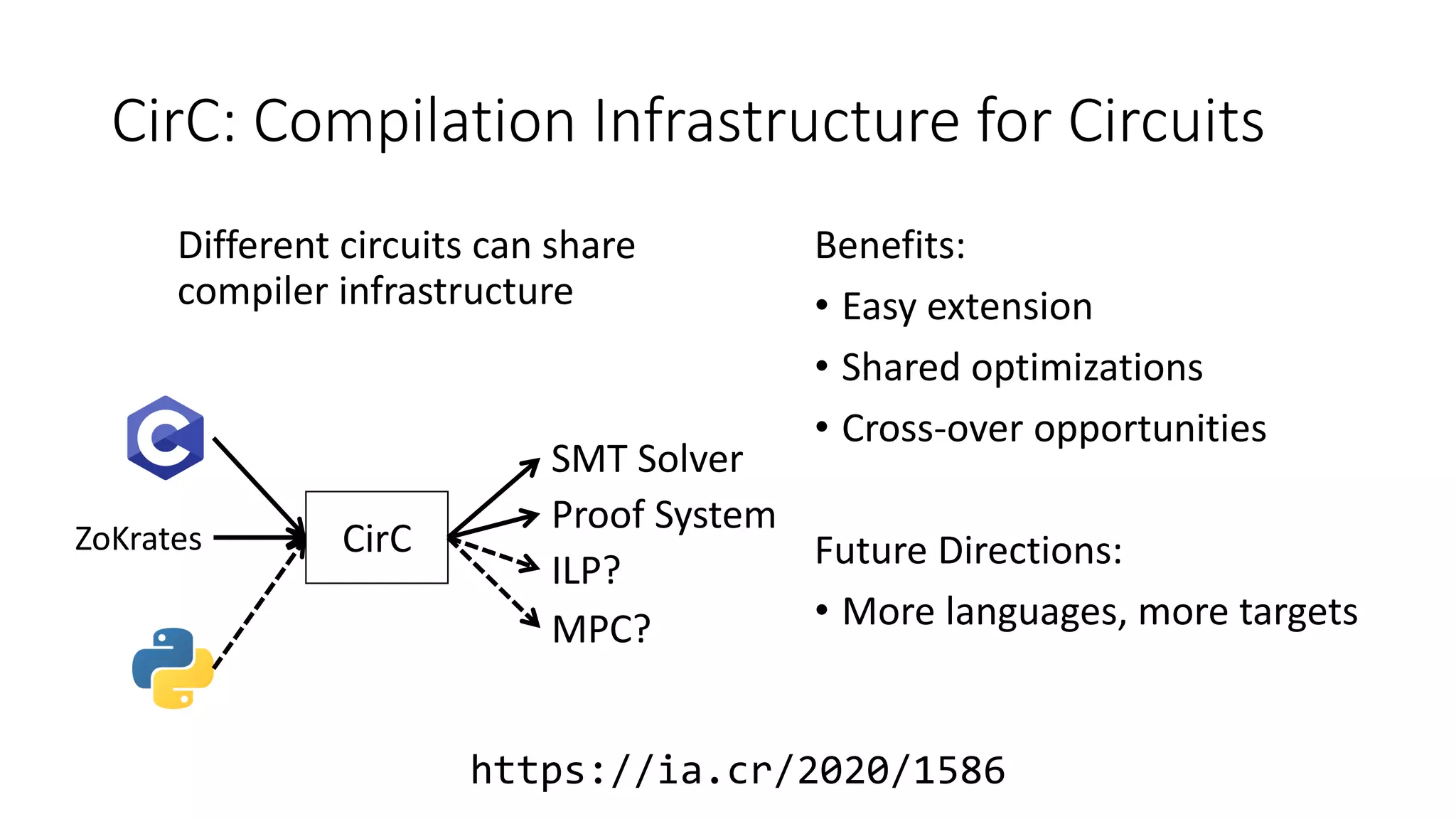
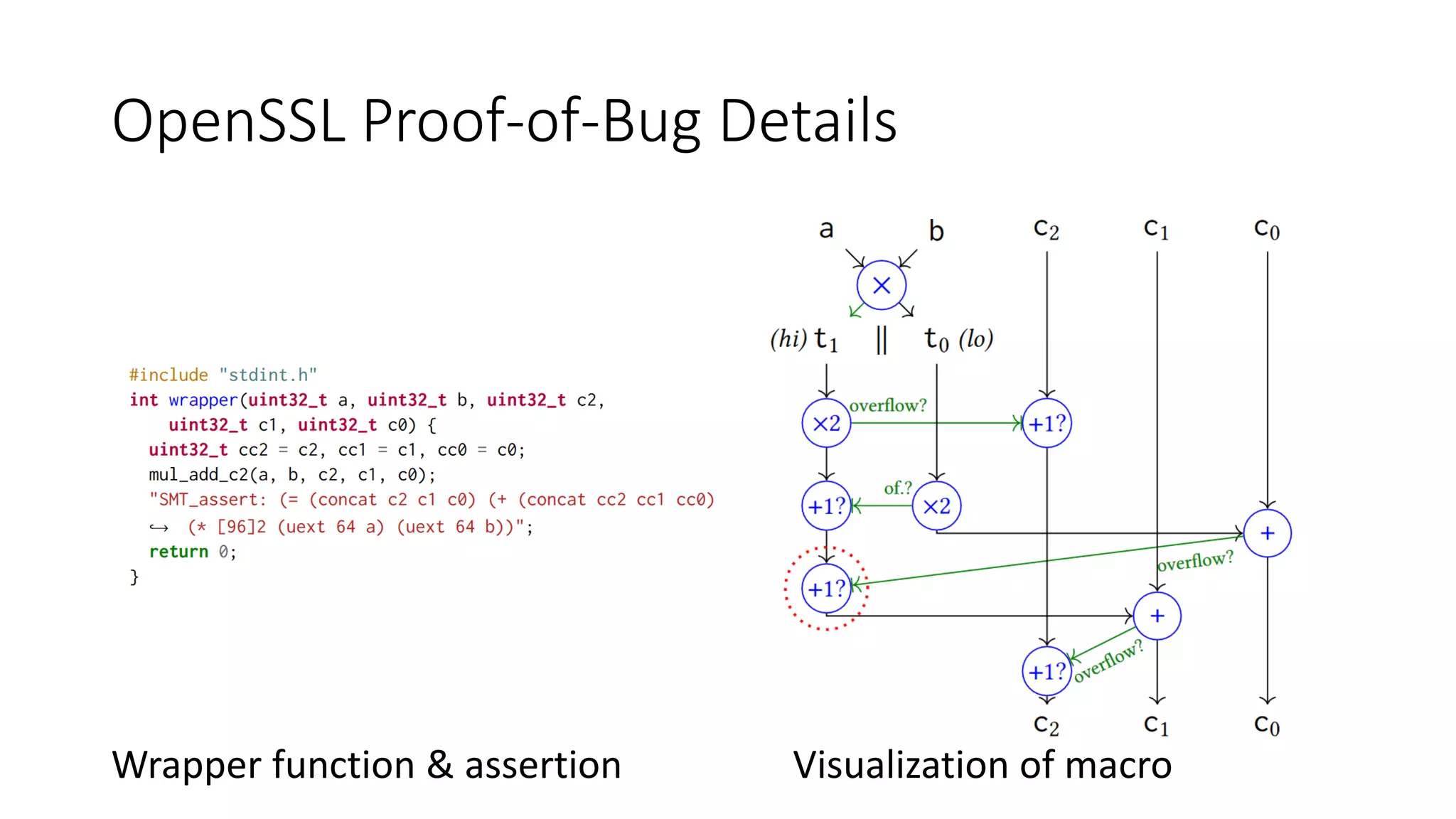
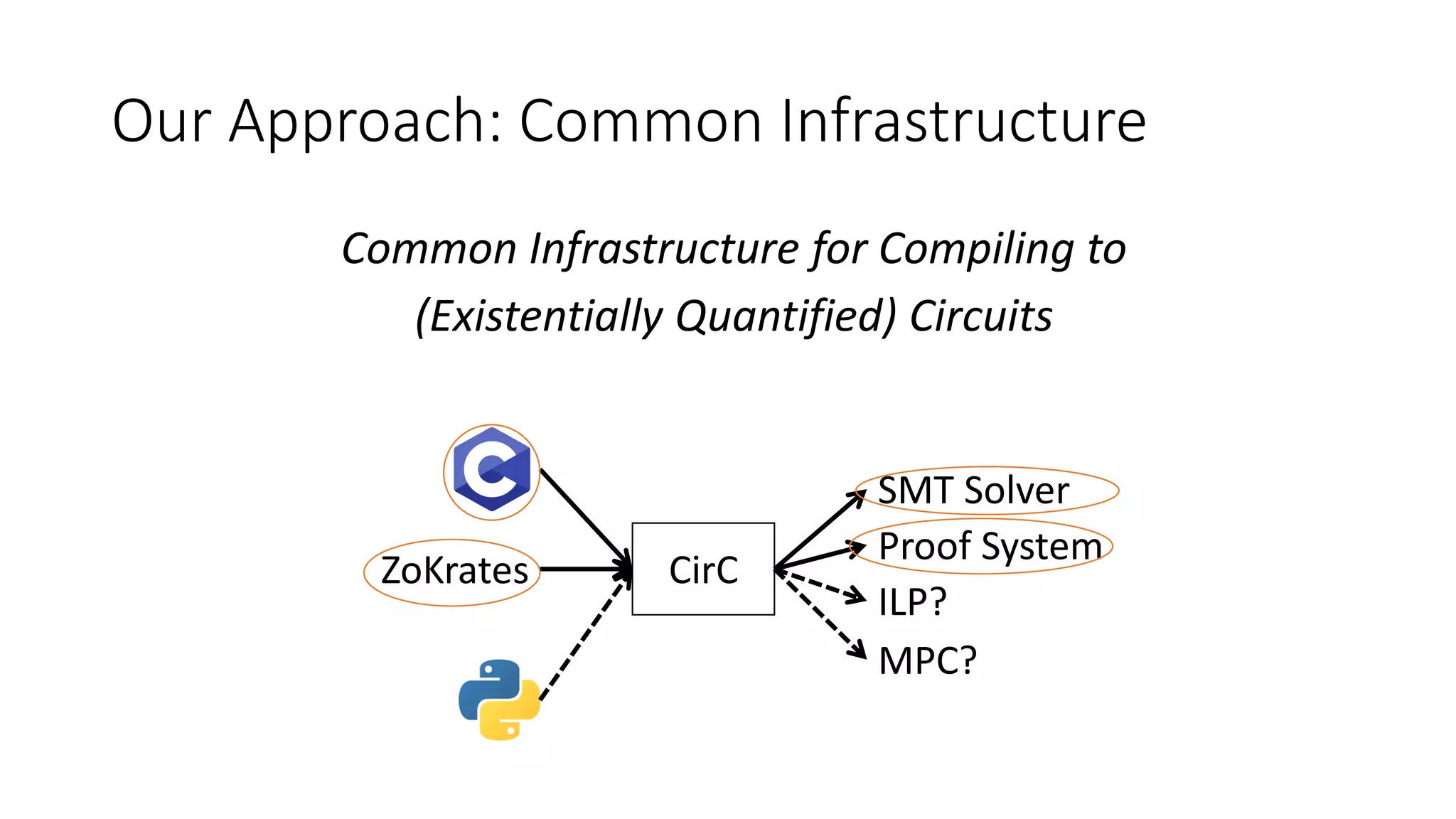
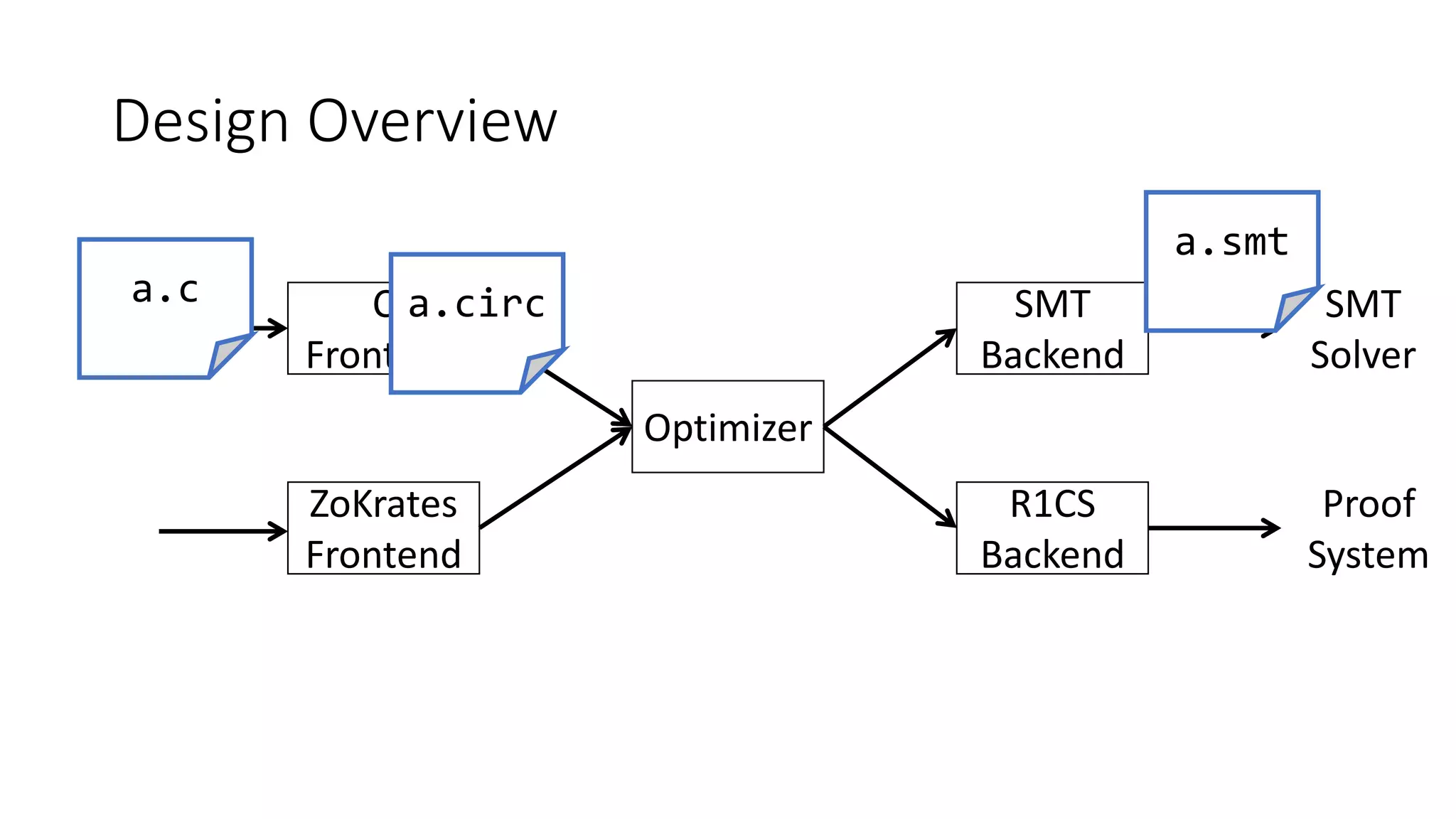
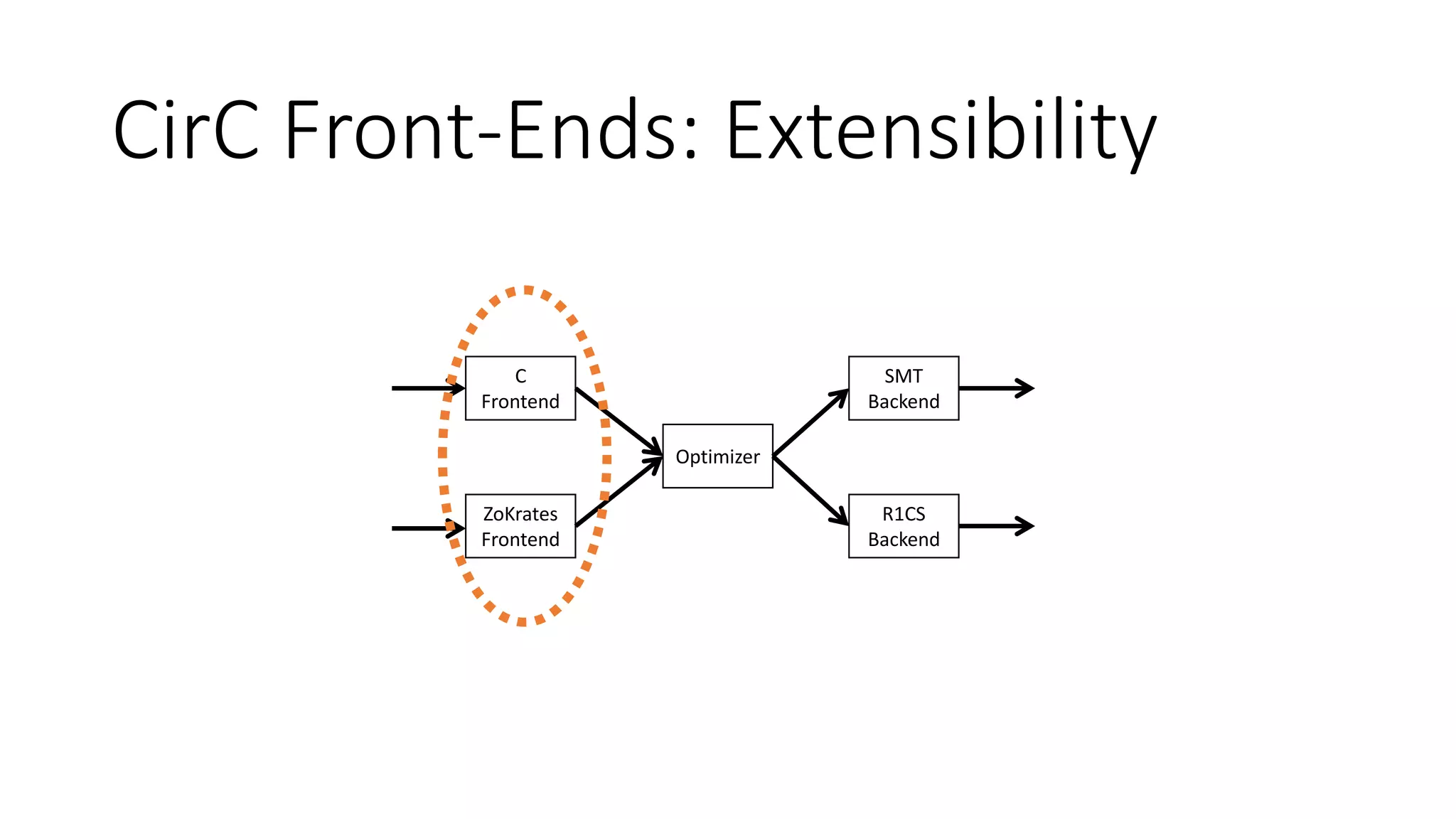
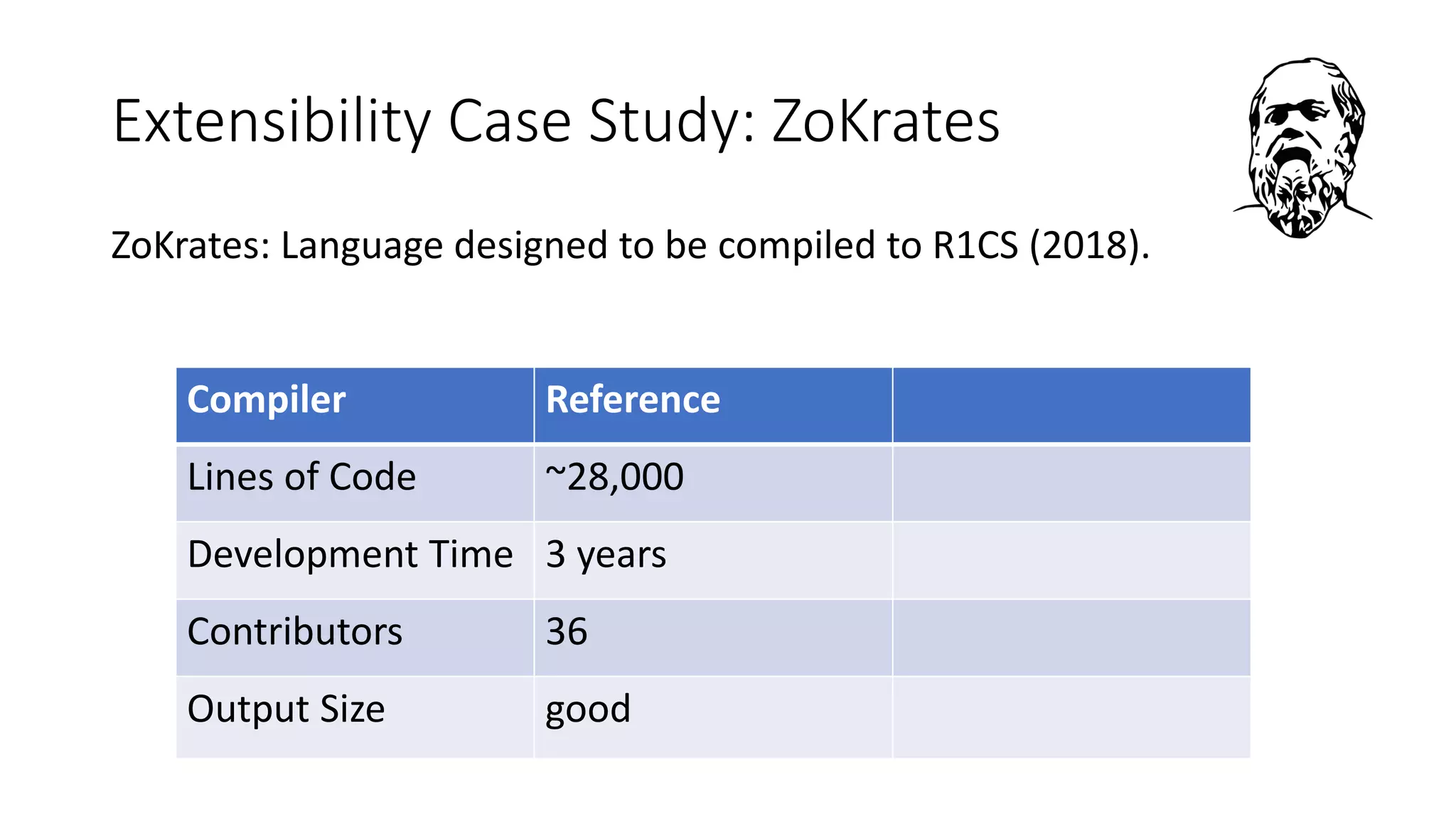
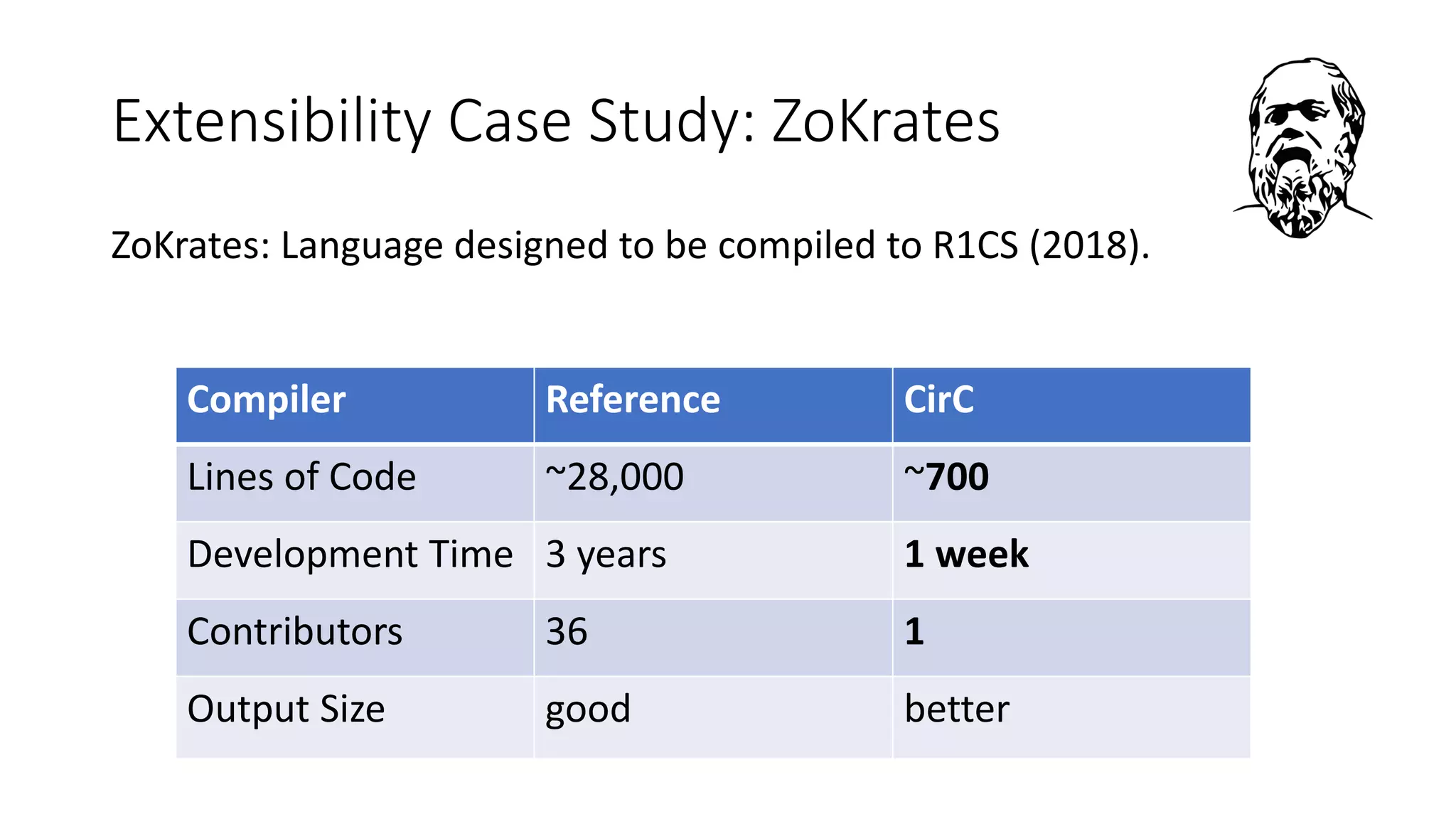
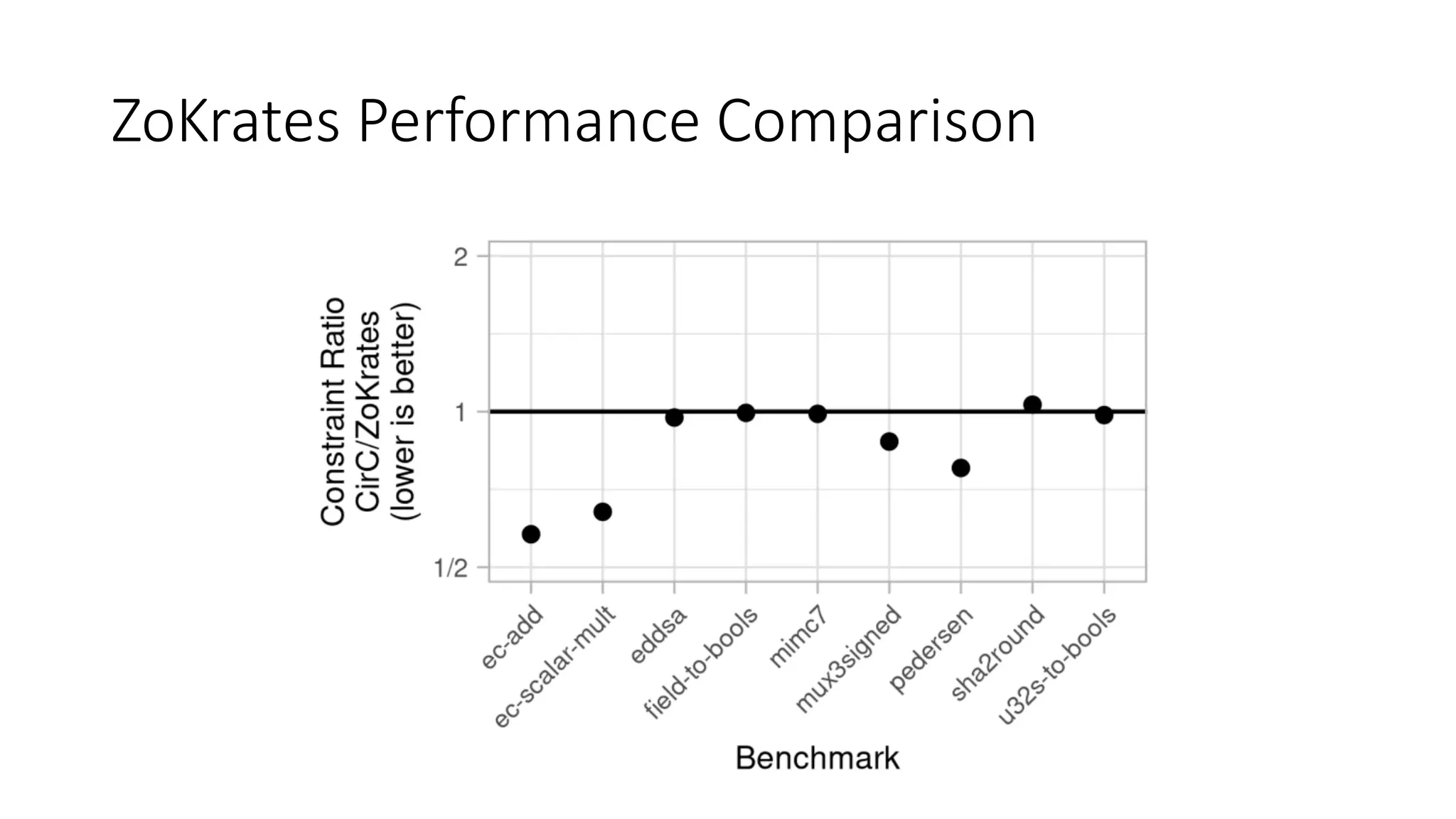
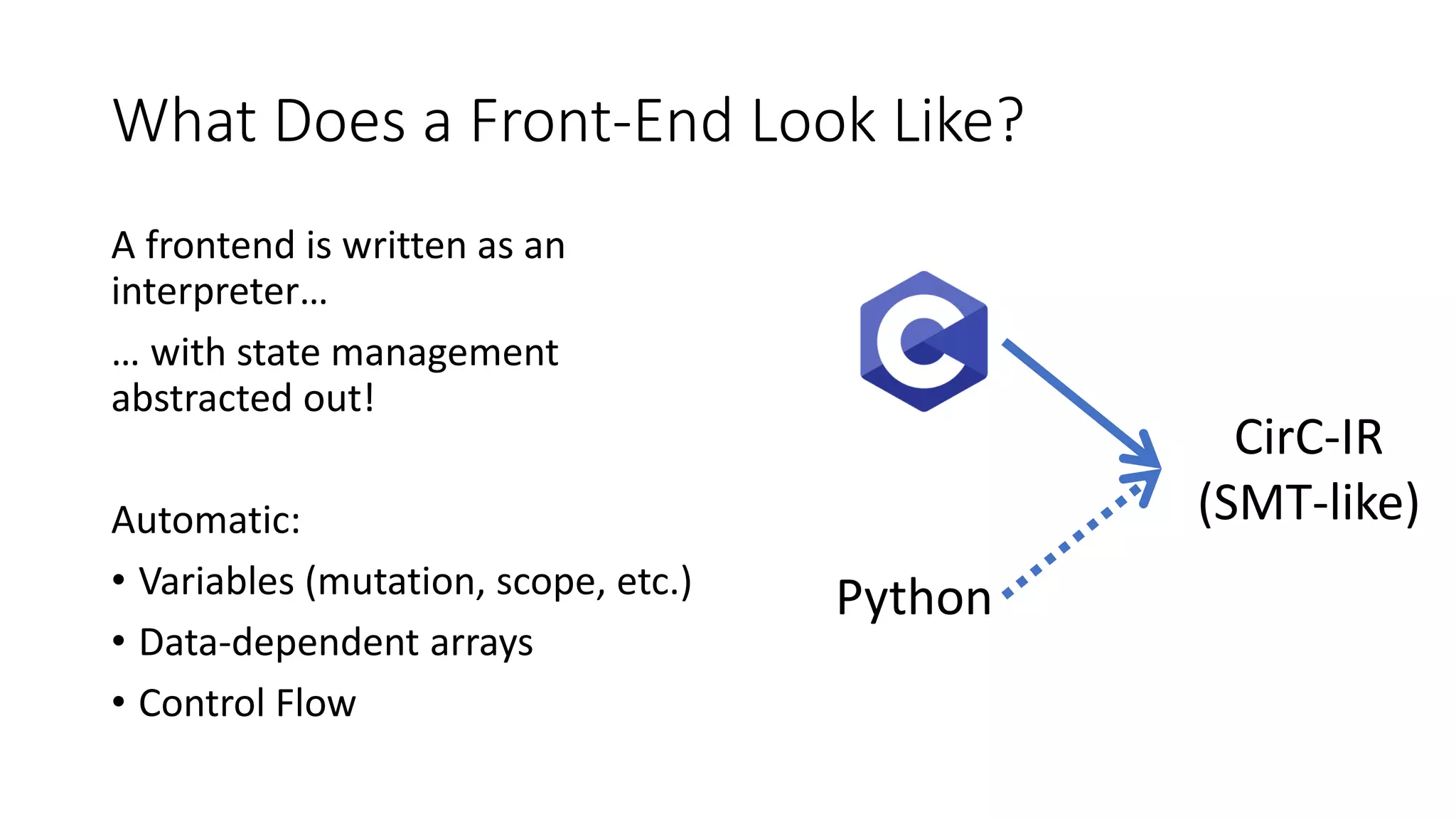
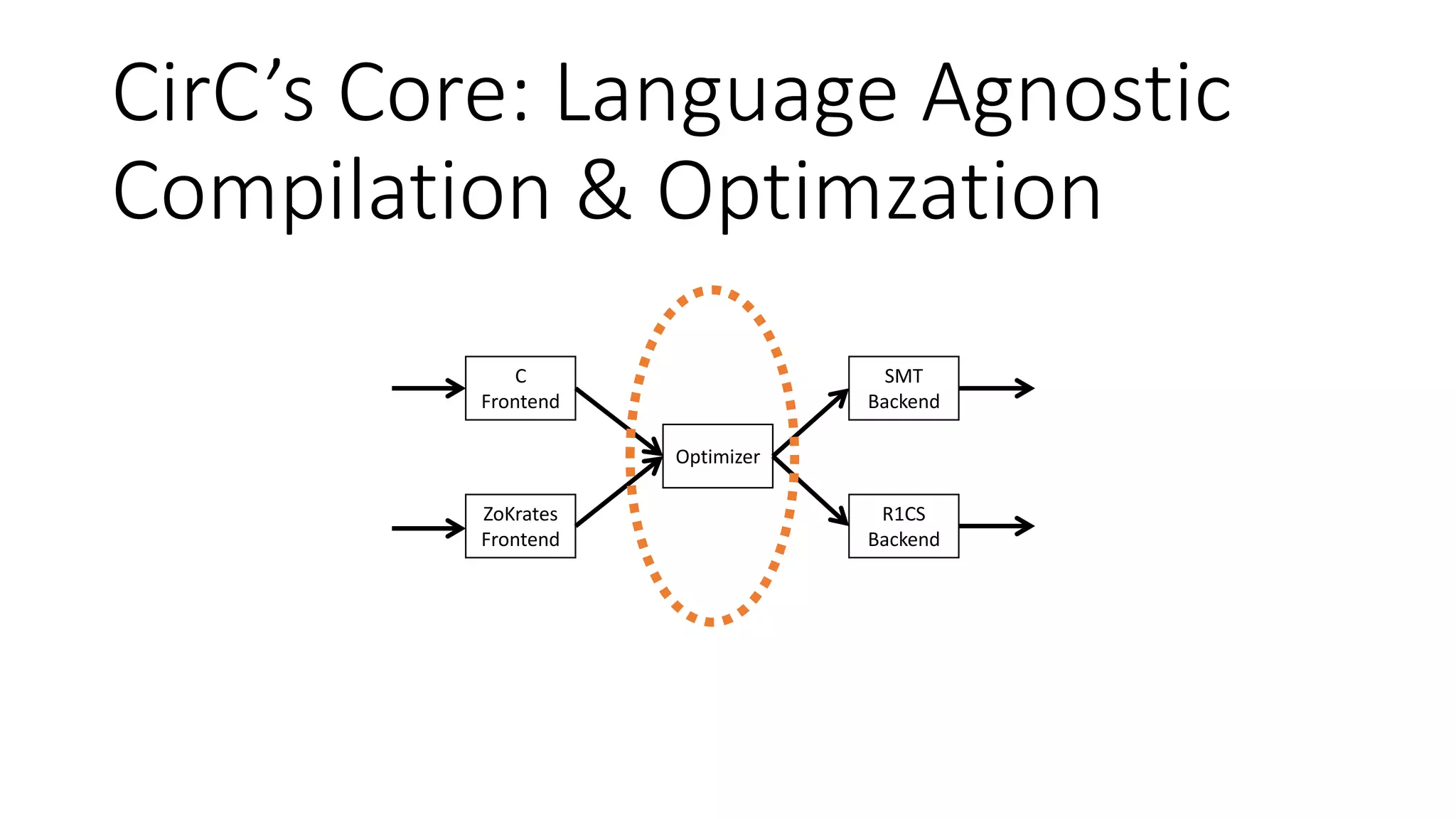
The document discusses a common compiler infrastructure designed for compiling programs into circuits, specifically focusing on zero-knowledge proofs and arithmetic constraints (R1CS). It highlights the benefits of using a shared optimization framework and presents case studies, such as Zokrates, demonstrating improved performance and extensibility. Future directions include expanding support for more programming languages and circuit types.
![Zero-Knowledge: Challenges
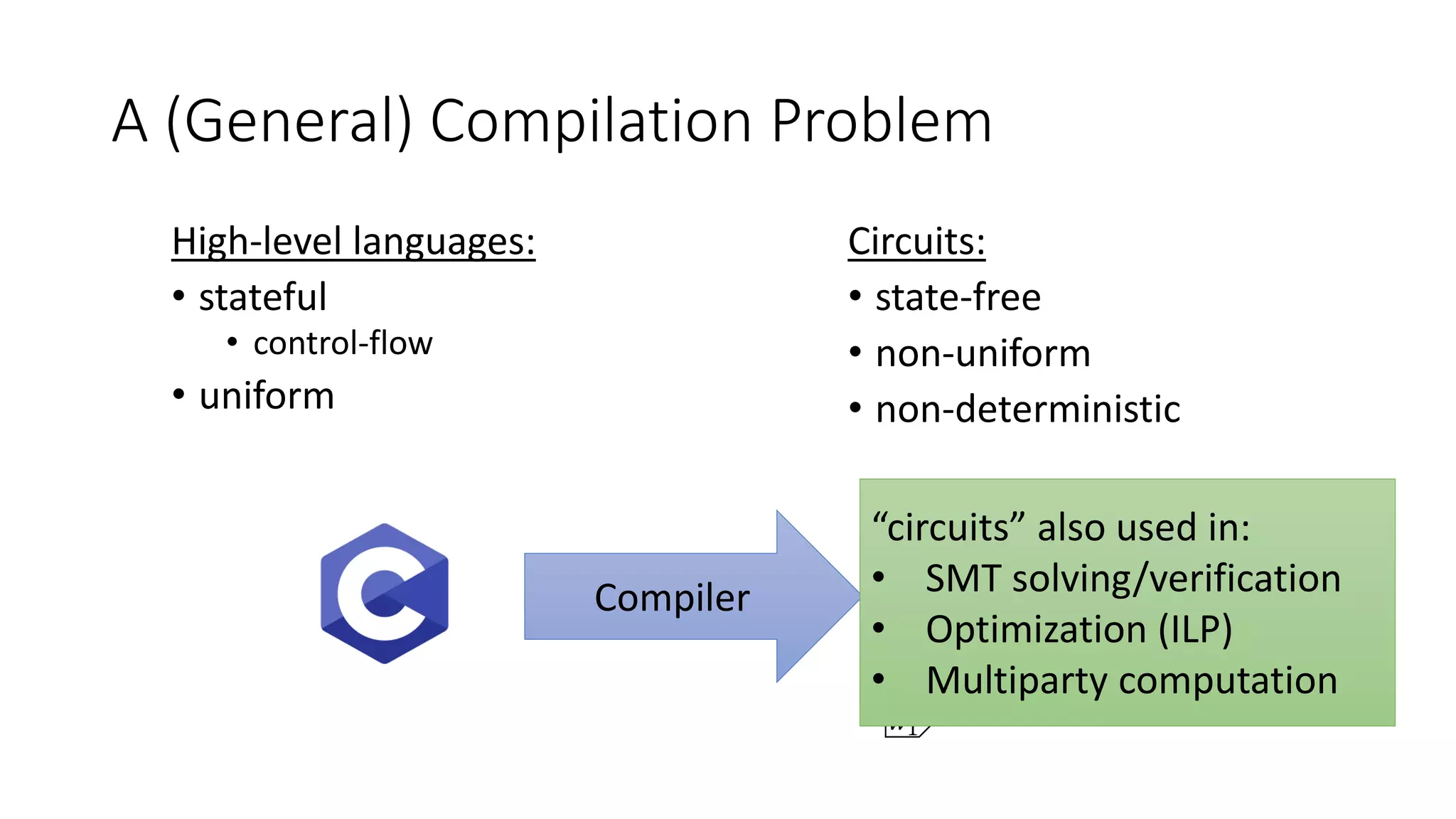
• For ZK-proofs, you need a system of arithmetic constraints (R1CS)
1. Need compilers from high level languages to R1CS with
• Small output (efficiency)
• Accurate output (correctness)
Pequin (C)
[SBVBPW’13]
[BFRSBW’13]
[WSRBW’15]
ZoKrates
[EbeTai’18]
Zinc
circom
xJSnark
[KosPapShi’18]
PySNARK (~py)
Leo
Snarky
Cairo
R1CS](https://image.slidesharecdn.com/circ-zkstudy-210213145332/75/zkStudyClub-CirC-and-Compiling-Programs-to-Circuits-4-2048.jpg)


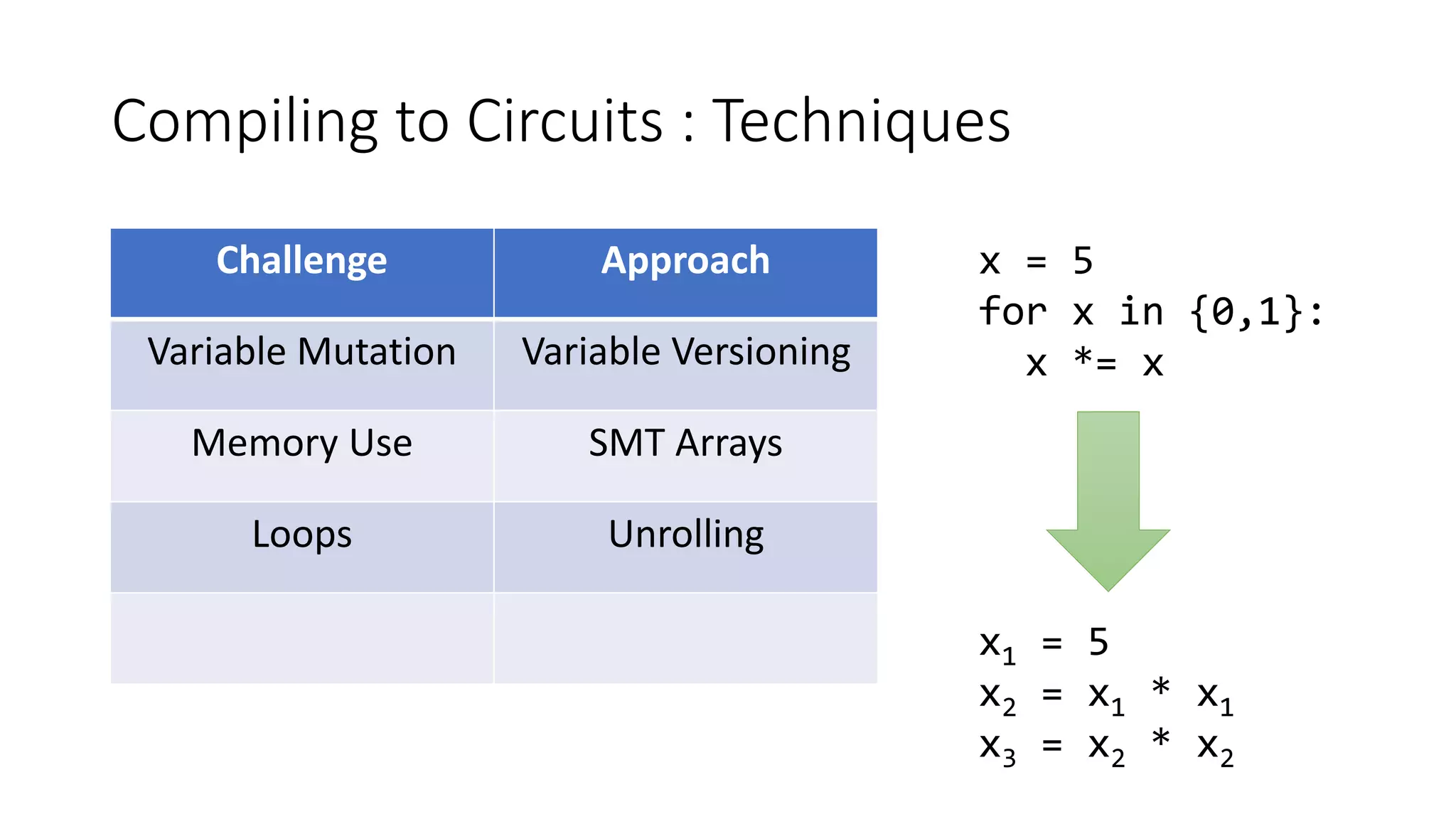
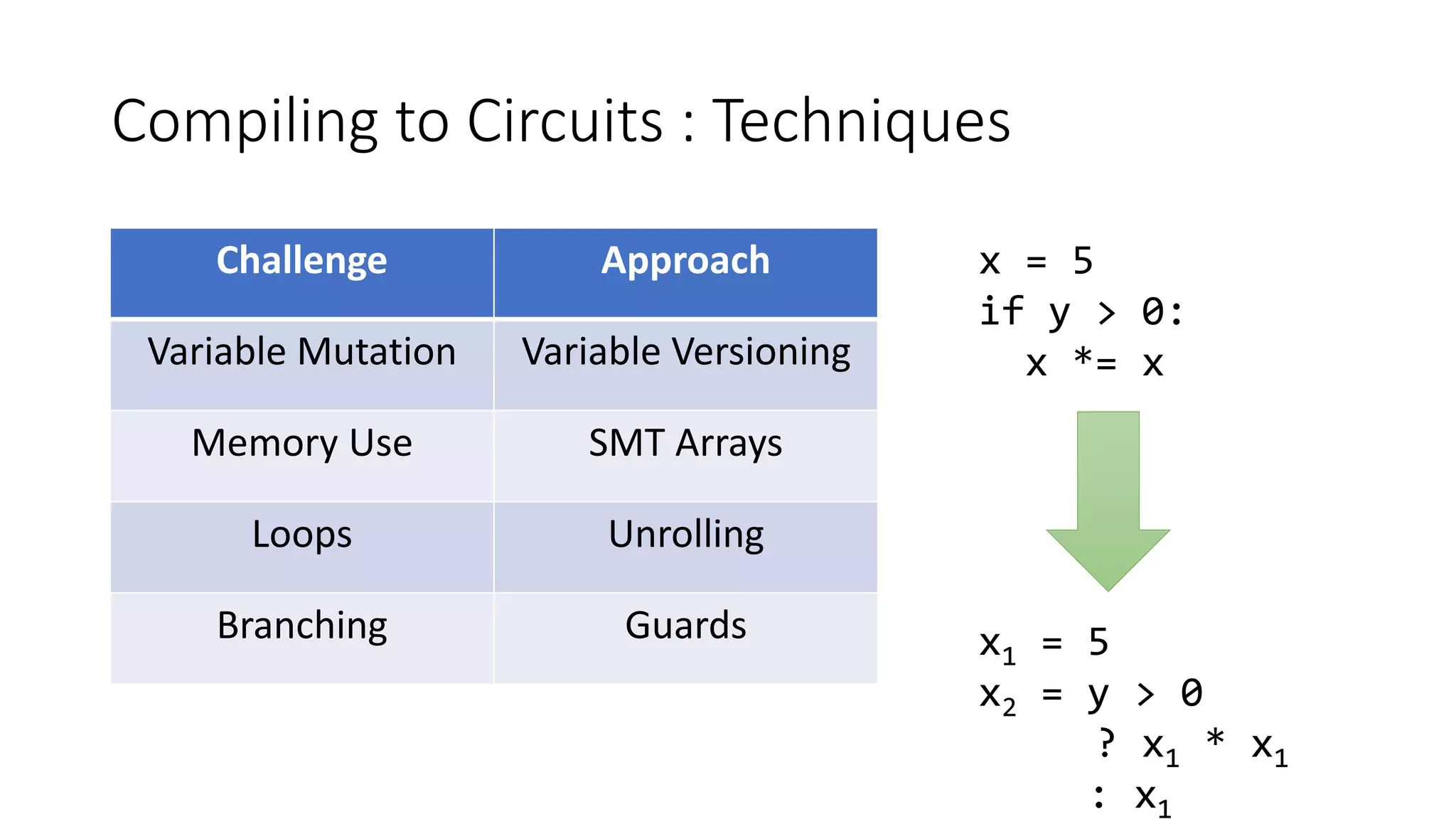
![Compiling to Circuits : Techniques
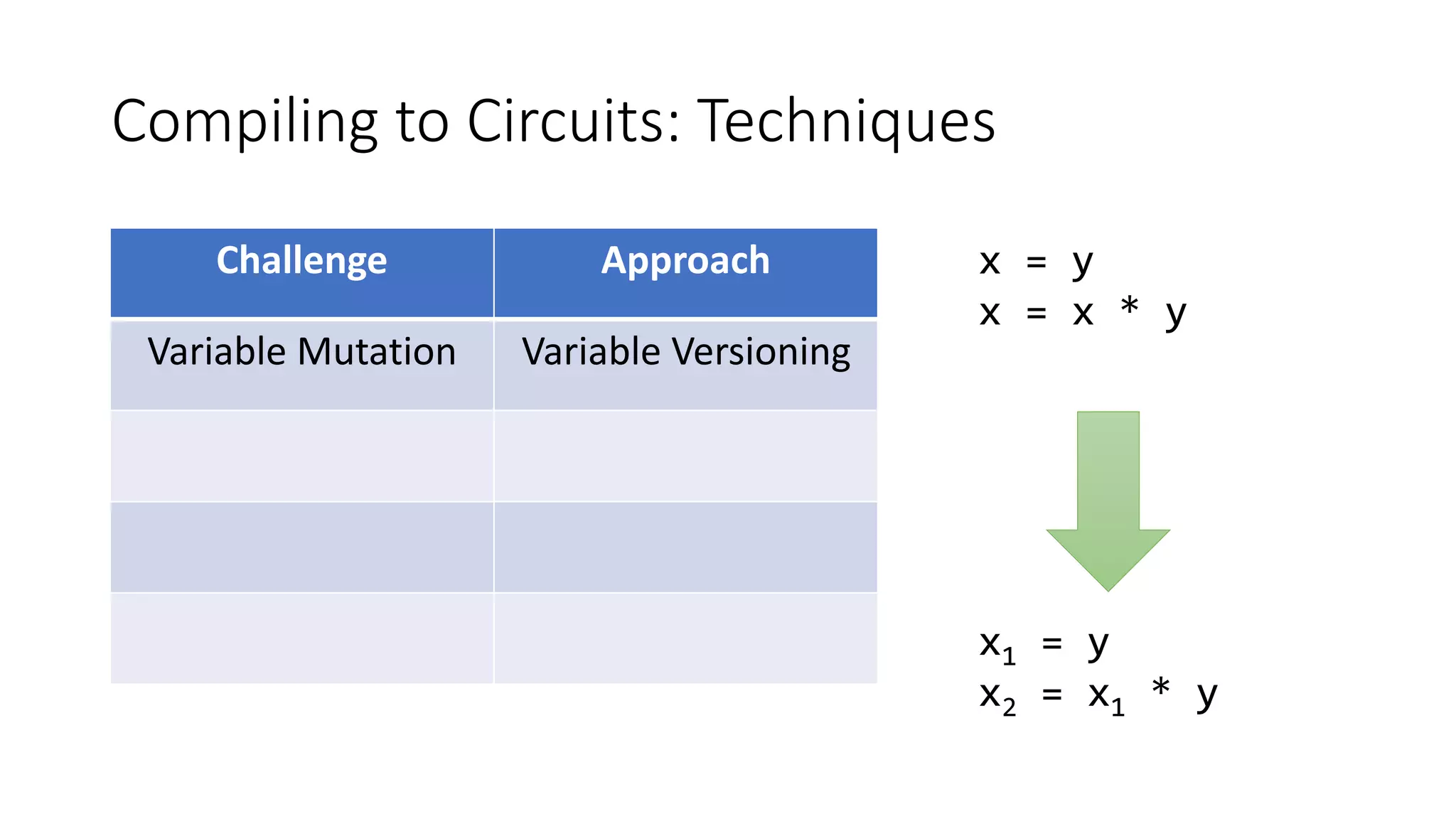
Challenge Approach
Variable Mutation Variable Versioning
Memory Use SMT Arrays
x[y] = z
x2 = x1[z @ y]](https://image.slidesharecdn.com/circ-zkstudy-210213145332/75/zkStudyClub-CirC-and-Compiling-Programs-to-Circuits-19-2048.jpg)
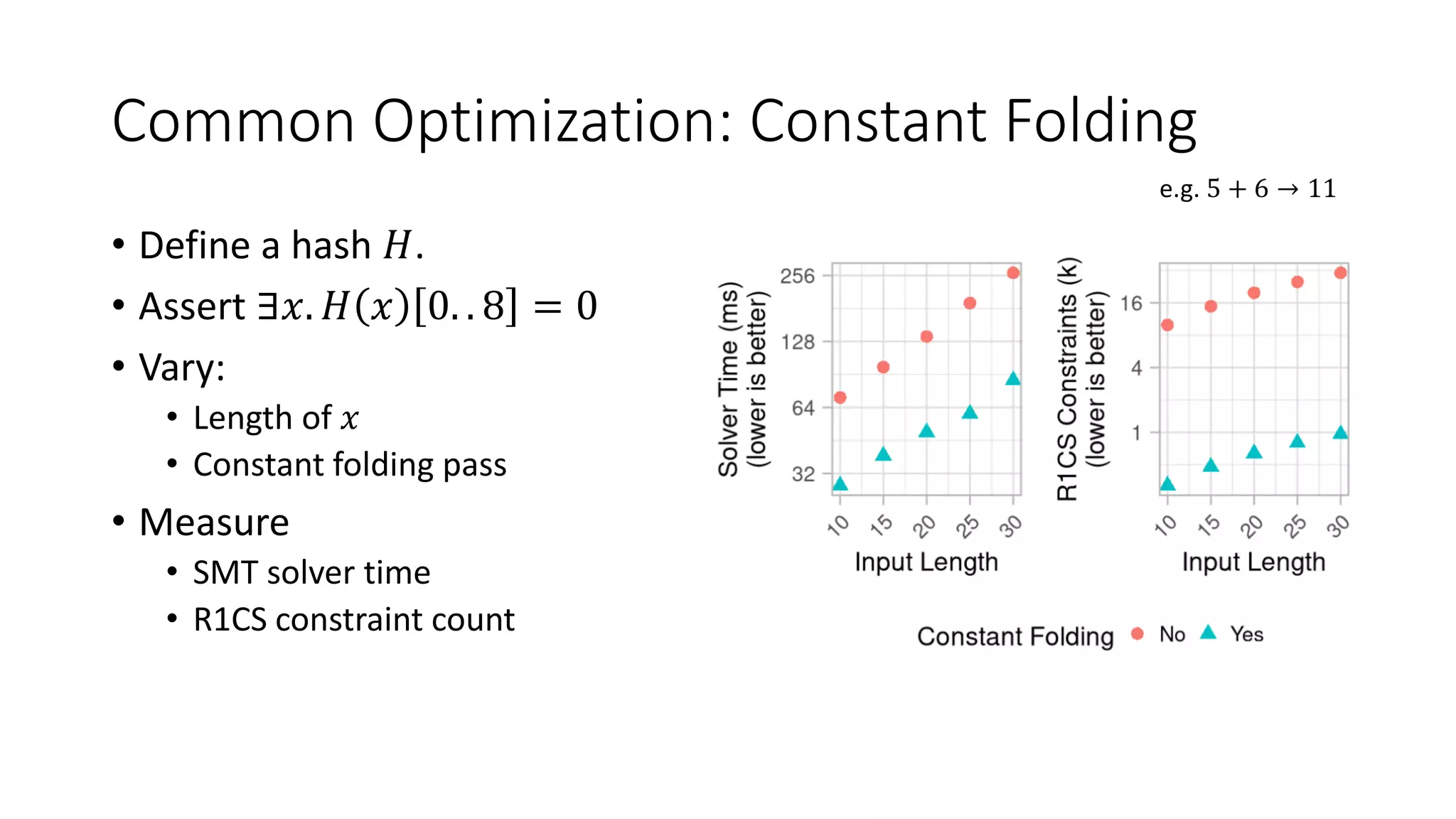
![Optimizations: Basic
• Constant folding
• 5 + 6 → 11
• 𝑥 ≪ 2 → 𝑥 2: ∥ [0,0]
• Operator flattening
• 𝑥 + 𝑦 + 𝑧 → 𝑥 + 𝑦 + 𝑧
• Substitution
• Peephole
• c & t | ~c & f ->
ITE(c,t,f)](https://image.slidesharecdn.com/circ-zkstudy-210213145332/75/zkStudyClub-CirC-and-Compiling-Programs-to-Circuits-22-2048.jpg)
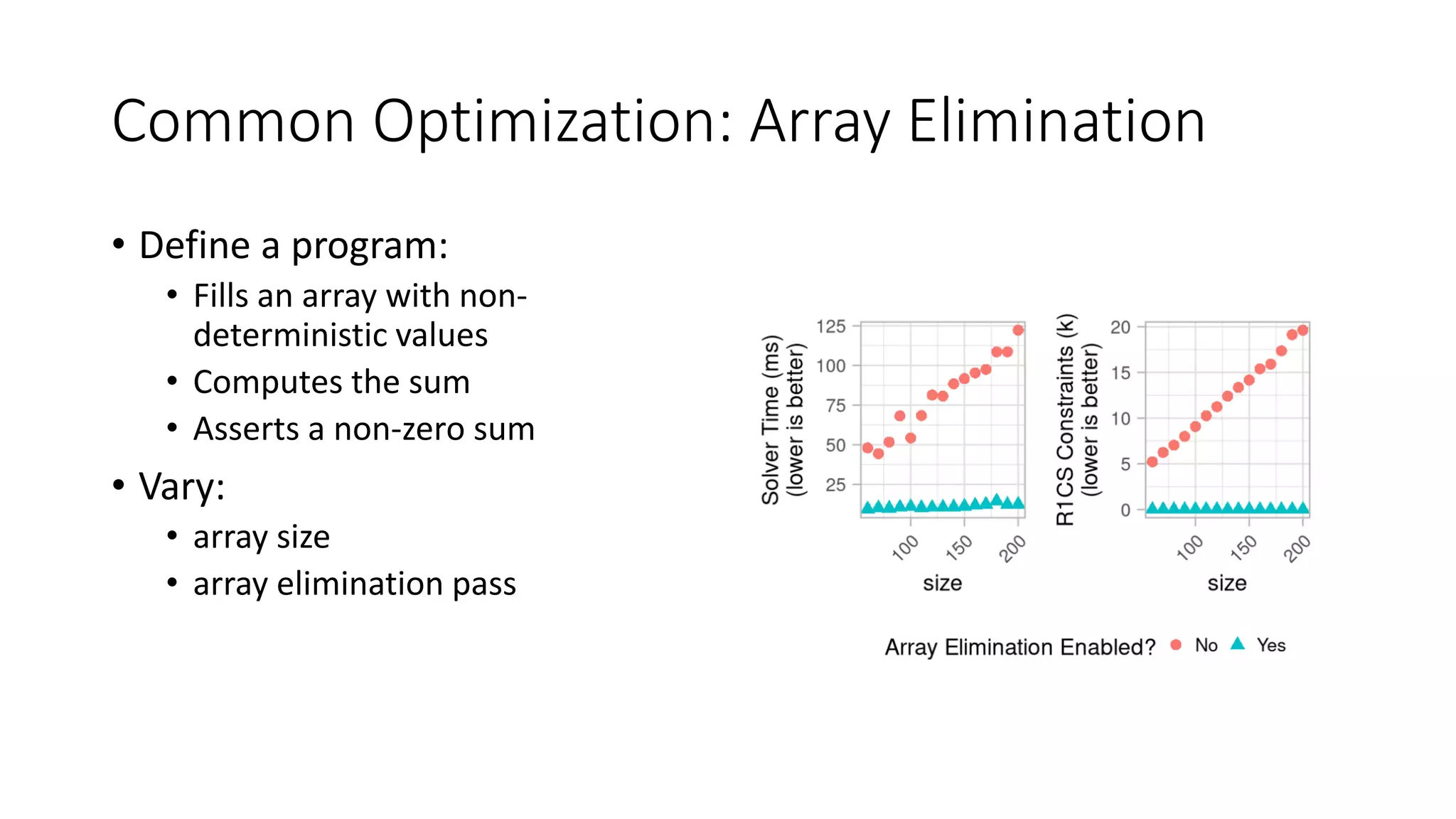
![Optimizations: Array Elimination
• Oblivious Arrays
• Arrays accessed at constant
indices
• Replaced with distinct terms
• Like scalar replacement
x = [y,z];
x[0] = x[1]+x[0];
y = x[0];
x01 = y1; x11 = z;
x02 = x01 + x11;
y2 = x02;](https://image.slidesharecdn.com/circ-zkstudy-210213145332/75/zkStudyClub-CirC-and-Compiling-Programs-to-Circuits-23-2048.jpg)
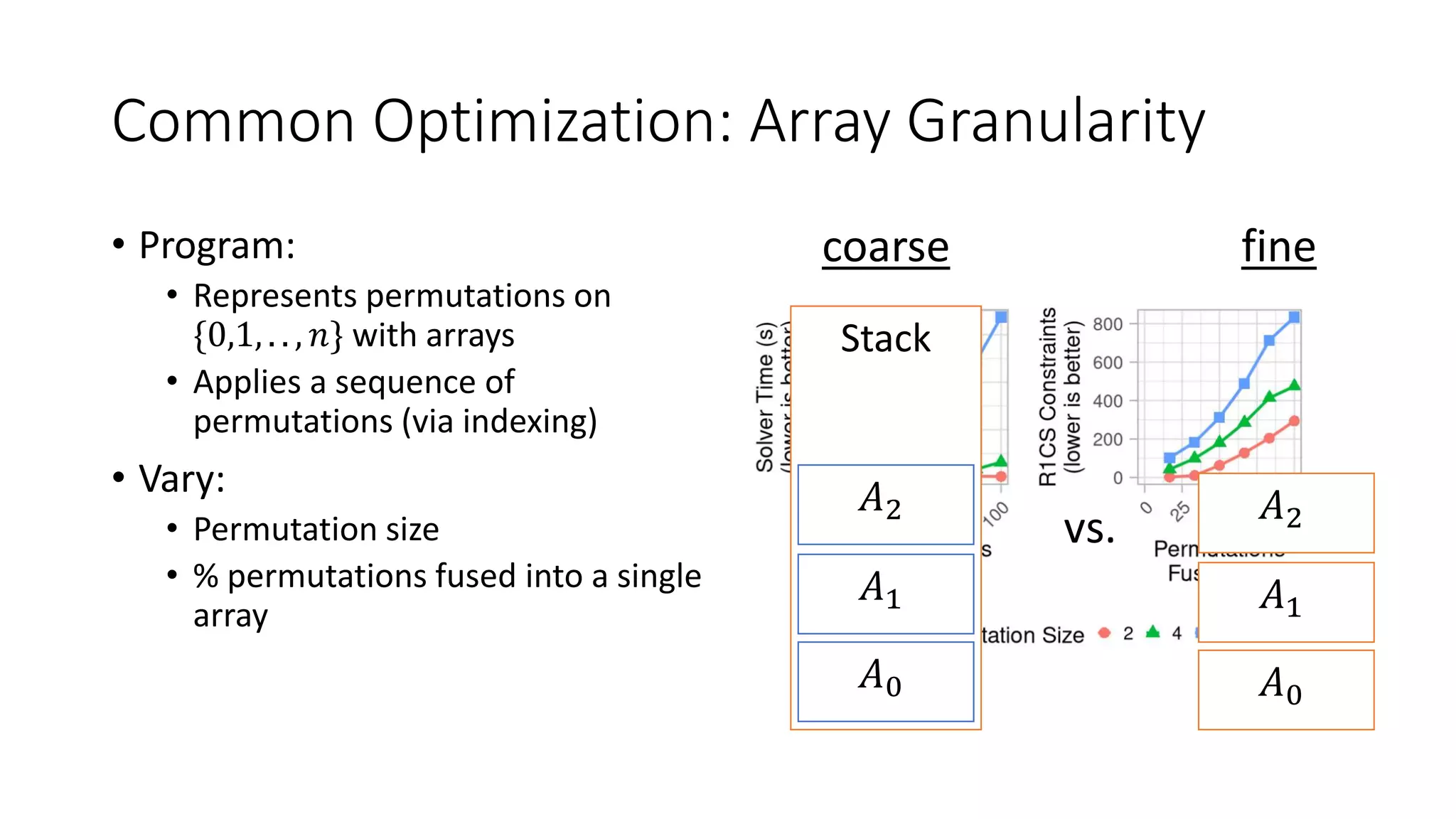
![Optimizations: Routing-Based Memory
• Replace memory operations (array encoded) with the following…
access 0 load addr val
access 1 load addr val
access 2 load addr val
access 3 load addr val
access 4 load addr val
Program Order
access id load addr val
access id load addr val
access id load addr val
access id load addr val
access id load addr val
Address Order
• Check
order
• Check read-
over-write
Waksman
routing network
(existential
switch settings)
[WSRBW’15] [BCTV’14] [BCGTV’13] [BEGKN’94]](https://image.slidesharecdn.com/circ-zkstudy-210213145332/75/zkStudyClub-CirC-and-Compiling-Programs-to-Circuits-24-2048.jpg)