Embed presentation
Downloaded 11 times





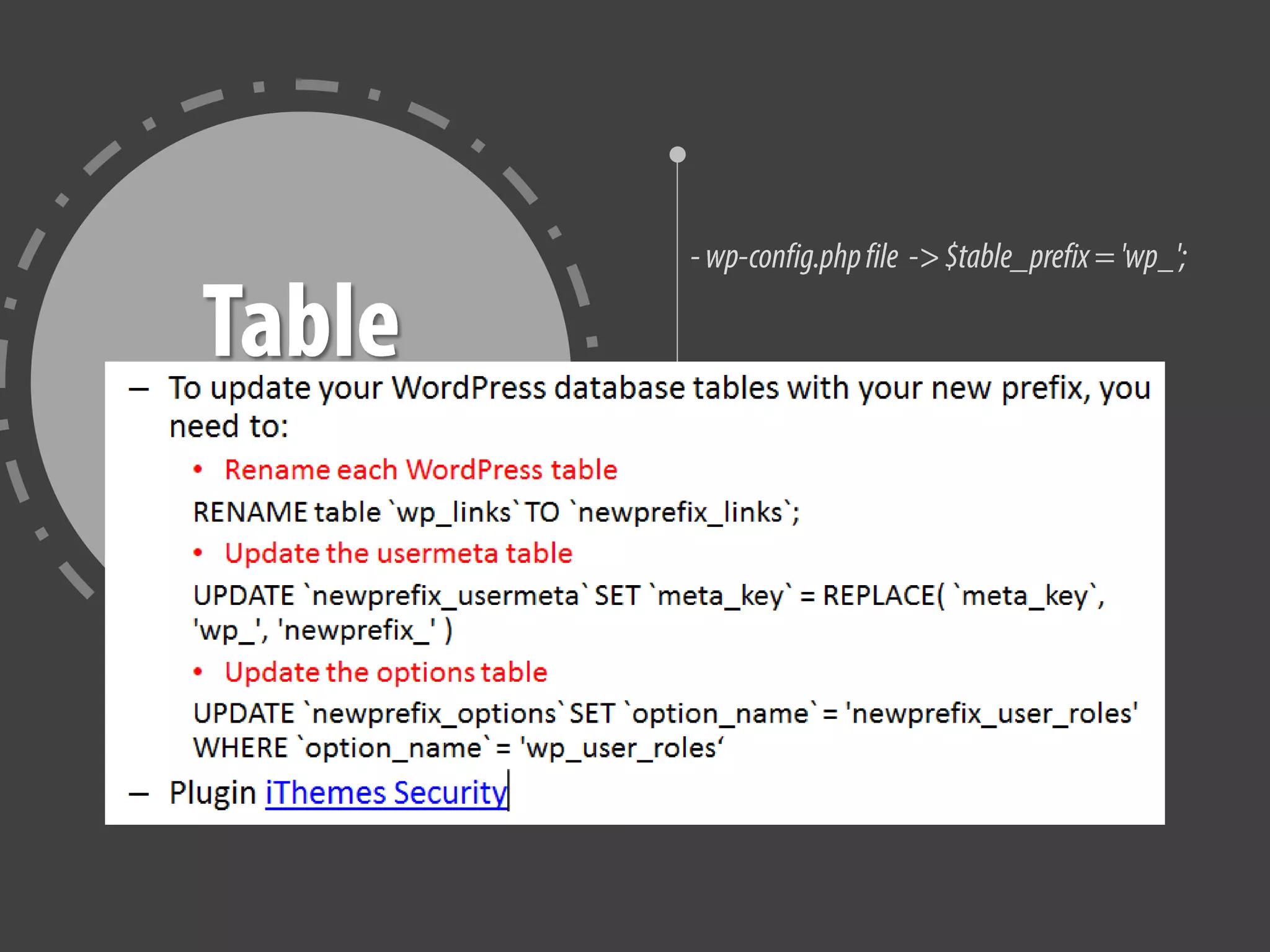




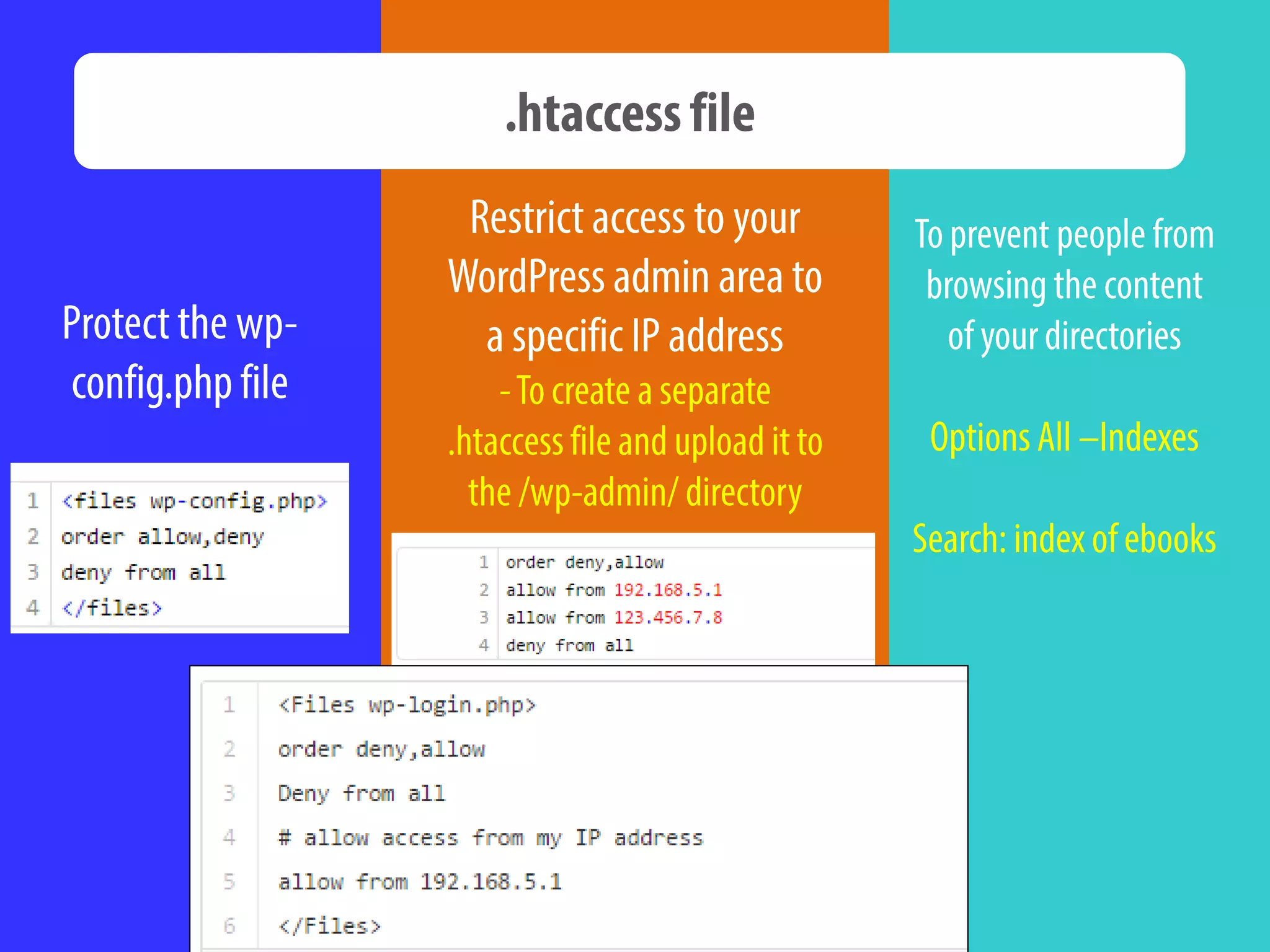




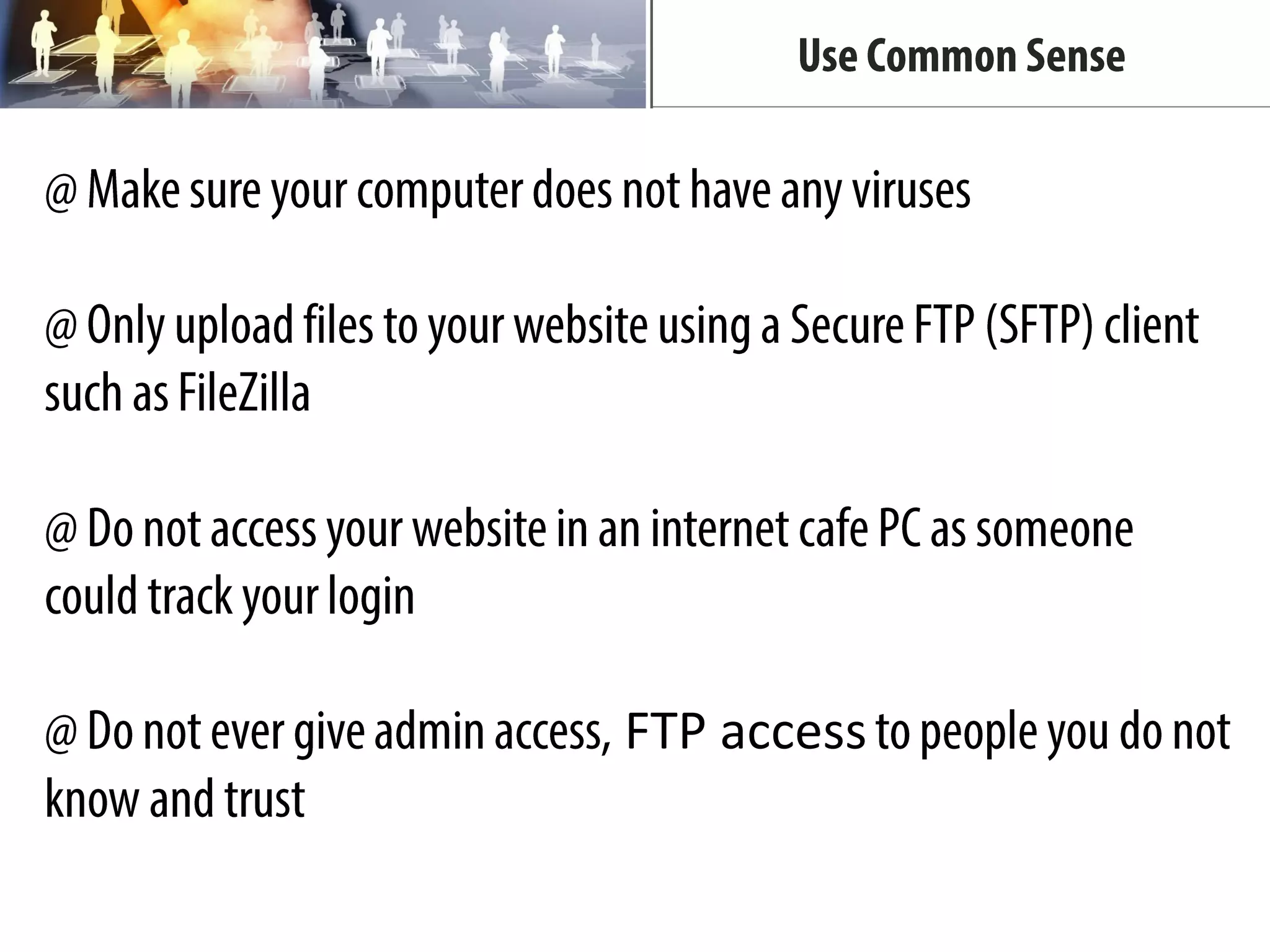
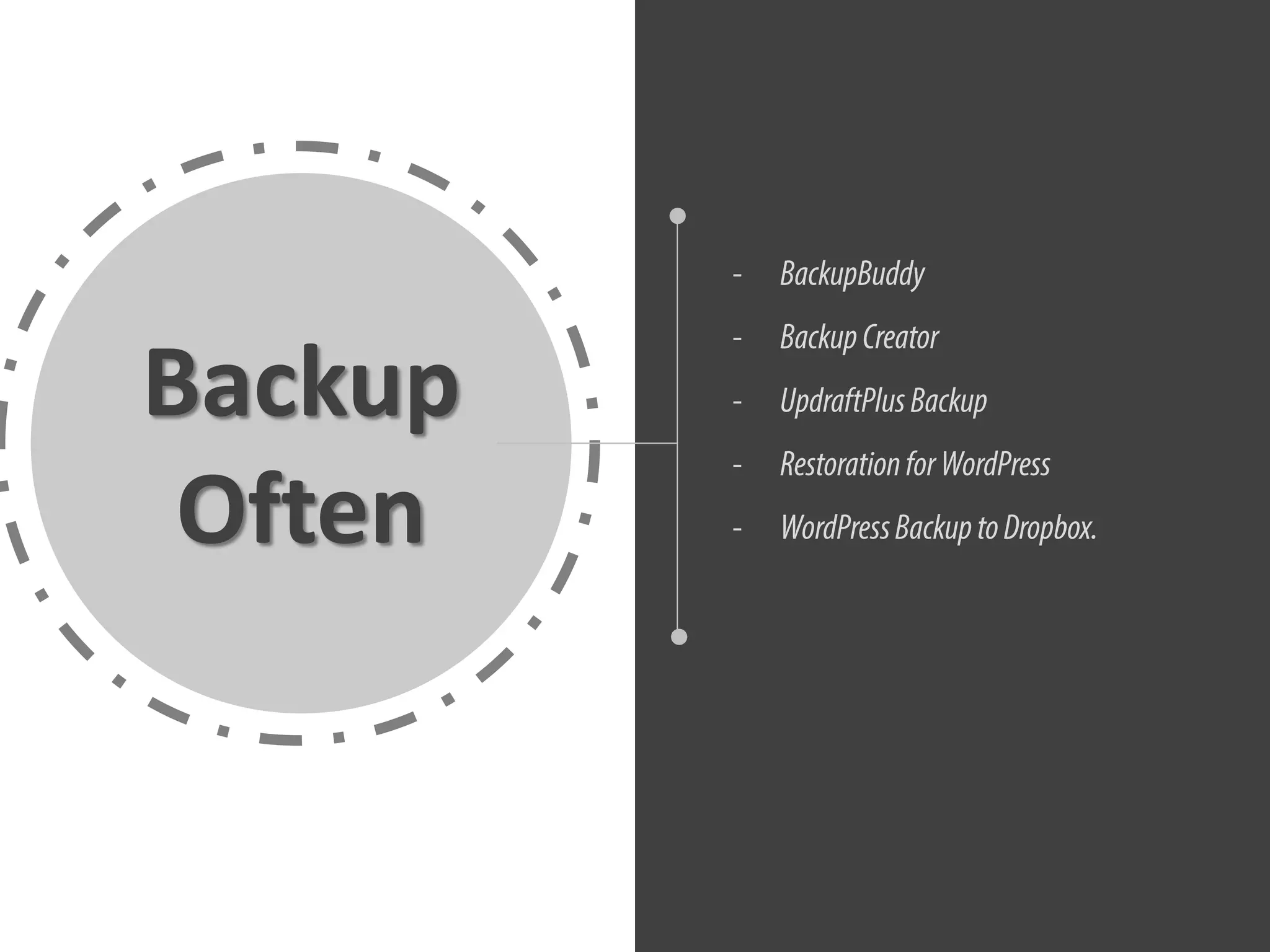




The document provides tips for improving WordPress website security, including deactivating and removing unused plugins to reduce vulnerabilities, only downloading themes and plugins from trusted sources, using regularly updated plugins and themes, changing file permissions, disabling error reporting, backing up the website often, and scanning the website for issues.



















