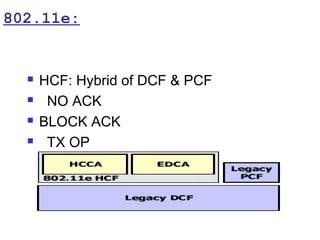
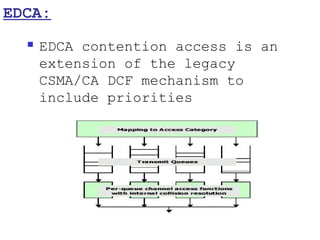
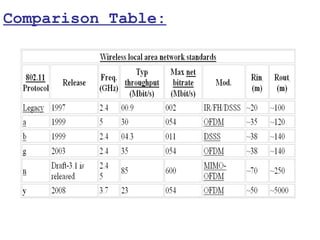
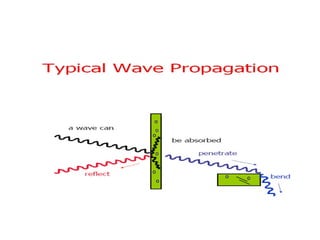
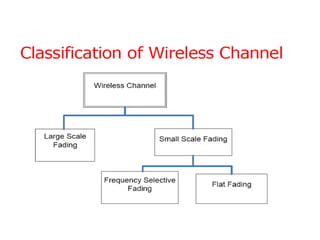
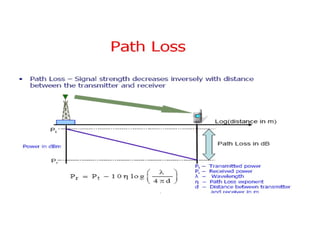
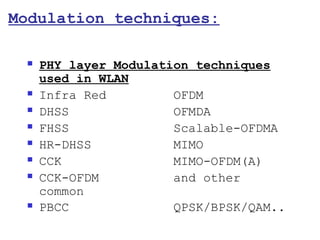
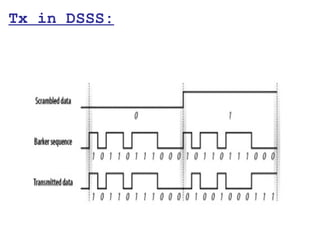
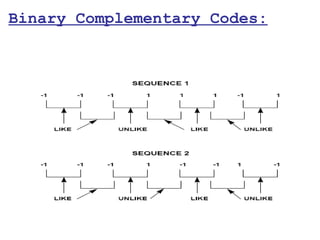
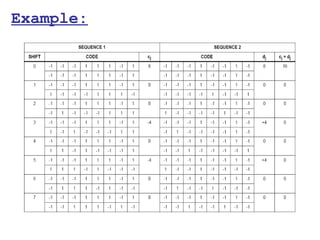
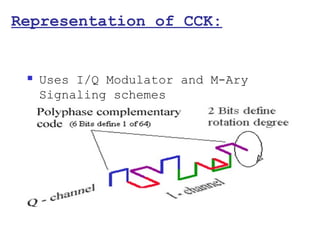
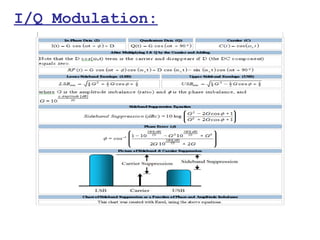
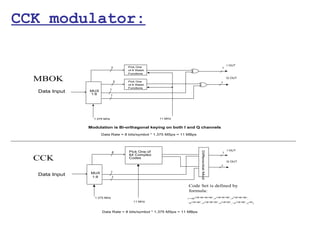
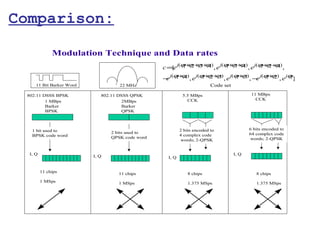
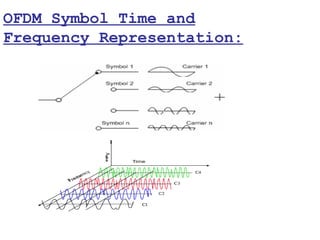
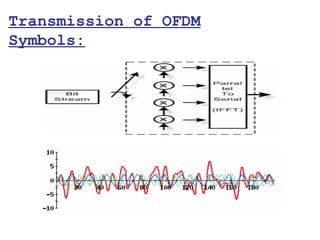
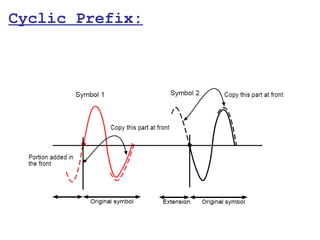
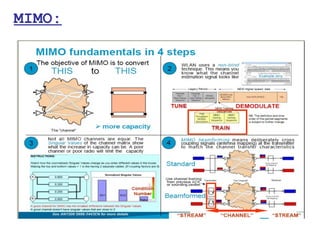
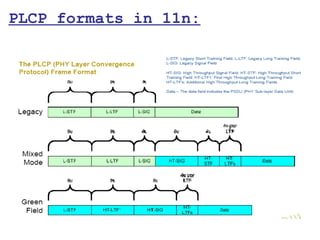
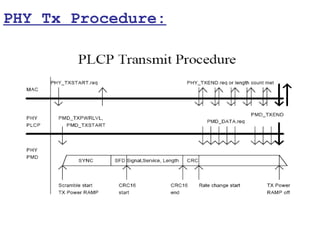
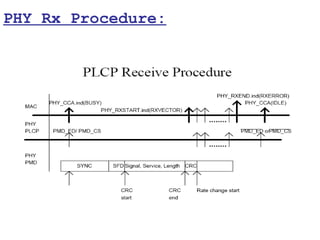
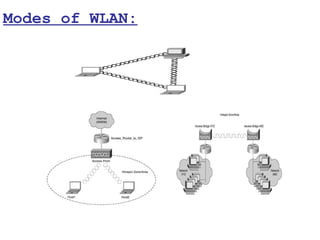
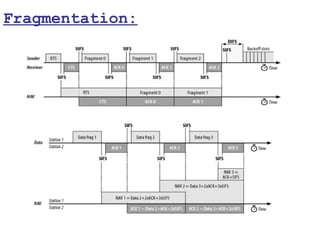
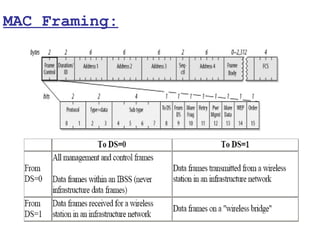
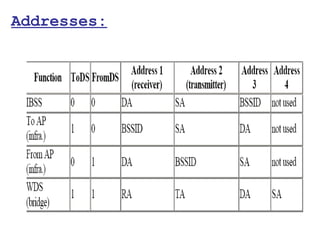
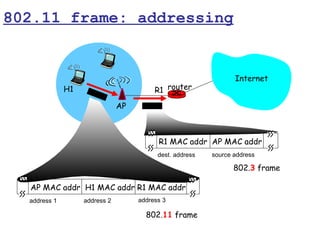
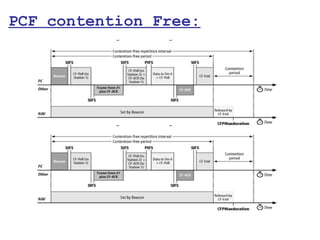
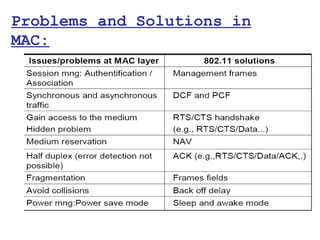
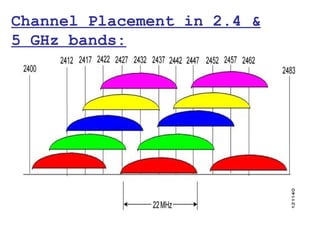
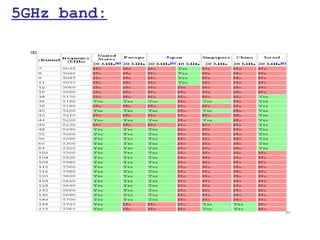
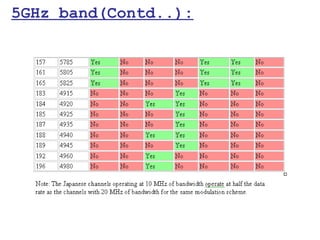
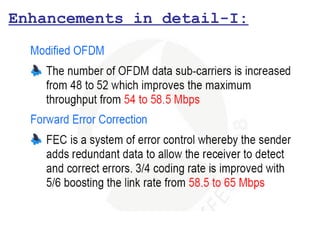
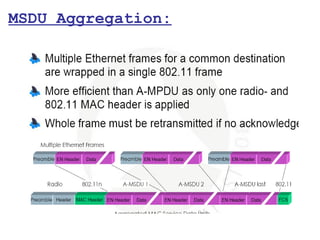
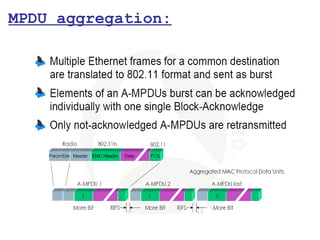
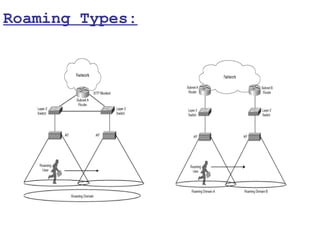
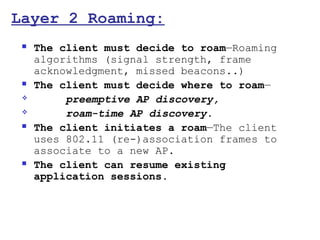
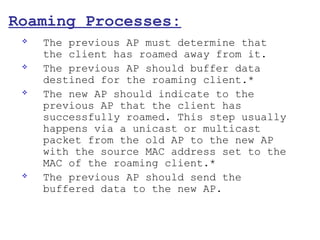
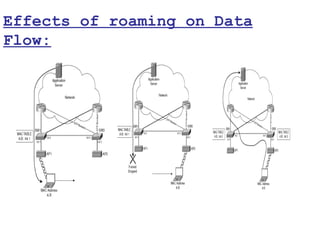
This document provides a comprehensive overview of 802.11 wireless LAN concepts, discussing the evolution of wireless standards, modulation techniques, and MAC layer functions. It details various wireless standards, including 802.11b/g/n, and explains the PHY and MAC layers in depth, including roaming and QoS. Key topics include wireless access methods, channel assessment, packet handling, and comparison of modulation techniques, aiming to enhance understanding of wireless network operation and efficiency.












































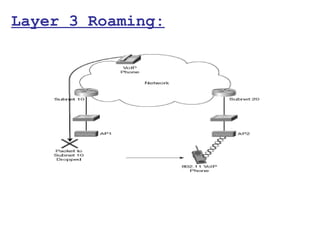




![ Upon determining it is on a
foreign subnet, the MN gleans the
CoA from the agent advertisement.
The CoA can take two forms:
The address of the FA.
CCoA (Note that the CCoA is not
advertised by the FA, but it is
probably acquired by the MN as a
Dynamic Host Configuration
Protocol [DHCP] option.)](https://image.slidesharecdn.com/wirelessconceptstk-130213005924-phpapp02/85/Wireless-LAN-WLAN-concepts-Modulation-to-Aggregation-117-320.jpg)