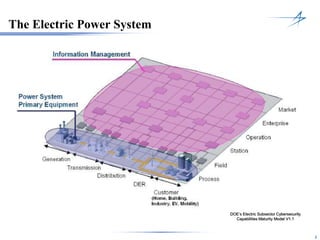
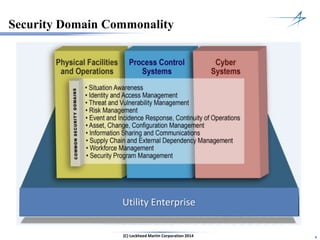
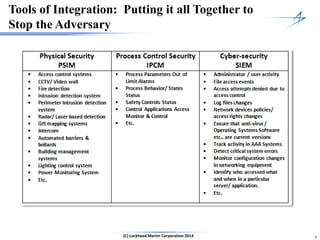
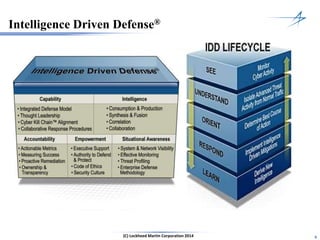
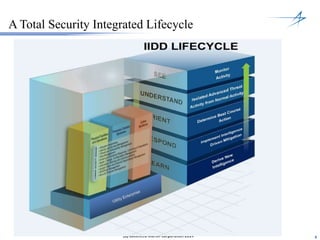
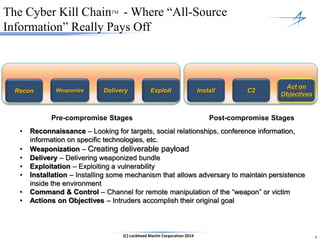
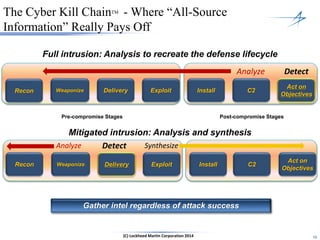
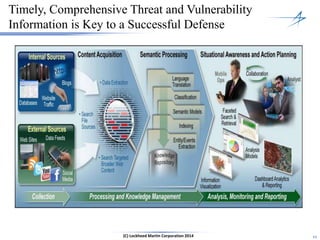
The document discusses the integration of cybersecurity within the energy and utilities industry, highlighting the rising threats and incidents reported in 2013. It outlines a comprehensive security approach that includes advanced threat detection and the importance of timely, comprehensive threat information. The proposed solution emphasizes a managed, stepwise integration of security processes to enhance overall resilience against cyber adversaries.
![1
Bill Lawrence, Ph.D. Commercial Cyber Security Services, Lockheed Martin
(C) Lockheed Martin Corporation 2014© Lockheed Martin Corporation. All Rights Reserved.
This document [or software] shall not be reproduced, modified, distributed or displayed without
the prior written consent of the Lockheed Martin Corporation
Closing the Gap between Physical, Process Control, and
Cybersecurity for the Energy and Utilities Industry](https://image.slidesharecdn.com/williamlawrence-lockheedmartinid-140823103736-phpapp01/75/An-Approach-to-Closing-the-Gaps-between-Physical-Process-Control-and-Cybersecurity-for-the-Energy-and-Utilities-Industry-1-2048.jpg)