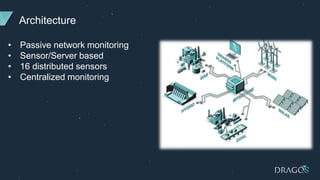
This document discusses how a mid-sized US electric utility implemented the Dragos cybersecurity platform to improve the visibility of its operational technology (OT) assets and threats, enhance compliance functions, and better support its limited OT security team. The Dragos solution included passive network monitoring sensors, asset characterization, and threat intelligence reporting. It helped the utility address compliance requirements, leverage Dragos' expertise through training and assistance, and improve its detection of OT threats through behavioral analytics and investigation playbooks. The solution demonstrated that combining technology with personnel support can effectively address common industrial control system security challenges faced by electric utilities.