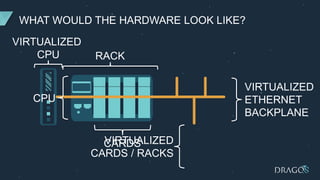
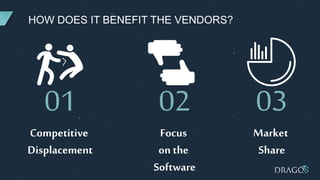
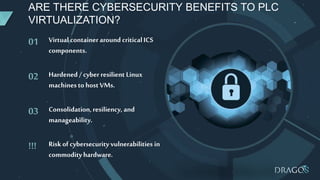
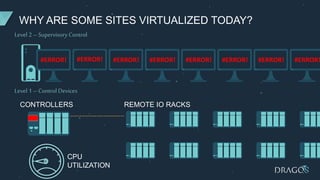
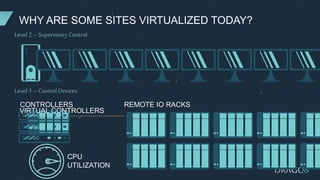
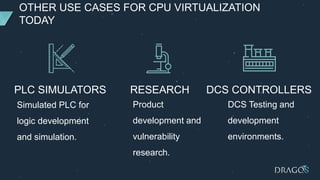
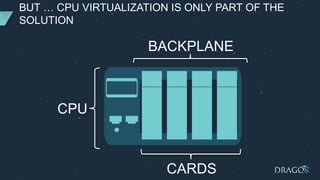
The document discusses PLC virtualization, defining it as a method to abstract technology layers to improve cost, flexibility, and support while addressing cybersecurity vulnerabilities. It highlights the essential attributes of PLCs that contribute to their reliability and proposes various virtualization use cases in operational technology environments. Additionally, it considers the implications for automation vendors, including competitive displacement and market share focus.





![LATENCY TOLERANCE
IT virtualization (x86) is
designed for general-
purpose workloads where
throughput takes priority
over latency.
In OT,anydeviationfromthe required
latencywill causea processtrip.
250 µs 280 µs
800 µs
Motion Control
[1]
Electrical Control
[2]
Process Control
[3]
ESTIMATED PLC BACKPLANE
LATENCY TOLERANCE
[1] C. E. Pereira and P. Neumann, Industrial Communication Protocols, S. Y. Nof, Ed. Heidelberg, Germany: Springer-Verlag, 2009.
[2] L. Kean, “Microcontroller to Intel architecture conversion: PLC using Intel atom processor,” Intel Corp., Santa Clara, CA, USA, White
Paper, 2010.
[3] S. Balacco and C. Lanfear, “The embedded software strategic market intelligence program 2002/2003 vol. I: Embedded systems market
statistics,” Venture Develop. Corp., Mill Valley, CA, USA, Tech. Rep., 2003.](https://image.slidesharecdn.com/plcvirtualizationdragoss42019feb-190208073301/85/PLC-Virtualization-Dragos-S4-2019-11-320.jpg)
![CAN WE ACHIEVE THE REQUIRED LATENCY IN A
REALTIME VM?
[1] Tiago Cruz, Paulo Simões, and Edmundo Monteiro “Virtualizing Programmable Logic Controllers: Toward a Convergent Approach” - IEEE EMBEDDED SYSTEMS LETTERS, VOL. 8,
NO. 4, DECEMBER 2016
(Gigahertz)](https://image.slidesharecdn.com/plcvirtualizationdragoss42019feb-190208073301/85/PLC-Virtualization-Dragos-S4-2019-12-320.jpg)