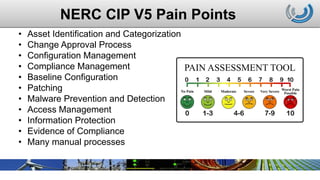
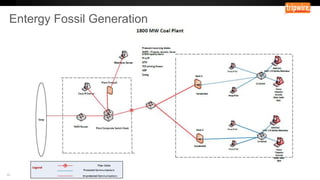
The document details a panel discussion on the challenges and lessons learned regarding NERC CIP v5 compliance and configuration change management. Key pain points include asset identification, change approval processes, and compliance management, along with the need for thorough documentation and security controls. The discussion emphasizes transitioning from manual processes to automated systems for improved compliance and cybersecurity.