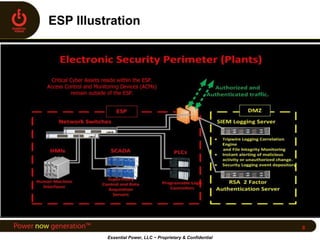
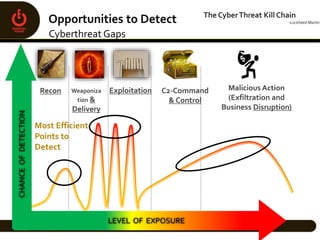
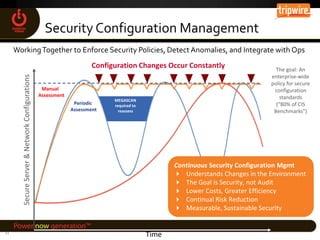
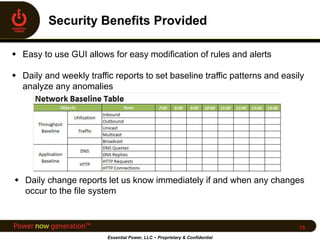
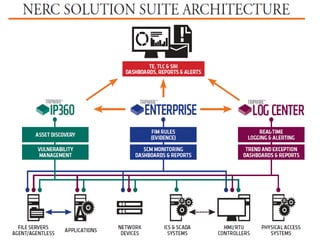
Essential Power, LLC, founded in 2008 and headquartered in Princeton, NJ, operates five generation facilities with a total capacity of over 2,000 megawatts, primarily using natural gas. The company faced significant cybersecurity challenges during the implementation of Critical Infrastructure Protection (CIP) regulations, necessitating retrofits and the adoption of a Security Information and Event Management (SIEM) system for log management and monitoring. To prepare for CIP version 5, Essential Power is updating documentation, conducting gap analyses, and leveraging enhanced vendor support and technologies to bolster their cybersecurity posture.