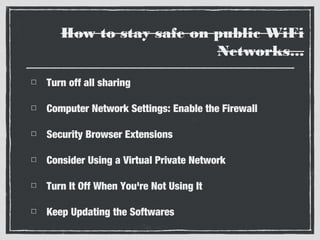
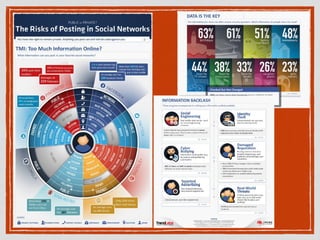
This document discusses wireless network security and social networks. It begins by describing different types of wireless networks like personal area networks and wireless local area networks. It then notes that the weakest point of wireless networks is their vulnerability since the information is transmitted over unprotected airwaves and mobile devices can be lost or stolen. The document outlines some basic security concepts for wireless communication like privacy, authentication, integrity, availability and access control. It provides examples of security threats on social networks and public WiFi networks. It concludes by emphasizing the integration of different wireless approaches and the need for security concepts like privacy and authentication on wireless networks.