The document addresses selective jamming attacks in wireless networks, where adversaries can disrupt critical communications by classifying and jamming important packets. It proposes four cryptographic schemes to mitigate these attacks, including the All Or Nothing Transformation-Hiding Scheme, Strong Hiding Commitment Scheme, Puzzle-Based Hiding Scheme, and Nonce-Based Authenticated Encryption Scheme. The proposed methods aim to combine physical layer attributes with cryptography to protect wireless communications from highly targeted jamming efforts.


![N. Vasumathi et al Int. Journal of Engineering Research and Applications www.ijera.com
ISSN : 2248-9622, Vol. 4, Issue 3( Version 2), March 2014, pp.15-19
www.ijera.com 19 | P a g e
3.5.1Security of the scheme
Intuitively, it is easy to see that, if MAC tree
construction is not used, and instead manage all of the
leaf counters Nk
(0)
in the trusted storage, then this
scheme guarantees both confidentiality and integrity
of the file content: all the block counters Nk
(0)
are
properly incremented, and no nonce is repeated, and
each file blocks are encrypted and authenticated
independent from each other. Essentially, the
confidentiality and the integrity of the resulting
scheme come from the security of the composite
authenticated encryption scheme, and the nonce-
respecting property. In this scheme, instead of
managing the leaf counters in the trusted storage, they
are stored in MAC tree and store only the root
counter in the trusted storage. Still, from the way the
MAC tree is constructed, the trust of the root counter
can be transferred to its descendants, as long as all of
the tag verifications along the path are successful. In
this way, it is ensured that our MAC tree construction
can safely replace counters stored in a trusted storage,
except negligible probability of successful attack.
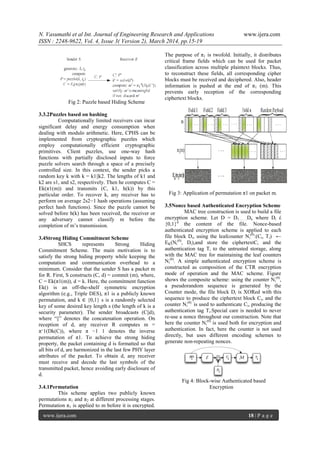
IV. System Design
Fig 5: Architecture for preventing real time packet
classification
V. Conclusion
The problem of selective jamming attacks in
wireless networks is addressed in this work. In these
attacks, the adversary is active only for certain period
of time, specifically targeting messages of high
importance. The advantages of selective jamming in
terms of network performance degradation and
adversary effort is illustrated. An internal adversary
model is considered, where the jammer is one of the
parts of the network under attack, thus it is aware of
the protocol specifications and shared network secrets.
The selective jammer can significantly impact
performance with very low effort. The selective
jamming attacks can be launched by performing real-
time packet classification at the physical layer. To
avoid these attacks, four schemes are developed such
as All Or Nothing Transformation-Hiding Scheme
(AONT-HS) - pseudo message is added with message
before transformation and encryption, Strong Hiding
Commitment Scheme(SHCS) - off-the-shelf
symmetric encryption is done, Puzzle Based Hiding
Scheme(PBHS)- using time lock and hash puzzles
and Nonce based Authenticated Encryption
Scheme(N-AES)-Nonce is used for encryption, that
prevent real-time packet classification by combining
cryptographic primitives with physical-layer
attributes.
VI. Future Work
To improve the efficiency of these schemes
in terms of time by using cryptography based
algorithms which consumes less time and provides
more security.
References
[1] T. X.Brown,J. E.James and
A.Sethi,―Jamming and sensing of encrypted
wireless ad hoc networks‖. In Proceedings
of MobiHoc, pages 120–130, 2006.
[2] M.Cagalj, S.Capkun, and J.-P. Hubaux,
‖Wormhole-based anti-jamming techniques
in sensor networks‖ .IEEE Transactions on
Mobile Computing, 6(1):100–114, 2007.
[3] A.Chan, X.Liu, G.Noubir and
B.Thapa.―Control channel jamming:
Resilience and identification of traitors‖. In
Proceedings of ISIT, 2007.
[4] T. Dempsey, G. Sahin, Y. Morton, and C.
Hopper.‖Intelligent sensing and
classification in ad hoc networks: a case
study‖. Aerospace and Electronic Systems
Magazine, IEEE, 24(8):23–30, August 2009.
[5] Y.Desmedt,― Broadcast anti-jamming
systems‖. Computer Networks,35(2-3):223–
236, February 2001.
[6] K. Gaj, P. Chodowiec, FPGA and ASIC
implementations of AES.‖Cryptographic
Engineering‖,pages 235–294, 2009.
[7] R. Rivest. ―All-or-nothing encryption and
the package transform‖. Lecture Notes in
Computer Science, pages 210–218, 1997.
[8] R. Rivest, A. Shamir, and D. Wagner.
―Time-lock puzzles and timed release
crypto‖. Massachusetts Institute of
Technology, 1996
[9] B. Schneier.‖Appliedcryptography:
protocols, algorithms, and source code in
C‖.John Wiley & Sons, 2007.](https://image.slidesharecdn.com/d43021519-140419004850-phpapp01/85/D43021519-5-320.jpg)