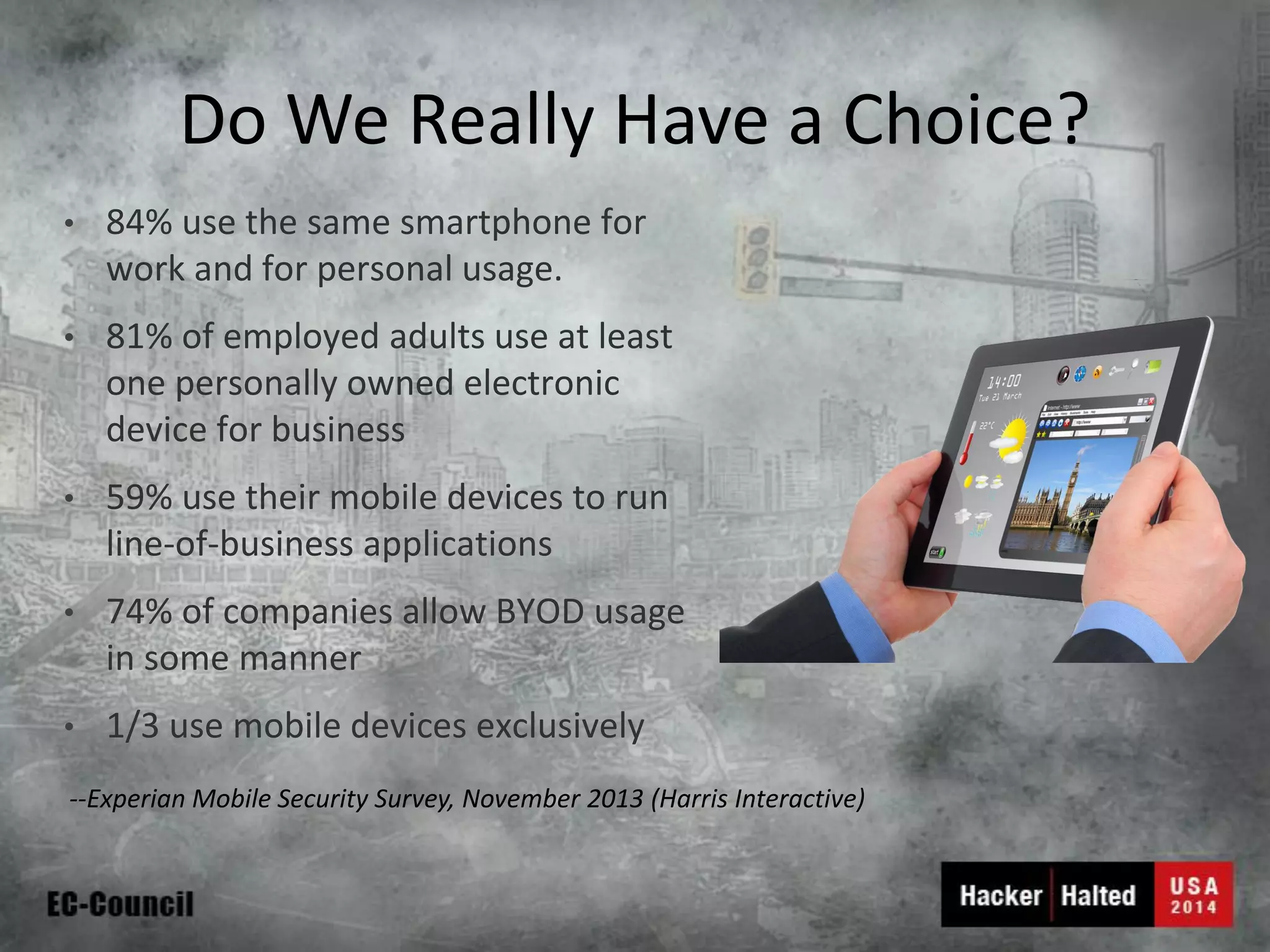
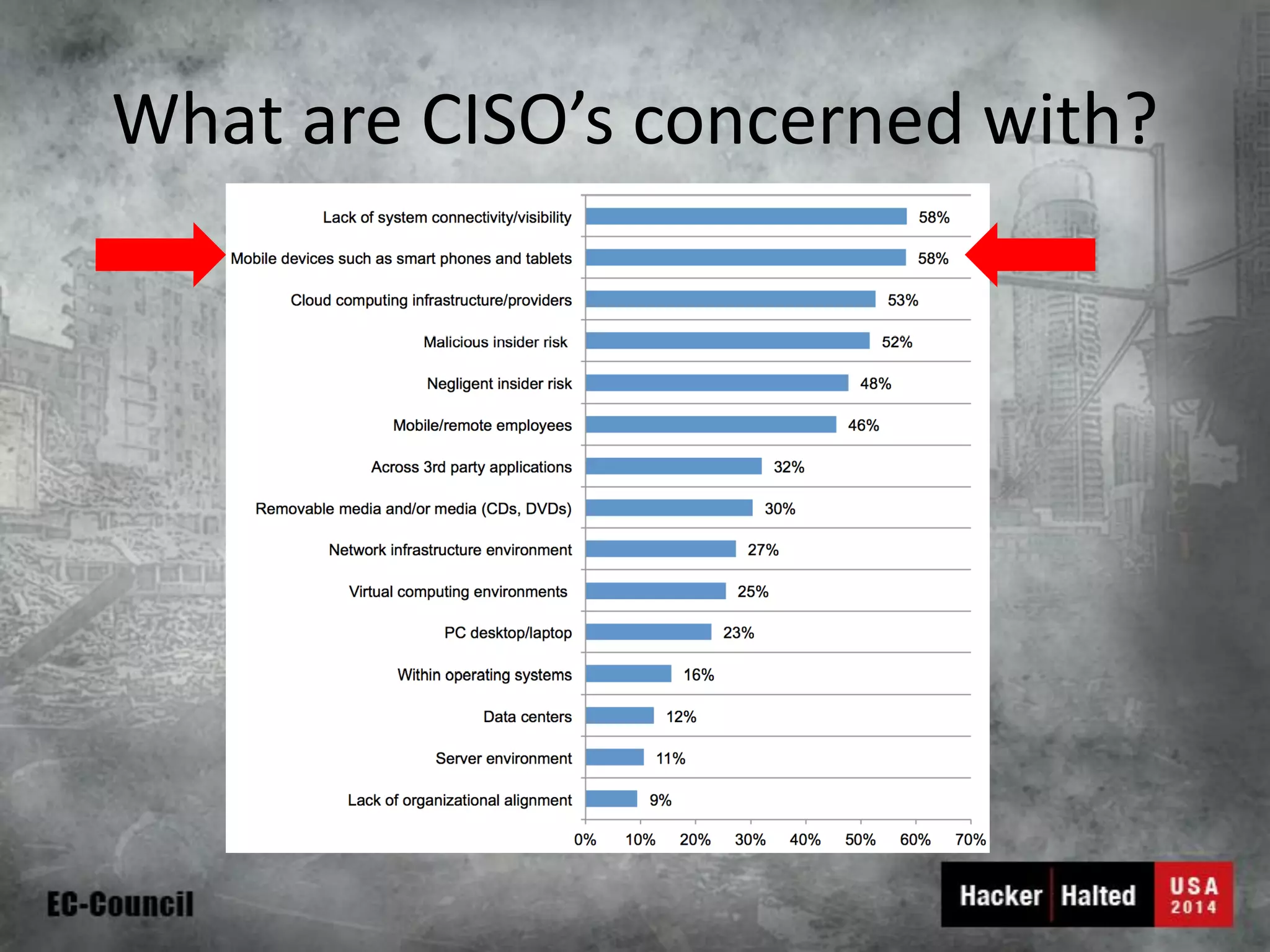
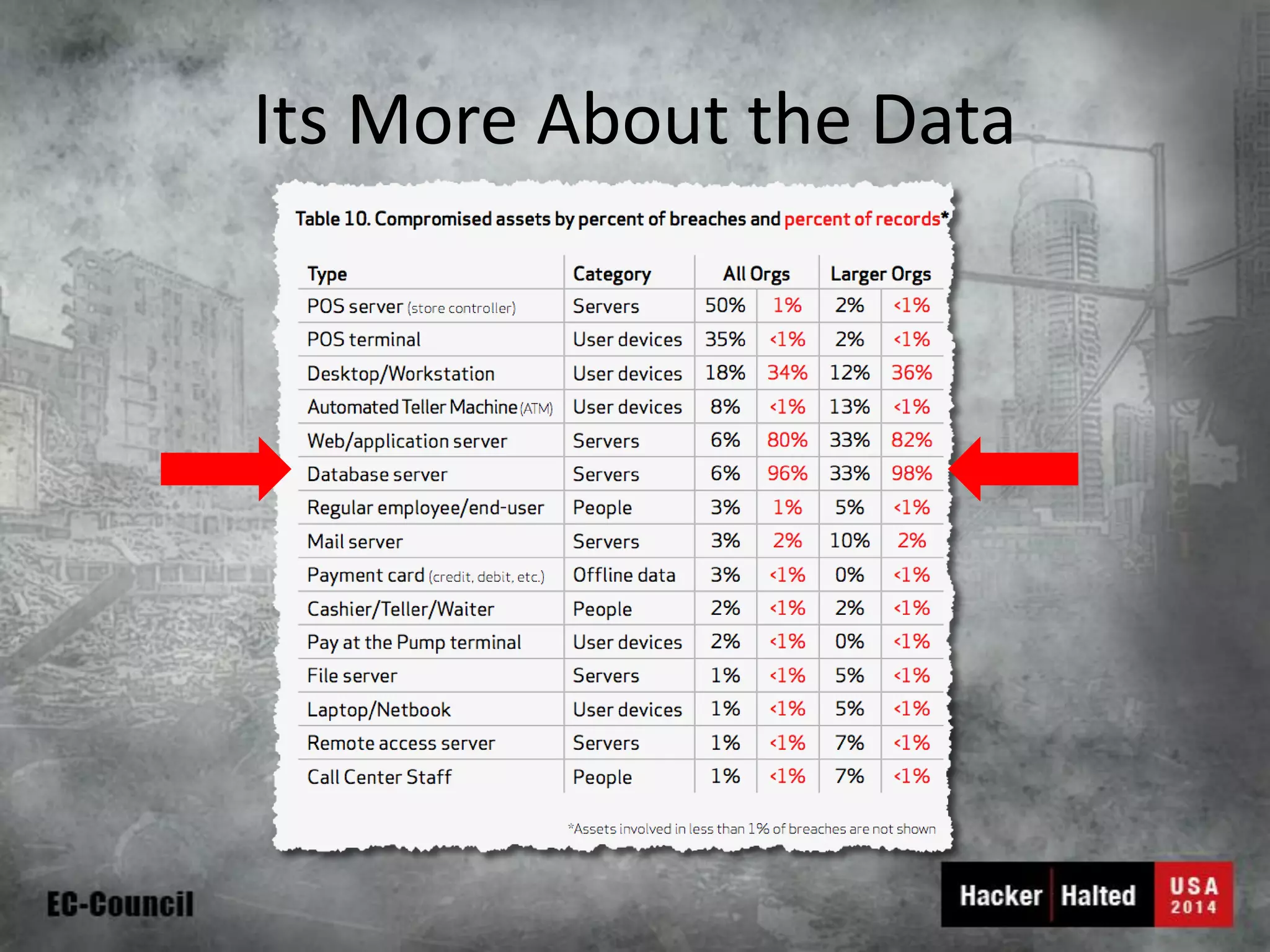
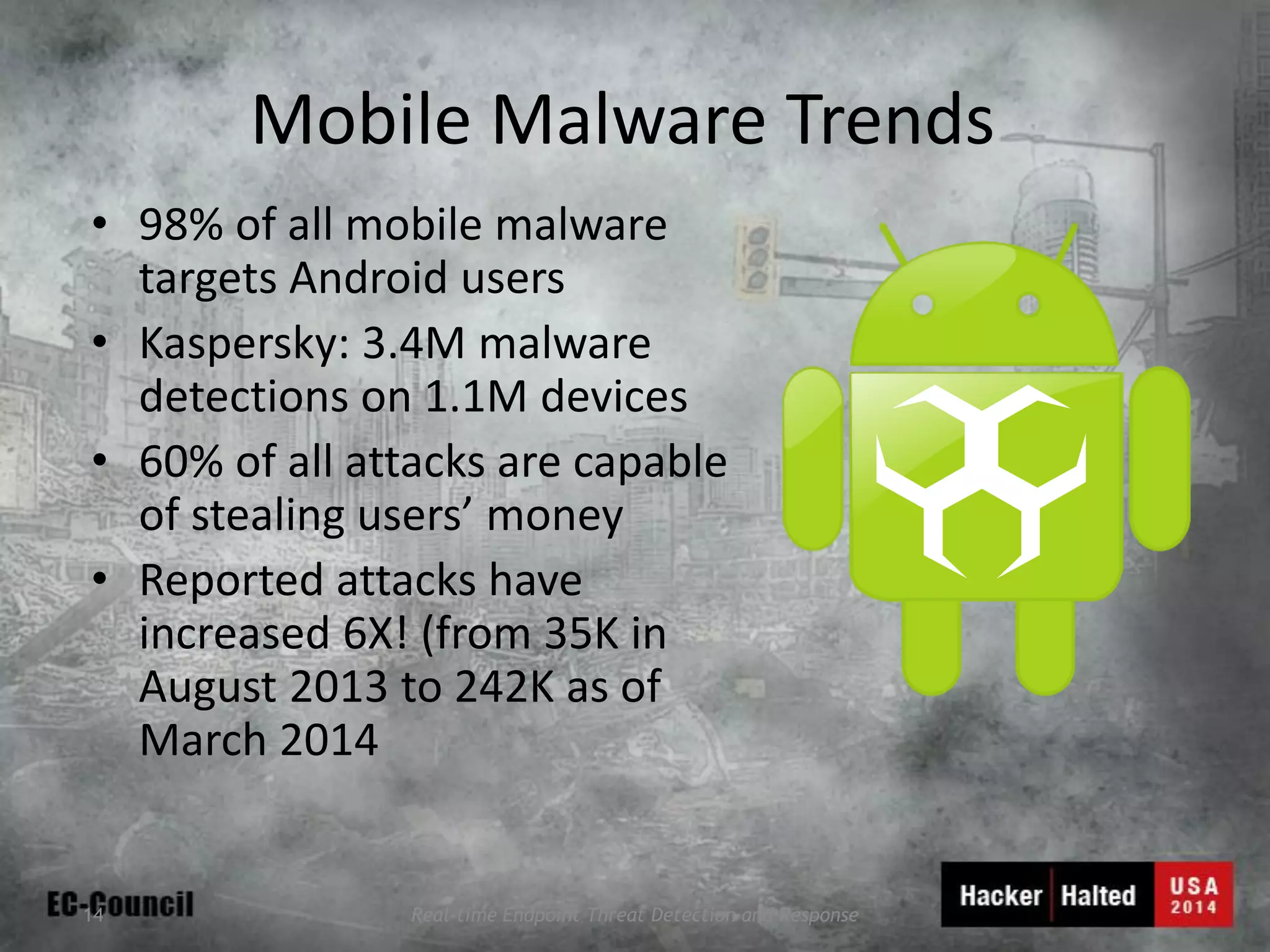
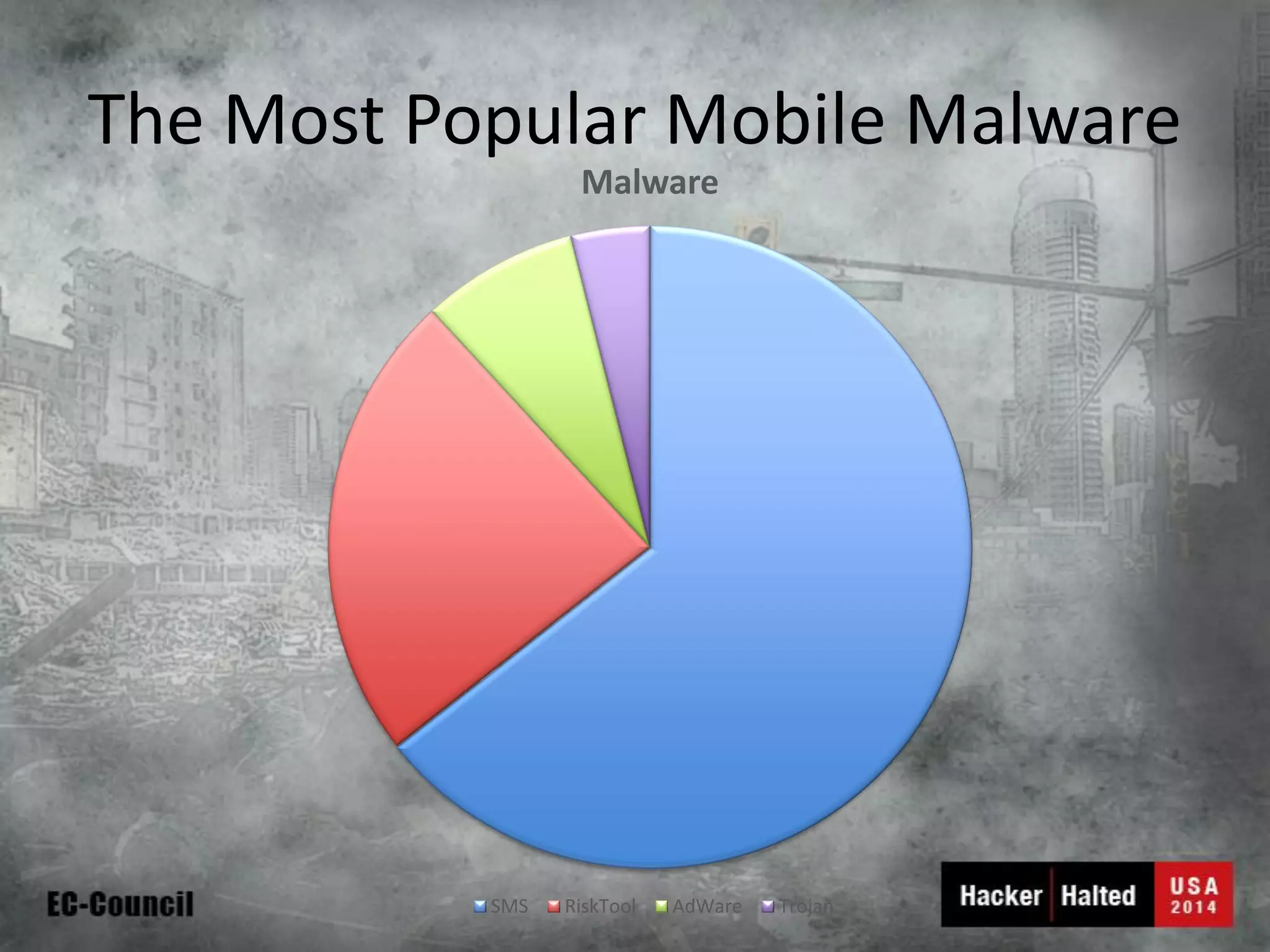
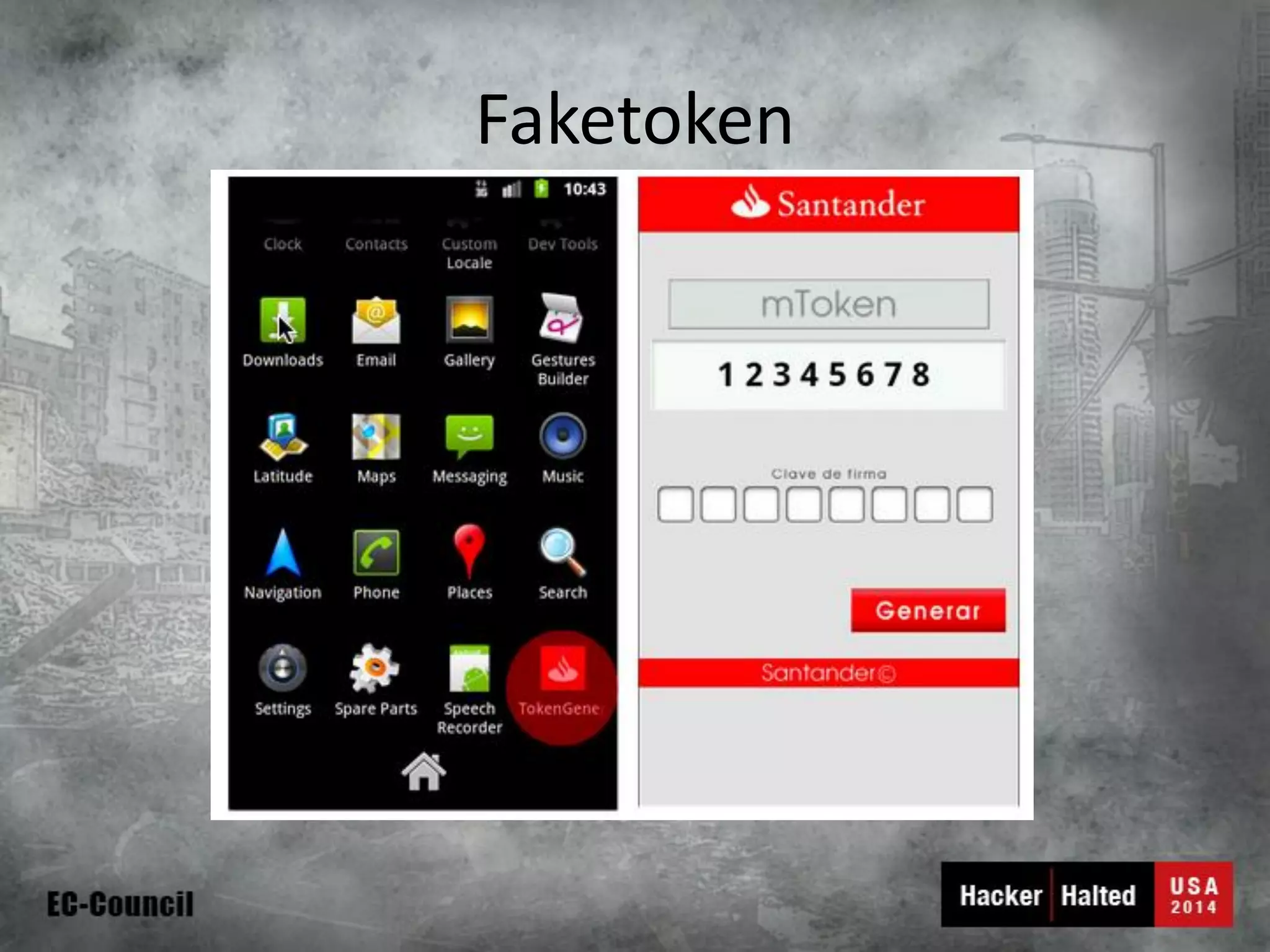
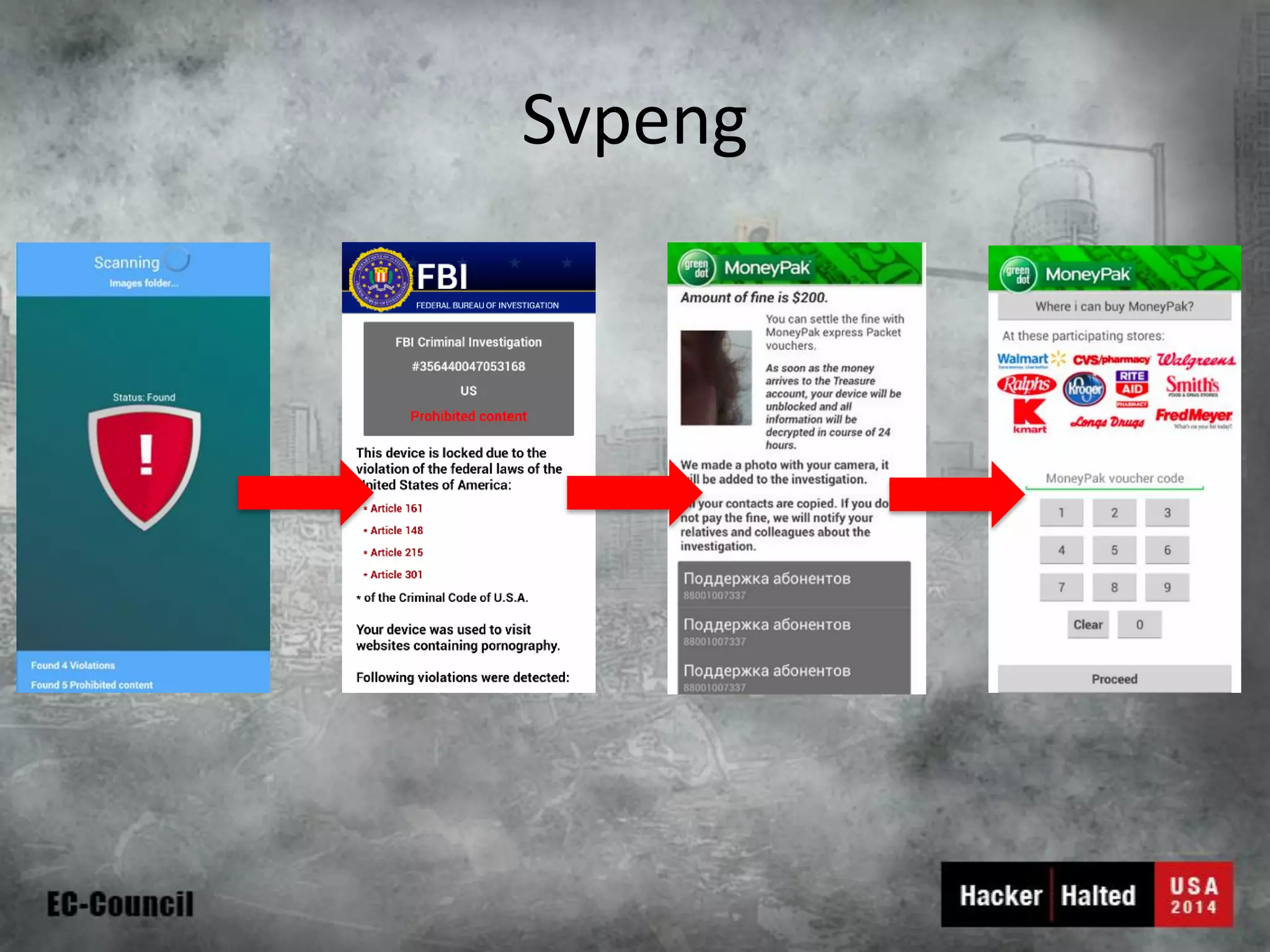
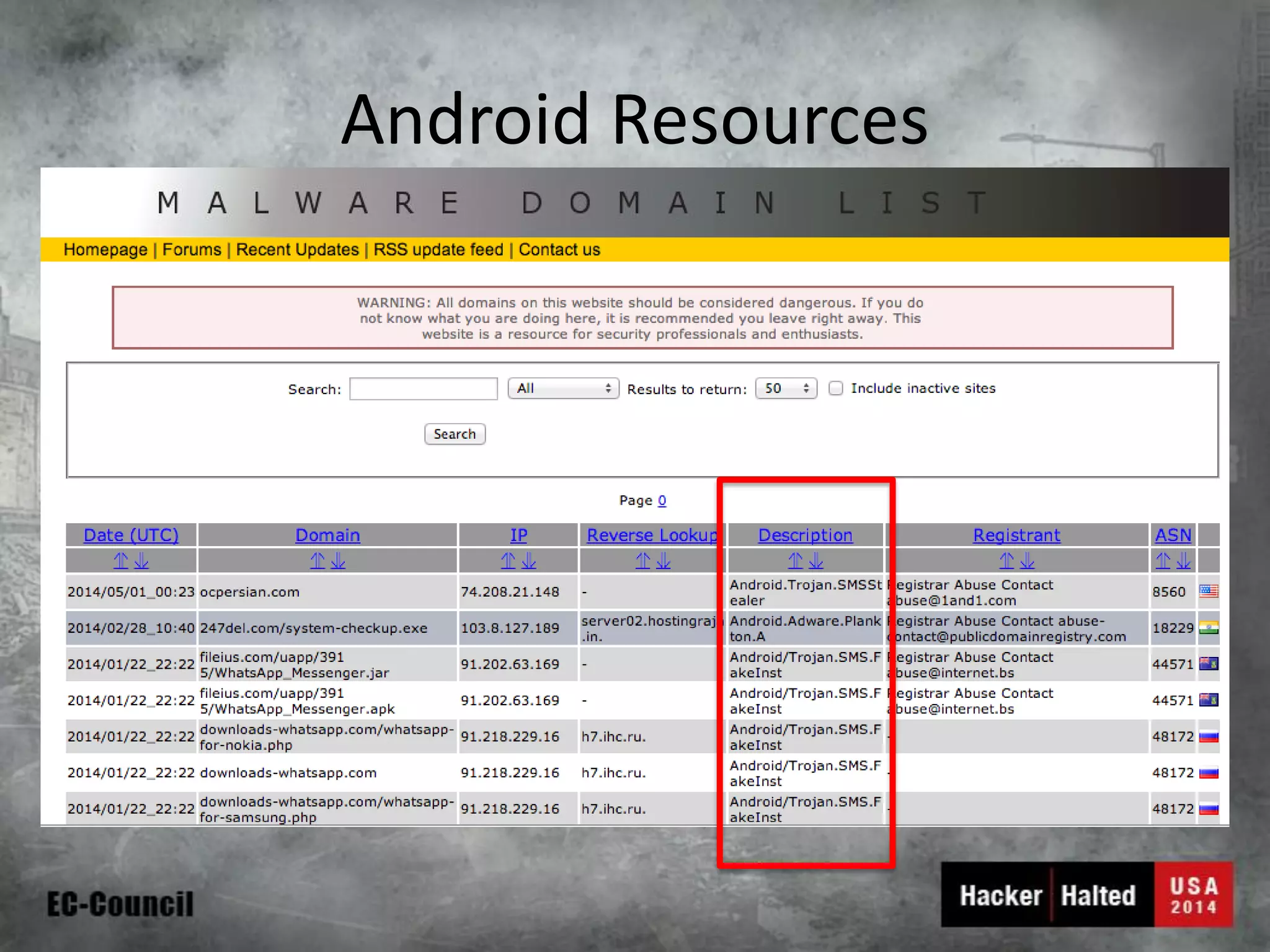
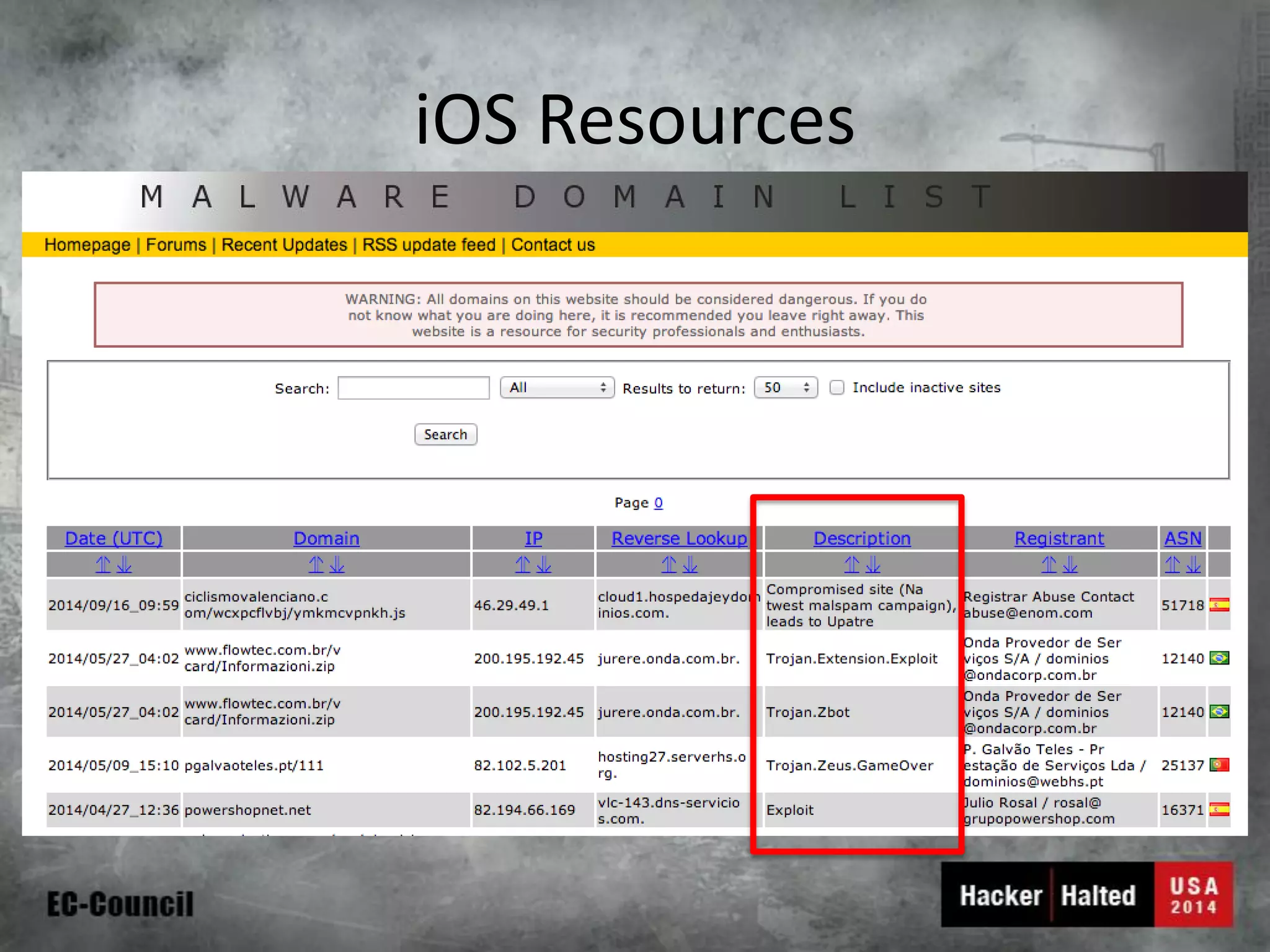
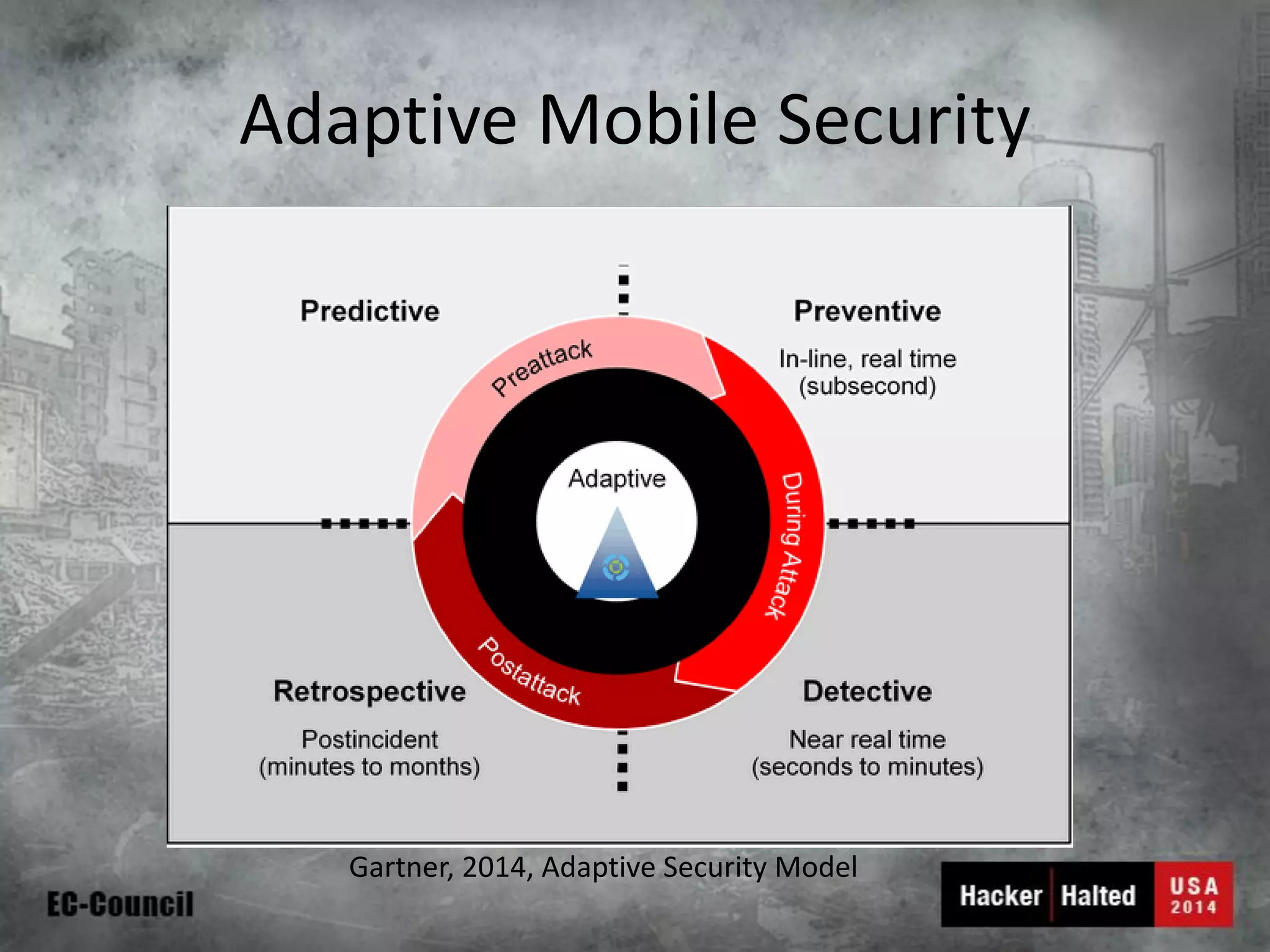
This document discusses considerations for building a mobile security model. It covers mobile security trends like the rise of BYOD and increased use of mobile devices for work. It also discusses common mobile security issues like inconsistent policies, malware threats, and data leakage. The document provides a checklist for creating a mobile security policy that assesses risks and validates controls. It emphasizes the need to understand how data will be used and accessed across devices to define clear and enforceable policies.