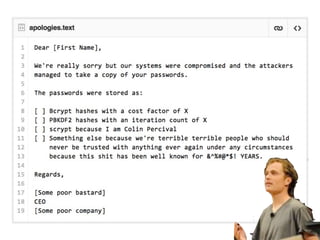
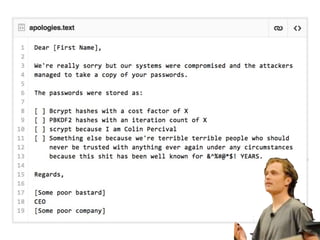
The document discusses vulnerabilities in various cryptographic hashing algorithms such as MD5 and SHA1, highlighting their inadequacies in security. It introduces password hashing techniques like PBKDF2, bcrypt, and scrypt, emphasizing their advantages over conventional methods. Additionally, it touches upon the importance of using HMAC for secure messaging and the limitations of SSL in ensuring data privacy.