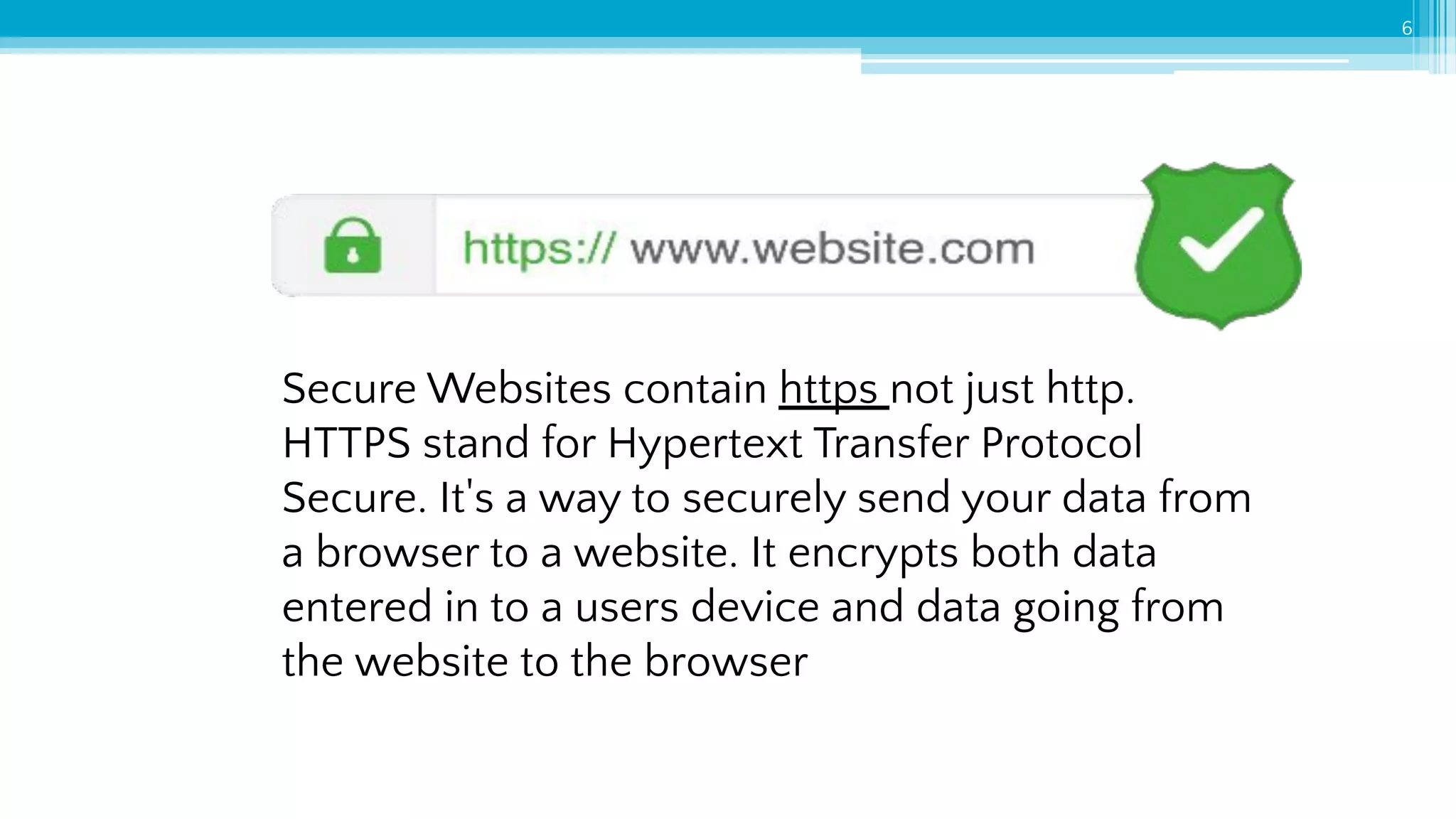
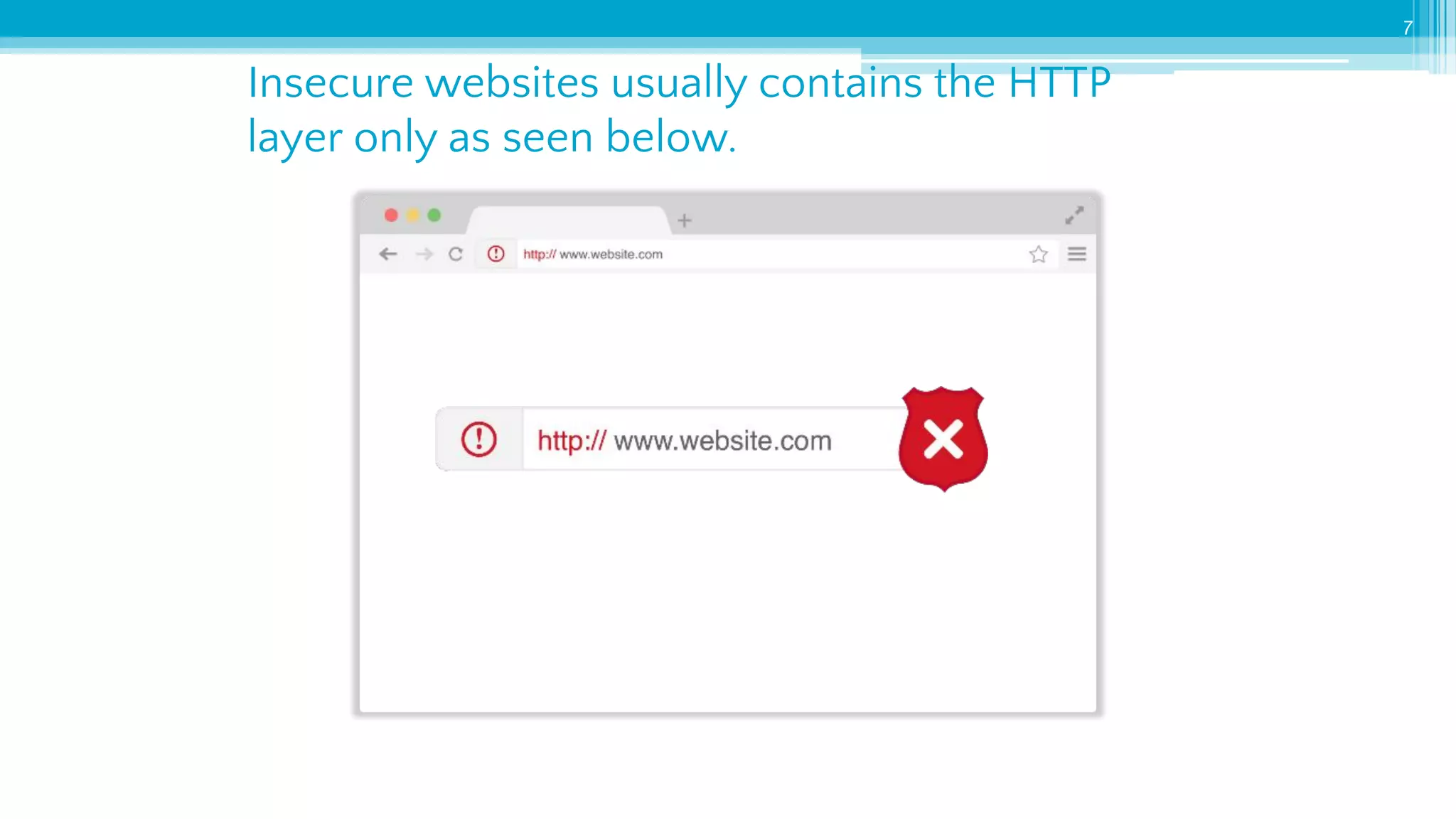
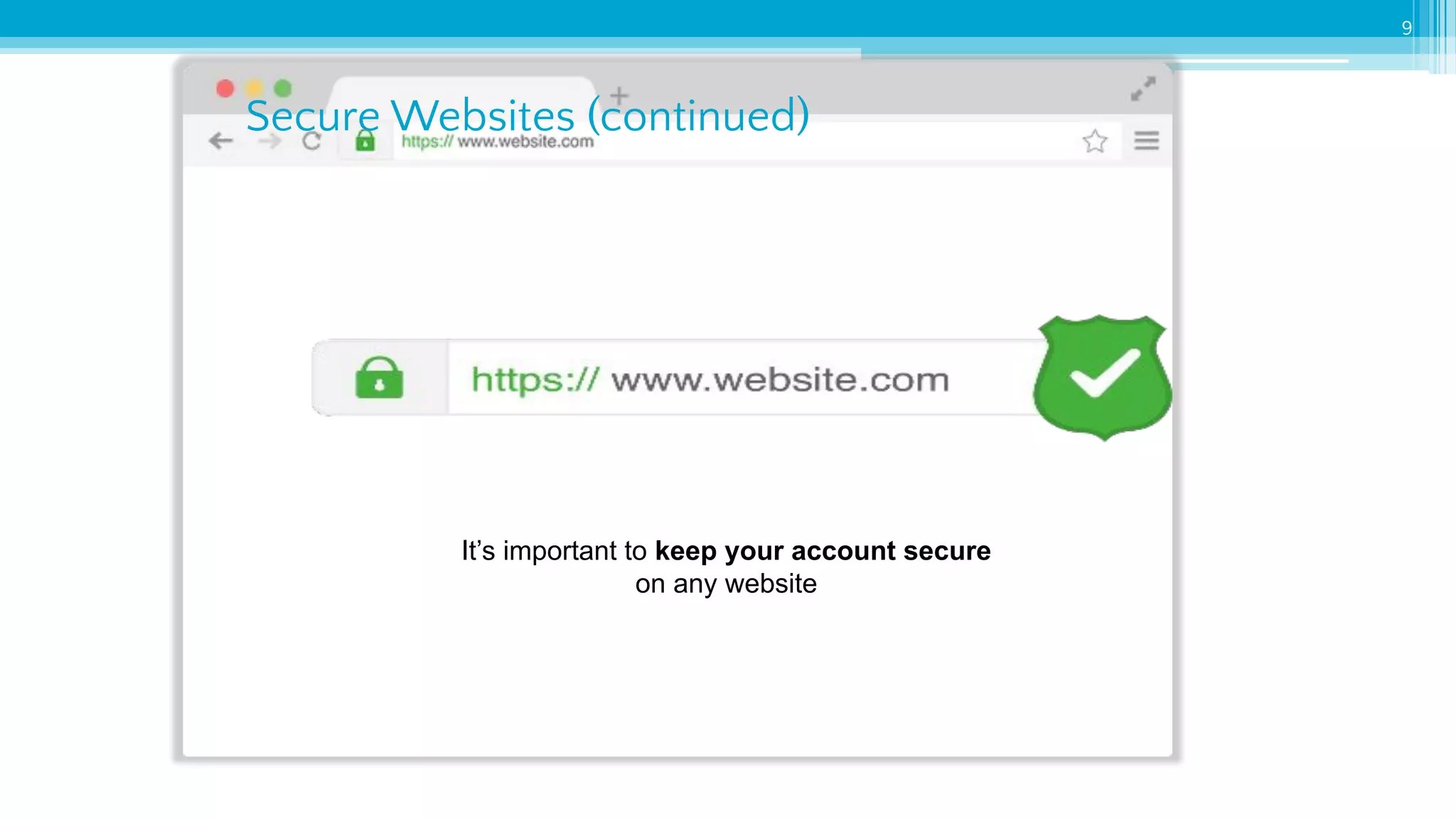
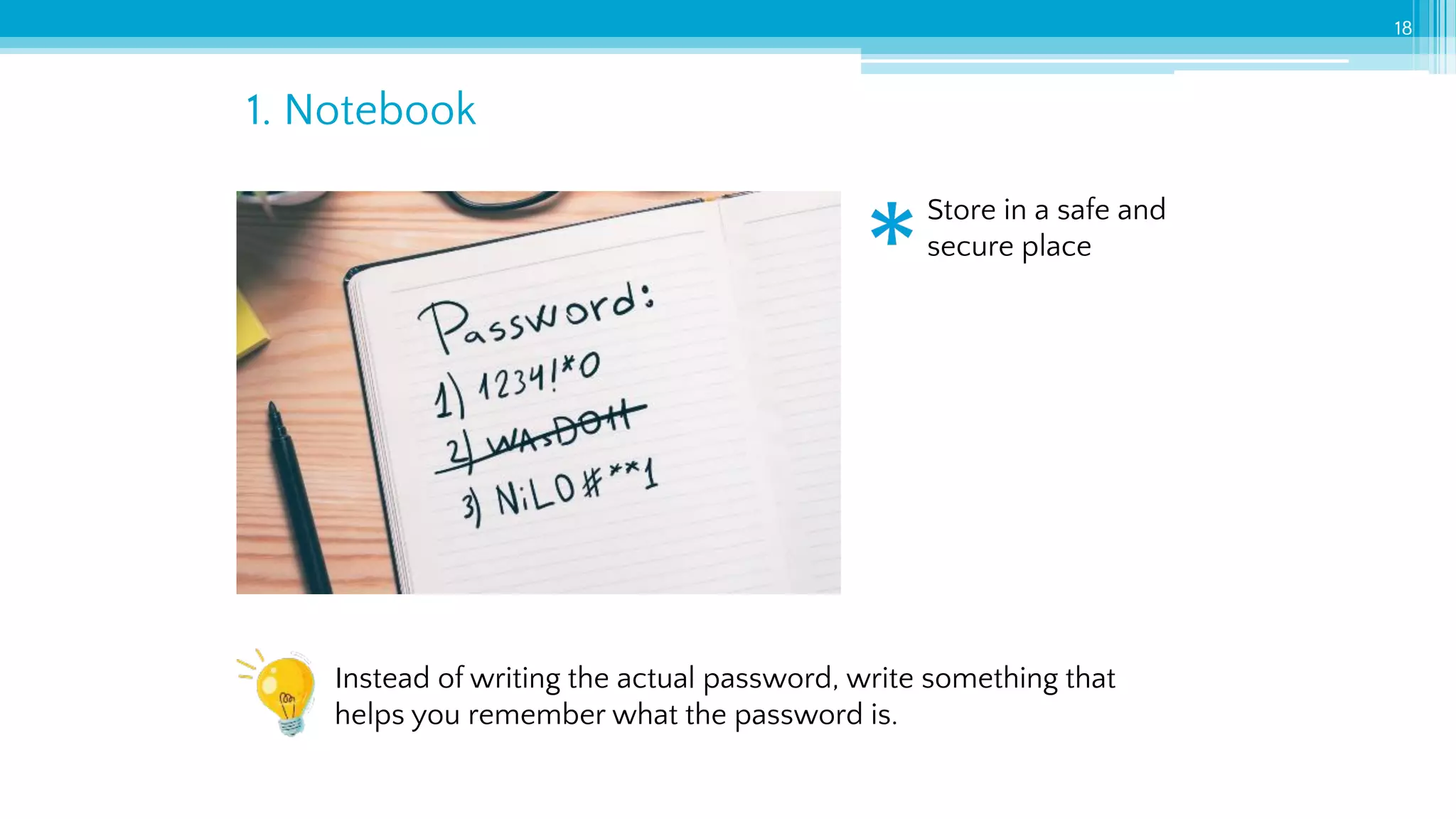
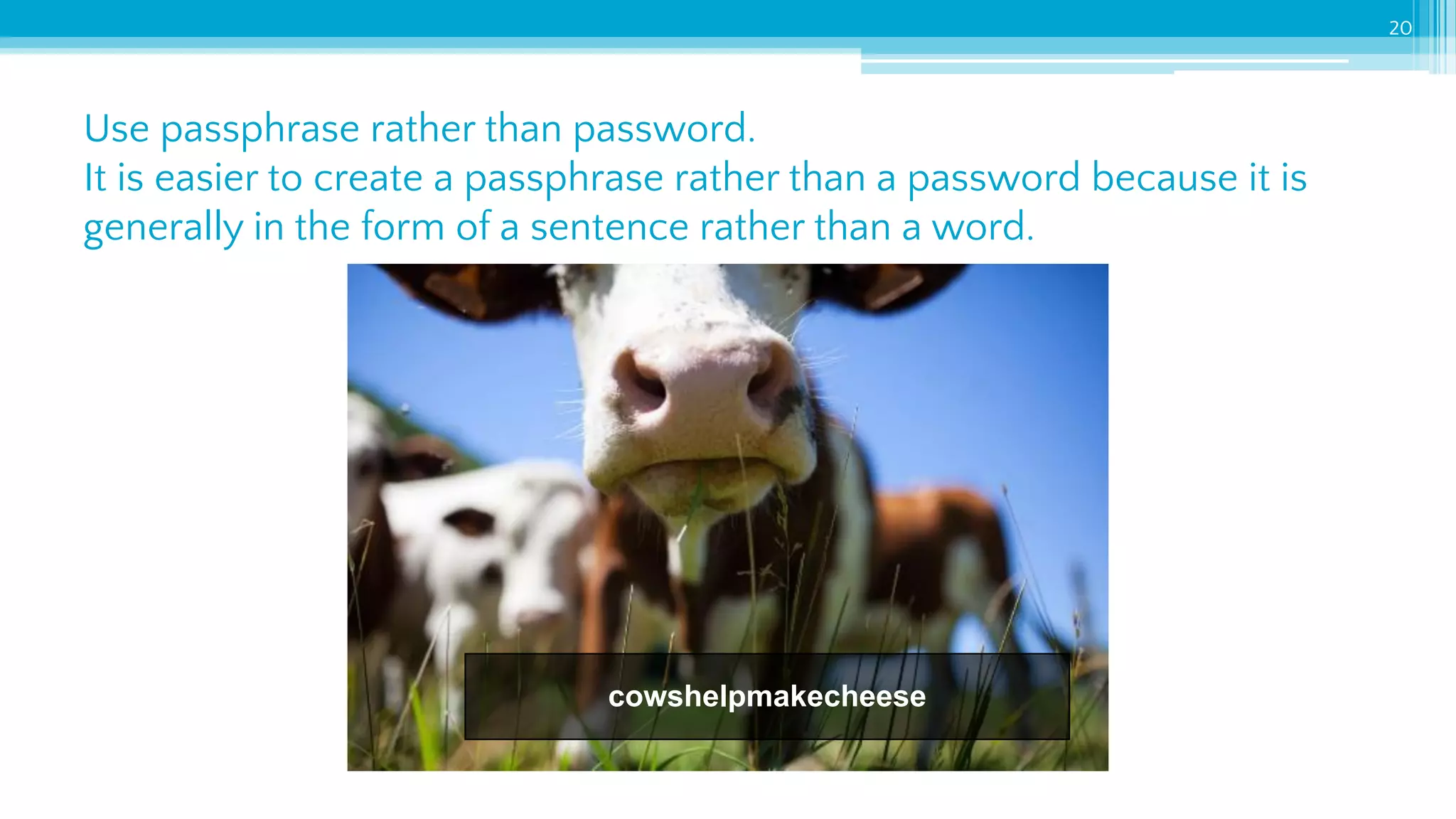
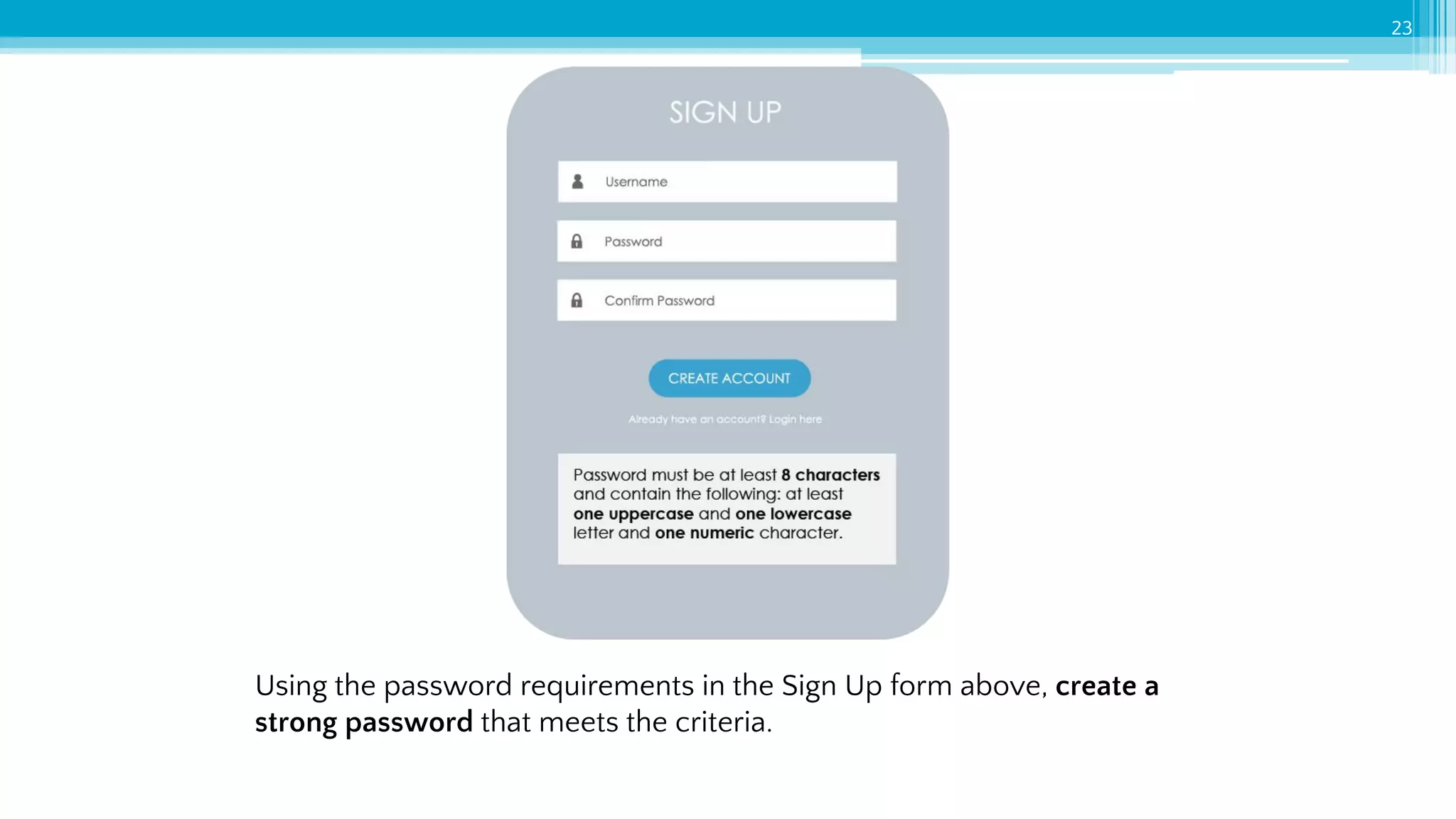
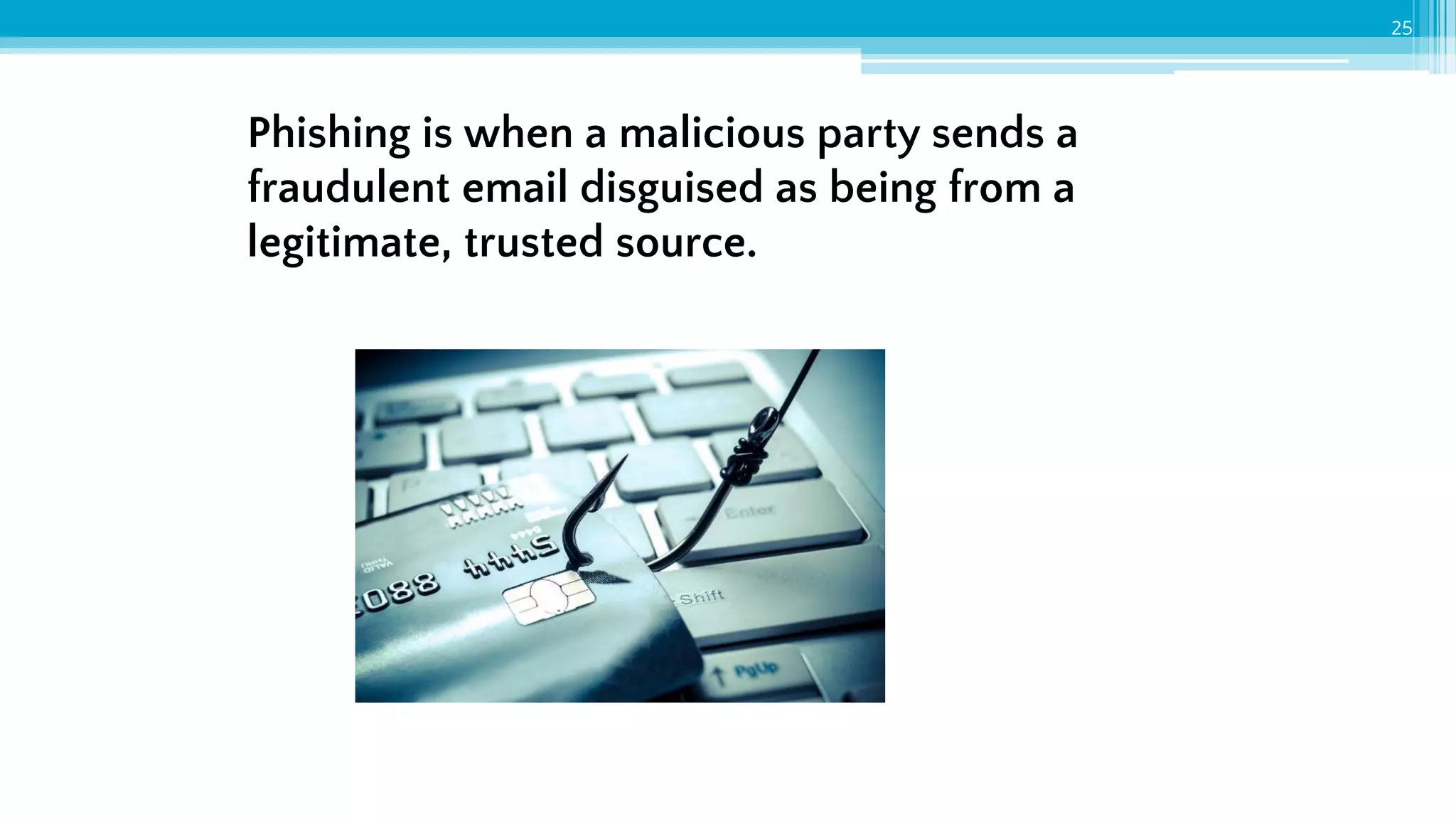
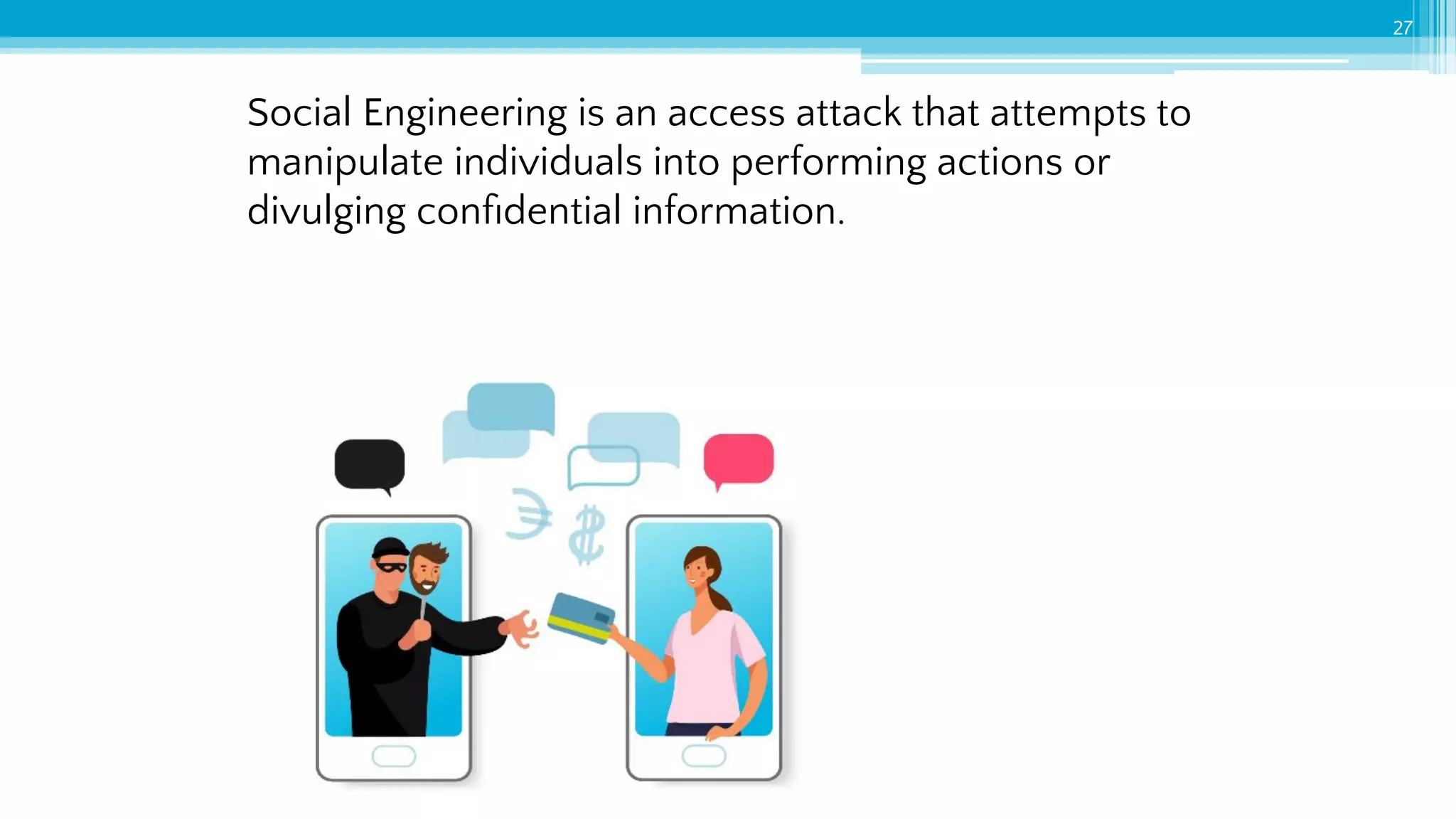
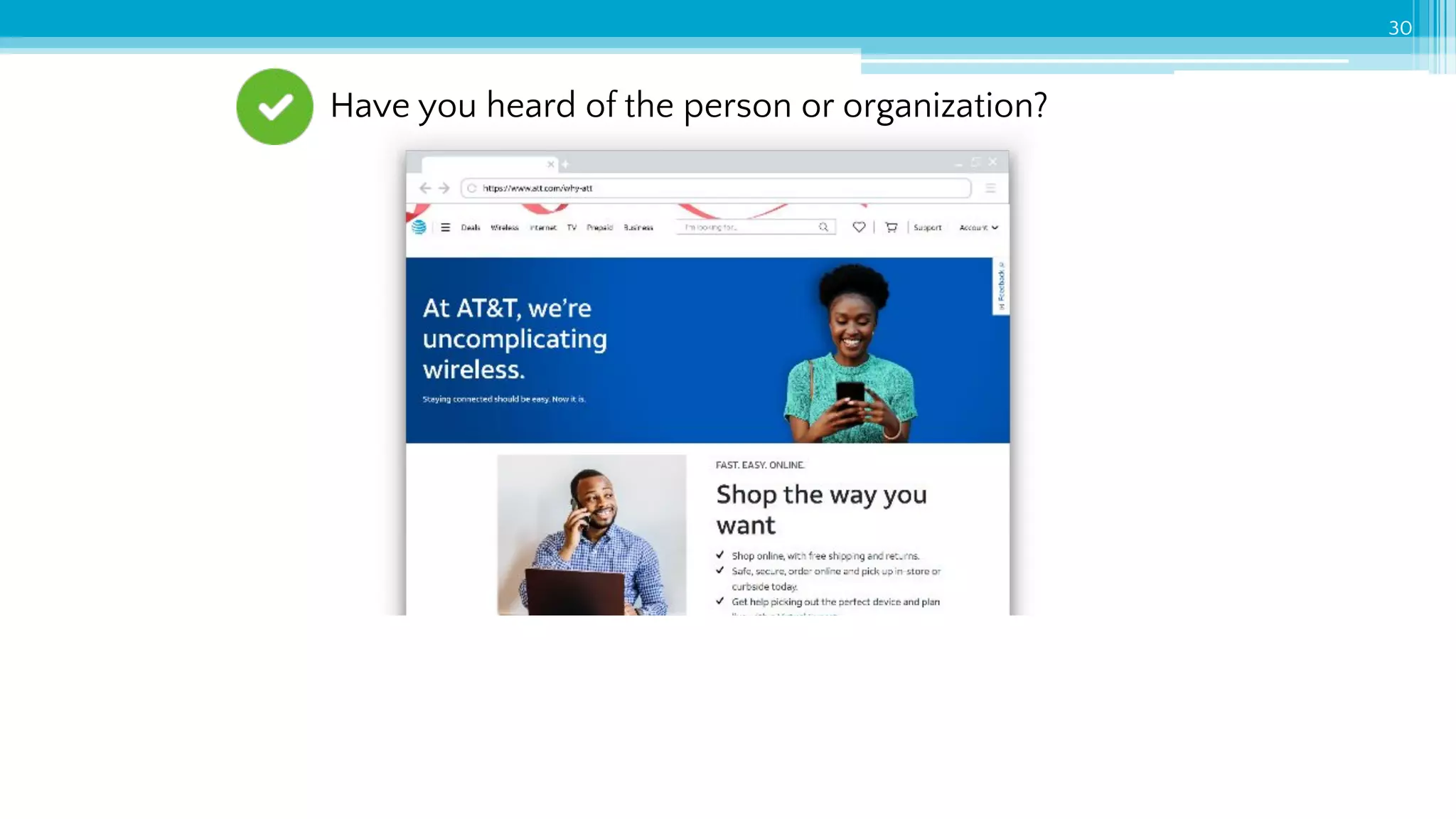
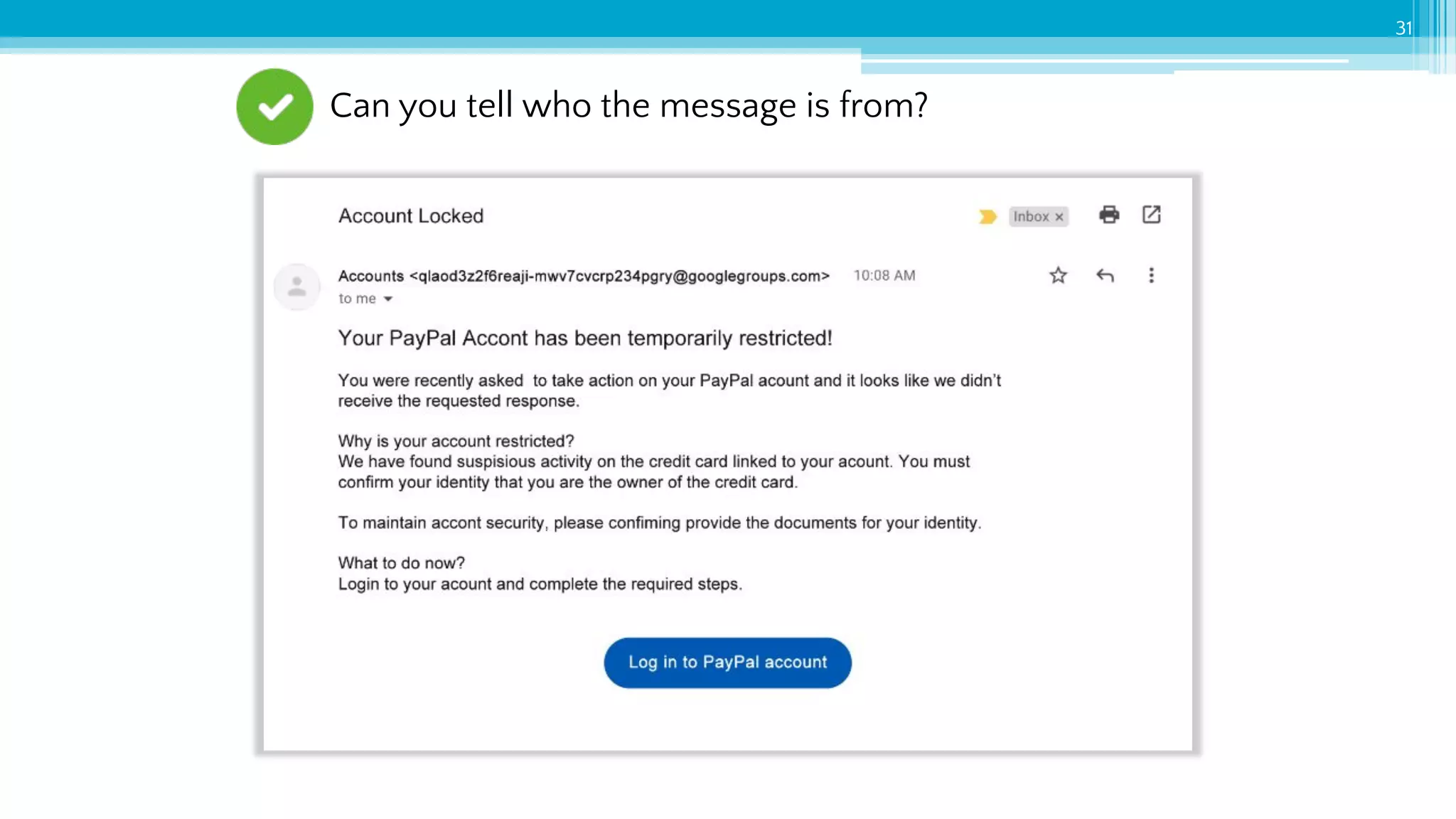
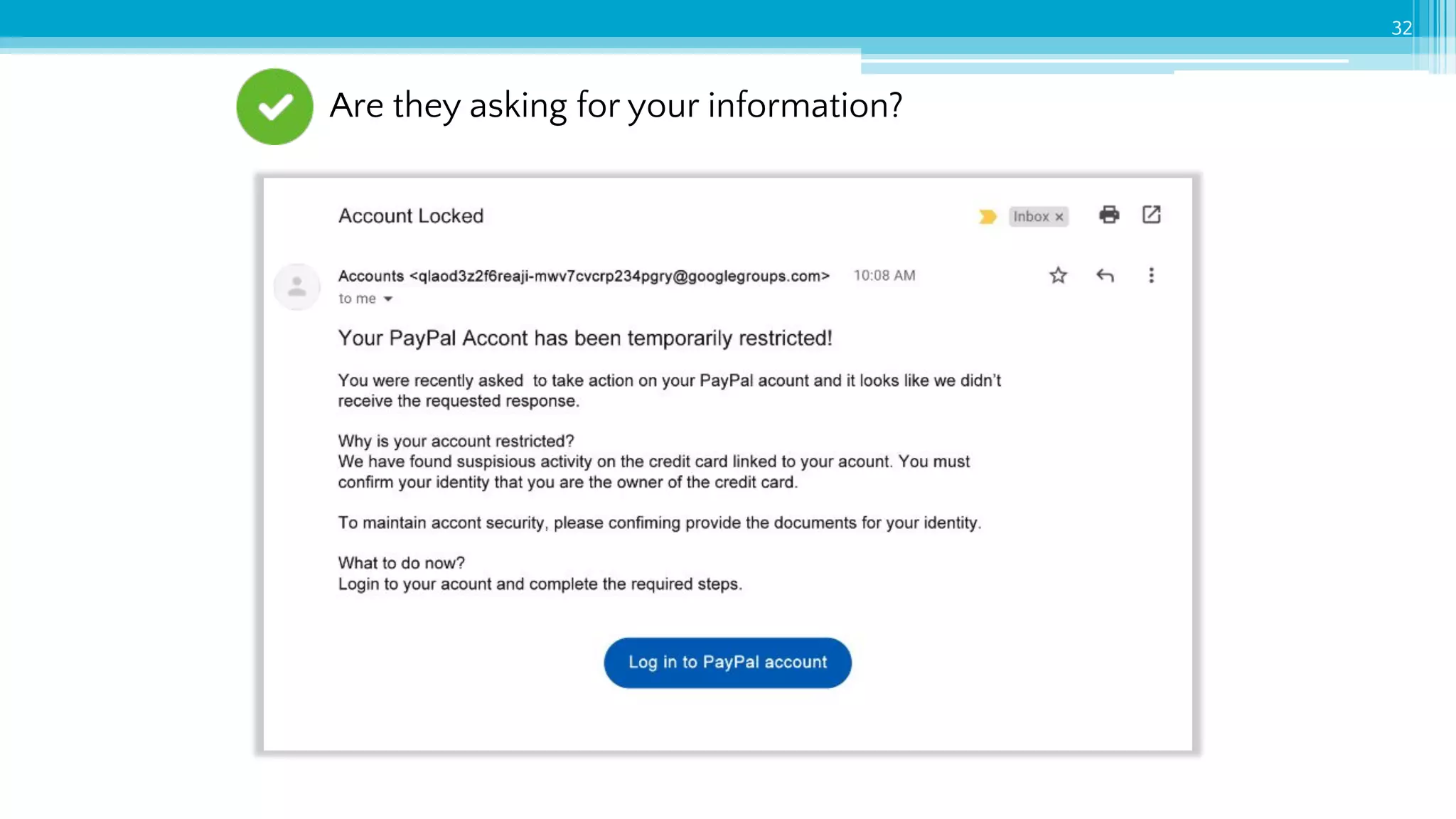
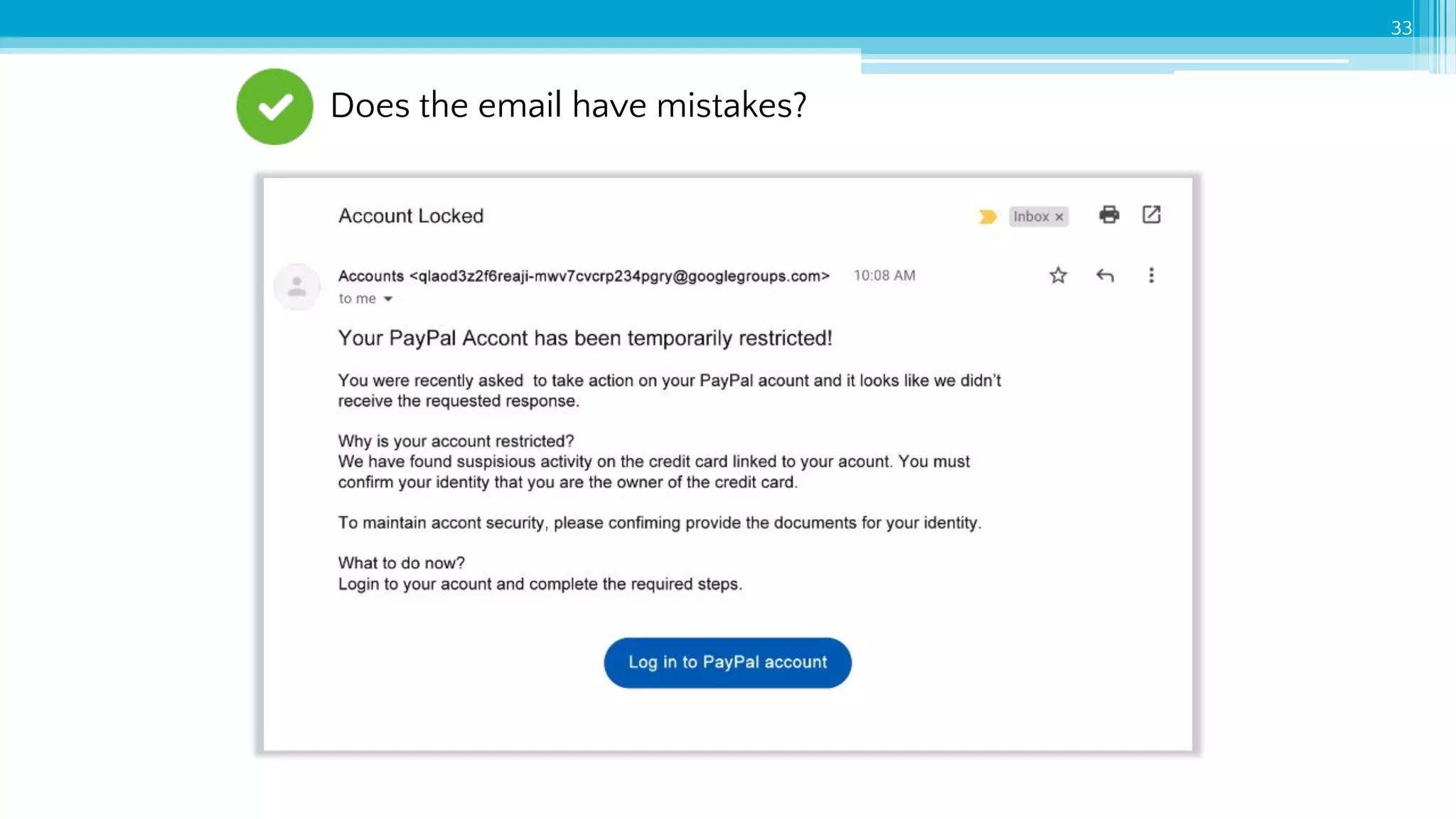
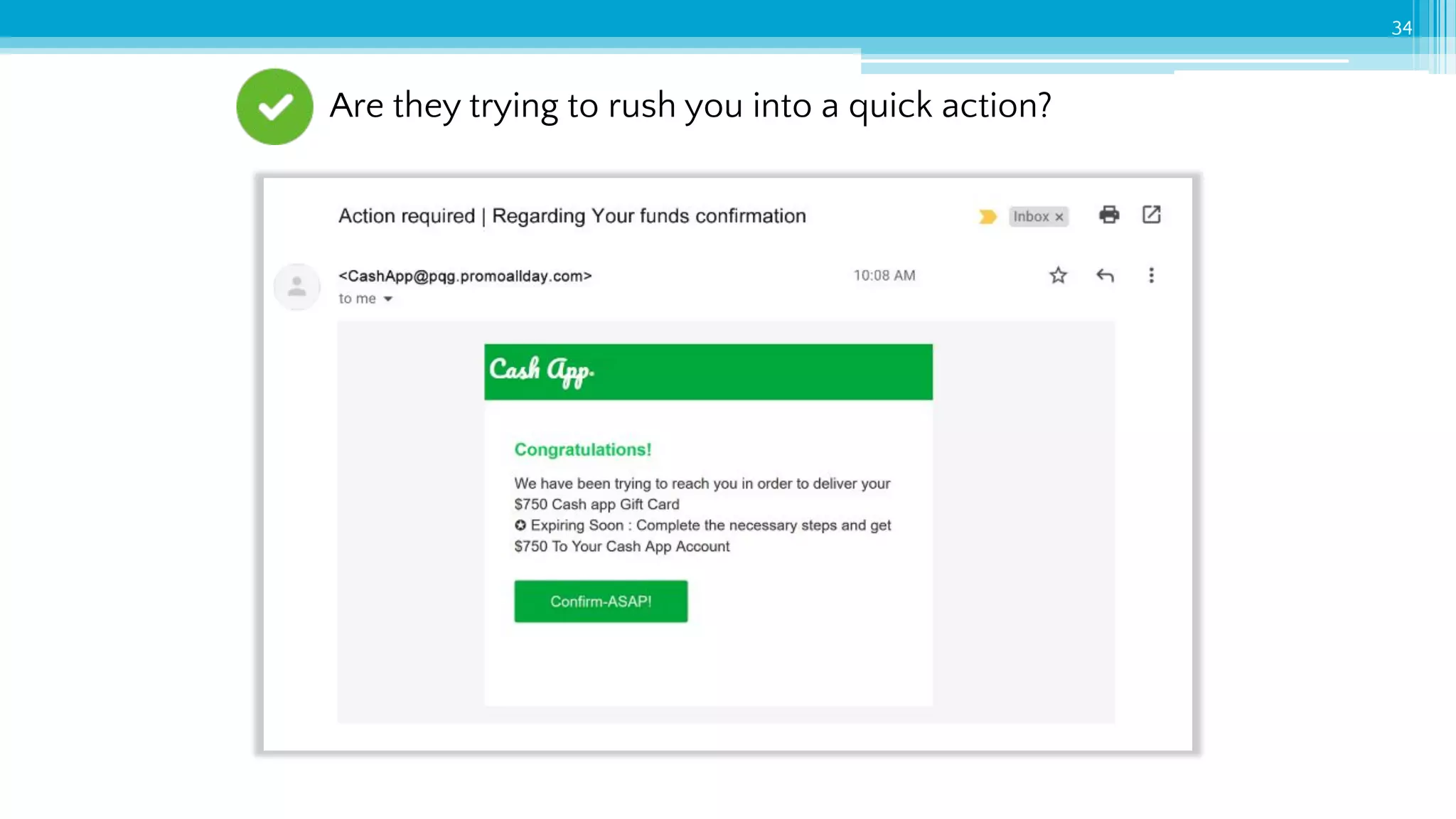
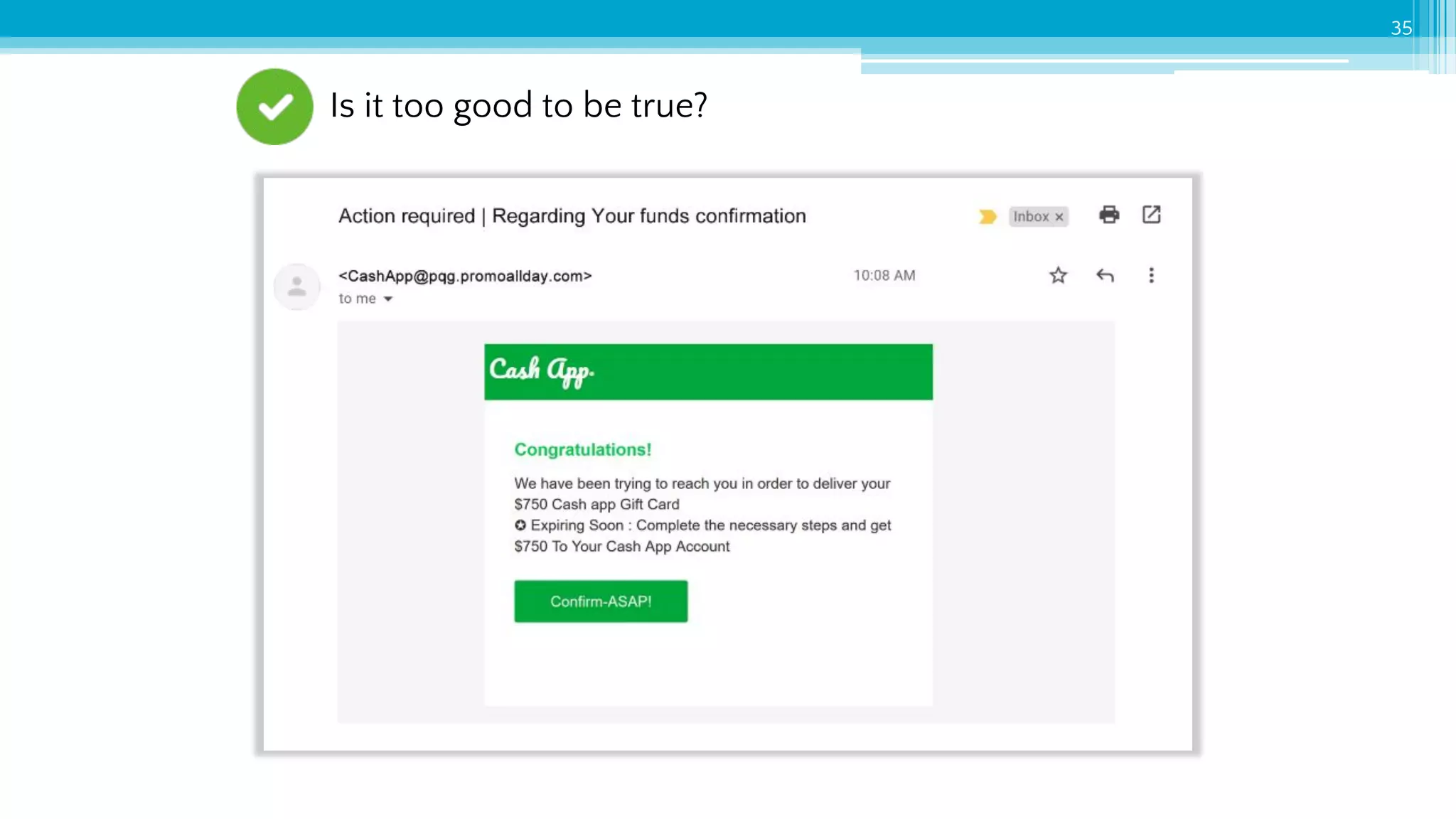
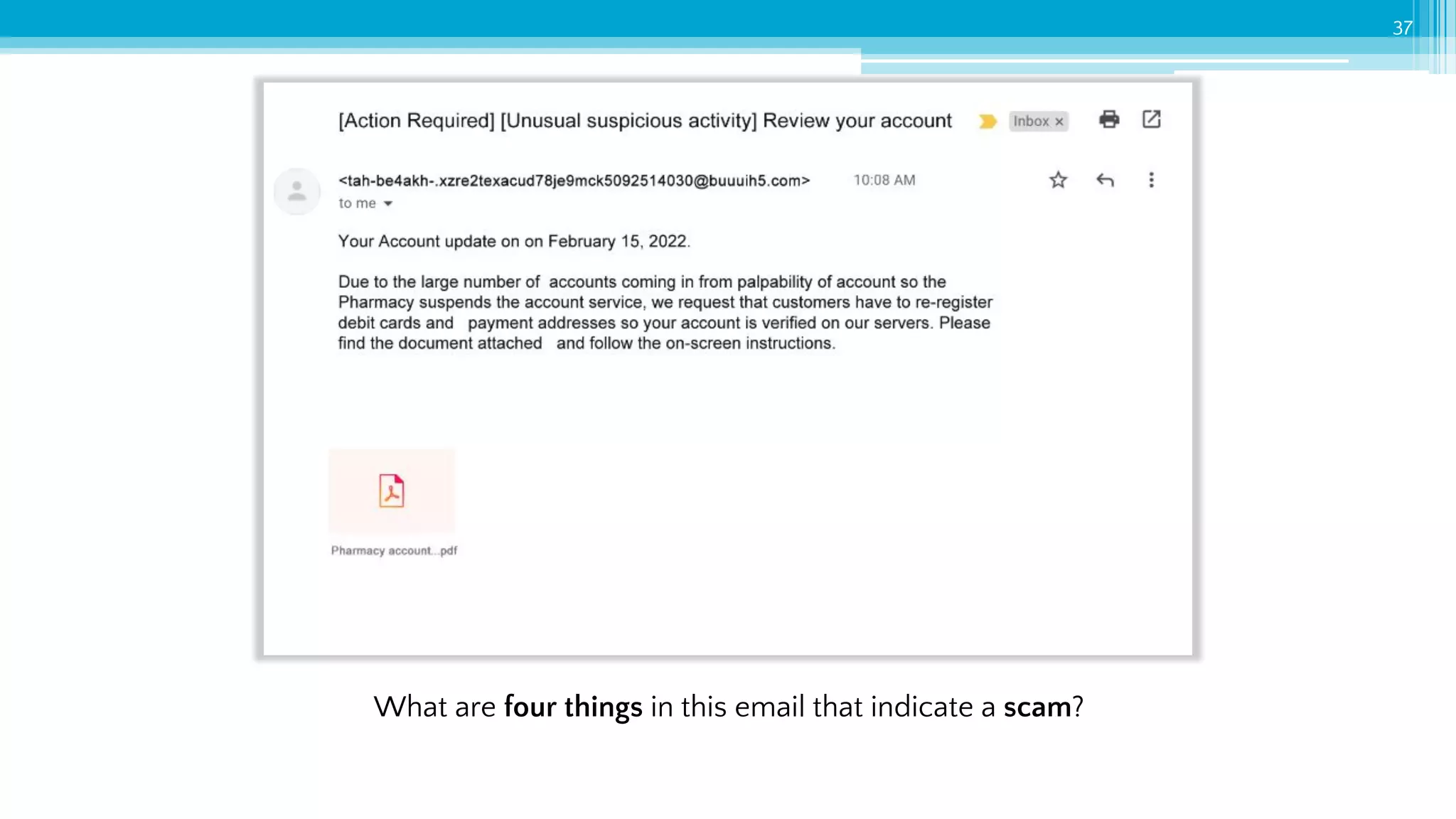
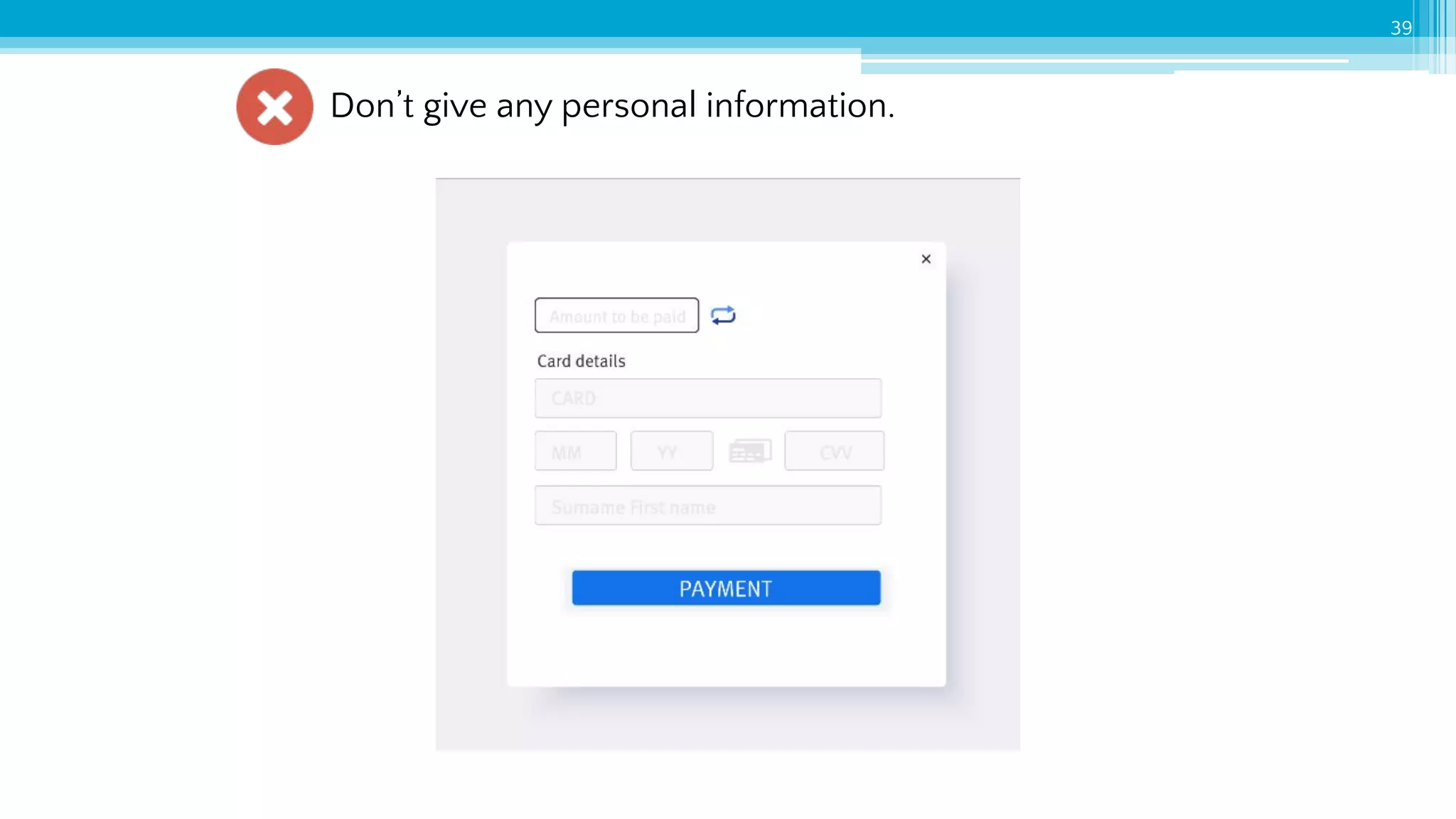
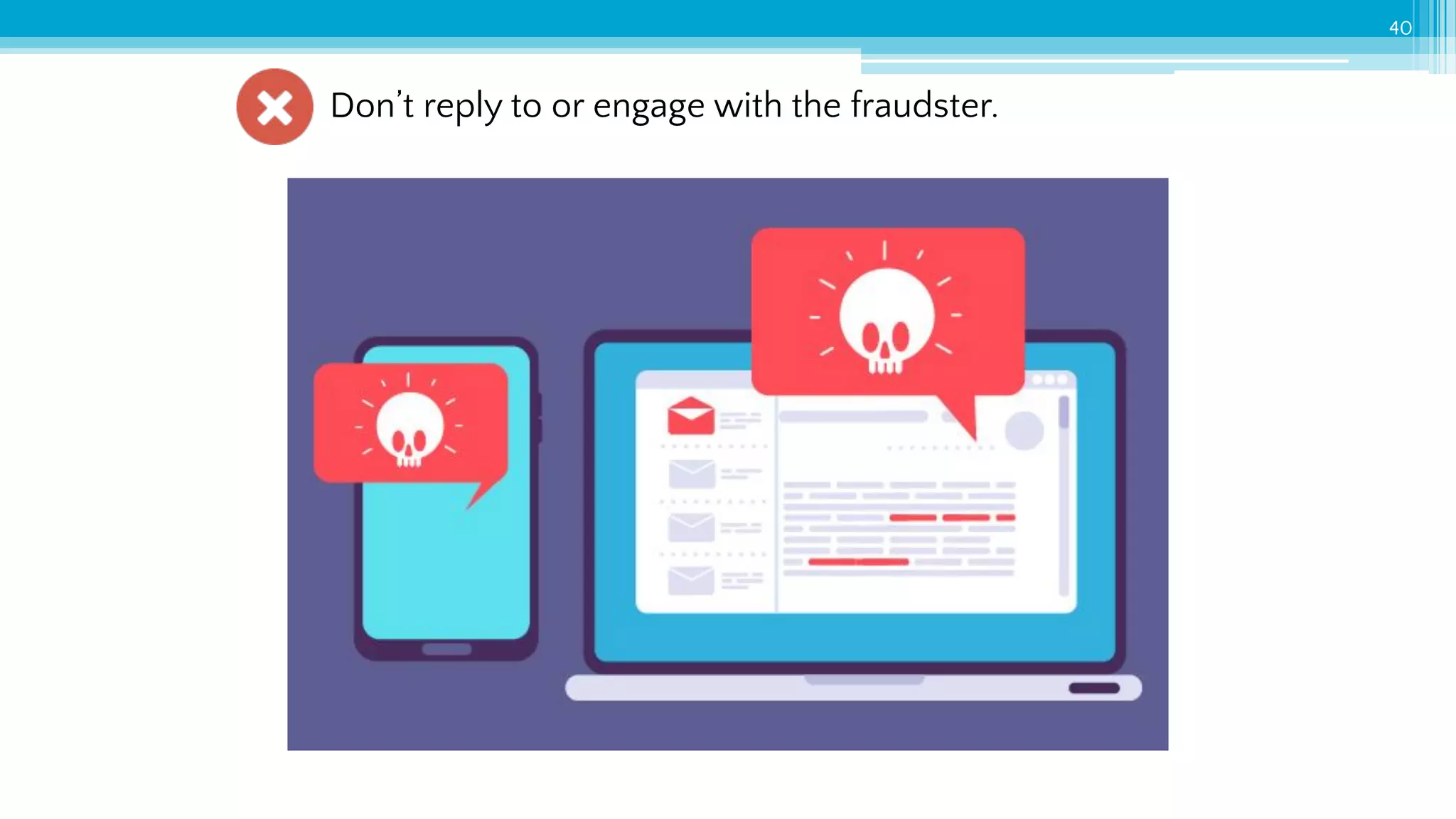
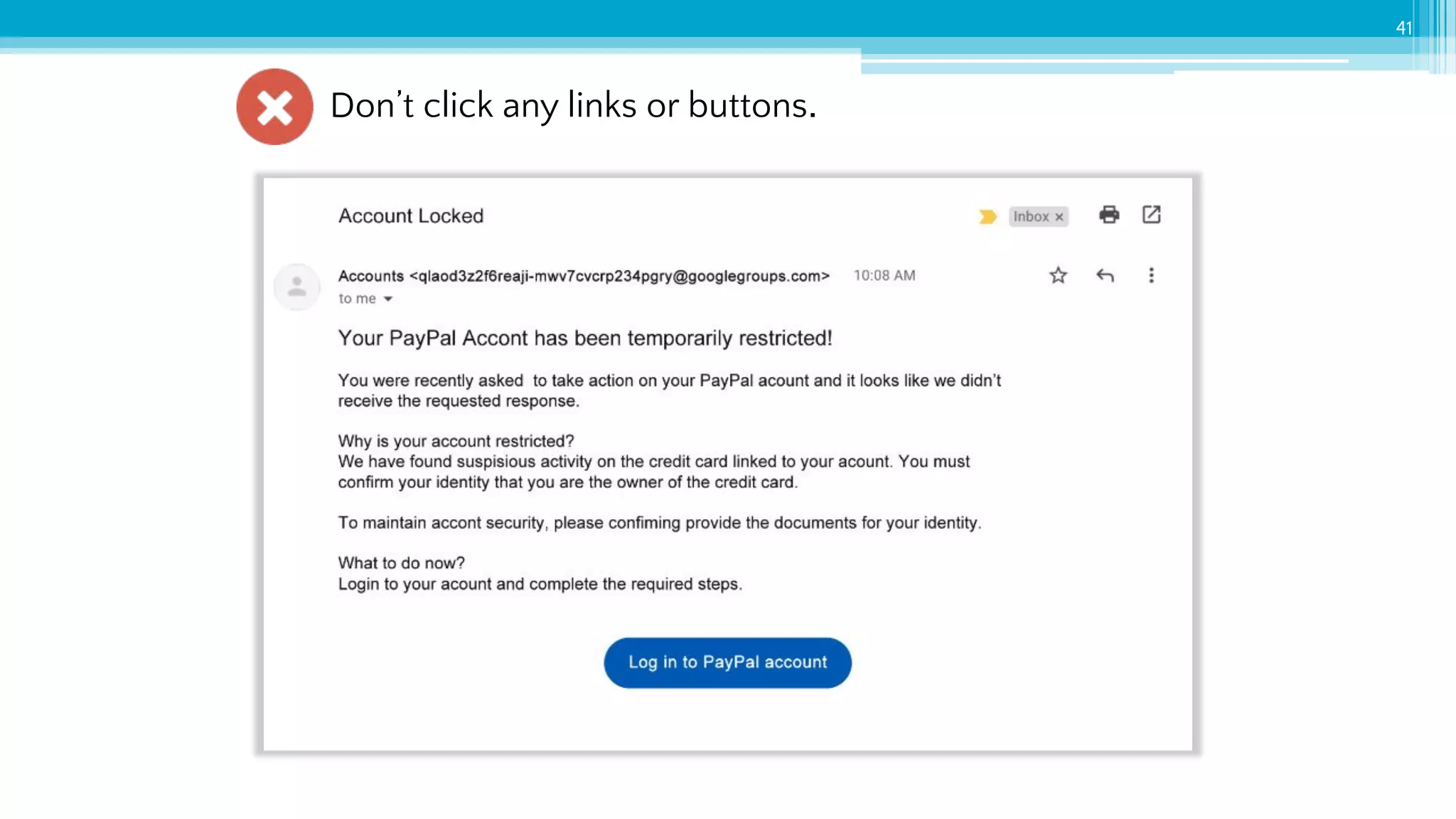
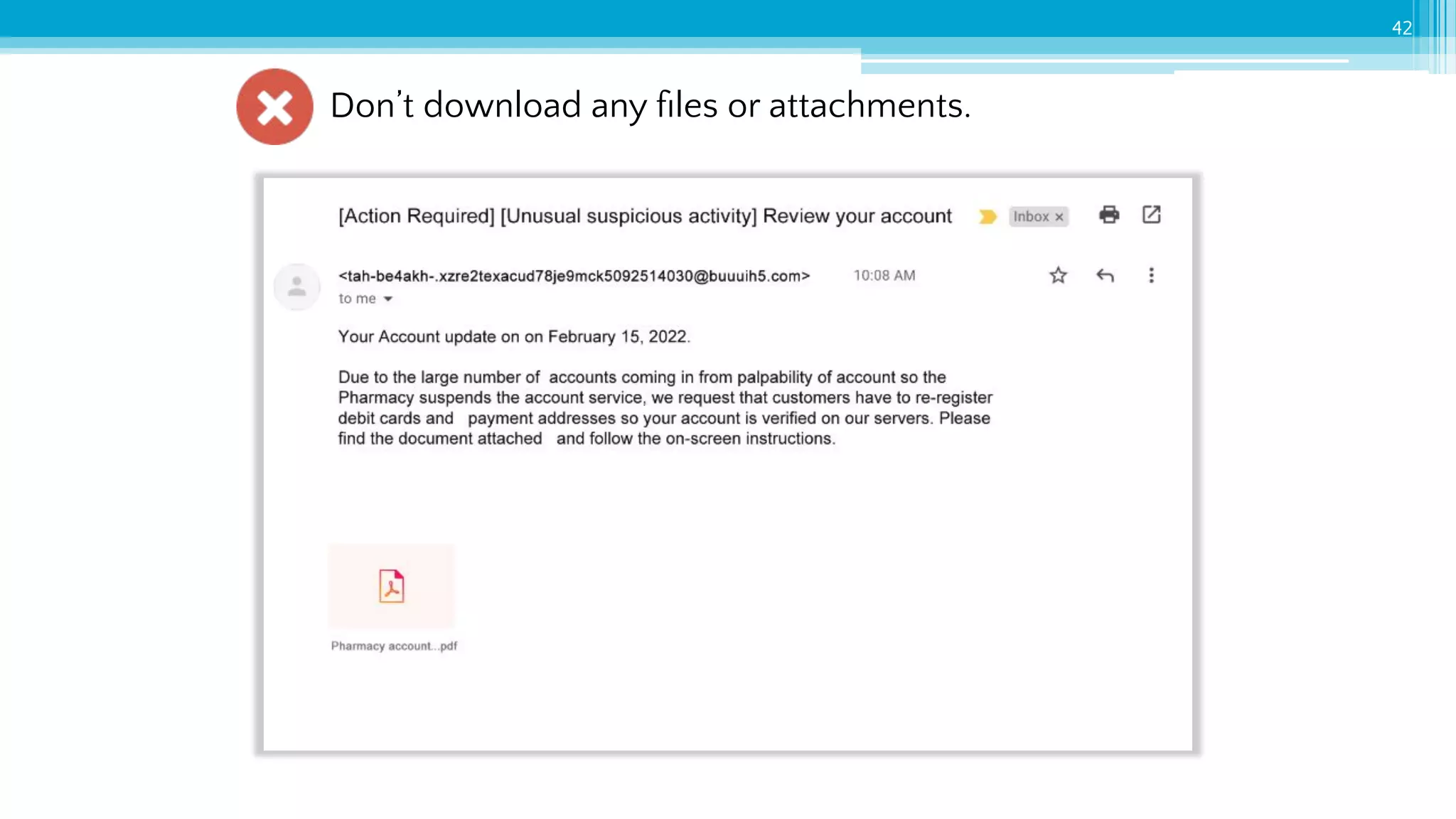
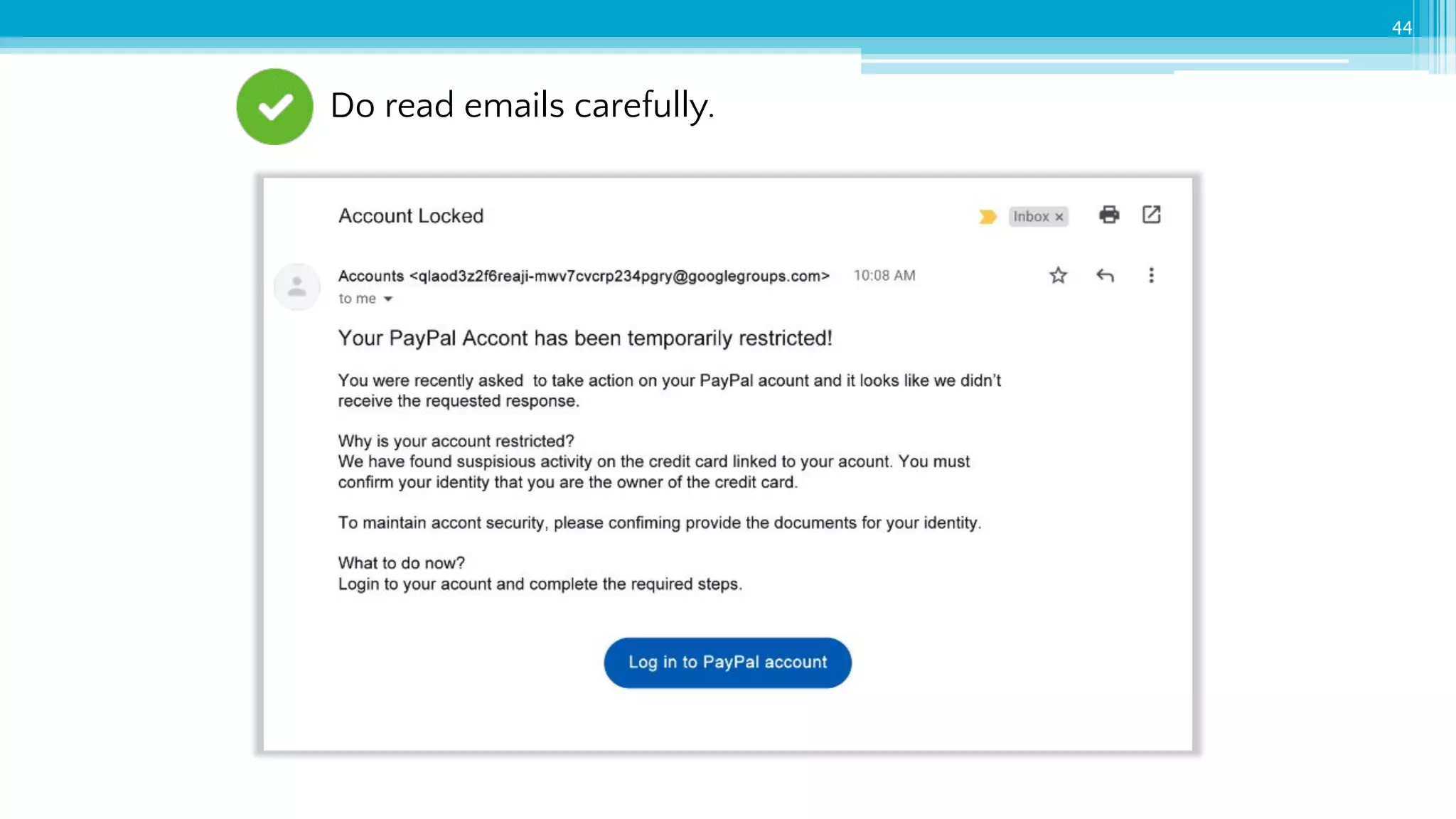
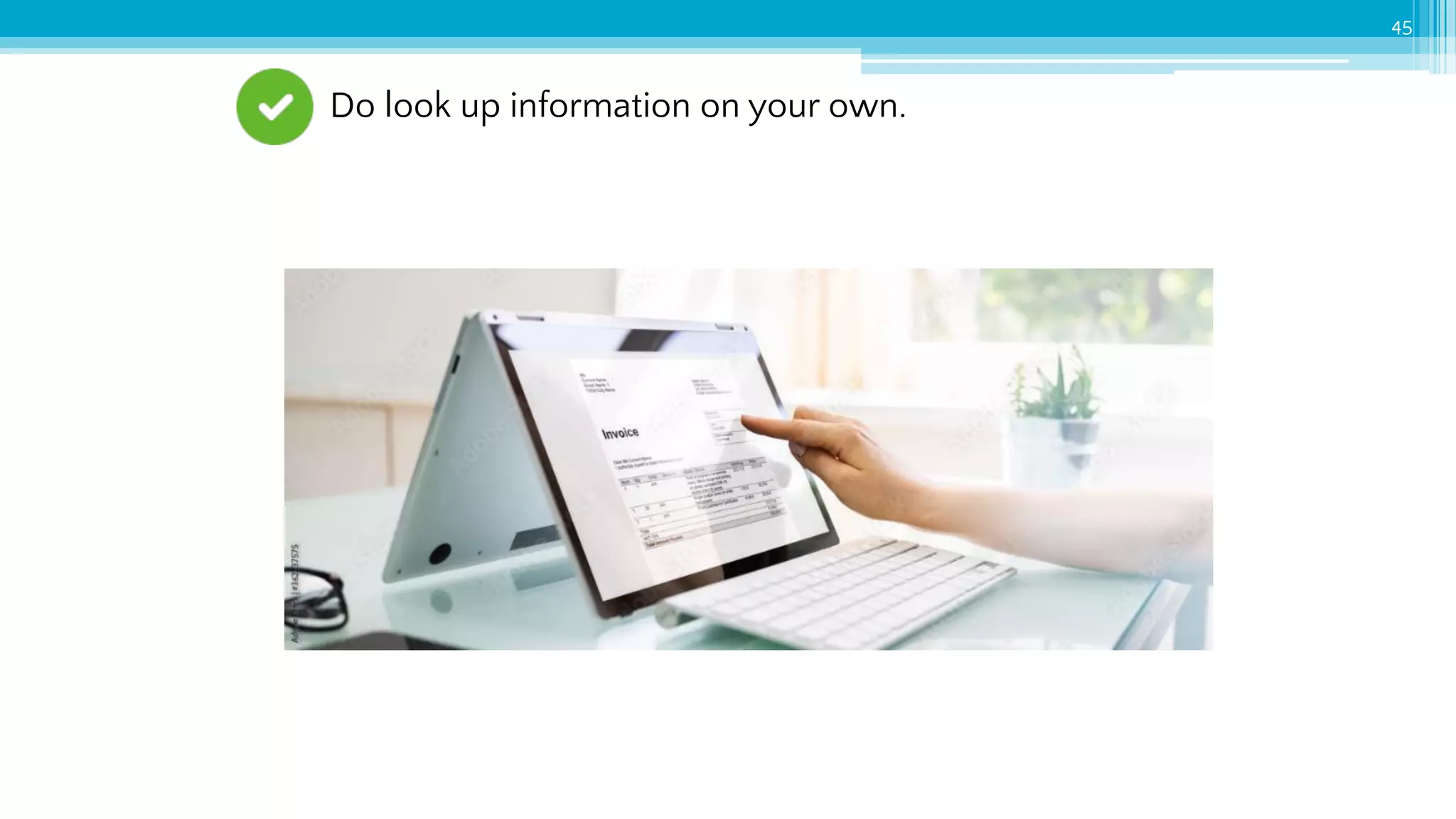
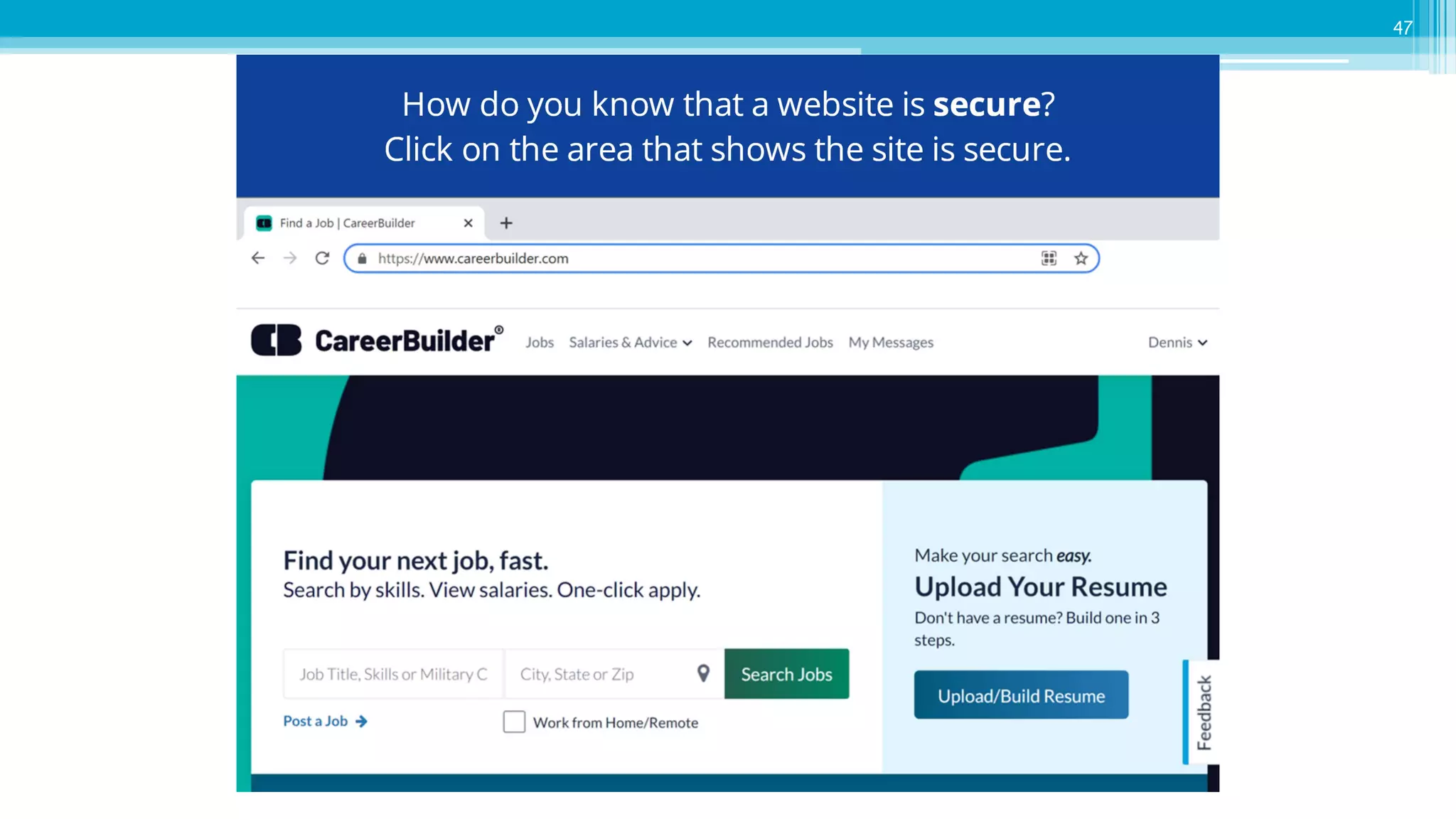
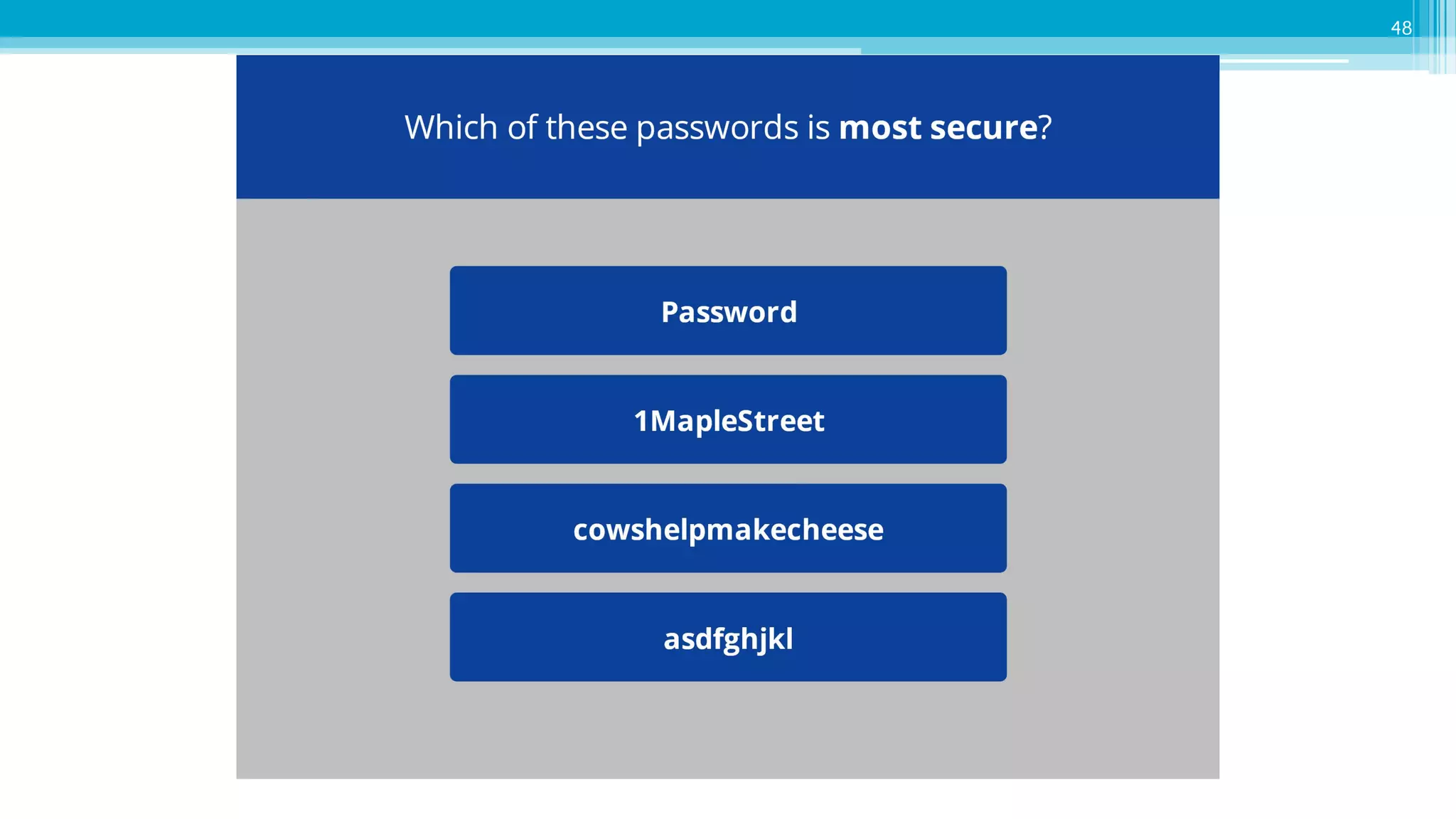
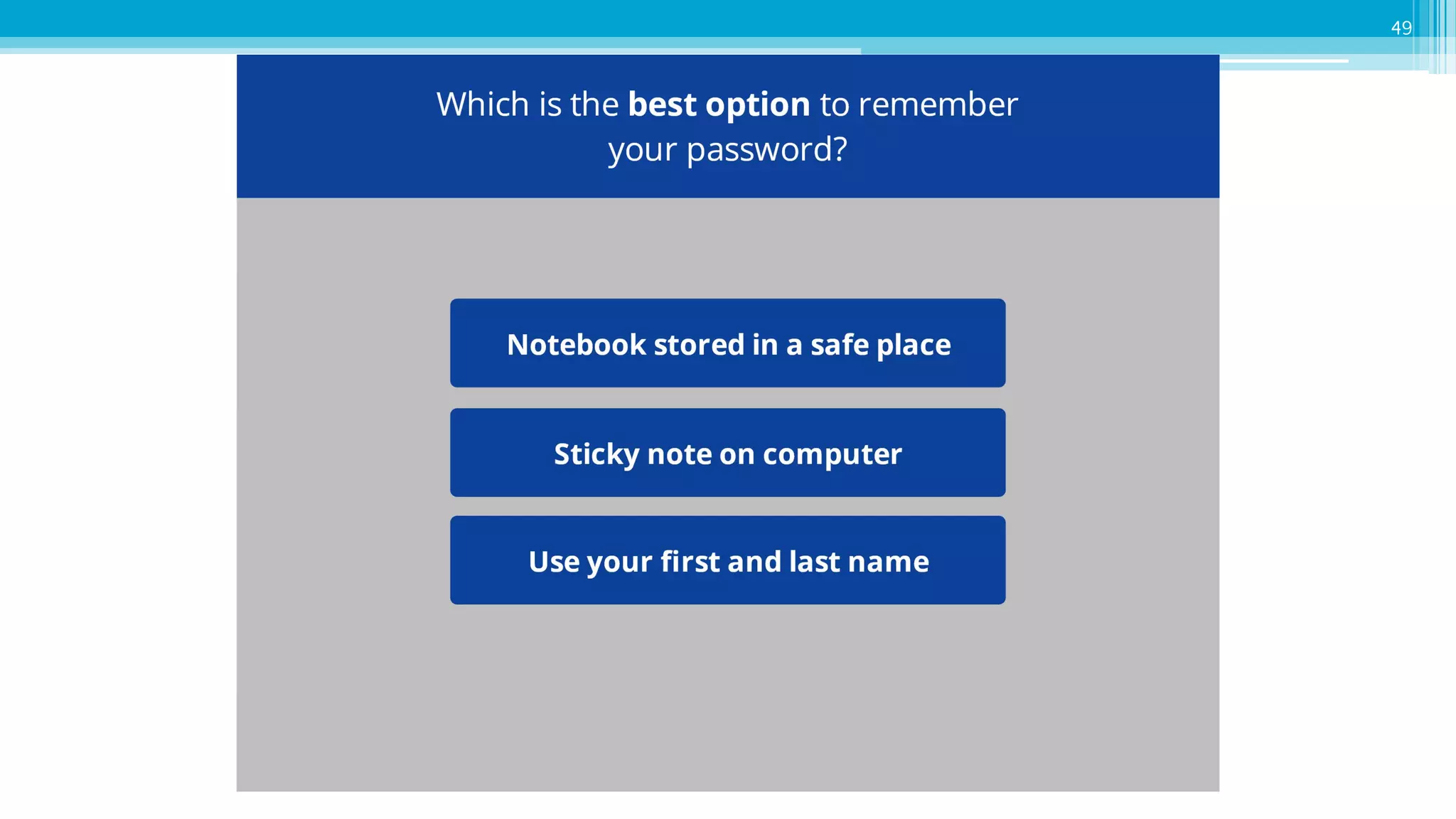
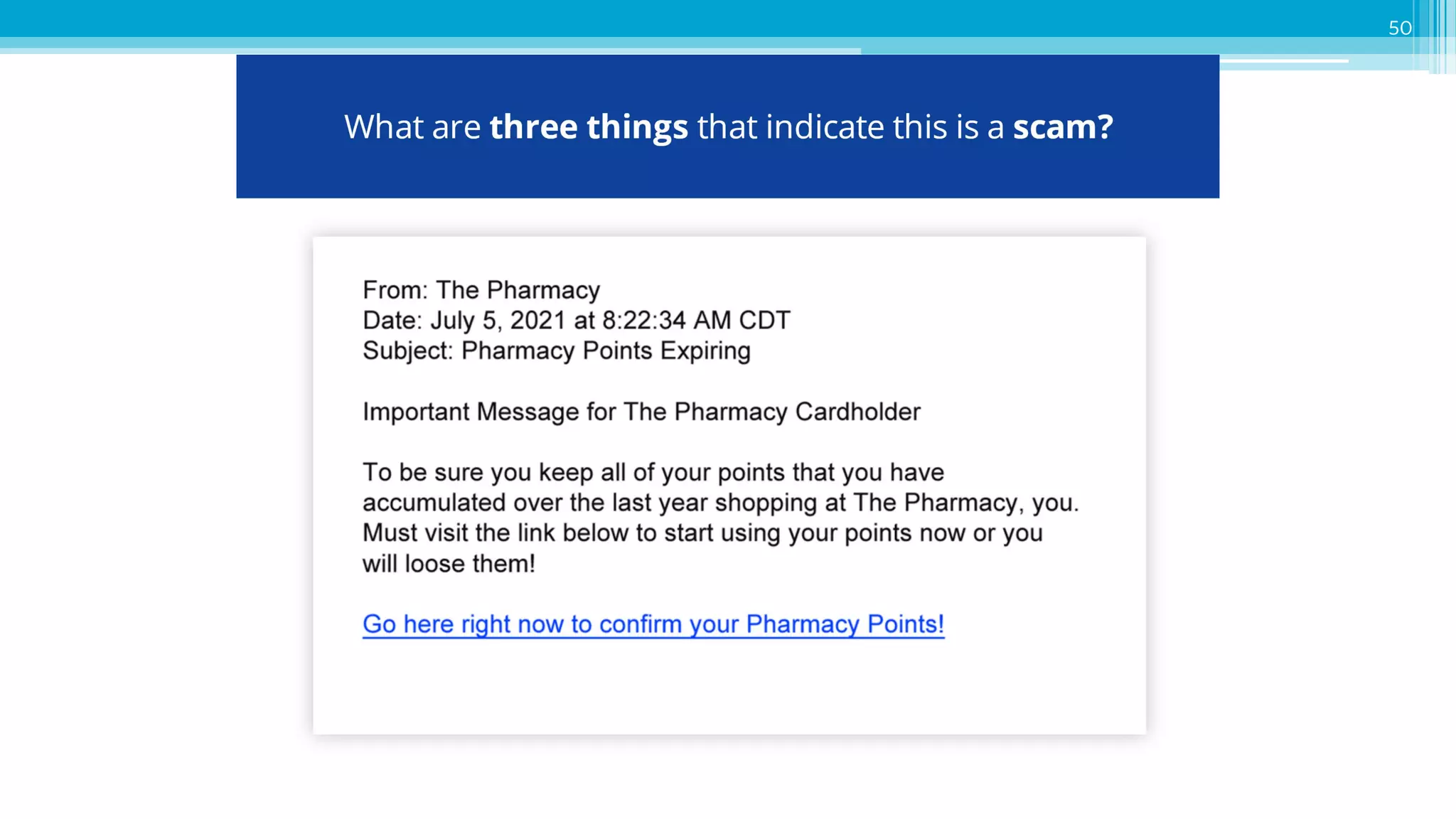
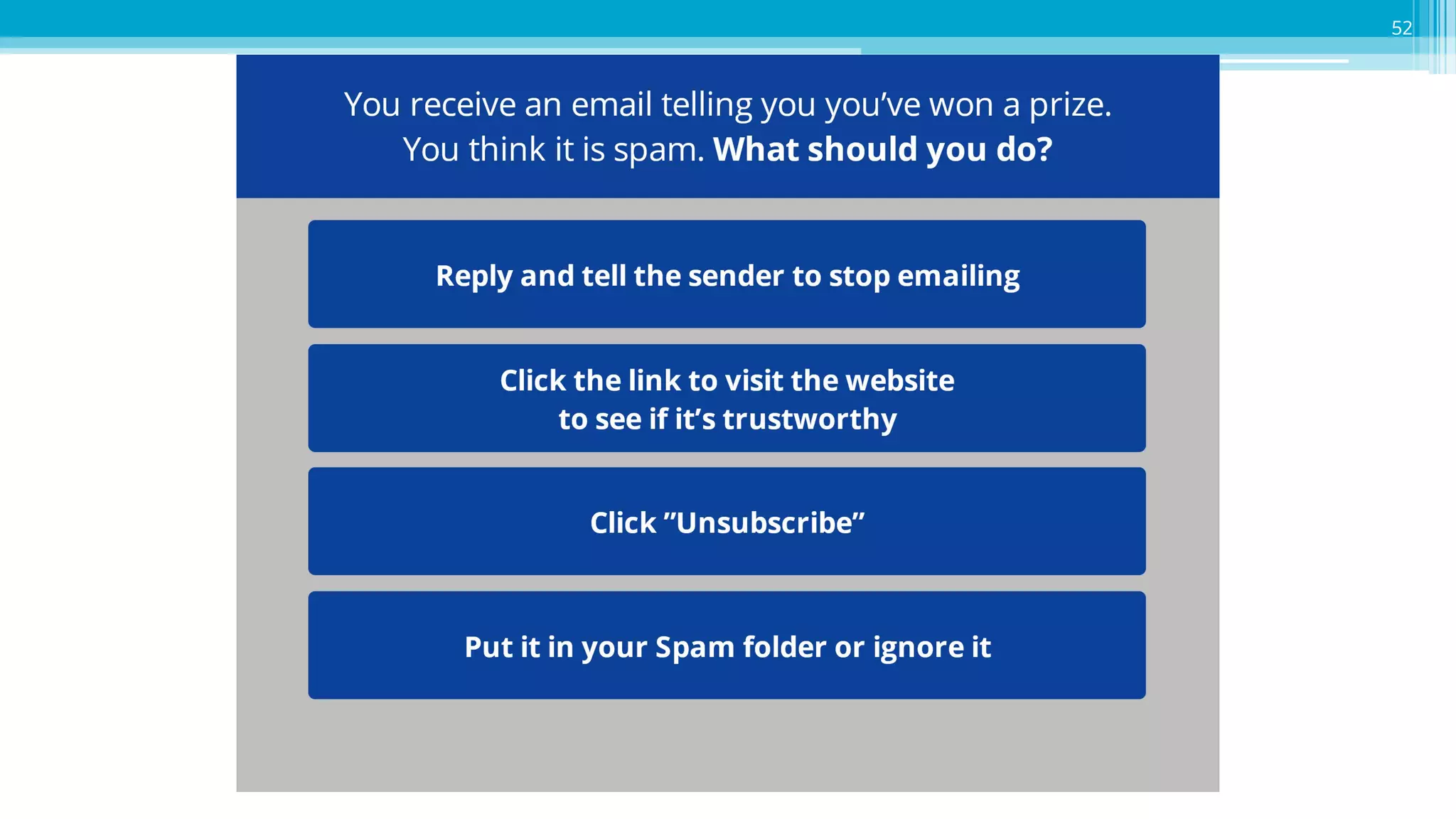
The document provides an introduction to cybersecurity and emphasizes the importance of protecting personal data online. It covers topics such as recognizing secure websites, creating strong passwords, and avoiding online scams, including phishing. Additionally, it offers practical tips and activities to help individuals enhance their online safety.