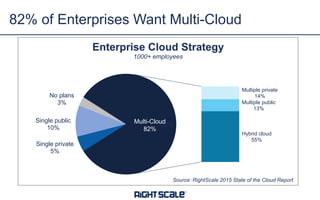
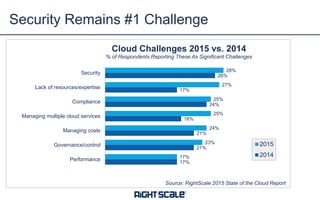
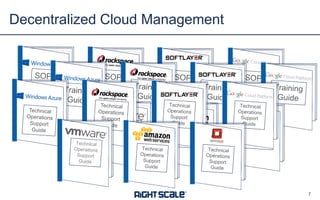
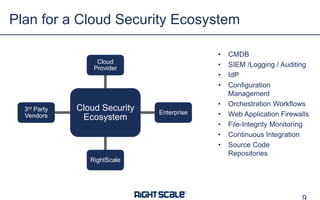
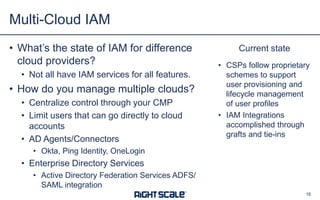
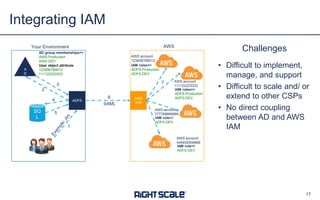
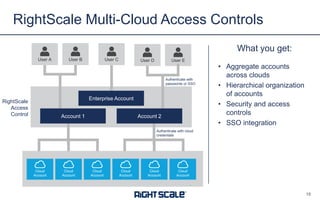
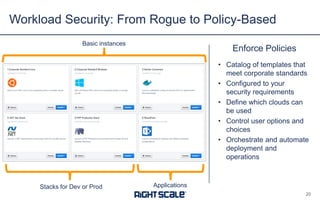
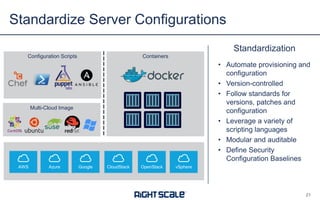
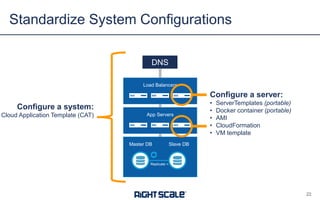
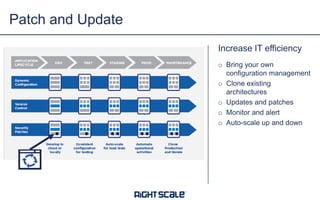
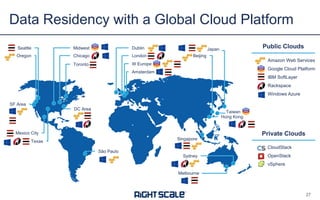
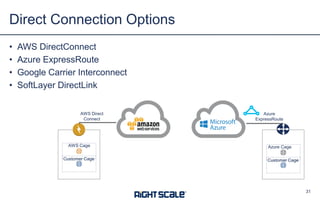
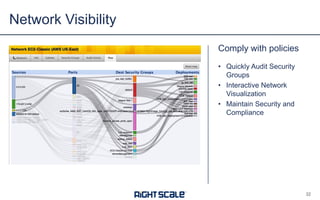
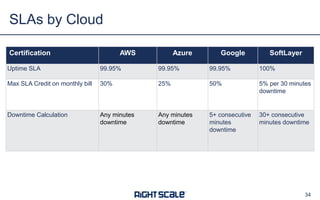
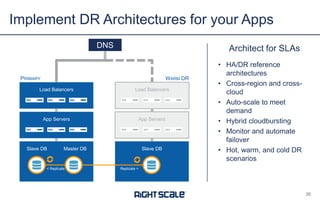
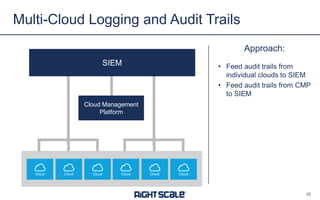
The document outlines eight essential elements of multi-cloud security, including visibility, identity and access control, workload security, data security, network security, business continuity/disaster recovery, audit, and compliance. It highlights the challenges enterprises face, such as security being the top concern, and discusses the need for a security ecosystem involving cloud providers and third-party vendors. Additionally, it emphasizes the importance of standardization, regulatory compliance, and disaster recovery strategies in managing multi-cloud environments.