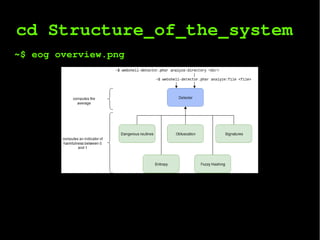
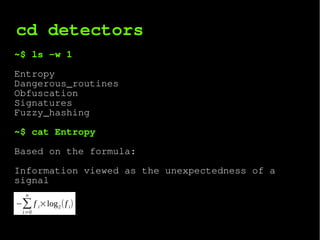
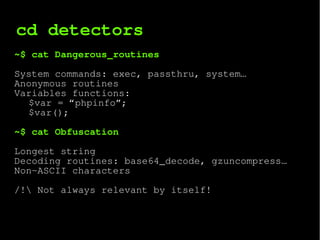
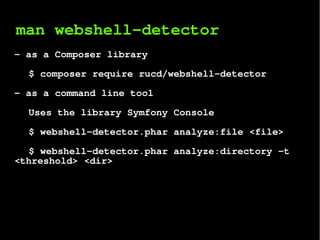
The document describes a webshell detector system that analyzes files and directories for malicious webshells. It uses multiple detection techniques including entropy analysis, checking for dangerous system routines, obfuscation detection, signature matching, and fuzzy hashing. The system is implemented as a Composer library that can also be run as a command line tool to analyze files and directories and detect webshells.