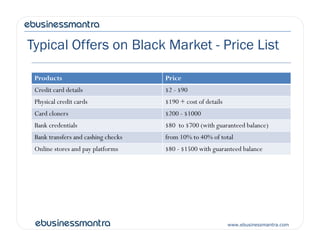
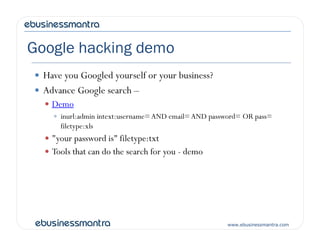
This document outlines the key points from a presentation on online security and privacy issues. It discusses the growing security landscape including major data breaches in 2012. It covers how cybercrime has become a profitable business and ways identities and financial data are sold on the black market. The presentation demonstrates common vulnerabilities like SQL injection and explains how even small businesses are at risk. It provides an overview of strategies to minimize risk, including secure coding practices, scanning tools, and compliance with standards like PCI DSS.