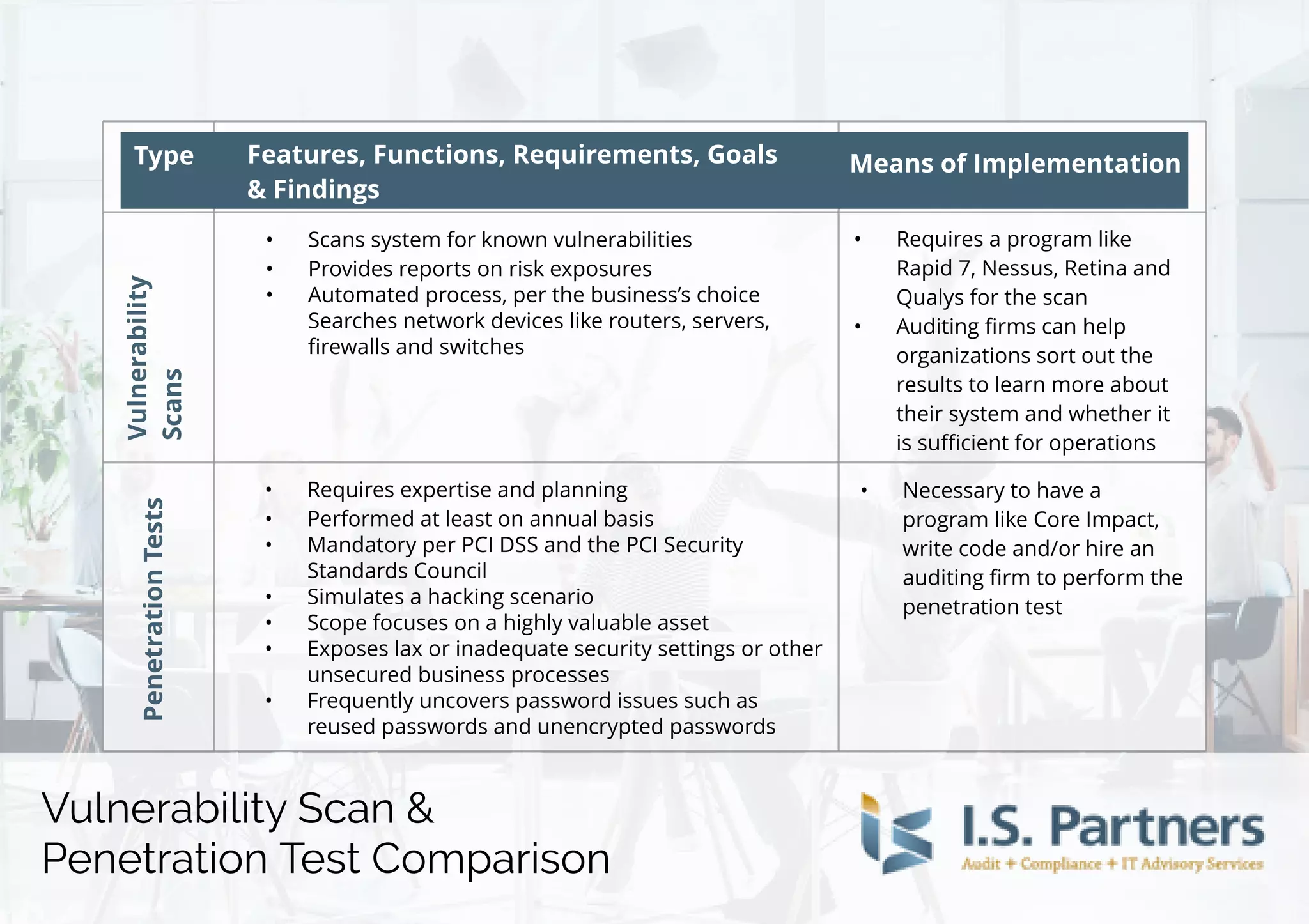
Vulnerability scans and penetration tests are automated processes that assess systems for known vulnerabilities and provide risk exposure reports. These assessments are necessary for compliance with PCI DSS standards and are typically performed annually, requiring expertise and specific scanning tools like Rapid7 or Nessus. They help identify weaknesses in security settings, including password vulnerabilities, and may involve the use of external auditing firms to interpret results.