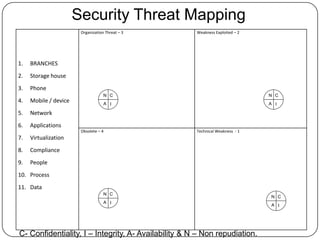
This document introduces a security threat mapping template for tracking threats on a continuous basis. The template is meant to track technical weaknesses, exploited vulnerabilities, and organizational threats. It also tracks the impact areas of confidentiality, integrity, availability, and non-repudiation. The template can be used to highlight existing and planned controls and display residual risk after controls are implemented.