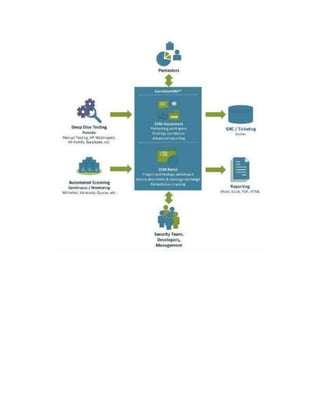
NetSPI's CVM is a management system designed by penetration testers to facilitate operational transformation and scalability of clients' red team and security testing processes. The system lowers risks associated with hosting vulnerable software through efficient and cost-effective workflows with high consistency and quality. NetSPI CVM brings order to challenging vulnerability management efforts, as demonstrated in hundreds of organizations on thousands of engagements, including some of the most critical applications on secure networks.