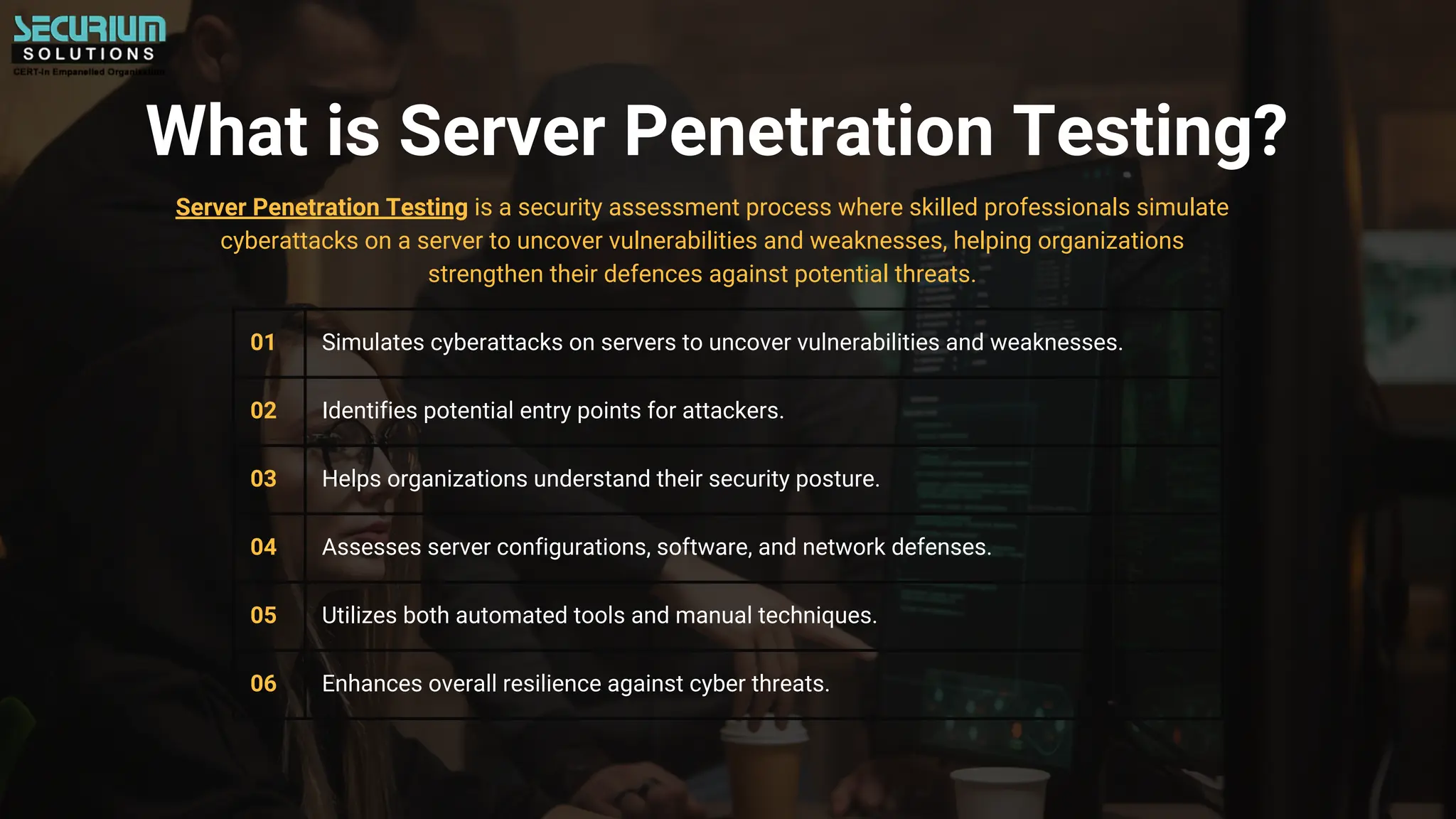
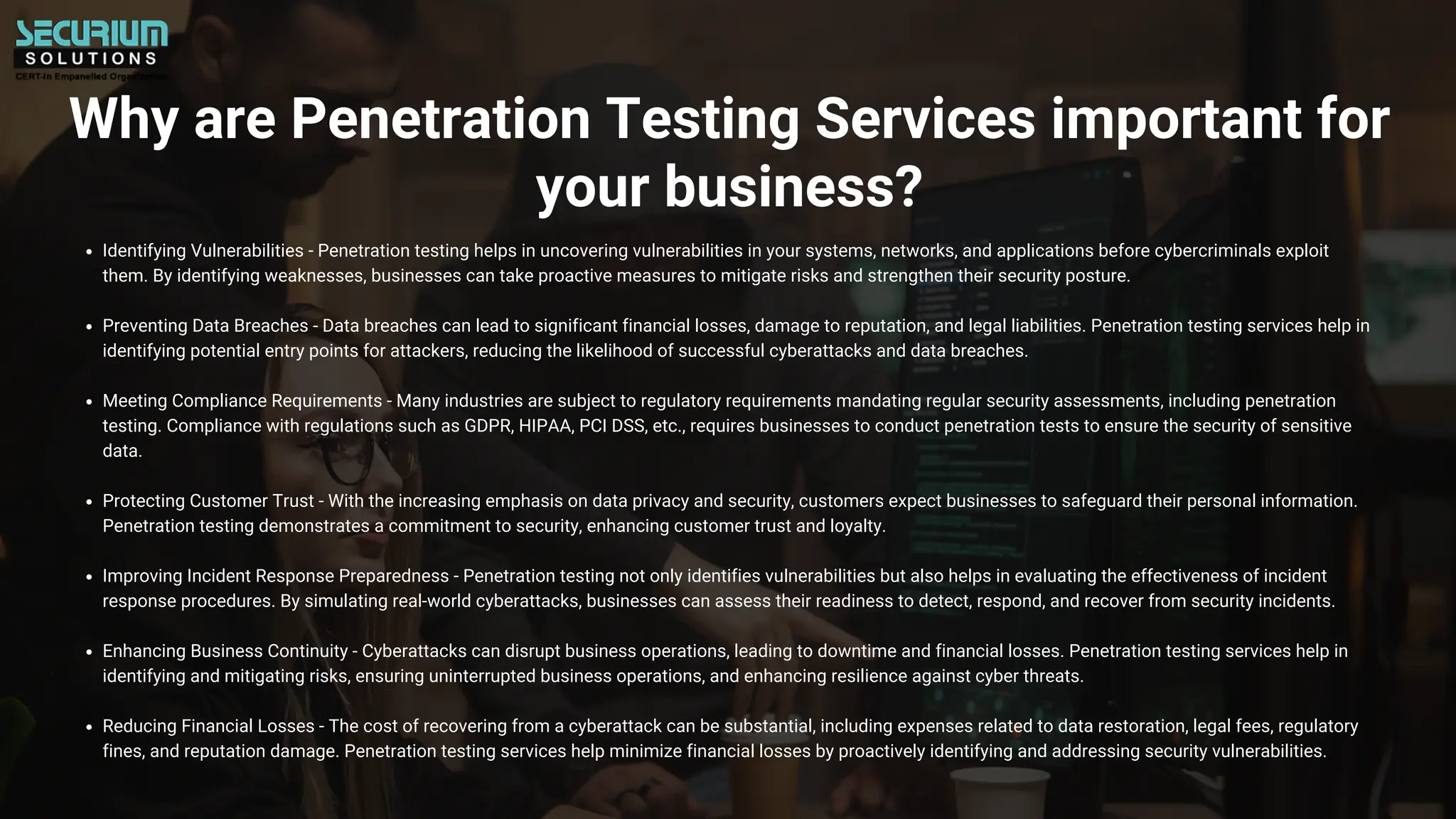
Server penetration testing simulates cyberattacks to uncover vulnerabilities in systems and enhances security measures for organizations. It helps identify entry points for attackers, prevent data breaches, meet compliance requirements, and improve incident response readiness. By proactively assessing and addressing security weaknesses, businesses can ensure better resilience against potential threats and protect customer trust.