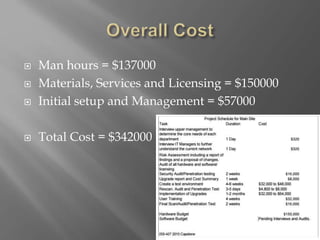
This document provides information about Alpha Team Technologies, a company that has helped businesses reduce IT costs, increase productivity, and streamline operations for 27 years. It discusses Alpha Team's 15-member team and customer-focused approach to providing daily IT support, helpdesk services, and infrastructure monitoring. The document also outlines several IT assessment, optimization, and security services Alpha Team can provide, including baseline assessments, policies and procedures, risk mitigation, backup solutions, hardware upgrades, patching, access controls, and disaster recovery planning. Cost estimates provided include $137,000 for man hours, $150,000 for materials/services/licensing, and $57,000 for initial setup and management, for a total cost of $342