Embed presentation
Download to read offline
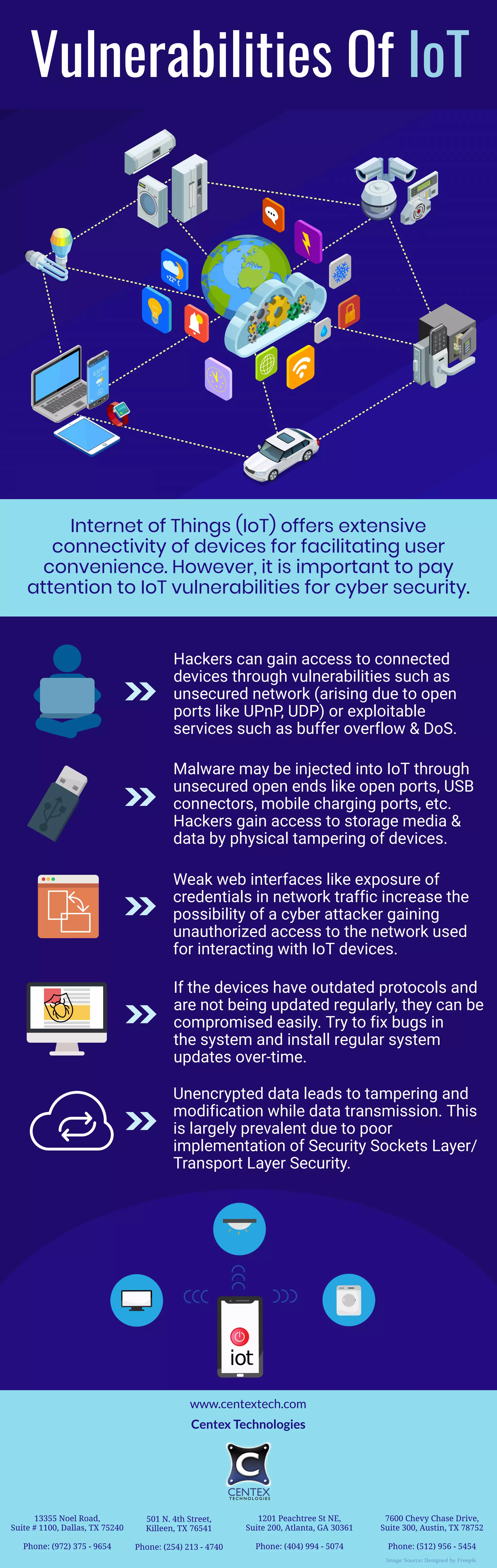
Vulnerabilities in IoT devices can allow hackers to gain unauthorized access. Devices may be compromised through unsecured networks, open ports, exploitable services, or physical tampering. Weak web interfaces that expose credentials or outdated systems without regular updates also increase risk. Unencrypted data transmission leaves the door open for tampering or modification of information as it passes between devices. To enhance security, device owners should ensure their networks are secured, update systems regularly to address bugs, and implement encryption of data in transit.
