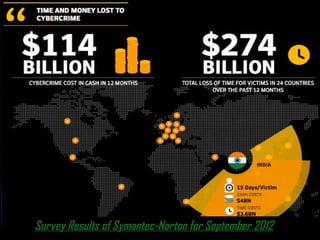
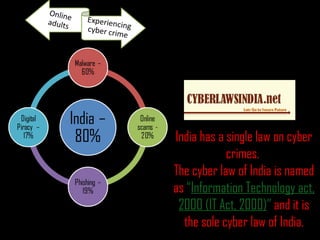
Cybercrime encompasses crimes facilitated by electronic devices, such as child pornography, digital piracy, and cyber terrorism. The Department of Justice categorizes these crimes as targeting others, using computers for traditional crimes, or storing illegal information. India's sole cyber law, the Information Technology Act of 2000, addresses these issues and highlights the significance of security measures like antivirus software and avoiding phishing scams.