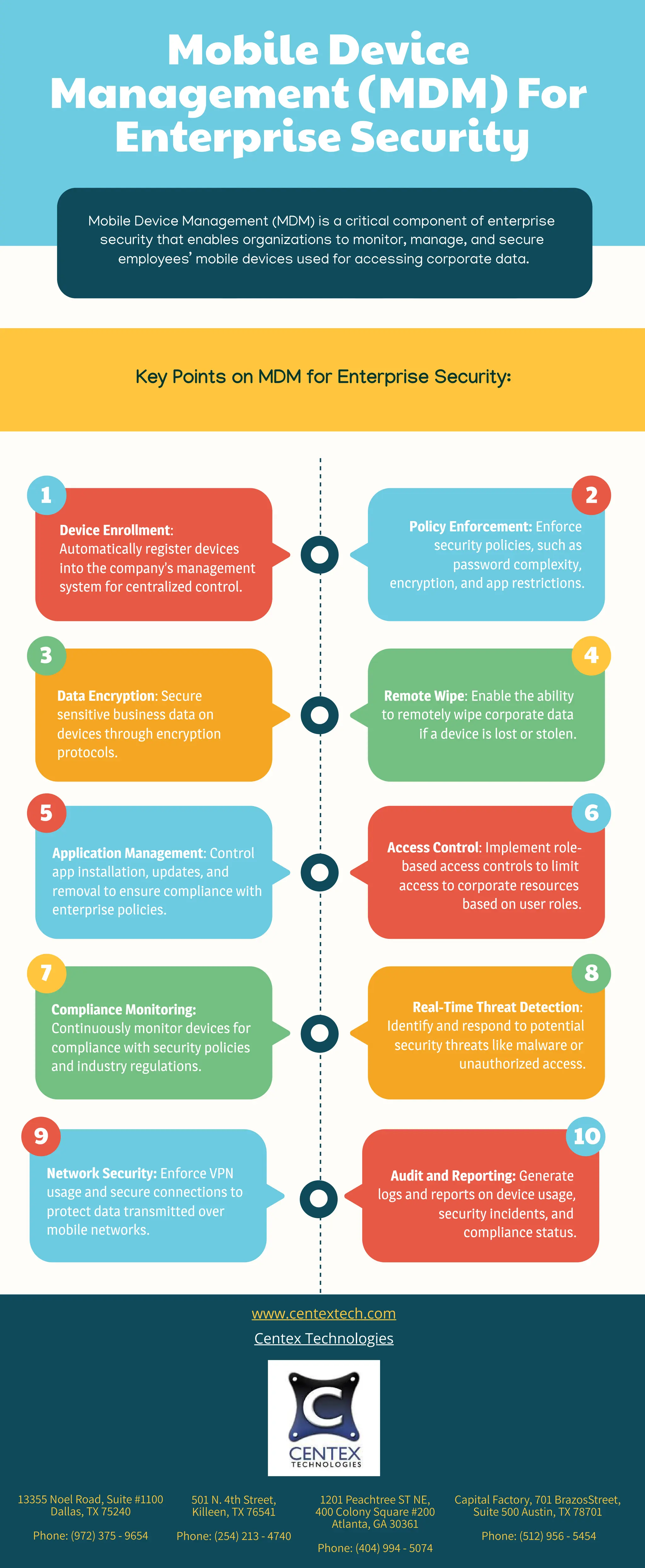
Mobile Device Management (MDM) is essential for enterprise security, allowing organizations to manage and secure mobile devices accessing corporate data. Key features include device enrollment, policy enforcement, data encryption, remote wipe capabilities, application management, access control, compliance monitoring, real-time threat detection, network security, and audit reporting. These tools help ensure that enterprises maintain a secure and compliant mobile environment.