Embed presentation
Download to read offline
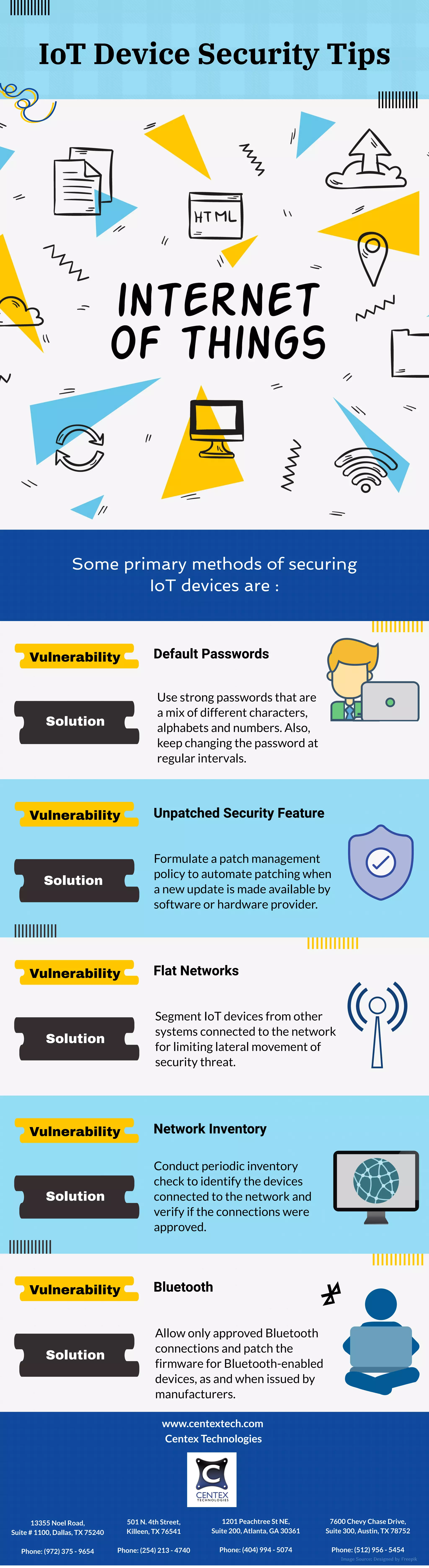
Some key methods for securing IoT devices include using strong and unique passwords that are changed regularly, keeping systems updated by automating security patches, segmenting IoT networks from other systems to limit threats, periodically inventorying connected devices to identify unauthorized access, and only allowing approved Bluetooth connections while keeping Bluetooth firmware up to date.
