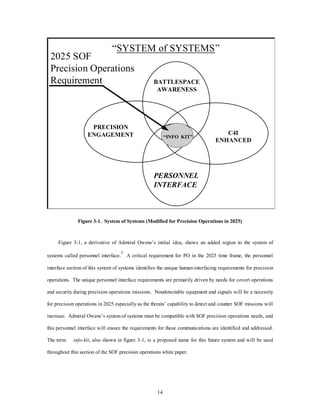
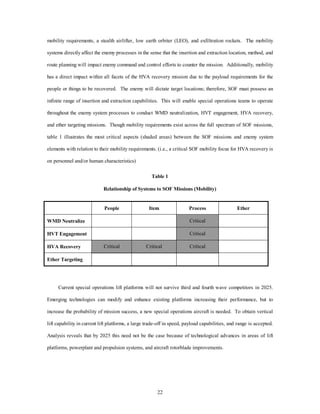
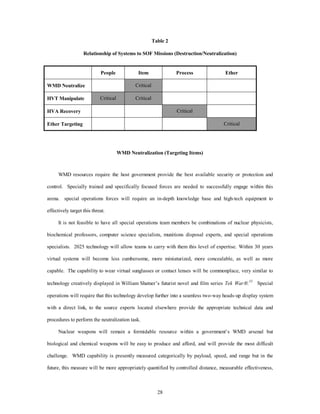
This document summarizes a research paper presented to Air Force 2025 that outlines special operations forces capabilities needed to conduct precision operations against weapons of mass destruction, high-value targets, and assets in the hypothetical world of 2025. The paper identifies communications, mobility, and destruction/neutralization as the top three enabling capabilities required for these missions. It then proposes various futuristic technologies that could fulfill requirements for these capabilities by 2025, such as stealth airlifters, extraction rockets, and targeting systems, to allow special operations forces to accomplish their missions with zero tolerance for error.